| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 Windows Server 2025 |
|
Category • Subcategory |
Logon/Logoff • Special Logon |
| Type | Success |
|
Corresponding events in Windows 2003 and before |
576
|
4672: Special privileges assigned to new logon
On this page
- Description of this event
- Field level details
- Examples
This event lets you know whenever an account assigned any «administrator equivalent» user rights logs on. For instance you will see event 4672 in close proximity to logon events (4624) for administrators since administrators have most of these admin-equivalent rights.
So, this is a useful right to detecting any «super user» account logons. Of course this right is logged for any server or applications accounts logging on as a batch job (scheduled task) or system service. See Logon Type: on event ID 4624. You can correlate 4672 to 4624 by Logon ID:.
Note: «User rights» and «privileges» are synonymous terms used interchangeably in Windows.
Admin-equivalent rights are powerful authorities that allow you to circumvent other security controls in Windows. Most admin equivalent privileges are intended for services and applications that interact closely with the operating system. With just a few exceptions, most admin equivalent privileges neither need nor should be granted to human user accounts.
Some Microsoft documentation puts this in the «Sensitive Privilege Use / Non-Sensitive Privilege Use» subcategory. However our testing finds this in the «Special Logon» Category.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4672
Subject:
The ID and logon session of the administrator-equivalent user that just logged on.
- Security ID: The SID of the account.
- Account Name: The account logon name.
- Account Domain: The domain or — in the case of local accounts — computer name.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events logged during the same logon session.
Privileges:
The names of all the admin-equivalent privileges the user held at the time of logon.
Supercharger Enterprise
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
The Active Directory auditor will show you different activities and processes running on your computer in the form of Event Log IDs. The Windows Security Log Event ID 4672 is one of these event IDs. It lets you know whenever an account assigned any Administrator equivalent user rights logs on.
However, this guide will discuss the event ID 4672 from appearing recurrently on your device. Check our guide on fixing the security log is now full – Event ID 1104 on Windows 11.
What causes event ID 4672 Special Logon error?
The Event ID 4672 Special logon prompt should appear on your computer just once without interrupting your activities. Experiencing the Special logon notification popping up on your screen from time to time indicates that something is wrong with its process. Some probable causes are:
- Issues with Event Viewer service – You can experience the event ID appearing often on your PC or why it prompts it to open due to the Event Viewer malfunctioning on your PC.
- Issues with the GPU driver – The GPU drivers are responsible for the graphics processing of your computer, and they need to be stable for the system to work correctly. However, issues with GPU drivers can cause the Event ID to keep appearing and interrupt your work.
- Issues with the processors on your PC – Processors provide the instructions and processing power the computer needs to do its work. So, if they are not intact or running correctly, it can affect the Active Directory event log processes on your PC.
Other factors like faulty Windows update may also cause the error. Nonetheless, we’ll guide you through fixing the Event ID 4672 Special logon error.
How can I fix event ID 4672?
Before trying any advanced troubleshooting steps, go through the following:
- Turn off background apps running on your PC.
- Temporarily disable antivirus software on your computer.
- Restart Windows in Safe Mode and check if the error persists.
If you can’t fix the error, proceed with the troubleshooting steps below:
1. Restart Windows Event Log Service
- Press Windows + R key to open the Run dialog box, type services.msc, and press Enter.
- Find the Windows Event Log service in the services list, right-click on it, and select Restart from the drop-down.
- Restart your PC and check if you can fix the error.
Restarting the Windows Event Log service will help refresh its log and clear off event logs incorrectly logged, causing it to run into errors.
2. Uninstall recent Windows updates
- Press Windows + I key to open the Settings app.
- Go to Windows Update and select Update history.
- Click the Uninstall updates button and select the most recent update.
- Click on Uninstall to confirm the process.
Uninstalling the recent Windows update should help fix any issue with the last build causing the error to occur. Check our guide on how to uninstall updates on Windows 11 for more steps.
- D3dx11_42.dll Not Found: How to Fix it
- Windows 11 Shutdown After Inactivity: 4 Ways to Stop it
- Windows Shuts Down Instead of Restarting: 4 Ways to Fix it
- Error no Ace Condition 804 (0x324): Fix it With 4 Steps
3. Update your GPU drivers
- Press Windows + R keys to prompt the Run window, type devmgmt.msc, and click OK to open the Device Manager.
- Click on the drop-down button to expand the Display Adapters option. Right-click your GPU and select the Update driver option.
- Select Search automatically for drivers.
- After the update is complete, restart your device and check if the error persists.
Updating the GPU driver will fix bugs affecting them and install the latest features to improve system performance.
Check other steps for updating drivers on Windows 10 if you have any issues.
Besides updating your drivers manually, which can sometimes be not as straightforward for some users, you can opt for dedicated software to execute this action automatically.
Ensure your system performs smoothly and avoids all GPU driver errors by using a complete driver update assistant, namely Outbyte Driver Updater, that will do the job for you.
