| Operating Systems | Windows Server 2019 and 2022 |
|
Category • Subcategory |
System • Other System Events |
| Type | Success |
|
Corresponding events in Windows 2003 and before |
5379: Credential Manager credentials were read
On this page
- Description of this event
- Field level details
- Examples
This is event is new in Windows Server 2019. This event occurs when a user performs a read operation on stored credentials in Credential Manager.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
5379
Subject:
The user and logon session that performed the action.
- Security ID: The SID of the account.
- Account Name: The account logon name.
- Account Domain: The domain or — in the case of local accounts — computer name.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events logged during the same logon session.
- Read Operation:
Supercharger Free Edition
Your entire Windows Event Collection environment on a single pane of glass.
Free.
Examples of 5379
Subject:
Security ID: %1
Account Name: %2
Account Domain: %3
Logon ID: %4
Read Operation: %8
This event occurs when a user performs a read operation on stored credentials in Credential Manager.
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
Stay up-to-date on the Latest in Cybersecurity
Sign up for the Ultimate IT Security newsletter
to hear about the latest webinars, patches, CVEs, attacks, and more.
Work Email:
|
Upcoming Webinars |
Additional Resources |
Attacks by malware are continuously growing. These malicious files use high-obfuscation algorithms to hide from traditional anti-malware detection solutions, and unfortunately, the threat actors are becoming more and more successful.
One technique that has seen a positive track record for evading detection is when a malicious document is password-protected, and the password is given in the email body, making it easy to trick unsuspecting users into opening the malicious file.
Password protection makes it harder for traditional detection solutions to scan the attachment for malicious code.
Also Read: Most Common Windows Event IDs to Hunt – Mind Map
Example of the Malware Attack
The employee receives an email that appears to be from a trusted and well-known sender, or a common brand, with a catchy subject (ex. ‘Invoice’, ‘Payment verification’, etc). The email contains an attached file that is zipped and password-protected by the attacker, and they’ll also include a full name (e.g. Tenesha Mitchell) to make it seem human. The password creates the illusion the attachment must contain confidential personal information that had to be secured.
When an employee receives the compromised email with the password-protected file and the required password to access the file, it raised no suspicions.
Also Read: Threat Hunting Using Windows Security Log
Attack Detection with Windows Event Logs
Example 1: Attack Detection Case
This event occurs when a user performs a read operation on stored credentials in Credential Manager. Example: Users open up ZIP files which are password-protected files with valid credentials.
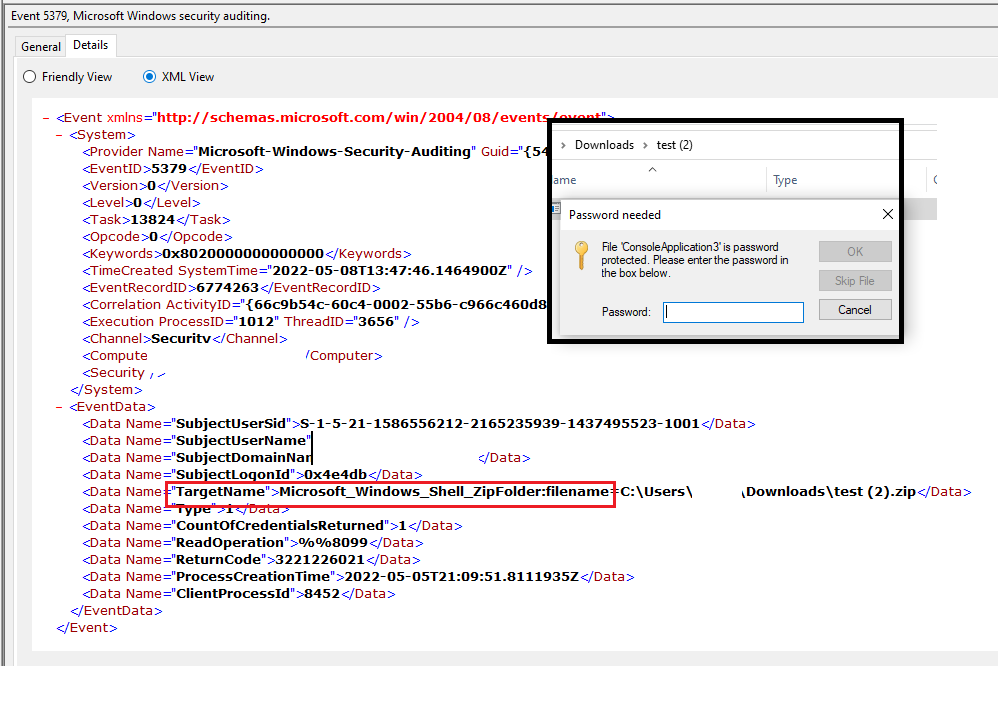
The above figure illustrates User has opened the test (2).zip file. SBousseaden says opening a password-protected zip file using Windows Explorer generates a credman event 5379 with Target “Microsoft_Windows_Shell_ZipFolder:filename=zip_fil_path”.
