The Microsoft Windows operating system records information about window viewing preferences — known as ShellBag information — in the Windows Registry.
It keeps track of several information such as the size, view mode, icon, access time and date, and position of a folder when a user uses Windows Explorer.
What makes Shellbag information interesting is the fact that Windows does not delete them when the folder gets deleted which means that the information can be used to prove the existence of folders on the system.
Forensics use the information for instance to keep track of which folders a user has accessed. It can be used to look up when a folder was last visited, modified or created on a system.
The information can also be used to display contents of removable storage devices that were connected to the computer in the past, and also information of encrypted volumes that were mounted on the system before.
Overview
Shellbags are created when a user visits a folder on the operating system at least once. This means that they can be used to prove that a user has accessed a particular folder at least once before.
Windows saves the information to the following Registry keys:
- HKEY_USERS\ID\Software\Microsoft\Windows\Shell\Bags
- HKEY_USERS\ID\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_USERS\ID\Software\Microsoft\Windows\ShellNoRoam
If you analyze the BagMRU structure you will notice many integers stored under the main key. Windows stores information about the recently opened folders here. Each item is related to a sub-folder on the system which is identified by binary date stored in those sub-folders.
The Bags key on the other hand stores information about each folder including its display settings.
Additional information about the structure are provided by a paper called «Using Shellbag information to reconstruct user activities» which you can download with a click on the following link: (Download Removed)
You can delete the Registry keys according to Microsoft to reset the settings for all folders:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\Bags
- HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\BagMRU
- HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags
On 64-bit systems additionally:
- HKEY_CURRENT_USER\Software\Classes\Wow6432Node\Local Settings\Software\Microsoft\Windows\Shell\Bags
- HKEY_CURRENT_USER\Software\Classes\Wow6432Node\Local Settings\Software\Microsoft\Windows\Shell\BagMRU
Afterwards, re-create the following keys:
- HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU
- HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags
On 64-bit systems additionally:
- HKEY_CURRENT_USER\Software\Classes\Wow6432Node\Local Settings\Software\Microsoft\Windows\Shell\Bags
- HKEY_CURRENT_USER\Software\Classes\Wow6432Node\Local Settings\Software\Microsoft\Windows\Shell\BagMRU
Software parsers
Software has been created to parse the information and display it in an easy to analyze way. There are quite a few programs available for that purpose. Some have been created to retrieve forensic evidence while others to clean the data for privacy.
Shellbag Analyzer & Cleaner is a free program by the makers of PrivaZer that can display and remove Shellbag related information.

You need to click on the analyze button to scan the system for Shellbag related information. The application displays all entries, existing ones and for folders that have been deleted, by default.
You can use the menu at the top to only display deleted folders, network folders, search results, existing folders or control panel and system folders.
Each entry is displayed with its name and path, the last time it was visited, its type, slot key in the Registry, creation, modification and access time and date, as well as windows position and size.
A click on clean displays options to remove specific types of information, but not individual entries, from the system. If you click on advanced options, you get additional features such as an option to overwrite the information, backup, or scramble the dates.
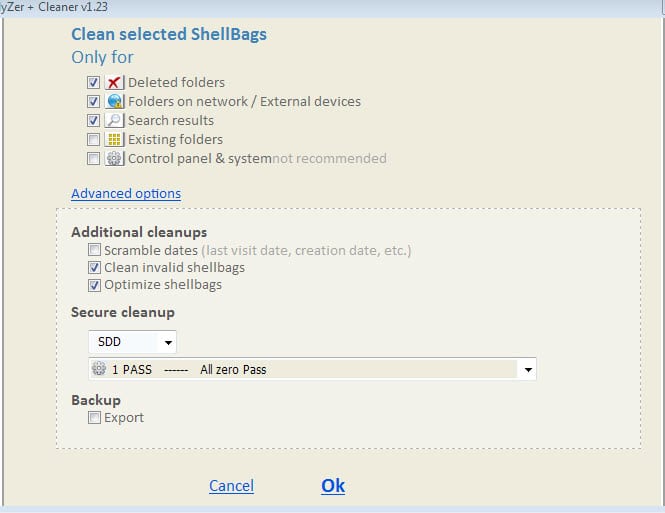
A success message is displayed in the end that informs you about the status of the operation.
