Все о файле Gathernetworkinfo.vbs. Что это такое и для чего нужен?
Особо внимательные пользователи, изучающие компоненты автозагрузки своей операционной системы Windows могут заметить некий файл Gathernetworkinfo.vbs. Естественно возникают вопросы по поводу происхождения и назначения данного файла, ведь он находится в автозагрузке и наверняка влияет на скорость загрузки Windows.
Что делает Gathernetworkinfo.vbs?
Файл Gathernetworkinfo.vbs является системным скриптом (запрограммированным набором действий), который присутствует во всех версиях Windows, начиная с Windows Vista.
Если разбить название файла по составляющим – Gather Network Info, то перевод звучит так: “Сбор информации о сети”.
Если зайти в планировщик задач Windows, то в нем можно обнаружить задание (скрипт) Gathernetworkinfo.vbs.
Задача Gathernetworkinfo.vbs в планировщике windows
Интересной особенностью данного файла является то, что он не имеет цифровой подписи несмотря на то, что является системным файлом (заданием планировщика windows).
Gathernetworkinfo.vbs имеет связь с файлами NetTrace.PLA.Diagnostics.xml и NetTrace.dll, которые помогают собирать информацию о сети. Она затем, скорее всего, отправляется в Microsoft для анализа.
Вывод
Файл Gathernetworkinfo.vbs, находящийся в автозагрузке совершенно точно не является вредоносным, несмотря на то, что многие программы могут утверждать обратное.
Небезопасность файла Gathernetworkinfo.vbs по мнению некоторых программ
Gathernetworkinfo.vbs это системный скрипт, запускаемый планировщиком операционной системой для запуска процедуры сбора статистики и информации о сетевом подключении (интернет). Куда затем идет эта самая статистика достоверно не известно, но очень вероятно что в Microsoft.
Если вы подозреваете Gathernetworkinfo.vbs во вредоносности, то без проблем можете проверить свой компьютер хорошим бесплатным антивирусом.
Лучшая благодарность автору — рассказать о статье у себя в соц.сетях:
I recently read the whitepaper“Using Windows Script Host and COM to Hack Windows” that is mentioning the GatherNetworkinfo.vbs script I hadn’t paid attention to yet. The gathernetworkinfo.vbs script comes by default with every Windows 7 installation and is located within the C:\Windows\System32\ folder.
The script does collect various networking information about the Windows 7 system and its configuration and dumps the information into the C:\Windows\System32\Config folder.
On a system where the script hasn’t been executed yet the Config folder looks as following:

Now open a command prompt with elevated rights and run cscript c:\windows\system32\gathernetworkinfo.vbs When the script has completed you will see that additional files have been added to the Config folder.

The structure of the script is quite easy to understand. Within the first part of the script all functions are defined, the second part defines the output file names and the last part actually calls the individual data collection functions including the output file parameter.
The script is also defined within a scheduled task called Nettrace which is not scheduled to run automatically.

In the rapidly evolving world of technology and cybersecurity, understanding the tools and scripts that operate in our digital environment is paramount. This article explores GatherNetworkInfo.vbs, a script often encountered in Windows operating systems, examining its function, significance, and potential security risks associated with its use.
Overview of VBS (Visual Basic Script)
Before delving into GatherNetworkInfo.vbs, it is essential to understand Visual Basic Script (VBS). VBS is an interpreted scripting language developed by Microsoft, primarily used for automating tasks in the Windows operating system. It allows developers to create complex scripts that can perform various functions, such as file manipulation, system administration tasks, and interacting with COM objects (Component Object Model).
VBS is commonly utilized for web development, enabling client-side scripting in Internet Explorer, but it can also be employed for test automation and administrative task automation in Windows environments. However, due to its ease of use and the power it wields, VBS can also be exploited for malicious purposes, which raises concerns regarding its security implications.
Understanding GatherNetworkInfo.vbs
GatherNetworkInfo.vbs is a script primarily used to gather network-related information from Windows operating systems. This includes information such as:
- IP Address
- Subnet Mask
- Default Gateway
- DNS Servers
- Network Adapter Details
- Active connections and their statuses
This script is often deployed by system administrators or IT support personnel to quickly assess network configurations and troubleshoot issues. By automating the collection of this information, it saves time and provides a clearer picture of the network environment, which can be crucial for diagnosing problems and optimizing performance.
Typical Use Cases
- Troubleshooting Network Issues: When users experience connectivity problems, network administrators can use GatherNetworkInfo.vbs to quickly gather pertinent information about the network setup and identify potential issues.
- Inventorying Network Configuration: IT departments might use the script to audit and document the network setup across various machines, ensuring compliance with internal policies or preparing for upgrades.
- Automating Reporting: In environments where frequent reporting on network status is required, the script can be integrated into regular system checks or monitoring systems, providing up-to-date insights without manual intervention.
How GatherNetworkInfo.vbs Works
The inner workings of GatherNetworkInfo.vbs rely on Windows Management Instrumentation (WMI) and other system commands to fetch network data. When executed, the script typically performs the following tasks:
- Collecting Data: The script makes use of WMI queries to gather data related to network adapters and connections.
- Formatting Output: Once the data is collected, it formats this information into a readable output, which can be displayed in a command prompt window or saved to a file for further analysis.
- Error Handling: The script may include basic error handling to manage scenarios where network interfaces are unavailable or other exceptions occur.
