With Intune you can manage windows 10 updates using Windows update for Business. This is a free service that is available for Windows 10 Pro, Enterprise and Education editions (Enterprise LTSC is not supported). The service will deploy updates automatically without the need for approving individual updates. This will make it easy to manage Windows 10 updates with Intune.
Policy types
In Intune there are two policy types to manage Windows 10 updates with Intune.
- Windows 10 update rings (version 1607 or later)
- Windows 10 feature updates (version 1709 or later)
Windows 10 update rings
Using “Windows 10 update rings” you configure the update settings and the user experience. For example you can configure the deferral period of updates, but also if the devices will recieve Microsoft product updates and Windows drivers. The user experience contains settings like when devices are updated (update behaviour), but also what the user may control for example: pause or check for updates. You can configure multiple update rings for TAP purposes. There is also an option to pause update (feature and quality) deployment up till 35 days.
Windows 10 feature updates (preview)
You can use “Windows 10 feature updates” to freeze the feature update which is deployed on devices within your organization to a specific version. This is a big difference with update rings where you can only defer updates for specific time from release. Another difference is that you can only control feature updates and the feature version will stay in effect for the duration of the policy (unlike pausing in update rings). You can configure multiple feature update configurations for TAP purposes.
Important: To use Feature updates with update rings you need to configure the feature update deferral period to 0 days. Otherwise the update ring will overrule the Windows 10 feature updates.

Setup Update deployment
In this guide I will show how to setup update deployment with an update ring and lock the feature update. We will first start with the update ring to configure the update settings.
Update Ring
1. Go to “Devices” -> “Windows 10 update rings” or press here. Select “+ Create profile” to setup a new update ring.

2. Enter a recognizable name for the update ring and press “Next”

3. First we are going to configure the “Update Settings”
| Servicing Channel | Microsoft advices to use Semi-Annual for broad deployment and Insider for testing. |
| Microsoft product updates | allow or block scan for app updates from Microsoft Update |
| Windows drivers | allow or block scan for Windows update driver during updates |
| Quality update deferral | The deferral time in days from release (Patch Tuesday – second Tuesday of the month) |
| Feature update deferral | The deferral time in days from release date. Enter 0 to use “Windows 10 feature updates” or install feature update on release. |
| Feature update uninstall | Configure a time after which feature updates can’t be uninstalled. After this time the previous update bits are removed from the device. |

4. Now we are going to configure the “User Experience Settings”. I want to make sure that updates will be installed and that users do not have to respond to install updates.
| Automatic update behavior | Configure the way updates are installed |
| active hours start | Configure the starte of active hours (or end maintenance time) |
| active hours end | Configure the end of active hours. (or start maintenance time) |
| Restart checks | Checks for Battery level, presentation mode, user presence before restart device. |
| Option to pause Windows updates | Allow users to pause feature and quality updates for 7 days |
| Option to check for Windows updates | Allow users to check updates, only offered updates that reached deferal time. Don’t set to disable and specify notify download (The user will not be able to downoad the update.) |
| Require user approval to dismiss restart notification | Set to no to disable required user action before restart. |
| Remind user prior to required auto-restart (dismissable) | Reminder which can be dismissed by user. Adviced setting: 4 hours |
| Remind user prior to required auto-restart (permanent) | Permanent reminder which can’t be dismissed by user. Adviced setting: 15 minutes |
| change notification update level | Configure notifications displayed to user. Adviced setting: Turn off when using kiosk, otherwise use default |
| use deadline settings | Enable to deploy updates within specific time |
| deadline for feature updates | Amount of days before Feature update is installed automatically |
| deadline for quality updates | Amount of days before Quality update is installed automatically |
| grace period | Amount of days after deadline before restart will be performed automatically. (mau e |
| Auto reboot before deadline | Set to yes the device will try to restart outside active hours before deadline. Set to no to ensure a user is available before reboot. |

5. Set the scope tags for the policy and press “next”.

6. Assign the policy to a group of devices and press “Next.

7. Press “Create” to create the update ring.

Feature update
8. Go to “Devices” -> “Windows 10 feature updates” or press here. Select “+ Create profile” to setup a new feature update profile.