Update: a new version of ShellBag Analyzer + Cleaner was released in April 2021. It introduced improved scans and scan speed, as well as an optimized user interface. End
Here are some alternatives that you can use instead:
- Shellbags is a cross-platform parser written in Python.
- Windows Shellbag Parser is a Windows console application
Summary
Article Name
How to remove old Shellbag entries in Windows
Description
How to remove Shellbag information from Windows to improve your privacy.
Author
Martin Brinkmann
Publisher
Ghacks Technology News
Logo
Advertisement
Создал рандомную папку по типу 999888777000, закинул туда различные файлы и поигрался с настройками. Затем сделал поиск в реестре название папки 999888777000. Выдало единственный результат в разделе:
BagMRU
HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU
Экспортировал весь раздел [по сути это мусорный раздел], изменял настройки папок, а затем импортировал раздел обратно. Результата не дало. Рядом с разделом BagMRU был еще раздел
Bags
HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags
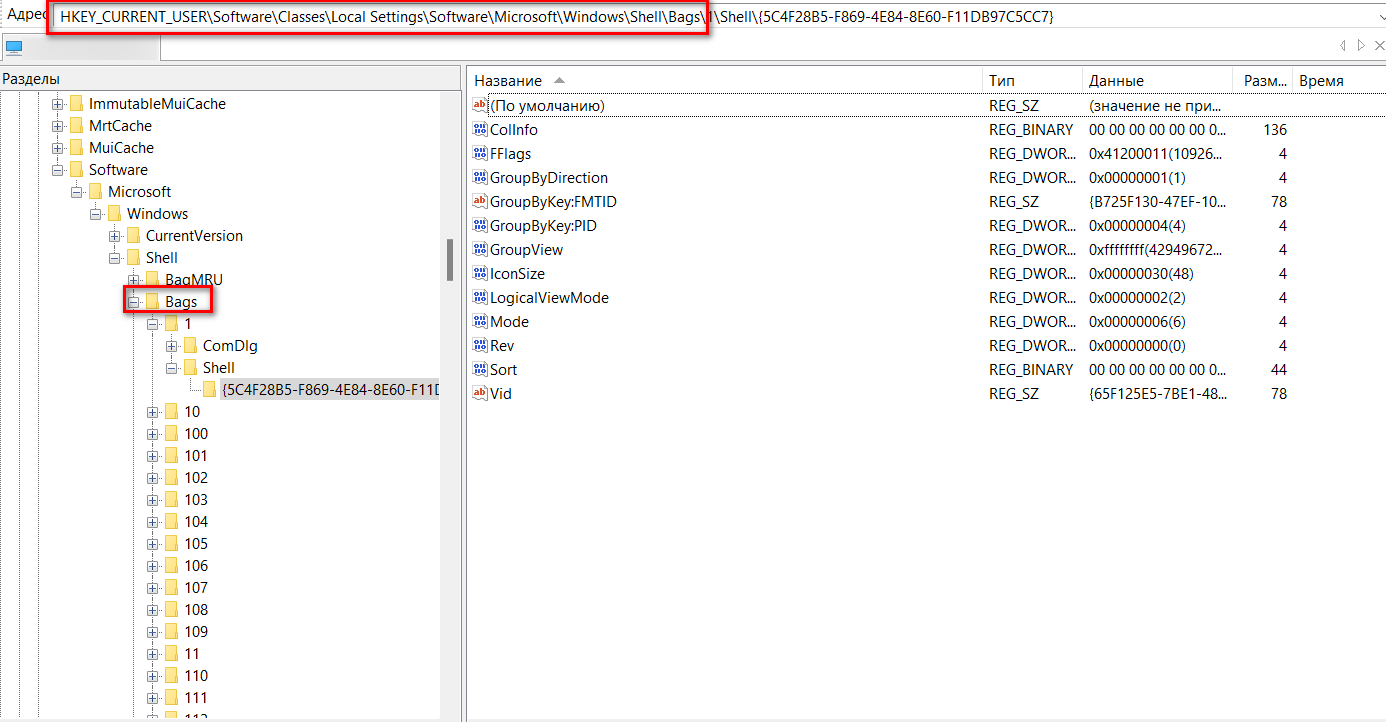
Глянул ключи в разделе и судя по их названию и значению это как раз то, что нужно. С этим разделом провернгул то же самое. Экспорт раздела, смена настроек папки, а затем импорт раздела. Сработало. Настройки всех папок хранятся в разделе Bags. Единственный недостаток в том, что невозможно узнать настройки конкретной папки и приходится сохранять весь раздел Bags целиком.
