TR/CoinMiner is a Trojan Horse that uses the infected computer’s resources to mine digital currency (Monero, Bitcoin, DarkCoin or Ethereum) without user permission.
TR/CoinMiner Trojan will use more than 70% of your CPU’s power and graphics cards power. What this means, is that when the miners are running you will find that your computer is running slower and games are stuttering or freezing because the TR/CoinMiner is using your computer’s resources to generate revenue for themselves. This will cause your CPU to run at very hot temperatures for extended periods of time, which could shorten the life of the CPU.
When a PC is infected with TR/CoinMiner malware, common symptoms include:
- Very high CPU and graphics cards usage
- Windows minimize and maximize slowly, and programs run slower.
- Programs don’t launch as quickly.
- General slowness when using the PC.
This guide was written to help Windows users remove the TR/CoinMiner, if your just looking for a way to block the TR/CoinMiner detection on a specific site, then you can use a free browser extension like Adblock.
Files reported as TR/CoinMiner may not necessarily be malicious. Should you be uncertain as to whether a file has been reported correctly, you can submit the affected file to https://www.virustotal.com/en/ to be scanned with multiple antivirus engines.
How to remove TR/CoinMiner Trojan (Virus Removal Guide)
This malware removal guide may appear overwhelming due to the amount of the steps and numerous programs that are being used. We have only written it this way to provide clear, detailed, and easy to understand instructions that anyone can use to remove malware for free.
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
To remove the TR/CoinMiner Trojan, follow these steps:
- STEP 1: Use Malwarebytes to remove the TR/CoinMiner Trojan
- STEP 2: Use HitmanPro to scan for malware and unwanted programs
- (Optional) STEP 3: Double-check for malicious programs with Zemana AntiMalware
STEP 1: Use Malwarebytes to remove the TR/CoinMiner Trojan
Malwarebytes is one of the most popular and most used anti-malware software for Windows, and for good reasons. It is able to destroy many types of malware that other software tends to miss, without costing you absolutely nothing. When it comes to cleaning up an infected device, Malwarebytes has always been free and we recommend it as an essential tool in the fight against malware.
The first time you install Malwarebytes, you’re given a free 14-day trial of the premium edition, which includes preventative tools like real-time scanning and specific protection from ransomware. After two weeks, it automatically reverts to the basic free version that will detect and clean up malware infections only when you run a scan. It is important to note that Malwarebytes will run alongside antivirus software without conflicts.
-
Download Malwarebytes.
You can download Malwarebytes by clicking the link below.
MALWAREBYTES DOWNLOAD LINK
(The above link will open a new page from where you can download Malwarebytes) -
Double-click on the Malwarebytes setup file.
When Malwarebytes has finished downloading, double-click on the mb3-setup-consumer-x.x.x.xxxx.exe file to install Malwarebytes on your PC. In most cases, downloaded files are saved to the Downloads folder.
You may be presented with an User Account Control pop-up asking if you want to allow Malwarebytes to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
-
Follow the on-screen prompts to install Malwarebytes.
When the Malwarebytes installation begins, you will see the Malwarebytes Setup Wizard which will guide you through the installation process. To install Malwarebytes on your PC, click on the “Agree and Install” button.
-
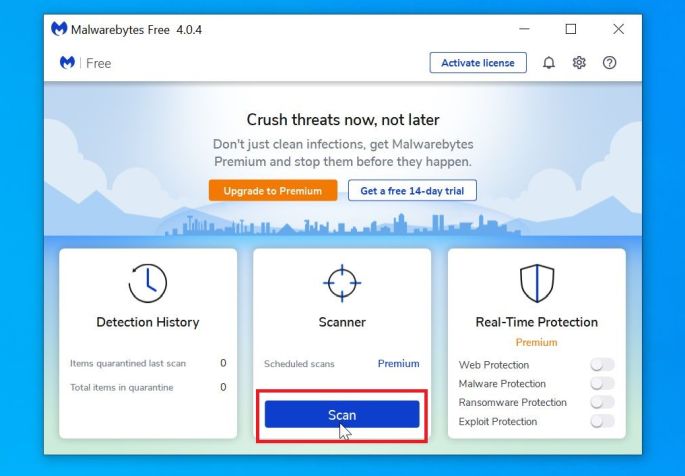
Click on “Scan Now”.
Once installed, Malwarebytes will automatically start and update the antivirus database. To perform a system scan, click on the “Scan Now” button.
-
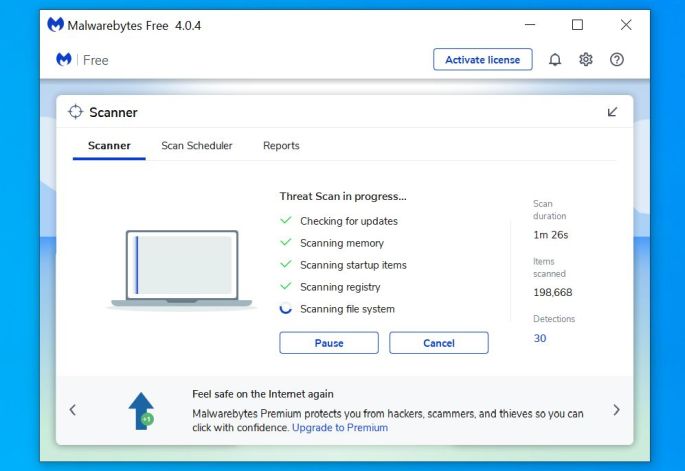
Wait for the Malwarebytes scan to complete.
Malwarebytes will now start scanning your computer for adware and other malicious programs. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
-
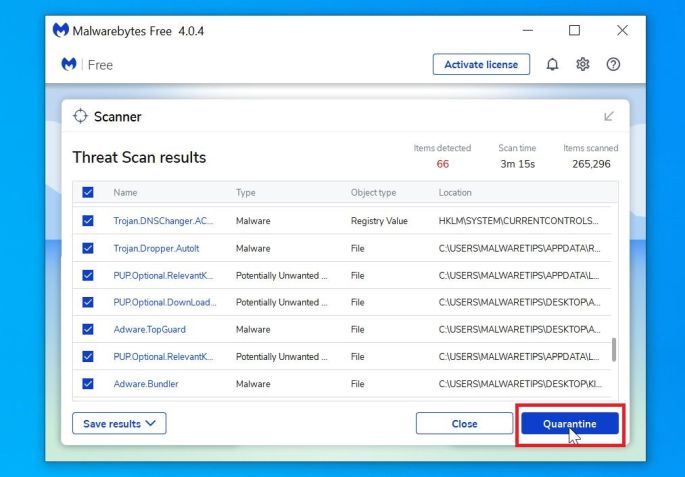
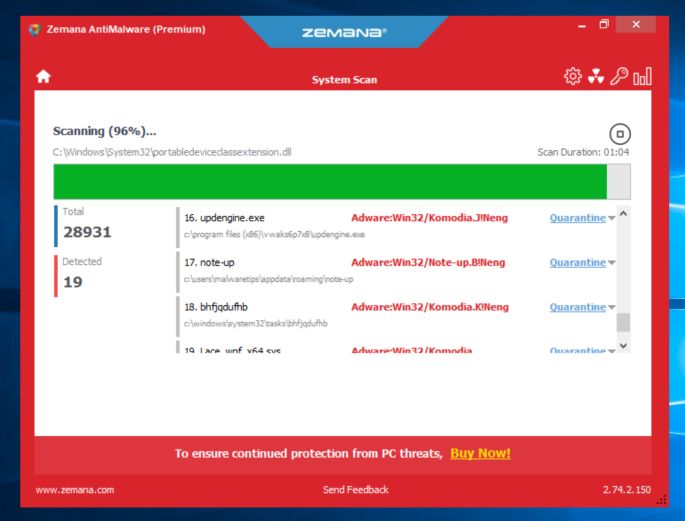
Click on “Quarantine Selected”.
When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected. To remove the malicious programs that Malwarebytes has found, click on the “Quarantine Selected” button.
-
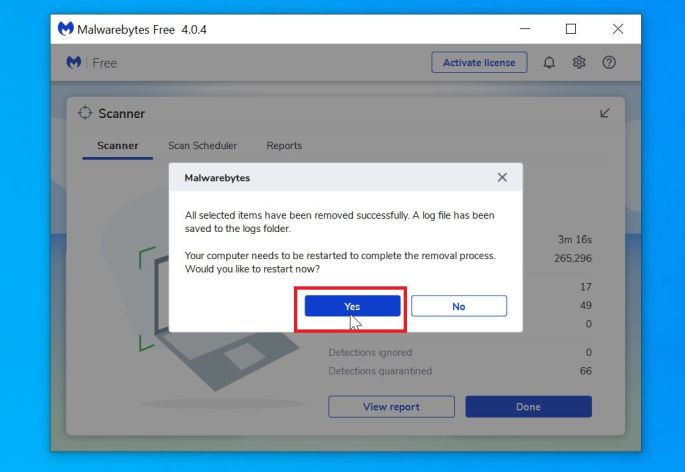
Reboot your computer.
Malwarebytes will now remove all the malicious files and registry keys that it has found. To complete the malware removal process, Malwarebytes may ask you to restart your computer.
When the malware removal process is complete, you can close Malwarebytes and continue with the rest of the instructions.
STEP 2: Use HitmanPro to scan for malware and unwanted programs
HitmanPro is a second opinion scanner that takes a unique cloud-based approach to malware scanning. HitmanPro scans the behavior of active files and also files in locations where malware normally resides for suspicious activity. If it finds a suspicious file that’s not already known, HitmanPro sends it to their clouds to be scanned by two of the best antivirus engines today, which are Bitdefender and Kaspersky.
Although HitmanPro is shareware and costs $24.95 for 1 year on 1 PC, there is actually no limit in scanning. The limitation only kicks in when there is a need to remove or quarantine detected malware by HitmanPro on your system and by then, you can activate the one time 30 day trial to enable the clean up.
-
Download HitmanPro.
You can download HitmanPro by clicking the link below.
HITMANPRO DOWNLOAD LINK
(The above link will open a new web page from where you can download HitmanPro) -
Install HitmanPro.
When HitmanPro has finished downloading, double-click on “hitmanpro.exe” (for 32-bit versions of Windows) or “hitmanpro_x64.exe” (for 64-bit versions of Windows) to install this program on your PC. In most cases, downloaded files are saved to the Downloads folder.
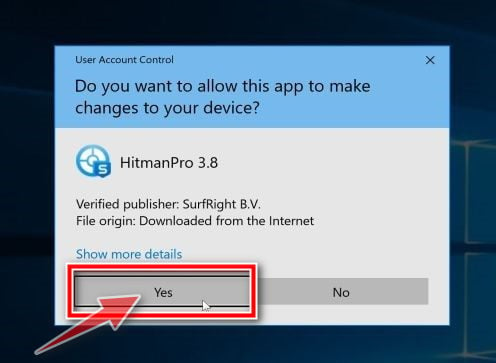
You may be presented with an User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
-
Follow the on-screen prompts.
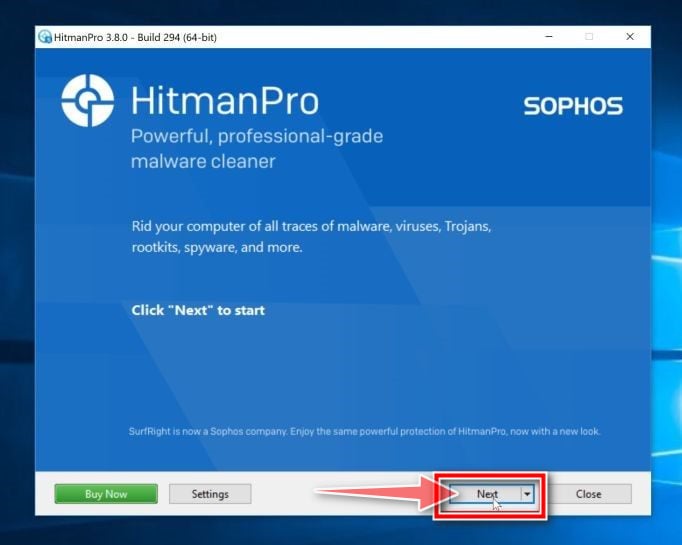
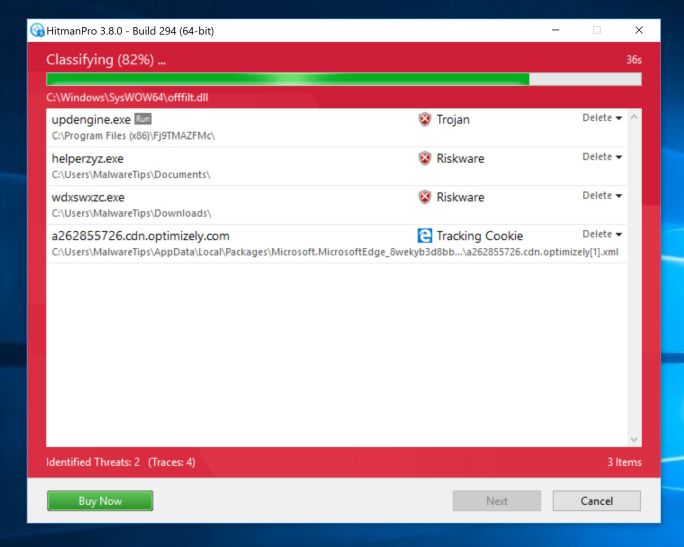
When HitmanPro starts you will be presented with the start screen as shown below. Click on the “Next” button to perform a system scan.
