В этой статье мы рассмотрим, как получить и проанализировать логи RDP подключений в Windows. Логи RDP подключений позволяют администраторам терминальных RDS серверов/ферм получить информацию о том, какие пользователи подключались к серверу, когда был выполнен вход и когда сеанс завершен, с какого устройства (имя или IP адрес) подключался пользователь.
Описанные методики получения и исследования RDP логов применима как к Windows Server 2022/2019/2016/2012R2, так и для десктопных версий Windows 11, 10, 8.1 c.
Содержание:
- События RDP подключений в журналах Windows (Event Viewer)
- Получаем логи RDP подключений в Windows с помощью PowerShell
- Логи RDP подключений на клиентах Windows
События RDP подключений в журналах Windows (Event Viewer)
Когда пользователь удаленно подключается к RDS серверу или удаленному столу Windows (RDP), информация об этих событиях сохраняется в журналы Windows. Рассмотрим основные этапы RDP подключения и связанные с ними события в Event Viewer.
- Network Connection
- Authentication
- Logon
- Session Disconnect/Reconnect
- Logoff
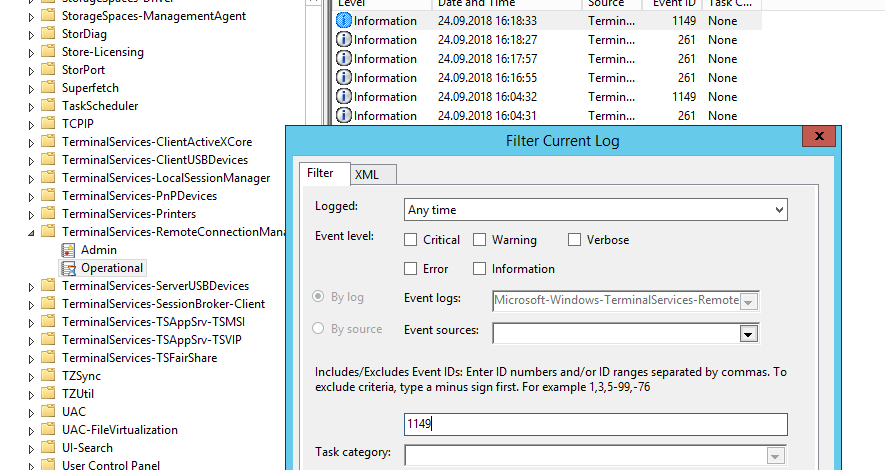
Network Connection: – событие установления сетевого подключение к серверу от RDP клиента пользователя. Событие с EventID – 1149 (Remote Desktop Services: User authentication succeeded). Наличие этого события не свидетельствует об успешной аутентификации пользователя. Этот журнал находится в разделе Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager -> Operational. Включите фильтр по данному событию (ПКМ по журналу-> Filter Current Log -> EventId 1149).
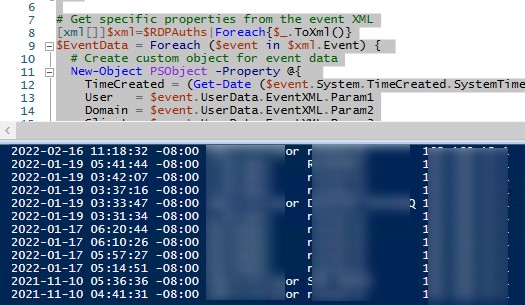
С помощью PowerShell можно вывести список всех попыток RDP подключений:
$RDPAuths = Get-WinEvent -LogName 'Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational' -FilterXPath '<QueryList><Query Id="0"><Select>*[System[EventID=1149]]</Select></Query></QueryList>'
[xml[]]$xml=$RDPAuths|Foreach{$_.ToXml()}
$EventData = Foreach ($event in $xml.Event)
{ New-Object PSObject -Property @{
TimeCreated = (Get-Date ($event.System.TimeCreated.SystemTime) -Format 'yyyy-MM-dd hh:mm:ss K')
User = $event.UserData.EventXML.Param1
Domain = $event.UserData.EventXML.Param2
Client = $event.UserData.EventXML.Param3
}
} $EventData | FT
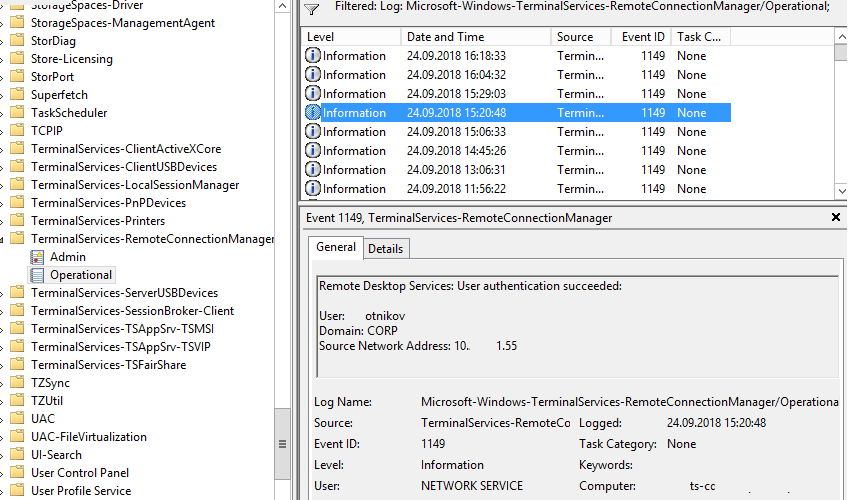
В результате у вас получится список с историей всех сетевых RDP подключений к данному серверу. В событии содержится имя пользователя, домен (если используется NLA аутентификация, при отключенном NLA текст события выглядит иначе) и IP адрес компьютера пользователя.
Authentication: – успешная или неудачная аутентификация пользователя на сервере. Журнал Windows -> Security. Здесь нас могут интересовать события с EventID – 4624 (успешная аутентификация — An account was successfully logged on) или 4625 (ошибка аутентификации — An account failed to log on). Обратите внимание на значение LogonType в событии.
- LogonType = 10 или 3 — при входе через терминальную службу RDP —.
- LogonType = 7, значит выполнено переподключение к уже существующему RDP сеансу.