Скриншот
Windows DFIR notes are no longer maintained on InfoSec-Notes. Updated versions can be found on: .
Location (starting from Windows 7):
-
Files:
%SystemDrive%:\Users\<USERNAME>\NTUSER.dat%SystemDrive%:\Users\<USERNAME>\AppData\Local\Microsoft\Windows\UsrClass.dat -
Registry keys:
-
UsrClass.dat:HKCU\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRUHKCU\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags=> Information related to
Windows Exploreractivity. -
NTUSER.DAT:HKCU\Software\Microsoft\Windows\Shell\BagMRUHKCU\Software\Microsoft\Windows\Shell\Bags=> Information related to Desktop and Network Locations activity.
HKCU\Software\Microsoft\Windows\ShellNoRoam\BagHKCU\Software\Microsoft\Windows\ShellNoRoam\BagMRU=> Unclear usage and limited forensic research.
-
Yield information related to files and folders access.
The Shellbags are Windows Registry keys designed as an user experience enhancing feature to keep track of Windows explorer graphical display settings on a folder-by-folder basis. For instance, a Shellbag entry is used to store the View mode of a folder (details, list, small / medium / large icons) as well as the column displayed (entry names, dates, sizes, etc.) and their order.
Shellbags contain folders and network shares to which a given user has navigated (using the Windows Explorer), but not files or subdirectories if they were not accessed. An exception is for ZIP files opened directly as folders through the Windows Explorer, that are stored as if they were folders (with their content thus partially referenced depending on the related activity). Shellbags entries are also generated by access to the Control Panel settings, on an interface-by-interface basis. The Shellbags entries related to the Control Panel can notably be useful to detect possible Windows Firewall (Control Panel\All Control Panel Items\Windows Defender Firewall\Customize Settings) or Credential Manager (Control Panel\User Accounts\Credential Manager) operations.
Various kinds of user activity may generate or update Shellbag entries (with different level of data depending on the activity):
-
first access or renaming of folders, removable devices, or network shares through the
Windows Explorersystematically generate aShellbagentry -
graphical opening of compressed archives or
ISOs -
access to the
Control Panelinterface -
modification of the folder view preferences
Shellbag entries are stored in registry as a tree-like data structure, with the root target having the topmost BagMRU key. Each sub-target (sub directory for example) of the parent target are then represented with both:
-
A registry subkey, named with a numerical value (starting from
0). -
A registry value (in the parent target’s registry key), named with the same numerical value and associated with binary data that notably contains the target’s name.
Each Shellbag BagMRU registry key also contains a MRUListEx value, that maintains the entries visited order, i.e the order in which the sub targets of a target were accessed (the last sub target accessed having a MRU position of 0).
For example, My Computer will be associated with the topmost BagMRU key, C: to BagMRU\0 if it was access first, C:\Users to BagMRU\0\2 if it was accessed third, and so on and so forth. A hierarchical view of the Shellbag entries can thus be established.
As the Shellbags entries are stored in user’s specific registry hives, targets (folders, Control Panel interfaces, etc.) access can be tied to a given user through its Shellbags. Shellbags entries are populated only upon interaction (i.e are not prepopulated), the mere presence of a Shellbag entry for a target is thus evidence that the user interacted with the given target. Shellbags entries are not automatically deleted upon deletion of the related folders and can thus be a source of historical information.
The Shellbags entry for a given target yield the following information of forensic interest:
-
the target name and absolute path.
-
the target
Modified, Access, and Created (MAC)timestamps (UTC), retrieved from the$MFTat theShellbagentry creation (and not further updated). -
each entry in
ShellBagsBagMRUmaintain aMRUListExlist, which records the order in which the sub targets of a target were accessed (the last sub target accessed having aMRU positionof 0).