-
Wait for the HitmanPro scan to complete.
HitmanPro will now begin to scan your computer for malicious programs. This process will take a few minutes.
-
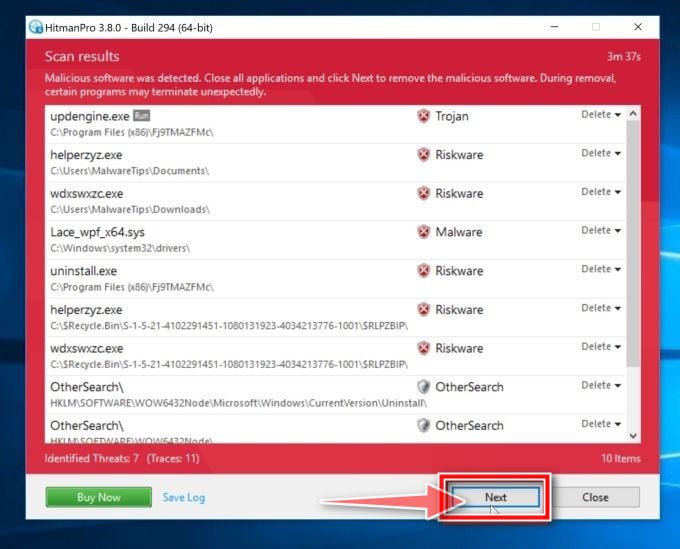
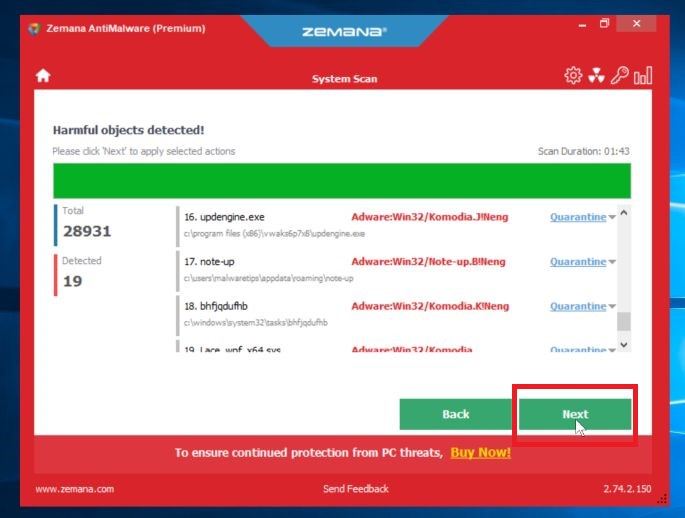
Click on “Next”.
When HitmanPro has finished the scan, it will display a list of all the malware that the program has found. Click on the “Next” button to remove the malicious programs.
-
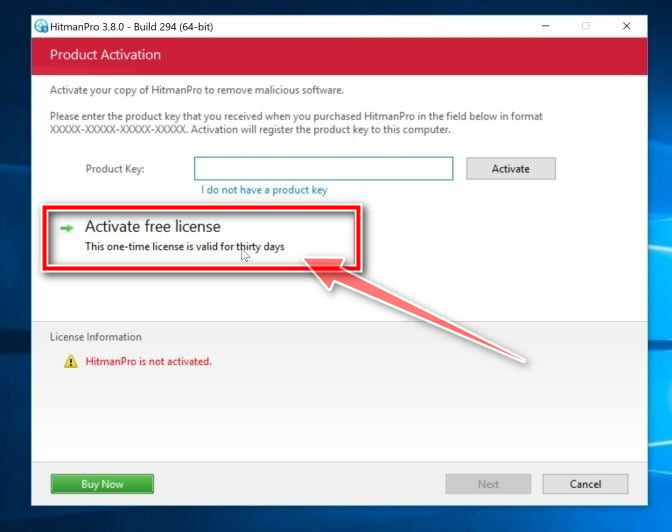
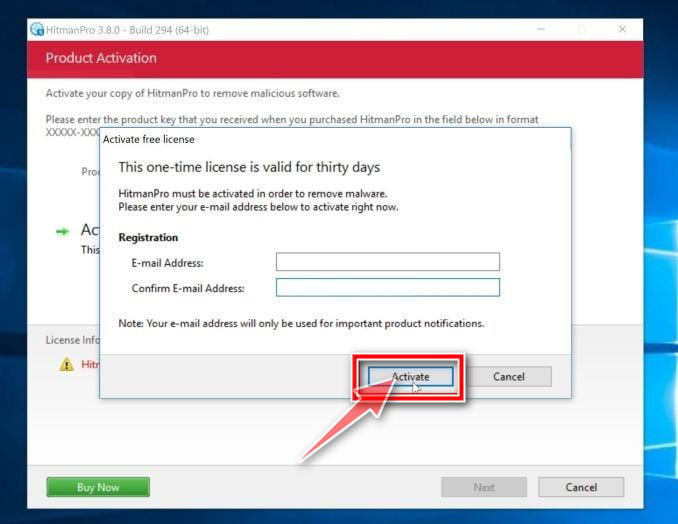
Click on “Activate free license”.
Click on the “Activate free license” button to begin the free 30 days trial and remove all the malicious files from your PC.
When the process is complete, you can close HitmanPro and continue with the rest of the instructions.
(OPTIONAL) STEP 3: Double-check for malicious programs with Zemana AntiMalware Free
Zemana AntiMalware is a free popular on-demand antivirus scanner which can detect and remove malware that even the most well-known anti-virus and anti-malware applications fail to find.
While the Malwarebytes and HitmanPro scans are more than enough, we’re recommending Zemana AntiMalware to users who still have malware related issues or just want make sure their PC is 100% clean.
-
Download Zemana AntiMalware.
You can download Zemana AntiMalware Free by clicking the link below.
-
Double-click on the setup file.
Double-click on the file named “Zemana.AntiMalware.Setup.exe” to start the installation of Zemana AntiMalware. In most cases, downloaded files are saved to the Downloads folder.
You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
-
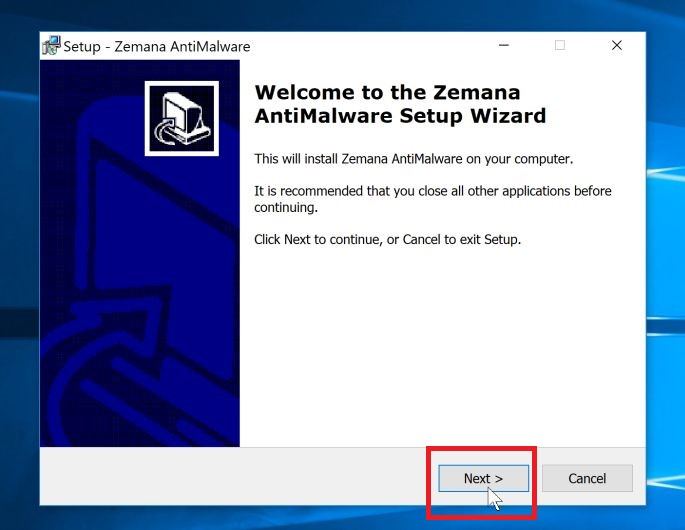
Install Zemana AntiMalware Free.
Click on the “Next” button to install Zemana AntiMalware on your PC. Follow the on-screen prompts to complete the install process.
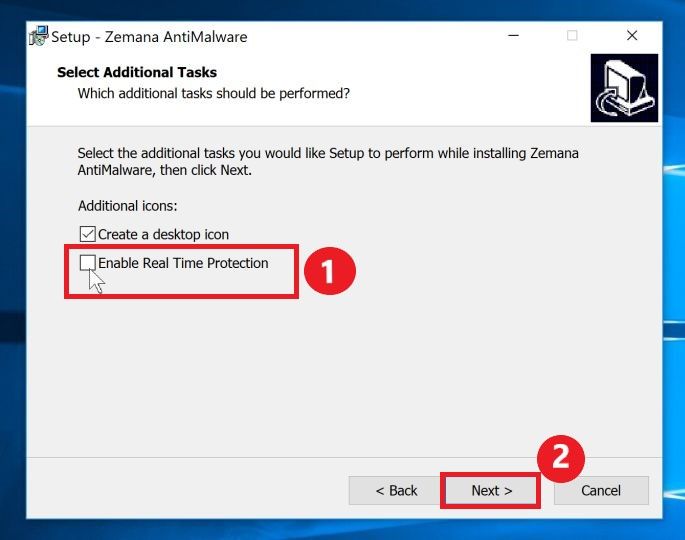
When you reach the “Select Additional Tasks” screen, you need to opt-out the “Enable Real Time Protection” option, then click on the “Next” button.
-
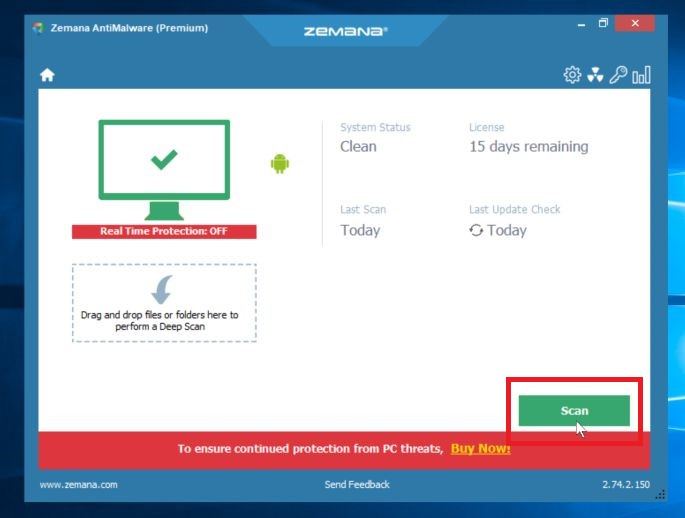
Click on “Scan”.
When Zemana AntiMalware will start, click on the “Scan” button to perform a system scan.
-
Wait for the Zemana AntiMalware scan to complete.
Zemana AntiMalware will now scan your PC for malicious files. This process can take a few minutes.
-
Click on “Next”.
When Zemana AntiMalware has finished it will display a list of all the malware that the program found. Click on the “Next” button to remove the malicious files from your computer.
-
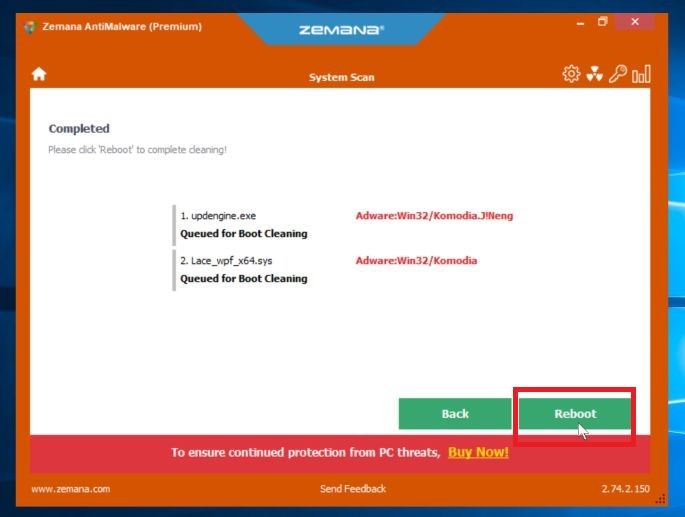
Restart your PC.
When the malware removal process is complete, Zemana AntiMalware may need to restart your computer. Click on the “Reebot” button to reset your PC.
Your computer should now be free of the TR/CoinMiner Trojan. If you are still experiencing problems while trying to remove TR/CoinMiner Trojan from your PC, please do one of the following:
- Run a system scan with Emsisoft Emergency Kit
- Ask for help in our Malware Removal Assistance for Windows forum.
Here are 10 basic security tips to help you avoid malware and protect your device:
Use a good antivirus and keep it up-to-date.
It’s essential to use a good quality antivirus and keep it up-to-date to stay ahead of the latest cyber threats. We are huge fans of Malwarebytes Premium and use it on all of our devices, including Windows and Mac computers as well as our mobile devices. Malwarebytes sits beside your traditional antivirus, filling in any gaps in its defenses, and providing extra protection against sneakier security threats.
Keep software and operating systems up-to-date.
Keep your operating system and apps up to date. Whenever an update is released for your device, download and install it right away. These updates often include security fixes, vulnerability patches, and other necessary maintenance.
Be careful when installing programs and apps.
Pay close attention to installation screens and license agreements when installing software. Custom or advanced installation options will often disclose any third-party software that is also being installed. Take great care in every stage of the process and make sure you know what it is you’re agreeing to before you click «Next.»
Install an ad blocker.
Use a browser-based content blocker, like AdGuard. Content blockers help stop malicious ads, Trojans, phishing, and other undesirable content that an antivirus product alone may not stop.
