Парольная политика в домене Active Directory задает базовые требования безопасности к паролям учетных записей пользователей такие как сложность, длину пароля, частоту смены пароля и т.д. Надежная политика паролей AD позволяет снизить возможность подбора или перехвата паролей пользователей.
Содержание:
- Настройка политики паролей в Default Domain Policy
- Основные параметры политики паролей в домене
- Управление параметрами политики паролей AD с помощью PowerShell
- Несколько парольных политик в домене Active Directory
Настройка политики паролей в Default Domain Policy
Настройки политика паролей пользователей в домене AD по умолчанию задаются через групповую политику Default Domain Policy. Вы можете просмотреть и изменить настройки парольной политики в домене с помощью консоли управления консоль управления доменными GPO
- Откройте консоль
gpmc.msc
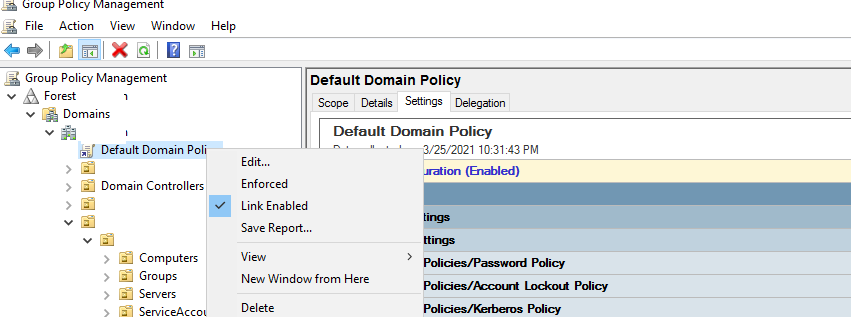
и выберите Default Domain Policy, которая назначена на корень домена; - Щелкните правой кнопкой по Default Domain Policy и выберите Edit;
- Разверните Конфигурация компьютера -> Политики -> Конфигурация Windows -> Параметры безопасности -> Политики учетных записей -> Политика паролей (Computer configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
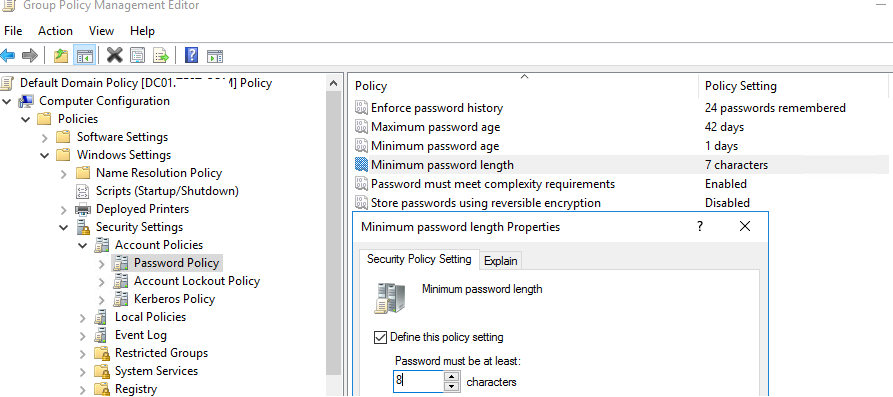
- В этом разделе есть шесть параметров политики паролей (описаны ниже);
- Чтобы изменить настройки параметра, дважды щелкните по ней. Чтобы включить политику, отметьте галку Define this policy settings и укажите необходимую настройку (в примере на скриншоте я задал минимальную длину пароля пользователя 8 символов). Сохраните изменения;
- Новые настройки парольной политики применяться ко всем пользователям домена после обновления настроек GPO на контролере домена с FSMO ролью PDC Emulator.
Основные параметры политики паролей в домене
Всего доступно шесть параметров политики паролей:
- Вести журнал паролей (Enforce password history) – задать количество старых паролей, которые хранятся в AD. Пользователь не сможет повторно использовать старый пароль (однако администратор домена или пользователь, которому делегированы права на сброс пароля в AD, может вручную задать для аккаунта старый пароль);
- Максимальный срок действия пароля (Maximum password age) – срок действия пароля в днях. После истечения срока действия пароля Windows потребует у пользователя сменить его. Обеспечивает регулярность смены пароля пользователями;
- Минимальный срок жизни пароля (Minimum password age) – как часто пользователи могут менять пароль. Этот параметр не позволит пользователю несколько раз подряд сменить пароль, чтобы вернуться к старому паролю, перезатерев пароли в журнале Password History. Как правило тут стоит оставить 1 день, чтобы пользователь мог самостоятельно сменить пароль в случае его компрометации;
- Минимальная длина пароля (Minimum password length) – не рекомендуется делать пароль короче, чем 8 символов (если указать тут 0 – значит пароль не требуется);
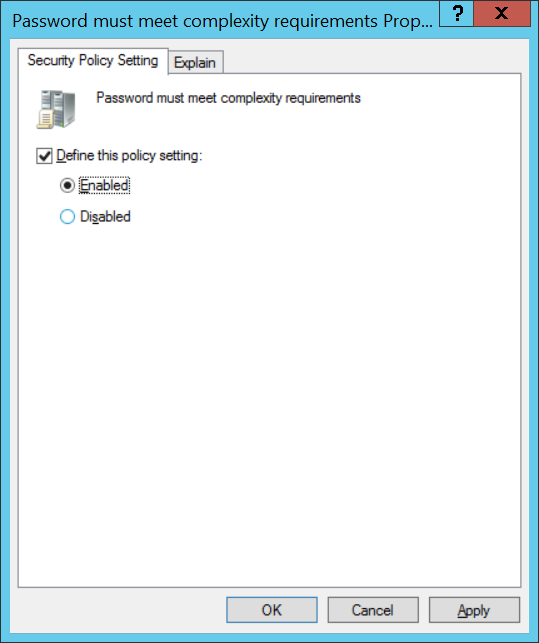
- Пароль должен отвечать требование сложности (Password must meet complexity requirements) – при включении этой политики пользователю запрещено использовать имя своей учетной записи в пароле (не более чем два символа подряд из
username
или
Firstname
). Также в пароле должны использоваться 3 типа символов из следующего списка: цифры (0 – 9), символы в верхнем регистре, символы в нижнем регистре, спец символы ($, #, % и т.д.).Чтобы исключить использование пользователями простых паролей (из словаря популярных паролей) рекомендуется периодически выполнять аудит паролей в домене.
- Хранить пароли, использую обратимое шифрование (Store passwords using reversible encryption) – пароли пользователей в базе AD хранятся в зашифрованном виде, но иногда нужно предоставить доступ некоторым приложениям к паролю. При включении этой политики пароли хранятся в менее защищенной виде (по сути, в открытом виде), что небезопасно (можно получить доступ к базе паролей при компрометации DC). При включении этой опции нужно дополнительно защищать пароли привилегированных пользователей на удаленных площадках с помощью внедрения Read-Only контроллеров домена (RODC).
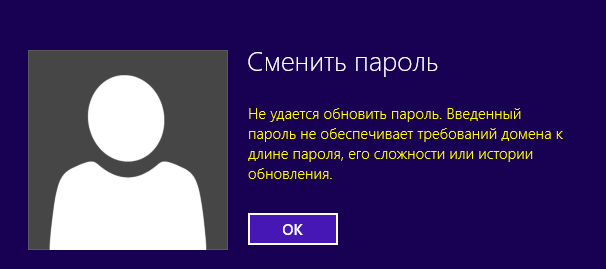
Если пользователь попытается задать пароль, которые не соответствует политике паролей в домене, Windows выдаст ошибку:
Не удается обновить пароль. Введенный пароль не обеспечивает требований домена к длине пароля, его сложности или истории обновления.
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
Обычно вместе с политикой паролей нужно настроить параметры блокировки пользователей при неправильном введении пароля. Эти настройки находятся в разделе GPO: Политика блокировки учетной записи (Account Lockout Password):
- Пороговое значение блокировки (Account Lockout Threshold) – через сколько попыток набрать неверный пароль учетная запись пользователя будет заблокирована;
- Продолжительность блокировки учетной записи (Account Lockout Duration) – длительность блокировки учетной записи, в течении которой вход в домен будет невозможен;
- Время до сброса счетчика блокировки (Reset account lockout counter after) – через сколько минут счетчик неверных паролей (Account Lockout Threshold) будет сброшен.