Here’s how to safely update your drivers:
- Download and install the Outbyte Driver Updater app.
- Launch the software and wait for the app to detect all incompatible drivers.
- Now, it will show you a list of all faulty drivers to select the ones to Update or Ignore.
- Click on Update & Apply Selected to download and install the newest versions.
- Restart your PC to ensure the applied changes.
OutByte
Keep your GPU in a flawless state without worrying about possible driver issues.
Disclaimer: You may need to upgrade the app from the free version to perform specific actions.
4. Update your BIOS
NOTE
The BIOS updating process varies on different PCs. However, the steps below are specifically for HP laptops.
- Go to the HP driver and software download website, select your product from the list, then input your serial number or exact computer model.
- Click the plus (+) button against All drivers, then click the (+) button against BIOS to expand it and see available updates, then click on Download.
- Double-click the downloaded file to install the .exe file, then follow the on-screen instructions to complete the installation.
- Restart your PC, then select the Apply Update Now option during the startup to implement the installed BIOS update.
Updating the BIOS will fix the Event ID 4672 Special logon error and enhance system stability. You can check our guide on how to check and update BIOS on various laptops.
Alternatively, our readers may be interested in fixing the Event Viewer reboot event ID error in Windows 11. Also, we have a detailed guide on fixing application popup event ID 1060 on Windows 11.
In conclusion, this article should help you troubleshoot event ID 4672. If you have further questions and suggestions, kindly drop them in the comments below.
Henderson Jayden Harper
Windows Software Expert
Passionate about technology, Crypto, software, Windows, and everything computer-related, he spends most of his time developing new skills and learning more about the tech world.
He also enjoys gaming, writing, walking his dog, and reading and learning about new cultures. He also enjoys spending private time connecting with nature.
4672 — Special Privileges
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4672
Event ID 4672 is a critical event in the Windows Security Event Log that signifies the assignment of special privileges to a new logon session. This event is automatically logged when a user logs on with an account that is a member of one of the following security groups: Administrators, Backup Operators, Domain Admins, Schema Admins, Enterprise Admins, or other groups that confer special privileges. Monitoring Event ID 4672 is essential for security professionals to track the use of high-privilege accounts, which can indicate legitimate administrative activities or potentially malicious actions if such privileges are abused.
The event is generated by the Security subsystem as part of the «Audit Special Logon» category and occurs whenever a user logs on with special privileges.
Category: Audit Special Logon
Significance:
-
Security Implications: The use of accounts with special privileges should be closely monitored, as these accounts have the potential to make significant changes to system configurations, access sensitive data, and perform other high-impact operations. Unauthorized use of such accounts could indicate an attempt to escalate privileges or move laterally within a network.
-
Operational Integrity: Ensuring that only authorized users are granted special privileges is vital for maintaining the security and integrity of IT systems. Event ID 4672 helps in verifying that privileged access aligns with organizational policies.
Details Included in Event ID 4672
-
Subject: Information about the user and session that was granted special privileges. This includes:
-
Security ID: The SID of the account.
-
Account Name: The name of the account.
-
Account Domain: The domain of the account.
-
Logon ID: A reference number to the logon session.
-
-
Privileges: Lists the specific privileges assigned to the user or session. Common privileges include
SeAssignPrimaryTokenPrivilege,SeBackupPrivilege,SeDebugPrivilege,SeTakeOwnershipPrivilege, among others.
How to Use Event ID 4672 for Security
Monitoring and Alerting: Security teams should configure alerts for Event ID 4672 to be informed of any logon sessions where special privileges are assigned. This is particularly important for detecting unexpected or unauthorized use of privileged accounts.
Forensic Analysis: In the context of an incident response, analyzing occurrences of Event ID 4672 can help in understanding how an attacker might have gained elevated privileges or which accounts were used to perform privileged actions during a breach.
Access Review and Compliance: Regularly reviewing events where special privileges are assigned supports efforts to ensure that only authorized personnel have privileged access and that such access is in compliance with least privilege principles and regulatory requirements.
Best Practices for Monitoring Event ID 4672
-
Enable Audit Policies: Ensure that audit policies for «Audit Special Logon» are enabled to capture Event ID 4672 in the Security Event Log.
-
Privileged Account Management (PAM): Implement a PAM solution to manage, monitor, and audit the use of privileged accounts, reducing the risk associated with high-privilege access.
-
Least Privilege Principle: Regularly review and adjust group memberships and privileges to ensure that users are only granted the privileges necessary to perform their job functions.
-
Anomaly Detection: Utilize SIEM systems to detect anomalies in the use of privileged accounts, such as logons at unusual times or from unexpected locations, which could indicate malicious activity.
While Event ID 4672 is valuable for indicating the use of special privileges, it does not by itself indicate malicious activity. Legitimate administrative tasks often require such privileges. Therefore, this event should be analyzed in conjunction with other indicators of compromise and the context of the user’s expected behavior and job responsibilities.
