What is Event ID 4771: Kerberos Pre-Authentication Failed. Event ID 4771 is a common error message that is generated by the Windows security auditing feature. It typically indicates that a user’s Kerberos pre-authentication attempt has failed.
In this article, we’ll explore the causes and consequences of this error message and discuss best practices for troubleshooting and resolving it.
What is Kerberos Pre-Authentication?
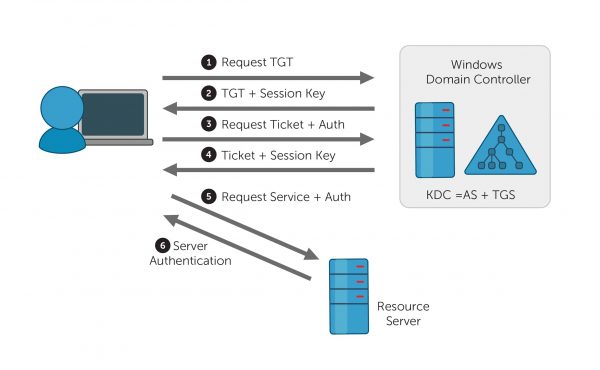
Kerberos is a widely used network authentication protocol in Windows. It provides secure authentication for network resources by using a ticket based system. When a user attempts to access a network resource, Kerberos creates a ticket that contains the user’s authentication information. The user then presents this ticket to the network resource to gain access.
To ensure the security of the authentication process Kerberos uses pre-authentication which is a process of checking user’s credentials before granting them access to a network resource. Windows encrypts the user’s password and sends it to the Kerberos server for validation during pre-authentication. Windows grants user a ticket for accessing network resources, if the password is correct.
What is Event ID 4771?
Event ID 4771 is a type of event log message generated by the Windows system’s security auditing feature. This message is logged after a failed user’s Kerberos pre-authentication attempt. The message contains information about the user, the computer, and the reason for the authentication failure.
The message contains:
- Logon Account: The user account used to log on to the computer.
- Source Workstation: Contains the name of the computer from which the user attempted to log on.
- Error Code: Contains the error code that the Kerberos pre-authentication process returned.
The error code provides valuable information about the cause of the authentication failure. Common error codes include:
- 0x18: This error code indicates an account lockout.
- 0x6: The user’s password has expired.
- 0x12: The user’s account is no longer active.
- 0x24: The user’s password is incorrect.
Try our Active Directory & Office 365 Reporting & Auditing Tools
Try us out for Free. 100’s of report templates available. Easily customise your own reports on AD, Azure AD & Office 355.
What Causes Event ID 4771?
There are several reasons why a Kerberos pre-authentication attempt might fail and generate Event ID 4771. The most common causes include:
- Incorrect Password: If a user enters an incorrect password during the pre-authentication process, Kerberos rejects the authentication attempt and generate this Event ID.
- Expired Password: If a user’s password has expired, Kerberos generates this event ID.
- Locked Out Account: If the Windows locks out a user due to too many failed login attempts, Kerberos rejects the authentication attempt and generates Event ID.
- Disabled Account: If Windows disables the account of a user, Kerberos rejects the authentication attempt and generates Event ID 4771.
- Clock Skew: If there is a significant difference in time between the client and the server, Kerberos generates this event ID.
- Malware or Other Security Threats: Sometimes, malware and other other security threats on the network cause this Event ID.
What are the Consequences of Event ID 4771?
Event ID 4771 can have several consequences for users and network administrators. For users, the most immediate consequence is the inability to access network resources. If a user’s Kerberos pre-authentication attempt fails, they are not be granted a ticket to access network resources, even if their password is correct.
For network admins, this event could indicate more dire implications. A large number of such Event ID messages indicate a potential security threat on the network, such as a brute force attack or a malware infection. Additionally, if this Event ID messages are ignored, this could lead to a loss of network security and data breaches.
How to Troubleshoot and Resolve Event ID 4771?

To troubleshoot and resolve Event ID 4771, network admins should follow the following best practices:
- Analyse the Event Log: The first step in troubleshooting this event ID is to analyse the event log message. The error code contained in the message provides valuable information about the cause of the authentication failure.
- Check the User Account: The second step is to check the user account associated with the failed authentication attempt. This may include checking the user’s password status, account status, and lockout status.
- Check the Source Workstation: Network admin should also check the source workstation associated with the failed authentication attempt. This may include checking the computer’s security status and antivirus software.