Be careful what you download.
A top goal of cybercriminals is to trick you into downloading malware—programs or apps that carry malware or try to steal information. This malware can be disguised as an app: anything from a popular game to something that checks traffic or the weather.
Be alert for people trying to trick you.
Whether it’s your email, phone, messenger, or other applications, always be alert and on guard for someone trying to trick you into clicking on links or replying to messages. Remember that it’s easy to spoof phone numbers, so a familiar name or number doesn’t make messages more trustworthy.
Back up your data.
Back up your data frequently and check that your backup data can be restored. You can do this manually on an external HDD/USB stick, or automatically using backup software. This is also the best way to counter ransomware. Never connect the backup drive to a computer if you suspect that the computer is infected with malware.
Choose strong passwords.
Use strong and unique passwords for each of your accounts. Avoid using personal information or easily guessable words in your passwords. Enable two-factor authentication (2FA) on your accounts whenever possible.
Be careful where you click.
Be cautious when clicking on links or downloading attachments from unknown sources. These could potentially contain malware or phishing scams.
Don’t use pirated software.
Avoid using Peer-to-Peer (P2P) file-sharing programs, keygens, cracks, and other pirated software that can often compromise your data, privacy, or both.
To avoid potential dangers on the internet, it’s important to follow these 10 basic safety rules. By doing so, you can protect yourself from many of the unpleasant surprises that can arise when using the web.
What is PUA:Win32/CoinMiner? PUA:Win32/CoinMiner is a malicious software. It can modify MS Windows OS and browsers settings, download and install other malicious software, adware and potentially unwanted apps. On current date, PUA:Win32/CoinMiner continues to increase the number of personal computers which have been infected.
PUA:Win32/CoinMiner use your computer’s resources to generate digital currency
Once installed, this virus will be configured to start automatically when Windows starts. PUA:Win32/CoinMiner can give a remote access to your personal computer and use your computer’s resources to generate digital currency. It will make your personal computer run very slow.
Moreover, the PUA:Win32/CoinMiner can gather lots of privacy information. This personal information, in the future, can be transferred to third parties. What creates the risk of theft of personal info about you
We suggest you to remove PUA:Win32/CoinMiner virus and free your computer of any malicious software as quickly as possible, until the presence of this virus has not led to even worse consequences. You need to follow the step-by-step tutorial below that will allow you to completely remove PUA:Win32/CoinMiner , using only the built-in Windows features and a few of specialized free utilities.
How to remove PUA:Win32/CoinMiner virus
When a malicious software such as the PUA:Win32/CoinMiner gets installed on your system without your knowledge, it’s not easy to delete. In most cases, there is no Uninstall application that simply remove PUA:Win32/CoinMiner virus from your personal computer. So, we advise using several well-proven free specialized utilities such as Zemana, MalwareBytes or Hitman Pro. But the best solution to remove PUA:Win32/CoinMiner virus will be to perform several manual steps, after that additionally run antimalware tools.
To remove PUA:Win32/CoinMiner, complete the following steps:
- Removing the PUA:Win32/CoinMiner, check the list of installed apps first
- Remove PUA:Win32/CoinMiner virus with Zemana
- Scan your PC and remove PUA:Win32/CoinMiner virus with Hitman Pro
- How to remove PUA:Win32/CoinMiner with MalwareBytes
- Delete PUA:Win32/CoinMiner virus from Microsoft Internet Explorer
- Get rid of PUA:Win32/CoinMiner virus from Firefox
- Remove PUA:Win32/CoinMiner from Chrome
- Use AdBlocker to stay safe online
- Finish words
Removing the PUA:Win32/CoinMiner, check the list of installed apps first
First method for manual virus removal is to go into the Windows “Control Panel”, then “Uninstall a program” console. Take a look at the list of apps on your machine and see if there are any questionable and unknown apps. If you see any, you need to remove them. Of course, before doing so, you can do an World Wide Web search to find details on the application. If it is a potentially unwanted program, adware or malicious software, you will likely find information that says so.
Make sure you have closed all browsers and other software. Press CTRL, ALT, DEL keys together to open the Windows Task Manager.
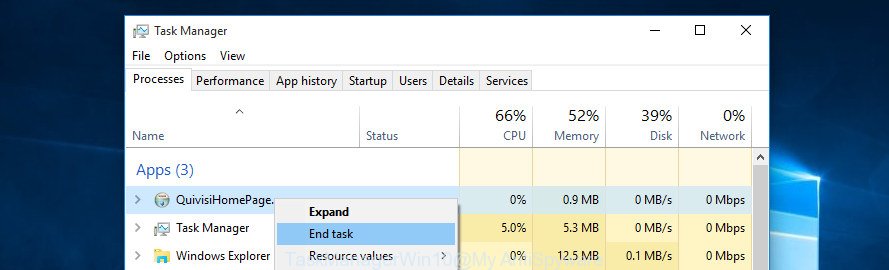
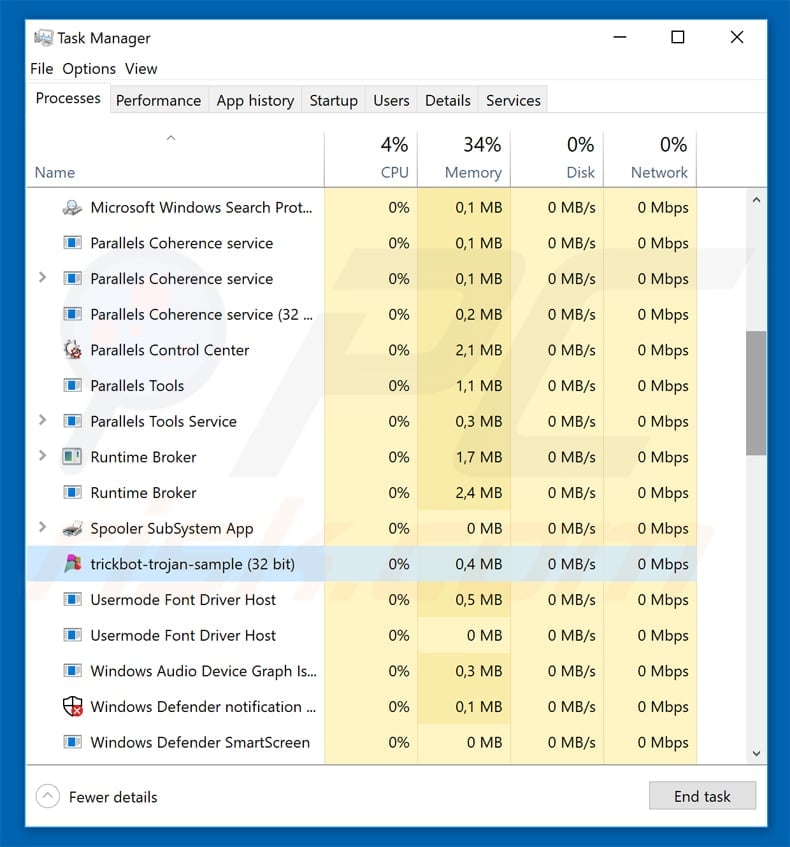
Click on the “Processes” tab, look for something suspicious that is the PUA:Win32/CoinMiner or other security threats then right-click it and select “End Task” or “End Process” option. Most often, malware masks itself to avoid detection by imitating legitimate Windows processes. A process is particularly suspicious: it’s taking up a lot of memory (despite the fact that you closed all of your applications), its name is not familiar to you (if you’re in doubt, you can always check the program by doing a search for its name in Google, Yahoo or Bing).
Next, remove any unrequested and suspicious applications from your Control panel.
Windows 10, 8.1, 8
Now, press the Windows button, type “Control panel” in search and press Enter. Select “Programs and Features”, then “Uninstall a program”.
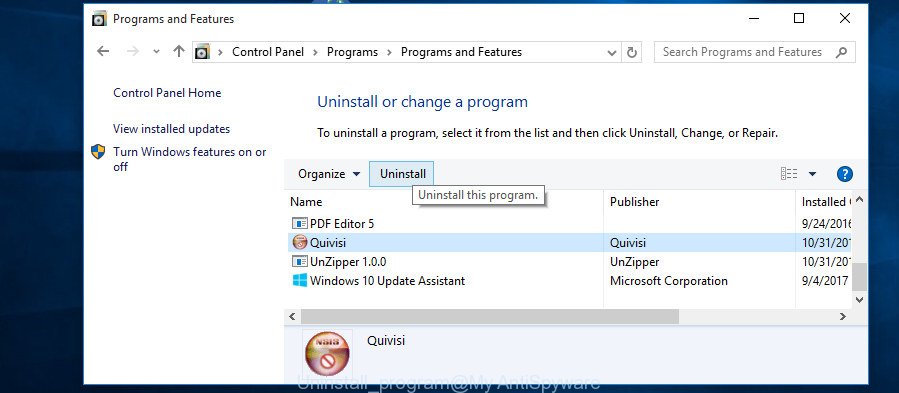
Look around the entire list of software installed on your PC. Most probably, one of them is malicious software. Select the questionable program or the program that name is not familiar to you and remove it.
Windows Vista, 7
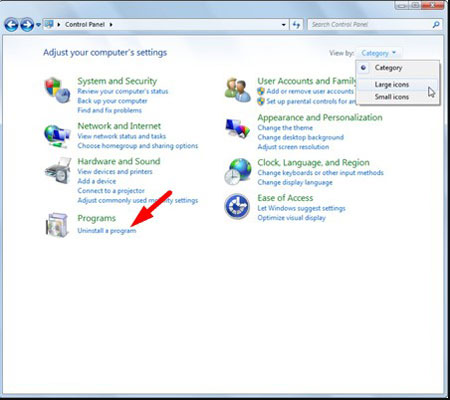
From the “Start” menu in Microsoft Windows, choose “Control Panel”. Under the “Programs” icon, select “Uninstall a program”.
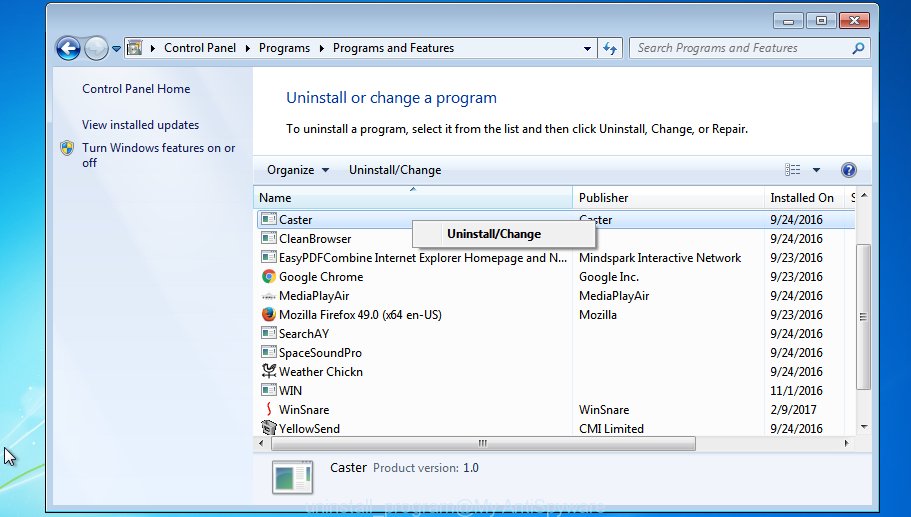
Select the questionable or any unknown apps, then click “Uninstall/Change” button to uninstall this undesired program from your PC.
Windows XP
Click the “Start” button, select “Control Panel” option. Click on “Add/Remove Programs”.
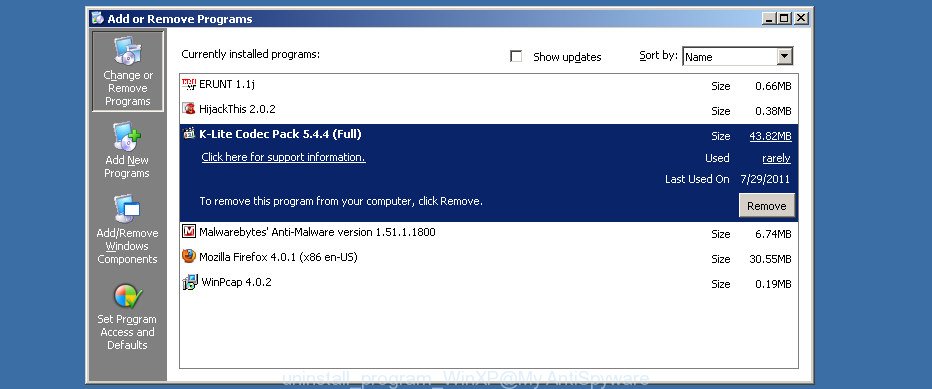
Select an unwanted program, then press “Change/Remove” button. Follow the prompts.
Remove PUA:Win32/CoinMiner virus with Zemana
Download Zemana Free to remove PUA:Win32/CoinMiner virus automatically from your PC system. This is a freeware utility specially developed for malware removal. This utility can remove adware, hijackers from your computer, installed browsers and Windows registry automatically.
Download Zemana Anti-Malware (ZAM) on your Windows Desktop by clicking on the link below.
