Windows 10: Workplace Join -> Automatic Device-Join task
Discus and support Workplace Join -> Automatic Device-Join task in Windows 10 Customization to solve the problem; Hello,
I’m wondering how Workplace Join -> Automatic Device-Join task works. We had it manually enabled on couple of systems and a week later…
Discussion in ‘Windows 10 Customization’ started by TatyanaM1, May 19, 2020.
-
Workplace Join -> Automatic Device-Join task
Hello,
I’m wondering how Workplace Join -> Automatic Device-Join task works. We had it manually enabled on couple of systems and a week later realized that it is back to disabled. Is this a normal behavior?
Regards,
Tatyana
-
Join Workplace on Domain PC
Hi Harish,
Thank you for writing to Microsoft Community Forums.
We understand that the domain joined computer is prompting a notification related to Workplace Join. In this case, let me help to point you in the right direction where you should get the appropriate assistance for issues related to domain environment.
I would suggest you to post your query in
TechNet Forums, where we have a dedicated team of professionals to help you with queries related to Workplace Join.Meanwhile, if it may help, you can check the following documents.
- Walkthrough: Workplace Join with a Windows Device
- Join
to Workplace from Any Device for SSO and Seamless Second Factor Authentication Across Company Applications - How To: Plan your hybrid Azure Active Directory join implementation
Regards,
Prakhar Khare
Microsoft Community – Moderator
-
What is automatic-workplace-join in the Windows 10 startup?
What is automatic-workplace-join in the Windows 10 startup?
-
Workplace Join -> Automatic Device-Join task
Join Workplace on Domain PC
All PC’s in my org are connected to domain .
Last week, one of the PC had to be restarted after an update post which the user got a msg «Windows saves your account and makes it easier to sign up for apps and websites. So you do not have to enter your password every time you access the resources of
your organization. You may need to allow your organization to manage certain settings on your device «.I am trying to find out when exactly a user would get this prompt & what happens if the PC which is connected to a domain is added to workplace .
If the user is allowed to add a device to the work place, will this also allow a personal pc also to be added to the same workplace account ?
***Original title:When would someone to get a pop up to join workplace ?***
Workplace Join -> Automatic Device-Join task
-
Workplace Join -> Automatic Device-Join task — Similar Threads — Workplace Join Automatic
-
JOIN THIS: forum.creative.gimkit.com
in Windows 10 Software and Apps
JOIN THIS: forum.creative.gimkit.com: forum.creative.gimkit.comforum.creative.gimkit.comJoin this for funhttps://answers.microsoft.com/en-us/windows/forum/all/join-this-forumcreativegimkitcom/0182ba9c-0682-437d-8263-a1cd68745c89
-
JOIN THIS
in Windows 10 Gaming
JOIN THIS: every monday and wednesday enter this link:https://app.zoom.us/wc/91443722143/join?fromPWA=1&pwd=MFB4a0tNSGhKQTFTYndQbnl1eGsrUT09&_x_zm_rtaid=YyD76EkVQdK5kFIgyDhQ3A.1701105586239.18f8e2fd5e0f8fbe41f72d87e7a046e4&_x_zm_rhtaid=5… -
JOIN THIS
in Windows 10 Software and Apps
JOIN THIS: every monday and wednesday enter this link:https://app.zoom.us/wc/91443722143/join?fromPWA=1&pwd=MFB4a0tNSGhKQTFTYndQbnl1eGsrUT09&_x_zm_rtaid=YyD76EkVQdK5kFIgyDhQ3A.1701105586239.18f8e2fd5e0f8fbe41f72d87e7a046e4&_x_zm_rhtaid=5… -
Windows 10 Workplace join AAD registered — risks
in Windows 10 Customization
Windows 10 Workplace join AAD registered — risks: Hi,I have read a lot of articles about Azure Active Directory, windows endpoint manager and Intune. I understand the differences between AAD joined devices and registered ones workplace joined.One thing I haven’t seen a clear answer to is the differences in options available… -
Joining a Domain
in Windows 10 Network and Sharing
Joining a Domain: I’m trying to join a domain that resides on my Synology NAS. When trying to join the domain I’m getting the following message:
[ATTACH]
I’ve also tried joining the domain using the «Network ID» button and I get the following message:[ATTACH]
I’m running Windows 10…
-
Workplace joined bitlocker
in AntiVirus, Firewalls and System Security
Workplace joined bitlocker: Please see the attached file of my workplace joined device with bitlocker keys. Should I disable the device first, and then attempt to reinstall Windows using the BitLocker keys?[ATTACH]… -
When would someone to get a pop up to join workplace ?