Attackers frequently rely on lateral movement techniques to infiltrate corporate networks and obtain privileged access to credentials and data. In particular, one common technique is pass-the-hash: Hackers use stolen password hashes to authenticate as a user without ever having the user’s cleartext password. This tactic enables them to bypass normal system access controls to move laterally within the environment.
This post explains exactly what to look for in the native Windows event logs to detect pass the hash, and offers additional options for spotting — and even preventing — these attacks.
Getting a Baseline: Understanding the Events Logged during the Normal NTLM Authentication Process
Pass the hash relies on NTLM authentication, so we need to first understand what events are normally generated during normal NTLM logon activity.
Authenticating as an Administrative User
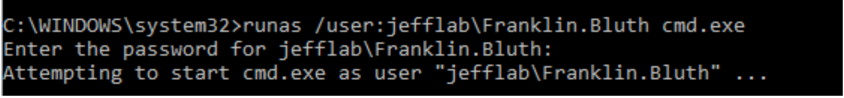
To generate these events, I launch a new command prompt as an administrative user, using the account’s actual password:
Next, I used the Sqlcmd utility to connect to a Microsoft server by its IP address. This command will generate NTLM authentication to the SQL database:
Sqlcmd –S [IP ADDRESS]
For good measure, I will also run the SELECT SYSTEM_USER command to show the user I am authenticated as:
Reviewing the Events Generated
Now let’s see what native Windows events were logged. That gives us a baseline for normal NTLM authentication behavior that does not involve pass the hash.
Workstation Logs
On my local workstation, I will see the following events:
- 4648 – A logon was attempted using explicit credentials.
- 4624 – An account was successfully logged on.
A 4624 event was logged with a Logon Type of 2, which means an interactive logon. This aligns with the way I used runas and entered my credentials interactively.

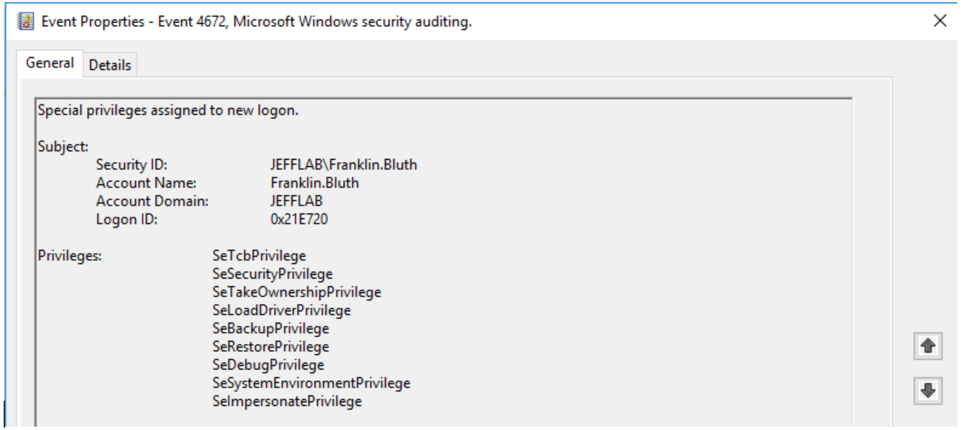
- 4672 – Special privileges assigned to new logon.
Because the account I used (Franklin.Bluth) is an administrative account, event 4672 gets logged to show what privileges are being assigned. This is a useful way to track the activity of administrative accounts.
Target Server Logs
On my SQL server, I see the following events:
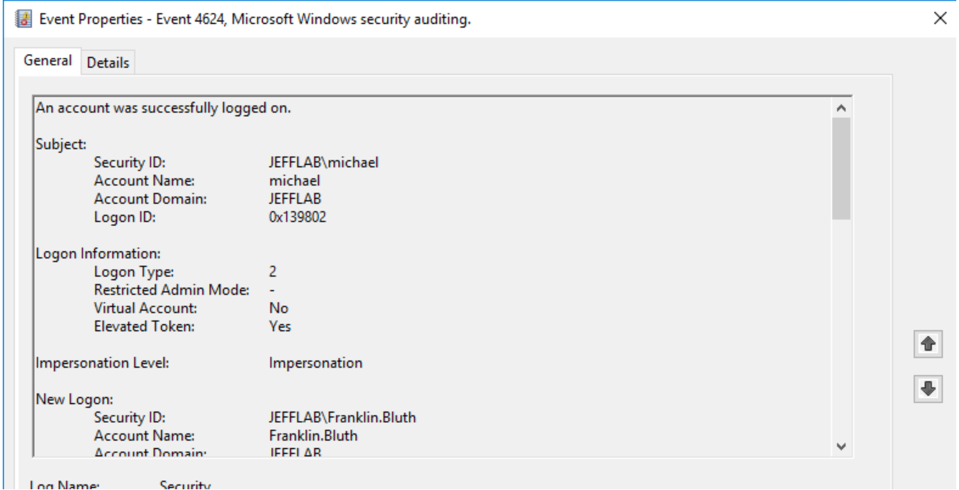
- 4624 – An account was successfully logged on.