Zemana AntiMalware
164846 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
When the downloading process is complete, close all windows on your computer. Further, launch the install file named Zemana.AntiMalware.Setup. If the “User Account Control” dialog box pops up as shown on the image below, press the “Yes” button.
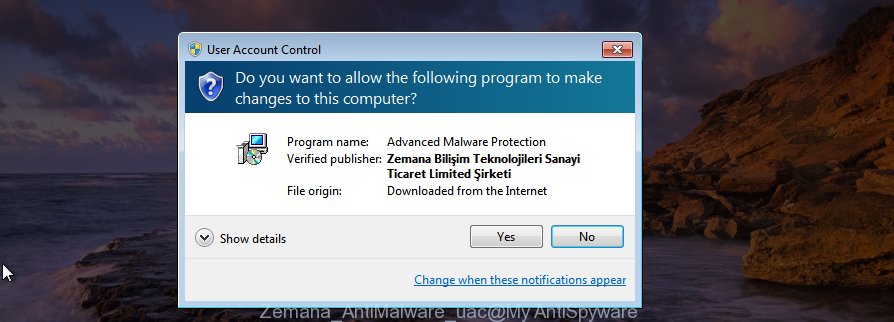
It will open the “Setup wizard” that will allow you install Zemana Anti-Malware on the machine. Follow the prompts and do not make any changes to default settings.
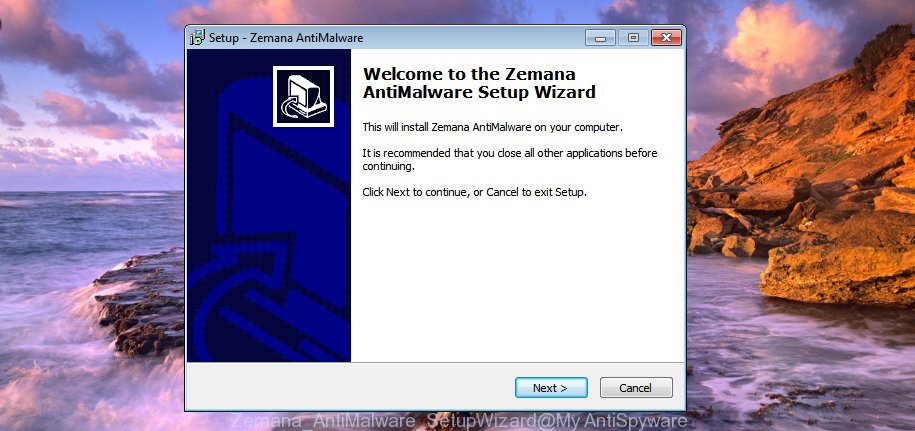
Once install is done successfully, Zemana will automatically start and you can see its main window as displayed on the image below.

Next, click the “Scan” button to detect PUA:Win32/CoinMiner and other malicious software. A scan can take anywhere from 10 to 30 minutes, depending on the count of files on your personal computer and the speed of your PC.

When finished, the results are displayed in the scan report. In order to delete all threats, simply click “Next” button.
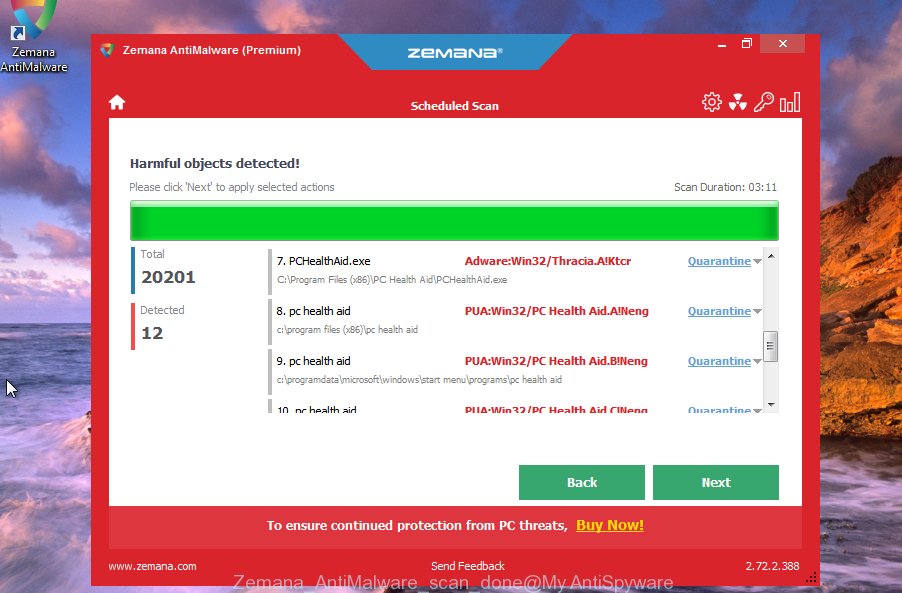
The Zemana Free will remove PUA:Win32/CoinMiner and other security threats. Once the cleaning procedure is done, you can be prompted to restart your system.
Scan your PC and remove PUA:Win32/CoinMiner virus with Hitman Pro
All-in-all, Hitman Pro is a fantastic utility to free your machine from any undesired programs like virus and other malicious software and potentially unwanted software. The Hitman Pro is portable application that meaning, you don’t need to install it to run it. HitmanPro is compatible with all versions of Windows OS from Windows XP to Windows 10. Both 64-bit and 32-bit systems are supported.
HitmanPro can be downloaded from the following link. Save it on your Desktop.
HitmanPro
12214 downloads
Author: Sophos
Category: Security tools
Update: June 28, 2018
After the downloading process is done, open the folder in which you saved it. You will see an icon like below.
Double click the Hitman Pro desktop icon. After the tool is launched, you will see a screen as displayed on the image below.
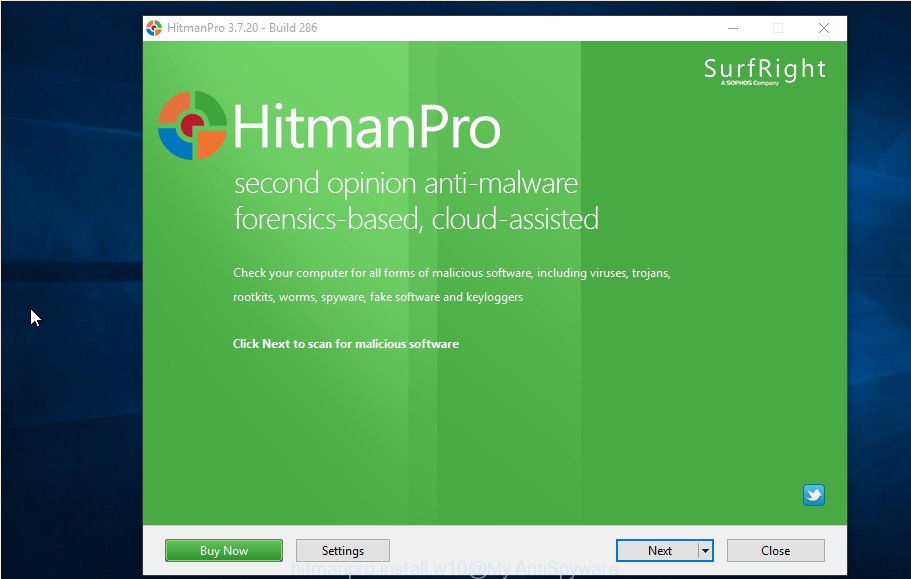
Further, click “Next” button to perform a system scan with this utility for the PUA:Win32/CoinMiner and other kinds of malicious software and potentially unwanted programs. This process may take some time, so please be patient. When the checking is finished, a list of all threats detected is created as on the image below.
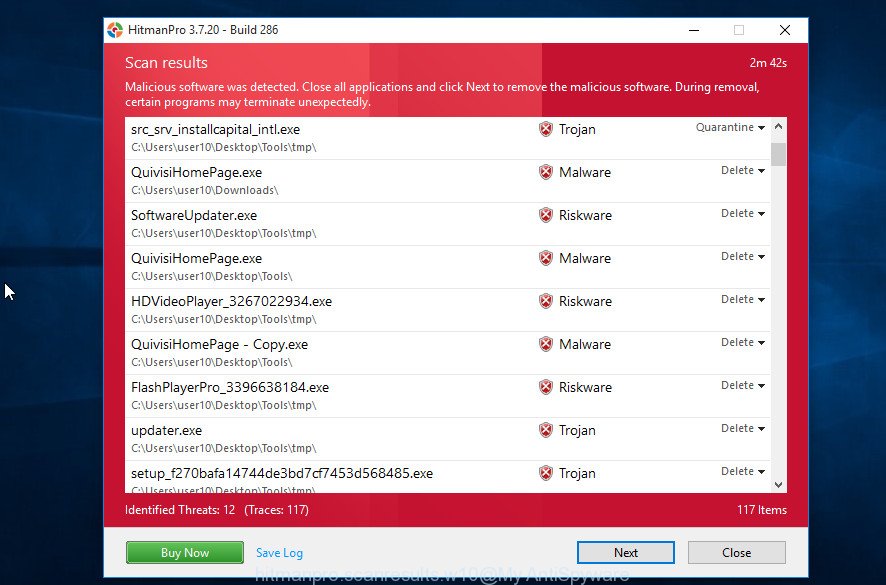
Once you have selected what you wish to delete from your PC click “Next” button. It will show a dialog box, click the “Activate free license” button.
How to remove PUA:Win32/CoinMiner with MalwareBytes
Get rid of PUA:Win32/CoinMiner virus manually is difficult and often the virus is not completely removed. Therefore, we advise you to use the MalwareBytes AntiMalware which are fully clean your personal computer. Moreover, the free program will help you to delete malicious software, PUPs, toolbars and adware software that your computer can be infected too.
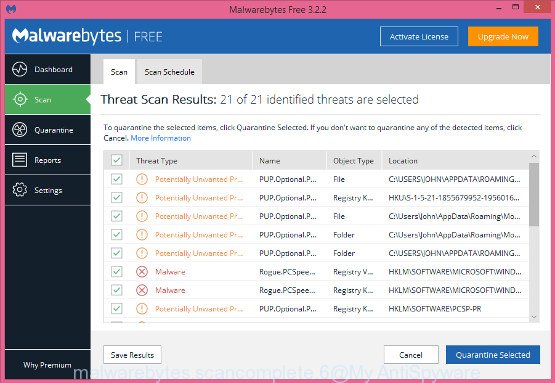
- Download MalwareBytes Free on your personal computer from the link below.
- When downloading is done, close all software and windows on your PC system. Open a file location. Double-click on the icon that’s named mb3-setup.
- Further, click Next button and follow the prompts.
- Once install is finished, press the “Scan Now” button . MalwareBytes AntiMalware program will scan through the whole system for the PUA:Win32/CoinMiner threat. A scan can take anywhere from 10 to 30 minutes, depending on the count of files on your machine and the speed of your PC. During the scan MalwareBytes Anti Malware (MBAM) will find threats exist on your computer.
- Once finished, MalwareBytes will open a scan report. You may remove items (move to Quarantine) by simply press “Quarantine Selected”. When disinfection is finished, you can be prompted to restart your machine.
The following video offers a few simple steps on how to remove browser hijackers, adware software and other malicious software with MalwareBytes Free.
Delete PUA:Win32/CoinMiner virus from Microsoft Internet Explorer
If you find that Microsoft Internet Explorer internet browser settings had been infected by the PUA:Win32/CoinMiner , then you may return your settings, via the reset internet browser procedure.
First, launch the IE, then press ‘gear’ icon . It will show the Tools drop-down menu on the right part of the internet browser, then click the “Internet Options” as displayed in the figure below.

In the “Internet Options” screen, select the “Advanced” tab, then click the “Reset” button. The IE will open the “Reset Internet Explorer settings” dialog box. Further, press the “Delete personal settings” check box to select it. Next, click the “Reset” button as displayed below.

After the procedure is done, click “Close” button. Close the Internet Explorer and reboot your personal computer for the changes to take effect. This step will help you to restore your web browser’s startpage, newtab and search provider to default state.
Get rid of PUA:Win32/CoinMiner virus from Firefox
If your Mozilla Firefox web-browser settings are affected by the PUA:Win32/CoinMiner virus, then it may be time to perform the internet browser reset. When using the reset feature, your personal information like passwords, bookmarks, browsing history and web form auto-fill data will be saved.
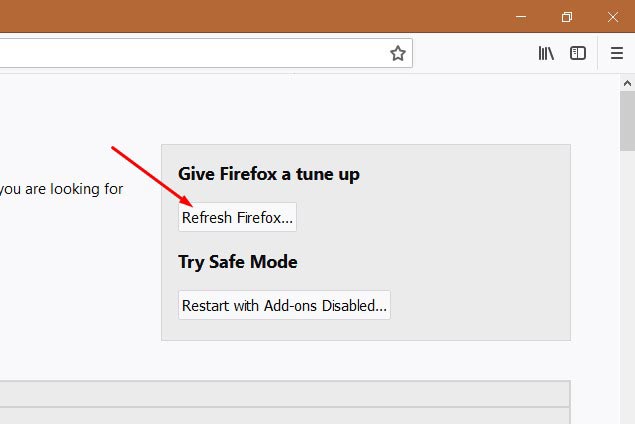
Start the Mozilla Firefox and press the menu button (it looks like three stacked lines) at the top right of the web browser screen. Next, click the question-mark icon at the bottom of the drop-down menu. It will show the slide-out menu.