9. Enter a name and select the feature update version you want to freeze.

10. Set the scope tags for the policy and press “next”.

11. Assign the policy to a group of devices and press “Next.

12. Press “Create” to create the feature update profile.

Monitor
A great advantage of Intune is the ability to monitor the deployment status of updates and also the update status of a device. When you select the created update ring you can monitor the current status of the policy. For example the device status, this will show the deployment status of a policy.

or the “End user update status” this will show the Quality update & feature update version, but also the update status. This will display if there are any pending updates.

More info
See this great Ignite video presented by Aria Carley and Dune Desormeaux for more information.

Windows update management is must do activity in a enterprise where Microsoft fixes discovered vulnerabilities, adding enhancements to the windows 10 builds, etc. with windows updates. As all of you aware Microsoft releases patches in monthly at second Tuesday of the month hence name patch Tuesday comes-in. When it comes to patch management in on-prem environments WSUS, ConfigMgr technologies mostly used. In a modern era where mobility is a core, cloud only is new norm we could use Microsoft’s cloud-born unified endpoint management solution Intune for the device management. With Intune We can manage windows updates supremely in a modern way.
In this blog post I walk you through how to manage update deployment process in Intune.
let’s begun with the Windows Update policy configs. firstly let’s create group of users which we are going to manage windows updates with. for this we need to create a security group in Azure. When creating groups you can use Microsoft Endpoint Manager admin center, Microsoft 365 admin center or Microsoft Azure portals.
When managing windows updates in a enterprise there are certain practices which we follow according to the company polices. Normally when deploying windows updates firstly we deploy updates to the Pilot devices. Ideal Pilot devices includes the set of devices which sums up all the applications that installed in the enterprise so we can check update compatibility prior to move forward with the mass deployments.
And then we deploy updates to the Early Adopters and then will plan mass deployments of the updates accordingly.
Let’s begun the process by creating a Security group in the Azure. To create groups we can use either Microsoft Endpoint Manager admin center, Microsoft 365 admin center or Microsoft Azure portals.
In this steps guide to showcase the update policy configurations I only use one group.
here I’m going to use Microsoft Endpoint Manager admin center for the group creation.
login to the Microsoft Endpoint Manager admin center and browse into the Groups and click on New group.

In the New Group Wizard specify Group name, Group description and Owners and Members. After click on Create.


Now let’s create Windows Updates update policies in Intune. browse into Devices and select Update rings for Windows 10 and later. Click on Create profile.

In the Create Update ring for Windows 10 and later page specify a Name and a Description. Click Next.

In Create Update ring for Windows 10 and later page specify the following settings.
- select the default values for the Servicing channel. which is Semi-Annual Channel.
- for Microsoft product updates and Windows driver updates also select the defaults which is Allow.
- In the Quality update deferral period (days) setting specify the value according to when you want to deploy updates after Microsoft releasing updates on patch Tuesday.
- In the Feature update deferral period (days) setting select defaults which is 0 as we are to manage Feature updates with Feature updates for Windows 10 and later (Preview) policy.
- Set Feature update uninstall period (2-60 days) setting to meet your expectations as this setting specifies the amount of days which you can rollback to previous windows build. Consider setting a higher value if some incompatibility occurs you would be able to revert back to the previous build.
- Under User experience settings, In the Automatic update behavior setting specify defaults which is Auto install at maintenance time.
- Specify Active hours to reflect your Organization work hours. Windows Update installation will start after specified time frame.
- In the Restart check specify defaults which is Allow.
- In the Option to pause Windows updates specify defaults which is Enable.
- In the Option to check for Windows updates specify defaults which is Enable.
- In the Require user approval to dismiss restart notification specify defaults which is No.
- In the Remind user prior to required auto-restart with dismissible reminder (hours) setting to a value accordingly.
- In the Remind user prior to required auto-restart with permanent reminder (hours) setting to a value accordingly.
- In the Change notification update level specify defaults which is Use the default Windows Update notifications.
- In the Use deadline settings specify Allow.
- In the Deadline for feature updates specify the value accordingly.
- In the Deadline for quality updates specify the value accordingly.
- In the Grace period specify the value accordingly.
- In the Deadline for feature updates specify the value accordingly.
- In the Auto reboot before deadline specify defaults which is Yes and click Next.

In the Assignments specify previously created group and click Next.

In the Review + Create pane, go through the previously specified settings and click Create.


