Пароль не отвечает требованиям политики — как исправить?
При изменении пароля в Windows 11, Windows 10 или других версиях системы вы можете столкнуться с сообщением: «Введенный пароль не отвечает требованиям политики паролей. Проверьте минимальную длину пароля, его сложность, отличие от ранее использованных паролей». Текст сообщения может варьироваться, в зависимости от того, какой именно способ вы будете использовать для изменения пароля Windows.
В этой инструкции подробно о том, как отключить требования к паролям в Windows путем настройки соответствующих политик безопасности. Способы приведены для компьютера с личной учетной записью, а не для учетной записи домена, впрочем, логика остается той же и для этого сценария. На близкую тему: Способы изменить пароль Windows 11 и Windows 10.
О каких политиках паролей и требованиях идет речь

Сообщение «Введенный пароль не отвечает требованиям политики» появляется в ситуации, когда в политиках безопасности заданы какие-либо ограничения для паролей, а именно:
- Минимальная длина пароля
- Требования к сложности пароля, которые включают в себя:
- Пароль не должен содержать имя или часть имени пользователя.
- Пароль должен содержать не менее 6 символов
- Пароль должен содержать символы по меньшей мере трёх из следующих видов: прописные латинские буквы, строчные латинские буквы, цифры, символы (не являющиеся буквами или цифрами).
В большинстве случаев оказывается включенным вторая из двух политик. Есть и другие политики паролей, например, задающие максимальный срок их действия, но появляющееся сообщение в этом случае будет другим: Пароль просрочен и должен быть заменен.
Если у вас нет задачи отключать требования к паролям или речь идёт о компьютере организации, просто установите пароль, соответствующий указанным требованиям (об определении заданной минимальной длины пароля — далее в инструкции).
В ситуации, когда это ваш личный компьютер, вы можете отключить требования к паролям несколькими способами.
Как отключить требования политики безопасности к паролям
Есть несколько способов отключения требований политики безопасности, относящихся к паролям. Основной — использование оснастки «Локальная политика безопасности». Шаги будут следующими:
- Нажмите клавиши Win+R на клавиатуре (или нажмите правой кнопкой мыши по кнопке «Пуск» и выберите пункт «Выполнить»), введите secpol.msc и нажмите Enter.
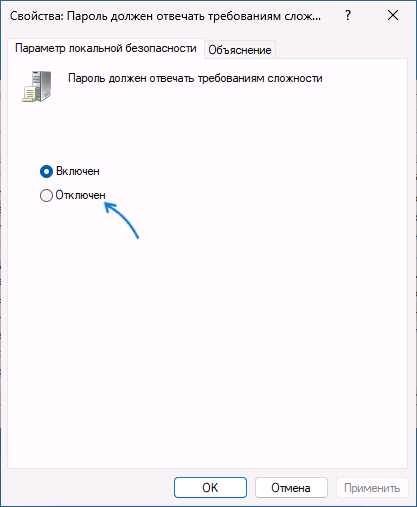
- Перейдите в раздел «Политики учетных записей» — «Политика паролей». По умолчанию, без настроенных ограничений все значения должны выглядеть как на изображении ниже.
- Если вы видите, что настроена минимальная длина пароля (значение отличается от 0) или включена политика «Пароль должен отвечать требованиям сложности», дважды нажмите по такой политике и измените значение на 0 или «Отключен» соответственно.
- Примените сделанные настройки.
Вторая возможность — использование Windows PowerShell. Отключить требования к минимальной длине пароля можно следующим образом:
- Запустите PowerShell или Терминал Windows от имени Администратора. Сделать это можно через меню по правому клику на кнопке Пуск.
- Введите команду net accounts и проверьте, установлена ли минимальная длина пароля.
- Если значение задано, используйте команду
net accounts /minpwlen:0
чтобы отключить требования к длине пароля.
Настроить требования политики к сложности пароля с помощью net accounts не получится, но можно использовать следующий набор команд:
secedit /export /cfg c:\edit.cfg
((get-content c:\edit.cfg) -replace ('PasswordComplexity = 1', 'PasswordComplexity = 0')) | Out-File c:\edit.cfg
secedit /configure /db $env:windir\security\edit.sdb /cfg c:\edit.cfg /areas SECURITYPOLICY
rm c:\edit.cfg

Также на эту тему может быть полезным: Как сбросить локальные групповые политики и политики безопасности в Windows.