Also Read: Malware Hiding Techniques in Windows Operating System
This can be correlated when malware is executed with windows legitimate processes ( Explorer.exe ) on specific file paths. Similar cases are also observed when users download, cracks/keygens to enable the full features of legitimate software. But ending up with system/network infections.
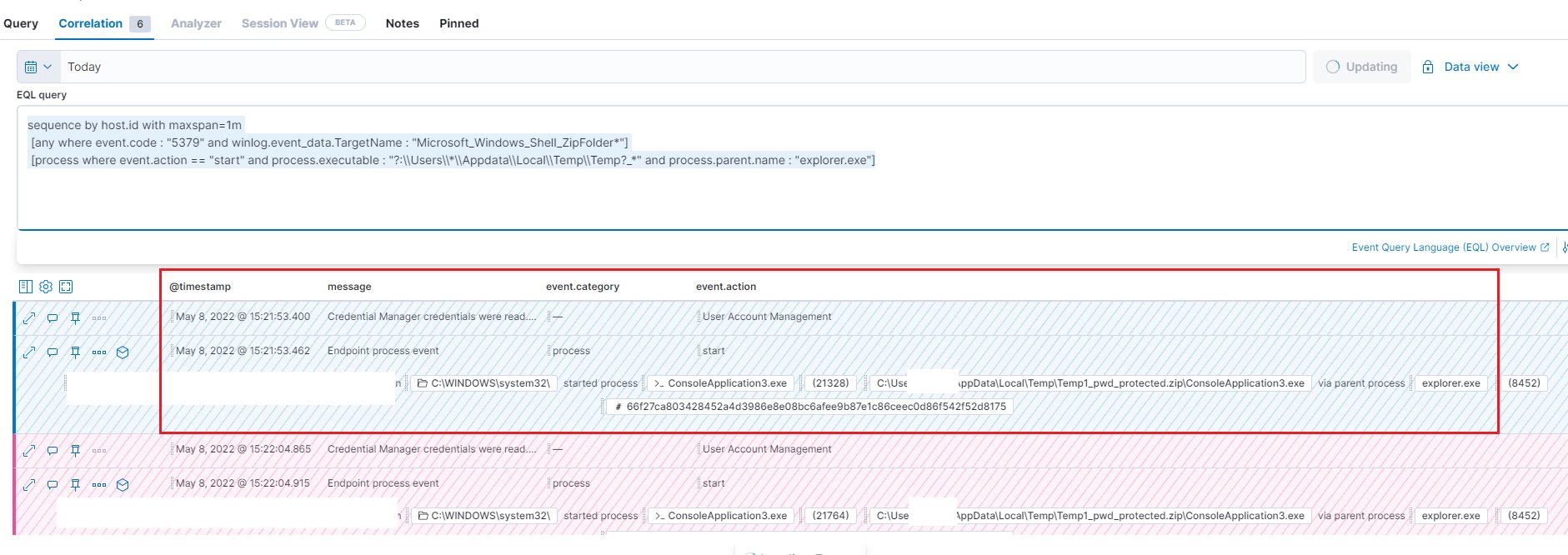
The above query shows that malware spread has been successfully detected using the event ID 5379.
Example 2: False Positive Case
Some people may experience Event ID 5379 flooding. It is good to review their user accounts/programs that are connected with the credential manager.