in Windows 10 Customization
When would someone to get a pop up to join workplace ?: All PC’s in my org are connected to domain .Last week, one of the PC had to be restarted after an update post which the user got a msg «Windows saves your account and makes it easier to sign up for apps and websites. So you do not have to enter your password every time you…
-
PC on Domain prompted to Join workplace
in Windows 10 Customization
PC on Domain prompted to Join workplace: Hi All,All PC’s in my organization are connected to a Domain. Last week, one of my user was prompted with the following screen
» Windows saves your account and makes it easier to sign up for apps and websites. So you do not have to enter your password every time you…
-
Joining a HomeGroup
in Windows 10 Network and Sharing
Joining a HomeGroup: I have been trying to join 2 laptops to a HomeGroup set up and there is no option showing to join. There are several guides that I’ve seen and all show options that do not appear on either laptop I’m trying to join with. Supposedly ther is a HomeGroup option within the…
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
Appearance settings
I have recently encountered an issue when a Citrix VDA version 1912 CU2 was joined as an Entra hybrid joined device. This was preventing users from launching applications published on Citrix. As soon as users will launch an application, VDA state on the Citrix management console would change to Unregistered state.
We had to spend a lot of time investigating on this issue, finally we decided to remove the affected Citrix server from Entra ID to fix it. Although this article is not based on Citrix, it focuses on removing a device from Entra hybrid joined status. I wanted to provide some background information on why I had to take this step to remove a device from Entra ID.
Contents
Turn Off Automatic Registration
First, turn off automatic registration on the device by modifying a scheduled task that triggers the registration process with Entra ID.
Go to Task Scheduler > Microsoft > Windows > Workplace Join > Automatic-Device-Join and perform below changes:
- Disable the Scheduled Task by right-clicking on the task and click on Disable.
- Open the Scheduled task and go to the Triggers Tab. Click on the Trigger(s) > Click Edit > Uncheck Enable checkbox to disable this trigger.
You can also delete this scheduled task completely instead of just disabling it.
Run dsregcmd.exe /debug /leave
Now open the command prompt as an administrator and execute dsregcmd.exe /debug /leave command. This will remove the device from entra hybrid join.
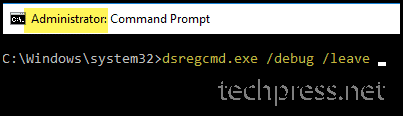
Check Device Join Status using dsregcmd.exe /status command.
Registry Keys to disable Entra ID Join
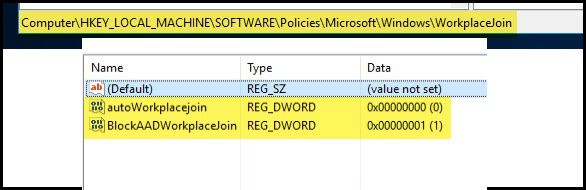
Above steps should remove the device from Hybrid Entra join status. However, you could also create registry keys on the device to ensure that the device will not join with Entra again.
- Press the Windows key + R to open the Run dialog box.
- Navigate to HKLM:\SOFTWARE\Policies\Microsoft\Windows\
- Create a new registry key called WorkplaceJoin (If it does not exist).
- Create below two registry entries:
- autoWorkplaceJoin REG_DWORD Value 0
- BlockAADWorkplacejoin REG_DWORD Value 1
Finally: Unsync the Device using Entra Connect
You can also move the server or device to an OU which is not in sync with Entra ID using Entra connect application and run a delta sync. This will ensure that device objects will not be synced or created in the cloud.
More Information:
- Microsoft Entra device management FAQ.
- Plan your Microsoft Entra hybrid join implementation.
- Troubleshoot devices by using the dsregcmd command.