Если учетные записи блокируются слишком часто, вы можете найти компьютер/сервер источник блокировки так.
Настройки парольных политик домена Active Directory по-умолчанию перечислены в таблице:
| Политика | Значение по-умолчанию |
| Enforce password history | 24 пароля |
| Maximum password age | 42 дня |
| Minimum password age | 1 день |
| Minimum password length | 7 |
| Password must meet complexity requirements | Включено |
| Store passwords using reversible encryption | Отключено |
| Account lockout duration | Не определено |
| Account lockout threshold | 0 |
| Reset account lockout counter after | Не определено |
Управление параметрами политики паролей AD с помощью PowerShell
Для просмотра настроек и изменения конфигурации политики паролей в AD можно использовать командлеты PowerShell из модуля Active Directory:
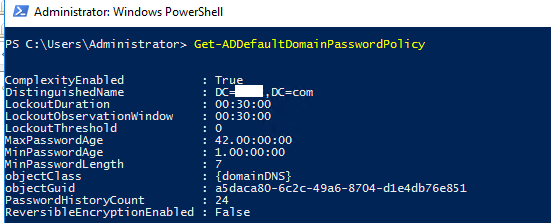
Вывести настройки дефолтной политики паролей:
Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled : True
DistinguishedName : DC=winitpro,DC=ru
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 0
MaxPasswordAge : 42.00:00:00
MinPasswordAge : 1.00:00:00
MinPasswordLength : 7
objectClass : {domainDNS}
objectGuid :
PasswordHistoryCount : 24
ReversibleEncryptionEnabled : False
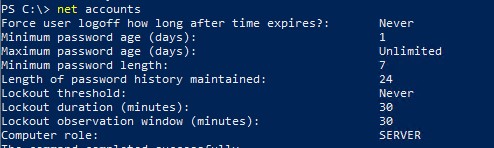
Или с помощью команды:
net accounts
Также вы можете узнать текущие настройки политики паролей AD на любом компьютере в отчете результирующей политики, сгенерированном с помощью консольной утилиты gpresult.
Вывести информацию о том, когда пользователь менял пароль последний раз, и когда истекает его пароль:
net user aivanov /domain
Изменить параметры политики паролей AD:
Set-ADDefaultDomainPasswordPolicy -Identity winitpro.ru -MinPasswordLength 14 -LockoutThreshold 10
Несколько парольных политик в домене Active Directory
С помощью групповых политик на домен можно назначить только одну политику, которая будет действовать на всех пользователей без исключения. Даже если вы создадите новую GPO с другими парольными настройками и примените ее к OU с пользователями, эти настройки фактически не применяться.
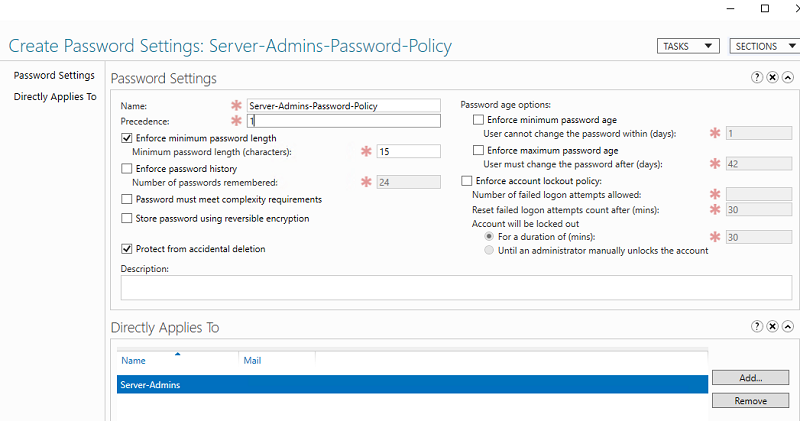
Начиная с версии Active Directory в Windows Server 2008 с помощью гранулированных политик паролей Fine-Grained Password Policies (FGPP) можно применять индивидуальный параметры политики паролей для конкретных пользователей или групп. Например, вы хотите, чтобы пользователи из группы Server-Admins использовали пароли с минимальной длиной 15 символов.
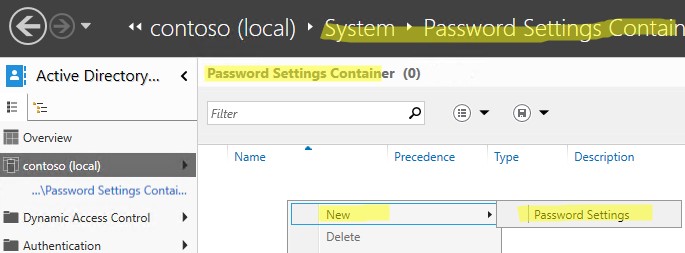
- Откройте консоль Active Directory Administrative Center (
dsac.exe
); - Перейдите в раздел System -> Password Settings Container и создайте новый объект PSO (Password Settings Object);
- В открывшемся окне укажите название политики паролей и ее приоритет. Включите и настройте параметры парольной паролей, которые вы хотите применить. В разделе Directly Applies to нужно добавить группы или пользователей, для которых должны применяться ваши особые настройки политики паролей.
Чтобы проверить, применяются ли к конкретному пользователю особая политика паролей, выполните команду:
Get-ADUserResultantPasswordPolicy -Identity aivanov
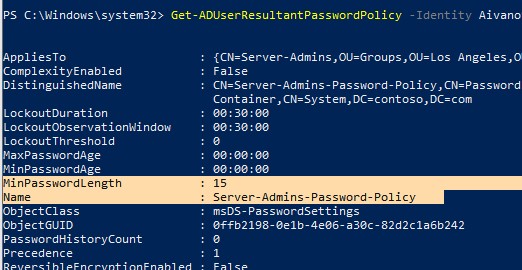
Команда выведет результирующие настройки политики паролей, которые дейсвтуиют на пользователя.

В обязанности системного администратора часто входит обеспечение безопасности вверенного ему домена. Одним из способов усиления безопасности является настройка парольной политики.
По умолчанию требования для паролей пользователей в домене AD настраиваются с помощью групповых политик (GPO). Смотрим в сторону политики домена по умолчанию: Default Domain Policy.
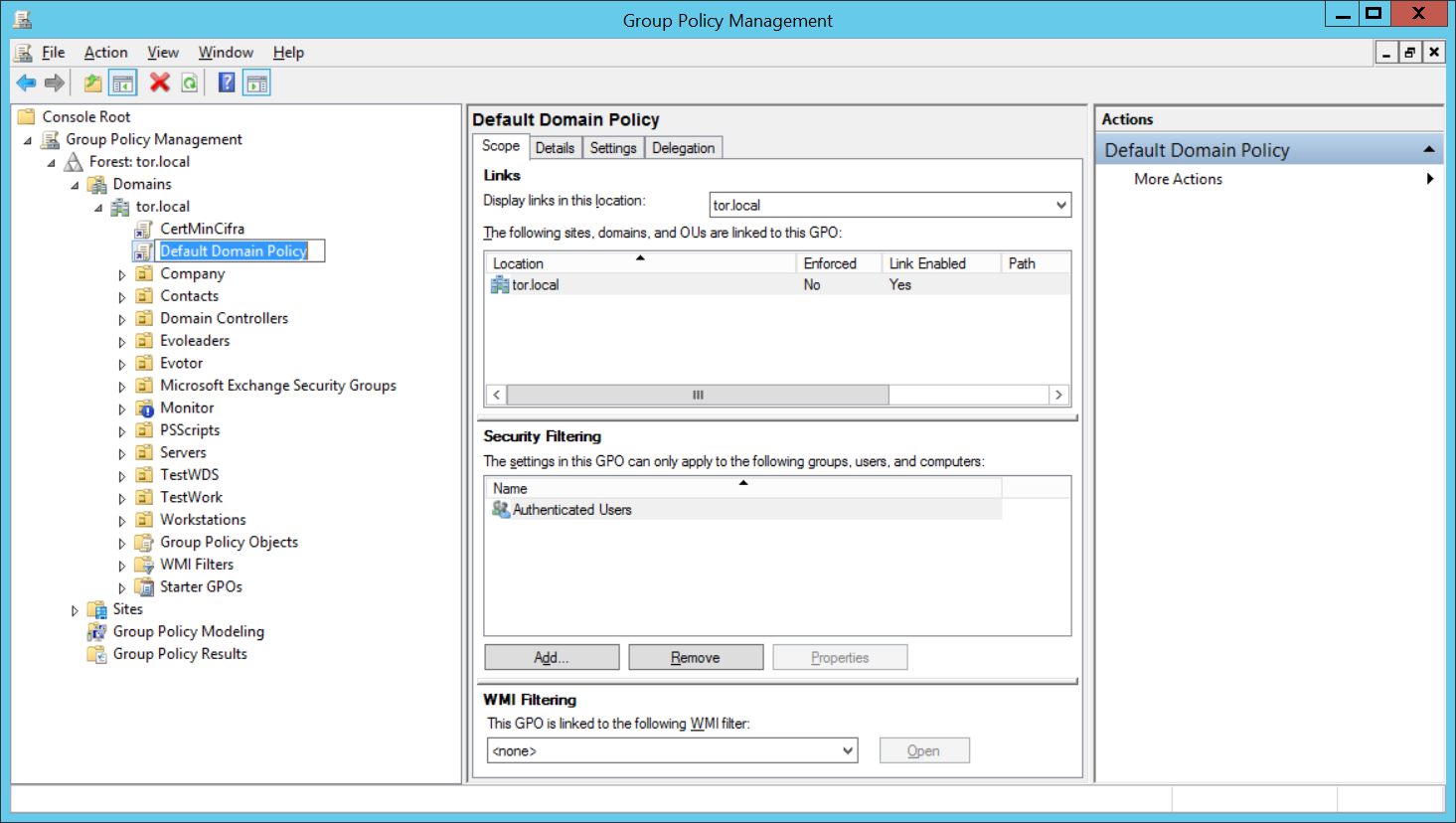
Политика паролей: Computer configuration → Policies → Windows Settings → Security Settings → Account Policies → Password Policy.