A Windows password policy sets standards for the use of login passwords on Windows 10 and 11 computers managed by your organization.
With Miradore, you can implement a password policy for Windows computers using the Password configuration profile. The Password configuration profile is available in all plans of Miradore. It enables you to enforce the use of Windows login passwords for local accounts, make users change their passwords, and set requirements for the passwords.

Preparations
- You need to have either Administrator or Editor role on your Miradore site.
- The Password configuration profile is applicable to fully enrolled Windows 10 and 11 computers that have Miradore’s MDM profile installed.
- The Password configuration profile affects only local user accounts. Neither Active Directory user accounts nor Microsoft accounts are affected by the profile.
How to create a password policy for Windows?
To create a passcode policy for all local users’ accounts on Windows devices, follow the steps below:
- Go to Management > Configuration profiles and create a new configuration profile (click Add > Windows > Password).
- Configure the password requirements and settings. See the table below for more details.
Setting Description Password required Specifies if a login password is required for all local user accounts on Windows 10 and 11 computers. Minimum length Specifies the minimum accepted length of the password. Minimum password age Specifies the shortest time to use each password. The default value is 1 which means that users can change their password once per day at most. The purpose of setting the password age is to prevent users from recycling their previous passwords back to active use too quickly. Expiration age Specifies the maximum period of time how long a password can be used before it must be changed. History restriction Specifies the number of previous passwords that cannot be reused. Maximum number of failed attempts Specifies the maximum number of failed login attempts. If the user exceeds this limit and BitLocker is configured, the device will be put on to the BitLocker recovery screen. If BitLocker is not configured, the device will be booted if the user exceeds the limit of failed login attempts. Maximum screen lock timeout Specifies how quickly an idle device will be automatically locked. Notice that the device user can set a shorter screen lock timeout for the device than the policy, but not longer. - Deploy the configuration profile to Windows computers either using the configuration profile deployment wizard or with the business policies.
- During the next login, the device users will be prompted to enter a password that fulfills the specified requirements.
How to make users change their Windows password?
You can force users to change their Windows login password periodically with the Expiration age configuration option.
If you deploy a password policy that is stricter than the user’s current password, the user must define a new password that meets the requirements.
Troubleshooting
Answers to common questions and possible solutions to known issues.
Why does the deployment of a Password configuration profile fail?
Deployment of the Password configuration profile can fail with the error Configuration profile deployment failed with error ‘ATOMIC_FAILED’ for several reasons, including the following:
- There is even one user account on a device that has the «User cannot change password» setting enabled. For example, if a Microsoft account is added to the device and a Password configuration profile is deployed to the device via Miradore.
- The «minimum password age» is equal to or greater than the «Expiration age» of the password.
- In the case of Windows 11 Pro, the «minimum password age» is set to more than 3 months.
How to clear/disable the password requirements?
Remove the deployed Password configuration profile from the device. Miradore will then restore the default password settings to the device.
Why device user cannot change the password although the profile has been removed already?
The minimum password age on Windows devices is one day. Perhaps enough time hasn’t passed since the last password change? You can try to create and deploy a new Password configuration profile to override that. If you want to allow the user not to use a password, you can set the «Password required = No».
Can I reset Windows passwords for the local user accounts remotely?
No. Resetting passwords for local user accounts is not possible with Miradore. A workaround is to create a Windows application running for example a PowerShell script. Local administrators can reset passwords for other local users.
Is it possible to bypass Windows password with Miradore?
No.
Have you already subscribed to our newsletter?
Fill in your email address to get the latest Miradore news and articles delivered directly to your inbox!
To view our Privacy Policy, click here
Changing password requirements on Windows 10 is a straightforward process that lets you customize the length and complexity of passwords for your system. By adjusting these settings, you can enhance security or make password management easier. To accomplish this, you’ll need to access the Local Security Policy editor, a tool in Windows that allows you to tweak various security settings, including password policies.
The following steps will guide you through changing the password requirements on your Windows 10 computer. It’s crucial to have administrative privileges to perform these actions, as they affect the security settings of your system.
Step 1: Open the Local Security Policy
Start by pressing the Windows key and typing “Local Security Policy” into the search bar.
After you type “Local Security Policy,” you should see an option pop up in the search results. Click on it to open the Local Security Policy editor, a tool where you can manage all sorts of security settings for your computer. This tool is your gateway to changing password rules.