Read Next
Like a user in your organization, a device is a core identity you want to protect. You can use a device’s identity to protect your resources at any time and from any location. You can accomplish this goal by managing device identities in Azure AD. Use one of the following methods:
- Azure AD join
- Hybrid Azure AD join
- Azure AD registration
The differences between them will be described in the following article from Microsoft under the Concepts menu point.
Azure AD device identity documentation
https://learn.microsoft.com/en-us/azure/active-directory/devices/
Bringing your devices to Azure AD maximizes user productivity through single sign-on (SSO) across your cloud and on-premises resources. You can secure access to your cloud and on-premises resources with Conditional Access at the same time.
You can deploy a managed environment by using password hash sync (PHS) or pass-through authentication (PTA) with seamless single sign-on. These scenarios don’t require you to configure a federation server for authentication.
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-managed-domains
In this post I want to configure Hybrid Azure AD join.
- Configure Hybrid Azure AD join
- Verify the registration by using dsregcmd
- Windows Task – Automatic-Device-Join
- Re-register a Windows 10 device for Hybrid Azure AD join
- Handling devices with Azure AD registered state
- MS-Organization-Access and MS-Organization-P2P-Access Certificate
- Troubleshooting
- Links
Configure Hybrid Azure AD join
To configure Hybrid Azure AD join we can also use the Azure AD Connect tool.
First we need to be sure, that besides our synced users also the computer objects will be synced to Azure AD.
So click on Customize synchronization options
Be sure to check all OUs where you store your computer objects which should be used for Hybrid Azure AD join and therefore must be synced to Azure AD.
For the actual configuration of Hybrid Azure AD join we need to select Configure device options
Select Configure Hybrid Azure AD join
I will only have Windows 10 clients in my environment.
Beginning with version 1.1.819.0, Azure AD Connect includes a wizard to configure hybrid Azure AD join. The wizard significantly simplifies the configuration process. The wizard configures the service connection points (SCPs) for device registration to discover your Azure AD tenant information.
- Select the forest.
- Select the authentication service. You must select AD FS server unless your organization has exclusively Windows 10 clients and you have configured computer/device sync, or your organization uses seamless SSO.
- Select Add to enter the enterprise administrator credentials.
After the configuration you can check the SCP as follows.
Open ADSIEDIT.MSC and open the Configuration Naming Context.
Configuration -> Services -> Device Registration Configuration
Under keywords the Azure AD domain is listed to what windows 10 will connect for device registration.
Microsoft Entra hybrid join requires devices to have access to the following Microsoft resources from inside your organization’s network:
- https://enterpriseregistration.windows.net
- https://login.microsoftonline.com
- https://device.login.microsoftonline.com
- https://autologon.microsoftazuread-sso.com (If you use or plan to use seamless SSO)
- Your organization’s Security Token Service (STS) (For federated domains)
Source: https://learn.microsoft.com/en-us/entra/identity/devices/how-to-hybrid-join#network-connectivity-requirements
To successfully complete hybrid Azure AD join of your Windows downlevel devices and to avoid certificate prompts when devices authenticate to Azure AD, you can push a policy to your domain-joined devices to add the following URLs to the local intranet zone in Internet Explorer:
- https://device.login.microsoftonline.com
- Your organization’s STS (For federated domains)
- https://autologon.microsoftazuread-sso.com (For seamless SSO)
You also must enable Allow updates to status bar via script in the user’s local intranet zone.