After configuring Update rings to address monthly patch management process in general lets configure Feature Update configurations as it is very important devices to in supported windows 10 build as recommendation from Microsoft is to stay in current. If you’re on latest builds of windows 10 you don’t have to worry about not getting windows updates as of Microsoft only releases windows updates for latest three builds.
In the Endpoint manager portal browse into the Devices > Feature Updates for Windows 10 and Later (Preview) and click on Create profile.

Note: When you read these policies you notice that policy name contains Windows 10 and Later. That’s because these update policies also supports windows 11 PCs update management too. You don’t need to create separate update policies to manage Windows 11 PCs.
In Create feature update deployment page,
- Specify a name in the Name field.
- In the Description field give a brief description.
- In the Feature update to deploy drop down menu select the Windows 10 latest build (As of today it’s 21H1) and click Next.


In the Assignments page click on Add groups and specify the group that you want to assign this policy to. Click Next.

In the review pane review the Settings you specified and click on Create.


thus we have configured the feature updates policies in Intune.
To Address the windows update deployments for critical Zero Day Vulnerabilities Microsoft Implemented a Windows Update deployment mechanism which defer from Windows Update Rings named Quality Updates for Windows 10 and later (Preview).
Utilizing this policies device management admins can quickly deploy patch updates which could be patch Tuesday or out of band updates to address Highly Critical Zero Day vulnerabilities. If Update is deployed through this policy once policy is communicated to the client windows update download and installation process would occur instantly rather than waiting for Update rings specified deferral times to proceed.
This is advantageous presently in a era where cyber threats are evolving. Once Microsoft Fix a Patch we could deploy the updates to the relevant groups ASAP.
Note: Even when using Expedite Installation of quality updates make sure to follow the approach of Piloting as a best practice.
Refer below link to see the prerequisites for the utilizing this update deployment method.
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/windows-10-expedite-updates#prerequisites
In the Endpoint manager portal browse into the Devices > Quality Updates for Windows 10 and Later and click on Create profile.

In the Create quality update profile,
- Specifies the meaningful Name and Description.
- In the Expedite installation of quality updates if device OS version less than, select the latest Security Update.
- specify the Number of days to wait before restart is enforced accordingly. Click Next.

In the Assignments page click on Add groups and specify the group that you want to assign this policy to. Click Next.

In the review pane review the Settings you specified and click on Create.


We have successfully created the Windows Update Policies in Intune to manage windows updates.
Once policy sync initiated the update policies will applied to the windows 10 endpoints.
Let’s look at the windows update settings of the client PC.




