Hashcat is my favorite password cracker. You can use it on any operating system or distribution, but it’s often easier to use Windows to avoid drivers issues (especially with a recent GPU). Anyway, I will explain how to install it on Windows in this tutorial.
Hashcat is officially supported on Windows, binaries files can be downloaded on the official website directly. Once the files extracted, Hashcat can be used directly in the command prompt, there is no installation required.
If you are new to this, it might not be obvious to you, but don’t worry, I’ll explain everything in this step-by-step tutorial.

Master Linux Commands
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
Hide your IP address and location with a free VPN:
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It’s free. Forever.
Here are the required steps to install Hashcat on Windows:
- Download the latest Hashcat version from the official website.
- Extract the files on your computer.
- Open a command prompt and run hashcat in command line.
I will now explain each step in details.
Download Hashcat
The first step is to download the latest Hashcat version. It’s available on their official website:
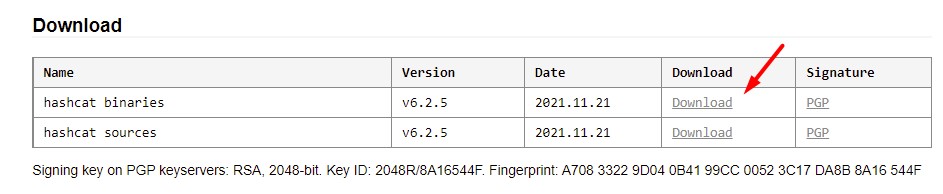
- Go to the Hashcat website homepage.
- Find the binaries and click on “Download” to get the archive on your computer.
The file is an archive, so the next step will be to extract the files before using them.
Extract the files
The files are compressed with 7zip. If you can’t open the archive, you might need to install it first:
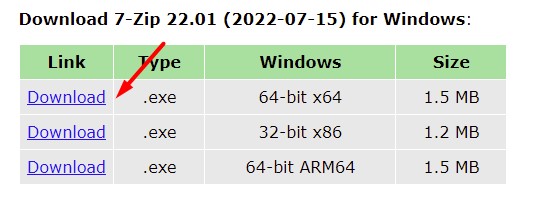
- Go to the 7zip website.
- Download the file corresponding to your operating system (the first link should be fine if your computer is recent, or use the 32-bit version if you have any doubt).
- Once downloaded, double-click on the file to install 7zip on your computer.
Follow the installation wizard, keep the default options.
Once done, you should be able to open the Hashcat archive and extract the files.
Click on the “Extract” button in the top bar:
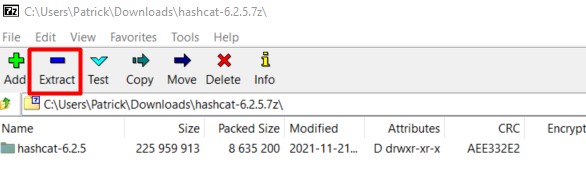
I recommend choosing a different path for the extract location. I don’t know you, but in my case, I tend to delete everything in the “Downloads” folder from time to time, and if I keep hashcat there, I will need to reinstall it eventually.
So, for the example, I’m extracting the files to C:\hashcat, but you can put them wherever you want:
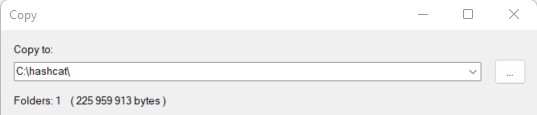
Remember the files location, as you’ll have to go to this path on the next step.
Run Hashcat for the first time
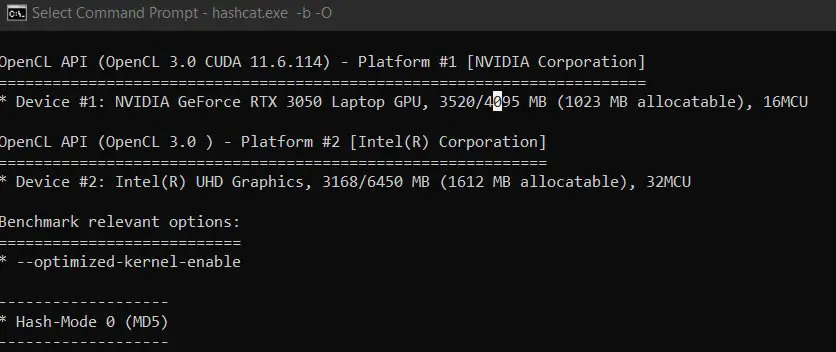
We are almost done, we’ll just make sure everything is working as expected:
This command will run a benchmark of your system, telling you the decryption rate you can expect on this computer, but also showing errors if there is something misconfigured on your system (like missing GPU drivers).
