Active Directory Users and Computers (ADUC) lets you take care of user accounts, groups, and other stuff in Active Directory (AD) through a nice visual setup. In the past, to get this tool, you had to download something called the Remote Server Administration Tools (RSAT) separately. But now, if you’re using Windows 11 or Windows 10, you don’t have to do that. RSAT is part of the “Features on Demand,” so you can just add it straight from the system itself.
This guide will show you how to add RSAT Active Directory Users and Computers and the Active Directory PowerShell module using either PowerShell or Command Prompt.
Install Active Directory Users and Computers in Windows 11 or 10 via PowerShell
PowerShell is likely the easiest way to add different features in Windows thanks to its easy yet powerful commands. The following steps will show you how to use it to install Active Directory Users and Computers on your Windows 11 or 10 PC.
- First, you need to open PowerShell as an admin. Press the Windows key, type “PowerShell,” right-click on “Windows PowerShell,” and pick “Run as administrator”.
- Make sure your PC is online before you start adding features with PowerShell.
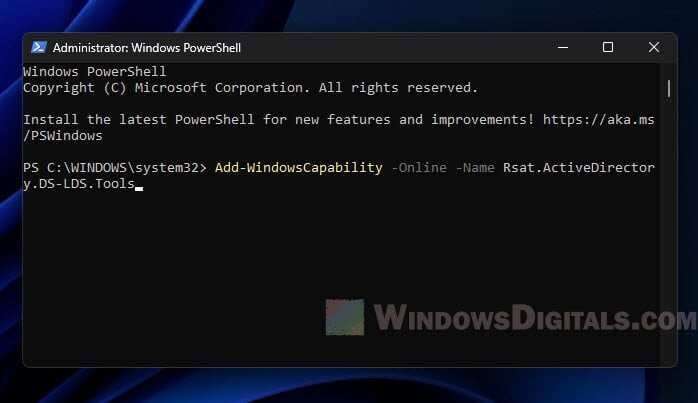
- To add ADUC, type in this command:
Add-WindowsCapability -Online -Name Rsat.ActiveDirectory.DS-LDS.Tools
- After you run the command, it will check with Windows Update to download and add what’s needed. You’ll see a message when it’s done.
It’s okay to skip adding a version number when you run the command. If you don’t add it, Windows will just get the newest version available.
Also see: Run CMD, PowerShell or Regedit as SYSTEM in Windows 11
Install Active Directory PowerShell Module
The Active Directory PowerShell Module is very useful for managing AD right from the command line. But it doesn’t come with the ADUC GUI tools, so you need to install it separately.
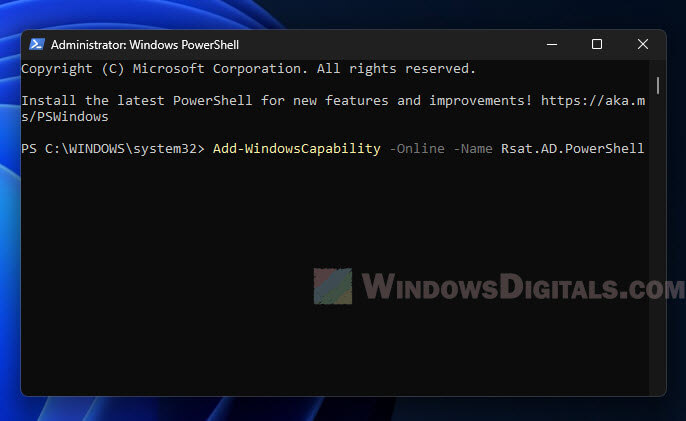
- Open PowerShell as an admin and run this command:
Add-WindowsCapability -Online -Name Rsat.AD.PowerShell
- Wait a bit, and you’ll see a message saying it’s done.
- Right after installing, you can start using the AD commands in your current session by typing:
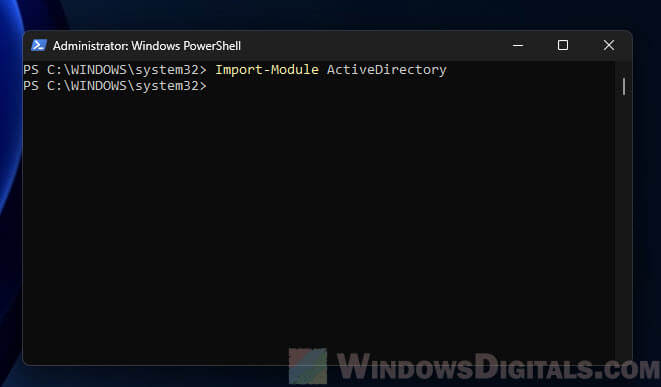
Import-Module ActiveDirectory
This loads the Active Directory module so you can use commands like
Get-ADUserandGet-ADComputerfor AD tasks.
Useful tip: How to Install Telnet via CMD or PowerShell in Windows 11
Install ADUC in Windows 11 or 10 via CMD
Although PowerShell is amazing for a lot of Windows admin tasks, some users might still prefer to use the old-school Command Prompt (CMD). Even though CMD doesn’t have as many fancy commands as PowerShell, you can still use DISM (Deployment Image Servicing and Management) to add features like ADUC.
- Open Command Prompt as an admin by pressing the Windows key, typing “cmd,” right-clicking on “Command Prompt,” and picking “Run as administrator”.
- Being online is important here too, since the features come from Windows Update.
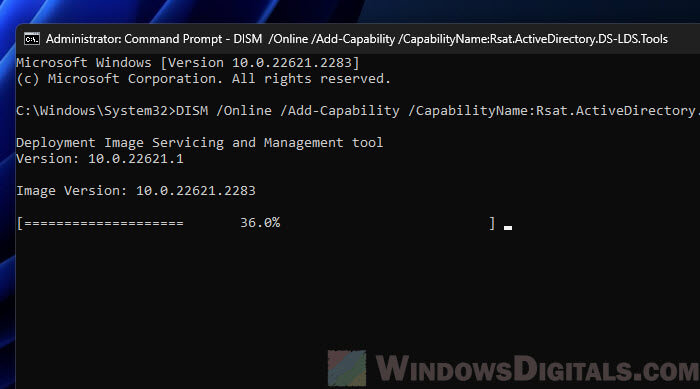
- To add ADUC with CMD, enter this command:
dism /online /add-capability /capabilityname:Rsat.ActiveDirectory.DS-LDS.Tools
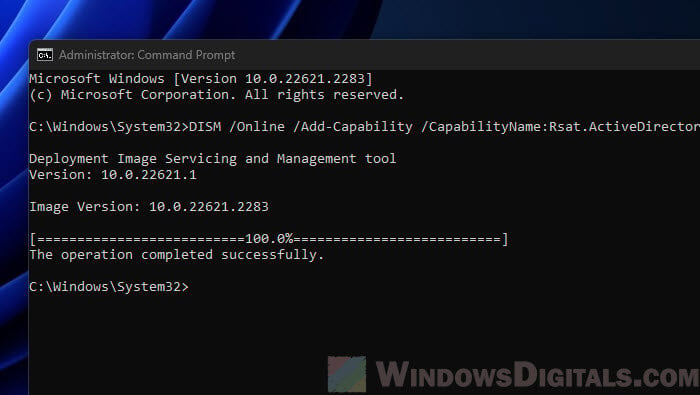
This also reaches out to Windows Update to download and add what you need. You’ll know it’s done when you see a message.
