Domain controllers are a vital part of your network. To protect them you should make sure that the firewall is enabled and only the required ports for your Domain Controller are opened. But which ports are those?
The primary function of the domain controller is of course the Active Directory. For the clients to be able to communicate with the AD, some ports need to be opened in the firewall.
In this article, we will look at which ports are required for the domain controller.
The Windows firewall is configured automatically when you install a new Domain Controller. All the required ports for your Active Directory are added automatically. But when you for example want to segment your network with VLANs, then you will need to make sure that the correct ports are open between your domain controller and clients.
Let’s first take a look at the ports that you need to open on your domain controller:
| Port | Protocol | Service |
|---|---|---|
| 53 | TCP/UDP | DNS |
| 88 | TCP/UDP | Kerberos authentication |
| 123 | UDP | W32Time |
| 135 | TCP | RPC Endpoint Mapper |
| 137/138 * | UDP | NetBIOS |
| 139 * | TCP | NetBIOS |
| 389 | TCP/UDP | LDAP |
| 445 | TCP | SMB |
| 464 | TCP/UDP | Kerberos password change |
| 636 | TCP | LDAP SSL |
| 9389 | TCP | Active Directory Web Services (ADWS) |
| 3268/3269 | TCP | LDAP Global Catalog / LDAP GC SSL |
| 49152-65535 | TCP | RPC Ephemeral Ports |
* If you are running Windows 2012 or higher, then the NetBIOS ports are not required anymore. Netbios is replaced with SMB (Samba).
If you plan to use the Active Directory PowerShell module or the Active Directory Administrative Center, then you will need to make sure that port 9389 is opened as well.
Tip
Make sure you checkout my Domain Controller Health reporting script as well.
The RPC Port range of 49152-65535 is needed for the communication between the clients and the domain controller. The port number is randomly assigned to the client. It’s possible to limit the range through a registry key, but it’s really not recommended to do this because it might break more than you want.
Port 53 – DNS
Domain Name System (DNS) communication takes place over TCP and UDP port 53. DNS resolution is critical for domain controller location and name resolution.
Port 88 – Kerberos
Kerberos is an authentication protocol used by Windows. It operates on TCP and UDP port 88. It’s essential for secure authentication within the domain.
Port 123 -W32Time
While not directly related to domain controller operations, port 123 plays a crucial role in maintaining the synchronization of time across a network. Accurate timekeeping is essential in IT environments, especially in Active Directory, as it ensures consistent and secure authentication and access control.
Port 135 – RPC Endpoint Mapper
Port 135 is a critical client/server port used by numerous Microsoft services. In this process, the client initially connects to the RPC mapper service on port 135 to determine the dynamic port range on which the desired service is listening. The RPC mapper then responds with the port information, allowing the client to establish a connection.
Port 389 – LDAP
Lightweight Directory Access Protocol (LDAP) operates on TCP and UDP port 389. It’s used for basic LDAP queries and directory updates. LDAP is the backbone of Active Directory, facilitating user authentication and directory lookups.
Port 445 – SMB
Port 445 is used for the SMB Protocol. It’s used by the Active Directory to get GPO information. Besides that, the protocol is also used for file and printer sharing.
Port 464 – Kerberos Password Change
This port is used for Keberos password changes and resets. When a user needs to change their password, the request is sent over port 464 to the Key Distribution Center on the domain controller.
Port 636 – LDAP
For enhanced security, LDAPS (LDAP over SSL) operates on TCP port 636. LDAPS encrypts the data transmitted between domain controllers, safeguarding sensitive information.
Port 3268/3269 – LDAP Global Catalog
The ports 3268 and the secure version 3269 (which uses SSL) are used for querying the LDAP Global Catalog.
Port 49152-65535 – RPC Ephemeral Ports
A port in this range is allocated to the client after the initial contact with the RPC Mapper on port 135.
ADFS Ports
If you are using Active Directory Federations Services (ADFS), then you will need to make sure that the following ports are open as well:
| Port | Protocol | Service |
|---|---|---|
| 80 | TCP/UDP | HTTP |
| 443 | TCP/UDP | HTTPS |
| 5985 | TCP/UDP | WinRM Listener |
| 49443 | TCP | Active Directory Federations Services (ADFS) |
Port 5985 is needed when using Azure AD Connect or Federation/WAP servers. Port 49443 is needed for ADFS when using certificate-based authentication.
Wrapping Up
The Windows Firewall on your domain controller is configured correctly by default when you install the Active Directory services. If you are using a third-party firewall on your domain controller, or planning to use VLANs, then you will need to make sure that the listed ports are opened.
As mentioned, NetBIOS ports are not really needed anymore, so it’s better to block them if you don’t have any apps that use them.
I hope you found this article helpful, if you have any questions, just drop a comment below.
Complete List of Active Directory Ports and What They Do Explained. In this article we will firstly introduce what is Active Directory (AD) is and how it functions.
What is Active Directory (AD)?

Active Directory is a combination of services and databases that connect end users with the network resources needed to get the job done. The database, also called the Directory, contains essential information about the network ecosystem, including details about the users and computers and their respective system rights.
To explain it in simple terms, if a directory has a list of 1000 user accounts with details like personal phone number, job title, and password, it will also record each individual system’s rights and permissions.
Active Directory predominantly controls most of the activity that goes on in an IT ecosystem. AD makes sure that every user who enters the environment is the person they claim to be (authentication) by checking their user ID and password and allowing them to access only those data for which they have the rights (authorization).