- Check the Time Synchronization: Time synchronization issues cause clock skew and lead to authentication failures. Therefore check the time synchronization settings on the client and server.
- Check for Malware and Security Threats: If Event ID 4771 messages continue to occur, network admins should check for malware and other security threats on the network.
- Reset Passwords and Unblock Accounts: If the cause of the authentication failure is due to an incorrect password or a locked-out account, network administrators should reset passwords and unblock accounts as needed.
- Implement Multi-Factor Authentication: Multi-factor authentication provides an additional layer of security and prevent brute-force attacks. Network admins should consider implementing multi-factor authentication on the network.
- Monitor the Event Log: Finally, network administrators should monitor the event log for Event ID 4771 messages and take appropriate action as needed: investigating potential security threats and implementing additional security measures.
What is Event ID 4771: Kerberos Pre-Authentication Failed Conclusion
Event ID 4771 is a common error message that is generated by the Windows security auditing feature. It indicates that a user’s Kerberos pre-authentication attempt has failed.
To troubleshoot and resolve it, network administrators should follow best practices that include analysing the event log, checking user accounts and source workstations, checking time synchronization, checking for malware and security threats, resetting passwords and unblocking accounts, implementing multi-factor authentication, and monitoring the event log.
By following these best practices, you can prevent security threats, ensure network security, and provide a secure environment for users to access network resources.
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
The Kerberos pre-authentication failed error indicates that the user cannot log in to Windows or any other network resource. This error occurs when there’s a problem with the Kerberos pre-authentication process.
It can occur if you use an incorrect username or password if your computer is offline or not connected to the network, or if an error occurs when connecting to a domain controller.
Why am I getting the Event ID 4771 error?
This error means that you tried to connect to a server using Kerberos pre-authentication, but the server did not respond to your request. In Windows, Kerberos pre-authentication verifies a user’s credentials before the KDC authenticates them.
If the pre-authentication fails, the user will be prompted for their password. For some users, the error code was Event ID 4771. Kerberos pre-authentication failed 0x18 on their PCs. For this code, the issue is a bad password. However, for Event ID 4771, this can happen for several reasons:
- Server clock mismatch – The likely cause is that your computer’s clock is out of sync with the server’s clock. This can happen if your computer was offline for a long time and returned online but failed to synchronize its clock.
- Incorrect password – Most users who encountered the Event ID 4771 error admitted to having recently changed their passwords. However, for unique IDs such as Event ID 4771 status 0x12, it means that the user’s credentials have been revoked.
- Cached credentials – Cached credentials are used to reduce login times and to improve security because they’re obtained automatically from the directory server. However, when you changed passwords, they may cause conflicts.
- Wrong domain – Make sure that you’re logging on to an account from the same domain as the computer you’re connecting from; otherwise, there will be no way for Active Directory to verify your credentials correctly.
How can I solve the Event ID 4771 error?
1. Enable failed logon auditing
- Hit the Windows + R keys to open the Run command.
- Type secpol.msc in the dialog box and hit Enter.
- Navigate to the following location:
Security settings/Local Policy/Audit Policies/Audit Logon Events - Double-click on Audit logon events, select Success/Failure, then click on Apply and OK.
This will generate a security event whenever a user attempts to log into a domain-joined computer and fails. Failed logon auditing will allow you to see when users have attempted to log onto the network unsuccessfully and to identify any duplicates.
Then, you can rename the accounts with duplicate names on one or more servers, or create new accounts for them with unique names.
2. Delete cached passwords
- Hit the Windows key, type cmd in the search bar and click Open.
- Type the following commands and hit Enter after each one:
psexec -i -s -d cmd.exerundll32 keymgr.dll KRShowKeyMgr - A list of stored usernames and passwords will appear. Delete them from your server and restart your PC.
This happens because the Kerberos subsystem caches the old password in memory. When you change the password, it doesn’t get cleared from memory until it expires.
The Kerberos client then tries to use the old cached password, which doesn’t work because it has been changed on the domain controller.
- Microsoft’s hotpatching for Windows Server 2025 to be subscription-based starting July
- Microsoft releases the Windows Server Build 26360, introducing the WDAC for enhanced security
- How to Fix ERROR_SCRUB_DATA_DISABLED on Windows Server
- Windows Server 2025 and System Center 2025 have entered general availability
3. Enable audit logon
- Hit the Windows key, type Powershell in the search bar and click Run as administrator.