- If you want the Active Directory PowerShell Module too, use this command:
dism /online /add-capability /capabilityname:Rsat.AD.PowerShell
After that, you’re set to use the AD-specific commands in PowerShell.
Just like with PowerShell, you don’t have to specify a version number. Leaving it out means Windows will pick the latest version for you.
Related resource: Using PowerShell to Test Port Connection Without Telnet
What to do after installing them
After you’ve added ADUC, below are some tips to get familiar with it and make sure everything’s running as intended.
Launch ADUC
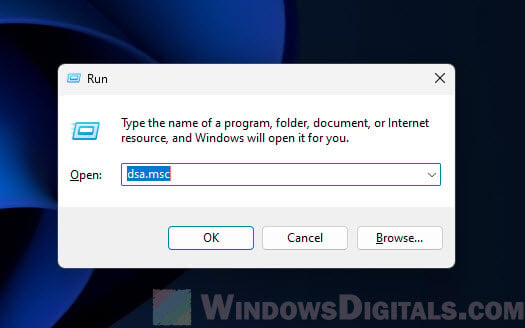
Press Windows + R, type “dsa.msc”, and hit Enter. This opens the Active Directory Users and Computers interface.
Connect to a Domain or a specific Domain Controller
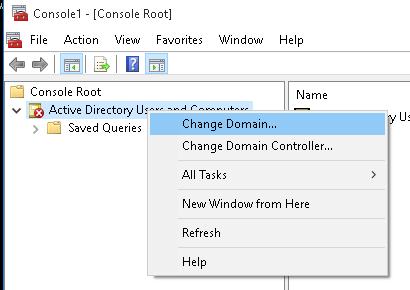
If your PC is part of an Active Directory domain, ADUC will usually find a domain controller by itself. But if you need to hook up to a different domain, right-click on “Active Directory Users and Computers” at the top left and pick “Change Domain”.
For connecting to a specific domain controller in your current domain, choose “Change Domain Controller”.
Trying out ADUC
Take some time to check out the different areas and organizational units (OUs) in the domain. This is where you manage all the users, groups, computers, and more.
PowerShell module
If you added the Active Directory PowerShell module, open PowerShell and type Import-Module ActiveDirectory to dive into using Active Directory commands.
Some common issues when installing ADUC
In most cases, there shouldn’t be any problem if you add ADUC using one of the ways described above. Below are some common problems you might see when installing ADUC and how to fix them.
Installation failures
Check you’re online since some parts might need to come from Windows Update. Make sure you have admin rights to run the commands.
ADUC not connecting to domain
Check your PC’s connection to the domain controller.
Make sure your domain login details are correct; you might need more rights to see or change certain things.
Missing tabs or features in ADUC
If you’re missing some options, it might be because you need more Windows features or the right permissions in Active Directory. For instance, the “Attribute Editor” tab shows up only if “Advanced Features” is turned on from the “View” menu.
PowerShell module errors
Double-check you’ve got the Rsat.AD.PowerShell feature added. Make sure you’re using PowerShell with admin rights too.
Some final notes
Usually, tools like Active Directory Users and Computers are set up on client PCs, not directly on servers. If you’re adding Active Directory Users and Computers to a client machine, the normal way is through the system settings: “Settings” > “Apps” > “Optional features”. This method is pretty straightforward and what most users would use because it’s visual and easy to understand.
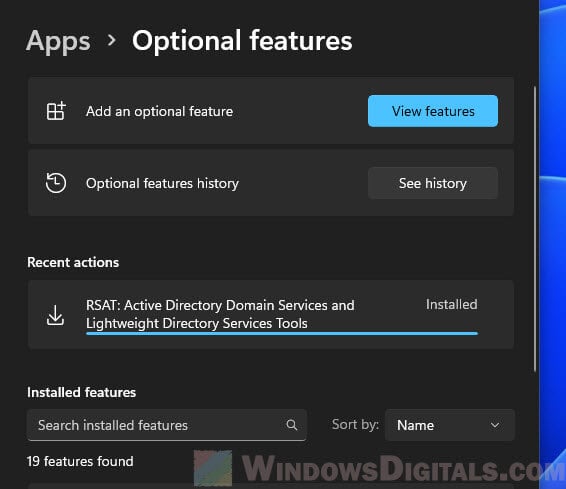
But, if you’re looking to add ADUC through the command line, either using PowerShell or Command Prompt, this guide will be of help for that. You should try these things on a test machine first before using them in a work environment.
Windows OS Hub / PowerShell / How to Install the PowerShell Active Directory Module and Manage AD
Every Windows system administrator should be able to use not only graphical AD snap-ins (usually it is ADUC, Active Directory Users and Computers), but also PowerShell cmdlets to perform everyday Active Directory administration tasks. Most commonly, the Active Directory module for Windows PowerShell is used for domain and object management tasks (users, computers, groups). In this article, we will look at how to install theRSAT-AD-PowerShell module on Windows, discover its basic features, and popular cmdlets that are useful to manage and interact with AD.
Contents:
- How to Install the Active Directory PowerShell Module on Windows 10 and 11
- Installing the RSAT-AD-PowerShell Module on Windows Server
- Active Directory Administration with PowerShell
- Importing Active Directory PowerShell Module from a Remote Computer
- Common PowerShell Commands for Active Directory
How to Install the Active Directory PowerShell Module on Windows 10 and 11
You can install the RSAT-AD PowerShell module not only on servers but also on workstations. This module is included in the RSAT (Remote Server Administration Tools) package for Windows.
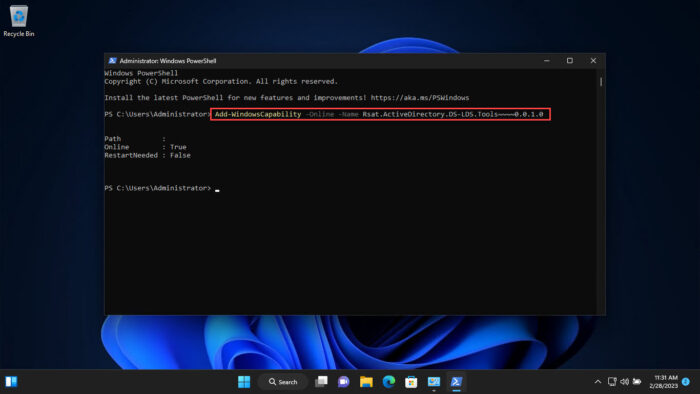
In current builds of Windows 11 and Windows 10, the RSAT components are installed online as Features on Demand. You can install the module by using the command:
Add-WindowsCapability -online -Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
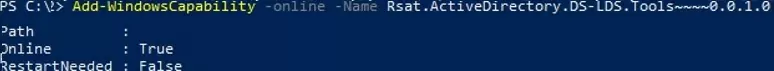
Or through via the Settings -> Apps -> Optional features -> Add a feature -> RSAT: Active Directory Domain Services and Lightweight Directory Services Tools.