On the SQL Server, there is a similar 4624 event; however, the Logon Type is 3, indicating a network logon.
The details show that the Authentication Package was NTLM, which confirms that we are performing NTLM authentication.
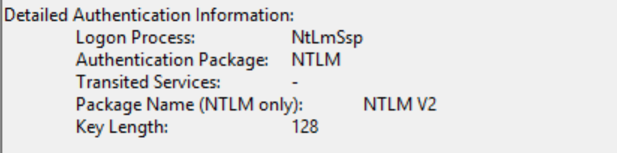
- 4672 – Special privileges assigned to new logon.
Because we used a privileged account, we also see a 4672 event, as illustrated earlier in the description of the workstation logs.
Domain Controller Logs
On the domain controller, we will find artifacts of both Kerberos and NTLM authentication. The Kerberos authentication, which is the default authentication method for Active Directory, happens first. That generated two events:
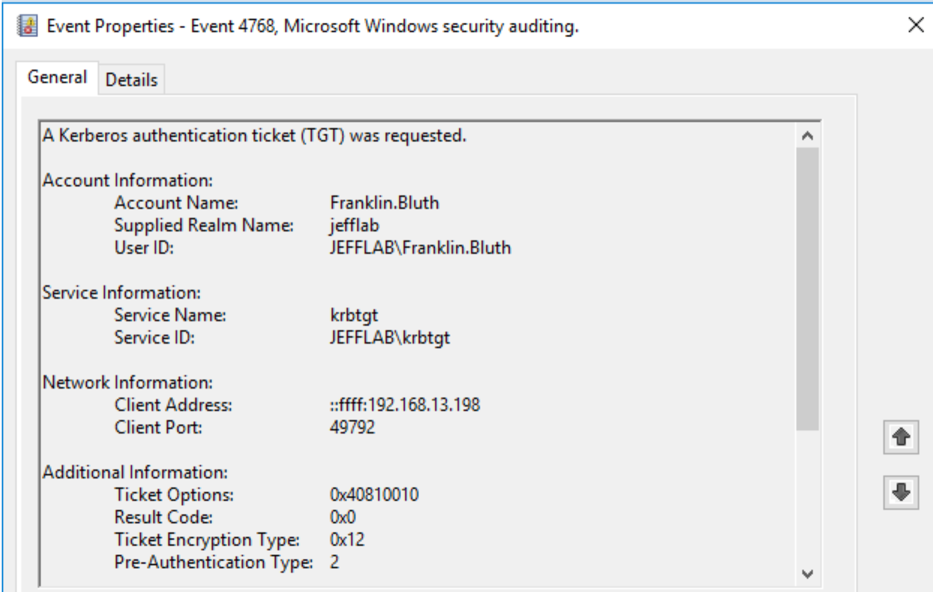
- 4768 – A Kerberos authentication ticket (TGT) was requested.
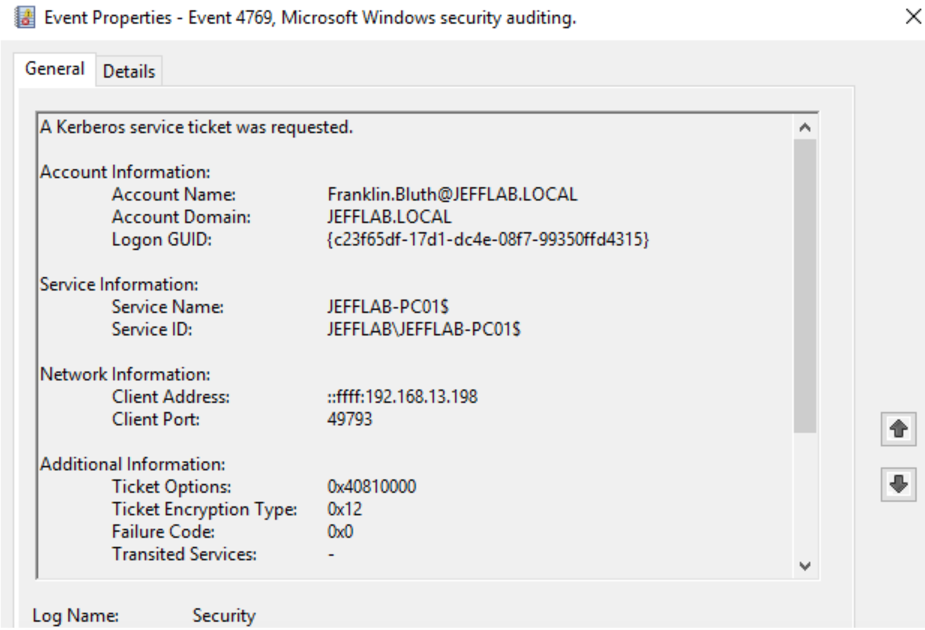
- 4769 – A Kerberos service ticket was requested.