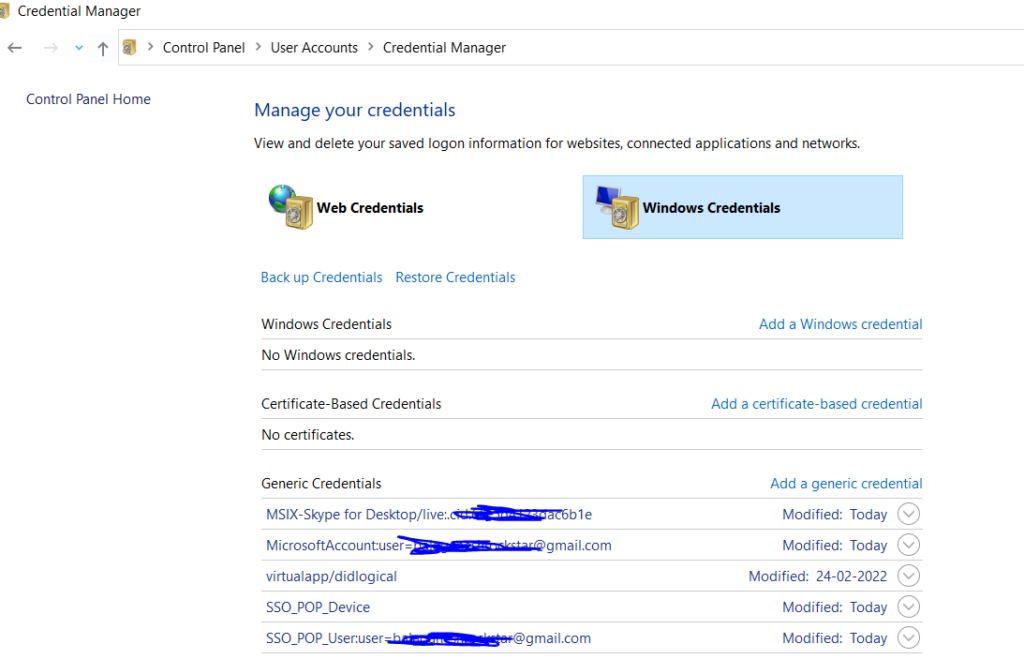
Assume Windows admin has disabled a user in my Active Directory (terminated the account). However, still getting the log that Event IDs 5379 (credential manager credentials were read.), 4673 (a privileged service was called.), 4656 (a handle to an object was requested.)
And the processes called are:
gfxdownloadwrapper.exe 4673
lsbupdater.exe 4673
cleanmgr.exe 4673
quickup.exe 4673
searchui.exe 4673
Disabling an account in AD doesn’t mean an account cannot log on to an endpoint due to cached credentials. The account may not have been disabled/removed from the machine in question, so some scheduled tasks associated with the account are still being executed on the machine (e.g. search indexing, disk cleanup, etc).
Considering the above scenario we can mark it as false-positive.
EQL Detection Query:
sequence by host.id with maxspan=1m [any where event.code : "5379" and winlog.event_data.TargetName : "Microsoft_Windows_Shell_ZipFolder*"] [process where event.action == "start" and process.executable : "?:\\Users\\*\\Appdata\\Local\\Temp\\Temp?_*" and process.parent.name : "explorer.exe"] Also Read: How to Detect Privilege Escalation Attacks and UAC Bypass on Windows
Other SIEM Products:
SOC analyst/ SOC Engineers use the below logic to create effective rules on their SIEMS to track Windows Event ID 5379 with malicious behaviors.
Correlate event ID 5379 with Target name "Microsoft_Windows_Shell_ZipFolder*" and process executable paths "?:\\Users\\*\\Appdata\\Local\\Temp\\Temp?_*" and parent process "explorer.exe" and process action is start.
Happy Hunting!
References:
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=5379
securityboulevard.com
https://serverfault.com/questions/1092543/a-user-activity-is-detected-from-a-disabled-account-in-active-directory
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Have you noticed an event ID 5379 popup in the event viewer at the same time as your mouse disconnects? If you have, you are probably wondering what the solution is.
In this article, we have investigated the problem, and we introduce probable triggers as well as the most practical solutions.
Why does my mouse disconnect with the event ID 5379 notification?