- LogonType = 5 – событие RDP подключения к консоли сервера (в режиме mstsc.exe /admin)
Вы можете использовать события с ошибками аутентификации для защиты от удаленного перебора паролей через RDP. СВы можете автоматически блокировать на файерволе IP адреса, с которых выполняется подбор пароля, простым PowerShell скриптом (см. статью).
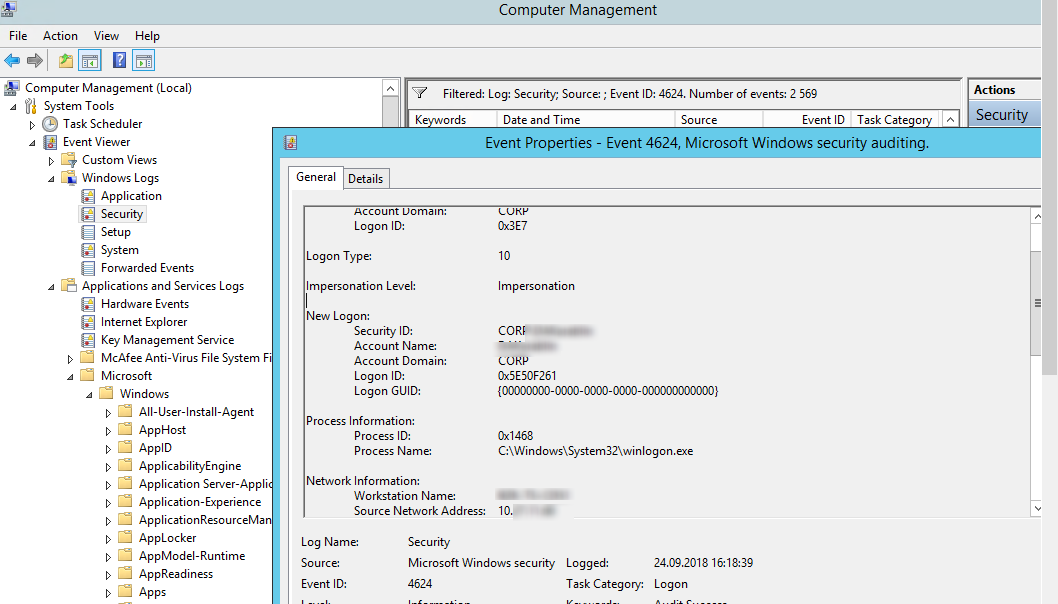
При этом имя пользователя содержится в описании события в поле Account Name, имя компьютера в Workstation Name, а имя пользователя в Source Network Address.
Обратите внимание на значение поля LogonID – это уникальный идентификатор сессии пользователя, с помощью которого можно отслеживать дальнейшую активность данного пользователя. Но при отключении от RDP сессии (disconnect) и повторного переподключения к той же сессии, пользователю будет выдан новый TargetLogonID (хотя RDP сессия осталась той же самой).
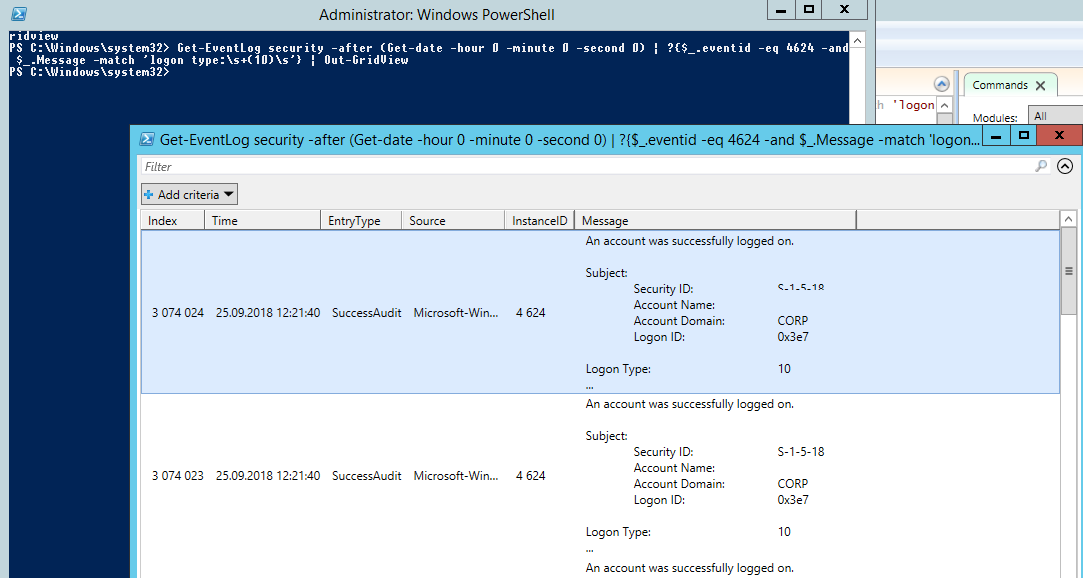
Вы можете получить список событий успешных авторизаций по RDP (событие 4624) с помощью такой команды PowerShell.
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ?{$_.eventid -eq 4624 -and $_.Message -match 'logon type:\s+(10)\s'} | Out-GridView
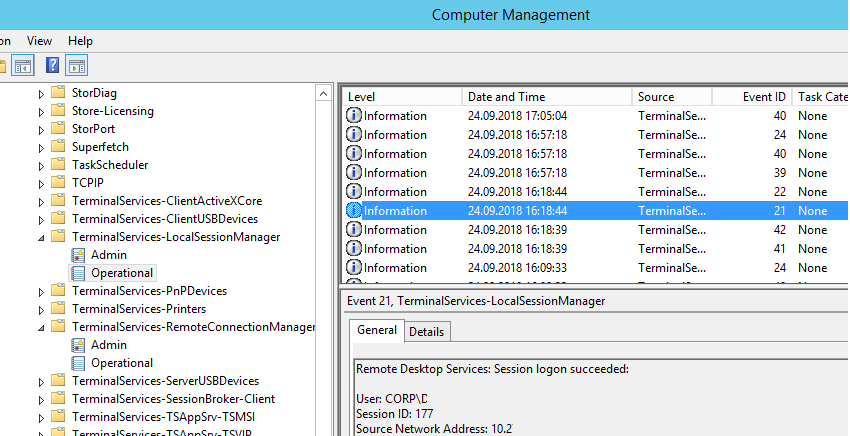
Logon: – RDP вход в систему, EventID – 21 (Remote Desktop Services: Session logon succeeded. Это событие появляется после успешной аутентификации пользователя. Этот журнал находится в разделе Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational. Как вы видите, здесь можно узнать идентификатор RDP сессии для пользователя — Session ID.