Once the TGT is received, a TGS was requested for the host. With this, the user Franklin Bluth can now interact with the PC to launch the command prompt.
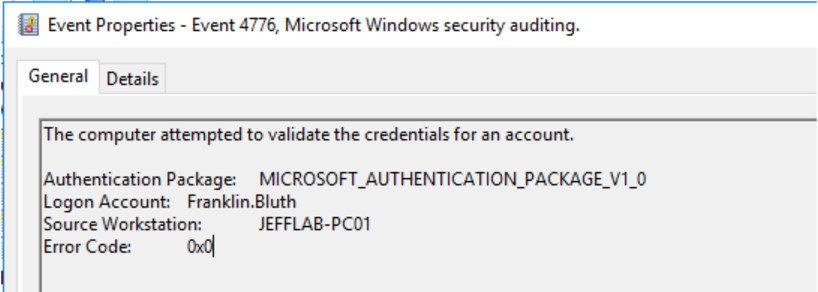
- 4776 – The computer attempted to validate the credentials for an account.
The 4776 event is specific to NTLM and will come last. It occurs when we execute the Sqlcmd command to force NTLM authentication.
Detecting Pass the Hash: Understanding Events Logged during an Attack
Now, let’s take a look at what events are generated when we use pass the hash to authenticate.
Authenticating using Pass the Hash
I can easily get the NTLM hash for the Franklin Bluth account from memory with this Mimikatz command:
sekurlsa::logonpasswords
Then I authentication using pass the hash with the following command:
Sekurlsa::pth /user:Franklin.Bluth /ntlm:[ntlm] /domain:jefflab.local
A new command window will open. By using the same Sqlcmd command to connect to the IP address of my SQL Server, we can see that I am now authenticated there as Franklin Bluth:
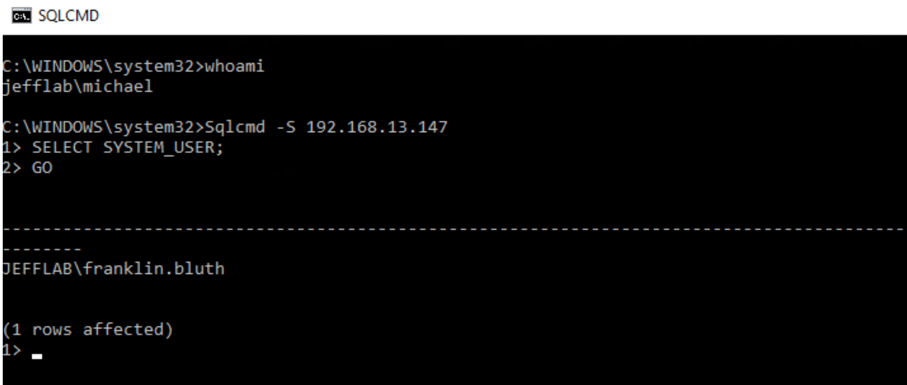
Reviewing the Events Generated
Let’s take a look at what events were generated by this pass-the-hash authentication.
Workstation Logs
On my local workstation, I will see the same events as for the legitimate NTLM authentication (4648, 4624 and 4672). However, there are a few key differences.
- 4624 event — This event now has a Logon Type of 9, which is NewCredential. This was identified by a security researcher, and I reliably reproduced it in my lab. It a very useful way to identify that a pass-the-hash event took place.