Step 2: Navigate to Account Policies
In the Local Security Policy window, click on “Account Policies” in the left pane.
Once you click on “Account Policies,” you’ll see a couple of options pop up: Password Policy and Account Lockout Policy. You’re going to focus on the Password Policy section, where you can tweak the settings to match your desired password complexity.
Step 3: Click on Password Policy
Now, click on “Password Policy” under Account Policies.
Within the Password Policy section, you’ll find various settings like minimum password length and password complexity requirements. This section is where you can do the real work in customizing how passwords function on your system.
Step 4: Adjust Password Requirements
Double-click on each policy setting to modify it according to your preference.
For instance, you can change the minimum password length by double-clicking it and entering a new number. Similarly, you can enable or disable complexity requirements, which dictate the types of characters that must be included in passwords. Feel free to adjust these settings to whatever you find suitable.
Step 5: Save Changes and Exit
Once you’re satisfied with the settings, click “OK” to save your changes and close the window.
After clicking “OK,” your new password requirements will be set. There’s no need to restart your computer for these changes to take effect; they apply immediately.
After completing these steps, your Windows 10 system will now enforce the new password requirements you set. Any new passwords created will need to meet these criteria, thereby enhancing or relaxing security based on your setup.
Tips for Changing Password Requirements on Windows 10
- Ensure you have administrative privileges before attempting any changes.
- Be cautious when lowering security measures, as it may leave your system vulnerable.
- Consider combining both length and complexity for stronger security.
- Regularly review and update your password policies to keep up with best practices.
- Document any changes you make for future reference or adjustments.
Frequently Asked Questions
Why can’t I find the Local Security Policy on my version of Windows 10?
The Local Security Policy editor is only available on Windows 10 Pro and Enterprise editions. If you’re using Windows 10 Home, you’ll need to change password settings through other means, like the command prompt.
How do I revert to the default password settings?
You can manually reset each setting in the Password Policy to its default state. Alternatively, you might consider using system restore if you want a broader reset.
What is the recommended minimum password length?
Generally, a minimum length of 8 characters is recommended for security purposes, but longer passwords are always better.
Will changing these settings affect existing user accounts?
No, altering these settings only impacts new passwords created after the changes. Existing passwords will remain unaffected.
Can I enforce a password expiration policy?
Yes, you can set a password expiration period within the Password Policy settings to require users to update their passwords regularly.
Summary
- Open the Local Security Policy.
- Navigate to Account Policies.
- Click on Password Policy.
- Adjust Password Requirements.
- Save Changes and Exit.
Conclusion
Changing password requirements on Windows 10 can significantly impact your system’s security, making it either more robust or more user-friendly depending on your needs. By accessing the Local Security Policy editor, you have the power to tailor how passwords operate on your computer. This flexibility is crucial in today’s world, where digital security is more important than ever.
With password policies in place, you can ensure that your system is less susceptible to unauthorized access, while also simplifying password management for yourself or your team. Remember, though, that with great power comes great responsibility. Always weigh the benefits of stronger security against the potential inconvenience to users.
As you go forward, consider exploring more about Windows 10’s security features. There’s a wealth of options available, each playing a unique role in safeguarding your digital environment. Whether you’re a casual user or a tech enthusiast, understanding these features will help you maintain a secure and efficient operation.
So why not take a few minutes to dive into those settings today? You might be surprised at how much control you have over your system’s security landscape.
Matt Jacobs has been working as an IT consultant for small businesses since receiving his Master’s degree in 2003. While he still does some consulting work, his primary focus now is on creating technology support content for SupportYourTech.com.
His work can be found on many websites and focuses on topics such as Microsoft Office, Apple devices, Android devices, Photoshop, and more.
What Is Password Policy?
Using password policy can enhance password’s security. It requires users to set password length, password age, password history, etc. Via password policy, you can set a more complicated password that’s hard to be guessed or cracked.
The Reasons of Setting Password Policy in Windows 10
It will be bad for your user account and PC if the login password is too simple. Setting password policy will enforce users to set a complicated password. And the password cannot be successfully created until it meets the requirements of policies. As a result your user account will be safer.
Step 1: Press “Win” + “R” key to open “Run” window. Type in: secpol.msc then click “OK”.