Group policy option – Detailed steps
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso-quick-start#group-policy-option—detailed-steps
Verify the registration by using dsregcmd
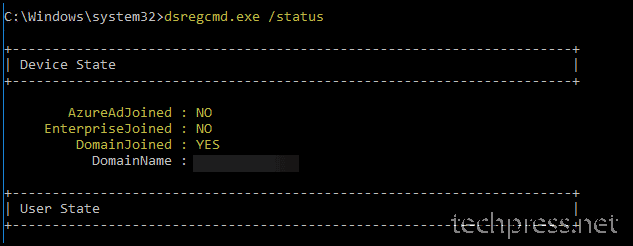
dsregcmd /status
AzureAdJoined : YES
This field indicates whether the device is joined. The value will be YES if the device is either an Azure AD joined device or a hybrid Azure AD joined device. If the value is NO, the join to Azure AD has not completed yet.WorkplaceJoined : NO
This field indicates whether the device is registered with Azure AD as a personal device (marked as Workplace Joined). This value should be NO for a domain-joined computer that is also hybrid Azure AD joined. If the value is YES, a work or school account was added prior to the completion of the hybrid Azure AD join. In this case, the account is ignored when using Windows 10 version 1607 or later.EnterpriseJoined : NO
If the device is Joined to an on-premises Device Registration Service (DRS). A device cannot be both EnterpriseJoined and AzureAdJoined. The Device Registration Service (DRS) is a new Windows service that is included with the Active Directory Federation Service (AD FS) Role on Windows Server 2012 R2. The DRS must be installed and configured on all of the federation servers in your AD FS farm. For information on deploying DRS, see Configure a federation server with Device Registration Service.DomainJoined : YES
This field indicates whether the device is joined to an on-premises Active Directory or not. If the value is NO, the device cannot perform a hybrid Azure AD join.EnterpriseJoined
The revealed prt token from mimikatz.
Windows Task – Automatic-Device-Join
The task Automatic-Device-Join below is by default disabled for standalone windows 10 computers and will be enabled after domain join. Also after leaving domain it will be disabled again.
After the first successful run of this task, the computer will be Hybrid Azure AD joined and the second Task Device-Sync will be enabled. Device-Sync will synchronize device attributes with Azure AD.
In order the Automatic-Device-Join task can run successfully, the computer object from on-premises first have to be synced to Azure AD, otherwise the following error will appear after running dsregcmd /status
The device object by the given id is not found.
Task Scheduler -> Microsoft -> Windows -> Workplace Join
In Azure Active Directory under Devices, you will see the synced computers from on-premises with the Join type Hybrid Azure AD join, also every computer with Azure AD registered and Azure AD joined.
Hybrid Azure AD joined computers in state Pending as below, means that the device has been synchronized from on-premises to Azure AD, and is waiting to complete the registration from the client. Therefore the Automatic-Device-Join task on the client first needs to run to complete the registration as mentioned above.
If you are using System Center Configuration Manager (SCCM) in your network, you may also know the Client Settings Automatically register new Windows 10 domain joined devices with Azure Active.
This behavior is also the default in Windows 10, version 1709.
https://docs.microsoft.com/en-us/mem/configmgr/core/clients/deploy/deploy-clients-cmg-azure#configure-client-settings
Users must be able to join devices to Azure AD, so switch to All or Selected and add the users who should be able to join.
Regarding System Center Configuration Manger (SCCM) and co-management with Microsoft Intune, please read my following post.
Re-register a Windows 10 device for Hybrid Azure AD join
First we need to remove the existing registration to Azure AD from the device as follow.
dsregcmd /leave
dsregcmd /debug /leave
Will display debug messages in addition
Also remove the following two certificates from the computer accounts personal store.
Sign out and sign in to trigger the scheduled task that registers the device again with Azure AD or execute the task by hand as follows:
Go to Task Scheduler > Microsoft > Windows > Workplace Join
Run the Automatic-Device-Join task
For Windows 10 Version 1607 and later Hybrid Azure AD join is invoked by a scheduled task which is by default created.
The task Automatic-Device-Join is by default disabled for standalone windows 10 computers and will be enabled after domain join.
By default will be triggered at every logon and every hour for on-premises domain joined devices.
Check that the two certificates was re-created.
Check again with dsregcmd /status if the device re-registered successfully.
Handling devices with Azure AD registered state
If your Windows 10 domain joined devices are Azure AD registered to your tenant, it could lead to a dual state of Hybrid Azure AD joined and Azure AD registered device. We recommend upgrading to Windows 10 1803 (with KB4489894 applied) or above to automatically address this scenario. In pre-1803 releases, you will need to remove the Azure AD registered state manually before enabling Hybrid Azure AD join. In 1803 and above releases, the following changes have been made to avoid this dual state:
- Any existing Azure AD registered state for a user would be automatically removed after the device is Hybrid Azure AD joined and the same user logs in. For example, if User A had an Azure AD registered state on the device, the dual state for User A is cleaned up only when User A logs in to the device. If there are multiple users on the same device, the dual state is cleaned up individually when those users log in. In addition to removing the Azure AD registered state, Windows 10 will also unenroll the device from Intune or other MDM, if the enrollment happened as part of the Azure AD registration via auto-enrollment.