How to use Hashcat on Windows
If the benchmark command is working correctly, you can now use Hashcat on your Windows computer with the same commands as on Linux. It’s the same thing.
I already have several tutorials on this topic on the website, so I won’t repeat myself here, but if you need further assistance, feel free to read these tutorials:
- Is MD5 Easy to Crack? (and how long does it really takes)
- How to Brute Force a Password? (MD5 Hash)
- How to Install and Use Hashcat to Decrypt MD5? (Tutorial)
Hashcat FAQ
Is there a GUI for Hashcat?
Hashcat doesn’t include a graphic interface by default, but a few projects exist with the goal to add an interface to it, like the hashcat GUI toolkit (Windows interface) or Crackerjack (web interface).
Hide your IP address and location with a free VPN:
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It’s free. Forever.
Is Hashcat cross-platform?
Hashcat can run on most operating systems (Linux, Windows and macOS). The installation is slightly different on each system, but the command usage is the same on all platforms.
You can find my guide on how to install Hashcat on Ubuntu there.
How to install OpenCL on Windows?
Running hashcat on Windows require the latest drivers for your OpenCL device (your GPU). AMD and Nvidia official drivers include OpenCL by default, and for Intel GPU you have to install an additional package (link here).
If you experience any issue, make sure you installed the latest version of your graphic card driver, downloading it from the official website.
Installing this on Linux could be a nightmare with some distributions and hardware, but on Windows it’s pretty straightforward (in theory).
Hi, my name is Patrick, I’m a web developer and network administrator. I have always been interested in security, and I created this website to share my findings with you.
In today’s digital age, the protection of sensitive information is of utmost importance. Whether it’s guarding our personal data or securing our online accounts, passwords play a vital role in safeguarding our digital lives. But have you ever wondered how secure your passwords really are? Welcome to “Unlocking the Power of Password Cracking:
A Step-by-Step Guide to Installing Hashcat on Windows.” In this comprehensive guide, we will take you through the fascinating world of password cracking and introduce you to Hashcat, a powerful tool used by ethical hackers and security professionals to test the strength of passwords.
Whether you’re a curious tech enthusiast wanting to enhance your knowledge or an aspiring cybersecurity professional looking to sharpen your skills. This guide will provide you with the essential knowledge and step-by-step instructions to get started with Hashcat on Windows. Get ready to delve into the world of password cracking and unlock the secrets to stronger digital security!
Complete Guide to Using Mask Attack With Hashcat
Understanding Hash Functions and Encryption
To comprehend the fundamentals of password cracking, it’s crucial to understand the concept of hash functions and encryption. A hash function is a mathematical algorithm that takes an input (in this case, a password) and generates a fixed-size string of characters, known as the hash value or hash code.
This process is irreversible, meaning you cannot derive the original password from the hash value alone. Encryption, on the other hand, involves transforming data into an unreadable format using an encryption key. Hash functions and encryption are essential components of password security, as they ensure that passwords are not stored in plain text.
However, with the advancement in computing power, traditional hashing algorithms have become vulnerable to various hacking techniques. One of the most prevalent methods used by ethical hackers and security professionals to assess password strength is password cracking. Password cracking involves attempting to guess or discover passwords by systematically testing all possible combinations or using precomputed tables of password hashes.
Hashcat, the subject of this guide, is a powerful password cracking tool that utilizes the computing power of modern GPUs to accelerate the cracking process. By understanding the inner workings of hash functions and encryption, you’ll be better equipped to grasp the significance of tools like Hashcat in evaluating the security of passwords.
What is Hashcat?
Hashcat is an open-source, advanced password recovery tool used for password cracking. Developed by Jens “Atom” Steube, Hashcat is renowned for its speed and versatility in cracking a wide range of hash types, including MD5, SHA-1, NTLM, and many others.
It leverages the power of modern GPUs to achieve unparalleled processing speeds, making it a go-to tool for security professionals and researchers. Hashcat supports various attack modes, including dictionary attacks, mask attacks, hybrid attacks, and rule-based attacks, providing flexibility and customization options to suit different cracking scenarios. Whether you’re testing the strength of passwords for an organization or conducting research on password security, Hashcat is a valuable tool in your arsenal.
Benefits of Using Hashcat for Password Cracking
Using Hashcat for password cracking offers several advantages over other password recovery tools. Firstly, Hashcat is highly optimized for GPU acceleration, allowing it to perform password cracking at lightning-fast speeds. Modern GPUs have thousands of cores, which Hashcat harnesses to perform parallel processing, significantly reducing the time required for cracking passwords compared to CPU-based approaches. Additionally, Hashcat supports distributed cracking, enabling multiple systems to work together in a coordinated manner, further enhancing cracking speed and efficiency.