Событие с EventID – 21 (Remote Desktop Services: Shell start notification received) означает успешный запуск оболочки Explorer (появление окна рабочего стола в RDP сессии).
Session Disconnect/Reconnect – события отключения и переподключения к сессии имеют разные коды в зависимости от того, что вызвало отключение пользователя (отключение по неактивности, заданному в таймаутах для RDP сессий; выбор пункта Disconnect в сессии; завершение RDP сессии другим пользователем или администратором и т.д.). Эти события находятся в разделе журналов Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational. Рассмотрим RDP события, которые могут быть полезными:
- EventID – 24 (Remote Desktop Services: Session has been disconnected) – пользователь отключился от RDP сессии.
- EventID – 25 (Remote Desktop Services: Session reconnection succeeded) – пользователь переподключился к своей имеющейся RDP сессии на сервере.
- EventID – 39 (Session <A> has been disconnected by session <B>) – пользователь сам отключился от своей RDP сессии, выбрав соответствующий пункт меню (а не просто закрыл окно RDP клиента). Если идентификаторы сессий разные, значит пользователя отключил другой пользователь (или администратор).
- EventID – 40 (Session <A> has been disconnected, reason code <B>). Здесь нужно смотреть на код причины отключения в событии. Например:
- reason code 0 (No additional information is available) – обычно говорит о том, что пользователь просто закрыл окно RDP клиента.
- reason code 5 (The client’s connection was replaced by another connection) – пользователь переподключился к своей старой сессии.
- reason code 11 (User activity has initiated the disconnect) – пользователь сам нажал на кнопку Disconnect в меню.
Событие с EventID – 4778 в журнале Windows -> Security (A session was reconnected to a Window Station). Пользователь переподключился к RDP сессии (пользователю выдается новый LogonID).
Событие с EventID 4779 в журнале Windows -> Security (A session was disconnected from a Window Station). Отключение от RDP сеанса.
Logoff: – выход пользователя из системы. При этом в журнале Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational регистрируется событие с EventID 23 (Remote Desktop Services: Session logoff succeeded).
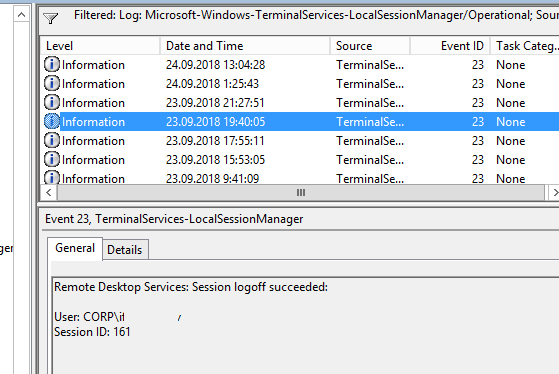
При этом в журнале Security нужно смотреть событие EventID 4634 (An account was logged off).
Событие Event 9009 (The Desktop Window Manager has exited with code (<X>) в журнале System говорит о том, что пользователь инициировал завершение RDP сессии, и окно и графический shell пользователя был завершен.
EventID 4647 — User-initiated logoff
Получаем логи RDP подключений в Windows с помощью PowerShell
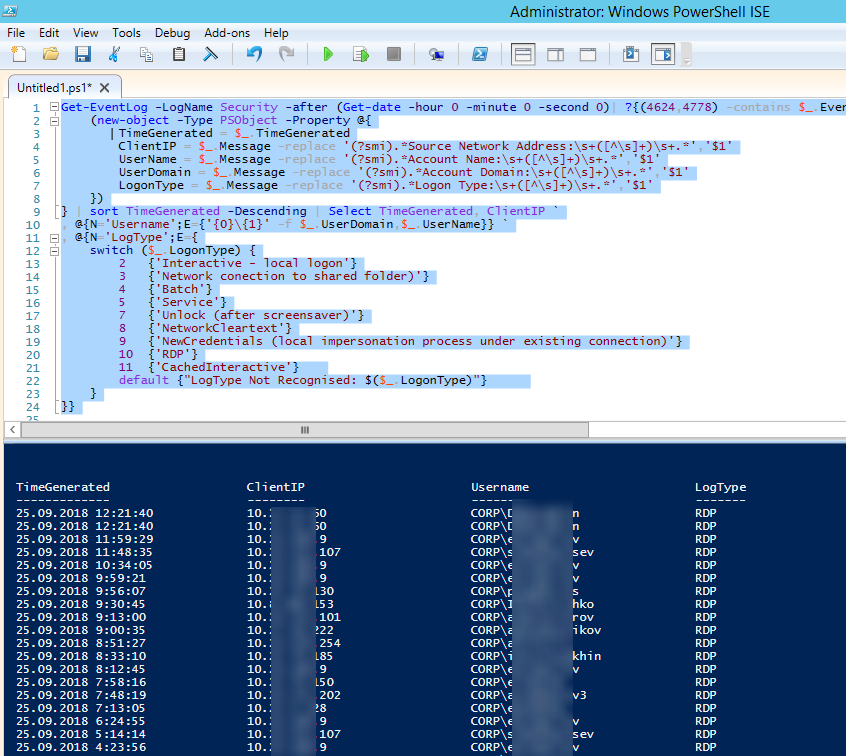
Ниже представлен небольшой PowerShell скрипт, который выгружает из журналов терминального RDS сервера историю всех RDP подключений за текущий день. В полученной таблице указано время подключения, IP адрес клиента и имя пользователя (при необходимости вы можете включить в отчет другие типы входов).
Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ?{(4624,4778) -contains $_.EventID -and $_.Message -match 'logon type:\s+(10)\s'}| %{
(new-object -Type PSObject -Property @{
TimeGenerated = $_.TimeGenerated
ClientIP = $_.Message -replace '(?smi).*Source Network Address:\s+([^\s]+)\s+.*','$1'
UserName = $_.Message -replace '(?smi).*\s\sAccount Name:\s+([^\s]+)\s+.*','$1'
UserDomain = $_.Message -replace '(?smi).*\s\sAccount Domain:\s+([^\s]+)\s+.*','$1'
LogonType = $_.Message -replace '(?smi).*Logon Type:\s+([^\s]+)\s+.*','$1'
})
} | sort TimeGenerated -Descending | Select TimeGenerated, ClientIP `
, @{N='Username';E={'{0}\{1}' -f $_.UserDomain,$_.UserName}} `
, @{N='LogType';E={
switch ($_.LogonType) {
2 {'Interactive - local logon'}
3 {'Network conection to shared folder)'}
4 {'Batch'}
5 {'Service'}
7 {'Unlock (after screensaver)'}
8 {'NetworkCleartext'}
9 {'NewCredentials (local impersonation process under existing connection)'}
10 {'RDP'}
11 {'CachedInteractive'}
default {"LogType Not Recognised: $($_.LogonType)"}
}
}}
Можно экспортировать логи RDP подключений из журнала в CSV файл (для дальнейшего анализа в таблице Excel). Экспорт журнала можно выполнить из консоли Event Viewer (при условии что логи не очищены) или через командную строку:
WEVTUtil query-events Security > c:\ps\security_log.txt
Или с помощью PowerShell:
get-winevent -logname "Microsoft-Windows-TerminalServices-LocalSessionManager/Operational" | Export-Csv c:\ps\rdp-log.csv -Encoding UTF8
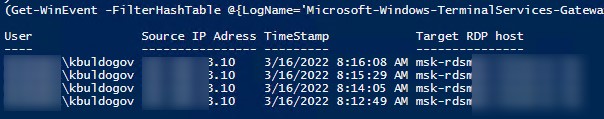
Если ваши пользователи подключаются к RDS серверам через шлюз удаленных рабочих столов Remote Desktop Gateway, вы можете обрабатывать логи подключений пользователей по журналу Microsoft-Windows-TerminalServices-Gateway по EventID 302. Например, следующий PowerShell скрипт выведет полную историю подключений через RD Gateway указанного пользователя:
$rdpusername="kbuldogov"
$properties = @(
@{n='User';e={$_.Properties[0].Value}},
@{n='Source IP Adress';e={$_.Properties[1].Value}},
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='Target RDP host';e={$_.Properties[3].Value}}
)
(Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-Gateway/Operational';ID='302'} | Select-Object $properties) -match $rdpusername
Другие события, связанные с подключениями пользователей на RD Gateway в журнале Microsoft-Windows-TerminalServices-Gateway:
- 300 —
The user %1, on client computer %2, met resource authorization policy requirements and was therefore authorized to connect to resource %4 - 302 —
The user %1, on client computer %2, connected to resource %4 - 303 —
The user %1, on client computer %2, disconnected from the following network resource: %4. Before the user disconnected, the client transferred %6 bytes and received %5 bytes. The client session duration was %7 seconds.
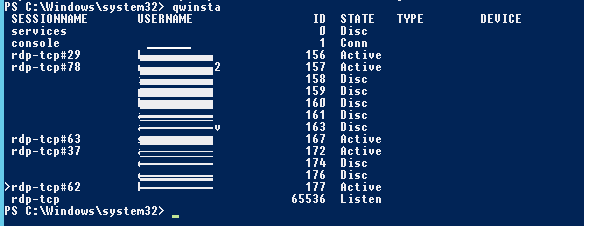
Список текущих RDP сессий на сервере можно вывести командой:
qwinsta
Команда возвращает как идентификатор сессии (ID), имя пользователя (USERNAME)и состояние (Active/Disconnect). Эту команду удобна использовать, когда нужно определить ID RDP сессии пользователя при теневом подключении.
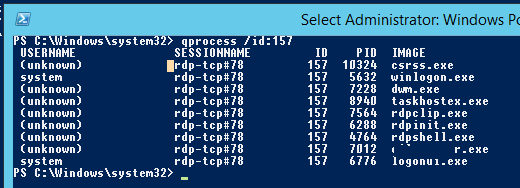
Список запущенных процессов в конкретной RDP сессии (указывается ID сессии):
qprocess /id:157
Логи RDP подключений на клиентах Windows
Также вы можете изучать логи исходящих подключений на стороне RDP клиента. Они доступны в журнале событий Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operation.
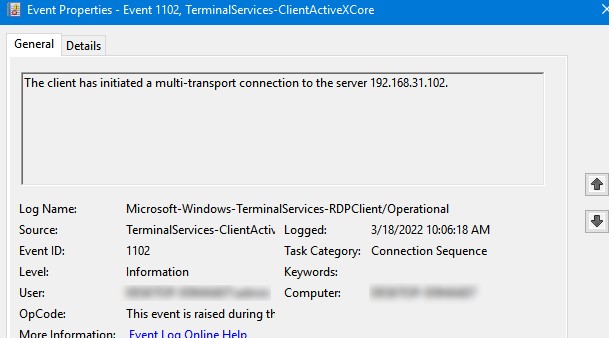
Например, событие с Event ID 1102 появляется, когда компьютер устанавливает подключение с удаленным RDS хостом Windows Server или компьютером с Windows 10/11 с включенной службой RDP (десктопные версии Windows также поддерживают несколько одновременных rdp подключений).
The client has initiated a multi-transport connection to the server 192.168.31.102.
Следующий RDP скрипт выведет историю RDP подключений на указанном компьютере (для получения событий Event Log используется командлет Get-WinEvent):
$properties = @(
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='LocalUser';e={$_.UserID}}
@{n='Target RDP host';e={$_.Properties[1].Value}}
)
Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-RDPClient/Operational';ID='1102'} | Select-Object $properties
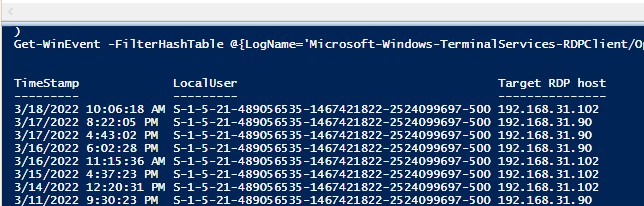
Скрипт возвращает SID пользователей, которые инициировали RDP подключения на этом компьютере и DNS имена/IP адреса серверов, к которым подключались пользователи. Вы можете преобразовать SID в имена пользователей.