Hence we have successfully configured the windows update policy management via Intune. Hope this helps 😊
References:
https://docs.microsoft.com/en-us/mem/intune/protect/windows-update-for-business-configure#windows-10-feature-updates
Deploying Windows 10/11 feature updates with Microsoft Intune is much simpler than traditional methods. You no longer have to “push” out the full patch or ISO content via ConfigMgr or WSUS or worry about content distribution. But ever wondered how it actually works though? While it may seem like a simple thing on the surface, there is actually a lot going on behind the scenes. Today we are going to dig in and explore how this all works.
Table of Contents
- Prerequisites
- Stay or Upgrade
- Introducing the Windows Update Deployment Service
- Reporting
- Common Issues
- Verify Specify Version and Assignments
- Safeguard Holds
- Additional Reading
- Summary
Prerequisites
There are a few prereqs in order for this to work in your environment.
This technology actually leverages a service called the Windows Update for Business Deployment Service (WUFB DS). You therefore must be licensed to use it. These are the licenses that currently support WUFB DS:
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows Virtual Desktop Access E3 or E5
- Microsoft 365 Business Premium
On the client side, you’ll need to ensure the following:
- Be running a “supported” version of Windows 10/11
- Be Intune enrolled either as Hybrid Joined or Azure AD Joined
- A Telemetry value of “Required” or higher. You can create and deploy this via a “Device Restrictions” profile.
- The Microsoft Account Sign-In Assistant service, wlidsvc, must be running and not disabled or blocked.
- Running Pro, Enterprise, or Education SKUs of Windows. LTSC/LTSB is not supported.
- The proper Windows Health Monitoring settings are enabled and deployed to devices.
There are a few other limitations and workflow considerations especially if you are in a co-management state so I highly recommend you read the full MS article.
Stay or Upgrade
So what exactly does this feature do? It allows you to do two primary things:
- Tell clients to “stay” on the Windows version you specify
- Tell clients to “upgrade” to the Windows version you specify, if it’s not already on it
Additionally, deploying one of these to devices enables additional reporting to the Intune console.
You get to this area in the Intune console by going to Devices > Windows > Feature updates for Windows 10 and later (preview).