Another notable benefit of Hashcat is its extensive hash type support. It can crack a wide range of hash algorithms commonly used in various operating systems, databases, and applications. This versatility makes Hashcat a valuable tool for assessing password security in diverse environments. Moreover, Hashcat allows for highly customizable attack modes, enabling users to tailor their cracking strategies based on specific requirements. From dictionary attacks to rule-based attacks that apply transformation rules to wordlists, Hashcat provides flexibility to adapt to different cracking scenarios.
System Requirements for Installing Hashcat on Windows
Before diving into the installation process, it’s essential to ensure that your system meets the necessary requirements for running Hashcat. Since Hashcat leverages GPU acceleration, having a compatible GPU is crucial. Ideally, you should have a modern NVIDIA or AMD GPU with CUDA or OpenCL support. Hashcat’s performance varies depending on the GPU model, so it’s recommended to use a high-end GPU for optimal cracking speed. Additionally, you’ll need a Windows operating system (Windows 7 or later) and the latest GPU drivers installed.
Apart from the hardware requirements, you’ll also need to have the appropriate software dependencies installed. Hashcat relies on a few libraries, namely, OpenCL runtime, OpenSSL, and zlib. These libraries are typically bundled with the GPU drivers, but you may need to install them separately if required. Ensuring that your system meets these requirements will pave the way for a smooth installation and usage of Hashcat on Windows.
Now that we have a solid understanding of the concepts and benefits of using Hashcat, let’s walk through the step-by-step process of installing Hashcat on a Windows system. Follow these instructions carefully to set up Hashcat and get ready for password cracking.
1. Download Hashcat: Visit the official Hashcat website (https://hashcat.net/hashcat/) and download the latest version of Hashcat for Windows. Choose the appropriate binary package based on your system architecture (32-bit or 64-bit).

2. Extract the Hashcat Archive: Once the download is complete, extract the contents of the Hashcat archive to a location of your choice. You can use a file archiving utility like 7-Zip to extract the files.
3. Install GPU Drivers: Ensure that you have the latest GPU drivers installed on your system. Visit the respective GPU manufacturer’s website (NVIDIA or AMD) to download and install the latest drivers compatible with your GPU model.
4. Open a Command Prompt: Press `Win + R` to open the Run dialog box, type `cmd`, and press Enter. This will launch the Command Prompt.
5. Navigate to the Hashcat Directory: In the Command Prompt, navigate to the directory where you extracted the Hashcat files using the `cd` command. For example, if you extracted the files to the `C:\Hashcat` directory, you would use the command `cd C:\Hashcat`.
6. Test Hashcat Installation: To verify that Hashcat is installed correctly, run the command `hashcat --version`. If Hashcat is installed properly, you should see the version information displayed in the Command Prompt.
Congratulations! You have successfully installed Hashcat on your Windows system. Now that Hashcat is up and running, let’s explore some additional configurations and techniques to maximize its performance and effectiveness.
Configuring Hashcat for Optimal Performance
While Hashcat works out of the box, tweaking certain configurations can enhance its performance and improve the chances of cracking passwords. Here are a few key configurations to consider:
1. **Choosing the Right Attack Mode**: Hashcat supports various attack modes, each with its own strengths and weaknesses. Depending on the nature of the passwords you’re cracking and the available information, you can select the most suitable attack mode. For example, dictionary attacks are effective when you have a list of potential passwords, while mask attacks are useful when you have knowledge about the password pattern.
2. **Optimizing Workload Distribution**: Hashcat allows you to distribute the workload across multiple GPUs or systems, improving cracking speed and efficiency. By utilizing distributed computing, you can harness the power of multiple GPUs or systems working in parallel.
3. **Fine-Tuning Rule-Based Attacks**: Rule-based attacks in Hashcat involve applying transformation rules to wordlists to generate variations of potential passwords. These rules can significantly increase the chances of cracking passwords by generating permutations based on common patterns. Experimenting with different rule sets and combinations can yield better results in cracking passwords.
By understanding and configuring these aspects of Hashcat, you can maximize its potential and achieve faster and more accurate password cracking results.
Generating and Using Wordlists for Password Cracking
Wordlists are a crucial component of password cracking, as they form the basis for dictionary attacks and rule-based attacks. A wordlist is essentially a text file containing a list of potential passwords that Hashcat will attempt to crack. While Hashcat comes with a default wordlist, creating custom wordlists tailored to the target environment can significantly improve cracking success rates. Here are a few methods for generating and using wordlists in Hashcat:
1. Using Prebuilt Wordlists:
Numerous prebuilt wordlists are available online, covering various categories such as common passwords, leaked passwords, and specific terms related to industries or interests. These wordlists can be used directly with Hashcat or serve as a starting point for further customization.