The following are the possible causes of this disconnecting mouse issue:
- Faulty or incompatible mouse driver – It’s possible that the mouse driver installed on your computer is either outdated, corrupted, or incompatible with your operating system.
- USB power management – Sometimes, when the system goes into power-saving mode, it might disable the USB ports, which can cause the mouse to disconnect.
- Wireless interference – If you use a wireless mouse, the connection may be affected by other devices or wireless signals in the surrounding area.
- Hardware or mouse defect – Sometimes, a faulty or malfunctioning mouse can cause frequent disconnections. It’s important to consider hardware issues as a potential factor.
How do I fix event ID 5379 caused by a disconnected mouse?
Before going into any detailed solution, try the following workarounds:
- Check for hardware damage – You may try the mouse on a different computer and replace your mouse if it is damaged.
- Restart the computer – In some cases, the glitch may be minor, and a simple reboot will force any problematic process causing the error to stop.
- Stay within range – If you use a wireless mouse, ensure you are within range to avoid disconnection.
- Check USB connections – Ensure the cables or USB ports are not damaged; you may clean them to remove particles.
If none of the pre-solutions work, proceed to the major fixes we explore below.
1. Update mouse drivers
- Right-click the Start menu and select Device Manager.
- Expand the Mice and other pointing devices category, right-click on your mouse, and click Update driver.
- Select Search automatically for drivers.
- Verify it fixes the mouse disconnection causing the event ID 5379.
Often, your computer system might not be able to update the generic drivers for your hardware and peripherals correctly. There are vital differences between a generic driver and a manufacturer’s driver. Finding the correct driver versions for every hardware component can become tiresome.That’s why a dependable updater can help you find and update your drivers automatically. We strongly suggest the Outbyte Driver Updater, and here’s how to do it:
- Download and install the Outbyte Driver Updater app.
- Launch the software and wait for the app to detect all incompatible drivers.
- Now, it will show you a list of all outdated drivers to select the ones to Update or Ignore.
- Click on Update & Apply Selected to download and install the latest versions.
- Restart your PC to ensure the applied changes.
Outbyte Driver Updater
Maintain your device healthy by letting OutByte Driver Updater find the latest driver options.
Disclaimer: You may need to upgrade the app from the free version to perform specific actions.
2. Restore the computer
- Press Windows + R to open the Run dialog.
- Type rstrui, and hit Enter.
- Click the Next button.
- Select a restore point and hit Next.
- Click on Finish.
- The computer would restart in the process, but at the end, verify that it fixes the mouse disconnection that triggers event id 5379.
- D3dx11_42.dll Not Found: How to Fix it
- Windows 11 Shutdown After Inactivity: 4 Ways to Stop it
- Windows Shuts Down Instead of Restarting: 4 Ways to Fix it
- Error no Ace Condition 804 (0x324): Fix it With 4 Steps
- Windows 11 Shutdown But User Stays Logged in: How to Fix it
3. Adjust the Power Management settings
- Right-click the Start menu and select Device Manager.
- Expand the Universal Serial Bus controllers category.
- Right-click on each USB Root Hub and select Properties.
- In the Properties window, go to the Power Management tab, then uncheck the box that says Allow the computer to turn off this device to save power.
- Click OK, and now, repeat these steps for all USB Root Hubs listed.
- Finally, restart your computer and check if the mouse disconnection issue persists.
There you have it. Note that we have not discussed these fixes in any particular order, so after the initial workarounds, you should try whatever seems the most applicable to your situation.
You may also want to read more on mouse disconnection issues if you need further troubleshooting.
Please let us know what worked for you in the comments section below.
Afam Onyimadu
Windows Software Expert
Afam is a geek and the go-to among his peers for computer solutions. He has a wealth of experience with Windows operating systems, dating back to his introduction to Windows 98. He is passionate about technology amongst many other fields. Aside from putting pen to paper, he is a passionate soccer lover, a dog breeder, and enjoys playing the guitar and piano.
RDP forensic event logs — RDP в журналах событий ОС Windows 10
(статья в стадии написания не окончена)
Журналы событий обеспечивают контрольный журнал, который записывает пользовательские события и действия на компьютере и являются потенциальным источником доказательств в цифровой криминалистике исследования.