Или: Конфигурация компьютера → Политики → Конфигурация Windows → Параметры безопасности → Политики учетных записей → Политика паролей.
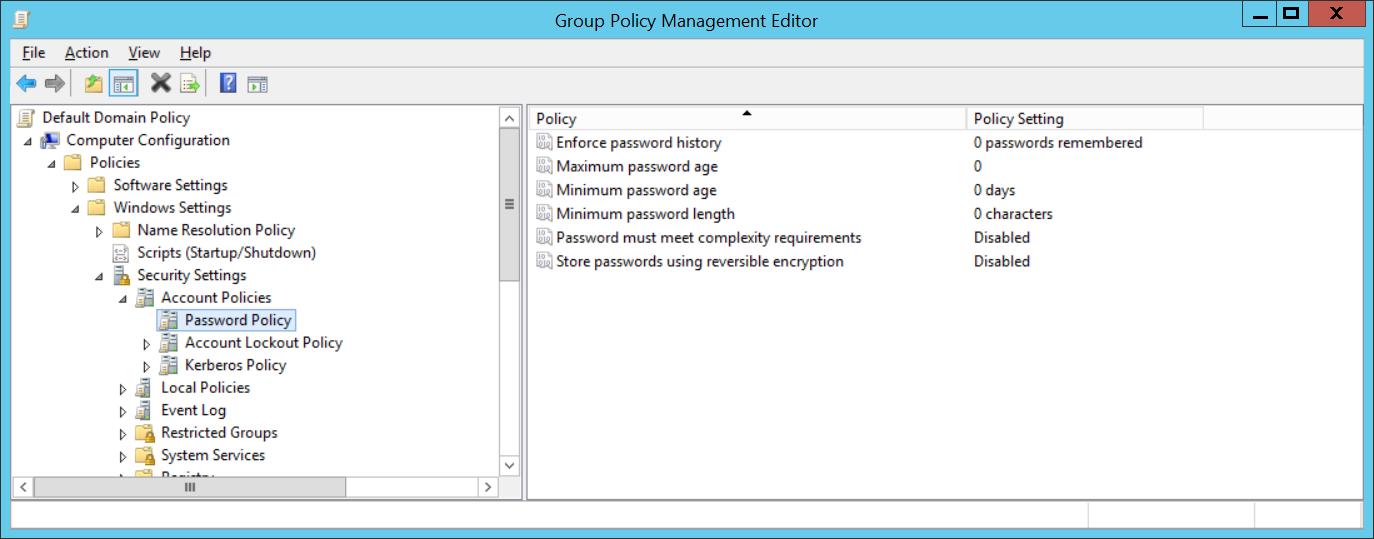
Видно, что по умолчанию нет никаких настроек.
Enforce password history (Вести журнал паролей) — количество запоминаемых предыдущих паролей, предыдущие пароли нельзя повторно использовать. Администратор домена или пользователь с правами на сброс пароля в AD могут вручную установить пароль для учётной записи, даже если он предыдущий.
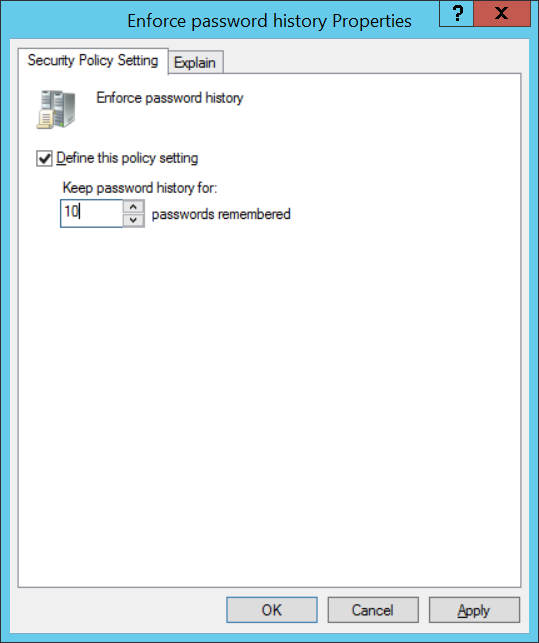
Maximum password age (Максимальный срок действия пароля) — срок действия пароля в днях, по истечении этого срока Windows попросит пользователя сменить пароль, что обеспечивает регулярность смены пароля пользователями. В параметрах учётной записи пользователя можно включить опцию «Срок действия пароля не ограничен», эта опция имеет приоритет.
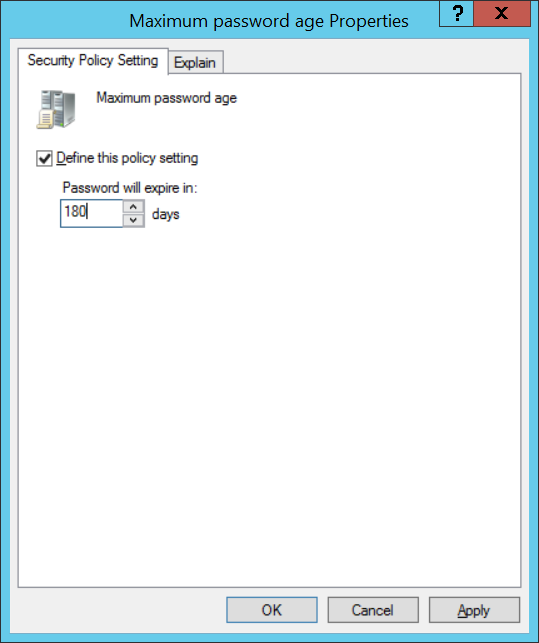
Minimum password age (Минимальный срок действия пароля) — этот параметр не позволит пользователю менять пароль слишком часто, а то некоторые слишком умные люди меняют 10 раз пароль, потом устанавливают старый. Обычно здесь ставим 1 день, чтобы пользователи могли сами сменить пароль, иначе его менять придётся администраторам вручную.
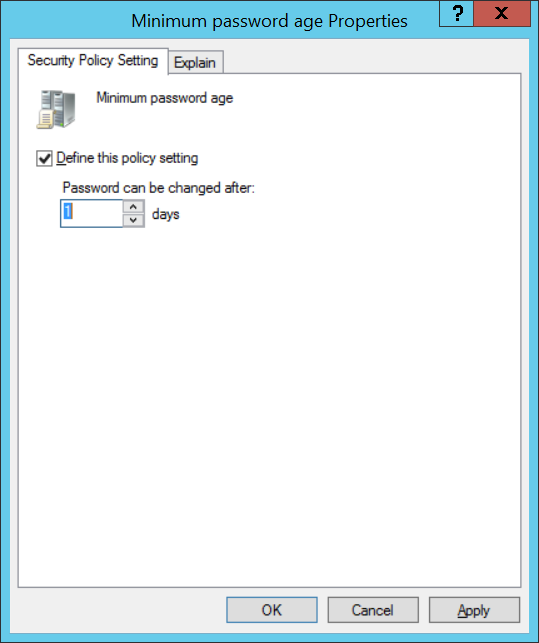
Minimum password length (Минимальная длина пароля) — рекомендуется, чтобы пароли содержали не менее 8 символов. Если указать 0, то пароль будет необязательным.