- Azure AD registered state on any local accounts on the device is not impacted by this change. It is only applicable to domain accounts. So Azure AD registered state on local accounts is not removed automatically even after user logon, since the user is not a domain user.
- You can prevent your domain joined device from being Azure AD registered by adding the following registry value to HKLMSOFTWAREPoliciesMicrosoftWindowsWorkplaceJoin: “BlockAADWorkplaceJoin”=dword:00000001.
- In Windows 10 1803, if you have Windows Hello for Business configured, the user needs to re-setup Windows Hello for Business after the dual state clean up.This issue has been addressed with KB4512509
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan
MS-Organization-Access and MS-Organization-P2P-Access Certificate
Both certificates will be populated by the User Device Registration Scheduled Task on the workstation.
The MS-Organization-P2P-Access certificates are issued by Azure AD to both, Azure AD joined and hybrid Azure AD joined devices. These certificates are used to enable trust between devices in the same tenant for remote desktop scenarios. One certificate is issued to the device and another is issued to the user. The device certificate is present in Local ComputerPersonalCertificates and is valid for one day. This certificate is renewed (by issuing a new certificate) if the device is still active in Azure AD. The user certificate is present in Current UserPersonalCertificates and this certificate is also valid for one day, but it is issued on-demand when a user attempts a remote desktop session to another Azure AD joined device. It is not renewed on expiry. Both these certificates are issued using the MS-Organization-P2P-Access certificate present in the Local ComputerAAD Token IssuerCertificates. This certificate is issued by Azure AD during device registration.
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/faq#what-are-the-ms-organization-p2p-access-certificates-present-on-our-windows-10-devices
The following service principal below will be automatically registered after a windows device has been successfully joined to Azure AD. (Azure AD joined and hybrid Azure AD joined devices)
Using this principal, Windows devices that are Azure AD joined will provision device certificates in their computer store with a name matching “MS-Organization-P2P-Access” that enables RDP using Azure AD credentials. Via PKI, these certificates trust the tenant root certificate that is registered on the “P2P Server” service principal in Azure AD.
Source: https://www.jasonfritts.me/tag/ms-organization-p2p-access/
Troubleshooting
The first tool to check if you encounter some issues regarding Hybrid Azure AD join is the command line tool dsregcmd.
Yo can check the status with
dsregcmd /status
Here I can saw that something went wrong and the computer wasn’t joined to Azure AD.
Therefore I checked the windows logs for the User Device Registration.
Event Viewer -> Microsoft -> Windows -> User Device Registration
Automatic registration failed at join phase.
Exit code: Unknown HResult Error code: 0x801c001d
errorPhase: discover
Source: User Device Registration
Event ID: 304
User: SYSTEM
Automatic registration failed. Failed to lookup the registration service information from Active Directory. Exit code: Unknown HResult Error code: 0x801c001d.
The reason for is, that in my lab environment, I will first need to configure Hybrid Azure AD join, which will create a Service Connection Point (SCP), which the devices needs to discover the Azure AD tenant information.
Beginning with version 1.1.819.0, Azure AD Connect includes a wizard that you can use to configure hybrid Azure AD join. The wizard significantly simplifies the configuration process. The related wizard:
- Configures the service connection points (SCPs) for device registration
- Backs up your existing Azure AD relying party trust
Links
Troubleshooting devices using the dsregcmd command
https://docs.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd
Reading Time: 7 minutes
Active Directory is a family of products. Besides the commonly known Active Directory Domain Services and Certificate Services siblings, the family consists of the Active Directory Lightweight Directory Services, Rights Management Services and Federation Services.
The latter received a major overhaul in Windows Server 2012 R2. One of the new features offered by Active Directory Federation Services is backed by Active Directory Domain Services: WorkPlace Join.
Active Directory Domain Services facilitate WorkPlace Join with a new object type, the msDS-Device object.
A primer on WorkPlace Join
WorkPlace Join, in my opinion, is a method to loosely couple devices (1) with a networking environment based on internet standards (2) to offer single sign-on (3) and rich authorization scenarios (4).