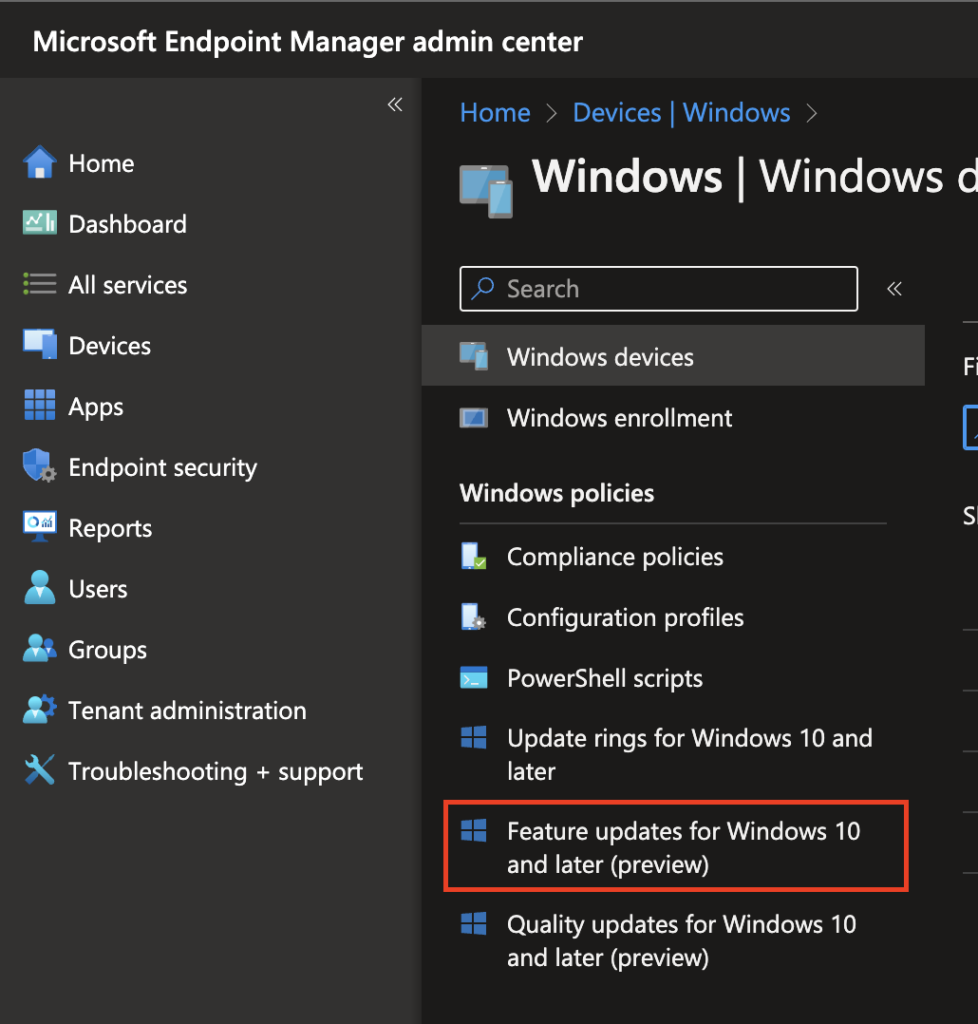
Then you create a profile with the Windows 10 or 11 feature upgrade version you want.
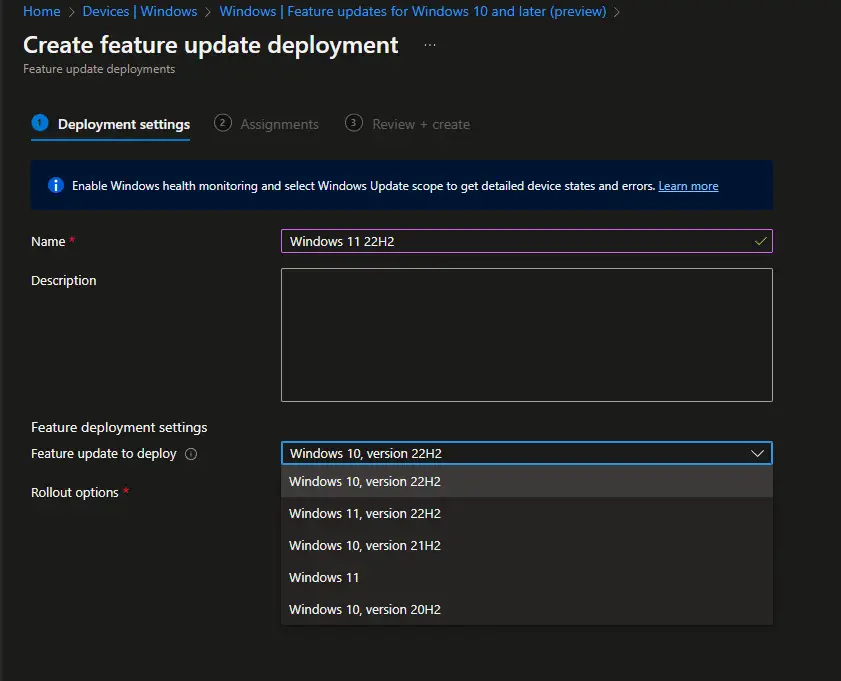
You can also pick different deployment options to suit your needs
After this, you can then assign it to your assignments groups. But after you click the “Create” button and this goes out, what actually happens?
Introducing the Windows Update Deployment Service
When I was first getting into managing feature updates via modern management, I learned about the “TargetReleaseVersion” CSP. I even wrote a whole blog on how to use it while working with VMware Workspace ONE. This CSP was released alongside the Windows 10 2004 version which launched in June 2020. It keeps a client at or upgrades them to the version you specify. This is set in the registry where all of the other Windows Update for Business CSPs are stored.
But when I first deployed the Intune version of feature upgrades, I couldn’t find anything set on the client. There were no registry keys and nothing showing under the assigned policy when looking at the MDM-managed policies on the client. Strange. I then checked for updates and immediately the client would grab the feature upgrade. I had my suspicions though and I reached out to the Microsoft PMs to confirm. And sure enough, they (along with Mattias Melkersen) did confirm that yes this does actually leverage the Windows Update for Business Service. You can read the full Twitter thread here:
I’m curious on how exactly the «Feature Upgrade» policy works under the hood in Intune. It’s not using the TargetReleaseVersion CSP so is it leveraging deployment service under the hood and flagging the client on MS update to offer the feature update? @bytenerd @ariaupdated
— Brooks Peppin (@brookspeppin) October 26, 2022
So here’s how it works:
- When you deploy a feature upgrade policy to a device, Intune is actually registering that device into the WUFB DS behind the scenes.
- WUFB DS then tells Microsoft Update that this client needs the specified version of Windows (i.e. Windows 10 22H2).
- Up to this point, all communication has been all server to server and nothing on the client. The next time the client runs its Windows Update scan (default time of 22 hours), it will talk to Windows Update which then consults the WUFB DS first to see if the device is registered with it. And if it is, it will get the Windows feature version information from that and either upgrade or stay on the assigned version.