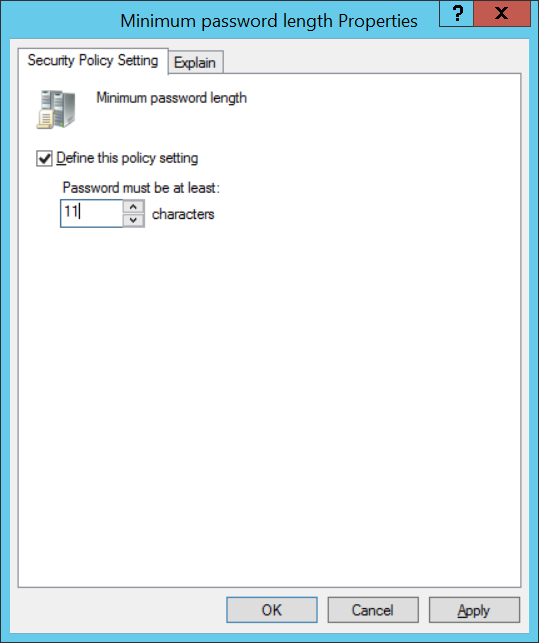
Password must meet complexity requirements (Пароль должен отвечать требованиям сложности) — если эта политика включена, то применяются требования к сложности пароля.
Пароли не могут содержать значение samAccountName пользователя (имя учетной записи) или полное значение displayName (полное имя). Ни один из этих проверок не учитывает регистр.
Параметр samAccountName проверяется в полном объеме только для того, чтобы определить, является ли параметр частью пароля. Если параметр samAccountName имеет длину менее трех символов, эта проверка пропускается. Параметр displayName анализируется на наличие разделителей: запятых, точек, тире или дефисов, подчеркиваний, пробелов, знаков фунта и табуляций. Если какой-либо из этих разделителей найден, параметр displayName разделяется, и подтверждается, что все проанализированные разделы (маркеры) не будут включены в пароль. Маркеры короче трех символов игнорируются, а подстроки маркеров не проверяются. Например, имя «Erin M. Hagens» разделяется на три маркера: «Erin», «M» и «Hagens». Так как второй маркер всего один символ в длину, он игнорируется. Таким образом, у этого пользователя не может быть пароля, который включает «erin» или «hagens» в качестве подстроки в любом месте пароля.
Пароль содержит символы из трех следующих категорий:
- Буквы верхнего регистра европейских языков (от A до Z, буквы с диакритическими знаками, греческие и кириллические знаки)
- Буквы нижнего регистра европейских языков (от a до z, эсцет, буквы с диакритическими знаками, греческие и кириллические знаки)
- Базовые 10 цифр (от 0 до 9)
- Небукенно-цифровые символы (специальные символы). (~!@#$%^&*_-+=`|\\(){}\[\]:;»‘<>,.?/) Символы валюты, такие как евро или британский фунт, не учитываются в качестве специальных символов для этого параметра политики.
- Любой символ Юникода, классифицируемый как цифра или буква, но не в верхнем или нижнем регистре. Эта группа включает символы Юникода из азиатских языков.
Правила, включенные в требования к сложности пароля Windows Server, являются частью Passfilt.dll, и их нельзя изменить напрямую. Этот параметр политики в сочетании с минимальной длиной пароля в 8 символов гарантирует, что есть как минимум 159 238 157 238 528 сочетаний для одного пароля.
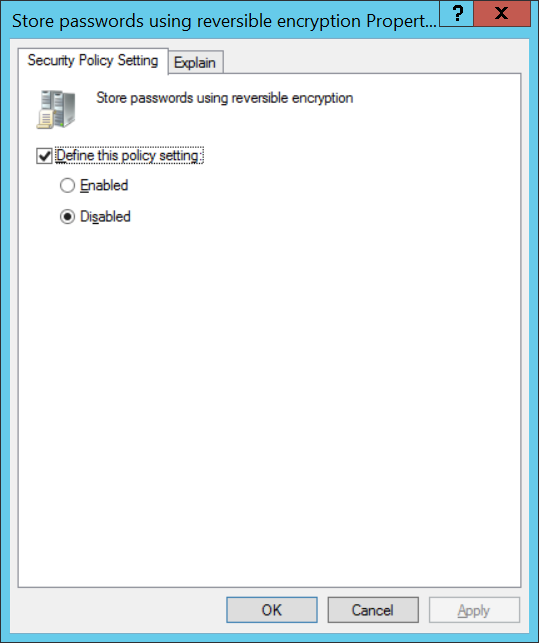
Store passwords using reversible encryption (Хранить пароли, используя обратимое шифрование) — пароли пользователей хранятся в зашифрованном виде в базе данных AD. Пароли можно шифровать таким способом, чтобы была возможна дешифрация, это небезопасно, но иногда может потребоваться, когда вам необходимо предоставить доступ к паролям пользователей для некоторых приложений. При этом пароли менее защищены. Если контроллер домена скомпрометирован, то злоумышленники могут дешифровать пароли всех пользователей.
Мы с вами только что настроили базовую парольную политику в домене. Если пароль пользователя при смене не удовлетворяет условиям, которые мы указали, то пользователь получит соответствующую ошибку:
Введённый пароль не отвечает требованиям политики паролей. Укажите более длинный или сложный пароль.
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
Продолжаем усиливать безопасность.
Политика блокировки учётной записи: Computer configuration → Policies → Windows Settings → Security Settings → Account Policies → Account Lockout Policy.
Или: Конфигурация компьютера → Политики → Конфигурация Windows → Параметры безопасности → Политики учетных записей → Политика блокировки учётной записи.
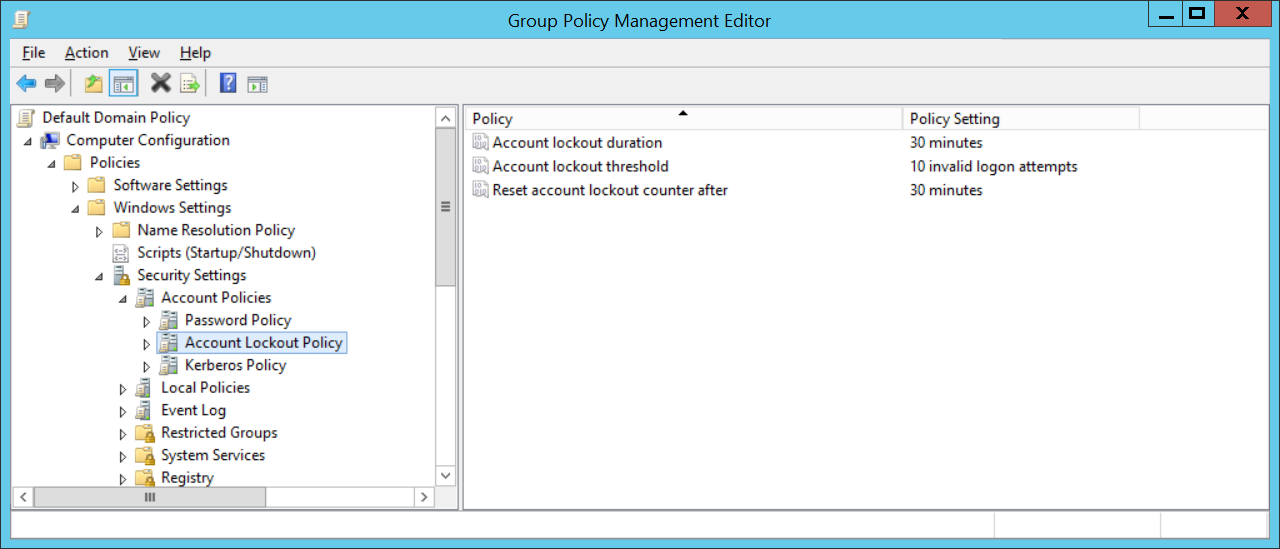
Account Lockout Duration (Продолжительность блокировки учётной записи) — срок блокировки учётной записи, после того как пользователь несколько раз ввёл неверный пароль.