Также история RDP подключений пользователя хранится в реестре.
To collect Windows-TerminalServices-RemoteConnectionManager/Operational, add the following to a inputs.conf
We’ve found that multiline data parses better natively without having to create a props/transforms.
[WinEventLog://Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational]
disabled = False
renderXml = False
index = win
What eventID’s are in Microsoft-Windows-TerminalServices-RemoteConnectionManager?
PS C:\Users\Administrator> (Get-WinEvent -ListProvider Microsoft-Windows-TerminalServices-RemoteConnectionManager).Events | Format-Table Id, Description
Id Description
-- -----------
2 %1
3 %1
4 %1
5 %1
6 %1
7 %1
8 %1
9 %1
256 Remote Desktop Services Remote Connection Manager is starting up
257 Remote Desktop Services Remote Connection Manager has finished start up. Return code %1
258 Listener %1 has started listening
259 Listener %1 has stopped listening
260 Listener %1 failed while listening. Error code %2
261 Listener %1 received a connection
262 Listener %1 has been asked to stop listening
1003 The remote desktop client '%1' has provided an invalid license.
1004 The Remote Desktop Session Host server cannot issue a client license. It was unable to issue the license due to a changed (mismatched) client license, insufficient memory, or an internal error. Further details for this problem may have been reported at th...
1006 The RD Session Host server received large number of incomplete connections. The system may be under attack.
1011 The remote session could not be established from remote desktop client %1 because its temporary license has expired.
1073742836 Remote session from client name %1 exceeded the maximum allowed failed logon attempts. The session was forcibly terminated.
3221226494 TermService clustering failed to redirect a client to an alternate clustered server, ntstatus=%1.
3221226496 TermService clustering failed to initialize because the Session Directory Provider failed to initialize, hresult=%1.
3221226500 The remote session could not be established from remote desktop client %1 because its license could not be renewed.
3221226507 RD Session Host Server listener stack was down. The relevant status code %1.
3221226508 RD Session Host Server session creation failed. The relevant status code was %1.
3221226513 Autoreconnect failed to reconnect user to session because authentication failed. (%1)
3221226515 The Remote Desktop Session Host server cannot communicate with the Remote Desktop license server %1. Ensure that the computer account for the Remote Desktop Session Host server is a member of the RDS Endpoint Servers group on the license server.
3221226518 Failed to load RD Session Host Server Profile path. Note that the profile path must be less than 256 characters in length. User Name: %1 Domain: %2
3221226522 The RD Session Host Server listener %1 is configured with inconsistent authentication and encryption settings. The Encryption Level is currently set to %2 and Security Layer is set to %3. These settings were automatically corrected to allow connections to ...
3221226523 The RD Session Host Server is configured to use SSL with user selected certificate, however, no usable certificate was found on the server. The default certificate will be used for RD Session Host Server authentication from now on. Please check the securit...
3221226524 The RD Session Host Server is configured to use a certificate that will expire in %2 days. %1 The SHA1 hash of the certificate is in the event data. Please check the security settings by using the Remote Desktop Session Host Configuration tool in the Admin...
3221226525 The RD Session Host Server is configured to use a certificate that is expired. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host Server authentication from now on. Please check the security s...
3221226526 The RD Session Host Server is configured to use a certificate that does not contain an Enhanced Key Usage attribute of Server Authentication. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host...
3221226527 The RD Session Host Server is configured to use a certificate but is unable to access the private key associated with this certificate. %1 The SHA1 hash of the certificate is in the event data. The default certificate will be used for RD Session Host Serve...
3221226528 A new self signed certificate to be used for RD Session Host Server authentication on SSL connections was generated. The name on this certificate is %1. The SHA1 hash of the certificate is in the event data.
3221226529 The RD Session Host Server has failed to create a new self signed certificate to be used for RD Session Host Server authentication on SSL connections. The relevant status code was %1.
3221226530 The RD Session Host Server has failed to replace the expired self signed certificate used for RD Session Host Server authentication on SSL connections. The relevant status code was %1.
3221226531 The RD Session Host Server authentication certificate configuration data was invalid and the service reset it. If the computer was configured to use a specific certificate, please verify it is available in the certificate store and use the administrative t...
3221226532 The Remote Desktop Services User Home Directory was not set because the path specified does not exist or not accessible. The default Home Directory Path was used instead. User Name: %1 Domain: %2
3221226533 Remote Desktop Session Host server was unable to retrieve users Licensing information from AD. Error %1
3221226534 The RD Session Host server is configured to use a template-based certificate for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption, but the subject name on the certificate is invalid. %1 The SHA1 hash of the certif...
3221226535 A new template-based certificate to be used by the RD Session Host server for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption has been installed. The name for this certificate is %1. The SHA1 hash of the certific...
3221226536 The RD Session Host server cannot install a new template-based certificate to be used for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption. The following error occured: %1.
3221226537 The template-based certificate that is being used by the RD Session Host server for Transport Layer Security (TLS) 1.0\Secure Sockets Layer (SSL) authentication and encryption has expired and cannot be replaced by the RD Session Host server. The following ...
3221226538 RD Session Host Server was unable to process session arbitration request. Error %1
3221226539 The RD Session Host server cannot register 'TERMSRV' Service Principal Name to be used for server authentication. The following error occured: %1.
1068 The RD Licensing mode has not been configured.
1069 The RD Licensing grace period has expired and Licensing mode for the Remote Desktop Session Host server has not been configured. Licensing mode must be configured for continuous operation.
3221226542 A logon request was denied because the RD Session Host server is currently in drain mode and therefore not accepting new user logons. To configure the server to allow new user logons, use the Remote Desktop Services Configuration tool.
3221226543 A connection request was denied because the RD Session Host server is currently configured to not accept connections. To configure the server to allow connections, use the chglogon command-line tool.
3221226600 The RD Licensing grace period has expired and the service has not registered with a license server with installed licenses. A RD Licensing server is required for continuous operation. A Remote Desktop Session Host server can operate without a license serve...
3221226601 The RD Licensing grace period is about to expire on %1 and the service has not registered with a license server with installed licenses. A RD Licensing server is required for continuous operation. A Remote Desktop Session Host server can operate without a ...