2. Customizing Wordlists:
Customizing wordlists involves tailoring them to the target environment or specific scenarios. This can be done by adding domain-specific terms, personal information, or relevant keywords that might be used in passwords. Combining prebuilt wordlists and customizing them can enhance the chances of cracking passwords in specific contexts.
3. Applying Transformation Rules:
Hashcat allows you to apply transformation rules to wordlists, generating variations of potential passwords. These rules can manipulate the words in the wordlist by capitalizing letters, adding common suffixes or prefixes, or substituting characters with similar-looking symbols. By applying rules, you can significantly expand the password search space and increase the chances of cracking complex passwords.
Generating and utilizing wordlists effectively is a skill that comes with experience. As you gain more knowledge and exposure to different password cracking scenarios, you’ll be able to create targeted wordlists and fine-tune your cracking strategies for optimal results.
Advanced Techniques for Password Cracking with Hashcat
While the previous sections covered the fundamentals of password cracking and the basic usage of Hashcat, there are several advanced techniques that can further enhance your password cracking endeavors. These techniques involve utilizing additional resources, employing specialized hardware, or leveraging specific attack methodologies. Here are a few advanced techniques to consider:
1. Using Rainbow Tables:
Rainbow tables are precomputed tables containing a vast number of password hashes and their corresponding plaintext passwords. These tables can significantly speed up the cracking process by eliminating the need to compute hashes for each password guess. Hashcat can utilize rainbow tables to crack passwords quickly, especially for common hash types. However, rainbow tables can be resource-intensive and require substantial storage space.
2. Utilizing Distributed Computing:
As mentioned earlier, Hashcat supports distributed computing, allowing multiple systems or GPUs to work together on a cracking task. By pooling the computational power of multiple resources, you can achieve faster cracking speeds and distribute the workload more efficiently.
3. Using Hardware Accelerators:
In addition to GPUs, Hashcat can utilize specialized hardware accelerators, such as FPGA (Field-Programmable Gate Array) or ASIC (Application-Specific Integrated Circuit) devices. These hardware solutions are designed to perform password cracking tasks efficiently and can offer significant speed improvements compared to traditional CPUs or GPUs.
4. Combining Attack Modes:
Hashcat allows you to combine different attack modes, such as dictionary attacks, mask attacks, and rule-based attacks, to create hybrid attacks. Hybrid attacks leverage the strengths of multiple attack modes, increasing the chances of cracking complex passwords. Experimenting with different combinations can yield better results in certain cracking scenarios.
By exploring these advanced techniques and staying up-to-date with the latest advancements in password cracking, you can further refine your skills and become a proficient password cracker.
Best Practices for Password Security
While password cracking can be a fascinating and educational endeavor, it’s essential to remember the importance of password security. As individuals and organizations, we should strive to implement robust password practices to protect our digital assets. Here are some best practices to keep in mind:
1. Use Strong and Unique Passwords:
Create passwords that are long, complex, and unique for each account. Avoid using common words, personal information, or easily guessable patterns. Consider using a password manager to generate and store strong passwords securely.
2. Enable Multi-Factor Authentication:
Whenever possible, enable multi-factor authentication (MFA) for your online accounts. MFA adds an extra layer of security by requiring additional verification, such as a fingerprint or a one-time password, in addition to your password.
3. Regularly Update Passwords:
Periodically update your passwords, especially for critical accounts or after a potential security breach. Changing passwords regularly minimizes the risk of unauthorized access to your accounts.
4. Stay Informed About Password Security:
Stay updated on the latest trends, techniques, and vulnerabilities related to password security. By staying informed, you’ll be better equipped to protect yourself and make informed decisions regarding password practices.
By following these best practices and adopting a security-conscious mindset, you can significantly enhance your personal and organizational password security.
Conclusion
In this comprehensive guide, we have explored the fascinating world of password cracking and introduced you to Hashcat, a powerful tool used by ethical hackers and security professionals. From understanding hash functions and encryption to installing and configuring Hashcat on Windows, we have covered the essential aspects of password cracking.
We have delved into advanced techniques, such as utilizing wordlists, optimizing performance, and exploring hybrid attacks. Additionally, we have emphasized the importance of password security and outlined best practices to protect your digital assets.
As you embark on your journey into the world of password cracking, remember to always approach this field ethically and responsibly. Password cracking is a valuable tool for evaluating the strength of passwords and enhancing digital security.
