Password security is one of the most important aspects of protecting your network and data from unauthorized access. Weak passwords can be easily guessed or cracked by attackers, compromising your systems and accounts. Therefore, it is essential to enforce strong password policies that require users to create complex and unique passwords that are hard to break. There has been a shift from the recommendation of shorter passwords that replace vowels with numbers and symbols to longer passwords that consist of phrases that are easy for the end users to remember. As such, a maximum configurable value of 14 for the minimum password length in Windows Server environment may be too short.
In this blog post, I will show you how to set up environments consisting of Windows Server 2022, Windows 10, and Windows 11 to enforce all users to set account passwords to be more than 14 characters long using a standard Group Policy Object (GPO). This will use the RelaxMinimumPasswordLengthLimits, MinimumPasswordLengthAudit, and MinimumPasswordLength Group Policy settings.
The default minimum password length in Windows is 8 characters, which is not enough to withstand brute force attacks that try every possible combination of characters. According to Microsoft, a password with 8 characters can be cracked in less than 2.5 hours, while a password with 14 characters can be substantially longer.
In Windows Server environments, the longstanding maximum value that can be set for the MinimumPasswordLength Group Policy settings is 14. Outside of using a Fine-grained Password Policy assigned to security groups, there is no way to require passwords longer than 14 characters in Windows.
To overcome this limitation, you need to enable the RelaxMinimumPasswordLengthLimits policy setting, which allows you to set the minimum password length to any value from 1 to 255. This setting works together with the MinimumPasswordLengthAudit and MinimumPasswordLength settings, which let you specify the minimum password length and audit the password changes that do not meet the requirement.
How to Configure the Password Policy Settings
To change the password policy settings in Windows Server 2022, you can follow these steps:
- Open the Group Policy Management Console (GPMC).
- Expand the Domains folder, choose the domain whose policy you want to access and choose Group Policy Objects.
- Right-click the Default Domain Policy GPO and click Edit.
- Navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy.
- Change “Relax minimum password length limits” to Enabled
- Change “Minimum password length audit” to the number of characters you want the minimum password length to be.
- Change “Minimum password length” to to the number of characters you want the minimum password length to be.
For more information on this Microsoft has this support article: Minimum Password Length auditing and enforcement on certain versions of Windows – Microsoft Support
Configuration Recommendations to Force Password Length Longer Than 14 Characters
The following gives more detail for each setting that you need to configure to enforce strong passwords in your environment:
Name: RelaxMinimumPasswordLengthLimits
Description: Allows you to set the minimum password length to any value from 1 to 255.
Value to require passwords greater than 14 characters: Enabled
Name: MinimumPasswordLengthAudit
Description: Specifies the minimum number of characters that a password must contain. If a user tries to change their password to a value that is shorter than this number, the system will generate a warning event in the Security log.
Value to require passwords greater than 14 characters: 15 or higher
Name: MinimumPasswordLength
Description: Specifies the minimum number of characters that a password must contain. If a user tries to change their password to a value that is shorter than this number, the system will reject the change and display an error message.
Value to require passwords greater than 14 characters: 15 or higher
Other Settings
In addition to the above, here is more detail on the remaining settings:
Name: Password must meet complexity requirements
Description: Determines whether passwords must meet a series of strong-password guidelines, such as containing characters from different categories and not including the username or full name.
Name: Enforce password history
Description: Determines the number of unique new passwords that must be associated with a user account before an old password can be reused.
Name: Maximum password age
Description: Determines the period of time (in days) that a password can be used before the system requires the user to change it.
Name: Minimum password age
Description: Determines the period of time (in days) that a password must be used before the user can change it.
Each of those settings should be thoughtfully considered to be a good mix of security and user acceptance.
By enforcing strong password policies, you can enhance the security of your network and data and comply with the best practices and standards.
Have any questions about how to use the Group Policy Object to enforce users to use long passwords over 14 characters in Windows? Please feel free to reach out to our experts at any time!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.
По умолчанию, для локальной учетной записи Windows 10 нет ограничения на длину пароля: в принципе, можно вообще не задавать пароль. Однако, при необходимости, вы можете установить минимальную длину пароля несколькими способами: это редко требуется домашним пользователям, но может пригодиться в организации.