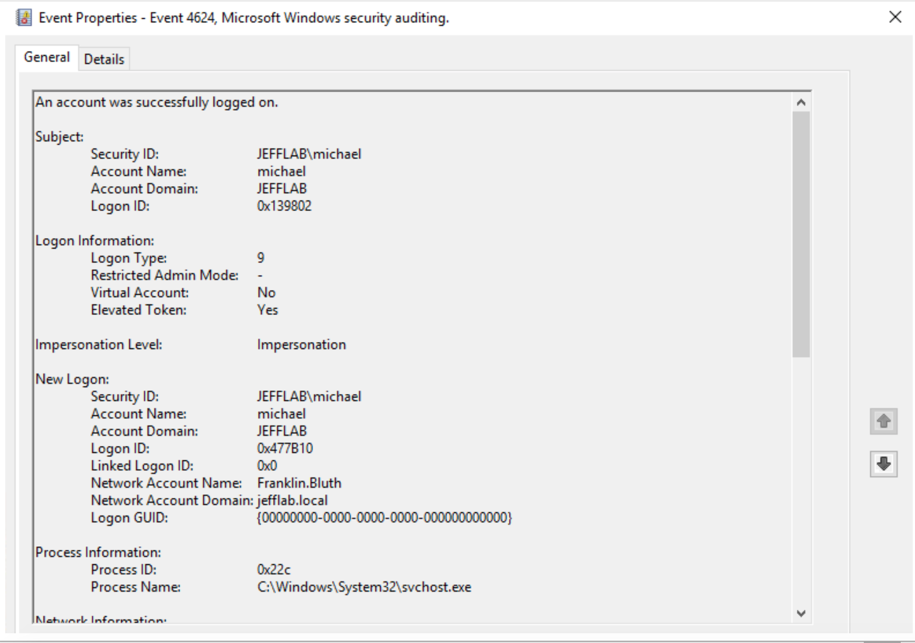
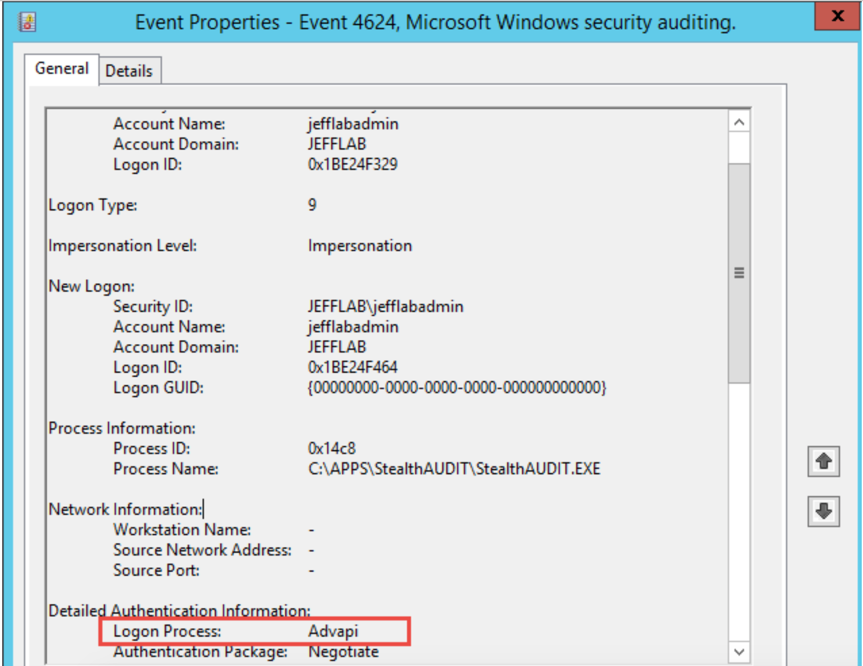
Logon Type 9 is very rare. However, I was able to generate some false positives running applications that use impersonation. The main difference to key off of is the Logon Process will always be “seclogo” for pass the hash (from my tests), so you can filter on that to reduce false-positive rates.
- 4672 event— In the normal authentication scenario, this event identified a privileged logon for the Franklin Bluth account. With pass-the-hash authentication, it registers the user that I am logged into my workstation as.
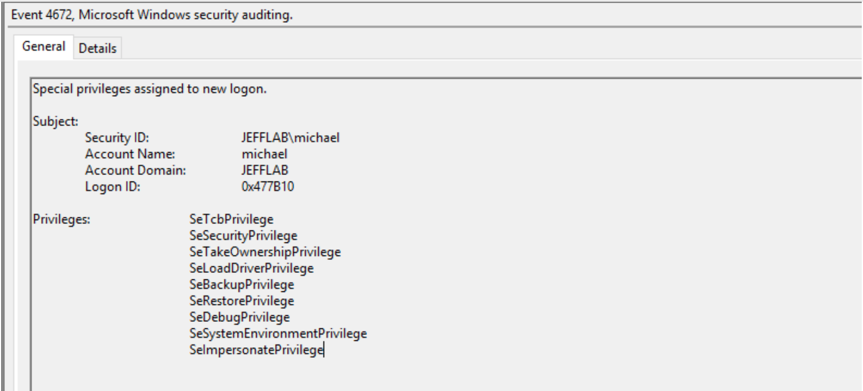
Target Server Logs
The logs on the SQL server are identical to those we saw doing legitimate NTLM authentication:
- 4624 – An account was successfully logged on. Logon Type 3, NTLM
- 4672 – Special privileges assigned to new logon.
Domain Controller Logs
On the domain controller, the key difference is that you will not see Kerberos authentication. However, that isn’t a very reliable way to detect pass the hash because it can happen for lots of valid reasons, including authentications originating from non-trusted domains.
Summary of Event Logs for Normal and Pass-the-Hash Authentication
Here’s a summary of the native Windows event logs we see when performing normal NTLM authentication:
|
Source Host |
Target Host |
Domain Controller |
|
|
|
And here is a summary of what we see when doing pass the hash, with the key differences bolded:
|
Source Host |
Target Host |
Domain Controller |
|
|
|
Detecting Pass the Hash using Sysmon
To conclusively detect pass-the-hash events, I used Sysmon, which helps to monitor process access events. With Sysmon in place when a pass the hash occurs, you will see Event ID 10 showing access to the LSASS process from Mimikatz (or other pass-the-hash tool).