By arming yourself with knowledge, staying up-to-date with advancements, and practicing good password hygiene, you can contribute to a safer digital world. So, go forth and unlock the secrets to stronger digital security with Hashcat!
Read Also:
20 Best Ethical Hacking Tools You Need to Know
The 9 Best Penetration Testing Tools for Linux
John the Ripper Password Cracking Tool: A Comprehensive Guide
Reading Time: 5 minutes
Hashcat is a powerful and fast password cracking tool widely used by security professionals, ethical hackers, and penetration testers. It supports a variety of hash algorithms such as MD5, SHA-1, SHA-256, bcrypt, and others, allowing users to crack encrypted passwords and test the security of systems. Hashcat’s ability to utilise both CPU and GPU for cracking makes it one of the fastest tools in the industry. In this comprehensive guide, we will walk you through the process of installing Hashcat on a Windows operating system.
Windows is one of the most popular operating systems, and Hashcat‘s compatibility with it makes it accessible to a wide range of users. Installing Hashcat on a Windows machine allows you to leverage the power of both the CPU and GPU to perform password cracking tasks more efficiently. Windows also offers compatibility with many popular graphics cards (from both AMD and NVIDIA), which can significantly accelerate Hashcat’s performance.
Whether you’re conducting a penetration test, performing security research, or recovering a lost password, Hashcat on Windows is a valuable tool. The installation process is straightforward, and once set up, Hashcat provides all the features you need to crack various types of password hashes effectively.
Prerequisites for Installing Hashcat on Windows
Before you begin the installation of Hashcat, there are a few things to ensure:
- System Requirements: Make sure your system meets the necessary hardware requirements. While Hashcat can run on both CPU and GPU, a powerful GPU (either from AMD or NVIDIA) will greatly accelerate cracking times.
- Graphics Drivers: Hashcat uses your system’s GPU to speed up the cracking process. Therefore, it’s crucial that you have the appropriate graphics card drivers installed for either AMD or NVIDIA GPUs.
- Operating System: This guide focuses on installing Hashcat on Windows 10 or Windows 11. The installation process may vary slightly for older versions of Windows.
- Administrator Privileges: You’ll need administrator privileges to install software and drivers on your Windows system.
- A Hash File: For testing Hashcat after installation, you’ll need a hash file. This file typically contains encrypted passwords that Hashcat will attempt to crack.
Methods for Installing Hashcat on Windows
There are two main methods for installing Hashcat on Windows: using precompiled binaries or building it from source. Most users will prefer the precompiled binary method due to its simplicity, but for those who want the latest features or need to make modifications, building from source is a viable option.
Method 1: Installing Hashcat Using Precompiled Binaries
The easiest and most straightforward way to install Hashcat on Windows is by downloading the precompiled binaries from the official Hashcat website. This method ensures that you are using a stable, up-to-date version of Hashcat, and it avoids the complexities of compiling from source.
Step-by-Step Guide:
- Download Hashcat Binaries: Visit the official Hashcat website to download the latest stable version of Hashcat for Windows. The download will be available as a
.7zarchive. You can also download it directly using a browser or use the followingwgetcommand if you have a command line tool:wget https://hashcat.net/files/hashcat-<version>.7z
Replace<version>with the version number (e.g.,6.2.6). - Extract the Archive: Once the
.7zarchive is downloaded, you will need to extract it using a tool like 7-Zip or WinRAR. If you don’t have 7-Zip installed, you can download it from here.After installing 7-Zip, right-click the downloaded file, select “7-Zip”, and choose “Extract Here” or “Extract to [folder]”. - Navigate to the Extracted Folder: After extraction, you’ll have a folder containing the Hashcat executable and associated files. Open the folder to locate the
hashcat.exefile. This is the main executable you’ll use to run Hashcat. - Install GPU Drivers (Optional): To use GPU acceleration, it’s crucial to install the appropriate drivers for your graphics card:
- For NVIDIA GPUs: Install the latest NVIDIA drivers from NVIDIA’s website, ensuring that you also install CUDA Toolkit and OpenCL support for enhanced performance.
- For AMD GPUs: Install the latest AMD drivers from AMD’s website, and ensure that OpenCL is supported.
- Verify the Installation: After extracting the files and installing the drivers, open a Command Prompt window in the folder containing
hashcat.exeby holding the Shift key and right-clicking the folder. Select “Open Command Window Here” or “Open PowerShell Window Here”.To check if Hashcat is installed correctly, type the following command and press Enter:hashcat --version
If installed correctly, the command will output the current version of Hashcat installed on your system. - Run Hashcat: Now, you are ready to start using Hashcat. For example, if you want to crack an MD5 hash using a dictionary attack, you can run the following command:
hashcat -m 0 -a 0 hashfile.txt wordlist.txt
Here:-m 0specifies the hash type (0 is for MD5).-a 0specifies the attack mode (0 is for a dictionary attack).hashfile.txtis your file containing hashes.wordlist.txtis your dictionary file.