В этой статье мы рассмотрим процесс экспертизы событий event logs в Windows 10 Версия 1809 (Сборка ОС 17763.195), 64 и 32 разрядных операционных систем, относящейся к RDP (Remote Desktop Protocol) – специальный протокол, разработанный компанией Microsoft для удаленного управления ОС Windows (протокол удалённого рабочего стола).
Версии Windows начиная с Vista включают ряд новых событий, которые не регистрируются системами Windows XP. Выпуски Windows Server содержат большее количество и типы событий.
журналы событий Windows получили расширение *.EVTX. Этот новый формат, называемый форматом Windows XML Event Log (EVTX), заменяет формат EVT, используемый в Windows XP. Помимо журналов событий начиная с Vista, существуют журналы приложений и служб, которые записывают события о конкретном компоненте или приложении, а не о системе. В системе Windows 7/2008 можно найти много файлов журнала событий в зависимости от ролей, выполняемых системой. Здесь Вы можете найти журналы событий приложений. Например, если в системе есть Symantec Endpoint, у Вас будет файл «Symantec Endpoint Protection Client.evtx». Различные категории описаны
Ссылка скрыта от гостей
К примеру в Windows XP и Server 2003 было 9 категорий, а начиная с Windows Vista их более 50.
C:\Windows\system32>auditpol /get /category:*
Таким образом, точная идентификация версии операционной системы Windows должна быть очень тщательно продумана при разработке цифрового процесса компьютерно-технической экспертизы, основанного на журналах событий (event logs).
Расположение журналов событий Windows по умолчанию:
Windows 2000/Server2003/Windows XP:
\%SystemRoot%\System32\Config\*.evt
Windows Vista/7/Server2008/10/Server2012/Server2016:
\%SystemRoot%\System32\winevt\Logs\*.evtx
Расположение журналов может быть изменено пользователем, изменением значения ключа реестра «
File
» в «HKEY_LOCAL_MACHINE» на локальном компьютере:
Application Events (События приложения):
Компьютер\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\Application
Hardware Events (Аппаратные события):
Компьютер\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\HardwareEvents
Security Events (События безопасности):
Компьютер\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\Security
System Events (Системные события):
Компьютер\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\System
Когда используется пользовательский путь, ключ создается в месте реестра:
Компьютер\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\[logname]
(например [logname] это: Microsoft-Windows-TerminalServices-LocalSessionManager/Admin)
Полезные события для криминалистического анализа
Коды входа в систему.
Одно из важных сведений, предоставляемых событием «Успешный/Неудачный вход в систему», является то, как пользователь/процесс пытался войти в систему (Тип входа в систему), но Windows отображает эту информацию в виде числа.
RDP Successful Logon — RDP Успешный вход
Рассмотрим практический пример с ПК physical IP 192.168.10.146 было подключение mstsc.exe к ПК distrusting IP 192.168.10.241 с учетной записью suspect
Осмотр событий ПК к которому мы подключились: host distrusting IP 192.168.10.241
Рассмотрим первое, место расположения Event ID 1149
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx это у нас Network Connection
Рассмотрим второе, место расположения Event ID 4624
%SystemRoot%\System32\Winevt\Logs\Security.evtx это у нас Authentication
на screen мы видим «Тип входа» выше есть «Список типа входа и их описание», так же видим host и IP
Рассмотрим третье и четвертое, место расположения Event ID 21 и ID 22
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx это у нас Logon
в данном конкретном примере мы видим что пользователь осуществил вход в систему в 13:07, а наше удаленное подключение было в 17:44, но обратите внимание чуть выше в 17:44 есть код event ID 25
и снова мы наблюдаем IP адрес подключившегося, для сравнения в 17:47 был осуществлен локальный вход в систему, рассмотрим его на screen ниже
Мы явно видим что вход в систему локальный — Адрес сети источника: ЛОКАЛЬНЫЕ
Осмотр событий ПК c которого осуществилось подключение мы подключились c: host physical IP 192.168.10.146
Event ID 5379
%SystemRoot%\System32\Winevt\Logs\Security.evtx это у нас запротоколирована по отдельности каждая цифра и символ введенные в GUI mstsc.exe в поле «Компьютер» с 17:43:31 по 17:43:56
В коде события 5379 изменяются значения «TargetName» и «Type»
Попытка входа в систему с использованием явных учетных данных
Event ID 4624
Это событие генерируется при создании сеанса входа (на конечном компьютере). Он генерируется на компьютере, к которому был получен доступ, где был создан сеанс.