Let me explain in more depth:
- Although you can easily WorkPlace Join Windows 8.1-based devices through the new Control Panel, and WorkPlace Join Windows 7-based devices, too (through a separate download), you can also WorkPlace Join iOS and Android-based devices.
- You join these devices to Active Directory Domain Services (Ad DS) through the Device Registration Service (DRS) in Active Directory Federation Services (AD FS), based on federation-based protocols, encrypted using TLS and transported over HTTPS (TCP 443).
- When a device is WorkPlace Joined, a cookie on the device offers single sign-on (SSO) to web-based applications and services for the user profile (if any) that was used to WorkPlace Join the device.
- WorkPlace-Joined Devices, by default, offer more claimtypes than non-WorkPlace-Joined devices. These additional claimtypes may be used in rich authorization scenarios within the aforementioned applications and services.
Granted, iOS and Android-based devices don’t offer user profiles, today.
On Windows-based devices, though, WorkPlace Join is offered to the combination of the device object and the user account. When the device is used with another user account, the benefits of single sign-on and rich authorization scenarios are unavailable,
Note:
WorkPlace Join is not available for Windows 8 (8.0).
Requirements
When you want to utilize WorkPlace Join, you need to meet these requirements:
- Your Active Directory Federation Services (AD FS) infrastructure needs to run Windows Server 2012 R2, or up.
- Your Active Directory Domain Services (AD DS) infrastructure needs to be prepared for Windows Server 2012 R2. This means you need to have run adprep.exe with the /forestprep and /domainprep switches and your Active Directory schema must read at least version 69.
- When you want to use the group Managed Service Account (gMSA) functionality for the Active Directory federation Services (AD FS) Service account(s), this requires the Windows Server 2012 Active Directory schema.
- Optionally, when you want to utilize the msDS-Primary-Computer attribute on user objects as a Group Policy scoping mechanism, this requires the Windows Server 2012 Active Directory schema and Windows 8.x clients.
Setting up WorkPlace Join
I’ve documented how to build an environment for WorkPlace Join (and other Windows Server 2012 R2-based Enterprise Mobility technologies like the Web Application Proxy and Work Folders) in Microsoft Azure for 4Sysops.com and you can find it through the links below:
- Building a BYOD lab in Microsoft Azure
- BYOD lab in Azure – Create virtual machines
- BYOD lab in Azure – Domain Controller, Certification Services
- BYOD lab in Azure – Active Directory Federation Services (AD FS)
- BYOD lab in Azure – Webserver
- BYOD lab in Azure – Trust relationships
WorkPlace Joining
Configuring WorkPlace Join on Windows 8.1 through the Control Panel
On devices running Windows 8.1 (and up), you can WorkPlace Join through the Control Panel of the New Interface.
To this purpose, perform these steps:
- Log on with the account that you wish to use to couple the device with the enterprise environment. This account does not need to have administrative privileges.
- While in the Start Screen, either:
- Press Ctrl + C to open the Charms menu. Click on Settings, then Change PC settings. In the Control Panel, in the left pane, click Network and then Workplace.
- Type (part of) Workplace settings and click on it in the Search results.

- In the text field under Enter your user ID to get workplace access or turn on device management enter the e-mail address or User Principal Name (UPN) for a valid account within Active Directory Domain Services. Click Join next.
- A pane will appear over the Control Panel section that allows you to authenticate to the Active Directory Federation Services (AD FS) infrastructure.

Note:
When you’ve enabled Multi-factor Authentication on WorkPlace Join, this pane will also feature the Multi-factor Authentication controls.
- When you successfully sign in, the combination of the device and user account will be WorkPlace-joined.

Note:
The Workplace settings screen can now be used to leave the workplace network, when you no longer want to combination of user and device to be trusted. The button labeled Leave serves this purpose.
- Now, after you’ve successfully authenticate to a claims-protected resource, the single sign-on (SSO) benefits for that resource will be enabled.
Configuring WorkPlace Join on Windows 8.1 through Group Policy
Windows 8.1 devices can also be automatically WorkPlace-Joined through Group Policy.
This behavior is governed by the Automatically workplace join client computers Group Policy setting under Policies, Administrative Templates, Windows Components, and finally Workplace Join.