Method 2: Building Hashcat from Source on Windows
For those who wish to compile Hashcat from source (perhaps to get the latest features or to customise the code), this method is an option. However, this process is more involved and may require additional software like Cygwin or Windows Subsystem for Linux (WSL).
Step-by-Step Guide:
- Install Dependencies:
- First, you will need Visual Studio (with C++ build tools), which can be downloaded from Visual Studio’s website. During installation, ensure that you select “Desktop development with C++”.
- Install Cygwin or enable Windows Subsystem for Linux (WSL) to provide the necessary Linux-like environment for compiling.
- Clone the Repository: Once you have the dependencies set up, clone the official Hashcat repository from GitHub:
git clone https://github.com/hashcat/hashcat.git - Build Hashcat: After cloning the repository, navigate to the
hashcatdirectory and use the following commands to compile it:cd hashcat make
This process will compile the source code into a usable executable file. Depending on your system’s resources, this could take some time. - Install the Necessary Drivers: If you intend to use GPU acceleration, make sure to install the relevant GPU drivers (NVIDIA or AMD) and ensure that OpenCL is properly set up.
- Run Hashcat: Once compiled and the necessary drivers are installed, you can run Hashcat as you would with the precompiled binary. Open a Command Prompt in the
hashcatfolder and use the following command to verify the installation:hashcat --version
This will output the current version of Hashcat, confirming that it’s ready to use.
Running Hashcat on Windows
Once Hashcat is installed, you can begin using it to crack password hashes. Below is an example of how to use Hashcat to crack a hash file:
- Prepare the Hash File: Make sure you have a hash file to crack. Hashcat supports various hash algorithms, and the hash file typically contains encrypted passwords.
- Choose an Attack Mode: Hashcat offers several attack modes, including:
- Dictionary Attack (
-a 0) - Brute-Force Attack (
-a 3) - Mask Attack (
-a 6) - Combinator Attack (
-a 1)
- Dictionary Attack (
- Run Hashcat: For example, to perform a dictionary attack on an MD5 hash file, use the following command:
hashcat -m 0 -a 0 hashfile.txt wordlist.txt
Replacehashfile.txtwith the path to your hash file andwordlist.txtwith the path to your dictionary.
Conclusion
Installing Hashcat on Windows is a relatively straightforward process, whether you choose to use precompiled binaries or compile from source. The ability to harness both CPU and GPU acceleration makes it a powerful tool for cracking password hashes, useful for penetration testers, ethical hackers, and security researchers alike.
By following the steps outlined in this guide, you should be able to install and begin using Hashcat on your Windows machine. Always remember to use Hashcat responsibly and ensure that you have the necessary permissions for the password cracking activities you engage in.
Disclaimer: This post may contain affiliate links. If you make a purchase through one of these links, Cyberly may earn a small commission at no extra cost to you. Your support helps us continue providing free tutorials and content. Thank you!
Содержание статьи
- Как пользоваться Hashcat на Windows
- Установка и настройка Hashcat в Windows
- Использование Hashcat в Windows
Ранее мы уже рассказывали про Hashcat в статье «Использовании Hashcat на Kali Linux». Сегодня покажу, как установить и использовать Hashcat на Windows. Будем взламывать хеш пароля в MD5, MD4, SHA1, SHA3 и коснемся других способов взлома хешей.
Еще по теме: Создание флешки Kali Linux (быстрый способ)
Hashcat — самый быстрый инструментом для взлома паролей. Он кроссплатформенный и доступен для Windows, macOS и Linux. Взломщик паролей поддерживает большое количество алгоритмов хеширования, включая LM Hash, NT hash, MD4, MD5, SHA-1 и 2 и многие другие. На сегодняшний день поддерживает 237 различных типов хешей.
Как пользоваться Hashcat на Windows
Рассмотрим команду использования Hashcat в Windows:
|
.\hashcat —m 0 —a 0 .\crackme.txt .\rockyou.txt |
.\hashcat -m 0 -a 0 .\файл_хешей.txt .\словарь.txt
- -m (тип хеша) — Например, MD5, SHA1 и т. д. В этом примере мы будем использовать
—m 0 для MD5. - -a (тип атаки) — Указывает Hashcat, каким методом взламывать пароль. Например, с использованием словаря слов, или перебора, или знаменитой комбинированной атаки. В этом примере мы будем использовать
—a 0 для атаки по словарю. - [файл_хешей.txt] — Задает расположение файла, содержащего хеш-коды, которые вы собираетесь взломать. В примере я использовал
crackme.txt. - [словарь.txt | маска | каталог] — Задает используемый словарь (список слов), маску или каталог. В этом примере мы будем использовать словарь для брута
rockyou.txt.