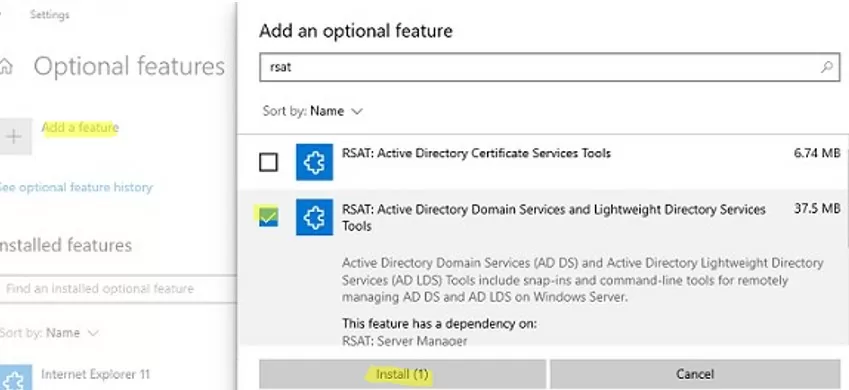
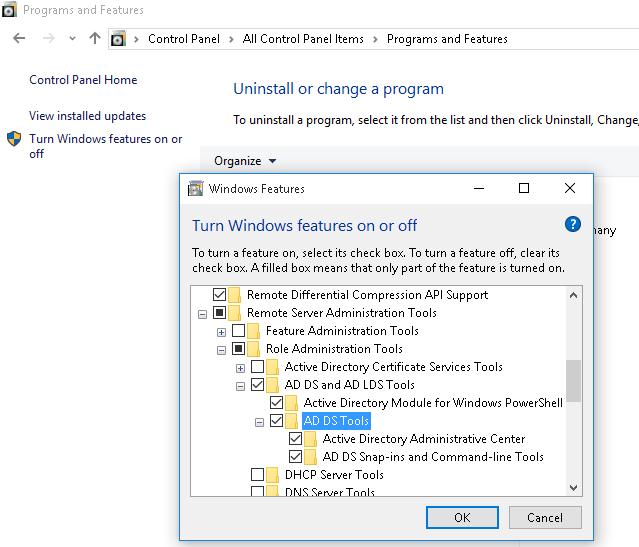
The RSAT package had to be manually downloaded and installed on previous versions of Windows. After that, you need to enable the AD module for PowerShell from the Control Panel: Programs and Features -> Turn Windows features on or off -> Remote Server Administration Tools-> Role Administration Tools -> AD DS and AD LDS Tools.
You must first install the WindowsCompatibility module to use AD cmdlets in PowerShell Core 6.x, 7.x:
Install-Module -Name WindowsCompatibility
Then load the module into your session:
Import-Module -Name WindowsCompatibility
Import-WinModule -Name ActiveDirectory
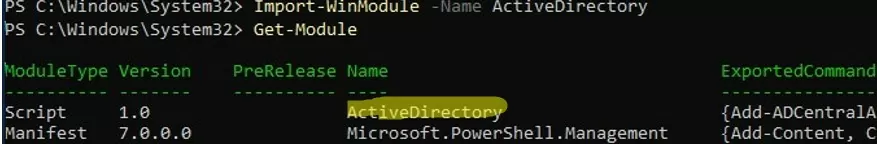
Now you can use AD cmdlets in your PowerShell Core 7.x scripts.
Installing the RSAT-AD-PowerShell Module on Windows Server
On Windows Server, you can install the Active Directory Module for Windows PowerShell from the Server Manager graphical console or by using PowerShell.
You can check that the Active Directory module is installed with the command:
Get-WindowsFeature -Name "RSAT-AD-PowerShell"
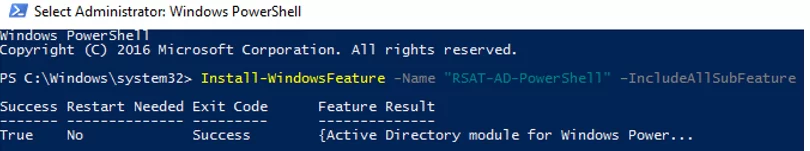
If the module is missing, install it:
Install-WindowsFeature -Name "RSAT-AD-PowerShell" –IncludeAllSubFeature
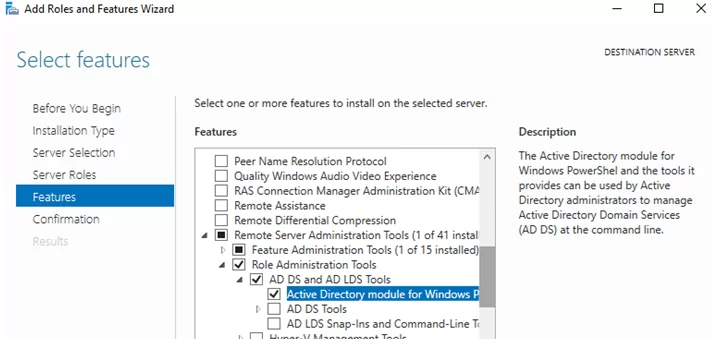
To install the module through the Server Manager, go to Add Roles and Features -> Features -> Remote Server Administration Tools -> Role Administration Tools -> AD DS and AD LDS Tools -> enable the Active Directory module for Windows PowerShell.
You do not need to use a local domain controller session to manage Active Directory by using the RSAT-AD PowerShell module. This module can be installed on any member server or workstation. On AD domain controllers, the module is automatically installed when the Active Directory Domain Services (AD DS) role is deployed (when the server is promoted to a DC).
The module interacts with AD through the Active Directory Web Service that must be running on your domain controller and available to clients on a TCP port 9389. Use the Test-NetConnection cmdlet to verify that this port is not blocked by a firewall on the DC:
Test-NetConnection MUN-DC1 -port 9389
Active Directory Administration with PowerShell
The Active Directory module for Windows PowerShell has a large number of cmdlets for interacting with AD. There are 147 AD PowerShell cmdlets available in the current version of the module for Windows Server 2022/Windows 11.
Check that the module is installed on the computer:
Get-Module -Name ActiveDirectory –ListAvailable
Before you can use the Active Directory module cmdlets, you must import it into your PowerShell session (starting from Windows Server 2012 R2/ Windows 8.1 the module is imported automatically).