Step 2: After you open “Local Security Policy”, select them in order: “Security Settings” > “Account Policies” > “Password Policy”.
Step 3: In the right pane, double click any policy and change the setting according to your needs.
Explanation of Setting Each Password Policy
Password Must Meet Complexity Requirements
If you enable this policy, the password will not be successfully created until it meets the complexity requirements.
Requirements as below:
1. More than two contiguous characters from user name cannot be contained in password.
2. Be at least six characters in length and three of following four types of character need to be included in password.
• English uppercase characters (A through Z)
• English lowercase characters (a through z)
• Base 10 digits (0 through 9)
• Non-alphabetic characters (for example, !, $, #, %)
Minimum Password Length
The longer the password, the safer it will be. A password should at least contain the minimum number of characters for a user account.
Minimum Password Age
This security setting determines the period of time (in days) that a password must be used before the user can change it. For example, if you set 10 days, then your password can be changed after 10 days. Besides, password can be changed anytime if the minimum password age is set to be 0.
Maximum Password Age
This security setting determines the period of time (in days) that a password can be used before the system requires the user to change it. For example, if you set 90 days, your password will expire in 90 days then system will require you to change it. But the password will not expire if the maximum password age is set to 0.
Enforce Password History
This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. It can ensure the old passwords are not reused continually. For example, if you keep 9 passwords remembered, then you need to change new passwords nine times before an old password can be reused.
Store Passwords Using Reversible Encryption
This security setting determines whether the operating system stores passwords using reversible encryption. If this policy is enabled, some bad guys may easily crack the password and access users’ PCs. It’s suggested to disable it unless application requirements are more important than the protection of password information.
Forget the complicated password and cannot sign in Windows? System rescue tool Renee PassNow can help you clear the password of target user account. Then you can access your PC and set a high-security login password again.
Unable to change Windows password and keep getting the error “The password you typed does not meet the password policy requirements“? How to make the system lock your account when a hacker tries to guess your password continuously? In this guide we’ll show you how to change the account lockout and password complexity requirement policy from Command Prompt, Local Security Policy Editor, or by exporting / importing your policy. These methods work on Windows 10, 8, 7, Vista and XP.
- Part 1: Local Security Policy
- Part 2: Change Password Complexity Requirement Policy
- Part 3: Change Account Lockout Policy
- Part 4: Change Local Security Policy by Exporting and Importing
Local Security Policy
Local Security Policy allows enforcing many system-wide, user and security-related settings, such as password policy, account lockout policy, audit policy and user rights.
When you want change a security setting this is how you launch the Local Security Policy Editor:
- Press the Windows key + R to bring up the Run box.
- Type secpol.msc and hit Enter.
When the Local Security Policy Editor opens, you can navigate to the security policy you’re interested.
Note that the Local Security Policy Editor is not available on the Home edition of Windows. So if you’re running Windows 10/8/7/Vista/XP Home, you have to change the local security policy from Command Prompt.
Change Password Complexity Requirement Policy
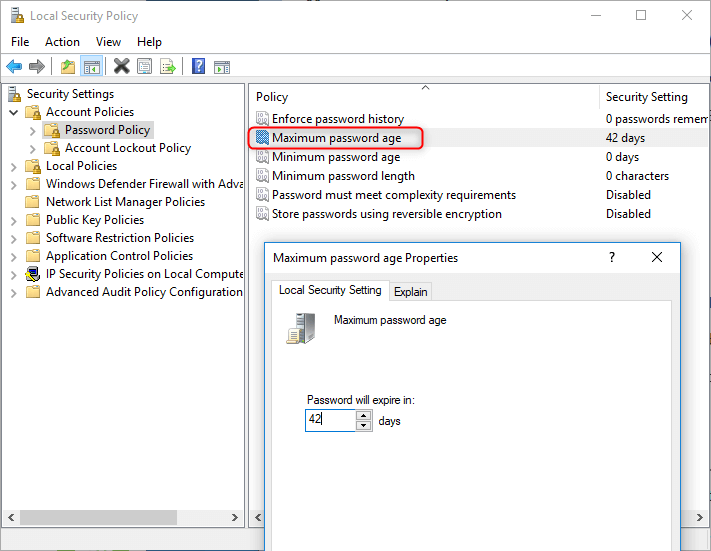
In the left pane of Local Security Policy Editor, expand Account Policies and then click Password Policy. In the right pane you see a list of password policy settings. Double-click on the policy you want to modify, it will open the Properties box and you can change the setting to desired value.