Установка и настройка Hashcat в Windows
Зайдите на сайт Хешкэт и скачайте бинарник (версию для Windows).
Запустите командную строку и с помощью команды
cd перейдите в папку с извлеченным из архива Hashcat.
Убедитесь, что находитесь в папке Hashcat введя hashcat.exe.
Создайте новый текстовый документ внутри папки hashcat, где будут хранятся хеши ваших паролей, в моем случае — это файл crackme.txt. Ниже приведен список тестовых хэшей, которые вы можете использовать.
|
6c569aabbf7775ef8fc570e228c16b98 e10adc3949ba59abbe56e057f20f883e 25f9e794323b453885f5181f1b624d0 5f4dcc3b5aa765d61d8327deb882cf9 d8578edf8458ce06fbc5bb76a58c5ca4 fcea920f7412b5da7be0cf42b8c93759 96e79218965eb72c92a549dd5a330112 25d55ad283aa400af464c76d713c07ad e99a18c428cb38d5f260853678922e03 7c6a180b36896a0a8c02787eeafb0e4c 3f230640b78d7e71ac5514e57935eb69 f6a0cb102c62879d397b12b62c092c06 |
Добавьте не менее 5 хешей.
Можете сгенерировать свои собственные хэши каким-нибудь онлайн-сервисом.
Теперь создайте словарь для брута. Hashcat имеет свой словарь example (файл DICT), но лучше использовать словарь Kali Linux rockyou.txt или свой словарь.
Использование Hashcat в Windows
Откройте командную строку и убедитесь, что находитесь в папке Hashcat.
Для справки введите команду:
Большой выбор алгоритмов хеширования:
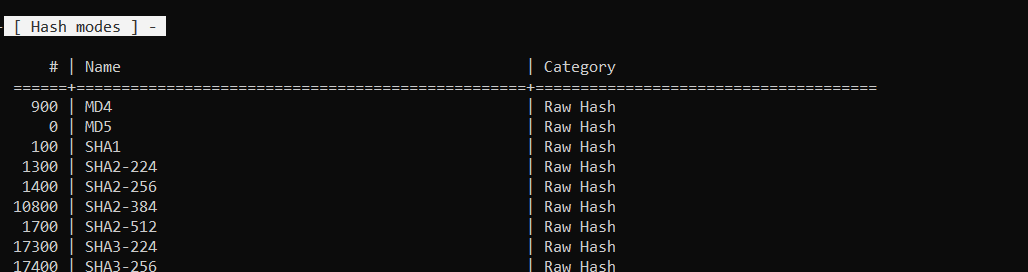
Для взлома наших хешей используем атаку по словарю
—a 0 на хеш MD5
—m 0.
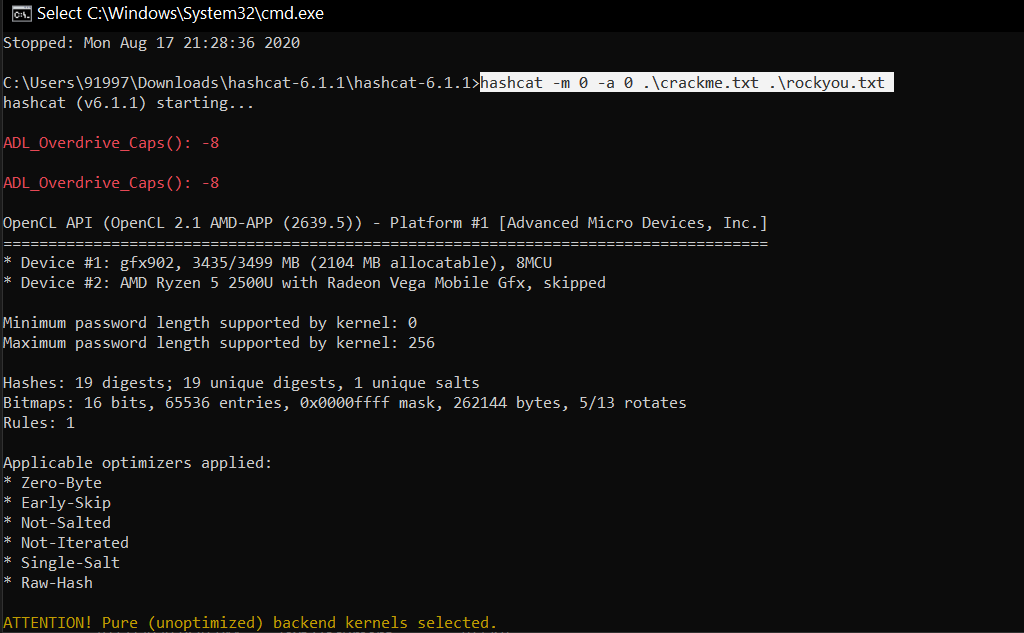
Как можно видеть на скрине ниже, Хешкэт взломал несколько хешей.