Import-Module ActiveDirectory
Make sure that the AD module is loaded in your PowerShell session:
Get-Module
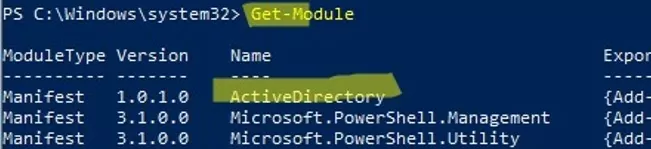
You can display a complete list of available Active Directory cmdlets:
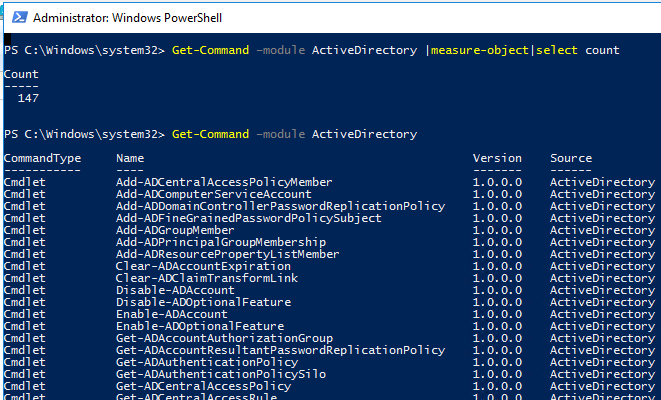
Get-Command –module ActiveDirectory
The total number of cmdlets in the AD module:
Get-Command –module ActiveDirectory |measure-object|select count
Most of the RSAT-AD PowerShell module cmdlets begin with the Get-, Set- or New- prefixes.
- Get– class cmdlets are used to get different information from Active Directory (
Get-ADUser— user properties,Get-ADComputer– computer settings,Get-ADGroupMember— group membership, etc.). You do not need to be a domain administrator to use these cmdlets. Any domain user can run PowerShell commands to get the values of the AD object attributes (except confidential ones, like in the example with LAPS); - Set- class cmdlets are used to set (change) object properties in Active Directory. For example, you can change user properties (Set-ADUser), computer settings (Set-ADComputer), etc. To perform these actions, your account must have write permissions on the objects you want to modify (see the article How to Delegate Administrator Privileges in Active Directory);
- Commands that start with New- allow you to create AD objects (create a user —
New-ADUser, create a group —New-ADGroup, create an Organizational Unit —New-ADOrganizationalUnit); - Cmdlets starting with Add-: add a user to a group (
Add-ADGroupMember), add a Fine-Grained Password Policy (Add-ADFineGrainedPasswordPolicySubject); - Remove- cmdlets are used to delete AD objects
Remove-ADGroup,Remove-ADComputer,Remove-ADUser).
There are specific PowerShell cmdlets that you can use to manage only certain AD components:
Enable-ADOptionalFeature– enable optional AD features (for example, AD Recycle Bin to restore deleted objects);Install-ADServiceAccount– configure managed service account (MSA, gMSA);Search-ADAccount– allows you to find disabled, inactive, locked user and computer accounts in Active Directory;Enable-ADAccount/Disable-ADAccount/Unlock-ADAccount– enable/disable/unlock an account.
By default, the PowerShell cmdlets connect to the nearest domain controller in your environment (LOGONSERVER). With the -Server parameter, you can connect to ADDS on a different domain controller or in a different domain (you can display a list of DCs in another domain using the nltest /dclist:newad.com command).
The -Server parameter is available for nearly all of the module cmdlets. For example
Get-ADuser j.smith -Server mun-dc1.woshub.com
You can also use the -Credential parameter to specify alternative Active Directory user credentials.
$creds = Get-Credential
Get-ADUser -Filter * -Credential $creds
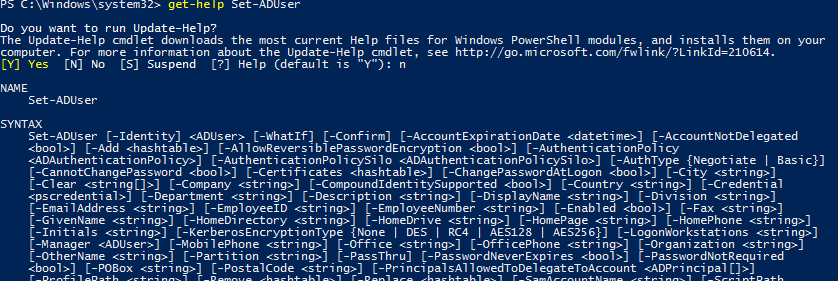
Here is how you can get help on any cmdlet
get-help Set-ADUser
You can display the examples of using Active Directory cmdlets as follows:
(get-help New-ADComputer).examples
Importing Active Directory PowerShell Module from a Remote Computer
It is not necessary to install the AD PowerShell module on all computers. An administrator can remotely import this module from a domain controller (domain administrator privileges are required) or from any other computer.
PowerShell Remoting is used to connect to a remote computer. This requires that Windows Remote Management (WinRM) is enabled and configured on the remote host.
Create a new session with the remote computer that has the AD PowerShell module installed:
$psSess = New-PSSession -ComputerName DC_or_Comp_with_ADPosh
Import the ActiveDirectory module from the remote computer into your local PS session:
Import-Module -PSsession $psSess -Name ActiveDirectory
Now you can run any commands from the Active Directory module on your computer as if the module was installed locally. However, they will be executed on a remote host.
You can add these commands to your PowerShell profile file to automatically import the module from the remote session when you start the powershell.exe console. Run the notepad $profile.CurrentUserAllHosts to open your PS profile file.
You can end a remote session with the command :
Remove-PSSession -Session $psSess
This method of importing the AD module through PowerShell implicit remoting allows you to use PowerShell cmdlets from Linux and MacOS hosts that cannot install a local copy of the module.
You can also >use the Active Directory Module for PowerShell without installing RSAT. To do this, simply copy some files from a computer where the RSAT-AD PowerShell module is installed:
- Directory
C:\Windows\System32\WindowsPowerShell\v1.0\Modules - File
ActiveDirectory.Management.dll - File
ActiveDirectory.Management.resources.dll
Then you need to import the module into your current session:
Import-Module C:\PS\ADmodule\Microsoft.ActiveDirectory.Management.dll
Import-Module C:\PS\ADmodule\Microsoft.ActiveDirectory.Management.resources.dll
After that, you can use all of the AD module cmdlets without installing RSAT.
Common PowerShell Commands for Active Directory
Let’s take a look at some typical administrative tasks that can be performed using the Active Directory for PowerShell cmdlets.
You can find some useful examples of how to use Active Directory for PowerShell module cmdlets on the WOSHub website. Follow the links to get detailed instructions.
New-ADUser: Creating AD Users
To create a new AD user, you can use the New-ADUser cmdlet. You can create a user with the following command:
New-ADUser -Name "Mila Beck" -GivenName "Mila" -Surname "Beck" -SamAccountName "mbeck" -UserPrincipalName "[email protected]" -Path "OU=Users,OU=Berlin,OU=DE,DC=woshub,DC=com" -AccountPassword(Read-Host -AsSecureString "Input User Password") -Enabled $true
For detailed info about the New-ADUser cmdlet (including an example on how to create user domain accounts in bulk), see this article.