How Does Active Directory Work?
The primary Active Directory service is Active Directory Domain Service (AD DS), and it is a part of the Windows Server operating system. The servers running the AD DS are called Domain Controllers (DCs). Every organization usually has many domain controllers and every DC would have a replica of the Directory for the entire domain.
If there is a change in the Directory on one domain controller, it is replicated to the other DCs as well so that they all stay up to date. You can include laptops, desktops and other systems running Windows (other than Windows Server) in the Active Directory environment. However, these devices do not run Active Directory Domain Service.
Active Directory Ports
Active Directory functions under the Local Security Authority Server Service- Lsass.exe method and contains the replication and authentication engines for Windows Domain Controllers. Client computers, domain controllers and application servers need network connectivity for Active Directory on particular hard coded ports. Furthermore, if there is no tunneling protocol to contain traffic to Active Directory, a series of transitory TCP ports between 1024 till 5000 and 49152 till 65535 are needed.
Active Directory correspondence involves a lot of ports and someone working as a system administrator would know about a few of them. Enterprises need Active Directory for workstation and server management, group policy management, authentication, etc. A complete list of Active Directory Ports and their functions, including services used by Microsoft clients and server operating systems are listed below.
The server products from Microsoft use a variety of protocols and network ports to connect with the client systems and various other server systems within the network. Also ensure you have implemented Active Directory security best practices.
| Application Protocol | Protocols | Ports |
|---|---|---|
|
Active Directory Web Services (ADWS) |
TCP |
9389 |
|
Active Directory Management Gateway Service |
TCP |
9389 |
|
Global Catalog |
TCP |
3269 |
|
Global Catalog |
TCP |
3268 |
|
ICMP |
– |
No Port Number |
|
Lightweight Directory Access Protocol (LDAP) Server |
TCP |
389 |
|
Lightweight Directory Access Protocol (LDAP) Server |
UDP |
389 |
|
Lightweight Directory Access Protocol Server (SSL) |
TCP |
636 |
|
IPsec ISAKMP |
UDP |
500 |
|
NAT-T |
UDP |
4500 |
|
RPC |
TCP |
135 |
|
RPC randomly allocated high TCP ports |
TCP |
1024 – 5000 |
|
SMB |
TCP |
445 |

with Infra SOS
AD Important Ports
- If your computer system network environment uses Windows Server 2008 and later versions (2012, 2016, 2019, 2022) Microsoft Windows have increased the dynamic client port range for outgoing connections. The new default start port is 49152, and the default end port is 65535 so you should enable network connectivity over the highest port range of 49152 to 65535.
- If your computer system network environment Windows Server 2008, Windows Server 2008 R2, Windows Vista, or Windows 7 along with Windows version that came earlier or before Windows Server 2008 and Windows Vista, then you must use connectivity over two port ranges, Lowest port range from 1025 to 5000 and highest port range from 49152 to 65535
- If your computer system network environment uses only versions that came earlier or before Windows Server 2008 and Windows Vista, then you should use network connectivity over the lowest port range from 1025 to 5000.
A summarized result would consist of a VPN gateway situated next to a filtering router that opts for the Layer 2 Tunneling Protocol (L2TP) along with IPsec. Under this summarized condition, you should allow the below mentioned items through the router rather than opening all the protocols and ports listed.
- IPsec Encapsulating Security Protocol (ESP) (IP protocol 50)*
- IPsec Network Address Translator Traversal NAT T (UDP port 4500)*
- IPsec Internet Security Association and Key Management Protocol (ISAKMP) (UDP port 500)*
Additionally, the Microsoft LDAP client enforces ICMP pings to authenticate that an LDAP server has a pending request present in the server network. The below mentioned settings are LDAP session points:
- PingKeepAliveTimeout = 120 seconds (the amount of time it would hold after the last response before resending the ping)
- PingLimit = 4 (the number of pings that are sent before closing the connection)
- PingWaitTimeout = 2000 ms (the amount of time it waits for ICMP to respond)
What’s more, if need be, you may hard code the port that you require for Active Directory replication by following Restricting Active Directory RPC Traffic to one particular port. The system service nomenclature is LSASS.
Active Directory ports client to domain controller
The communications of Active Directory take place using multiple ports. These ports in question are required by both Domain Controllers and Client Computers. For example, whenever a client computer searches for a domain controller, it sends a DNS Query over Port 53 to find the domain controller name within the domain.
Mentioned below is the list of ports for Active Directory communication and their services:
- UDP Port 88 for Kerberos authentication.
- UDP and TCP Port 135 for the client to domain controller operations and domain controllers to domain controller operations.
- TCP Port 139 and UDP 138 are used for File Replication Service between domain controllers.
- UDP Port 389 for LDAP to handle regular queries from client computers to domain controllers.
- TCP and UDP Port 445 for File Replication Service.
- TCP and UDP Port 464 for Kerberos Password Change.
- TCP Port 3268 and 3269 for Global Catalog from client to domain controller.
- TCP and UDP Port 53 for DNS from domain controller to domain controller and client to the domain controller.
Active Directory will be enabled to function properly by opening the above mentioned ports between domain controllers or between domain controllers and client controllers in Firewall.
How Secure is Your Active Directory ?
78% of companies have an insecure Active Directory and are vulnerable to a potential attack!!