3221226602 The Remote Desktop Session Host server does not have a Remote Desktop license server specified. To specify a license server for the Remote Desktop Session Host server, use the Remote Desktop Session Host Configuration tool.
3221226603 The Remote Desktop Session Host server could not contact the Remote Desktop license server %1. Ensure that the Remote Desktop Licensing service is running on the license server, that the license server is accepting network requests, and that the license se...
3221226604 The Remote Desktop license server %1 does not support the version of the operating system running on the Remote Desktop Session Host server.
3221226605 The certificate issued by the Remote Desktop license server to the Remote Desktop Session Host server is not valid. The license server will not issue Remote Desktop Services client access licenses to clients connecting to the Remote Desktop Session Host se...
1136 RD Session Host Server role is not installed.
1137 The roaming user profile cache manager for Remote Desktop Services could not start. Error Code: %1
1138 The roaming user profile cache manager for Remote Desktop Services could not start because an incorrect value was specified for the monitoring interval. Error Code: %1
1139 The roaming user profile cache manager for Remote Desktop Services could not start because an incorrect value was specified for the maximum cache size. Error Code: %1
1140 The "Limit the size of the entire roaming user profile cache" Group Policy setting has been enabled, but the roaming user profile cache manager for Remote Desktop Services has encountered a problem. Error Code: %1
1141 The "Limit the size of the entire roaming user profile cache" Group Policy setting has been disabled, but the roaming user profile cache manager for Remote Desktop Services has encountered a problem. Error Code: %1
1142 The "Limit the size of the entire roaming user profile cache" Group Policy setting has been enabled.
1143 The "Limit the size of the entire roaming user profile cache" Group Policy setting has been disabled.
1144 The roaming user profile cache manager for Remote Desktop Services could not delete the roaming user profile for the user %1. The roaming user profile cache might still exceed the %2 gigabyte limit. Error Code: %3
1145 The roaming user profile cache manager for Remote Desktop Services deleted the roaming user profile for the user %1 because the roaming user profile cache exceeded the %2 gigabyte limit.
1146 Remote Desktop Services: Remote control session initiated:...
1147 Remote Desktop Services: Remote control session connection succeeded:...
1148 Remote Desktop Services: Remote control session connection failed:...
1149 Remote Desktop Services: User authentication succeeded:...
1150 Remote Desktop Services: User config data have been merged:...
1151 The remote user's connection was declined by the logged on user....
1152 Failed to create KVP sessions string. Error Code %1
3221226624 The Remote Desktop Virtualization Host server cannot issue a client license. It was unable to issue the license due to a changed (mismatched) client license, insufficient memory, or an internal error. Further details for this problem may have been reporte...
1153 Failed to write KVP sessions string. Error Code %1
3221226625 The RD Licensing grace period has expired and Licensing mode for the Remote Desktop Virtualization Host server has not been configured. Licensing mode must be configured for continuous operation.
3221226626 The RD Licensing grace period has expired and the service has not registered with a license server with installed licenses. A RD Licensing server is required for continuous operation. A Remote Desktop Virtualization Host server can operate without a licens...
1155 The Remote Connection Manager selected Kernel mode RDP protocol stack.
3221226627 The RD Licensing grace period is about to expire on %1 and the service has not registered with a license server with installed licenses. A RD Licensing server is required for continuous operation. A Remote Desktop Virtualization Host server can operate wit...
1156 The Remote Connection Manager selected User mode RDP protocol stack.
3221226628 The Remote Desktop Virtualization Host server does not have a Remote Desktop license server specified. To specify a license server for the Remote Desktop Virtualization Host server, use the RDS module for Windows PowerShell.
1157 The listener named %1 has modified some configuration settings.
3221226629 The Remote Desktop Virtualization Host server could not contact the Remote Desktop license server %1. Ensure that the Remote Desktop Licensing service is running on the license server, that the license server is accepting network requests, and that the lic...
1158 Remote Desktop Services accepted a connection from IP address %1.
3221226630 The Remote Desktop license server %1 does not support the version of the operating system running on the Remote Desktop Virtualization Host server.
3221226631 The certificate issued by the Remote Desktop license server to the Remote Desktop Virtualization Host server is not valid. The license server will not issue licenses to clients connecting to the Remote Desktop Virtualization Host server. To resolve this is...
3221226632 The Remote Desktop Virtualization Host server cannot communicate with the Remote Desktop license server %1. Ensure that the computer account for the Remote Desktop Virtualization Host server is a member of the RDS Endpoint Servers group on the license server.
1280 Remote Desktop Configuration service could not remove user %1\%2 from administrators group, error Code: %3
1281 Remote Desktop Configuration service could not remove user %1\%2 from Remote Desktop Users group, error Code: %3
1282 Remote Desktop Configuration service could not remove user with SID %1 from administrators group, error Code: %2
1283 Remote Desktop Configuration service could not remove user with SID %1 from Remote Desktop Users group, error Code: %2
1284 Remote Desktop Configuration service has added user %1\%2 to administrators group
1285 Remote Desktop Configuration service has added user %1\%2 to Remote Desktop Users group
1286 Remote Desktop Configuration service has removed user with SID %1 from administrators group
1287 Remote Desktop Configuration service has removed user with SID %1 from Remote Desktop Users group
1288 Remote Desktop Configuration service has removed user %1\%2 from administrators group
1289 Remote Desktop Configuration service has removed user %1\%2 from Remote Desktop Users group
2304
2305
2306
2307
20480 Remote Desktop Services Network Fair Share started.
20481 Remote Desktop Services Network Fair Share stopped.
20482 Remote Desktop Services Network Fair Share was enabled for the user account %1 with a weight of %2.
20483 Remote Desktop Service Network Fairshare has been enabled for connection on session %1 with weight of %2.
20484 Remote Desktop Services could not enable Network Fair Share for the user account %1. The error code is %2.
20485 Remote Desktop Services could not enable Network Fair Share for the connection on session %1. The error code is %2.
20486 Remote Desktop Services could not enable Network Fair Share for session %1. The error code is %2.
20487 Remote Desktop Services Network Fair Share was disabled for the user account %1.
20488 Remote Desktop Services Network Fair Share was disabled for the connection on session %1.
20489 Remote Desktop Services could not disable Network Fair Share for the user account %1. The error code is %2.
20490 Remote Desktop Services could not disable Network Fair Share for the connection on session %1. The error code is %2.