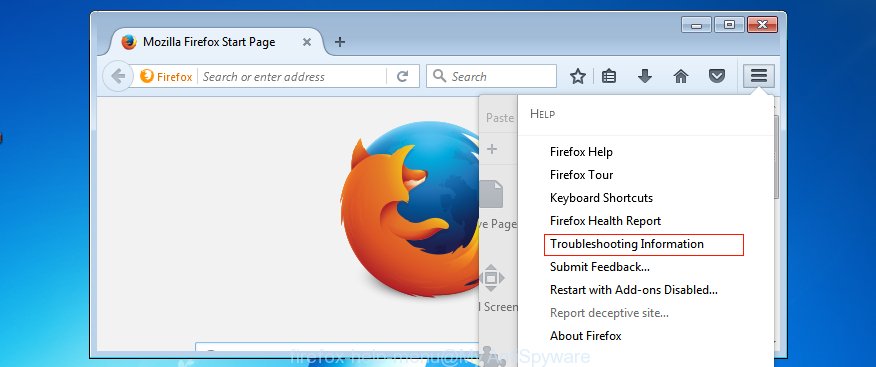
Select the “Troubleshooting information”. If you’re unable to access the Help menu, then type “about:support” in your address bar and press Enter. It bring up the “Troubleshooting Information” page as displayed in the following example.
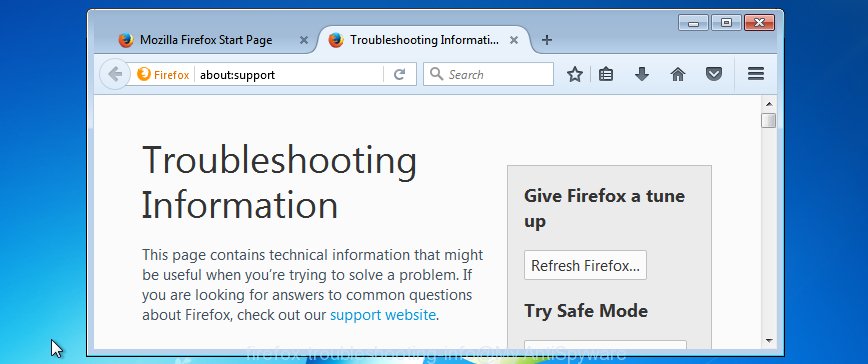
Click the “Refresh Firefox” button at the top right of the Troubleshooting Information page. Select “Refresh Firefox” in the confirmation prompt. The Mozilla Firefox will begin a process to fix your problems that caused by the PUA:Win32/CoinMiner virus. Once, it’s finished, click the “Finish” button.
Remove PUA:Win32/CoinMiner from Chrome
If you have malware problem or the Google Chrome is running slow, then reset Google Chrome settings can help you. In the steps below we will show you a way to reset your Google Chrome settings to default values without reinstall. This will also help to remove changes to internet browser settings created by PUA:Win32/CoinMiner virus.
Open the Google Chrome menu by clicking on the button in the form of three horizontal dotes (). It will display the drop-down menu. Choose More Tools, then click Extensions.
Carefully browse through the list of installed addons. If the list has the extension labeled with “Installed by enterprise policy” or “Installed by your administrator”, then complete the following tutorial: Remove Google Chrome extensions installed by enterprise policy otherwise, just go to the step below.
Open the Google Chrome main menu again, press to “Settings” option.
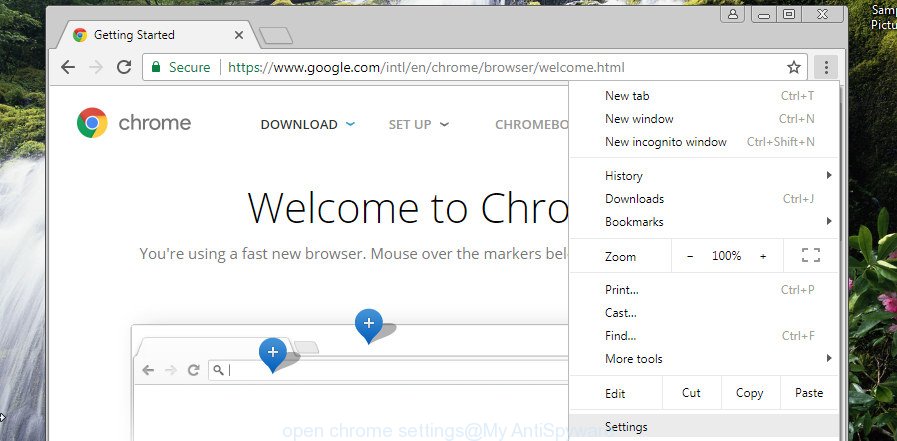
Scroll down to the bottom of the page and click on the “Advanced” link. Now scroll down until the Reset settings section is visible, like below and click the “Reset settings to their original defaults” button.
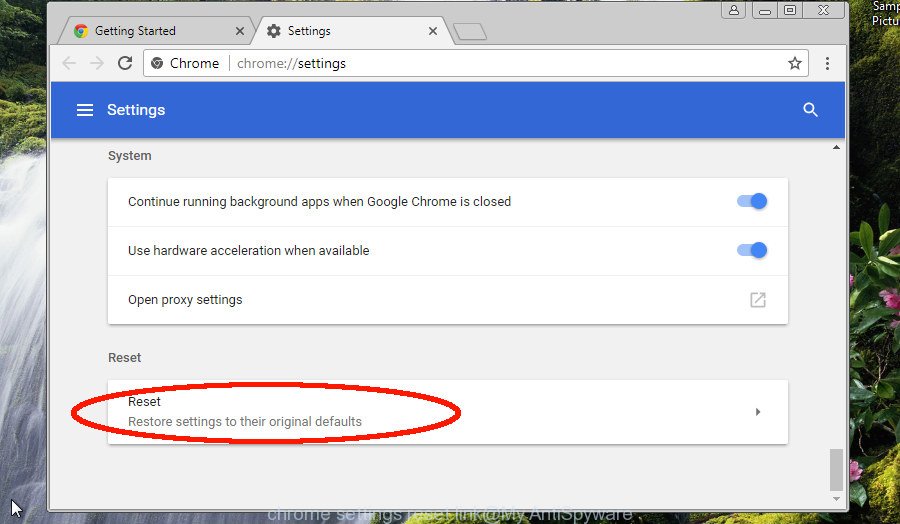
Confirm your action, click the “Reset” button.
Use AdBlocker to stay safe online
We suggest to install an adblocker program that may block harmful webpages, undesired advertisements and other intrusive webpages. Security experts says that using adblocker applications is necessary to stay safe when browsing the Internet.
Visit the following page to download AdGuard. Save it on your Microsoft Windows desktop or in any other place.
Adguard download
26854 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading is complete, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as shown on the image below.
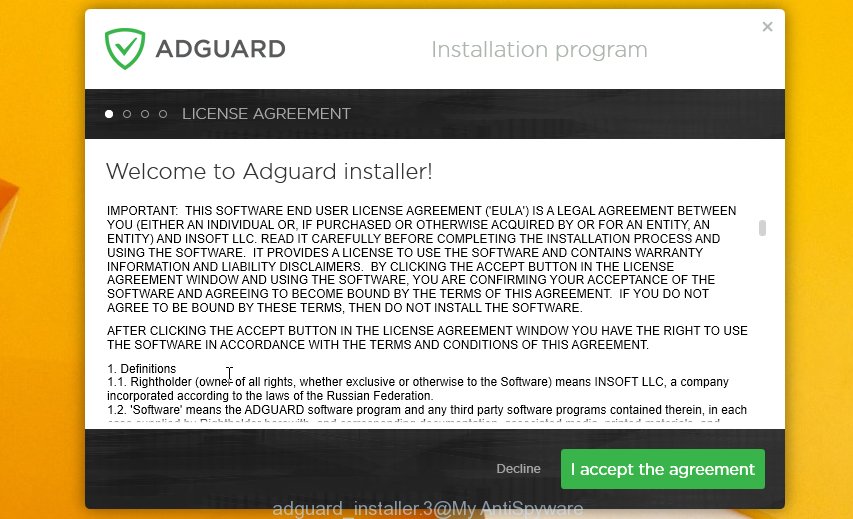
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick tutorial as displayed in the following example.

Click “Skip” button to close the window and use the default settings, or click “Get Started” to see an quick guide that will assist you get to know AdGuard better.
Each time, when you launch your computer, AdGuard will run automatically and stop unwanted advertisements, block harmful or misleading web pages. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that is located on your desktop.
Finish words
Now your personal computer should be clean of the PUA:Win32/CoinMiner virus. We suggest that you keep Zemana Free (to periodically scan your personal computer for new malicious software and other security threats) and AdGuard (to help you block undesired pop-up ads and harmful webpages). Moreover, to prevent any malware, please stay clear of unknown and third party software, make sure that your antivirus program, turn on the option to search for PUPs.
If you need more help with PUA:Win32/CoinMiner virus related issues, go to here.
COINMINER is a backdoor Trojan that quietly infiltrates the system and performs cryptocurrency mining. Its threat actors are distributing in hijacked ASUS software updates, with an emphasis on specific entities using notebook systems. It is spread through emails and targets discord users, which acts as an essential part of the Windows OS process and stops you from deleting or corrupting the critical files on your system. Users unintentionally install it when installing MS Office app like MS Word, MS Excel, MS Presentation, and more. More such malicious programs are – Zeus, ShadowHammer, Taskeng.exe.
COINMINER Trojan virus can perform one, more, or all of the following on your system:
- Install other dangerous malware on your systems like Spyware, Ransomware, and others.
- Give remote access of your PC to attackers.
- Malicious pop-ups randomly appear on the browser.
- Use your computer’s power to carry out illicit activities.
- Collect information from your system such as keystrokes, user credentials, etc., store them, and send them to the cybercriminals.
When COINMINER Trojan Virus attacks your system, you would sense the following symptoms on your computer:
- High RAM and GPU usage, making the system heat up even without heavy use.
- Application on the system load prolonged because the Trojan is using most of the computing power
- You will find random file and application downloaded automatically on your system
- Internet usage is unnaturally surged up
In this guide, we will walk through the process of removing the COINMINER Trojan from the system.
What is COINMINER Trojan?
COINMINER pretends to be a useful program but in reality, it is a Trojan that can perform a set of malicious activities. It can provide backdoor access to your PC to the hacker or can also exploit the vulnerability of the software. COINMINER is a dangerous program that looks legitimate, but in the background, it harms your computer in several ways.
How does COINMINER Trojan enter your PC?
COINMINER Trojan can use several mediums to enter your PC. In every medium, the user downloads it thinking as genuine software. It could be bundled with the free or pirated software and when you download and install that software the Trojan enters your PC. It can also use a phishing attack to trick you into downloading. Also, it can use social media, the cybercriminals may send you the Trojan from the name of someone you knew and you trust them blindly. COINMINER Trojan can also enter using the browser’s vulnerability.
Below are some common signs that you have Trojan on your system:
- Slow PC with frequent crashes
- High disk and network usage
- Seeing unexpected errors and pop-ups
- Unusual browser behaviour
- Unknown suspicious programs in your PC.
- Disabled security software
You should always pay attention while installing software specially the free software, because often, such installers includes bundled software. Don’t click on Install before checking everything.
Always opt for the custom/advanced installation mode and deselect anything other than the actual program, especially recommended software that you don’t need. In short, you should not install suspicious software. Also, never download pirated software
How to remove COINMINER Trojan (Removal Guide)
This removal guide contain complicated steps. However, our intention was not to make it complex rather we include strong measurements in the guide that can help you to remove the malware from your PC completely.
Please perform all the steps in the correct order. If you have any questions or doubt at any point, comment down and we will try to assist you.
To remove the COINMINER Trojan, follow these steps:
- STEP 1: Stop the COINMINER Trojan Process
- STEP 2: Clear the Temporary Files
- STEP 3: Uninstall Suspicious Programs
- STEP 4: Reset Browsers to Remove COINMINER Infection
- STEP 5: Scan with MalwareFox Antimalware
STEP 1: Stop the COINMINER Trojan Process
To remove COINMINER Trojan, you should first stop it from running. So that it can’t interfere with the removal process. If the Trojan keeps running it won’t allow you to uninstall the program and may create duplicate processes.
To stop COINMINER Trojan, open the task manager. Right-click on the taskbar and choose “Task Manager”.
Now you will see the list of processes. Now find the COINMINER process in the process list. Select it and click on “End task”.

Now check the “Startup” tab. If the process is there, select it and click on “Disable”. Now it won’t run again when you restart the PC.

STEP 2: Clear the Temporary Files
Trojan hides in the temporary files so that they can re-infect your PC. So you should clear the temporary files from your system. To that, click on the “Start” menu, and type “Disk Cleanup”. Click on it to open.