В этой инструкции подробно о том, как установить минимальную длину пароля Windows 10 для локальной учетной записи 2-мя способами: в командной строке или редакторе локальной групповой политики. Также может быть интересным: Как ограничить количество попыток ввода пароля Windows 10, Как ограничить срок действия пароля Windows 10, Как отключить запрос пароля при входе в Windows 10 и при выходе из режима сна.
Установка ограничения на длину пароля в командной строке
Самый простой метод установить минимальную длину пароля — использовать командную строку:
- Запустите командную от имени администратора, в Windows 10 для этого удобно использовать поиск в панели задач, но есть и другие способы.
- В командной строке введите следующую команду, нажав Enter после неё:
net accounts /minpwlen:N
В этой команде вместо N вставьте необходимое число (от 0 до 14), которое и задаст минимальное количество символов в пароле.
На этом процесс завершен, минимальная длина пароля установлена. Если вам потребуется отменить ограничение, просто установите его равным 0.
Внимание: на текущий пароль это изменение не повлияет (то есть если он меньше нужного, вам об этом не сообщат), но при смене пароля или при установке пароля для нового пользователя задать пароль меньшей длины уже не получится, о чем вы увидите уведомление, например, как на скриншоте ниже.

В редакторе локальной групповой политики
Если на вашем компьютере установлена Windows 10 Pro, корпоративная или для образовательных учреждений, то подойдет следующий метод:
- Нажмите клавиши Win+R на клавиатуре, введите gpedit.msc и нажмите Enter. Откроется редактор локальной групповой политики.
- Перейдите в раздел «Конфигурация компьютера» — «Конфигурация Windows» — «Параметры безопасности» — «Политики учетных записей» — «Политика паролей».
- Дважды нажмите по параметру «Минимальная длина пароля» и задайте нужное значение, не превышающее 14.
После применения настроек будет установлена минимальная длина пароля Windows 10 при следующей его смене или при установке паролей для новых пользователей. Напомню, речь идет только о локальных аккаунтах, здесь может оказаться полезным: Как создать локальную (автономную) учетную запись при установке Windows 10 Домашняя.
How to Set Minimum Password Length on Windows 10
In today’s digital landscape, the security of our personal information is paramount, especially when using devices connected to the internet. One of the most fundamental ways to protect your data is through strong passwords. Windows 10 provides users with the ability to set policies that govern password complexity and length, which can significantly enhance the security of your system. In this article, we will explore the steps to set a minimum password length on Windows 10, the significance of this setting, and additional best practices for managing passwords securely.
Understanding Password Policies
Before we dive into the specifics of setting a minimum password length, let’s first understand what password policies are and their relevance to security.
Password policies are rules established by system administrators that dictate how passwords must be created, managed, and updated. These policies are crucial for maintaining the integrity of user accounts and minimizing the risk of unauthorized access. Some common password policy components include:
- Minimum Password Length: This specifies the shortest allowable password, encouraging users to create more secure passwords.
- Password Complexity Requirements: This includes stipulations on using uppercase letters, lowercase letters, numbers, and special characters.
- Maximum Password Age: This dictates how long a password can be used before it must be changed.
- Account Lockout Policy: This outlines what happens after a certain number of failed login attempts, such as locking the account temporarily.
By implementing these policies, organizations and individual users can bolster their defenses against various forms of cyberattacks, such as brute-force attacks.
Why Set a Minimum Password Length?
The minimum password length plays a crucial role in strengthening security. Short passwords are inherently weaker and easier for attackers to guess or crack using automated tools. Here are a few reasons to enforce a minimum password length:
- Increased Resistance to Cracking: Longer passwords significantly increase the number of possible combinations, making it exponentially harder for attackers to use brute-force methods.
- Improved Security Awareness: Setting a minimum length compels users to think about password creation and fosters a culture of security awareness.
- Regulatory Compliance: Many industries require adherence to specific security standards, including password policies, to protect sensitive data.
How to Set Minimum Password Length on Windows 10
There are multiple ways to set the minimum password length in Windows 10, including using the Local Group Policy Editor for Professional or Enterprise editions and using the Registry Editor for all editions of Windows 10. Below, we’ll cover the step-by-step process for each method.