- Maximum password age
Set the maximum number of days that a password is valid. After this number of days, the password is expired and Windows will force you to change the password at the next logon. You can set the Maximum password age between 1 and 999, or set it to 0 so your password will never expire. - Minimum password age
This security setting determines the period of time (in days) that a password must be used before the user can change it. You can set a value between 1 and 998 days, or set it to 0 for allowing to change password anytime. This policy allows you to limit how frequently a user may change the password.
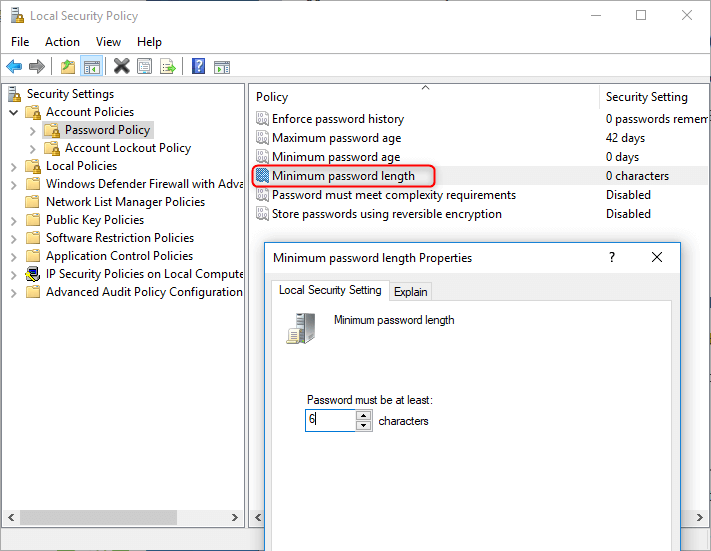
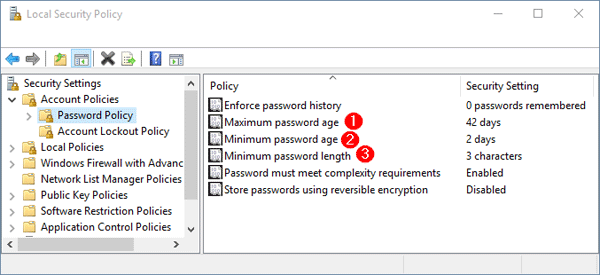
Note: The Minimum password age must be less than the Maximum password age, unless the Maximum password age is set to 0. - Minimum password length
Specify the least number of characters a password can have. You can set a value of between 1 and 14 characters, or set to 0 if you allow blank password. This policy can reject a user to set a short password that does not meet a minimum password length. For security reasons you’ll generally want passwords of at least six characters because long passwords are usually harder to crack than short ones. - Password must meet complexity requirements
If this policy is enabled, passwords must meet the following minimum requirements:- Be at least six characters long
- Contain a combination of at least three of the following characters: uppercase letters, lowercase letters, numbers, symbols (punctuation marks)
- Don’t contain the user’s user name or screen name
You can also change the password policy from an elevated Command Prompt. This is especially useful if you’re running Windows Home edition.
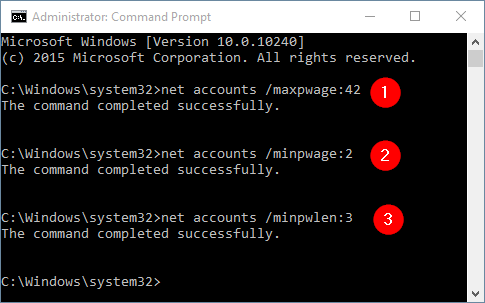
For example, if you want to change Maximum password age to 42 days, type the command:
net accounts /maxpwage:42
Set Minimum password age to 2 days, type:
net accounts /minpwage:2
Set Minimum password length to 3 characters, type:
net accounts /minpwlen:3
Change Account Lockout Policy
In the left pane of Local Security Policy Editor, expand Account Policies and then click Account Lockout Policy. In the right pane you see three policy settings. Double-click on the policy and you can change the setting to desired value.