Sample Code Overview
While presenting an entire VBS script may be overly technical for a general audience, a very simplified version of how such a script might function is as follows:
Option Explicit
Dim objWMIService, colNetAdapters, objNetAdapter
Dim strComputer, output
strComputer = "." ' Local Computer
Set objWMIService = GetObject("winmgmts:\" & strComputer & "rootcimv2")
Set colNetAdapters = objWMIService.ExecQuery("Select * from Win32_NetworkAdapter")
For Each objNetAdapter in colNetAdapters
output = output & "Description: " & objNetAdapter.Description & vbCrLf
' Other properties can also be collected here
Next
WScript.Echo outputThis basic example demonstrates how a script collects network adapter descriptions. The actual GatherNetworkInfo.vbs can be far more complex and may incorporate various other features, such as logging and detailed reporting.
Is GatherNetworkInfo.vbs a Security Risk?
Given that GatherNetworkInfo.vbs can access sensitive network information, its presence raises the question of whether it poses a security risk. The answer is nuanced and can be explored from various perspectives.
Origin and Distribution
GatherNetworkInfo.vbs itself is not inherently malicious. It is often placed on systems either by IT departments for legitimate purposes or can be included as part of software installations that require network configuration data. However, if a malicious actor were to deploy a modified version of the script, it could be used to collect private data without user consent, leading to potential security breaches.
Detection and Identification
From a security standpoint, identifying the legitimate GatherNetworkInfo.vbs script can help distinguish between benign and malicious applications. Typically, legitimate versions of the script originate from known IT personnel or reputable sources. They do not exhibit suspicious behavior such as attempts to connect to unauthorized external servers or perform operations beyond gathering network data.
Potential Threats
- Data Leakage: If an unauthorized variant of GatherNetworkInfo.vbs is executed, it can extract sensitive information from a machine and communicate that data to an external party, leading to data breaches.
- Remote Access: Advanced malware may embed scripts like GatherNetworkInfo.vbs to gather information about network configurations to aid in further exploits, such as unauthorized access or lateral movement within networks.
- Social Engineering: Cybercriminals may use knowledge gathered from such scripts to devise targeted phishing campaigns, tailoring their messages based on the gathered network intelligence.
Prevention and Mitigation
The best way to mitigate potential risks associated with GatherNetworkInfo.vbs includes:
- Restrict Execution: Limit the execution of scripts in your environment to trusted users and applications. Enforce policies that control script execution to reduce the likelihood of unauthorized use.
- Implement Security Software: Use updated antivirus and anti-malware solutions that can detect and block suspicious scripts operating within your network.
- Educate Employees: Conduct training on recognizing social engineering attacks and the risks associated with unauthorized scripts or software.
The Security Context of VBS Scripts
Understanding GatherNetworkInfo.vbs often leads to discussions about the broader implications of using VBS in a security context. Since VBS scripts can be created and modified easily, they are often targets for attackers who want to create obfuscated, malicious payloads.
Security Implications of VBS Usage
- Ease of Use can Foster Misuse: The accessibility of VBS means that even novice users can write potentially harmful scripts that could exploit system vulnerabilities.
- Execution Policies: Windows has included features such as execution policies that can limit the execution of scripts based on user permission. However, these policies can be circumvented if users have elevated privileges.
- Script Obfuscation: Evil actors often obfuscate malicious scripts to hide their true intent, making detection challenging. GatherNetworkInfo.vbs could be misused for hiding logics that fetch and exfiltrate sensitive information while masquerading as a legitimate network diagnostics utility.
Regulatory Perspectives on VBS Scripts
From a regulatory compliance perspective, companies that handle sensitive information must consider the potential vulnerabilities that tools like GatherNetworkInfo.vbs could introduce. Organizations governed by compliance frameworks such as GDPR, HIPAA, or PCI-DSS need to ensure that all scripts operating within their environments adhere to strict guidelines to prevent data loss or breaches.
Future Trends
As technology continues to evolve, the use of scripts like GatherNetworkInfo.vbs may also change. The rise of PowerShell, for instance, has begun to supplant VBS for many administrative tasks due to its enhanced security features and more powerful capabilities.
PowerShell provides built-in security features, including script execution policies and more granular permissions systems compared to VBS. Organizations may consider transitioning towards more secure scripting methods to reduce risks associated with VBS.
Conclusion
GatherNetworkInfo.vbs is a powerful tool that serves a crucial purpose in the realm of network management and diagnostics. While it presents numerous benefits for system administrators, there exists a legitimate concern regarding its potential for misuse, especially if unauthorized variants are executed on machines.
As with many technical tools, the risks associated with GatherNetworkInfo.vbs hinge on user behavior, access controls, and overall security practices. By implementing rigorous security measures, educating users, and utilizing advanced software solutions, organizations can mitigate the risks while benefiting from the utility of GatherNetworkInfo.vbs.
In conclusion, GatherNetworkInfo.vbs is not, by itself, a security risk. However, it has the potential to become one depending on its usage context and execution environment. As technology and cybersecurity threats continue to evolve, staying informed about the tools within our digital ecosystems will help ensure both safety and efficiency in network management practices.
Время на прочтение7 мин
Количество просмотров40K
Автоматическая установка операционных систем семейства Windows требует от системного администратора тщательной проработки всех этапов выполнения. Давно интересуюсь данной темой, однако, в ходе многолетнего опыта по созданию собственных настроенных и обновлённых сборок Windows мной был упущен аспект работы с Планировщиком заданий. Разработчики Windows закладывают задачи, выполняемые в будущем по-расписанию, но ненужные и порой вредные «рядовому» пользователю. Список этих задач предлагаю к рассмотрению и обсуждению в данной статье.