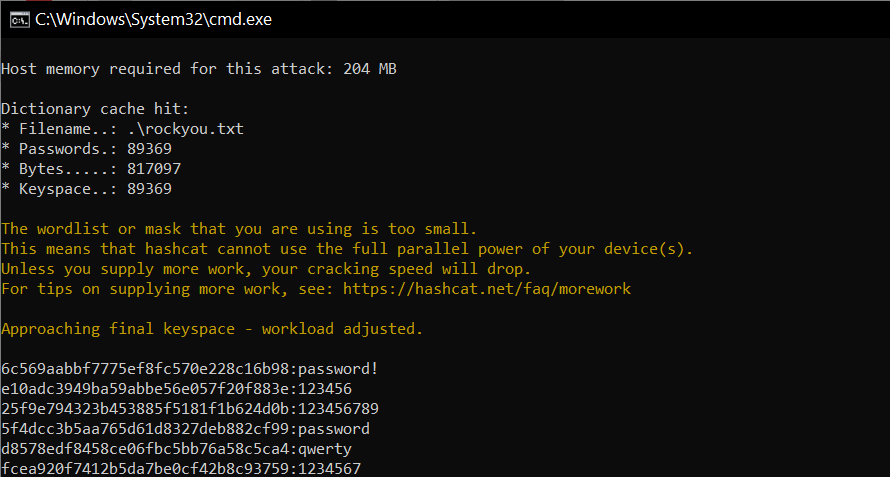
Hashcat добавляет все взломанные пароли в файл potfile и сохраняет в своей папке.
На этом все. Теперь вы знаете как пользоваться мощным инструментом Хешкэт, для взлома паролей.
ПОЛЕЗНЫЕ ССЫЛКИ:
- Лучшие словари для Hashcat
- Актуальные методы взлома паролей
- Брут секретного ключа JWT с помощью Hashcat
This is a guide to installing hashcat on a windows 10 build. Hashcat allows for the use of GPUs to crack hashes which is significantly faster then within a VM and/or using a CPU alone.
Legal Usage:
The information provided by executeatwill and this website is to be used for educational purposes only. The website creator and/or editor is in no way responsible for any misuse of the information provided. All the information on this website is meant to help the reader develop penetration testing and vulnerability aptitude to prevent attacks discussed. In no way should you use the information to cause any kind of damage directly or indirectly. Information provided by this website is to be regarded from an “ethical hacker” standpoint. Only preform testing on systems you OWN and/or have expressed written permission. Use information at your own risk.
By continued reading, you acknowledge the aforementioned user risk/responsibilities.
Keep in mind by using your GPU the faster the clock speed the faster it will crack hashes. Understand with increased speed comes increased heat. Our goal should be to ensure we control the heat being generated from large password lists to which I recommend MSI Afterburner.
(recommended) — MSI Afterburner can be used to monitor/overclock GPUs and is found at:
within the hash.txt — add hashes you would like to crack.
within the cracked.txt — you should have cracked hashes append here.
Testing a MD5 hash
create a quick MD5 hash at: http://www.miraclesalad.com/webtools/md5.php
1 |
|
change directory and navigate to hashcat directory.
1 |
|
1 |
|
in my case I have x1 GTX 1070 for cracking.
In this example it took 10s to crack this MD5 hash using brute force with x1 GTX 1070.
Hashcat GUI
For a bit easier user experience I recommend checking out Hashcat GUI.
Setup:
Start by downloading the HashcatGUI_1.1beta0.zip from above website.
We are going to need to extract the zip and copy all the contents from the orginal hashcat into GUI directory.
files from hashcat folder were pasted into GUI folder.
where are you going to find wordlists you ask? Lets checkout SecLists on github: https://github.com/danielmiessler/SecLists
hashkiller download section also has an frequently updated password list:
https://hashkiller.co.uk/downloads.aspx
configure the input file to the hash.txt and the output file to the cracked.txt.
untick “Disabled Pot File”
untick “CPU only”
change Format: Plain
change Hashcat Path
configured in my case to crack MD5 hashes.