Download our FREE Active Directory Security Best Practices Compliance Checker
Ports, Protocols Required For Checking Active Directory, Group Policy And Exchange
| Port | Protocol | Target | What They Do |
|---|---|---|---|
|
389 |
TCP |
Domain Controllers |
LDAP Common Queries |
|
3268 |
TCP |
Domain Controllers |
LDAP, Group Membership, GC Search |
|
3269 |
TCP |
Domain Controllers |
Global Catalog LDAP over SSL |
|
88 |
TCP/UDP |
Domain Controllers |
Kerberos Authentication |
|
135, 1024 – 65535 |
TCP |
Domain Controllers |
Windows Management Instrumentation |
|
445 |
TCP |
Domain Controllers |
Authenticated communication between Server and Domain Controllers |
|
53 |
UDP |
DNS Server |
DNS Client |
|
135 and 1024 – 65535 |
TCP |
Exchange Server |
Windows Management Instrumentation., Retrieve Exchange Server configuration settings |
|
5985, 5986 |
TCP |
Exchange Server |
Windows Remote Management, PowerShell Connections: 5985 – For HTTP |
|
80, 443 |
TCP |
Exchange Server |
PowerShell Connections |
Active Directory Domain Controller Communication Ports List
Below are the additional Active Directory Ports that are used for Active Directory communications:
- TCP, UDP port 135: RPC (Remote Procedural Call)
- TCP, UDP port 137: NetBIOS name service
- UDP port 138: DFSN, NetBIOS Datagram Service, NetLogon
- TCP port 139: DFSN, NetBIOS Session Service, NetLogon
- TCP, UDP port 389: LDAP
- TCP port 636: LDAP SSL
- TCP, UDP port 445: SMB, NetLogon, SamR
- TCP, UDP port 1512: WINS Resolution
- TCP, UDP port 42: WINS Replication
- TCP Dynamic: RPC, DCOM, NetLogonR
Active Directory Replication Ports
The ports given below are used for Active Directory Replication.
- TCP port 135: RPC (Remote Procedure Call)
- TCP, UDP port 389: LDAP
- TCP, UDP port 636: LDAP SSL
- TCP 3268 port: Global Catalog LDAP
- TCP 3269 port: Global Catalog LDAP SSL
- TCP, UDP port 53: DNS
- TCP, UDP port 88: Kerberos
- TCP port 445: SMB
Active Directory Authentication Ports
The below mentioned ports are used for Active Directory authentication:
- UDP port 389: LDAP
- TCP port 53: DNS
- TCP, UDP port 88: Kerberos
- TCP, UDP port 445: SMB over IP
Active Directory Errors
With Active Directory ports, you can understand which ports to allow in the firewall. If the ports are not configured in the firewall, it could lead to blocking requests in Active Directory communications.
There are certain common problems that Active Directory ports face. They are:
- Replication traffic is unsuccessful on port 3268, or there could be some other issues with replication.
- LDAP is unable to authenticate users while using LDAPS over SSL.
- Kerberos is unable to authenticate users while using TGS over SSL.
- Replication fails to perform over port 3268.
- LDAP fails to authenticate users while using LDAP over SSL.
An Active directory port could either be a TCP or a UDP port that services Active Directory Domain Controller for requests. Active Directory Domain Controllers (DCs) use the various ports mentioned above for data transfer and communication. The most common protocols used are:
- LDAP
- Kerberos
- RPC
- DNS
- SMB over IP
Depending upon the requirements, a system administrator can configure which port needs to be opened.
The Ephemeral Ports
Also known as service response ports, Ephemeral ports are very important for communications. These ports are established dynamically for sessions response to each client that establishes a session. The client is not restricted to Windows OS only. It could be Linux and Unix as well. Once the sessions are dissolved, the ports are reinstated back into the pool for reuse.
The following chart tells you what the Ephemeral ports are based on the Operating System in use and what they do.
| Operating System | Ports And Protocols | What they Do |
|---|---|---|
|
Windows 2003 and new versions |
TCP and UDP 1024 – 5000 |
Ephemeral Dynamic Service Response Ports |
|
Windows 2008 and newer versions |
TCP and UDP 49152 – 65535 |
Ephemeral Dynamic Service Response Ports |
|
TCP Dynamic Ephemeral |
RPC, DCOM, EPM, DRSUAPI, NetLogonR, SamR, FRS |
Replication, Computer and User Authentication, Group Policy, Trusts |
|
UDP Dynamic Ephemeral |
DCOM, RPC, EPM |
Group Policy |
Port Requirements RODC — Read Only Domain Controllers
| Traffic | Type Of Traffic |
|---|---|
|
UDP 53 DNS |
DNS |
|
TCP 53 DNS |
DNS |
|
TCP 135 |
RPC, EPM |
|
TCP Static 53248 |
FRsRPc |
|
TCP 389 |
LDAP |
|
TCP and UDP Dynamic |
Ephemeral Ports |
|
TCP and UDP Dynamic |
Ephemeral ports |
Restricting Access To Ports Across A Firewall
You can restrict the Domain Controller to Client communications and Domain Controller to Domain Controller traffic to certain specific ports. It all depends on what service and ports you want to have restricted access to. When selecting this option, you must be particular about the correct ports for the exemplary service.
1. Method A
This method is used to set the particular AD replication port. It uses the dynamic port to replicate data from one Domain Controller site to another as a standard process. It is applicable for restricting AD replication to a specific port group.