Я уже писал здесь статьи про быструю и тонкую настройку операционной системы путём применения собранных мной твиков реестра, также была серия статей посвященных работе с образом Windows посредством DISM, где выкладывались мои скрипты: добавления пакетов обновлений, отключения компонентов, удаления «магазинных» приложений, получения информации из образа Windows. Скрипт приведённый в этой статье элементарный, основной интерес направлен на сам список задач, которые я предлагаю убрать из Планировщика заданий.
Скрипт
@echo off
schtasks /Delete /tn "\Microsoft\Windows\AppID\SmartScreenSpecific" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\Application Experience\AitAgent" /f &rem 7 9 -
schtasks /Delete /tn "\Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Application Experience\ProgramDataUpdater" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Application Experience\StartupAppTask" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\ApplicationData\appuriverifierdaily" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\ApplicationData\appuriverifierinstall" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\Autochk\Proxy" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Customer Experience Improvement Program\BthSQM" /f &rem - 9 -
schtasks /Delete /tn "\Microsoft\Windows\Customer Experience Improvement Program\Consolidator" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Customer Experience Improvement Program\UsbCeip" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Defrag\ScheduledDefrag" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Device Information\Device" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\Diagnosis\Scheduled" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\LanguageComponentsInstaller\Installation" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\LanguageComponentsInstaller\Uninstallation" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\Maintenance\WinSAT" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Maps\MapsToastTask" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\Maps\MapsUpdateTask" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\Mobile Broadband Accounts\MNO Metadata Parser" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\MobilePC\HotStart" /f &rem 7 - -
schtasks /Delete /tn "\Microsoft\Windows\MUI\LPRemove" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\NetTrace\GatherNetworkInfo" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\RAC\RacTask" /f &rem 7 9 -
schtasks /Delete /tn "\Microsoft\Windows\RemoteAssistance\RemoteAssistanceTask" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\RetailDemo\CleanupOfflineContent" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\SettingSync\BackgroundUploadTask" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\SettingSync\BackupTask" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\SettingSync\NetworkStateChangeTask" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\Setup\EOSNotify" /f &rem 7 9 -
schtasks /Delete /tn "\Microsoft\Windows\Setup\EOSNotify2" /f &rem 7 9 -
schtasks /Delete /tn "\Microsoft\Windows\Setup\SetupCleanupTask" /f &rem - 9 B
schtasks /Delete /tn "\Microsoft\Windows\Speech\SpeechModelDownloadTask" /f &rem - - B
schtasks /Delete /tn "\Microsoft\Windows\SystemRestore\SR" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Time Synchronization\SynchronizeTime" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\Windows Error Reporting\QueueReporting" /f &rem 7 9 B
schtasks /Delete /tn "\Microsoft\Windows\WindowsBackup\ConfigNotification" /f &rem 7 - -
schtasks /Delete /tn "\Microsoft\Windows\WS\License Validation" /f &rem - 9 -
schtasks /Delete /tn "\Microsoft\Windows\WS\WSRefreshBannedAppsListTask" /f &rem - 9 -
schtasks /Delete /tn "\Microsoft\XblGameSave\XblGameSaveTask" /f &rem - - B
schtasks /Delete /tn "\Microsoft\XblGameSave\XblGameSaveTaskLogon" /f &rem - - B
timeout 3 > nul
Использование
Запуск под учётной записью администратора приводит к выполнению последовательности команд schtasks с аргументом /Delete (удалить) последующее имя задачи за аргументом /tn. Ключ /f подавляет вывод уведомлений о подтверждении. Достаточно одного выполнения скрипта, а повторные запуски лишь отобразят список ошибок из-за невозможности удалить то, чего уже нет. Скрипт не наделён «интерактивностью», так как используется в процессе автоматической установки Windows.
Применимость
Список задач, подлежащих удалению данным скриптом, составлен для следующих версий ОС: Windows 7 Professional VL SP1 (updated Jan 2020 — End of Support), Windows 8.1 Professional VL Update3 (updated Jan 2023 — End of Support), Windows 10 v1607 Enterprise LTSB (updated Jan 2023). Изначально хотел написать отдельные скрипты для каждой версии Windows, но увидел, что список задач значительно повторяется и поэтому объединил в один. В планах добавить в список ненужные задачи из следующих версий ОС: Windows 10 v1809 Enterprise LTSC, Windows 10 v21H2 Professional BE (business editions) — на базе которых также делаю свои сборки.
Комментирование
Чтобы не запутаться в списке задач — откуда каждая из них взялась и стоит ли её удалять — в комментарии, в конце строки каждой команды можно видеть подсказку в каких версиях Windows удаляемая задача встречается. Это удобно для анализа и редактирования списка. Также присутствует алфавитная сортировка задач, с группировкой разделов по первой букве. Взгляните, в Windows 7 ненужных задач было не много — всего 22, в Windows 8.1 их уже стало 30, в Windows 10 LTSB уже 41! Страшно представить сколько «мусора» в Планировщике заданий я обнаружу в версии Windows 10 Enterprise LTSC и особенно в Windows 10 21H2.
Откуда список
Я составлял данный список путём вдумчивого чтения описания каждой задачи и анализа параметров её запуска. За дополнительной информацией обращался к источникам в Интернете, в том числе англоязычным, в том числе официальным. Не всегда мне удавалось найти однозначный ответ на вопрос: «стоит удалять данную задачу или нет?». Бывало так, что описание у задачи отсутствовало, параметры запуска скрыты, триггеры срабатывания отсутствуют, но при этом задача почему-то выполнялась. В сети Интернет не нашел аналогичного списка с развёрнутой дискуссией обсуждения целесообразности включения в него тех или иных задач.
Удаление или отключение?