20491 Remote Desktop Services could not disconnect a user disk for the user account with a SID of %1. The error code is %2.%3
20492 Remote Desktop Services could not detach a user disk for the user account with a SID of %1. The error code is %2.%3
20493 Remote Desktop Services could not apply a user desktop for a user account with a SID of %1. A temporary profile was enforced for the user. Verify that the user profile disk settings are correct. The error code is %2.%3
20494 Remote Desktop Services could not obtain a user profile disk for the user account with a SID of %1. Verify that the user profile disk location is accessible, the server's computer account has read and write permissions to it, and that the location has a us...
20495 Remote Desktop Services could not attach a user profile disk for a user account with a SID of %1. The error code is %2.%3
20496 Remote Desktop Services could not apply a user desktop for a user account with a SID of %1. A temporary profile could not be enforced for the user. The user will get a normal profile, and the user's state will be discarded when the user logs off. Verify th...
20497 The RD Licensing has taken too long to process the client license
20498 Remote Desktop Services has taken too long to complete the client connection
20499 Remote Desktop Services has taken too long to load the user configuration from server %1 for user %2
20500 Remote Desktop Services took %3 milliseconds to load the user configuration from server %1 for user %2
20501 Remote Desktop Services failed to shutdown within the time allocated
20502 Remote Desktop Services failed to retrieve information about a connection for session %1 within the time allocated
20503 Shadow View Session Started...
20504 Shadow View Session Stopped...
20506 Shadow Control Session Started...
20507 Shadow Control Session Stopped...
20508 Shadow View Permission Granted...
20509 Shadow View Permission Denied...
20510 Shadow Control Permission Granted...
20511 Shadow Control Permission Denied...
20512 Shadow Session Failure...
20513 Shadow Session Failure...
20514 Shadow Session Failure...
20515 Session %1 has been idle over its time limit, and was logged off
20516 Session %1 has been idle over its time limit, and was disconnected
20517 Session %1 has exceeded its time limit, and was logged off
20518 Session %1 has exceeded its time limit, and was disconnected
20519 Session %1 has exceeded its disconnect time limit, and was logged off
20520 User config info will be loaded from domain controller for this %1 connection
20521 User config info will be loaded from local machine for this %1 connection
20522 Shadow Session Clipboard Copy Request...
Skip to content
Published on May 19, 2023
Last updated on March 3, 2025
What Is It?
The “Windows Terminal Server – Remote Connection Manager Log” records events associated with the Remote Connection Manager, which is part of the “Remote Desktop Services” (RDS) service. RDS was previously called “Terminal Services”.
The log contains information about Windows Remote Desktop connections, which are Inbound Logon Artifacts. Note that there are several other logs that contain information about RDS activity and remote logons.
What Does It Contain?
This log contains audit and debug information associated with the “Remote Connection Manager”. The Remote Connection Manager is responsible for managing the listening RDP network port (TCP port 3389) and interacting with other parts of Windows, such as “winlogon” for authentication.
The log contains several types of events, such as:
- When the service starts up
- When connections are made to it
A list of events is given below.
Relevance to DFIR?
This event log is useful when investigating inbound Windows RDP remote logins. RDP can be used by attackers to remotely control a system once they have account credentials.
Note that if the attackers used remote access software other than WIndows RDP, then this log will not have entries for those logins.
Found a Suspicious Logon?
Use our guide to analyzing suspicious logons with a free trial of Cyber Triage to quickly confirm if it’s malicious.
Storage Details
The event log file can be found at:
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
It can be disabled by setting the “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational/Enabled” key to “0”.
Specific Events
The notable event types in there include:
- Event ID 261 – Connection
- Event ID 1149 – “User Authentication Succeeded”
Note that nothing in this log will indicate a failed logon.
Cyber Triage Status
Cyber Triage collects this log file and parses it to make Inbound Logon sessions.
Sources
- https://dfironthemountain.wordpress.com/2019/02/15/rdp-event-log-dfir/
- https://ponderthebits.com/2018/02/windows-rdp-related-event-logs-identification-tracking-and-investigation
- http://blog.kiddaland.net/2015/02/remote-desktop-connections-terminal.html
- https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-r2-and-2008/cc727363(v=ws.10)

В первой части статьи (Кто и когда подключался по RDP) я в конце говорил, что скрипт не записывает ip адрес подключившегося, но при просмотре логов, ip адрес очень легко получить.
Подключение средствами RDP.
Необходимо просмотреть логи Microsoft-Windows-TerminalServices-RemoteConnectionManager по событию 1149, что бы получить возможность сопоставить пользователя с ip адресом. По умолчанию, логи настроены на малое количество записей, поэтому не забываем настроить максимальный объем журнала.
Сам скрипт выглядит вот так:
|
Get-WinEvent «Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational» | ?{$_.ID -eq «1149»} | %{ New-Object PSObject -Property @{ MachineName = $_.MachineName TimeCreated = $_.TimeCreated User = $_.Properties[0].Value Domain = $_.Properties[1].Value SourceIP = $_.Properties[2].Value } }| Out-GridView |
Данный скрипт необходимо запускать на терминальном сервере.
Подключение средствами RDG.
В случае если используется подключение через защищенное соединение — RDG (Remote Desktop Gateway), то необходимо обратиться к логам Microsoft-Windows-TerminalServices-Gateway, которые так же необходимо настроить на максимальный объем хранения.
300 — The user «%1», on client computer «%2», met resource authorization policy requirements and was therefore authorized to connect to resource «%4».
302 — The user «%1», on client computer «%2», connected to resource «%4».
303 — The user «%1», on client computer «%2», disconnected from the following network resource: «%4». Before the user disconnected, the client transferred %6 bytes and received %5 bytes. The client session duration was %7 seconds.