Procedure: Modify registry to select a static port.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
Applies to: all supported versions of Windows Server
Restricting Active Directory replication traffic and client RPC traffic to a specific port
http://support.microsoft.com/kb/224196
2. Method B
This method is used for configuring the port range within the Windows firewall. The default dynamic port range for IP/TCP has been changed from Windows Server 2008
Netsh – use the following examples to set a starting port range, and number of ports after it to use
netsh int ipv4 set dynamicport tcp start=10000 num=1000
netsh int ipv4 set dynamicport udp start=10000 num=1000
The default dynamic port range for TCP/IP has changed from Windows Vista and in Windows Server 2008 and also Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows 10 – all editions
http://support.microsoft.com/kb/929851
3. Modify the registry
Modification of registry is for Windows services communication. It also affects Active Directory communications.
HKEY_LOCAL_MACHINE\Software\Microsoft\Rpc
How to configure RPC dynamic port allocation to work with firewalls
http://support.microsoft.com/kb/154596/en-us
Complete List of Active Directory Ports and What They Do Explained Conclusion
Now that you read about what Active Directory Ports are and what they do, it is essential to implement the ports with a complete understanding of the technology. Active Directory is dependent on multiple communication services to communicate between Domain Controller and client computers. Understanding how AD communicates can be critical when working with Domain Controllers and client computers separated by routers or firewalls.
In this post, I will explore the TCP and UDP ports used by Active Directory from client to server.
I will use WireShark and a series of tests to determine what ports are used.
Tests I’ll be running:
- Ports Used When a User Logs into a Computer
- Ports used when running gpupdate
- Ports used when joining a computer to the domain
- Ports Used When Rebooting
Test Environment:
- Server 2022 with IP 192.168.100.10 (Active Directory Server)
- Windows 10 Pro with IP 192.168.100.20
- Wireshark is installed on the Active Directory server
- The Active Directory server is a default install
Here is a list of ports used by Active Directory by a default install. This is between the domain controller and a domain-joined computer.
- TCP 135 Microsoft RPC
- TCP/UDP 49152 – 65535 RPC Dynamic Ports
- TCP 88 Kerberos
- TCP 389 LDAP
- UDP 53 DNS
- TCP 445 SMB
TCP 135 Microsoft RPC Mapper
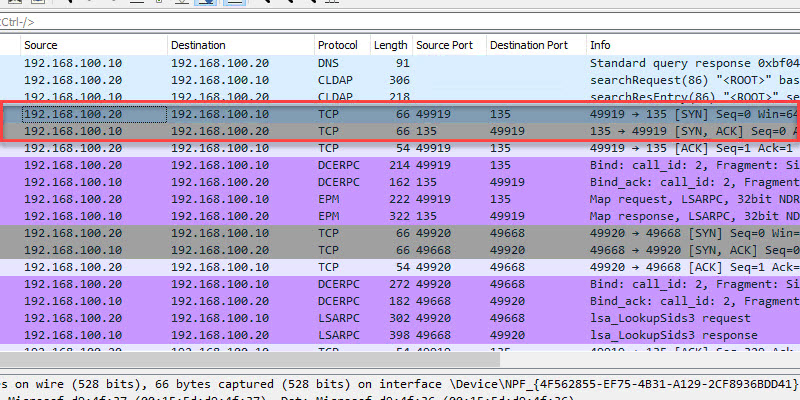
- Description: Port 135 is a critical client/server port. This port is used by many Microsoft services and should not be blocked by a firewall. First the client connects to the RPC mapper service (port 135) and asks the mapper what port a given service is listening on (which will be a dynamic port range… see below). The RPC mapper responds to the client with the port and then the client connects to that port. You can see this in the above screenshot.
- Firewall: Allow between client and server. Port 135 should not be exposed to the internet.
TCP/UDP 49152 – 65535 RPC Dynamic Ports
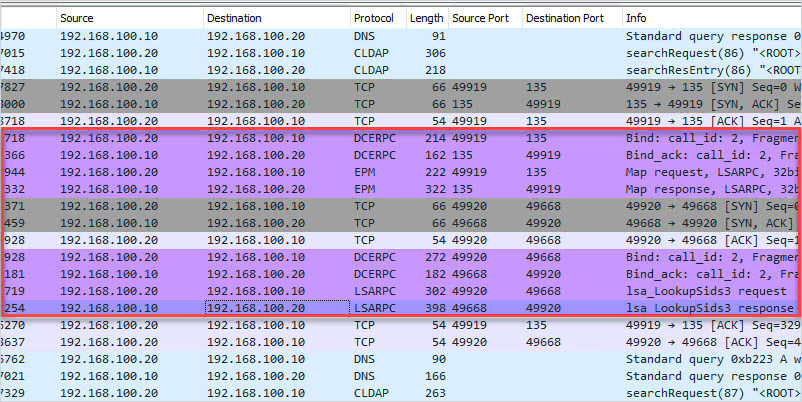
- Description: The dynamic port range is used by various server applications. RPC dynamic port allocation instructs the RPC program to use a particular random port in the range configured for TCP and UDP, based on the implementation of the operating system used. The RPC mapper (port 135) is used to connect clients to services running on these dynamic ports.