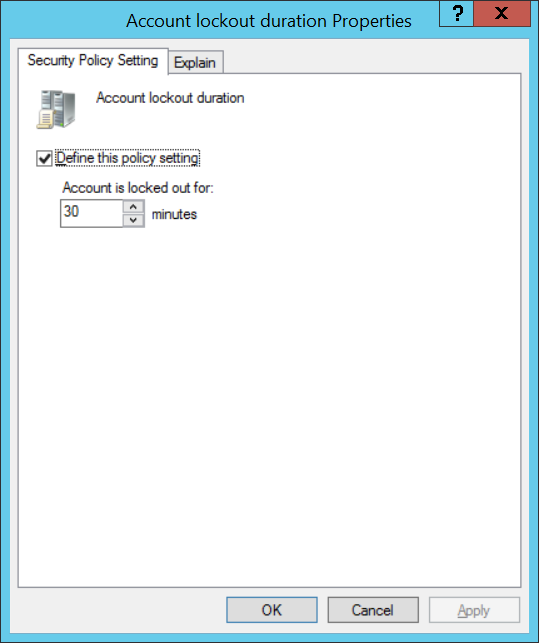
Account Lockout Threshold (Пороговое значение блокировки) — сколько раз можно вводить неверный пароль до блокировки учётной записи.
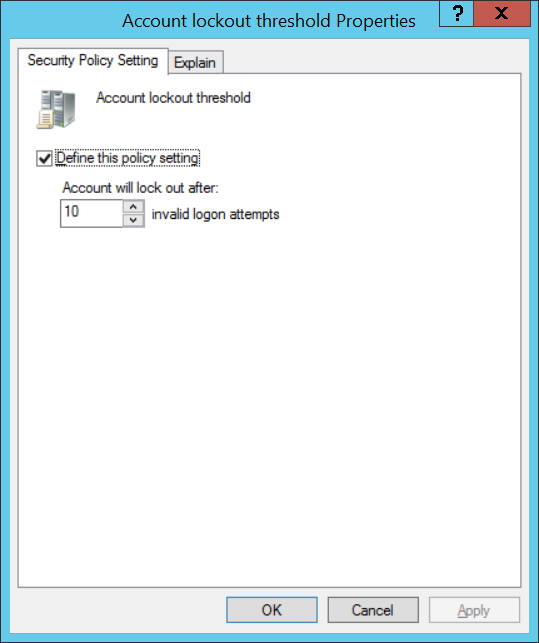
Reset account lockout counter after (Время до сброса счётчика блокировки) — через сколько минут сбрасывать счётчик порога блокировки учётной записи.
Теперь если в течение 30 минут 10 раз ввести неверный пароль, то тебя заблокирует на 30 минут.
Microsoft рекомендует использовать следующие параметры политики паролей:
- Использовать историю паролей: 24
- Максимальный срок действия пароля: не установлен
- Минимальный возраст пароля: не установлен
- Минимальная длина пароля: 14
- Пароль должен соответствовать сложности: Включено
- Хранить пароли с использованием обратимого шифрования: Отключено
Powershell
Информация о политике паролей:
Get-ADDefaultDomainPasswordPolicy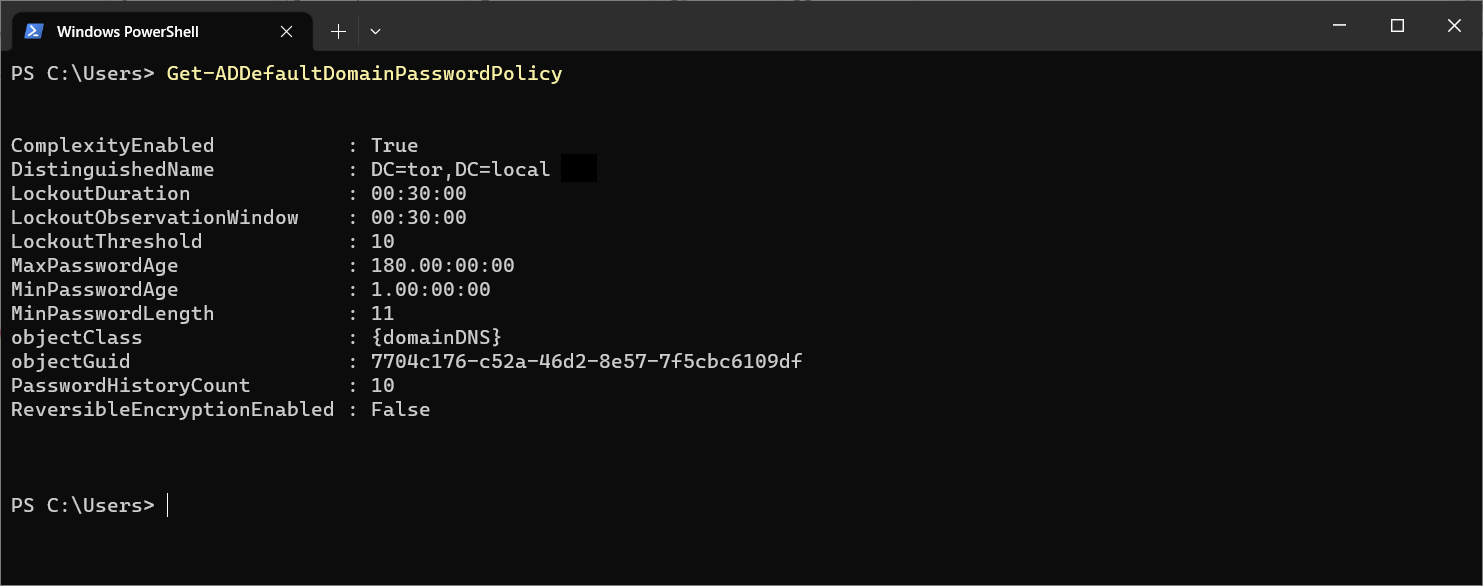
Ссылки
Как придумать хороший пароль?
Password security is one of the most important aspects of protecting your network and data from unauthorized access. Weak passwords can be easily guessed or cracked by attackers, compromising your systems and accounts. Therefore, it is essential to enforce strong password policies that require users to create complex and unique passwords that are hard to break. There has been a shift from the recommendation of shorter passwords that replace vowels with numbers and symbols to longer passwords that consist of phrases that are easy for the end users to remember. As such, a maximum configurable value of 14 for the minimum password length in Windows Server environment may be too short.
In this blog post, I will show you how to set up environments consisting of Windows Server 2022, Windows 10, and Windows 11 to enforce all users to set account passwords to be more than 14 characters long using a standard Group Policy Object (GPO). This will use the RelaxMinimumPasswordLengthLimits, MinimumPasswordLengthAudit, and MinimumPasswordLength Group Policy settings.
The default minimum password length in Windows is 8 characters, which is not enough to withstand brute force attacks that try every possible combination of characters. According to Microsoft, a password with 8 characters can be cracked in less than 2.5 hours, while a password with 14 characters can be substantially longer.
In Windows Server environments, the longstanding maximum value that can be set for the MinimumPasswordLength Group Policy settings is 14. Outside of using a Fine-grained Password Policy assigned to security groups, there is no way to require passwords longer than 14 characters in Windows.
To overcome this limitation, you need to enable the RelaxMinimumPasswordLengthLimits policy setting, which allows you to set the minimum password length to any value from 1 to 255. This setting works together with the MinimumPasswordLengthAudit and MinimumPasswordLength settings, which let you specify the minimum password length and audit the password changes that do not meet the requirement.
How to Configure the Password Policy Settings
To change the password policy settings in Windows Server 2022, you can follow these steps:
- Open the Group Policy Management Console (GPMC).
- Expand the Domains folder, choose the domain whose policy you want to access and choose Group Policy Objects.
- Right-click the Default Domain Policy GPO and click Edit.
- Navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy.
- Change “Relax minimum password length limits” to Enabled
- Change “Minimum password length audit” to the number of characters you want the minimum password length to be.
- Change “Minimum password length” to to the number of characters you want the minimum password length to be.
For more information on this Microsoft has this support article: Minimum Password Length auditing and enforcement on certain versions of Windows – Microsoft Support
Configuration Recommendations to Force Password Length Longer Than 14 Characters
The following gives more detail for each setting that you need to configure to enforce strong passwords in your environment:
Name: RelaxMinimumPasswordLengthLimits
Description: Allows you to set the minimum password length to any value from 1 to 255.