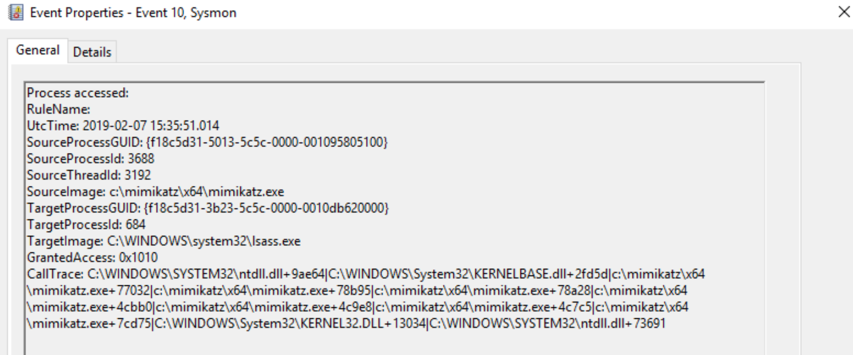
Building Detections for Pass the Hash
Now that we’ve looked at all the evidence, the simplest way to build detections for pass the hash is to look for:
- 4624 events on your workstations with:
- Logon Type = 9
- Authentication Package = Negotiate
- Logon Process = seclogo
- Sysmon 10 events for LSASS process access
With a custom event log filter, you can easily see when these two things happen at the same exact time, which indicates pass-the-hash activity on your network.
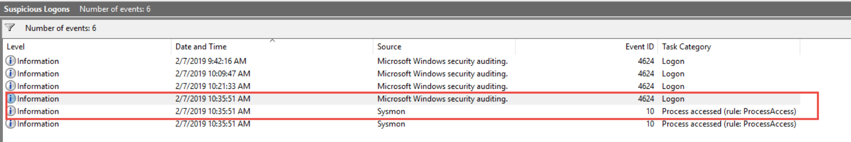
Here is a custom event filter you can use to surface that specific information.
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID='4624')]
and
EventData[Data[@Name='LogonType']='9']
and
EventData[Data[@Name='LogonProcessName']='seclogo']
and
EventData[Data[@Name='AuthenticationPackageName']='Negotiate']
]
</Select>
</Query>
<Query Id="0" Path="Microsoft-Windows-Sysmon/Operational">
<Select Path="Microsoft-Windows-Sysmon/Operational">
*[System[(EventID=10)]]
and
*[EventData[Data[@Name='GrantedAccess'] and (Data='0x1010' or Data='0x1038')]]
</Select>
</Query>
</QueryList>How Netwrix Solutions Can Help
Setting up and monitoring custom event filters is tedious, and it requires enabling logging on all endpoints. To simplify the work while leveraging more advanced techniques, consider a third-party threat detection solution.
Netwrix Threat Manager is an effective tool for detecting pass-the-hash attacks. Here are two techniques that the solution supports:
- Honey tokens — You can inject fake credentials into LSASS memory on target machines and monitor for the usage of those credentials. If you see the credentials in use, you know they were retrieved from memory on one of the honeypot machines and used for lateral movement.
- Abnormal behavior detection — Baselining normal user behavior helps you spot anomalous use of accounts that is indicative of pass-the-hash and other lateral movement attacks. Behavior to look for includes:
- An account is used from a host it never authenticated before
- An account is used to access a host it never before accessed
- An account accessing a large number of hosts across the network in a way that contradicts normal access patterns
To mitigate the risk of pass-the-hash attacks being launched in the first place, use Netwrix Access Analyzer, which empowers you to:
- Minimize administrative rights on servers and desktops
- Prevent users from logging into workstations using administrative rights
- Monitor for suspicious PowerShell commands that can be used for performing credential extraction and pass the hash
- Restrict highly privileged accounts from logging into lower privileged systems
- Ensure that LSA Protection is enabled on critical systems to make it more difficult to extract credentials from LSASS
Jeff Warren is SVP of Products at Netwrix. Before joining Netwrix, Jeff has held multiple roles within Stealthbits — now part of Netwrix, Technical Product Management group since joining the organization in 2010, initially building Stealthbits’ SharePoint management offerings before shifting focus to the organization’s Data Access Governance solution portfolio as a whole. Before joining Stealthbits — now part of Netwrix, Jeff was a Software Engineer at Wall Street Network, a solutions provider specializing in GIS software and custom SharePoint development.
With deep knowledge and experience in technology, product and project management, Jeff and his teams are responsible for designing and delivering Stealthbits’ high quality, innovative solutions.
Jeff holds a Bachelor of Science degree in Information Systems from the University of Delaware.