- Firewall: Allow between client and server. This port range should not be exposed to the internet.
we recommend that you reconfigure the firewalls to allow traffic between servers in the dynamic port range of 49152 through 65535. This range is in addition to well-known ports that are used by services and applications.
https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/default-dynamic-port-range-tcpip-chang
TCP 88 Kerberos
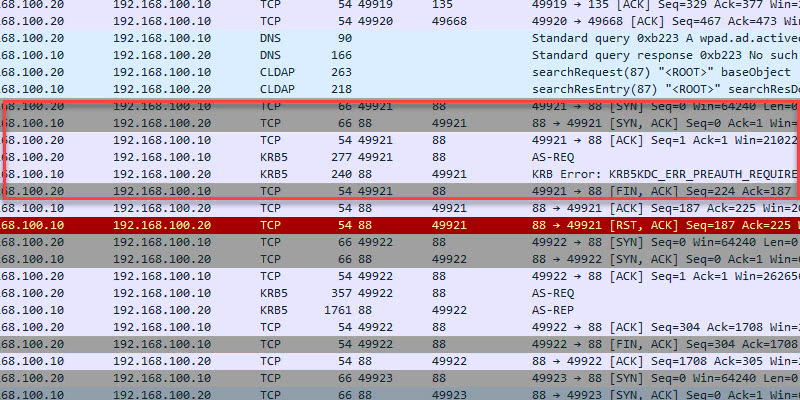
- Description: Kerberos is an authentication protocol that authenticates requests between a client and server in a secure manner. This is Microsoft Window’s default authentication method for domain-joined devices.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
TCP 389 LDAP
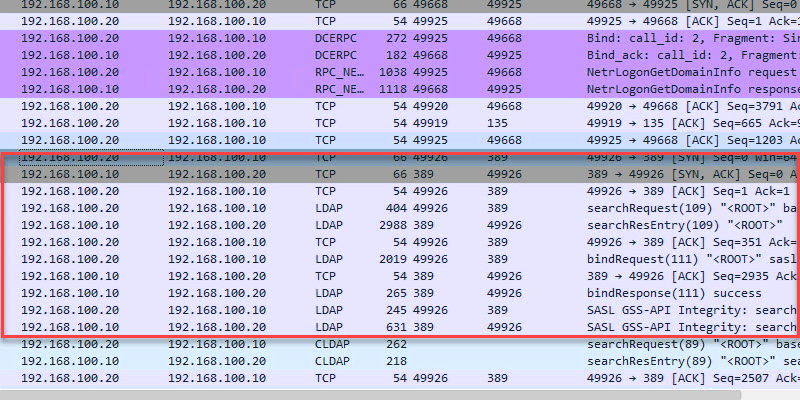
- Description: LDAP is a directory access protocol. This protocol is used to search, add/delete, authenticate and modify data in a Directory Server such as Active Directory.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
UDP 53 DNS
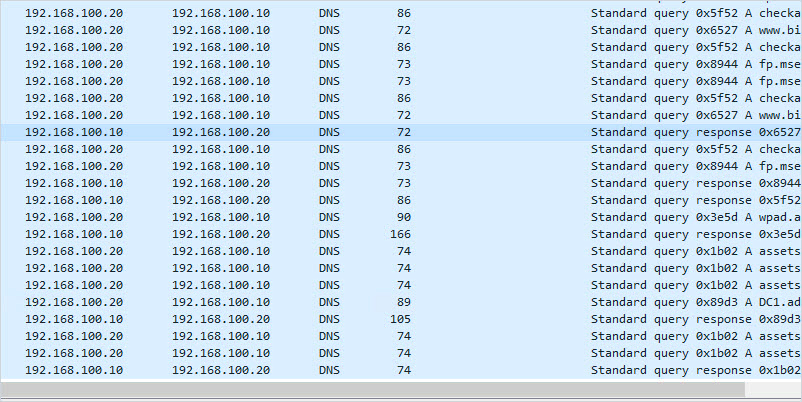
- Description: DNS is a critical service used to map IP addresses to host names. This is a critical service used by clients to locate resource records in the domain and lookup external domain names.
- Firewall: Allow between client and server. If DNS is running on your Active Directory server I do not recommend exposing it to the internet.
TCP 445 SMB
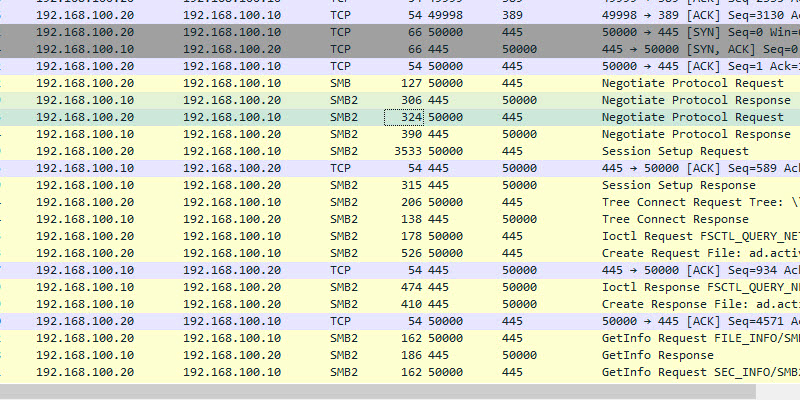
- Description: Server message blocks (SMB protocol) is a client-to-server communication protocol used for accessing files, printers, and data on a network. This port is used during startup to get GPO information, it is also used when running the gpupdate command.
- Firewall: Allow between client and server. Do not expose this port to the internet.
Ports Used When a User Logs into a Domain-Joined Computer
In this example, I will log into computer PC1 (192.168.100.20) and capture the network packets from the domain controller.
Here is a conversation view of the TCP/UDP ports used. This is traffic sent from the client to the domain controller and destination ports.