Value to require passwords greater than 14 characters: Enabled
Name: MinimumPasswordLengthAudit
Description: Specifies the minimum number of characters that a password must contain. If a user tries to change their password to a value that is shorter than this number, the system will generate a warning event in the Security log.
Value to require passwords greater than 14 characters: 15 or higher
Name: MinimumPasswordLength
Description: Specifies the minimum number of characters that a password must contain. If a user tries to change their password to a value that is shorter than this number, the system will reject the change and display an error message.
Value to require passwords greater than 14 characters: 15 or higher
Other Settings
In addition to the above, here is more detail on the remaining settings:
Name: Password must meet complexity requirements
Description: Determines whether passwords must meet a series of strong-password guidelines, such as containing characters from different categories and not including the username or full name.
Name: Enforce password history
Description: Determines the number of unique new passwords that must be associated with a user account before an old password can be reused.
Name: Maximum password age
Description: Determines the period of time (in days) that a password can be used before the system requires the user to change it.
Name: Minimum password age
Description: Determines the period of time (in days) that a password must be used before the user can change it.
Each of those settings should be thoughtfully considered to be a good mix of security and user acceptance.
By enforcing strong password policies, you can enhance the security of your network and data and comply with the best practices and standards.
Have any questions about how to use the Group Policy Object to enforce users to use long passwords over 14 characters in Windows? Please feel free to reach out to our experts at any time!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.
Whether you’re running a small business or managing a large-scale corporate network, having robust security measures in place is vital. A longer password is a powerful defense that can significantly enhance your organization’s resilience against unauthorized access.
TOC
Why Enforce Passwords Above 14 Characters?
In Windows Server 2019 environments, the default maximum enforceable password length via standard Group Policy is 14 characters. However, modern security demands stronger defenses. Lengthy passwords are statistically harder to crack. This helps protect against brute force attacks and lessens the likelihood of unauthorized data breaches. Below are some compelling reasons why moving beyond 14 characters is a good idea:
- Higher Entropy and Complexity
With every additional character, the total combinations increase exponentially, making it more difficult for attackers to guess or brute-force passwords. - Better Compliance
Many industry-specific standards and regulations—like PCI-DSS, HIPAA, and others—lean toward stronger authentication methods. Longer passwords can help meet or exceed these regulations. - Reduced Risk of Credential Stuffing Attacks
Cybercriminals often leverage stolen credentials from other services. Longer, more unique passwords decrease the probability that these attacks will be successful. - Enhanced User Awareness
Encouraging (or requiring) users to craft longer passwords helps cultivate a culture of security-minded behavior.
The Legacy 14-Character Limitation
In previous versions of Windows Server, especially prior to 2008, password length constraints were more rigid. Even after these older limits were formally removed, the built-in Group Policy Management Console still caps the “Minimum password length” setting at 14 characters. This can give the impression that 14 characters is the absolute maximum. Fortunately, Windows Server 2019 supports Fine-Grained Password Policies, a feature introduced in Windows Server 2008 that helps you surpass this limit.
Key Takeaway
While 14 characters was once considered sufficiently secure, today’s cyber threats are more sophisticated. Adopting a minimum password length beyond 14 helps ensure that your organization is prepared for emerging threats.
Configuring Fine-Grained Password Policies
Fine-Grained Password Policies (FGPP) allow administrators to apply custom password policies to specific users or groups within a domain, bypassing limitations that apply to the default domain policy. This approach enables you to require a minimum password length of 15, 16, 20, or even 24 characters—whatever your organizational security posture demands. Let’s explore the steps in detail.
Step 1: Access the Active Directory Administrative Center
- Open the Start Menu
Click on the Start button and type Active Directory Administrative Center in the search box. - Launch Active Directory Administrative Center
Press Enter to open it. You’ll see various nodes, such as your domain name, local users, and domain controllers.
Step 2: Create a New Password Settings Object (PSO)
- Select Your Domain
In the left pane, expand your domain to reveal additional nodes and containers. - Navigate to the Password Settings Container
You will see a container named Password Settings Container. This is where you can store all your custom Password Settings Objects (PSOs). - Right-Click and Choose “New > Password Settings”
In the center pane, right-click and select New > Password Settings. This opens a new dialog box for configuring the fine-grained password policy.
Step 3: Configure the PSO Attributes
In the Password Settings dialog, configure the following:
- Name: Provide a clear name, such as “MinPwdLength15” or “LongPasswordPolicy.”
- Precedence: Set a numeric value to determine this PSO’s priority. Lower numbers have higher priority. For example, a PSO with a precedence of 1 overrides a PSO with a precedence of 2.
- Minimum Password Length: Enter a value greater than 14, like 15 or 20, depending on your needs.
- Password Complexity: Decide if you want to require uppercase, lowercase, numbers, and special characters.
- Maximum Password Age: Specify how long the password can remain valid before a user must change it.
- Minimum Password Age: Control how soon a password can be changed after it is set.
- Password History: Determine how many previous passwords are disallowed for reuse.
- Reversible Encryption: Typically set this to Disabled for stronger security.
Special Considerations
- Precedence
If multiple PSOs apply to the same user or group, the PSO with the lower precedence number takes effect. - Naming Conventions
Use descriptive names that easily indicate the policy’s purpose—for example, “HQ_DeptFinance_MinLen16” to target the Finance department in a headquarters domain.
Step 4: Apply the PSO to Users or Groups
- Direct Applies To
In the Password Settings dialog, look for the Direct applies to field. - Select Users or Groups
Click Add. In the dialog that appears, you can enter the usernames or group names to which the policy should apply. - Click OK
After making your selections, click OK to save and close the dialog.
Step 5: Verification
You can verify your newly configured policies in multiple ways:
- PowerShell
- Run
Get-ADFineGrainedPasswordPolicy -Filter *to list all existing fine-grained password policies. - Use
Get-ADUserResultantPasswordPolicy -Identity <username>to see which policy applies to a specific user. - Active Directory Administrative Center
- Navigate back to the Password Settings Container and confirm that your new policy is listed.
- Double-check the Direct applies to field to ensure the correct users or groups are targeted.
- Testing
- Attempt to change a user’s password to something shorter than your specified limit to confirm enforcement.
Comparing Policy Settings in a Table
Below is a sample table illustrating the attributes of a sample Fine-Grained Password Policy vs. a default domain policy:
| Policy Attribute | Default Domain Policy | Sample Fine-Grained Policy |
|---|---|---|
| Minimum Password Length | 14 characters | 16 characters |
| Maximum Password Age | 42 days | 30 days |
| Minimum Password Age | 1 day | 2 days |
| Password History | 24 passwords | 24 passwords |
| Complexity Requirement | Enabled | Enabled |
| Reversible Encryption | Disabled | Disabled |
| Precedence | N/A (GPO) | 1 (PSO) |
The table underscores how a FGPP can exceed the limitations of the default Group Policy, particularly regarding minimum password length.
Advantages of Longer Passwords
While traditional complexity rules (requiring uppercase letters, numbers, symbols) add a security layer, longer passwords remain the most effective safeguard against brute-force attacks. Here’s a closer look at the advantages:
- Greater Security
Passwords with 15 or more characters take exponentially longer to break than shorter passwords. This holds true whether attackers employ dictionary attacks, rainbow tables, or pure brute force. - Adaptability
With Fine-Grained Password Policies, you can tailor separate password requirements for different groups. For instance, administrative accounts can have more stringent rules compared to standard users. - Future-Proofing
As technology advances, computational power grows. Requiring more extended passwords helps ensure that your policies remain robust for the foreseeable future. - Behavioral Change
Longer minimum password lengths often lead users to choose more passphrase-like passwords, which can be both memorable and complex—like “SunsetInHawaii2025!” instead of “Pa$$w0rd123.”
Common Misconceptions
- “Longer Passwords Are Harder to Remember”
While this can be true for random strings, passphrases (e.g., multiple words strung together) balance memorability and complexity. - “Users Will Write Them Down”
Educating users on creating passphrases that are meaningful yet hard to guess mitigates the risk of writing down passwords on sticky notes. - “Passwords Above 14 Characters Won’t Work Everywhere”
All recent Windows and Active Directory infrastructures support lengths well beyond 14, especially once Fine-Grained Password Policies are correctly configured.