- Type the following command and hit Enter:
auditpol /set /subcategory:”logon” /failure:enable
When you enable logon auditing, it helps you determine if someone is trying to gain unauthorized access to your systems by guessing passwords or attempting other brute-force attacks.
Hopefully, you have bypassed the Event ID 4771 Kerberos pre-authentication failed error with one of these methods.
You may also come across an Event ID 4768, where your Kerberos authentication ticket is requested. If so, don’t hesitate to check out our expert article.
In the comment section below, let us know what solution fixed this error for you.
Claire Moraa
Windows Software Expert
Claire has a knack for solving problems and improving the quality of life for those around her. She’s driven by rationality, curiosity, and simplicity, and always eager to learn more about Microsoft’s products.
With a background in teaching and reviewing, she breaks down complex topics into easily understandable articles, focusing mostly on Windows 11, errors, and software.
Last Updated on February 28, 2025 by Satyendra

What is Kerberos?
Kerberos is a network authentication protocol used in Windows domains. It is used to verify the identity of users and computers across an untrusted network such as the internet. Kerberos support is built into all major computer operating systems, including Microsoft Windows.
Pre-authentication is an initial step in the Kerberos process where the client proves its identity to the Key Distribution Center (KDC).
Since Windows 2000, the Kerberos protocol has been used by Microsoft as the default authentication method, and it is a fundamental part of the Windows Active Directory (AD) service.
What is Event ID 4771?
Event ID 4771, “Kerberos pre-authentication failed,” is a common security event in Windows environments.
This event generates every time the Key Distribution Center (KDC) fails to issue a Kerberos Ticket Granting Ticket (TGT) and indicates that the Key Distribution Center (KDC) could not validate the client’s initial identity claim. The event is logged on domain controllers.
Note that this event is not generated if the “Do not require Kerberos preauthentication” option is set for the account.
The following are some of the common causes for event ID 4771 to be generated:
| Causes | Description |
|---|---|
| Incorrect Password | This is the most frequent cause |
| Expired Password | The user’s password has expired |
| Locked-Out Account | The user’s account has been locked due to too many failed login attempts |
| Disabled Account | The user’s account has been disabled in Active Directory. |
How Lepide Auditor Helps
It is essential that an administrator has visibility over what is happening in their Active Directory. This ensures that any suspicious activity relating to potential security threats is identified and can be responded to immediately.
The Lepide Active Directory Auditing Tool enables effective monitoring, auditing, and reporting on all Active Directory states and changes including account logon events. The Lepide Auditor includes pre-configured account logon reports to help identify malicious users attempting to logon to machines that require elevated privileges.
- Active Directory
| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 |
|
Category • Subcategory |
Account Logon • Kerberos Authentication Service |
| Type | Failure |
|
Corresponding events in Windows 2003 and before |
675
|
4771: Kerberos pre-authentication failed
On this page
- Description of this event
- Field level details
- Examples
This event is logged on domain controllers only and only failure instances of this event are logged.
At the beginning of the day when a user sits down at his or her workstation and enters his domain username and password, the workstation contacts a local DC and requests a TGT. If the username and password are correct and the user account passes status and restriction checks, the DC grants the TGT and logs event ID 4768 (authentication ticket granted).
If the ticket request fails Windows will either log this event, failure 4771, or 4768 if the problem arose during «pre-authentication». In Windows Kerberos, password verification takes place during pre-authentication.
The User field for this event (and all other events in the Audit account logon event category) doesn’t help you determine who the user was; the field always reads N/A. Rather look at the Account Information: fields, which identify the user who logged on and the user account’s DNS suffix. The User ID field provides the SID of the account.
Windows logs other instances of event ID 4768 when a computer in the domain needs to authenticate to the DC typically when a workstation boots up or a server restarts. In these instances, you’ll find a computer name in the User Name and fields. Computer generated kerberos events are always identifiable by the $ after the computer account’s name.