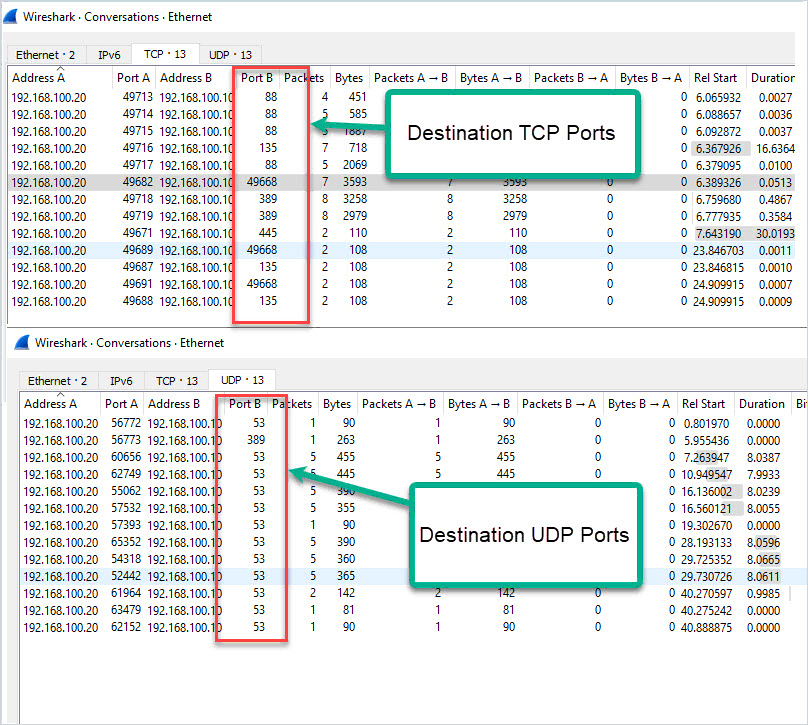
Here is a summary of the destination ports used by the client.
- TCP 88 (Kerberos)
- TCP 135 (Microsoft RPC)
- TCP 389 (LDAP)
- TCP 445 (Microsoft DS)
- TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
- UDP 53 (DNS)
- UDP 389 (LDAP)
Ports Used When Running Gpupdate
While logged into the client PC I will run the gpupdate command to see what ports are used.
Results below. It Looks like TCP port 445 is used the most when running a gpupdate.
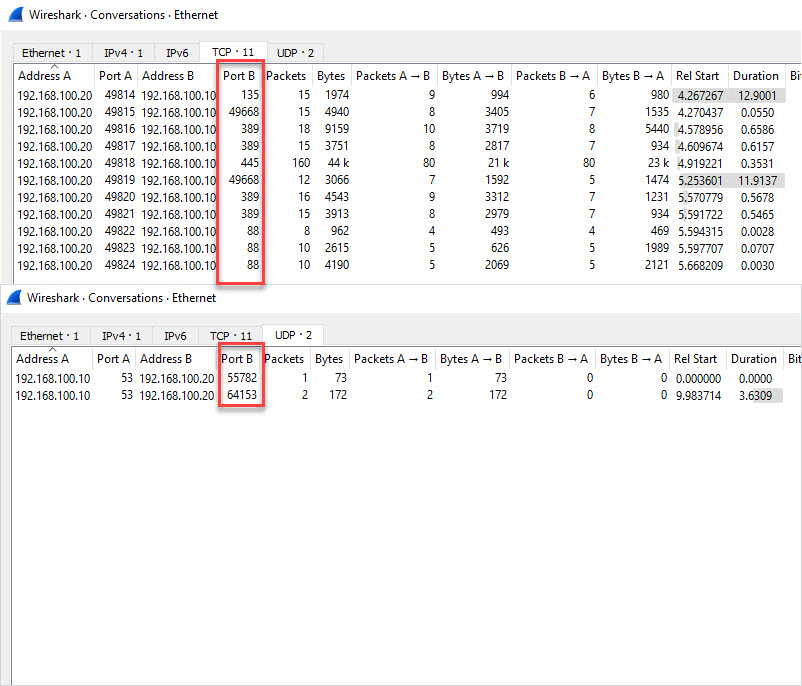
Ports Used When Joining a Computer to The Domain
This looked similar to the other packet captures.
TCP 88 (Kerberos)
TCP 135 (Microsoft RPC)
TCP 389 (LDAP)
TCP 445 (Microsoft DS)
TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
UDP 53 (DNS)
Ports Used When Rebooting
Nothing new, I see the same ports used when compared to the other packet captures.
Hopefully, this guide helps you to understand the ports used between a client and an Active Directory server. Keep in mind this test was a default domain controller install with no additional services running, the more services you install the more ports that may be used.
Resources:
- Service overview and network port requirements for Windows
- Service Name and Transport Protocol Number Registry
In an Active Directory (AD) environment, Domain Controllers (DCs) must communicate over a variety of ports to provide services such as authentication, replication, and management. Properly configuring network firewalls to allow these ports is critical to ensure the domain operates smoothly without disruptions.
This post outlines all the required ports for Domain Controllers to function correctly in a secure and reliable AD environment.
Key Services and Associated Ports
A Domain Controller performs several critical functions, including Kerberos authentication, LDAP queries, replication, and more. Below is a list of key services and the ports required for them:
1. Kerberos Authentication (UDP/TCP 88)
Kerberos is the authentication protocol used by Active Directory to verify the identity of users and services. It uses port 88 for both UDP and TCP.
- Service: Kerberos
- Port: UDP/88, TCP/88
- Description: Used for authentication requests.