The first and last interacted timestamps can be indirectly deducted for some targets:
-
The
First Interactedtimestamp can be inferred for some targets thanks to the tree like data structure ofShellBagsentry. Indeed, for entries that do not have subkeys (i.e directory for which no subdirectory were accessed) theFirst Interactedtimestamp is equal to the key’sLastWriteTimetimestamp. This is due to the fact that the key is created when a target is first accessed, and further activity for that target (such as display settings modifications) will only update the key’s values. In such circumstances, theLastWriteTimetimestamp reflect the timestamp of the key initial creation (as it is not updated upon updates to a key’s values). When a subkey is created for the target (i.e when a subdirectory is accessed for that particular directory), the timestamp becomes unreliable as it reflect the creation of the subkey. -
The
Last Interactedtimestamp can be deducted for the sub target that was last interacted with. Indeed, as eachShellbagentry corresponds to a registry key, the key’sLastWriteTimetimestamp indicates when theShellbagentry was last updated. The child-bag / sub-target that was last interacted with being known (MRU positionof 0), this timestamp correspond to the last interaction timestamp for the sub target that was last interacted with.
Note however that major updates of the Windows operating system may result in modification of ShellBags entries, resulting in updated last written timestamp.
Eric Zimmerman’s ShellBagsExplorer.exe and SBECmd.exe tools (KAPE‘s SBECmd module) can be used to parse ShellBags entries.
ShellBagsExplorer.exe displays the ShellBags entries in a graphical user interface that allow browsing of the referenced targets, in a similar manner to Windows Explorer.
# Recursively enumerates the users' registry hives in the specified directory and parses their ShellBags entries.
SBECmd.exe --csv <CSV_DIRECTORY_OUTPUT> -d <C:\Users\<USERNAME> | C:\Users\ | DIRECTORY>
# Parses the ShellBags entries in the live registry.
SBECmd.exe --csv <CSV_DIRECTORY_OUTPUT> -lhttps://www.sans.org/reading-room/whitepapers/forensics/windows-shellbag-forensics-in-depth-34545
https://www.sans.org/blog/computer-forensic-artifacts-windows-7-shellbags/
https://lifars.com/wp-content/uploads/2020/04/LIFARS-WhitePaper-Windows-ShellBags-Forensics-Investigative-Value-of-Windows-ShellBags.pdf
Вы тут: Главная → Windows → Как отключить автоматическое упорядочивание файлов и папок в проводнике Windows 7
Вы настолько привыкли упорядочивать папки и файлы в проводнике перетаскиванием их на нужное место, что Windows 7 изменила вашу жизнь к худшему? Да, теперь везде, кроме рабочего стола, работает автоматическое упорядочивание файлов, для отключения которого в системе не предусмотрено настройки.
Честно говоря, я никогда не пользовался ручным упорядочиванием, и оно мне кажется тем более не нужным при наличии таких богатых возможностей сортировки и группировки в папках проводника Windows 7. Однако тем, кто привык работать с файлами и папками по-старинке и не желает переучиваться, это изменение портит немало крови.
Можно отключить автоматическое упорядочивание в проводнике, и ваш порядок файлов и папок будет запоминаться. На рисунках ниже видно, что ручное упорядочивание перетаскиванием файлов работает.
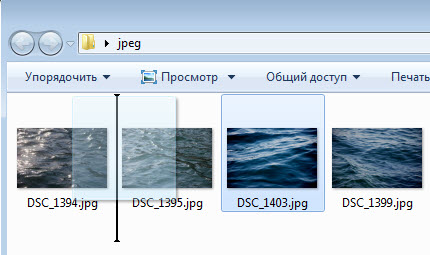
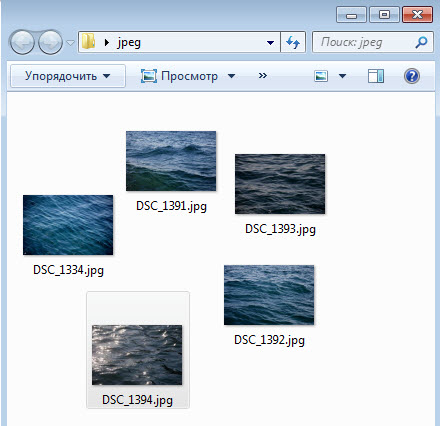
Вы даже можете включать и отключать упорядочивание в отдельных папках.
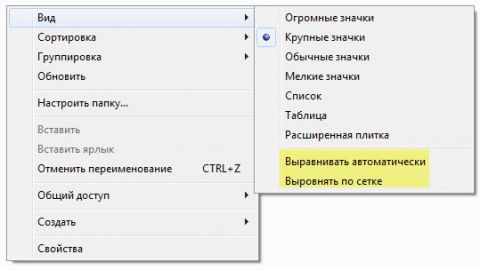
Увеличить рисунок
Но отключение автоматического упорядочивания сопряжено со следующими ограничениями:
- Автоматическое упорядочивание невозможно отключить в папках, входящих в библиотеки.