Result codes:
| Result code | Kerberos RFC description | Notes on common failure codes |
| 0x1 | Client’s entry in database has expired | |
| 0x2 | Server’s entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client’s key encrypted in old master key | |
| 0x5 | Server’s key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid — try again later | |
| 0x16 | Server not yet valid — try again later | |
| 0x17 | Password has expired | The user’s password has expired. |
| 0x18 | Pre-authentication information was invalid | Usually means bad password |
| 0x19 | Additional pre-authentication required* | |
| 0x1F | Integrity check on decrypted field failed | |
| 0x20 | Ticket expired | Frequently logged by computer accounts |
| 0x21 | Ticket not yet valid | |
| 0x21 | Ticket not yet valid | |
| 0x22 | Request is a replay | |
| 0x23 | The ticket isn’t for us | |
| 0x24 | Ticket and authenticator don’t match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28 | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | may be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4771
Account Information:
- Account Name: logon name of the account that just authenticated
- Supplied Realm Name: domain name of the account
- User ID: SID of the account
Service Information:
- Service Name: always «krbtgt»
- Service ID:
Network Information:
- Client Address: IP address where user is present
- Client Port: source port
Additional Information:
- Ticket Options: unknown. Please start a discussion if you have information to share on this field.
- Failure Code: error if any — see table above
- Pre-Authentication Type: unknown. Please start a discussion if you have information to share on this field.
Certificate Information:
This information is only filled in if logging on with a smart card.
- Certificate Issuer Name:
- Certificate Serial Number:
- Certificate Thumbprint:
Supercharger Enterprise
Load Balancing for Windows Event Collection
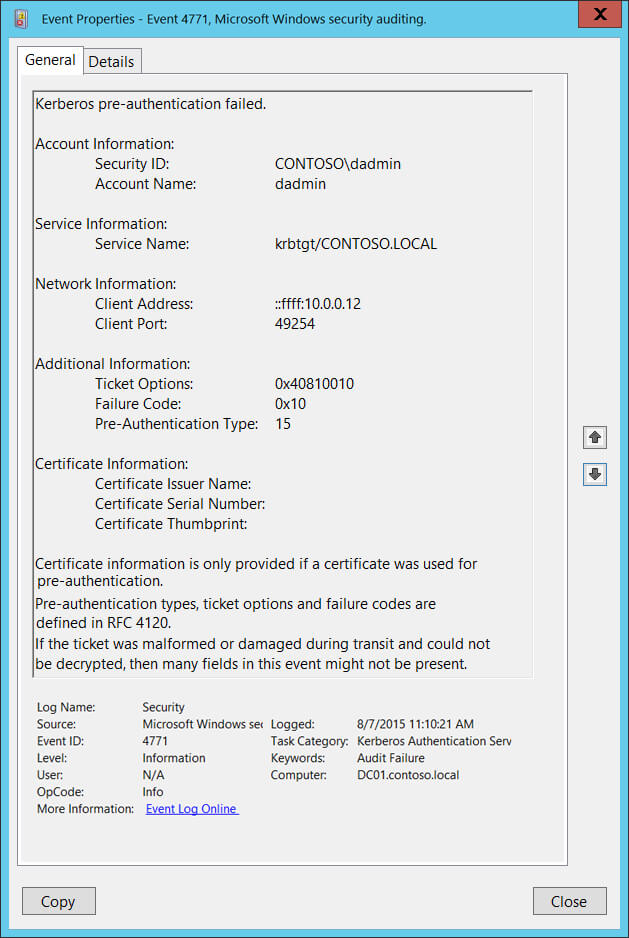
Examples of 4771
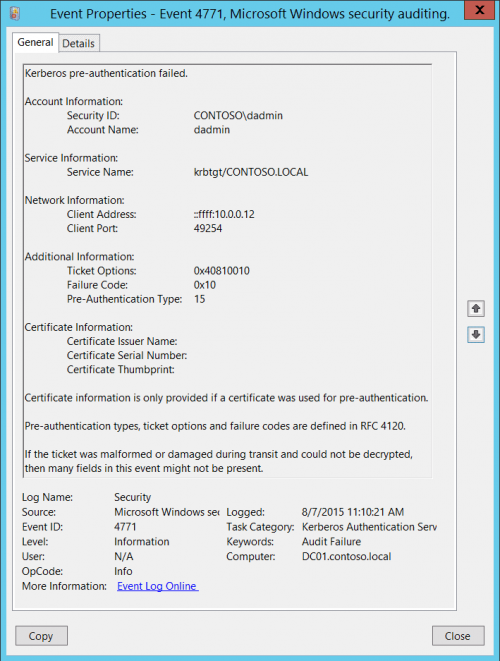
Kerberos pre-authentication failed.