Event ID 4672
Это событие генерируется для новых учетных записей, если для нового сеанса входа назначены какие-либо из следующих конфиденциальных привилегий
SeTcbPrivilege — действует как часть операционной системы
SeBackupPrivilege — Резервное копирование файлов и каталогов
SeCreateTokenPrivilege — создает объект токена
SeDebugPrivilege — отладка программ
SeEnableDelegationPrivilege — позволяет доверять учетные записи компьютеров и пользователей для делегирования.
SeAuditPrivilege — Генерация аудита безопасности
SeImpersonatePrivilege — выдавать себя за клиента после аутентификации
SeLoadDriverPrivilege — загрузка и выгрузка драйверов устройств
SeSecurityPrivilege — Управление журналом аудита и безопасности
SeSystemEnvironmentPrivilege — Изменить значения среды прошивки
SeAssignPrimaryTokenPrivilege — заменяет токен уровня процесса
SeRestorePrivilege — Восстановление файлов и каталогов,
SeTakeOwnershipPrivilege — стать владельцем файлов или других объектов.
P:S
(статья в стадии написания не окончена)
Данная статья будет дополняться и получать новые примеры to by continued…
Windows 10: Suspicious Log On In Windows Security Logs And Several Event 5379
Discus and support Suspicious Log On In Windows Security Logs And Several Event 5379 in AntiVirus, Firewalls and System Security to solve the problem; I checked log on activities and saw some weird log on with security ID : NULL SID, what does this mean? And there also a bunch of events 5379 saying…
Discussion in ‘AntiVirus, Firewalls and System Security’ started by Ai Vo, Sep 24, 2024.
-
Suspicious Log On In Windows Security Logs And Several Event 5379
I checked log on activities and saw some weird log on with security ID : NULL SID, what does this mean? And there also a bunch of events 5379 saying that credentials manager were read some of them has defaultuser0 name other is my desktop name. Should i factory reset this computer to get rid of them?
-
Excessive Security Log Events — Event ID 5379 — Windows 10
I’m having the same problem. The system was fine last November and sat for about four months. When I turned it on last night, after all updates were applied and Outlook was downloading emails, the «freezing» issue started. After rebooting it stopped and I was hoping it was a one-time deal. After using the system for about 5 hours today, it started up again. Last night I was able to still use the computer, albeit very difficult. Today I wasn’t even able to close windows (I think I managed to get two before I gave up and hit CTRL+ALT+DEL). The system was back to being normal/responsive after the ctrl/alt/del screen appeared (no idea what it’s called). I logged out, forced applications to shut down (the shutdown process took a bit longer than usual), logged back in and the problem persisted. I rebooted the computer and the issue stopped.
I decided to take a peak in the Event Viewer since the issue seems bizarre. I, too, found many 5379 events. I usually don’t even bother with the Event Viewer because of the plethora of events that tend to be logged in there. However, in this case, I think the 5379 events ARE significant. Looking at the time stamps, they began occurring around the same time the freezing issue began. I tried to use the computer while the issue was happening for about ten minutes and there were eight pages (around 130 entries) of 5379 events occurring within seconds of each other.
The same seems to be true from last night. There was a handful of 5379 events when I first logged in but during the first five hours of use there weren’t hundreds of them, so… I’m off to search for more answers on this. Will come back here if I find one.
-
Excessive Security Log Events — Event ID 5379 — Windows 10i had ex[eriences like that last night — my laptop so slowly
-
Suspicious Log On In Windows Security Logs And Several Event 5379
Excessive Security Log Events — Event ID 5379 — Windows 10
@RemoteComputerTechnician as you have posted several «solutions» on here, that have only turned out to NOT change the issue, I would respectfully suggest that you THOROUGHLY test any and ALL changes that you try, for at least 1 to 2 weeks, before posting them on here, as it may cause confusion, and if users try these, it might cause them issues if they no not have the proper skills to do it properly, and be unable to revert a bad change.