Источник: MS
В итоге получаем вот такой скрипт:
|
$Events = Get-WinEvent -FilterHashtable @{Logname = «Microsoft-Windows-TerminalServices-Gateway/Operational» ; ID = 300,302,303 } $date = Get-Date -format yyyy-MM-dd $ArrayList = New-Object System.Collections.ArrayList Foreach ($Event in $Events) { [xml]$Xml = $Event.ToXml() $Row = «» | Select Username,TimeCreated,IPAddress $Row.Username = $Xml.Event.UserData.EventInfo.Username $Row.TimeCreated = $Event.TimeCreated.ToString() $Row.IPAddress = $Xml.Event.UserData.EventInfo.IpAddress [void]$ArrayList.Add($Row) } $ArrayList | export-csv C:\LogFile\$date.csv -nti |
P.S.
Уже даже нарисовал формочку для скрипта:
Но это уже тема для другой статьи. 🙂
Last Updated: 12/16/2024
[Reading Time Required: 3.5 minutes]
Windows 7 Event Log files such as Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx utilize the EVTX file extension. This file is considered a System (Windows 7 Event Log) file, and was first created by NCH Software for the NCH Express Scribe 8.26 software package.
The initial introduction of Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx released in KMPlayer 2019.06.13.02 was for Windows 10 on 06/13/2019.
The newest file release date for NCH Express Scribe 8.26 was 11/27/2019 [version 8.26].
Below, you find comprehensive file information, instructions for simple EVTX file troubleshooting, and list of free Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx downloads for each available file version.
What are Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx Error Messages?
General Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx Runtime Errors
Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx file errors often occur during the startup phase of NCH Express Scribe, but can also occur while the program is running.
These types EVTX errors are also known as “runtime errors” because they occur while NCH Express Scribe is running. Here are some of the most common Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx runtime errors:
- Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx could not be found.
- Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx error.
- Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx failed to load.
- Error loading Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx.
- Failed to register Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx / Cannot register Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx.
- Runtime Error — Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx.
- The file Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx is missing or corrupt.
Microsoft Visual C++ Runtime Library
Runtime Error!
Program: C:\Windows\System32\winevt\Logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx
This application has requested the Runtime to terminate it in an unusual way.
Please contact the application’s support team for more information.
Most EVTX errors are due to missing or corrupt files. Your Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx file could be missing due to accidental deletion, uninstalled as a shared file of another program (shared with NCH Express Scribe), or deleted by a malware infection. Furthermore, Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx file corruption could be caused from a power outage when loading NCH Express Scribe, system crash while loading or saving Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx, bad sectors on your storage media (usually your primary hard drive), or malware infection. Thus, it’s critical to make sure your anti-virus is kept up-to-date and scanning regularly.
How to Fix Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx Errors in 3 Steps (Time to complete: ~5-15 minutes)
If you’re encountering one of the error messages above, follow these troubleshooting steps to resolve your Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx issue. These troubleshooting steps are listed in the recommended order of execution.
Step 1: Restore your PC back to the latest restore point, «snapshot», or backup image before error occurred.
To begin System Restore (Windows XP, Vista, 7, 8, and 10):
- Hit the Windows Start button
- When you see the search box, type «System Restore» and press «ENTER«.
- In the search results, find and click System Restore.
- Please enter the administrator password (if applicable / prompted).
- Follow the steps in the System Restore Wizard to choose a relevant restore point.
- Restore your computer to that backup image.
If the Step 1 fails to resolve the Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx error, please proceed to the Step 2 below.
Step 2: If recently installed NCH Express Scribe (or related software), uninstall then try reinstalling NCH Express Scribe software.
You can uninstall NCH Express Scribe software by following these instructions (Windows XP, Vista, 7, 8, and 10):
- Hit the Windows Start button
- In the search box, type «Uninstall» and press «ENTER«.
- In the search results, find and click «Add or Remove Programs«
- Find the entry for NCH Express Scribe 8.26 and click «Uninstall«
- Follow the prompts for uninstallation.
After the software has been fully uninstalled, restart your PC and reinstall NCH Express Scribe software.
If this Step 2 fails as well, please proceed to the Step 3 below.
NCH Express Scribe 8.26
NCH Software
Step 3: Perform a Windows Update.
When the first two steps haven’t solved your issue, it might be a good idea to run Windows Update. Many Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx error messages that are encountered can be contributed to an outdated Windows Operating System. To run Windows Update, please follow these easy steps:
- Hit the Windows Start button
- In the search box, type «Update» and press «ENTER«.
- In the Windows Update dialog box, click «Check for Updates» (or similar button depending on your Windows version)
- If updates are available for download, click «Install Updates«.
- After the update is completed, restart your PC.
If Windows Update failed to resolve the Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx error message, please proceed to next step. Please note that this final step is recommended for advanced PC users only.
If Those Steps Fail: Download and Replace Your Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx File (Caution: Advanced)
If none of the previous three troubleshooting steps have resolved your issue, you can try a more aggressive approach (Note: Not recommended for amateur PC users) by downloading and replacing your appropriate Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx file version. We maintain a comprehensive database of 100% malware-free Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx files for every applicable version of NCH Express Scribe. Please follow the steps below to download and properly replace you file:
- Locate your Windows operating system version in the list of below «Download Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx Files».
- Click the appropriate «Download Now» button and download your Windows file version.
- Copy this file to the appropriate NCH Express Scribe folder location:
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\Show 71 more directories +
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\
Windows 10: C:\Windows\System32\winevt\Logs\ - Restart your computer.
If this final step has failed and you’re still encountering the error, you’re only remaining option is to do a clean installation of Windows 10.
GEEK TIP : We must emphasize that reinstalling Windows will be a very time-consuming and advanced task to resolve Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx problems. To avoid data loss, you must be sure that you have backed-up all of your important documents, pictures, software installers, and other personal data before beginning the process. If you are not currently backing up your data, you need to do so immediately.
Download Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx Files (Malware-Tested 100% Clean)
CAUTION : We strongly advise against downloading and copying Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx to your appropriate Windows system directory. NCH Software typically does not release NCH Express Scribe EVTX files for download because they are bundled together inside of a software installer. The installer’s task is to ensure that all correct verifications have been made before installing and placing Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Admin.evtx and all other EVTX files for NCH Express Scribe. An incorrectly installed EVTX file may create system instability and could cause your program or operating system to stop functioning altogether. Proceed with caution.
You are downloading trial software. The purchase of a one-year software subscription at the price of $29.97 USD is required to unlock all software features. Subscription auto-renews at the end of the term (Learn more). By clicking the «Start Download» button above and installing «Software», I acknowledge I have read and agree to the Solvusoft End User License Agreement and Privacy Policy.