- В папках, не входящих в библиотеки, вид Плитка замещается видом Расширенная плитка, хотя внешние они аналогичны.
- Ручное упорядочивание не работает, если папка имеет вид Список.
- Если после отключения автоматического упорядочивания, вы переименуете или переместите папку, заданный вами вручную порядок сбросится. Нужно будет снова вручную упорядочить файлы, после чего проводник запомнит их порядок.
- В папке «Компьютер» не будет работать вид с индикаторами заполнения дисков.
- Если включена область предпросмотра, двойной щелчок по текстовому файлу переводит в режим переименования файла, вместо того, чтобы открыть его.
Не исключены и другие побочные эффекты. Если вы согласны на такие ограничения (а лучшего решения все равно пока не придумано), следуйте инструкциям ниже.
- Загрузите архив с двумя REG-файлами и распакуйте его.
- Запустите файл Disable_Auto_Arrange.reg и согласитесь на внесение изменений в реестр.
- Чтобы изменения вступили в силу, выйдите из системы и снова выполните вход.
Теперь вы можете упорядочивать файлы перетаскиванием.
Чтобы вернуть назад автоматическое упорядочивание, запустите файл Default _Folder _Views.reg и согласитесь на внесение изменений в реестр. Изменения вступят в силу после выхода из системы.
Возможность упорядочивания привносит параметр FFLags, который устанавливается для каждого из шаблонов вида папки.
Windows Registry Editor Version 5.00
;Отключение автоматического упорядочивания файлов в папках проводника
;Учтите ограничения /10971/
;Сброс вида папок
[-HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags]
; Отключение упорядочивания для шаблона "Общие элементы"
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7}]
"FFLAGS"=dword:43000000
"Mode"=dword:00000004
; Отключение упорядочивания для шаблона "Документы"
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\{7D49D726-3C21-4F05-99AA-FDC2C9474656}]
"FFLAGS"=dword:43000000
"Mode"=dword:00000004
; Отключение упорядочивания для шаблона "Музыка"
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\{94D6DDCC-4A68-4175-A374-BD584A510B78}]
"FFLAGS"=dword:43000000
"Mode"=dword:00000004
; Отключение упорядочивания для шаблона "Изображения"
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\{B3690E58-E961-423B-B687-386EBFD83239}]
"FFLAGS"=dword:43000000
"Mode"=dword:00000004
; Отключение упорядочивания для шаблона "Видео"
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\{5FA96407-7E77-483C-AC93-691D05850DE8}]
"FFLAGS"=dword:43000000
"Mode"=dword:00000004
Трудно сказать, кто раскопал это первым, но похоже, что это был мой коллега MVP Ramesh Srinivasan. Он разбирался с твиком выделения только имени файла или папки в проводнике (вместо выделения целой строки), а отключение автоматического упорядочивания явилось побочным эффектом этого твика. К сожалению, он не обозначил и половины проблем и ограничений, которые я перечислил выше (их пришлось собирать из разных источников, в том числе и по результатам вопросов на OSZone).
Оригинал статьи находится здесь.
The settings for desktop icon placement in Windows XP (or Vista) are located in the the
HKCU\Software\Microsoft\Windows\Shell\Bags\1\Desktop registry key.
This registry key contains a number of values, the most relevant if
which are the ItemPos<screenresolution> values, the Sort value and
the FFlags value.
The sort value controls the sort order of the icons (by name, by
type, by size etc.), the FFlags value controls the arrangement of the
icons (align to grid, auto align etc.)
Finally there may be any number of ItemPos values (appended with
different screen resolutions eg. ItemPos800x600), which control the user
defined positions of the icons for different screen resolutions.
For more details about the content of HKCU\Software\Microsoft\Windows\Shell values:
ShellBagsView v1.05
Regarding the Icon view used for any folder of one’s choosing, I believe the position of icons would be stored in:
HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags\[x]\Shell\{yyyyyyy-yy...}\ItemPoswith ‘x’ representing one of your many folder specific settings.
Добавлю, также, что в Microsoft Windows NT Resource Kit tools есть расширение shell для сохранения и восстановления иконок десктопа, см. здесь.