As I have posted on here a few times, these 5379 Audit Success event logs are a NORMAL part of the Microsoft Security reporting «system», and do NOT signify a problem that any users need to fix, and there is NO PROBLEM with their hardware or software, and NO rogue processes running doing bad stuff.
Many enterprise users actually WANT auditing events, that is why they are there, HOWEVER, most regular users do NOT want this (as it can be excessive), and ideally, Microsoft should be providing a setting for Windows 10 Home and Pro users to be able to turn this OFF.
Maybe those who aggree with that, should be posting that suggestion in the Feedback Hub, and vote up any others who have done this.
For users getting freezes, and game-play lags, performance issues, should NOT look here for a solution, as these 5379 events have NOTHING to do with that.
It may well be the other well posted problem of long run times for the scheduled runs of WaasMedic and CompatTelrunner services.
Suspicious Log On In Windows Security Logs And Several Event 5379
-
Suspicious Log On In Windows Security Logs And Several Event 5379 — Similar Threads — Suspicious Log Security
-
Suspicious Log On In Windows Security Logs And Several Event 5379
in Windows 10 Gaming
Suspicious Log On In Windows Security Logs And Several Event 5379: I checked log on activities and saw some weird log on with security ID : NULL SID, what does this mean? And there also a bunch of events 5379 saying that credentials manager were read some of them has defaultuser0 name other is my desktop name. Should i factory reset this… -
Suspicious Log On In Windows Security Logs And Several Event 5379
in Windows 10 Software and Apps
Suspicious Log On In Windows Security Logs And Several Event 5379: I checked log on activities and saw some weird log on with security ID : NULL SID, what does this mean? And there also a bunch of events 5379 saying that credentials manager were read some of them has defaultuser0 name other is my desktop name. Should i factory reset this… -
Suspicious Windows Security Logs In Event Viewer
in Windows 10 Gaming
Suspicious Windows Security Logs In Event Viewer: I checked event viewer windows/security logs and found some activites such as log on, user management, Credentials Manager were read… happened on my computer but i didnt use my computer at that time. Some of them has the Security ID like: SYSTEM, DESKTOP/myuser and some other… -
Suspicious Windows Security Logs In Event Viewer
in Windows 10 Software and Apps
Suspicious Windows Security Logs In Event Viewer: I checked event viewer windows/security logs and found some activites such as log on, user management, Credentials Manager were read… happened on my computer but i didnt use my computer at that time. Some of them has the Security ID like: SYSTEM, DESKTOP/myuser and some other… -
Suspicious Windows Security Logs In Event Viewer
in AntiVirus, Firewalls and System Security
Suspicious Windows Security Logs In Event Viewer: I checked event viewer windows/security logs and found some activites such as log on, user management, Credentials Manager were read… happened on my computer but i didnt use my computer at that time. Some of them has the Security ID like: SYSTEM, DESKTOP/myuser and some other… -
Event Viewer Suspicious Windows System Logs
in AntiVirus, Firewalls and System Security
Event Viewer Suspicious Windows System Logs: I checked my event viewer the windows system logs and saw some kernel general and other activites on my computer at 1:20 AM. But that time i was sleeping, Is that a sign that i got hacked and someone was using my computer on that time??… -
Event Viewer Suspicious Windows System Logs
in Windows 10 Gaming
Event Viewer Suspicious Windows System Logs: I checked my event viewer the windows system logs and saw some kernel general and other activites on my computer at 1:20 AM. But that time i was sleeping, Is that a sign that i got hacked and someone was using my computer on that time??… -
Event Viewer Suspicious Windows System Logs
in Windows 10 Software and Apps
Event Viewer Suspicious Windows System Logs: I checked my event viewer the windows system logs and saw some kernel general and other activites on my computer at 1:20 AM. But that time i was sleeping, Is that a sign that i got hacked and someone was using my computer on that time??… -
Excessive Security Log Events — Event ID 5379 — Windows 10
in Windows 10 BSOD Crashes and Debugging
Excessive Security Log Events — Event ID 5379 — Windows 10: I have been experiencing Windows Application crashes on my 3 month old Windows 10 install. While troubleshooting, I noticed that there 50+ security events each minute in the Event Viewer under Windows Logs > Security.Is this normal?
The majority are Audit Success…