Консольная команда schtasks имеет полный набор аргументов для управления Планировщиком заданий Windows. В ходе поиска информации по отдельным задачам в сети Интернет мне попадались скрипты других авторов, где ненужные задачи отключались (подаргумент /disable аргумента /Change). Я использую более радикальный подход — просто удаляю (аргумент /Delete) ненужные мне задачи. Ведь вариант «отключение» подразумевает что мне когда-нибудь понадобится включить некоторую задачу. Не представляю себе ситуацию, когда мне понадобится снова включить, например, уведомление об окончании срока поддержки или телеметрию. Что скажете?
Вердикт на удаление
Какие задачи в Планировщике заданий принимать к рассмотрению? Рассмотрим какие задачи бывают, в каком состоянии и насколько открыты. На начальном этапе были мысли написать простой скрипт, который бы удалял вообще все задачи (без разбора), но данный подход опасен тем, что может привести к снижению производительности и надёжности системы, так что пришлось разбираться. Итак:
- Состояние — Отключено
Я не включал в список на удаление задачи в состоянии «Отключено». Как правило это либо «артефакты» прошлых версий Windows, либо уже отключенные самими разработчиками посредством пакетов обновлений, либо ещё что… - Бесполезное обслуживание
Это пример задач которые запускают ежедневное/еженедельное выполнение различных служб в назначенное время, как правило ночью. Как итог, эти задачи не выполняются так как ночью мой компьютер («рядового» пользователя) отключён. Также мне не надо чтобы днём отвлекались ресурсы моего компьютера. - Телеметрия
Это страшное слово знакомо многим системным администраторам и не только. Значительная часть удаляемых по моему списку задач относится к средствам телеметрии и слежения за пользователем со стороны компании Майкрософт. Мой компьютер — это МОЙ КОМПЬЮТЕР! - «Тёмные лошадки»
Самая сложная категория задач. Как правило, много их появилось в версии Windows 10. Отличительные особенности: описание размыто или отсутствует, параметры запуска скрыты, триггеры срабатывания отсутствуют, но при этом задача каким-то чудом регулярно запускается, о чём указано в поле «Время прошлого запуска».
Обсуждение
Конечно, представленный мной список может быть не полным или наоборот избыточным. Есть вероятность, что я не распознал в какой-то задаче «скрытого пожирателя ресурсов» или наоборот включил в список задачу удаление которой скорее навредит работоспособности ОС. Прошу аргументированно высказывать своё мнение, делится опытом. В данном ключе обсуждение может начинаться по двум сценариям:
- Вы включили в список задачу «X», удаление которой приведёт к следующим негативным последствиям…
- Вы не включили в список задачу «Y», которая является вредной, так как выполняет следующие действия…
Список составлен для компьютера предназначенного для домашнего использования. Прошу к рассмотрению и обсуждению!
GatherNetworkInfo – What you need to know
GatherNetworkInfo is a legitimate file name used by respected programs, but fraudsters exploit it to conceal their malicious software. It should be mentioned that it may cause damage to the computer system, therefore it is advisable to remove it as soon as possible.
One of the most prevalent techniques of infiltration is software bundling, in which their malicious program is mixed in with legitimate software such as video editing apps and other utility utilities. As a result, the malware is installed when the consumer installs the program.
Another typical way dangerous files like GatherNetworkInfo enter the system is through suspicious email attachments; many people become infected this way because malware developers utilize appealing material to lure the user to click on the malicious attachment contained in the email.
When it is clicked, the virus spreads across the computer, compromising the user’s privacy and data. If your computer is infected by the mysterious GatherNetworkInfo, you may notice lag and system overheating every time you use it.
The appearance of Windows PowerShell and Command Prompt every few minutes indicates that the machine is infected with malware. Please proceed to the section below and follow the removal instructions to remove GatherNetworkInfo from the computer system.
The methods provided below will assist you in removing the harmful GatherNetworkInfo trojan virus. We made sure that it will assist you in resolving the malware issue on your system.
Removing malware from the system should be thorough and carefully executed; therefore, please follow every step provided.
Our team has recently tested this procedure and has confirmed that it is still working and up-to-date. Learn More
We made the instructions below easy to understand so non-tech-savvy users can still remove the computer threat without needing help from tech support or a computer technician.
If you come across a method that doesn’t appear to be working, please contact us via our Contact Page. We appreciate your feedback and will address the issue as soon as possible.
Step 1: Uninstall GatherNetworkInfo from the computer
We have provided two methods for removing the malicious GatherNetworkInfo trojan from your computer: standard uninstallation and, if that fails, an advanced uninstall method that ensures the removal will proceed without any complications.
Remove GatherNetworkInfo via Control Panel
Uninstalling the application via the Control Panel is the most common approach employed for removing trojans from the computer. Within the list of applications, you can find the developer’s name in addition to all of the installed applications.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.
2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
4. Right-click GatherNetworkInfo and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
It is widely known to be enough to remove malicious programs that are evading uninstallation. If you encounter such an issue when proceeding to uninstall the app, you may utilize the uninstaller to do the job for you.
Note: If you were not able to find GatherNetworkInfo from the list of applications, please skip the following step and head over to the next method to remove the harmful file manually.
Alternative: Remove GatherNetworkInfo via Revo Uninstaller
For computer users who are uncertain of their next steps. You may choose to utilize Revo Uninstaller instead, as it is considerably more efficient and user-friendly. Revo Uninstaller is a useful application for consumers of Windows.
This uninstaller ensures that program modifications are also eliminated from the computer, including the Host File, Windows Registry, and other relevant locations. You can remove the GatherNetworkInfo trojan by installing and utilizing Revo Uninstaller in accordance with the instructions below.