2. LDAP (TCP/UDP 389)
The Lightweight Directory Access Protocol (LDAP) is used for querying and modifying directory services. It operates on port 389 for unencrypted connections.
- Service: LDAP
- Port: TCP/389, UDP/389
- Description: Used for directory queries and modifications.
3. LDAP over SSL (LDAPS) (TCP 636)
LDAP over SSL (LDAPS) is used when securing LDAP communications with SSL encryption. This ensures the confidentiality and integrity of LDAP queries.
- Service: LDAPS
- Port: TCP/636
- Description: Secured LDAP communications over SSL.
4. Global Catalog (TCP 3268, 3269)
The Global Catalog (GC) is a distributed data repository used by AD for searching objects across domains. It runs on port 3268 for unencrypted traffic and 3269 for encrypted (SSL) traffic.
- Service: Global Catalog
- Port: TCP/3268 (unencrypted), TCP/3269 (SSL)
- Description: Provides search functionality across multiple domains in the forest.
5. SMB over TCP (TCP 445)
Server Message Block (SMB) is used for file sharing and other communications in a Windows environment. Domain Controllers use SMB for various administrative tasks, including Group Policy replication.
- Service: SMB
- Port: TCP/445
- Description: File sharing and other administrative tasks.
6. RPC Endpoint Mapper (TCP 135)
The Remote Procedure Call (RPC) Endpoint Mapper listens on port 135 and helps clients locate the service they need, such as Active Directory replication and management tasks.
- Service: RPC Endpoint Mapper
- Port: TCP/135
- Description: Used to map RPC services and endpoints.
7. DNS (TCP/UDP 53)
Domain Name System (DNS) is critical in AD environments for resolving domain names to IP addresses. DNS traffic typically operates on port 53.
- Service: DNS
- Port: TCP/53, UDP/53
- Description: Used for DNS queries and zone transfers.
8. Replication (RPC over TCP 135, 49152-65535)
AD replication uses RPC over TCP, with the RPC Endpoint Mapper assigning the port dynamically between 49152 and 65535.
- Service: AD Replication
- Port: TCP/135, Dynamic ports 49152-65535
- Description: Active Directory replication services between Domain Controllers.
9. NetBIOS (UDP 137, 138; TCP 139)
NetBIOS is an older protocol that is still required for some legacy services and communication, particularly in environments running older systems.
- Service: NetBIOS Name Service, Datagram Service, Session Service
- Port: UDP/137 (Name Service), UDP/138 (Datagram Service), TCP/139 (Session Service)
- Description: NetBIOS over TCP/IP services.
10. NTDS RPC (TCP 135)
This port is used for Active Directory management and replication over RPC (Remote Procedure Call). It is required for Domain Controllers to communicate with each other.
- Service: NTDS RPC
- Port: TCP/135
- Description: Used for AD replication and management tasks.
Optional Ports for Additional Services
If your Domain Controller is also providing additional services, such as Windows Time Service (W32Time) or certificate services, you will need to open the following ports:
11. W32Time (UDP 123)
The Windows Time Service (W32Time) ensures that all systems in an Active Directory forest have synchronized time. Time synchronization is crucial for Kerberos authentication.
- Service: W32Time
- Port: UDP/123
- Description: Time synchronization across the domain.
12. Certificate Services (TCP 443, 9389)
If your Domain Controller is also hosting a Certification Authority (CA) for issuing certificates, ports 443 (HTTPS) and 9389 are required for certificate enrollment.
- Service: Certificate Services
- Port: TCP/443, TCP/9389
- Description: Used for Certificate Authority services.
Conclusion
For proper functionality, Domain Controllers must communicate over specific ports to handle tasks such as authentication, replication, and DNS resolution. Ensuring that these ports are open and accessible across your network will prevent issues with AD services, such as authentication failures or replication delays.
While it’s essential to secure these ports using firewalls and access controls, understanding which ports are required is a critical first step in maintaining a healthy Active Directory environment.
While configuring the network security it is essential to set up the Active Directory (AD), and one of its critical parts involves the secure communication between the AD server and clients. For instance, if your organization is deploying AD to manage user authentication, group policies, and access to shared resources, one of the key steps is to configure your firewall to open certain ports. Without opening these ports, users may face issues logging in, accessing files, or receiving policy updates, causing disruptions across the networks.
Active Directory acts as a central repository for a user, group, and computer accounts, as well as a variety of other objects, such as shared resources and security policies, and for the proper communication the following ports are required:
- TCP/UDP port 53: Port 53 acts as the port used for Domain Name Services, or DNS. DNS Servers are used to communicate with a web client and translate domain names to IP addresses. Most organizations will utilize DNS to make it easier for the different users to reach devices without needing to memorize IP addresses.
- TCP/UDP port 88: Port 88 is used to give users access to the Kerberos authentication protocol. This allows access to privileged network resources using tickets given by the server.
- TCP/UDP port 135: Port 135 is used for Remote Procedure Call or RPC. RPC is a Windows service relied upon by many services like AD to allow for remote client-server communications.
- TCP/UDP port 137-139: Ports 137, 138, and 139 are all used for providing different features relating to SMB protocol over NetBIOS. SMB, or Server Message Block, protocol is mainly used for sharing printers and files within a Windows-based network. Port 137 provides name services across TCP or UDP for SMB, port 138 provides diagram services across UDP for SMB, and port 139 provides session services across TCP or UDP for SMB. As a note, port 138 specifically uses UDP alone, it is not used with TCP.