Balancing Complexity and Usability
You might consider relaxing certain complexity requirements if you’re pushing for significantly longer passwords. For example, you could reduce mandatory special characters while increasing overall length. The final choice depends on your environment’s risk tolerance and user feedback.
Dealing with Legacy Systems and Compatibility
If your organization still relies on older systems or services that might not fully support FGPP:
- Evaluate Compatibility
Confirm whether these systems can handle passwords longer than 14 characters. Many modern services do, but it’s worth verifying for any specialized or outdated applications. - Plan Phased Migrations
If you discover compatibility issues, schedule a phased approach. Implement the new, stricter policy in parts of the organization that support it while gradually retiring or upgrading the incompatible systems. - Provide Clear Communication
Warn users of any upcoming password changes well in advance. Offer guidelines on how to create longer, more secure passphrases to facilitate a smoother transition.
Integrating FGPP with Existing Security Frameworks
Windows Server security doesn’t exist in a vacuum. Fine-Grained Password Policies should align with your broader security architecture:
- Multi-Factor Authentication (MFA)
Even with stronger password policies, adding MFA raises the security bar significantly. - Privilege Access Management (PAM)
For sensitive roles (domain admins, service accounts), PAM solutions can enforce rotations and additional controls. - Security Auditing
Regularly audit policy adherence and investigate any anomalies or repeated password reset attempts. - Monitoring and Alerting
Set up alerts for suspicious logon attempts or sudden spikes in password reset requests.
Best Practices for Rolling Out New Password Policies
Shifting password requirements can cause confusion. Minimizing disruption requires thoughtful planning:
- Communicate Early
Send out multiple communications explaining why passwords must now be longer. Provide helpful guidelines to users on how to create secure passphrases. - Offer Training Sessions
Brief tutorials or interactive workshops can help users transition to the new policy painlessly. - Grace Period
Allow a window where both old and new requirements coexist. This ensures that users aren’t forced to update passwords at once. - Measure Compliance
Use reporting tools within Active Directory or third-party solutions to monitor how quickly users comply. - Encourage Password Managers
If allowed by your security policy, recommend secure password managers. This helps users cope with more complex requirements.
Example: Communicating Policy Changes
Below is a suggested timeline for rolling out a fine-grained password policy that sets a 16-character minimum:
- Week 1: Announcement email explaining the new policy, the reasons for change, and tips on creating passphrases.
- Week 2: Optional training sessions or Q&A videos on best practices for longer passwords.
- Week 3: Final reminder email. Notify users that the policy will be enforced in the coming week.
- Week 4: Policy enforcement date. Users attempting to change passwords now must meet the 16-character minimum.
Maintaining Momentum
Don’t let security measures stagnate. Continually review your environment:
- Frequent Audits
Check if any user accounts are still not adhering to the new policy. - Policy Revisions
Over time, you might need to adjust password length, complexity requirements, or other FGPP attributes. - Ongoing Education
Keep security training relevant and up to date, emphasizing the importance of strong authentication.
Fine-Grained Password Policies vs. Group Policy
Standard domain Group Policy still plays a crucial role. However, Fine-Grained Password Policies offer a more granular approach:
- Target Specific Groups
You’re not forced to enforce a one-size-fits-all policy across the entire domain. Sensitive accounts can have more stringent requirements. - Flexible Precedence
If you have overlapping policies, you control which one overrides by setting a “Precedence” value. - Scalability
As your organization grows, you can create multiple PSOs for different departments without rewriting the entire domain-level policy.
Common Challenges
- Policy Conflicts
If a user falls under two or more PSOs with different requirements, the one with the lowest precedence number wins. - Lack of Documentation
Over time, administrators may create multiple PSOs. Document each carefully, specifying name, precedence, scope, and rationale. - Insufficient Permissions
Only domain admins or equivalent privileges can create and link PSOs. Ensure you have the correct role before attempting to set them up.
Troubleshooting Tips
- Check Event Viewer
Look for relevant logs under Windows Logs > Security that might give clues about policy application errors. - Use PowerShell Validation
If the new policy isn’t working as expected, confirm that it has been assigned to the correct user or group withGet-ADUserResultantPasswordPolicy. - Replicate Domain Controllers
In multi-DC environments, ensure replication is healthy. Delayed or failed replication can prevent PSOs from applying consistently.
Going Beyond Passwords
While focusing on password length and complexity is important, a holistic security strategy includes:
- Account Lockout Policies
Limit the number of failed logon attempts to deter brute force attacks. - Security Updates
Regularly update your Windows Server 2019 environment with the latest patches. - Administrative Tiering
Use separate administrative accounts for everyday tasks to reduce the risk of privileged credential exposure. - Network Segmentation
Restrict lateral movement by segmenting your network, so a breach in one area doesn’t compromise everything. - Logging and Monitoring
Capture and review logs frequently to catch early signs of suspicious activity.
Additional FGPP Features to Explore
Beyond just minimum password length, Fine-Grained Password Policies allow you to:
- Lock Out Duration: After a certain number of failed attempts, lock the account.
- Lock Out Threshold: Set how many times a user can fail before the lockout.
- Observation Window: Configure how long failed attempts are counted toward the lockout threshold.
Final Thoughts
Increasing the minimum password length above 14 characters in Windows Server 2019 is not only possible but also strongly recommended to maintain robust security. Fine-Grained Password Policies give you the flexibility to apply customized rules, ensuring different user groups have the right level of protection without imposing uniform constraints across your entire domain. By following best practices such as early communication, gradual enforcement, and continuous auditing, you can seamlessly transition your organization to these stronger password requirements.
Remember, a good password policy is only one part of a comprehensive security strategy—pair it with strong operational procedures, ongoing user education, and additional safeguards like MFA to protect your infrastructure effectively.
Did you know that cyber security and safety of company networks have become an integral element in all computer systems in 2022, including Windows Server? One important factor in providing the needed security is having a secure password policy, and the Windows Server 2022 password requirements are here to make sure your company boasts a lock-tight network. Every business must become familiar with these new password standards to stay safe online. By ensuring that your password protects all your data, you can avoid any possible data theft, cyber-attacks, and unwanted security breaches. Enhance your company’s cybersecurity with the Windows Server 2022 password requirements.
1. Making Sure Your Passwords Are Secure: Windows Server 2022 Password Requirements
Making sure your Windows Server 2022 passwords are secure is an important step in protecting your data. Most users may not be aware of the required password standards, so here are a few basic rules to ensure your passwords are secure:
- Minimum of 8 characters: The password should have a minimum of 8 characters. This makes it harder for a hacker to guess your password.
- Contain Uppercase and Lowercase Letters: Your password should include a mix of uppercase and lowercase letters to increase the level of difficulty.
- Include Special Characters: Adding a special character such as (!, #, $, etc.) will make your password even more secure.
- Do not use common words: It is recommended that you avoid using common words as passwords. This will make it harder for hackers to guess your password.
These requirements not only protect you from cyberattacks but also prevent the risk of data theft or unauthorized access to your systems. By following these guidelines, you can help ensure that your Windows Server 2022 passwords remain secure.
2. Understanding What Makes a Good Password
Strong Passwords Are Key to Protection
Creating a strong password is one of the most important steps you can take to protect yourself online. A good password will keep your online accounts safe, preventing criminals from accessing your activity, identity, and data.
Knowing what makes a good password is the first step to creating one. To protect your account, make sure your password has the following attributes:
- A minimum of 12 characters.
- A combination of upper and lowercase letters.
- At least one number and one special character (such as ! @, #, $).
- No names or words can be found in the dictionary.
Additionally, make sure to never share your password with anyone and to never use the same password for multiple accounts. Passwords should also be changed regularly to ensure that your accounts remain safe and secure. By keeping these few pieces of advice in mind you can help protect yourself from any potential cyber threats.
3. Step-by-Step Guide for Setting Your Password Requirements
Creating Secure Passwords
Having a secure password is essential to keeping your online accounts safe. Luckily, setting secure password requirements doesn’t have to be a difficult task. Using this step-by-step guide, you’ll have the right parameters in place for creating stronger passwords in no time.
- Consider adding more than 8 characters. While 8 characters is the standard for many passwords, adding 1 or 2 more can make yours tougher for unauthorized users to guess.
- Password expiration times are essential. How often you need to change passwords depends on the sensitivity of the information stored on the system, but a good rule of thumb is to have your passwords expire every 90 days.