Method 1: Using Local Group Policy Editor
The Local Group Policy Editor is a powerful tool available in Windows 10 Professional, Enterprise, and Education editions. It’s designed for system administrators to configure and manage operating system, application, or user settings.
Step 1: Open the Local Group Policy Editor
- Press
Windows + Rto open the Run dialog box. - Type
gpedit.mscand press Enter. This will launch the Local Group Policy Editor.
Step 2: Navigate to Password Policy
- In the left pane, expand the following folders:
Computer ConfigurationWindows SettingsSecurity SettingsAccount PoliciesPassword Policy
Step 3: Set Minimum Password Length
- In the right pane, double-click on the “Minimum password length” setting.
- A new window will appear. Select the Enabled option.
- Enter the desired minimum password length (the default is usually set to 0, meaning there’s no minimum).
- Click OK to save your changes.
Step 4: Close the Local Group Policy Editor
You can now close the Local Group Policy Editor. The new minimum password length policy will take effect after the next user logs in or the system is rebooted.
Step 5: Testing the Policy
To test whether the policy has taken effect, log out of your current session or restart your computer. Try to change your password through the Settings app or Control Panel. If the system requires a password that meets the new minimum length, you have successfully set the policy.
Method 2: Using Registry Editor
For users of Windows 10 Home or anyone who prefers using the Registry Editor, here’s how to set a minimum password length:
Step 1: Open Registry Editor
- Press
Windows + Rto open the Run dialog. - Type
regeditand press Enter. Click Yes if prompted by User Account Control.
Step 2: Navigate to the Password Policy Key
- In the Registry Editor, navigate to the following path:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem
Step 3: Create or Modify ‘MinimumPasswordLength’
- In the right pane, look for an entry named “MinimumPasswordLength”. If it doesn’t exist, you will need to create it.
- Right-click in the right pane, hover over New, and click DWORD (32-bit) Value.
- Name the new value MinimumPasswordLength.
- Double-click on MinimumPasswordLength and set the Value data to your desired minimum password length (e.g., 8).
- Click OK to save the changes.
Step 4: Exit Registry Editor
After making these changes, close the Registry Editor. The minimum password length policy will apply after the next login or system restart.
Step 5: Verifying the Change
Just like before, log out or restart your system and try changing your password to see if the new policy is enforced.
Additional Password Management Best Practices
Setting a minimum password length is an excellent step towards improving security, but it’s just one part of a more extensive password management strategy. Here are some additional best practices you can adopt:
-
Use Password Managers: Password managers can generate and store complex passwords for you, so you don’t have to memorize them. They help ensure that each password is unique and complex.
-
Implement Multi-Factor Authentication (MFA): Whenever possible, enable MFA on your accounts. This provides an extra layer of security by requiring another form of verification, such as a text message code, in addition to your password.
-
Educate Yourself and Others: Stay informed about the latest security practices and potential threats. Share this knowledge with family, friends, or colleagues to help them protect their sensitive information.
-
Regularly Update Passwords: Regularly updating your passwords can minimize the risk of accounts being compromised, especially if you suspect a data breach.
-
Avoid Common Passwords: Do not use easily guessable passwords like “123456”, “password”, or your name. Always opt for a unique combination of characters.
-
Don’t Share Passwords: Never share your passwords with others. If necessary, use secure password management tools that allow sharing without revealing the actual password.
-
Be Wary of Phishing Scams: Always be cautious of emails or messages that request personal information, including passwords. Look for signs of phishing attempts, such as suspicious links or addresses.
-
Use Different Passwords for Different Accounts: Using unique passwords for each account minimizes the risk of widespread compromise if one password is breached.
Conclusion
Setting a minimum password length on Windows 10 is a straightforward yet crucial step in safeguarding your digital life from unauthorized access. By understanding and implementing password policies, utilizing tools like Local Group Policy Editor or the Registry Editor, and adhering to password management best practices, you can significantly enhance the security posture of your device and accounts.
While technology continues to advance, cyber threats evolve alongside it. Thus, a proactive approach to security—starting with enforceable password policies—will serve you well in protecting your personal information. As you navigate the digital world, remain vigilant and adaptable, ensuring that your security measures keep pace with emerging threats.
By taking steps to strengthen your password practices today, you’ll be better prepared for the challenges of tomorrow.