Get-ADComputer: Getting Computer Object Properties
To get the properties of computer objects in a particular OU (the computer name and the last logon date), use the Get-ADComputer cmdlet:
Get-ADComputer -SearchBase ‘OU=CA,OU=USA,DC=woshub,DC=com’ -Filter * -Properties * | FT Name, LastLogonDate -Autosize
Add-ADGroupMember: Add Active Directory Users to Group
To add users to an existing security group in an AD domain, run this command:
Add-AdGroupMember -Identity LondonSales -Members e.braun, l.wolf
Display the list of users in the AD group and export it to a CSV file:
Get-ADGroupMember LondonSales -recursive| ft samaccountname| Out-File c:\ps\export_ad_users.csv
Set-ADAccountPassword: Reset a User Password in AD
In order to reset a user’s password in AD with PowerShell:
Set-ADAccountPassword m.lorenz -Reset -NewPassword (ConvertTo-SecureString -AsPlainText “Ne8Pa$$0rd1” -Force -Verbose) –PassThru
How to Unlock, Enable, and Disable Active Directory Accounts?
To disable the AD user account:
Disable-ADAccount m.lorenz
To enable an account:
Enable-ADAccount m.lorenz
Unlock an account after it has been locked by a domain password policy:
Unlock-ADAccount m.lorenz
Search-ADAccount: How to Find Inactive and Disabled AD Objects?
To find and disable all computers in the AD domain that have not logged on for more than 90 days, use the Search-ADAccount cmdlet:
$timespan = New-Timespan –Days 90
Search-ADAccount -AccountInactive -ComputersOnly –TimeSpan $timespan | Disable-ADAccount
New-ADOrganizationalUnit: Create an Organizational Unit in AD
To quickly create a typical Organizational Unit structure in AD, you can use a PowerShell script. Suppose you want to create multiple OUs with states as their names and create typical object containers. It is quite time-consuming to create this AD structure manually through the graphical ADUC snap-in. AD module for PowerShell allows solving this task in seconds (except the time to write the script):
$fqdn = Get-ADDomain
$fulldomain = $fqdn.DNSRoot
$domain = $fulldomain.split(".")
$Dom = $domain[0]
$Ext = $domain[1]
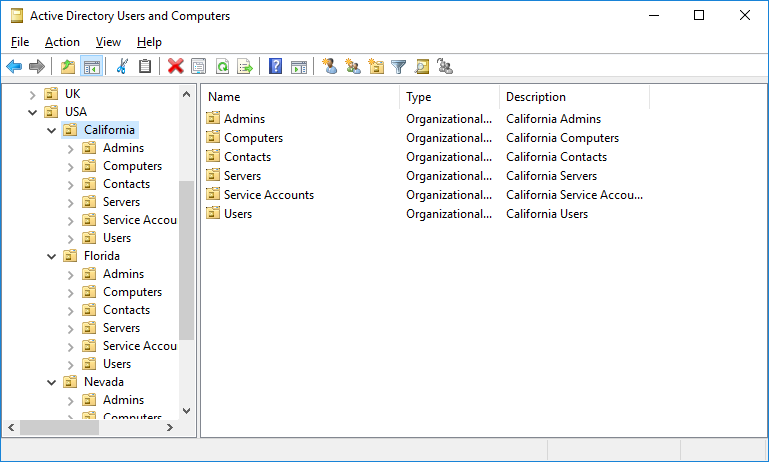
$Sites = ("Nevada","Texas","California","Florida")
$Services = ("Users","Admins","Computers","Servers","Contacts","Service Accounts")
$FirstOU ="USA"
New-ADOrganizationalUnit -Name $FirstOU -Description $FirstOU -Path "DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
foreach ($S in $Sites)
{
New-ADOrganizationalUnit -Name $S -Description "$S" -Path "OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
foreach ($Serv in $Services)
{
New-ADOrganizationalUnit -Name $Serv -Description "$S $Serv" -Path "OU=$S,OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
}
}
After you run the script, you will see the following OU structure in the Active Directory.
To move objects between AD containers, you can use the Move-ADObject cmdlet:
$TargetOU = "OU=Sales,OU=Computers,DC=woshub,DC=com"
Get-ADComputer -Filter 'Name -like "SalesPC*"' | Move-ADObject -TargetPath $TargetOU
Get-ADReplicationFailure: Check Active Directory Replication
You can use the Get-ADReplicationFailure cmdlet to check the status of replication between AD domain controllers:
Get-ADReplicationFailure -Target NY-DC01,NY-DC02
To get information about all DCs in the domain, use the Get-AdDomainController cmdlet:
Get-ADDomainController –filter * | select hostname,IPv4Address,IsGlobalCatalog,IsReadOnly,OperatingSystem | format-table –auto
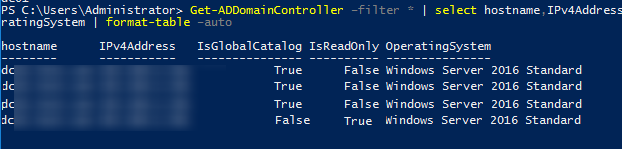
In this article, we looked at how to install and use the Active Directory PowerShell module for AD domain administration. I hope this article will encourage you to further explore this module and start automating most of your AD management tasks.
Any Windows Server administrator must have used the Active Directory Users and Computers (ADUC) Microsoft Management Console on a Domain Controller (DC). Using this console, you can control and manage users, user groups, computers, and the Organizational Units (OUs) in the domain.
The ADUC console is no longer limited to servers anymore. You can install the Active Directory Users and Computers snap-in on a Windows 11 or Windows 10 computer as well, which performs the same functions as the original Server console. This snap-in is part of the Remote Server Administration Tools (RSAT) for Windows operating systems.
We have written separate posts for installing any RSAT tools on Windows 11 and Windows 10. This article focuses on installing specifically the Active Directory Users and computers snap-in on a Windows PC and then using it to manage your domain.
Table of Contents
How to Install Active Directory Users and Computers (ADUC) on Windows
All RSAT tools, including the Active Directory Users and Computers snap-in, allow you to manage the different Active Directory components as if you are on the server itself. This way, you do not always have to access the server, neither physically nor remotely, to perform an action.
You can download and install the Active Directory Users and Computers snap-in using the Settings app, from the Command Prompt, and Windows PowerShell.
Note: On Windows 10 v1803 and older, you must download and install all RSAT tools using the MSI files. You can find the MSI files for your version of Windows here.
Install Active Directory Users and Computers from Settings App
The easiest way to install the ADUC snap-in on a Windows PC is from the settings app. It does involve more steps than the other methods shared below, but this is the only method using the Windows GUI.
Use these steps to install the ADUC snap-in from the Settings app:
-
Navigate to the following:
Settings app >> Apps >> Optional Features
-
Click “View features.”
Add an optional feature -
Search for “Active Directory,” select “RSAT: Active Directory Domain Services and Lightweight Directory Services Tools,” and click Next.
Select Active Directory Users and Computers -
Click “Install.”
Install Active Directory Users and Computers from the Settings app -
Once installed, restart the computer.
The Active Directory Users and Computers snap-in will now be installed. If you prefer installing it using the command line, refer to the sections below. To learn how to use the snap-in, continue reading down.
Install Active Directory Users and Computers from Command Prompt
Below are the simple steps to install Active Directory Users and Computers snap-in using the Command Prompt:
-
Open an elevated Command Prompt instance.
-
Run the following command:
DISM /Online /Add-Capability /CapabilityName:Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0Install Active Directory Users and Computers snap-in using Command Prompt
The ADUC snap-in should now be installed. Run the following command in Command Prompt to confirm that the Active Directory Users and Computers snap-in has been installed:
DISM.exe /Online /Get-CapabilityInfo /CapabilityName:Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
You should see “Installed” in front of Status.