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
Download Revo Uninstaller
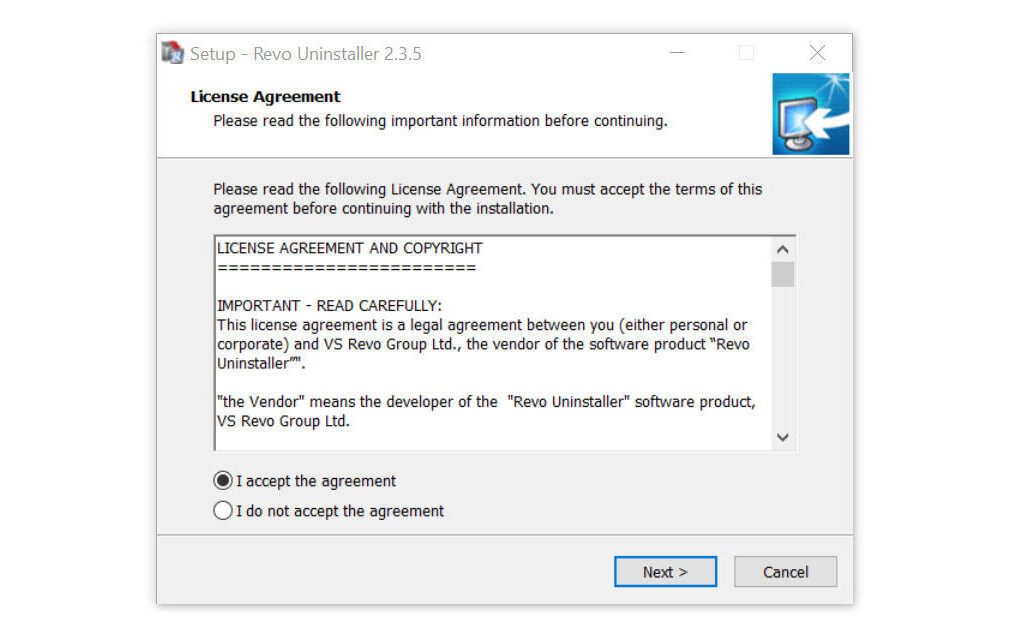
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
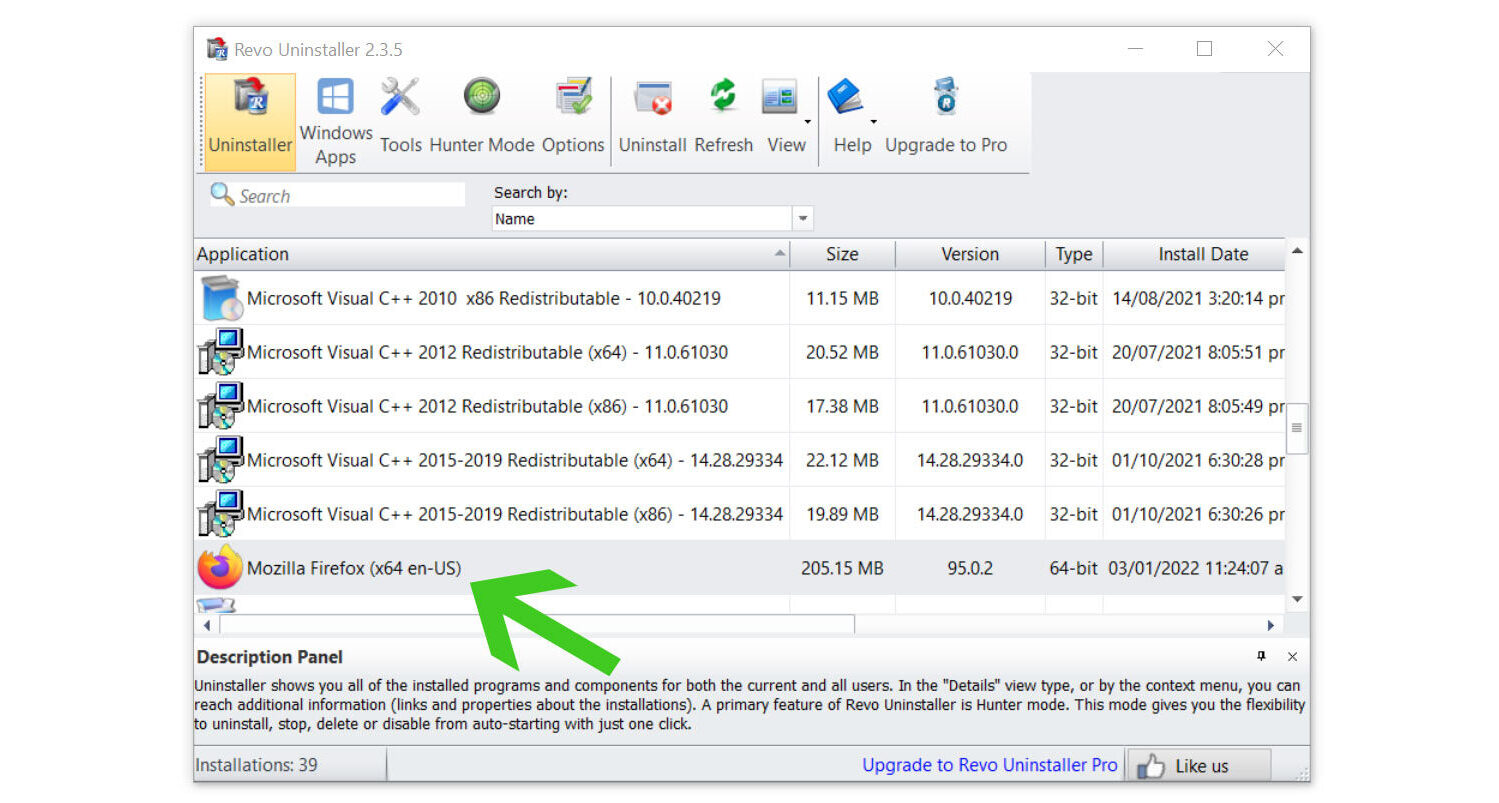
3. Once the software has launched, find the harmful GatherNetworkInfo trojan and double-click the program to uninstall it.