Then select the system drive and click “OK”.
Now here, deselect everything and select “Temporary Files” and “Temporary Internet Files”. Then click on “OK”.

Click on “Delete Files” to confirm your action.
STEP 3: Uninstall the Suspicious Program
In this first step, we will be identifying and uninstalling the malicious software from our PC.
-
Go to “Programs and Features”.
Windows 10
Windows 8
Right-click on the Start button and select “Programs and Features”. You will directly reach to the list the of programs installed.
- If there is no Programs and Features in the Start menu, then type “programs and features” into the search bar at the bottom of the Start window, then click the “Programs and Features” result.
- If you don’t see the a Start button, you are likely running Windows 8 instead of Windows 8.1. So, press the Windows key + X to open the menu instead and select “Programs and Features”.
Windows 7
- Click on Start, then click on “Control Panel”.
If you don’t see “Control Panel” here, type control panel into the search bar at the bottom of the Start window, then click the “Control Panel” result.
- Once you see the “Control Panel”, click on “ Uninstall a Program” from the Programs category.
-
Find the malicious program and uninstall it.
Now you will see the list of all installed programs in the PC, carefully observe every program and find the unwanted applications, then select it, and click the “Uninstall” button.
Your PC may have different malicious program thus the name may not match. If you cannot find any unwanted malicious programs on your PC, then you can skip to the next step
-
Follow the screen instructions to uninstall the program.
In the next screen prompt, click on Yes, and then follow the prompts to uninstall the program.
Read all screen instructions carefully during installation, because malicious programs always try to trick you in hoping that you won’t read properly.
If the program you are uninstalling is stubborn and doesn’t easily uninstall, then you can use Revo Uninstaller Free. It will help you to remove an unwanted program completely from your PC.
STEP 4: Reset Browsers to Remove COINMINER Infection
If you are still seeing COINMINER site on your browser, then you need to reset the web browser settings to their defaults. If your issue has been solved by the above methods, then there is no need to follow this step.
Google Chrome
To remove COINMINER trojan infection from Google Chrome, you need to reset the browser to its default settings. Resetting the browser settings will undo the unwanted changes due to malicious software. However, resetting will not affect the bookmarks and passwords saved in the Chrome.
-
Open Chrome’s “Settings” menu.
Click on Chrome’s main menu button, located in top right corner and looks like three vertical dots. Now click on “Settings”.
-
At the bottom, click “Advanced”.
You will see Chrome’s “Settings” in a new tab. Next, scroll down to the bottom and click on the “Advanced” button.
-
Under the section “Reset,” click “Reset”.
Now you will see Chrome’s advanced settings. Scroll down to the “Reset and clean up” section. Then click on the “Reset settings to their original defaults” button.
-
Confirm by clicking “Reset”.
Now you will see a confirmation dialog, detailing the components that will be restored to their default state should you continue on with the reset process. To confirm the reset action, click on the “Reset Settings” button.
Mozilla Firefox
To remove COINMINER Trojan infection from Mozilla Firefox, you need to reset the browser to its default settings. Resetting will remove several changes done by malicious software or add-ons, however it doesn’t affect important things like bookmarks, web form auto-fill information, passwords, browsing history and open tabs.
-
Go to the “Help” menu.
Click on Firefox’s main menu button, located in the top right corner, represented by three horizontal lines. Then click on “Help“.
-
Click “Troubleshooting Information”.
Now click on “Troubleshooting Information“.
If you’re unable to access the “Help” menu, then you can type about:support in the address bar and press enter to directly open troubleshooting page.
-
Click on “Refresh Firefox”
Now click on the “Refresh Firefox” button which is on the upper-right corner of the “Troubleshooting Information” page.
-
Confirm.
Now you will see the confirmation message telling you the action you are about to take. Click on the “Refresh Firefox” button to confirm the action.
-
Click on “Finish”.
Firefox gets closed and its settings will reset. Then it will display the list with information that was imported. Now click on the “Finish“.
Firefox will collect the information that it removed and put it in the “Old Firefox Data“ folder on the desktop. If resetting does not fix the problem you can restore this information by putting the files in the current profile folder. This folder contains senstive information, so if you don’t need it then delete it so that it doesn’t get in hands of other people.
Internet Explorer
To remove COINMINER Trojan infection from Internet Explorer, you need to reset the browser to its default settings. Resetting will help you to take Internet Explorer settings to the stat when it was first installed on your computer.
-
Go to “Internet Options”.
Open Internet Explorer browser, click on the gear icon in the top right part of the browser, now select “Internet Options“.
-
Go to “Advanced” tab, then click “Reset”
In the “Internet Options”, click on the “Advanced” tab, then select the “Reset” button.
-
Click on “Reset”.
In the “Reset Internet Explorer settings” window, click on the “Delete personal settings” checkbox, then click on the “Reset” button.
-
Click on “Close”.
Once the Internet Explorer completes all the action, click on the “Close” button.
Now you need to restart the Internet Explorer browser.
Microsoft Edge
To remove COINMINER Trojan infection from Microsoft Edge, you need to reset the browser to its default settings. You can repair or reset the Microsoft Edge settings after the Windows 10 Fall Creators Update (version 1709).
-
Go to “Apps and Features”.
Right-click on the Start button and select “Apps and Features“. It will open the list of all installed programs.
-
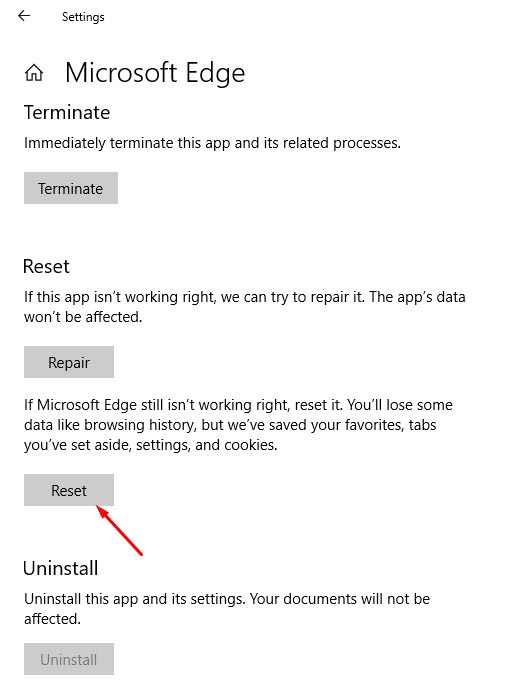
Find Microsoft Edge from the list, then click “Advanced Options”.
You will see the list of all programs in your PC. Scroll through the list and locate “Microsoft Edge”, select it, and then click on the “Advanced options”.
-
Click on “Reset”.
Now you will see the “Advanced Options”. Find the “Reset” section, as shown in the picture below. Then click on the “Reset” button.
STEP 5: Scan with MalwareFox Antimalware
MalwareFox is antimalware that works on heuristic approach to detect and remove malware from your PC. It analyzes the malware signatures as well as their behaviour. If a program acts like a malware then MalwareFox blocks it right there. It is lightweight on your system resource and finishes the scan quickly.
Its not like I am recommending you to install a costly software to remove the malware. The MalwareFox subscription charges are fairly low. But that is for a fully featured program with real-time protection capabilities. The scanning works even with the free version, though you can try the MalwareFox Premium for 14 days. Also, you don’t need to remove your current antivirus, MalwareFox will work effectively without any conflicts.
-
Download MalwareFox.
You can download MalwareFox by clicking the link below.
MALWAREFOX DOWNLOAD LINK
(The above link will open a new page from where you can download MalwareFox) -
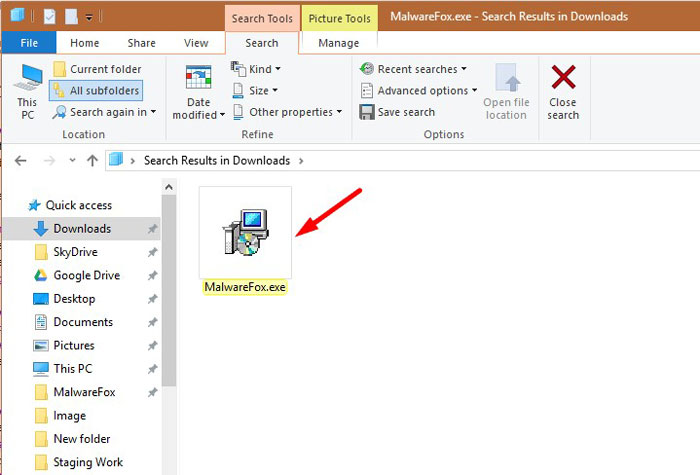
Double-click on the MalwareFox setup file.
Once the MalwareFox is downloaded, double click on MalwareFox.exe file to install it on your PC. The downloaded files are mostly saved to the Downloads folder.
You will see an User Account Control pop-up asking if you want to allow MalwareFox to make changes to your device. Click on “Yes” to proceed with the installation steps.
-
Follow the on-screen prompts to install MalwareFox.
First MalwareFox installer ask you to choose the language, select your preferend language and click on OK.
Then the MalwareFox installation Wizard appears, click on Next and follow the screen instructions to setup MalwareFox on your PC.
Once the installation is complete, MalwareFox will download the latest version and virus signatures from the server. Let it update.
-
Click on “Scan” Button.
To perform a system scan, click on the “Scan” button.
-
Wait for MalwareFox scan to complete.
MalwareFox is now scanning your computer for adware, pop-ups, browser hijackers, and other malicious programs. This process can take a few minutes, so you can do some other work while it is scanning your PC, don’t worry the PC won’t get slow during the scan.
-
Click on “Next”.
Once the scan has completed, you will see the list of detected threats on your PC. To remove the malware that MalwareFox has found, click on the “Next” button.
When the malware removal process is complete, you can close MalwareFox and continue with the rest of the instructions.
Your computer should now be clean. If you face any issues while removing COINMINER Trojan then please comment down your problem. We will try to help you as much as possible.
What is COINMINER?
As most of us are aware, 2017 was a very successful year for cryptocurrency miners. The price of popular cryptocurrencies jumped dramatically (for example, in early 2017, Bitcoin was equivalent to ~$1000, while at the end of the year it reached nearly $20,000).
Therefore, mining cryptocurrency became even more popular. Cyber criminals also started to partake in this enterprise: to generate revenue, they proliferated malware that stealthily mined cryptocurrency.
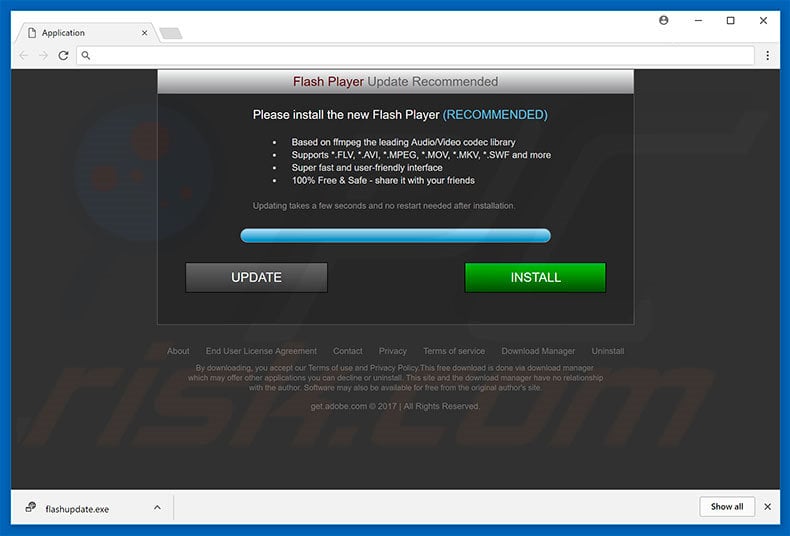
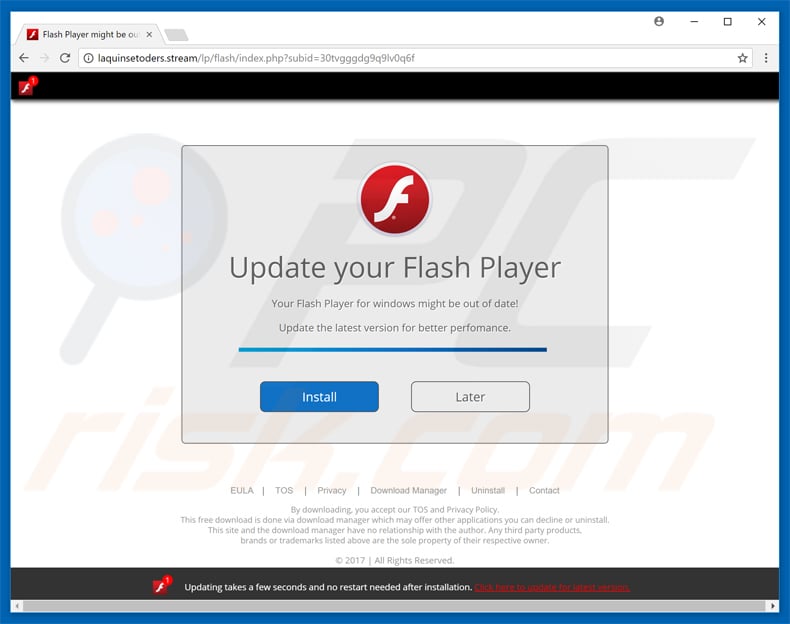
To proliferate COINMINER malware, cyber criminals typically employ fake Flash Player updaters. This method is called «bundling» (potentially unwanted programs are also proliferated in this way). Immediately after infiltration, bogus software (so-called COINMINER) starts mining Bitcoins in the background.