-
Home
-
Partition Manager
- How to Set a Minimum Password Length in Windows 10 [2 Ways]
By Linda | Follow |
Last Updated
Setting a minimum password length for your local user accounts can ensure the security of the accounts. In this post, MiniTool shows you how to set a minimum password length in Windows 10 with 2 ways.
In general, Microsoft requires a minimum password length for all Microsoft accounts, while the local user accounts on Windows 10 don’t require a password by default. The minimum password length is an effective way to secure your account.
Windows 10 Local Account VS Microsoft Account, Which One to Use?
By setting a minimum password length for each user on Windows 10, you can reinforce all local accounts. Then, there are a couple of ways to apply the minimum password length to your accounts. You can get them in the following content.
Set a Minimum Password Length Via Command Line
This method works well in all Windows 10 editions, including Home Edition, Pro Edition, etc. The, follow the steps below to set a minimum password length with command lines:
Step 1: Run Command Prompt or PowerShell as administrator.
- Use Command Prompt:click the Start button, type “cmd” into the search box, then right-click on the “Command Prompt” result, and select “Run As Administrator”.
- Use PowerShell:Press “Windows + X” keys simultaneously and then click “PowerShell (Admin)”.
Step 2: Type the following command “net accounts /minpwlen:#”. Please note that “#” is a number that stands for the minimum password length. You should replace it accordingly. Then, press the Enter key, and you’ll see a prompt telling you the command completed successfully.
Tip: You can technically choose anything from 1-20 characters in length. But I recommend you to choose something that provides adequate security and doesn’t make it too difficult to remember the passwords.
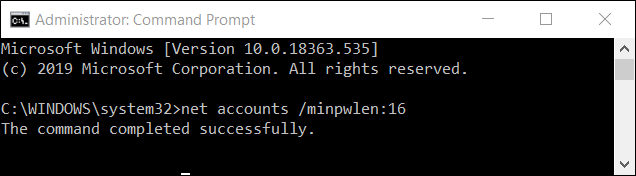
Now, the minimum password length is set. If you want to make sure it’s been applied, you can enter the following command to check: “net accounts”. If you want to remove the minimum password length, you can enter the following command: “net accounts /minpwlen:0”.
Set a Minimum Password Length Via Group Policy
This method is only available in Windows 10 Pro and Enterprise Edition. If you are using Pro or Enterprise Edition and you don’t want to mess around with Command Prompt, you can take advantage of the Local Group Policy Editor, which takes a graphical interface. The detailed steps are as follows:
Tip: Before you making changes to Group Policy, you should make a System Restore point in case some errors happen.
Step 1: Press “Windows+R” keys, type “gpedit.msc” into the Run box, and then press the Enter key to open the Local Group Policy Editor.
Step 2: Navigate to Computer configuration > Windows settings > Security settings > Account policies > Password policy. Then, double-click the setting “Minimum password length”. This will trigger a new window.
Step 3: In the new window, type in the minimum password length you want to apply and click OK button when you finish.
Tip: There is a setting “Password must meet complexity requirements”. If you enable it, when you next change or create passwords, the passwords must meet specific criteria. Thus, your passwords can be more secure.
About The Author
Position: Columnist
Linda has been working as an editor at MiniTool for 5 years. She is always curious about computer knowledge and learns it crazily. Her articles are simple and easy to understand. Even people who do not understand computer can gain something. By the way, her special focuses are disk management, data recovery and PDF editing.
Setting and enforcing a policy for strong passwords should be a top priority for organizations in their cyber hygiene practice. Best practices and recommendations keep being updated since this issue is so critical for attack prevention. In fact, compromised passwords are responsible for 81% of successful attacks.
Changing passwords setting configuration is part of the hardening task. Making sure all machines are configured correctly and that nothing breaks because of the configuration change, makes this task very complex. Many organizations do not change password configuration due to these challenges, resulting in an increased attack surface. To overcome these challenges, we recommend using hardening automation tools. These tools will let you know the impact of each change and will automatically enforce your desired settings on your production.
This guide will screen the recommendations of two cyber industry best practices publishers – the Center for Internet Security (CIS) password setting recommendations and the National Institute of Standard and Technology (NIST) recommendations. CIS recommendations are based on the 2019 CIS Benchmarks. NIST recommendations are taken from the NIST Digital Identity Guidelines, updated in 2020.