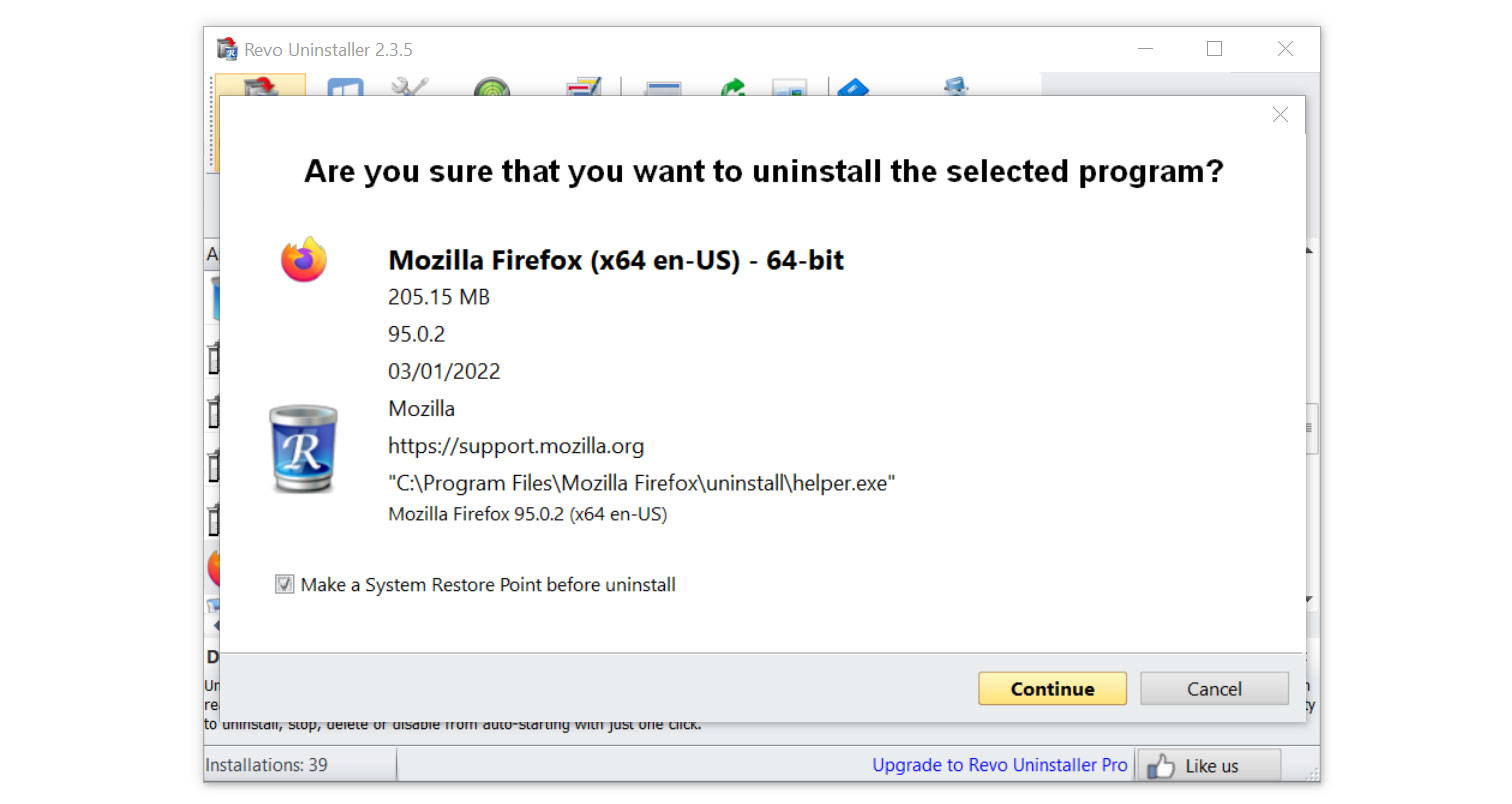
4. Click on the Continue button and follow the procedure to start uninstalling the GatherNetworkInfo trojan virus. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case. (We will be using Firefox as a demonstration.)
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.