- TCP/UDP port 389: Ports 389 focuses around Lightweight Directory Access Protocol, or LDAP. LDAP allows clients to access protected network resources. Port 389 allows an unencrypted connection to LDAP.
- TCP port 445: Port 445, also referred to as Microsoft-ds, works very similarly to ports 137-139, except it allows access to SMB without the need for NetBIOS. This means that NetBIOS layer is not required, and port 445 is mainly used by system administrators to manage objects on the network.
- TCP/UDP port 464: Similar to port 88, port 464 is used to interact with Kerberos. Port 464, however, is specifically used for password changes within Microsoft Active Directory (AKA Entra), as Kerberos is the native authentication protocol of Entra.
- TCP/UDP port 636: Port 636 also allows users to interact with LDAP, however it uses an encrypted connection. This encryption is generated by SSL/TLS, so you will often see port 636 as connecting to LDAPS.
- TCP/UDP port 3268-3269: Ports 3268 and 3269 also connect to services via LDAP, however they are specific to the global catalog. Port 3268 is the unencrypted connection and port 3269 is for encrypted connections.
In addition to these ports, other ports may be required depending on your AD environment’s specific components and features. For example, if you are using Group Policy, the following ports will also be required:
- TCP port 80: Port 80 is specifically used for communication between web browsers and servers using HTTP. This port transports data to the web browser in plaintext, an unencrypted method of sending data.
- TCP/UDP port 443: Port 443 delivers messages between web servers and browsers via HTTPS, the encrypted connection version of HTTP.
- TCP port 445: Port 445 allows access to SMB without the need for NetBIOS.
If you are using ADFS (Active Directory Federation Services) for single sign-on, the following ports will also be required:
- TCP port 80
- TCP port 443
- TCP port 49443: Port 49443 is specifically used for Active Directory Federation Services, or ADFS. ADFS is a method of certificate authentication within Microsoft AD, so this is a critical port in PKIs.
Ports required for PKI communication
In order for a PKI to function properly, certain ports need to be opened on the firewall to allow communication between the various components of the PKI system. These ports include:
-
TCP port 80
This port is used for HTTP communication, which is required for clients to access the certificate revocation list (CRL) and other information from the certificate authority (CA) server.
-
TCP port 389
This port is used for LDAP communication, which is required for clients to access the certificate database on the CA server.
-
TCP port 636
This port is used for LDAPS communication, a secure version of LDAP that uses SSL/TLS for encryption. This is required if you are using LDAP over a public network.
-
TCP port 9389
This port is used for the Web Services for Management (WS-Management) protocol, which is required for clients to access the CA server using the Certificates snap-in in the Microsoft Management Console (MMC).
In addition to these ports, you may also need to open other ports depending on your PKI system’s specific components and configuration. For example, if you are using Online Certificate Status Protocol (OCSP) to check the status of certificates, you will need to open TCP port 2560.
Troubleshooting firewall issues with PKI
To troubleshoot common firewall issues with a PKI, you can follow these steps:
- Verify that the necessary ports are open on the firewall. You can do this by using the netstat command to list all of the open ports on the system and compare the results with the list of ports that are required for your PKI system.
- Check the firewall logs to see any entries related to the PKI system. This can help you to identify any specific rules or settings that may be blocking the necessary ports.
- Test the connectivity between the PKI components to ensure they can communicate properly. You can do this by using the ping, telnet, or tracert commands to test the connectivity between the client and the CA server and between other components of the PKI system.
- If you are still having issues with the firewall, try temporarily disabling the firewall to see if this resolves the problem. This will help you to determine whether the firewall is the cause of the issue or if there is a problem with another component of the PKI system.
Some Frequently asked questions
Here is a set of questions you might ask to identify the root cause of AD misconfiguration and connection issues. These are tailored specifically to help troubleshoot potential issues based on real-world scenarios:
Ques 1: Have you verified if the key ports, such as 389 (LDAP), 88 (Kerberos), and 445 (SMB) for AD communications, are properly configured and not being blocked by firewall?
Ques 2: Are all Domain Controllers resolved through DNS and is there any discrepancy between DNS entries and the actual AD server locations?
Ques 3: Is there any replication issue in AD that could cause inconsistencies between Domain Controllers and clients?
Ques 4: Is there any skew in the time settings between AD components that might cause Kerberos authentication failures?
Ques 5: Are there any specific error codes or warning messages in the event logs that could pinpoint a misconfiguration or service failure?
Ques 6: Is the account used by key AD such as Kerberos, DNS, LDAP still functioning properly, and does it have the necessary permissions?
How can Encryption Consulting help?
Encryption Consulting’s PKI Services and PKI-as-a-service can help you manage your PKI and secure the digital network of your organization. We can design, implement, manage, and migrate your PKI systems according to your specific needs. Managing PKI can seem daunting with the increase in the number of cyber threats. But you can rest assured because our experienced staff will help you build and monitor your PKI. We can assess your PKI based on our custom framework, providing you with best practices for PKI and HSM deployments.
Conclusion
Maintaining the firewall configuration is important in ensuring that your Active Directory and PKI systems function properly. By verifying that the necessary ports are open and troubleshooting any firewall issues that may arise, you can help to keep your Active Directory and PKI systems secure and reliable. For Active Directory, maintaining open communication channels for key ports such as, LDAP, DNS and Kerberos are critical. Similarly, for PKI, enabling ports for HTTP, LDAP and Secure Communication Protocol ensures that certificate service functions effectively, supporting certificate issuance, revocation and status checks.