This guide will help you build a password policy suitable for your organization. It will cover the following topics:
- Microsoft Local Administrator Password Solution (LAPS).
- Password age and expiration time.
- Local admin password management.
- Password length and complexity.
Microsoft Local Administrator Password Solution (LAPS):
LAPS is a free tool provided by Microsoft for Windows Server environments, that allows organizations to automatically set randomized, strong passwords to domain-attached workstations and Member Servers. The passwords are stored confidently in the domain account and can be accessed from the Active Directory by a sysadmin. The LAPS provides a solution for using an identical password on all domain computers by default.
To install LAPS you need to update the AD schema and the installation of Group Policy Client Side Extension (CSE). This CSE is not installed by default, and it is recommended by the CIS to ‘Ensure LAPS AdmPwd GPO Extension / CSE is installed’. This is a key step in managing server types and Group Policy Objects (GPOs) effectively.
Password Age and Expiration Time:
There are two different approaches when setting password’s age and expiration time:
CIS Password Age Recommendations:
In the CIS Benchmarks there are 2 rules that address this issue:
- Do not allow password expiration time longer than required by policy – which means that according to the CIS you should set a period that after acceding it, the password should expire
- Ensure ‘Password Settings: Password Age (Days)’ is set to ‘Enabled: 30 or fewer’ (for domain members, and Member Servers).
NIST Password Age Recommendations:
According to the NIST Identity Guidelines, frequent password changes can worsen security, increasing the potential impact of certain types of cyber attacks. NIST claims that since the main challenge in setting a good password is to remember it, and it is often that users must have many different passwords to remember, passwords change policy will result in users changing passwords in predictable patterns.
In this case, if an attacker knows the user’s previous password, cracking the new one won’t hold a challenge. Therefore, according to NIST, you should avoid requiring a periodic password change.
Local Admin Password Management:
Using the same password on all workstations and Member Servers on deployment is a common practice in many organizations. The main reason for that is the difficulty in managing local Administrator’s passwords.
This practice is a major risk to the organizations since if an attacker compromises one system and gets access to its password, he can leverage it to gain access to all other machines using the same password. Therefore, Enabling Local Admin Password Management and installing LAPS will enforce random passwords on each machine and solve this issue.
Note! When enabling a local admin password, if you need to retrieve a local Administrator password and the AD is not available (for example, when recovering from an attack), you won’t be able to. In this case, consider using a local password reset tool.
Minimum Password Length & Complexity Requirements:
Password length is critical for lowering the chance of attackers hacking it. Longer passwords take longer to crack, so when they configure the passwords, organizations should take care to ensure they are long enough. The CIS recommends requiring users to set aminimum password length of at least 14 characters long. CIS security configuration is:
Ensure ‘Minimum password length’ is set to ’14 or more character(s)’ (Automated)
The recommended state for this setting is: 14 or more character(s).
Password complexity is a different issue, and in this case, the CIS and NIST hold different approaches complexity requirements policy setting.
CIS password complexity recommendations:
According to the CIS Benchmarks, you should ensure that ‘Password must meet complexity requirements’ is set to Enabled. This policy will require the user to set his password according to the following rules:
- Password should not contain the user’s account name or parts of his full name (more than two consecutive characters).
- Have at least six characters.
- Contain uppercase characters, lowercase characters, digits, and non-alphabetic characters.
While it is reasonable to think that using complex passwords will improve security, NIST suggests a different approach for this issue.
How Hardening is Reflected in the Different NIST Standards
NIST password complexity recommendations:
Research shows that requiring password complexity may actually be a poor security practice. According to NIST, you can predict the patterns most users will use to solve the challenge of adding complexity for their passwords. For example, a common scenario to see is users capitalizing the first letter of their password or adding ‘1’ or ‘!’ at its end. Attackers know those common patterns, and they will use them when trying to decrypt stolen passwords in a brute force attack. In addition, adding complexity will increase user’s tendency to reuse passwords, which can further expose them to credential stuffing attack, if one of their accounts have been breached.
For these reasons, password complexity can result in increasing the attack surface. NIST recommends concentrating on minimum password length to lower the attack surface, in addition to following key Windows password guidelines.