- Mix in numbers, letters, and symbols. There’s no one-size-fits-all approach here, but using a combination of different characters is necessary to create a secure password.
- Don’t use real words. Easy-to-guess passwords like “password” or “123456” are too easy to hack. Instead, opt for phrases or gibberish words that only make sense to you.
Finally, make sure your password requirements are easy for your users to understand. If your requirements are too complicated, chances are they’ll just give up and choose weaker passwords, thereby undermining the effectiveness of the system.
4. Stay Safe and Keep Your Data Secure with Windows Server 2022 Password Rules!
Enforce Complex Password Rules
It is important to secure your data on Windows Server 2022 by setting complex password rules. Creating difficult passwords helps guard your account from intruders. To remain safe, consider the following guidelines while creating a password:
- Use at least 8 characters with a mix of letters, symbols, and numbers.
- Do not use personal information such as name, date of birth, address, etc.
- Do not use common words, phrases, or well-known numbers.
- Don’t repeat the same password on different accounts.
Regularly Change Your Password
To maintain a high level of security for your account, it is recommended to make password changes regularly. Storing passwords in a password manager is a great way to remember them while keeping them safe from prying eyes. Additionally, it would be advisable not to share your passwords with anyone. Having an effective password policy in place can greatly reduce the risks of data breaches and secure your account on Windows Server 2022.
When it comes to password security, there are a plethora of factors to consider in order to ensure the protection of sensitive information. From minimum password length to complexity requirements to password expiration policies, organizations must implement a robust password policy to fend off potential threats such as brute force attacks and dictionary attacks. Active Directory, as a key component in many organizations’ IT infrastructure, plays a vital role in enforcing password policies and settings. By configuring parameters such as minimum password age, maximum password age, and password history, administrators can enhance the security of user accounts and prevent unauthorized access to sensitive data.
Additionally, the use of fine-grained password policies allows for the customization of password complexity requirements based on specific user groups or organizational units. It is essential for organizations to regularly audit password lengths and enforce stringent password requirements to mitigate the risk of successful attacks. Adhering to best practices in password management, such as enabling multi-factor authentication and implementing strong password policies, is crucial in safeguarding against malicious software and suspicious activity. By staying informed about the latest password security guidelines and utilizing powerful tools and services, organizations can stay ahead of potential threats and protect their valuable data. (Source: Microsoft Active Directory Security Guide)
Password security is a critical aspect of maintaining the integrity of any system, particularly when it comes to managing user accounts and preventing unauthorized access. To ensure a robust and secure password policy, organizations often implement a variety of password complexity requirements. These requirements may include specifications such as minimum password length, the use of uppercase characters, and the prevention of common passwords. Active Directory, commonly used in Windows environments, allows for the configuration of password policies within an organization’s domain. These policies can dictate settings such as minimum and maximum password age, password history, and the enforcement of password expiration. Additionally, the use of fine-grained password policies can provide organizations with greater flexibility in creating and enforcing password rules for specific user groups.
In order to protect against malicious attacks, such as brute force attacks or dictionary attacks, organizations may also employ mechanisms for content and user account password auditing. These measures help to identify and address potential vulnerabilities in the system, ensuring that passwords are strong and secure. Furthermore, the use of multi-factor authentication and the regular auditing of password lengths can further enhance the security of user accounts and prevent unauthorized access.
Overall, implementing strong password policies and security settings is crucial for maintaining the integrity and security of an organization’s systems and data. By following best practices and staying informed about the latest developments in password security, organizations can reduce the risk of security breaches and protect sensitive information from potential threats. Sources: Microsoft TechNet, NIST Special Publication 800-63B, SANS Institute.
When it comes to password security, there are various considerations to keep in mind. Password length requirements play a crucial role in determining the strength of a password. Shorter passwords and weak passwords are more susceptible to brute force attacks, where hackers attempt to gain access by trying different combinations. Domain Controller settings and Default values for password parameters can impact the security of an organization’s network. The default domain policy often includes guidelines like requiring 14-character passwords and setting password length limits. The operating system stores passwords for user accounts and service accounts, which should be protected with additional resources such as custom password filters or external password filters. It is important for organizations to have effective password policies in place to prevent common user passwords, password reuse, and frequent password changes. Regular password audits and enforcement of password policies can help mitigate the risk of brute force password attacks and ensure the complexity of passwords meets the necessary security standards. Sources: Microsoft TechNet, NIST Special Publication 800-63B.
Event ID, audit warning events, Directory-Services-SAM Event ID, Directory-Services-SAM 16978 events, and the channel for security events are crucial components in monitoring and managing authentication functions in an organization. Two-factor authentication is a widely used method for enhancing security by requiring users to provide two forms of identification before granting access. Biometric authentication, which involves using physical characteristics such as fingerprints or facial recognition for verification, is another advanced method gaining popularity. Credential stuffing attacks, where hackers use stolen credentials to gain unauthorized access, are a real threat faced by companies. Active Directory Groups and Reports play a key role in managing users and their permissions within a network. Compliance with policies and guidelines is essential for ensuring data security and avoiding legal issues. Overall, understanding and implementing effective authentication methods and policies is essential for protecting sensitive information in today’s digital age.
Windows Server 2022 Password Security Guidelines
| Password Requirement | Description |
|---|---|
| Minimum of 8 characters | The password should have at least 8 characters for increased security. |
| Include Uppercase and Lowercase Letters | Use a mix of uppercase and lowercase letters in your password for added complexity. |
| Include Special Characters | Add special characters like !, #, $ to make your password more secure. |
| Avoid Common Words | Avoid using common words or phrases to prevent easy guessing by hackers. |
| Change Password Regularly | It is recommended to change your password periodically for enhanced security. |
Q&A
Q: What are the password requirements for Windows Server 2022?
A: To help keep your computer and data secure, Windows Server 2022 requires a password that’s at least eight characters long and includes a combination of uppercase and lowercase letters, numbers, and symbols. It must also not be a commonly used password and must be regularly changed.
Q: What are the minimum password requirements in Active Directory’s password complexity policy?
A: The minimum password requirements in Active Directory’s password complexity policy typically include a combination of uppercase letters, lowercase letters, numbers, and special characters to ensure strong password security.
Q: What is the purpose of setting a minimum password length in the password policy settings?
A: Setting a minimum password length helps enforce stronger password security by requiring users to create passwords that are a certain number of characters long, reducing the likelihood of password guessing attacks.
Q: How can administrators prevent brute force attacks on user accounts?
A: Administrators can prevent brute force attacks on user accounts by enforcing password complexity requirements, implementing strong password policies, setting account lockout policies, and monitoring for suspicious login attempts.
Q: What is the significance of password expiration policies in Active Directory?
A: Password expiration policies in Active Directory help ensure that users regularly update their passwords, reducing the risk of unauthorized access due to compromised or outdated passwords.
Q: How does Active Directory enforce password history requirements?
A: Active Directory enforces password history requirements by remembering previous passwords used by users and preventing them from reusing the same passwords, thereby enhancing password security.
Q: What is a fine-grained password policy and how does it differ from the default domain password policy?
A: A fine-grained password policy allows administrators to define specific password requirements for different sets of users or groups, providing more flexibility and control over password security than the default domain password policy.
Q: How can organizations audit password lengths to ensure compliance with security standards?
A: Organizations can audit password lengths by using tools or scripts to analyze password length data, identify any passwords that do not meet the minimum length requirements, and address any non-compliant passwords to enhance overall security.
Conclusion
For those seeking the best solution to Windows Server 2022 Password Requirements, look no further than LogMeOnce – the perfect choice. This reputable and reliable password management software has been created specifically for IT professionals, yet it remains hassle-free and simple to use. Set up a free LogMeOnce account today and access one of the most comprehensive and secure password management solutions available. LogMeOnce makes it easy to store data securely, even as Windows Server 2022 password requirements become more complex. This free password manager offers simple and robust security solutions for Windows Server users with industry-leading password strength and SSL encryption ensuring all data is safe in the cloud.
Faye Hira, a distinguished graduate from the University of Okara, has carved a niche for herself in the field of English language education and digital marketing. With a Bachelor of Science in English, she specializes in Teaching English as a Second or Foreign Language (ESL), a skill she has honed with dedication and passion. Her expertise extends beyond the classroom and content writer, as she has also made significant strides in the world of Content and Search Engine Optimization (SEO). As an SEO Executive, Faye combines her linguistic prowess with technical acumen to enhance online visibility and engagement.