Account Information:
Security ID: ACME\administrator
Account Name: Administrator
Service Information:
Service Name: krbtgt/acme
Network Information:
Client Address: ::ffff:10.42.42.224
Client Port: 50950
Additional Information:
Ticket Options: 0x40810010
Failure Code: 0x18
Pre-Authentication Type: 2
Certificate Information:
Certificate Issuer Name:
Certificate Serial Number:
Certificate Thumbprint:
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options and failure codes are defined in RFC 4120.
If the ticket was malformed or damaged during transit and could not be decrypted, then many fields in this event might not be present.
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
- Insider Gone Bad: Tracking Their Steps and Building Your Case with the Security Log
- Building a Security Dashboard for Your Senior Executives
- 27 Most Important Windows Security Events
- 5 Ways to Reduce Information Overload from Your Log Management/SIEM
- Daily Security Log Check for the SMB IT Admin
- Integrating Splunk with native Windows Event Collection (WEC) and Optional 2-Stage Noise Filtering
- How to do Logon Session Auditing with the Windows Security Log
- Top Windows Security Log Events for User Behavior Analysis
- 4 Threat Detections using Active Directory Authentication Events from the Windows Security Log
- Understanding Active Directory Authentication Events in the Windows Security Log and Beyond
- Security Log Deep Dive: Mapping Active Directory Authentication and Account Management Events to MITRE ATT&CK TTPs
- Detecting and Preventing AD Authentication Risks: Golden Tickets, NTLM, Pass-the-Hash and Beyond
- Windows Security Log Deep Dive: Understanding Kerberos Authentication Events from Domain Controllers
- Assessing the Security of Your Active Directory: User Accounts
- The Changing Landscape of Authentication and Logon Tracking in Hybrid Environments of Entra and AD
4771 — Kerberos Failure
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4771
Event ID 4771 is a critical event in Windows security auditing, indicating a Kerberos pre-authentication failure. This event is logged on the domain controller that receives the pre-authentication request and plays a vital role in monitoring and diagnosing issues related to Kerberos authentication processes. Understanding the details and substatus codes of Event ID 4771 is crucial for identifying authentication issues, potential attack vectors, and maintaining secure access controls.
Key Details of Event ID 4771
-
Log Location: Security log on domain controllers.
-
Category: Audit Kerberos Authentication Service
Event ID 4771 is logged when a Kerberos pre-authentication request fails. This can occur in various scenarios, such as:
-
Incorrect user password entries.
-
Attacks attempting to guess passwords.
-
Configuration or communication issues between the client and the domain controller.
Information Contained in the Log
An Event ID 4771 log contains several pieces of information crucial for diagnosing authentication issues:
-
Client Address: Shows the IP address of the client from which the logon attempt was made.
-
Client Port: Indicates the port number used by the client machine for the connection.
-
Pre-authentication Type: Specifies the type of pre-authentication used, often indicating the use of passwords (type 2).
-
Failure Code: A key element that specifies why the pre-authentication failed.
-
User Name: The name of the user for whom the logon attempt was made.
-
Service Name: The name of the service that was requested, typically the Kerberos Ticket Granting Service (TGS).
-
Ticket Options: Specifies various flags related to the ticket that was requested.
Common Failure Codes and Their Meanings
Understanding the failure codes provided in Event ID 4771 logs is essential for diagnosing and addressing authentication issues:
-
0x18: Pre-authentication information was invalid. This often indicates an incorrect password was entered.
-
0x12: Account restrictions are preventing this user from signing in. For example: not allowed to log in from this computer, logon hours restrictions, or account disabled.
-
0x25: The user has to reset their password.
-
0x1F: An unspecified error has occurred.
Event ID 4771 is instrumental in security monitoring for several reasons:
-
Detecting Brute-Force Attacks: Multiple 4771 events with failure code 0x18 from the same client address may indicate a brute-force password guessing attack.
-
Identifying Configuration Issues: Failures related to account restrictions (code 0x12) can highlight misconfigurations that may inadvertently prevent legitimate access.
-
Password Attack Detection: An unusually high volume of 4771 events across various accounts might signal a more extensive password spray attack.
Tools and Strategies for Analysis
-
Windows Event Viewer: Manually inspect the Security log on domain controllers for 4771 events.
-
PowerShell: Automate the extraction and analysis of 4771 events from domain controllers’ logs.
-
SIEM Systems: Aggregate and correlate 4771 events with other security logs to detect patterns indicative of attacks or systemic issues.