In other words, cyber criminals stealthily misuse system resources (specifically, the GPU) to generate revenue without users’ consent. This significantly reduces overall system performance. Another way to stealthily mine cryptocurrency is to use JavaScript code called Coinhive. Unlike COINMINER, however, Coinhive mines Monero cryptocurrency, rather than Bitcoins.
Monero is optimized for CPU mining and JavaScript is capable of making better use of the computer CPU, rather than GPU. Cyber criminals inject Coinhive script into various websites. In some cases, these sites are legitimate — they are either hijacked by cyber criminals or the hosts are dubious enough to take advantage of unsuspecting users.
Visiting these sites always leads to a reduction in system performance, since most of the resources are used to mine cryptocurrency.
If you feel that the system suddenly ‘lags’ without any particular reason, there may be a COINMINER infection or you are visiting dubious websites. In any case, immediately remove all dubious applications/browser plug-ins and ensure that visited sites are legitimate.
Threat Summary:
| Name | COINMINER virus |
| Threat Type | Cryptominer, cryptocurrency miner. |
| Detection Names | Avast (Win64:Trojan-gen), Avira (TR/AD.CoinMiner.sjwdw), BitDefender (Gen:Variant.Ulise.36452), ESET-NOD32 (a variant of Win64/CoinMiner.OZ), Full List (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate victim’s computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Decreased computer performance, system crashes, hardware overheat. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo Cleaner To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
As mentioned above, COINMINER is distributed using fake update tools. Therefore, there is a high probability that it will be delivered with various potentially unwanted programs (PUPs). Most of these programs deliver various intrusive ads (coupons, banners, pop-ups, etc.) that conceal underlying content, thereby diminishing the browsing experience.
Furthermore, some ads will redirect to malicious websites or even run malicious code that stealthily downloads and installs malware/PUPs. Therefore, clicking them risks further computer infections. Another downside is information tracking. Research shows that PUPs gather various information that typically includes personal data that is sold to third parties.
There is a high probability that information tracking will lead to serious privacy issues or even identity theft. Potentially unwanted programs must be eliminated immediately.
Many PUPs offer various useful features, however, since their only purpose is to generate revenue for the developers, these claims are merely attempts to give the impression of legitimacy. Only a small percentage of PUPs provide the features promised — most are useless for regular users.
Rather than (or together with) enabling functionality, PUPs pose a direct threat to your privacy and Internet browsing safety.
How did COINMINER install on my computer?
COINMINER and PUPs are typically distributed using the «bundling» method — stealth installation of third party software together with regular (typically free) software.
Developers hide «bundled» apps within «Custom/Advanced» settings of the download or installation processes. Many users rush and skip these sections, thus exposing their systems to risk of various infections and compromising their privacy.
How to avoid installation of potentially unwanted applications?
The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. Therefore, carefully analyze each window of the download/installation dialogs and opt-out of all additionally-included programs.
We also strongly recommend that you download your software from official sources only and, preferably, using a direct download links (most third party downloaders/installers are monetized using the «bundling» method).
Intrusive ads often look legitimate, however, they redirect to dubious websites (gambling, pornography, etc.) If you experience these redirects, uninstall all suspicious programs/browser add-ons.
Fake Flash Player update promoting COINMINER:
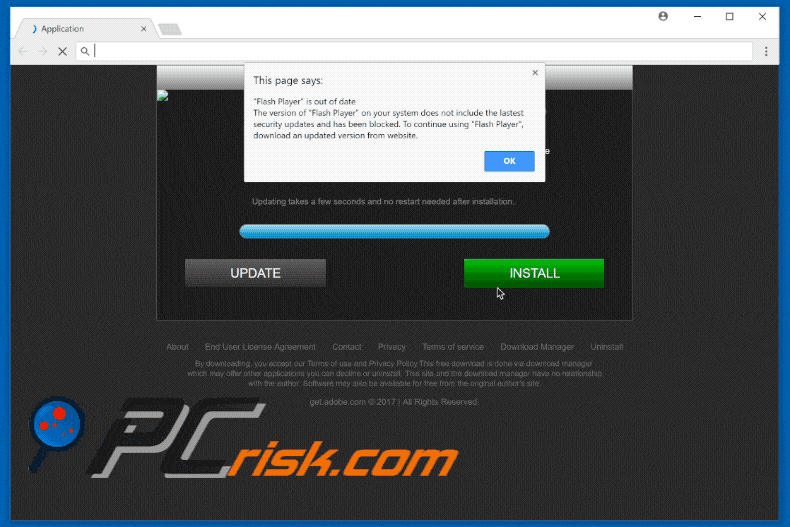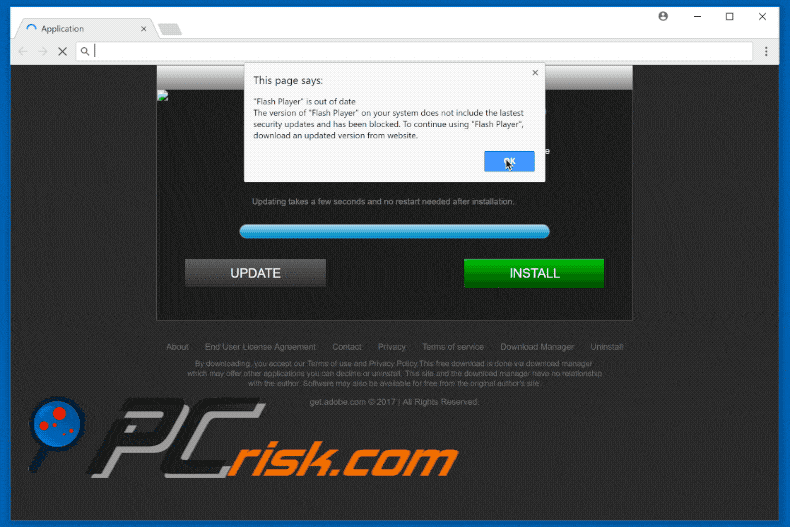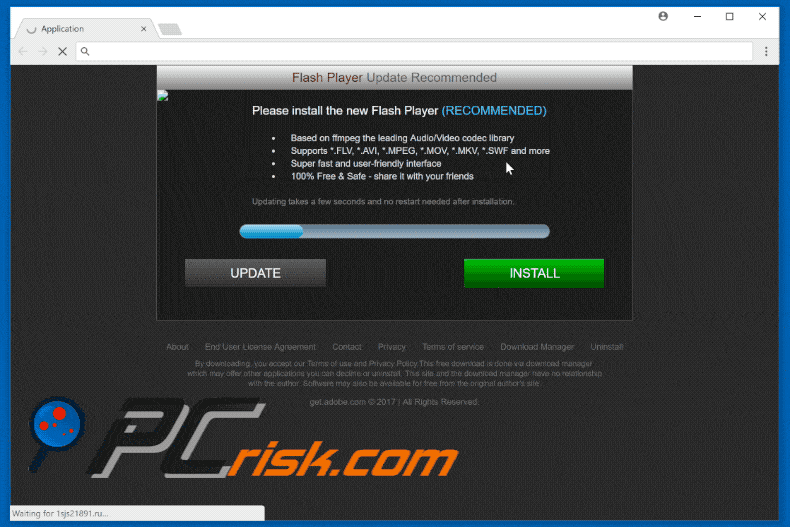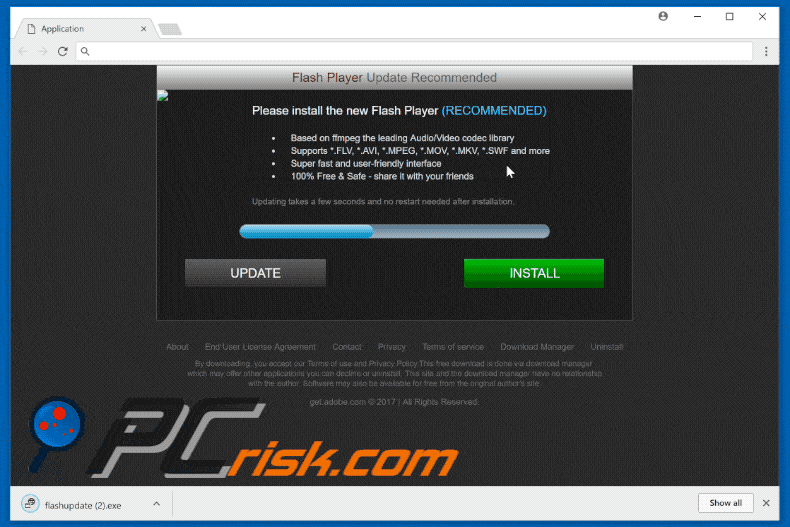
Another variant of a fake flash player update pop-up distributing Coinminer malware:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is COINMINER?
- STEP 1. Manual removal of COINMINER malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task, usually it’s better to let antivirus or anti-malware programs do it automatically. To remove this malware we recommend using
Combo Cleaner Antivirus for Windows. If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here’s an example of a suspicious program running on user’s computer:
If you checked the list of programs running on your computer, for example using task manager and identified a program that looks suspicious you should continue with these steps:
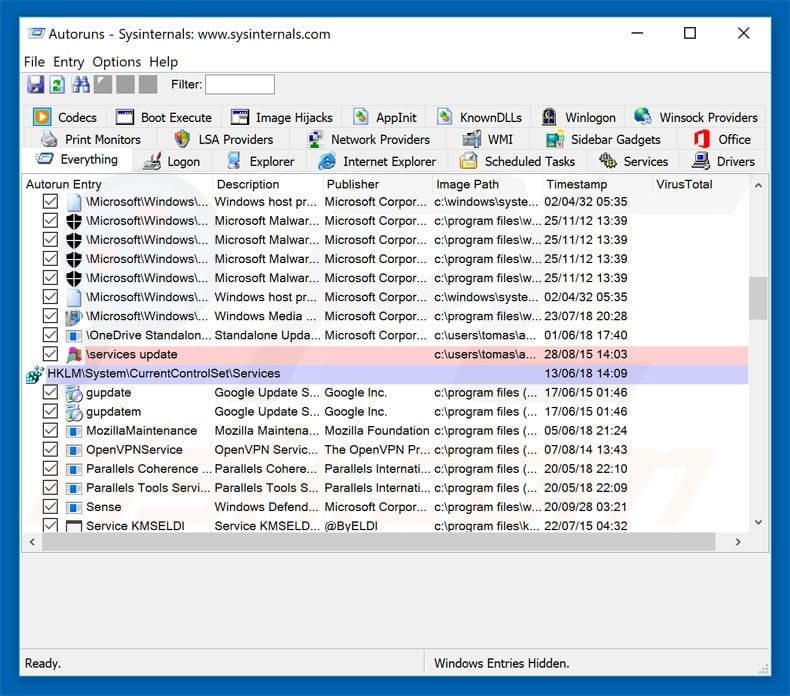
Download a program called Autoruns. This program shows auto-start applications, Registry and file system locations:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in «Safe Mode with Networking»:
Windows 8 users: Start Windows 8 is Safe Mode with Networking — Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened «General PC Settings» window, select Advanced startup. Click the «Restart now» button. Your computer will now restart into the «Advanced Startup options menu».
Click the «Troubleshoot» button, and then click the «Advanced options» button. In the advanced option screen, click «Startup settings». Click the «Restart» button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in «Safe Mode with Networking»:
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click «Restart» while holding «Shift» button on your keyboard. In the «choose an option» window click on the «Troubleshoot», next select «Advanced options». In the advanced options menu select «Startup Settings» and click on the «Restart» button.
In the following window you should click the «F5» button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in «Safe Mode with Networking»:
Extract the downloaded archive and run Autoruns.exe file.
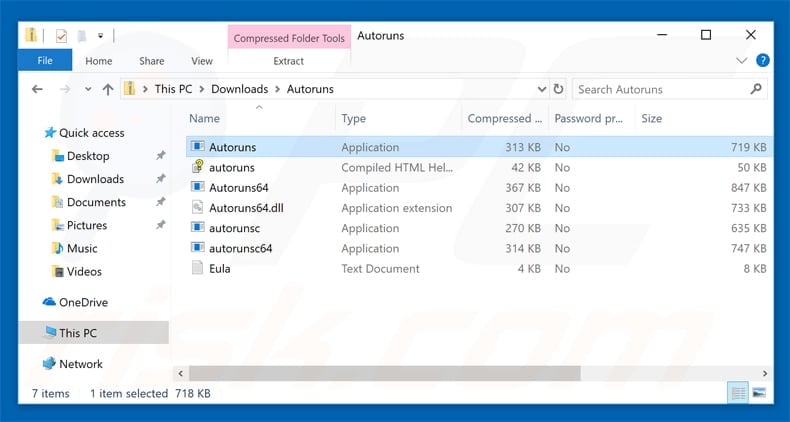
In the Autoruns application click «Options» at the top and uncheck «Hide Empty Locations» and «Hide Windows Entries» options. After this procedure click the «Refresh» icon.