When you configure this Group Policy setting to Enabled, any colleague that signs in with a domain user account on a domain-joined device in scope for the Group Policy object will be automatically and silently Workplace-Joined.
The Group Policy enables a Scheduled Task on the system that runs in the user’s context and is triggered on user sign-in. The task will silently Workplace Join the user and device with Active Directory after the User signs-in is complete, when the device is considered to be on the Intranet by the Federation Server.
Additional requirements
Automatic WorkPlace Join has the following specific and additional requirements to the general requirements listed above:
- Devices must have connectivity to an Active Directory Domain Controller in order to Workplace Join. You cannot automatically WorkPlace Join through a reverse proxy solution, such as the Web Application Proxy.
- The AD FS Global Primary Authentication Policy must be configured to allow Windows Integrated Authentication for the Intranet. The Federation server used, needs to see the device to be joined as an inside device.
- Internet Explorer must use the following settings for the Local intranet security zone:
- Don’t prompt for client certificate selection when only one certificate exists: Enable
- Allow scripting: Enable
- Automatic logon only in Intranet zone: Checked
Luckily, the specific settings above are the default settings.
Configuring WorkPlace Join on Windows 7
For Windows 7 clients, both the Workplace Join functionality and the Control Panel of the New Interface are unavailable, by default. Although the New Control Panel will never make it to Windows 7 (and some people are very grateful for that), the WorkPlace Join functionality can be installed separately. The software package is available for download at the Microsoft Connect website.
You can distribute this package to Windows 7 devices through Group Policy and, for instance, System Center Configuration Manager. The use of the /quiet parameter is recommended in these scenarios.
Workplace Join for Windows 7 does not require or include a user interface. Once installed on the machine, any domain user that logs into the machine will be automatically and silently Workplace Joined with Active Directory; the installer creates a scheduled task on the system that runs in the user’s context and is triggered on user sign-in. The task silently Workplace-Joins the user and device with Active Directory after the user signs-in is complete. The Scheduled Task can be found in the Task Scheduler Library under Microsoft > Workplace Join.
The same additional requirements that apply to Automatic WorkPlace Join on Windows 8.1 apply to WorkPlace Join on Windows 7.
The msDS-Device Object
When you Workplace Join a device through this Active Directory Federation Services (AD FS) process, a Registered Device object is automatically created by the Device Registration Service (DRS) from within Active Directory Federation Services (AD FS). The Registered Device object, by default, is created in Active Directory Domain Services (AD DS) in a new container, labeled RegisteredDevices:

Registered Device objects (msDS-Device objects), by default, will be automatically created within this container for each of the devices you Workplace Join.
The first thing you’ll notice when examining these objects, is that, in contrast to domain-joined devices, the names for these objects are not very straightforward:

Additionally, in the left pane, many of the sections you’d normally see with user and device objects are missing. For instance, the ability to add Registered Devices to groups is not present.
However, in its attributes, a lot of useful information can be found on the device and the user account that was used to register it:
- DisplayName
This attribute contains the hostname for the registered device. - msDS-CloudIsManaged and msDS-IsManaged
These attributes contain true and false values to indicate whether the device is managed through Microsoft Intune and/or System Center Configuration Manager. - msDS-DeviceOSType and msDS-DeviceOSVersion
These attributes contain strings to indicate the Operating System on the device, at the time when the device was registered. (If the device is upgraded, these attributes are not updated, unless a Mobile Device Management solution updates them for it.) - msDS-RegisteredOwner
When looking for the user account object that registered the device, this attribute contains the Security identifier (SID) for it.
Concluding
WorkPlace Join for Windows 7 and Windows 8.1-based devices offers a strategic expansion to Active Directory Domain Services into a dual identity stack. For iOS and Android-based devices, WorkPlace Join merely offers single sign-on (SSO) to enterprise applications and services. Something colleagues on these devices will appreciate strongly.
Further reading
Walkthrough Guide: Workplace Join with a Windows Device
Walkthrough Guide: Workplace Join with an iOS Device
Automatic and Silent Workplace Join
IT Guide to Windows 8.1: Workplace Join
Workplace Join for Windows 7
WorkPlace Join overview
Join to Workplace from Any Device for SSO and Seamless Second Factor Authentication Across Company Applications