The keys to successful incident response equate to having the proper people, processes, and tools in place to act decisively when an incident occurs, which is a recurring theme in our incident response articles. Without proper logging occurring ahead of time, which is a large part of the picture for security operations and incident response, teams, it will make it difficult to prove how long a threat actor was in an environment, and depending on the lack of logs, could be very difficult to provide analysis on activities taken by the threat actors or insider threats depending on the case scenario.
Key Window Event Logs to Focus on Initially
While the volume of logs generated by Windows machines can be overwhelming, for the purpose of this article, we will focus on just six to get you started on the most common ones which will indicate malware breaches and suspicious account activity. The event IDs we are going to focus on for this article are 4688, 4670, 4672, 1125 and 1006/1007.
Windows security event log ID 4688
Event 4688 documents each program (or process) that a system executes, along with the process that started the program. What’s fascinating about this event ID is that it logs any process that is created by a user or even spawned from a hidden process. For example, if there’s malware present on your Windows system, searching event 4688 will reveal any processes executed by that malicious program. Child processes with a different parent process ID than the original process, as well as processes running outside of C: Program Files or C: windowssystem32, are red flags for malicious activity..
In addition, you can get information about a user’s administrative privileges through the Token Elevation Type field. A Type 1 token refers to a “full token” with all privileges granted to that user account, such as when UAC (User Access Control) is disabled or when the user is in a service or built-in administrator account. Type 2 hints that an elevated token was issued through the “Run as administrator” option while the UAC was enabled. Type 3 is a limited token with no administrative groups or privileges. It’s issued when the user doesn’t launch a program using Run as administrative or when an application doesn’t require administrative privileges. While event 4688 can tell you a lot, it should be used in conjunction with other event logs to get a full picture of an intrusion.
Windows security event log ID 4670
One of the best ways to identify unauthorized access (and ultimately data leakage) is by tracking File Server permission changes. That’s where event 4670 comes in handy — it triggers itself when a user modifies an object’s access control list. Hackers are known to change permissions when attempting to move laterally or inject ransomware into a system; monitoring who takes ownership of an intrusion is a critical step in tracing the source of an attack. Advanced users can also dive into SDDL to further understand what permissions have been changed. Besides intrusion detection, you can also use event 460 to get insights into user activity. It can help you get information on peak logon times, user attendance and more. Pro tip: Make sure to enable the audit policy of objects when viewing event 4670 in your Windows Event Viewer or SIEM.
Windows security event log ID 4672
This event informs you whenever an administrator equivalent account logs onto the system. You can track it to look for a potential Pass-the-Hash (PtH) attack. If the “SubjectSecurity ID” in the Event Viewer doesn’t contain “LocalSystem, NetworkService, LocalService”, it’s not an admin-equivalent account and requires careful analysis.
But event 4672 isn’t the only Windows security event log ID to indicate a pass-the-hash attack. Many other events, including 4648 (a logon was attempted with explicit credentials), 4624 (an account was successfully logged on) and 4776 (the computer attempted to validate the credentials for an account), can indicate that a system has been or is being breached collectivity.
It’s not easy to detect lateral movement from Pass-the-Hash attacks, but an SIEM that lets you create correlation rules around the movement can help you identify the other events linked to PtH.
Windows security event log ID 1125 (Error)
Windows typically manages its configuration settings on servers and workstation using “Active Directory Group Policy.” Monitoring event 1125 helps you identify potential failures pertaining to policy application or unsanctioned changes to policy objects in Active Directory, rather than user error. If the policy cannot be applied, there’s a chance that the system has a security issue.
Besides AD policy, it’s also beneficial to keep tabs on firewall rules. Because Windows Firewall offers a critical line of defense, a malicious actor may attempt to modify its rules in order to gain access to your system. Use the firewall logging feature to check for dynamic and disabled port openings, as well as analyze dropped packets on the send route.
In case you identify a malicious activity, open the log file in Notepad and use the DROP command to filter all entries in the action field, analyzing which destination IPs end with a number that’s not 255. If you detect many such IPs, take note of packets’ destination IP addresses for troubleshooting.
Windows defender event 1006 and event 1007
Consider investing the notifications for identifying, preventing and removing malware in Windows Defender. Yes, even the built-in antivirus can be used to conduct malicious activity. Start by reviewing event ID 1006, which is triggered when the Defender detects unwanted software. Then review Event 1007 to see if the antivirus acted to protect your system from potential infiltration. All these events are present in a sublog.
You can use the Event Viewer to monitor these events. Open the Viewer, then expand Application and Service Logs in the console tree. Now click Microsoft → Windows → Windows Defender Antivirus”. The last step is to double-click Operational, which will open the “Details” pane, where you’re able to see events.
Conclusion
Windows event logs are an indispensable tool for detecting errors and malicious activity. Keeping a watchful eye on them can alert you to intrusions before they grow in presence and scale. Given that the first step in responding to malware is often to track the infiltration source, event IDs are a valuable piece of information available to Windows users. If you pay attention to what they’re telling you, you’ll detect malicious activity as early into the kill chain as possible.