Install Active Directory Users and Computers from PowerShell
Use the following steps to install the Active Directory Users and Computer snap-in using PowerShell:
-
Launch an elevated PowerShell instance.
-
Run the following command to install ADUC:
Add-WindowsCapability -Online -Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0Install Active Directory Users and Computers snap-in using PowerShell
The ADUC snap-in should now be installed. To confirm its status, run the following command in PowerShell:
Get-WindowsCapability -Online | Where-Object {$_.Name -like "RSAT.ActiveDirectory*"}
You should see “Installed” in front of State.
These are all the methods to install the Active Directory Users and Computers snap-in on a Windows 11/10 PC. Let us now continue to see how to use this tool.
How to Use Active Directory Users and Computers
How to Open Active Directory Users and Computers Snap-In
Now that Active Directory Users and Computers is installed, you can open it by searching for it in the Start menu, or running the following in the Run Command box:
dsa.mscAlternatively, you can also open the ADUC snap-in through the Control Panel at the following location:
Control Panel >> System and Security >> Windows Tools
If your computer is connected to a domain and you are logged in from an authorized domain account, then the ADUC snap-in will automatically connect to the server. However, if one is not connected, then you must connect to the Domain Controller.
Connect ADUC to Domain Controller
Use these steps to connect to a Domain Controller. You can also use these to change your domain/Domain Controller.
-
From the ADUC console, click “Action,” and then click “Change Domain Controller.”
Change or connect to Domain Controller The Change Directory Server window will now open.
-
Select the “This Domain Controller or AD LDS instance” radio button, then select the Domain Controller from the give list and click Ok.
Select and connect to Domain Controller
The ADUC will now connect to the Domain Controller and populate the fields.

Now that you are connected to the Domain Controller, you can now begin making changes and managing the different components of the domain.
Manage Users, Computers, Organizational Unit using ADUC

You can now begin adding new users, computers, printers, and Organizational Units to the domain. Simply right-click on the OU that you want to add the new device/user to, expand “New”, and select the element that you want to add.
Once you have selected the element to add, the respective window will open, where you can then configure the component to add.
You can now also use other operators to manage the users, devices, and other elements configured inside the domain directly from your Windows PC.
Additionally, you can also manage what you see inside the snap-in. Click “View” from the top menu and select the things that you want to see. You can then also click “Filter options” to open the advanced viewing options.
The list does not end here. There are a bunch of other management options you can perform directly from the ADUC snap-in on a Windows PC. We suggest that you play around to discover all the options. However, we advise caution and only use the console if you know what you are doing.
What is Active Directory Users and Computers Used For
By now, we have a pretty good understanding of what the ADUC snap-in can be used for. However, there is more to it than meets the eye. The Active Directory Users and Computers RSAT tool can be used to perform the following actions:
- Create and manage user accounts, computers, and Active Directory groups.
- View and edit AD object attributes with ADSI Edit.
- Search for AD objects.
- Change or reset user password in Active Directory.
- Create organizational units and build hierarchical structures for AD objects. You can also delegate administrative permission on these OUs to other domain users.
- Delegate administrative permissions.
- Raise domain functional level, and transfer FSMO roles with PowerShell to another domain controller.
From this, it is understood how useful the ADUC snap-in is for administrators that use Windows client PCs.
Оснастка Active Directory Users and Computers (или ADUC) – это одна из наиболее часто используемых консолей управления объектами в домене Active Directory. Вы можете установить mmc оснастку ADUC как на Windows Server, так и на десктопные Windows 10 и 11. Консоль ADUC входит в состав набора компоненту администрирования Microsoft Remote Server Administration Tools (RSAT). В этой статье мы покажем, как установить и использовать консоль управление Active Directory Users and Computers в Windows.
Содержание:
- Установка оснастки RSAT Active Directory в Windows 10 и 11
- Как пользоваться консолью Active Directory?
- Подключение консоли ADUC к домену из рабочей группы
Установка оснастки RSAT Active Directory в Windows 10 и 11
В современных версиях Windows 10 (начиная с билда 1809) и в Windows 11 инструменты администрирования RSAT устанавливаются онлайн в виде Features on Demand. Чтобы установить инструменты администрирования RSAT Active Directory в Windows 10/11, перейдите в Settings -> Apps -> Optional Features -> Add an optional feature (View features).
Наберите в поисковой строке Active Directory и выберите для установки компонент RSAT: Active Directory Domain Services and Lightweight Directory Services Tool.
Нажмите Next-> Install для начала установки.
Windows подключится к серверам Microsoft, скачает и установит набор инструментов для управления Active Directory (включает в себя графические консоли Active Directory, утилиты командной строки и модуль Active Directory PowerShell).
Либо вы можете установить набор компонентов администрирования AD с помощью PowerShell:
Add-WindowsCapability –online –Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
В изолированных сетях, в которых нет доступа в интернет, вы можете установить инструменты RSAT Active Directory с помощью ISO образа Windows 10 Features on Demand (образ FoD можно скачать из кабинета лицензирования Microsoft).
Для установки инструментов Active Directory, из сетевого каталога с содержимым образа FoD выполните команду:
Add-WindowsCapability -Online -Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 -LimitAccess -Source \\fs01\Distr\Windows10-FOD\
В предыдущих билдах Windows 10, а также в Windows 8.1, установить RSAT можно с помощью MSU обновления. Скачать RSAT можно здесь:
- RSAT для Windows 10 1803/1709 — https://www.microsoft.com/en-us/download/details.aspx?id=45520
- RSAT для Windows 8.1 — https://www.microsoft.com/en-us/download/details.aspx?id=39296
Скачайте версию файла RSAT в зависимости от разрядности вашей операционной системы и установите его. Дважды щелкните по файлу для начала установки:
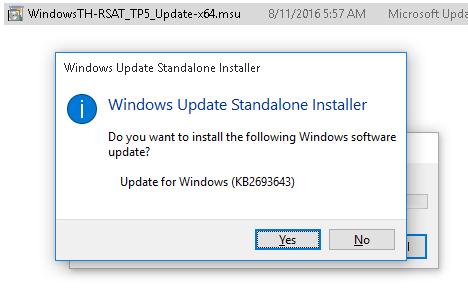
Или установите MSU файл RSAT из командной строки в «тихом» режиме:
wusa.exe c:\Install\WindowsTH-RSAT_TP5_Update-x64.msu /quiet /norestart
После окончания установки RSAT нужно перезагрузить компьютер.
Осталось активировать необходимый функционал RSAT. Для этого:
- Щелкните ПКМ по кнопке Start и выберите Control Panel (Панель управления)
- Выберите Programs and Features (Программы и компоненты)
- В левой панели нажмите кнопку Turn Windows features on or off
- В дереве компонентов разверните Remote Server Administration Tools-> Role Administration Tools -> AD DS and AD LDS Tools
- Отметьте раздел AD DS Tools и нажмите OK.