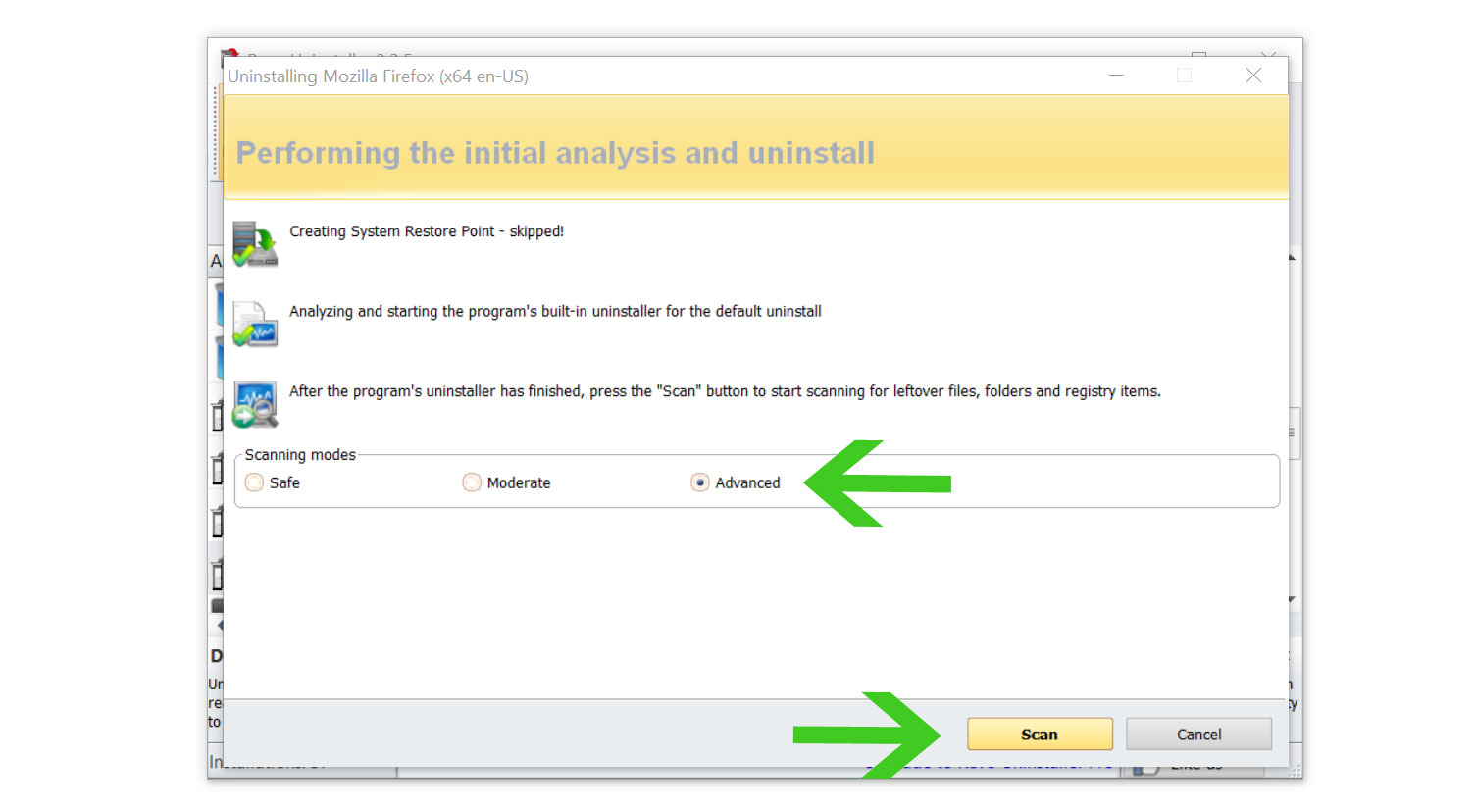
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
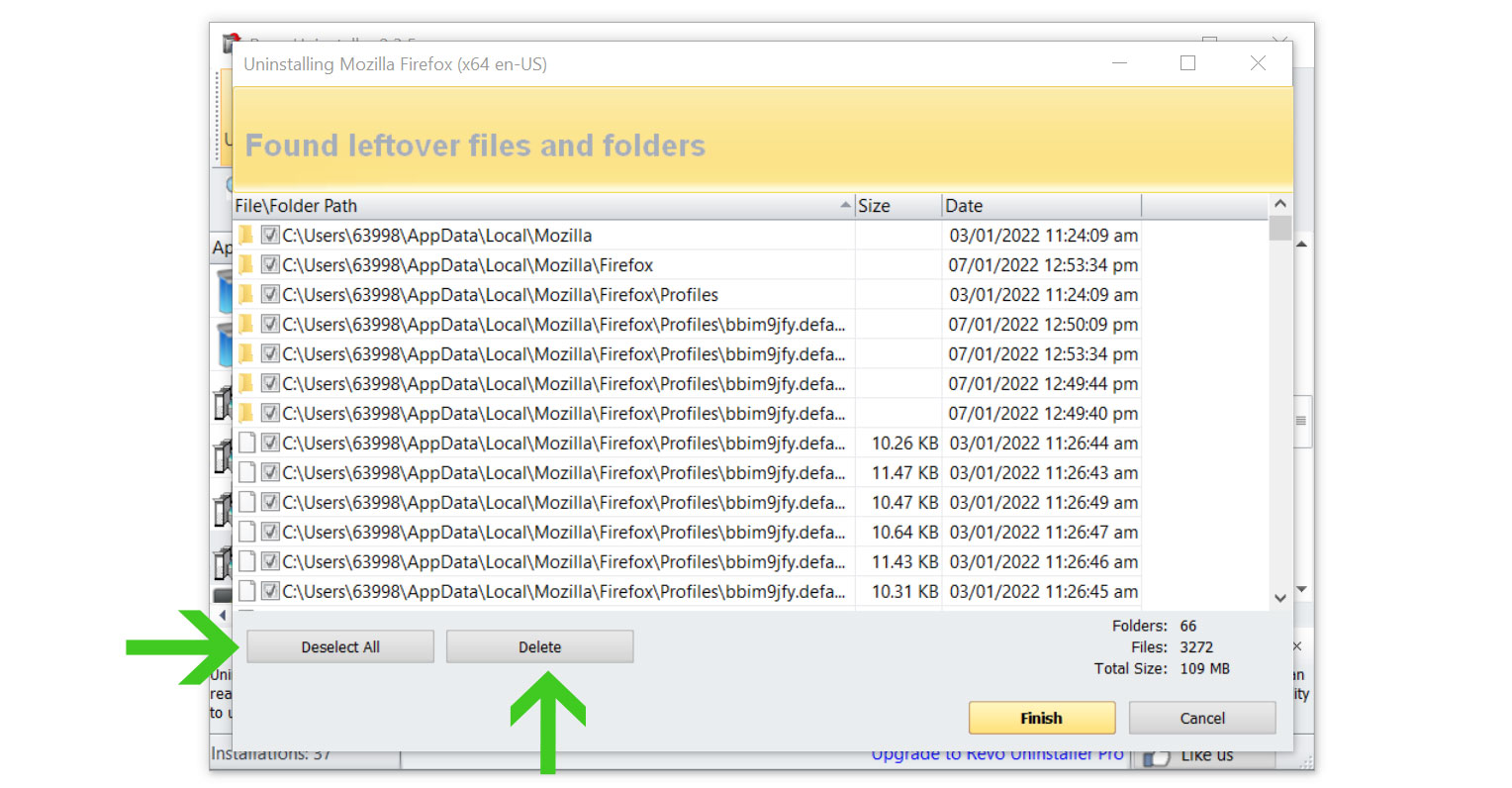
Once the window closes, you have successfully removed GatherNetworkInfo from your computer system.