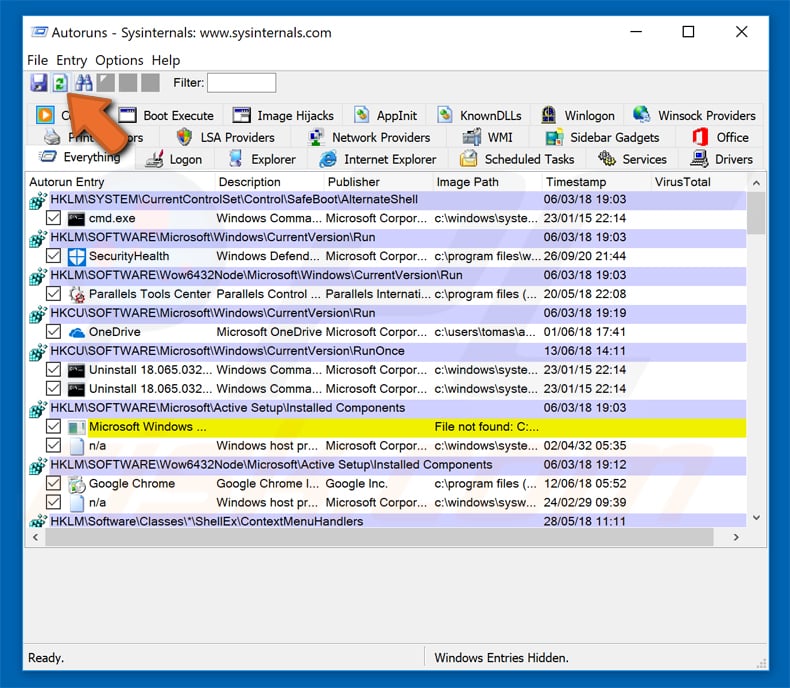
Check the list provided by Autoruns application and locate the malware file that you want to eliminate.
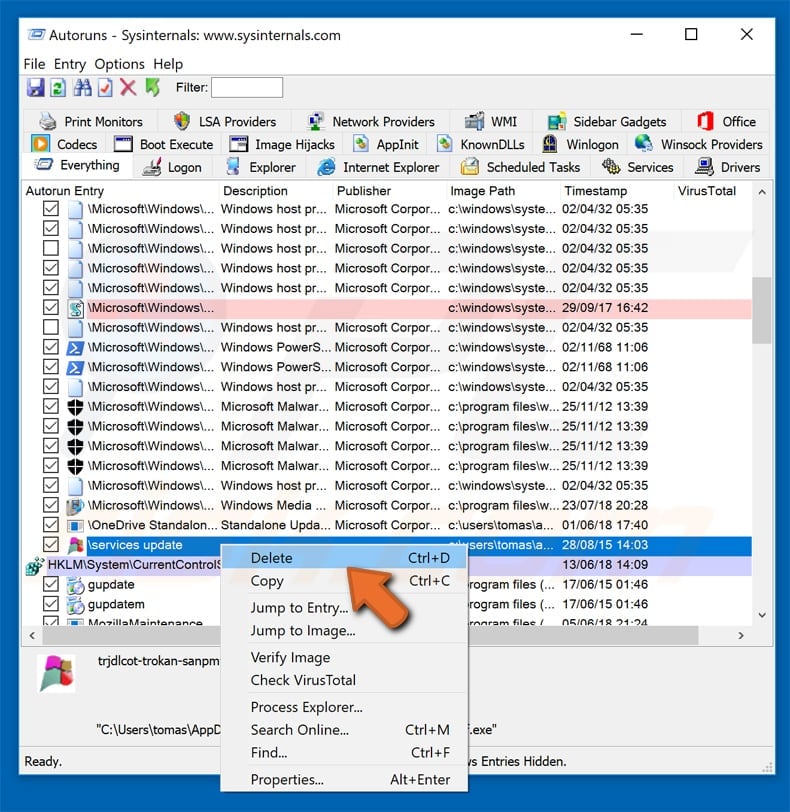
You should write down it full path and name. Note that some malware hides their process names under legitimate Windows process names. At this stage it’s very important to avoid removing system files. After you locate he suspicious program you want to remove right click your mouse over it’s name and choose «Delete»
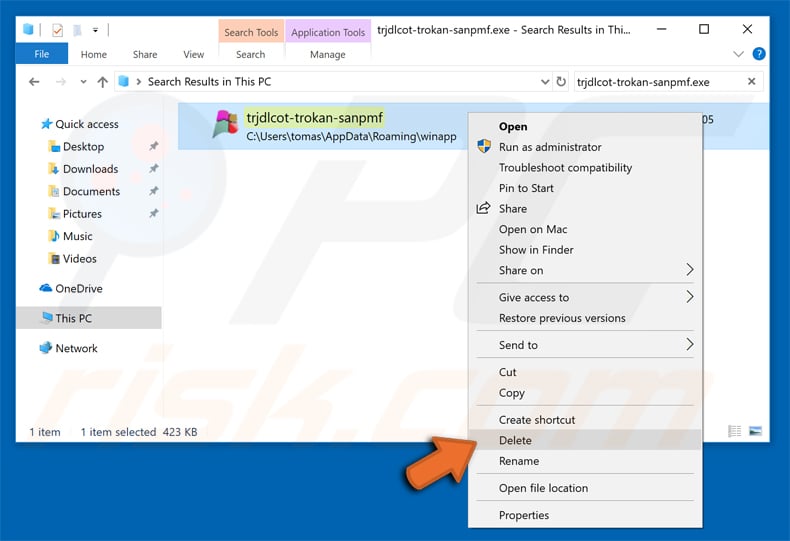
After removing the malware through Autoruns application (this ensures that the malware won’t run automatically on the next system startup) you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the file of the malware be sure to remove it.
Reboot your computer in normal mode. Following these steps should help remove any malware from your computer. Note that manual threat removal requires advanced computer skills, it’s recommended to leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it’s better to avoid getting infected that try to remove malware afterwards. To keep your computer safe be sure to install latest operating system updates and use antivirus software.
To be sure your computer is free of malware infections we recommend scanning it with
Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with COINMINER malware, should I format my storage device to get rid of it?
No, COINMINER’s removal does not necessitate removal.
What are the biggest issues that COINMINER malware can cause?
COINMINER is a cryptominer — a type of malware that abuses system resources to generate revenue. The primary threats posed by such infections include decreased system performance or failure, data loss, hardware damage, and financial losses.
What is the purpose of COINMINER malware?
Most malicious programs are used to generate revenue, and this applies to COINMINER as well since it is a cryptocurrency miner. It is worth mentioning that cyber criminals also use malware to amuse themselves, realize personal grudges, disrupt processes (e.g., websites, services, companies, etc.), and even launch politically/geopolitically motivated attacks.
How did COINMINER malware infiltrate my computer?
Malware is primarily distributed through drive-by downloads, spam emails and messages, online scams, untrustworthy download sources (e.g., freeware and third-party websites, P2P sharing networks, etc.), illegal program activation tools («cracks»), and fake updates. Furthermore, some malicious programs can self-proliferate via local networks and removable storage devices (e.g., USB flash drives, external hard drives, etc.).
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner can detect and eliminate most of the known malware infections. It is noteworthy that high-end malicious programs typically hide deep within systems — therefore, running a complete system scan is crucial.
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
21.04.2023, 07:45. Показов 3484. Ответов 11 Здравствуйте, уважаемые.
0 |
|
Programming Эксперт 39485 / 9562 / 3019 Регистрация: 12.04.2006 Сообщений: 41,671 Блог |
21.04.2023, 07:45 |
|
Ответы с готовыми решениями: JS CoinMiner AV CoinMiner CoinMiner 11 |
|
22347 / 15823 / 3056 Регистрация: 08.10.2012 Сообщений: 64,377 |
|
|
21.04.2023, 09:01 |
|
|
Здравствуйте! Скачайте AV block remover (или отсюда). Если и так не сработает, запускайте из безопасного режима с поддержкой сети. В результате работы утилиты появится отчёт AV_block_remove_дата-время.log, прикрепите его к следующему сообщению. После перезагрузки системы соберите новый CollectionLog Автологером (уже в нормальном режиме).
1 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
21.04.2023, 10:39 [ТС] |
|
|
Отработало только из защищённого режима. Но…
0 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
21.04.2023, 10:42 [ТС] |
|
|
И ещё вот с такой ошибкой при запуске (во вложении). Миниатюры
0 |
|
22347 / 15823 / 3056 Регистрация: 08.10.2012 Сообщений: 64,377 |
|
|
21.04.2023, 10:46 |
|
|
Сообщение было отмечено ip322000 как решение РешениеДействительно, есть проблема. Автор постарается исправить. Пока в безопасном режиме сделайте: Пофиксите в HijackThis следующие строчки: Code O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [1] = eav_trial_rus.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [2] = avast_free_antivirus_setup_online.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [3] = eis_trial_rus.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [4] = essf_trial_rus.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [5] = hitmanpro_x64.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [6] = ESETOnlineScanner_UKR.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [7] = ESETOnlineScanner_RUS.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [8] = HitmanPro.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [9] = 360TS_Setup_Mini.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [10] = Cezurity_Scanner_Pro_Free.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [11] = Cube.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [12] = AVbr.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [13] = AV_br.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [14] = KVRT.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [15] = cureit.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [16] = FRST64.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [17] = eset_internet_security_live_installer.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [18] = esetonlinescanner.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [19] = eset_nod32_antivirus_live_installer.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [20] = MBSetup.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [21] = PANDAFREEAV.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [22] = bitdefender_avfree.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [23] = drweb-12.0-ss-win.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [24] = Cureit.exe O7 - Policy: HKCU\..\Policies\Explorer\DisallowRun: [25] = TDSSKiller.exe O7 - Taskbar policy: HKCU\..\Policies\Explorer: [DisallowRun] = 1 O22 - Tasks: \Microsoft\Windows\WindowsBackup\OnlogonCheck - C:\Programdata\ReaItekHD\taskhostw.exe O22 - Tasks: \Microsoft\Windows\WindowsBackup\RealtekCheck - C:\Programdata\ReaItekHD\taskhost.exe O22 - Tasks: \Microsoft\Windows\WindowsBackup\TaskCheck - C:\Programdata\ReaItekHD\taskhostw.exe O22 - Tasks: \Microsoft\Windows\WindowsBackup\WinlogonCheck - C:\Programdata\ReaItekHD\taskhost.exe O22 - Tasks: \Microsoft\Windows\Wininet\winser - C:\ProgramData\Windows Tasks Service\winserv.exe Task Service\winserv.exe O22 - Tasks: \Microsoft\Windows\Wininet\winsers - C:\ProgramData\Windows Tasks Service\winserv.exe Task Service\winserv.exe Перезагрузите компьютер. В нормальном режиме: Примечание: необходимо выбрать версию, совместимую с Вашей операционной системой. Если Вы не уверены, какая версия подойдет для Вашей системы, скачайте обе и попробуйте запустить. Только одна из них запустится на Вашей системе. Нажмите кнопку Сканировать (Scan).
1 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
21.04.2023, 12:55 [ТС] |
|
|
Благодарю Вас, уважаемый Sandor!
0 |
|
Sandor 22347 / 15823 / 3056 Регистрация: 08.10.2012 Сообщений: 64,377 |
||||
|
21.04.2023, 16:12 |
||||
|
Внимание! Рекомендации написаны специально для пользователя ip322000. Если рекомендации написаны не для вас, не используйте их — это может повредить вашей системе. Дочистим кое-какой мусор. Примите к сведению — после выполнения скрипта (возможно) все открытые вкладки браузеров будут закрыты, произойдет выход из аккаунтов, временные файлы, корзина, история браузеров, куки и кэш будут очищены.
Компьютер будет перезагружен автоматически.
1 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
21.04.2023, 17:27 [ТС] |
|
|
Отработало, перезагрузилось.
0 |
|
22347 / 15823 / 3056 Регистрация: 08.10.2012 Сообщений: 64,377 |
|
|
22.04.2023, 16:57 |
|
|
Хорошо. Если проблема решена, в завершение: Остальные утилиты лечения и папки можно просто удалить. 2.
1 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
22.04.2023, 17:24 [ТС] |
|
|
Спасибо, Sandor! Всё отработало без ошибок, проблема более не проявляется. Лог во вложении.
0 |
|
22347 / 15823 / 3056 Регистрация: 08.10.2012 Сообщений: 64,377 |
|
|
23.04.2023, 11:28 |
|
|
По возможности исправьте: Читайте Рекомендации после удаления вредоносного ПО
1 |
|
1 / 1 / 0 Регистрация: 21.04.2023 Сообщений: 7 |
|
|
23.04.2023, 18:40 [ТС] |
|
|
Обязательно))
1 |
|
inter-admin Эксперт 29715 / 6470 / 2152 Регистрация: 06.03.2009 Сообщений: 28,500 Блог |
23.04.2023, 18:40 |
|
12 |