Установка оснастки ADUC также может быть выполнена из командой строки. Последовательно выполните 3 команды:
dism /online /enable-feature /featurename:RSATClient-Roles-AD
dism /online /enable-feature /featurename:RSATClient-Roles-AD-DS
dism /online /enable-feature /featurename:RSATClient-Roles-AD-DS-SnapIns
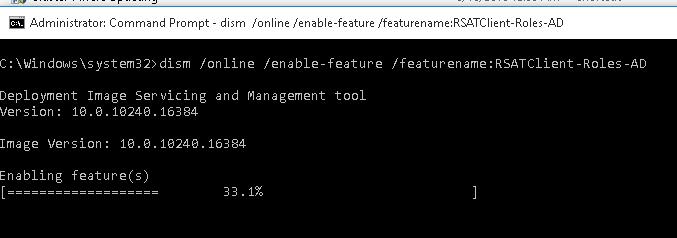
После установки оснасток управления, в разделе Administrative Tools панели управления (Control Panel\System and Security\Windows Tools) появится ссылка на консоль Active Directory Users and Computers.
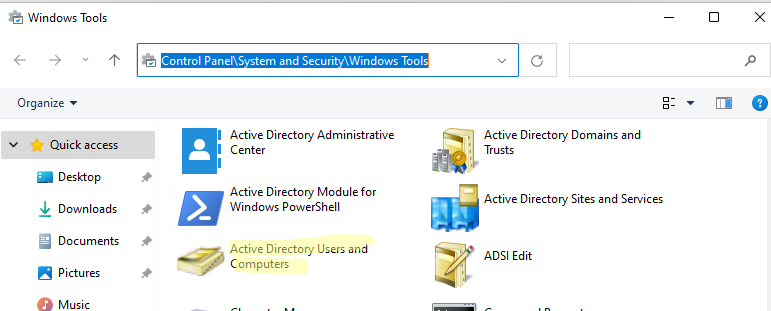
Как пользоваться консолью Active Directory?
Чтобы запустить консоль ADUC, щелкните по ярлыку в панели управления или выполните команду:
dsa.msc
Все аутентифицированные пользователи домена могут использовать консоль ADUC для просмотра объектов Active Directory.
Если ваш компьютер состоит в домене Active Directory, то консоль ADUC подключится к контролеру домена, на основании текущего Logon сервера. Имя контроллера домена, с которого вы получаете информации указано в верху.
Вы можете подключиться к другому контроллеру домена AD или другому домену, щелкнув по корню консоли и выбрав пункт в контекстном меню.
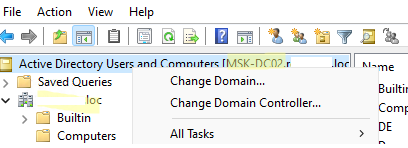
В консоли Active Directory отображается древовидная структура организационных юнитов (Organizational Unit, OU) вашего домена (и отдельный раздел с сохраненными запросами/ Saved Queries AD).
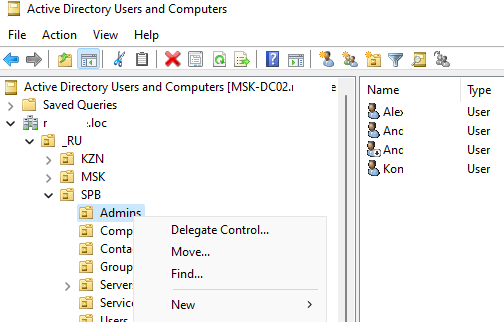
Администратор домена может создавать контейнеры (OU) в соответствии с физической или логической структуры предприятиями. С помощью контекстного меню можно создать новые объекты в AD (пользователей, группы, компьютеры, OU, контакты), переименовать, переместить или удалить объекты. В зависимости от типа объекта, который вы выбрали пункты контекстного меню могут отличаться.
Например, у пользователя есть опции на сброс пароля в AD или блокировку/разблокировку учетной записи.
Вы можете использовать контекстное меню Search для поиска объектов в AD.
Администратор может делегировать права на создание/редактирование/удаление объектов в Active Directory другим пользователям или группам.
С помощью меню View -> Add/Remove columns можно добавить атрибуты объектов, которые вы хотите отображать в консоли ADUC.
В консоли ADUC можно посмотреть или изменить свойства объектов домена. Например, можно открыть свойства пользователя и изменить его настройки. Часть свойств пользователя находится на соответствующих вкладках, а полный список атрибутов пользователя доступен на вкладке редактора атрибутов AD (Attribute Editor).
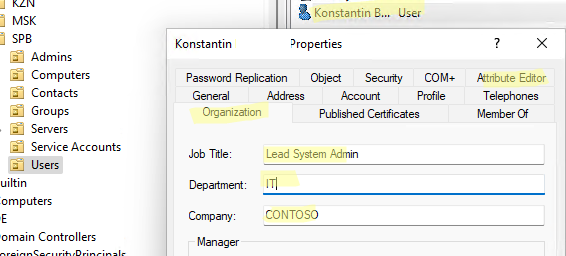
Можно добавить отдельную вкладку с фотографией пользователя AD.
Чтобы показывать системные контейнеры и свойства объектов в оснастке AD (по умолчанию скрыты), включите опцию View -> Advanced features.
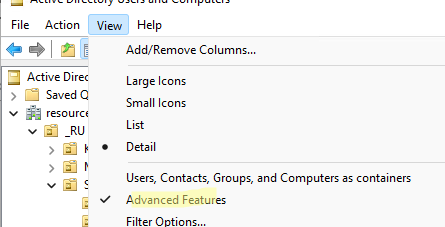
После этого у всех объектов появится ряд системных вкладок. Например, на вкладке Object можно получить каноническое имя объекта, дату создания учетной записи и включить опцию защиты от удаления (protect object from accidental deletion).
Подключение консоли ADUC к домену из рабочей группы
Если вы хотите подключится консолью ADUC к контроллеру домена с компьютера, который не включен в домен (состоит в рабочей группе), воспользуйтесь таким методом:
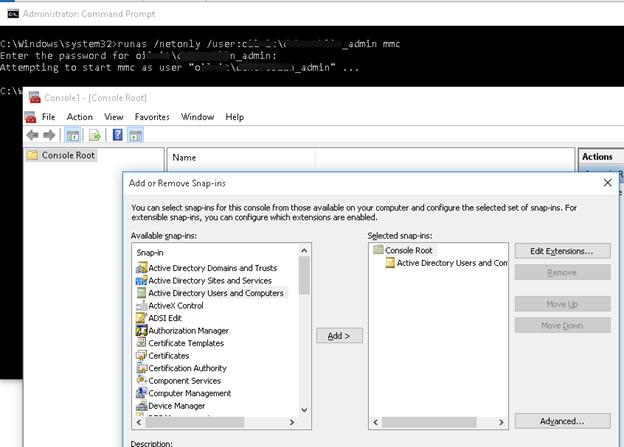
- Запустите командную строку и выполните команду запуска оснастки от имени другого пользователя:
runas /netonly /user:winitpro\aaivanov mmc - В пустой консоли MMC выберите File->Add/Remove Snap-In
- Перенесите оснастку Active Directory Users and Computers в правую панель и нажмите Add;
- Чтобы подключится к домену, щелкните по корню консоли и выберите Change domain. Укажите имя домена.