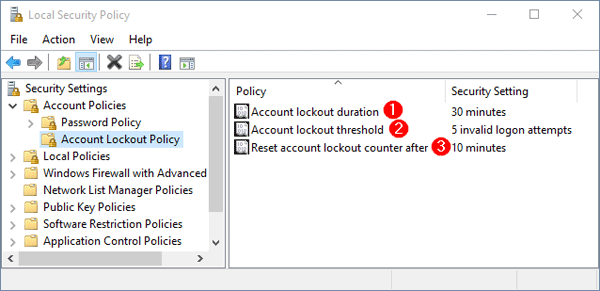
- Account lockout duration
Specify the number of minutes that a locked account remains inaccessible before it automatically becomes unlocked. You can set the account lockout duration between 1 and 99,999 minutes. If you set it to 0, then a locked out account will remain locked until an administrator manually unlocks that account. This policy has to set along with Account lockout threshold policy. - Account lockout threshold
Set the number of invalid logon attempts that are allowed before an account becomes locked out. The lockout threshold can be set to any value from 0 to 999. If the lockout threshold is set to zero, accounts will never be locked out due to invalid logon attempts. - Reset account lockout counter after
Specify the time (in minutes) that must elapse after a failed logon attempt before logon attempt counter is reset to 0. The available range is 1 minute to 99,999 minutes.Note: The Account lockout duration must be greater than or equal to the Reset account lockout counter after time.
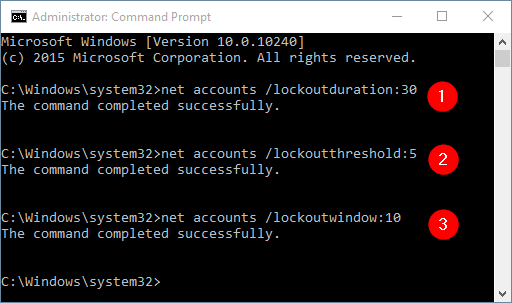
Here is how you can change the account lockout policy from an elevated Command Prompt.
For example, if you want to set Account lockout duration to 30 minutes, type:
net accounts /lockoutduration:30
Set Account lockout threshold to 5 bad logon attempts, type:
net accounts /lockoutthreshold:5
Set Reset account lockout counter after to 10 minutes, type:
net accounts /lockoutwindow:10
Change Local Security Policy by Exporting and Importing
How to copy local group policy objects from one machine to another? Is it possible to disable the “Password must meet complexity requirements” policy using Command Prompt? All these can be achieved by exporting & importing the local security policy. Here’s how:
- Open an elevated Command Prompt.
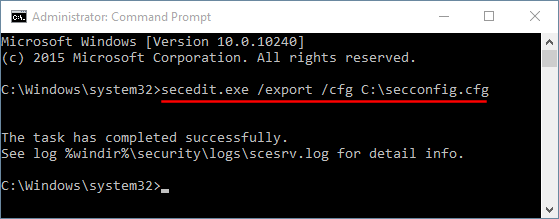
- Type the following command and press Enter. This will export all the settings of local security policy to a text file.
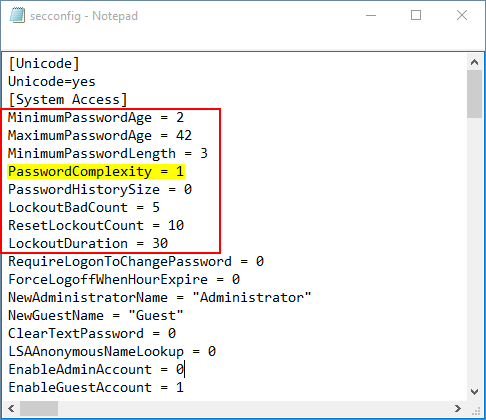
secedit.exe /export /cfg C:\secconfig.cfg - Open the C:\secconfig.cfg file with NotePad and you can view and modify the policy for your own purpose. For example, if you want to disable the password complexity requirements policy, just set the value PasswordComplexity to 0 and save your changes.
- Type the following command to import the local security policy from the file C:\secconfig.cfg. Of course, you can move the secconfig.cfg file to another computer and then import the policy.
secedit.exe /configure /db %windir%\securitynew.sdb /cfg C:\secconfig.cfg /areas SECURITYPOLICY - Restart your computer and the imported security policy will take effect.
- Previous Post: How to Turn on / off Adaptive Brightness in Windows 10 / 8
- Next Post: How to Restore Local Security Policy to Default in Windows 10, 8, 7, Vista and XP