Step 2: Delete GatherNetworkInfo manually
There is a chance that GatherNetworkInfo may not be an installed Windows program but rather a single executable file that is hiding in the computer. If this is the case, then you can remove it by locating the source of the file and deleting it from there.
Please follow the instructions below to find and delete GatherNetworkInfo manually from the computer.
1. When the trojan virus is causing your computer to overheat, launch Task Manager by simultaneously pressing the Ctrl, shift, and Esc buttons. Another option is via the Run program by pressing the Windows key and R, then typing taskmgr.
2. Check the processes that are running on your computer right now to discover how much hardware they are using once Task Manager has opened. Once you have located it, right-click on it and select Open file location.
3. Make that the file location does not originate from a Windows system directory, such as the C:Windows\System32, after the File Explorer has opened up while highlighting the GatherNetworkInfo file, since you may risk unintentionally deleting a system file. If the software is not from a crucial directory, delete it by selecting it with the right-click menu.
If the file refuses to be deleted because the process is running as well as if certain programs are preventing it from being uninstalled, simply enter Windows Safe Mode and delete it from there.
Before doing so, please remember the directory where GatherNetworkInfo is located because Safe Mode prevents non-essential files from running on the computer.
To boot into Safe Mode, first, open the system configuration by pressing the Windows Key + R button then type «msconfig.exe«.
Once the System Configuration window appears, click Boot next to General then check the Safe Boot from Boot options. Below that, tick the Network option to allow internet within the Safe Mode then click Apply, once everything is done the computer should be restarted into safe mode.
After booting into the said mode, go to the directory where GatherNetworkInfo is located and delete it. It should be able to be deleted now that the configurations preventing it from being removed are blocked in Safe Mode.
Step 3: Scan with powerful malware removal software
GatherNetworkInfo may be hard to delete and for users who are not knowledgeable about their technology, it is best to utilize a program dedicated to removing such threats from the computer.
An antivirus program is your all-in-one solution for dealing with malware. It serves as a preventive and corrective step, quickly detecting and eliminating malware from your device.
We cannot emphasize enough the significance of using antivirus software especially when facing a threat like the GatherNetworkInfo trojan virus.
Having antivirus software on your computer offers several significant benefits, including:
- Detection, filtering, and automatic removal of malware ranging from harmless adware to extremely severe ransomware.
- Providing caution and notifications for possibly risky websites that you may visit, helping you in mitigating online risks.
- Antivirus threat databases are regularly updated to ensure the detection of new viruses and the protection of your device.
- Keeping your operating system clean by protecting all files on your computer, assuring their safety and integrity.
Which antivirus should I use?
The answer is dependent on how you use your computer, as several antivirus applications on the market offer benefits and drawbacks. Because most of them identify and remove malware at the same rate, we recommend choosing your choice based on research.
For example, if you use your computer for resource-intensive applications such as video editing, you might want to avoid resource-consuming antivirus programs.
Fortunately, there are numerous publications that provide extensive comparisons of each antivirus’s merits and cons. However, for the best of all worlds, we recommend one of the following antivirus programs:
- Malwarebytes Anti Malware
- Kaspersky Antivirus
The majority of free versions are already sufficient for removing and blocking viruses from your computer. Some antivirus products also provide free trials that allow you to learn more about its capabilities before making a purchase choice. However, in the end, the free version usually provides everything needed to remove malware.
For a better and safer web browsing experience, we’ve provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing the GatherNetworkInfo trojan and other malware from the computer is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are continuously improving their methods in order to infect users and steal money and information from them.
Before leaving this page, we firmly advise you to implement the measures outlined below to guarantee absolute security, as we strongly believe in the importance of web security and maintaining a secure online presence.
Safeguard your data and privacy online by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
Use a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks.
Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
Bottom Line
Although this may seem like standard procedure, we strongly advise against visiting illicit streaming or torrenting websites and, more significantly, against downloading anything from them, as doing so could lead to the installation of malware and viruses.
It is crucial to consistently ensure that your device is safeguarded against hidden exploits and cyberattacks. Although exercising caution and avoiding questionable websites are vital, safeguarding your network and data requires an effective line of defense.
If you experience another computer issue, please visit our website to find a solution for your problem or get in touch with us, and SecuredStatus will be happy to assist you once again.