В результате консоль ADUC подключится к контроллеру домена, получит и отобразит структуру контейнеров (OU) данного домена Active Directory.
One of the main tools for performing administrative tasks in an Active Directory domain is the Active Directory Users and Computers (ADUC) MMC snap-in. The ADUC is a Microsoft Management Console snap-in dsa.msc which is used to manage users, groups, computers, and Organizational units in the AD domain.
In this article, we will look at how to install the Active Directory Users and Computers console on computers running Windows Server and desktop editions of Windows 10 and 11.
Installing Active Directory Users and Computers Snap-in on Windows Server
The ADUC console is automatically installed on a Windows server when it’s promoted to the domain controller as part of the Active Directory Domain Services (AD DS) role deployment. You can manually install the ADUC snap-in on any Windows Server member host.
You can install ADUC console on Windows Server 2022/2019/2016 using Server Manager (Add roles and features > Features > Remote Server Administration Tools > Role Administration Tools > AD DS and AD LDS Tools > AD DS Tools > AD DS Snaps-Ins and Command Line Tools) or with the PowerShell command:
Install-WindowsFeature -Name RSAT-ADDS-Tools

Check that the ADUC console is installed on Windows Server:
Get-WindowsFeature -Name RSAT-ADDS-Tools

How to Install ADUC on Windows 10 and 11
An ADUC snap-in can be installed as part of the Remote Server Administration Tools (RSAT) on the Pro and Enterprise editions of Windows 10 and Windows 11 (but not on the Home editions). You can install ADUC on Windows 10 and 11 by using the Settings app or with PowerShell.
Enable Active Directory Users and Computers Console on Windows 10 and 11
On modern versions of Windows 10 and 11 (with build 1809 and later), you can install the ADUC console from the modern Settings app.
- Press the Start menu > Settings > System;
- Select Optional Features > Add a feature;
- From the list of optional features, select RSAT: Active Directory Domain Services and Lightweight Directory Tools, and press Install.
- Windows will download the ADUC RSAT binary files and install them on your computer.
- You will need to restart your computer when the RSAT installation is complete.
The RSAT was distributed as a separate MSU update file in previous versions of Windows. For example, to install RSAT on Windows 10 1803, you must download and install the KB2693643 update. You can then enable a specific RSAT option using the Control Panel > Turn Windows Features On or Off applet (optionalfeatures.exe).
Install the ADUC Snap-in on Windows 10 or 11 Using PowerShell
You can use PowerShell to install the Active Directory console on Windows 10 and 11. Open an elevated PowerShell prompt and run the command to check whether the RSAT Active Directory feature is installed on your computer:
Get-WindowsCapability -Online | Where-Object {$_.Name -like "RSAT.ActiveDirectory*"}

In this case the RSAT: Active Directory Domain Services and Lightweight Directory Services Tools feature is not installed (State > NotPresent).
If the RSAT ActiveDirectory Tools feature is missing, you can install it:
Add-WindowsCapability -Online -Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0

You can also use the DISM command to install the RSAT ADUC feature:
DISM /Online /Add-Capability /CapabilityName:Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0

Check the AD RSAT status. The State should be changed to Installed.

Note. The PowerShell Active Directory module is also installed with the ADUC console.
Unable to Install RSAT Active Directory on Windows
The RSAT components in the latest versions of Windows are delivered as Features on Demand (FoD). Windows doesn’t store the local RSAT binaries on a local drive; instead, it downloads the RSAT files from the Microsoft Update servers. If your computer is in an isolated (disconnected) environment, you will receive an error when you try to install the ADUC snap-in:
0x800f0954 No features to install
You can use the FoD ISO image to install the RSAT components on offline computers. FoD DVD medias is available for download from your Volume License Servicing Center (VLSC) or on my.visualstudio.com.

Download and mount the FoD ISO image to a virtual drive (for example, to drive F:). You can then install the ADUC feature from local media using the command:
Add-WindowsCapability -online -name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 -source -Source "F:\" –LimitAccess
If you are using WSUS or SCCM to deploy Windows updates to client devices, you must enable the special GPO option to correctly install Features on Demand (including ADUC) on computers.
- Open the local Group Policy Editor (gpedit.msc) and go to Computer Configuration > Administrative Templates > System;
- Enable the GPO option Specify settings for optional component installation and component repair and check the Download repair content and optional features directly from Windows Update instead of Windows Server Update Services (WSUS);
- Update the Group Policy settings on the computer by using the command: gpupdate /force.
Without this option, Windows 11 will try to get RSAT from your local Windows Update Server (errors 0x8024402c and 0x800f081f).
How to Open and Use Active Directory (DSA.msc) Snap-in on Windows
To run the Active Directory snap-in on Windows 11, go to Start Menu > All Programs > Windows Tools.
On Windows 10 (and previous versions) the AD Management snap-ins are available in the Administrative Tools section of the Control Panel.

As you can see, it refers to the MMC console %SystemRoot%\system32\dsa.msc.
This means that you can quickly open the ADUC console by pressing Win+R, typing dsa.msc and clicking OK.

If your computer is joined to the Active Directory domain, the ADUC console will automatically connect to the nearest DC in your Active Directory site.
If the console can’t find the domain controller, you can use the PowerShell command to get the name of your LogonServer:
$env:LOGONSERVER
Right-click on the root in the ADUC console and select Change Domain Controller. Select the name of your logon DC from the list.
Always use the nearest domain controller when managing Active Directory from ADUC. The RSAT console may become slow when working with a domain controller at a remote site.
If you want to connect to AD using the dsa.msc snap-in from a non-domain joined computer, you must:
- Run the command:
runas /netonly /user:Domain_Name\Domain_USER mmc
- Select File > Add/Remove Snap-In;
- Add Active Directory Users and Computers snap-In to the right pane and press OK;
- Connect to the domain with right-click on ADUC > Connect to the domain and enter the domain name.
The ADUC snap-in should display your Active Directory domain structure.

You will see a standard set of Active Directory OUs and containers:
- Saved Queries — saved search criteria for quick searches against Active Directory (LDAP query supported);
- Builtin — built-in user accounts;
- Computers — default container for computer accounts;
- Domain Controllers — default container for domain controllers;
- ForeignSecurityPrincipals — contains information about objects from trusted external domains;
- Users — default container for user accounts.
Depending on the domain structure, the ADUC console may contain other containers. Some AD containers are not displayed by default. To display them, select View > Advanced Features in the top menu.

In the ADUC console, you can perform the following actions:
- Create and manage user accounts, computers, and Active Directory groups;
- View and edit AD object attributes with ADSI Edit;
- Search for AD objects;
- Change user password in Active Directory or reset it;
- Create Organizational Units and build hierarchical structures for AD objects. Enable or disable OU accidental deletion protection;
- Delegate administrative permission to OUs to non-admin domain users;
- Raise domain functional level, and move FSMO roles to another domain controller.
Cyril Kardashevsky
I enjoy technology and developing websites. Since 2012 I’m running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.