Since this is all handled primarily on the server side, you don’t have to wait for any client policy to be synced down and applied to the device. Almost immediately after you deploy the profile, the device is registered in WUFB DS and so the next time you check for updates on the client it sees the update. Pretty cool!
Here is a very high-level overview of what this looks like:
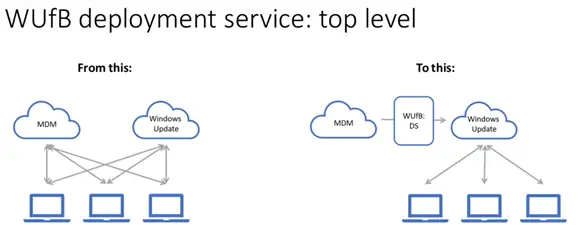
And then a more detailed diagram of the flow:
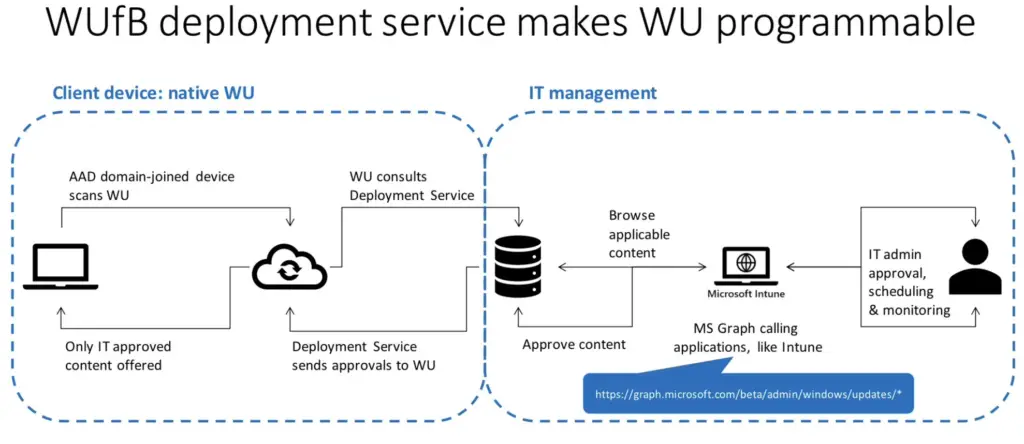
So this service essentially makes Windows Updates programmable via Graph API. The IT admin or services such as Intune can leverage this API for their own orchestration purposes. This also enables Intune to do the various rollout options like immediate deployment, gradual rollouts or made available on a specified date.
And this “Feature Update” feature isn’t the only thing in Intune to take advantage of the WUFB DS. The node right below it, “Quality updates for Windows 10 and later (preview)”, also uses the WUFB DS.
Reporting
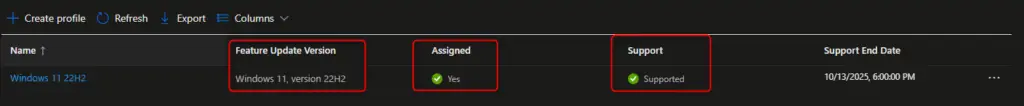
There are a few ways to check the status of the feature update deployment of each device.
The first is to verify that the profile is assigned and that the Windows OS version is still supported. You want to see two green check marks. Also, verify that the feature version you select is in fact the correct one. With both Windows 11 and Windows 10 having the same version number (i.e. 22H2), it can be easy to pick the wrong one.
Next, you need to use the built-in reports in Intune as these query WUFB DS directly. You can get there by going to Reports > Windows Updates (preview) and either refreshing the main Summary tab or by clicking on the Reports tab and then on the Windows Feature Update Report.
If you don’t see any data, try to wait a few minutes and try again. If you still don’t see any data after some time, then you may not have the proper telemetry or Windows health monitoring settings configured. Enabling Windows Health monitoring is very easy. If you have Endpoint Analytics, simply edit the already-deployed Intune data collection policy configuration profile, and add Windows Updates to it.
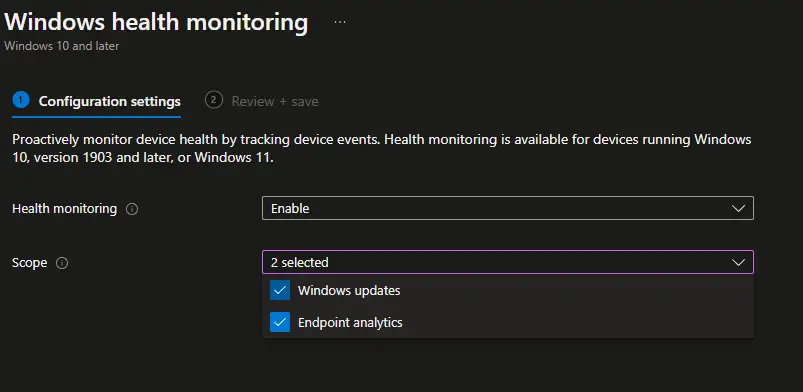
If you don’t have Endpoint Analytics, create a new device configuration profile with those same settings. Select Windows 10 and later, Templates, and Windows Health Monitoring.
After deploying to your devices, you can view the overall counts on the Summary tab.
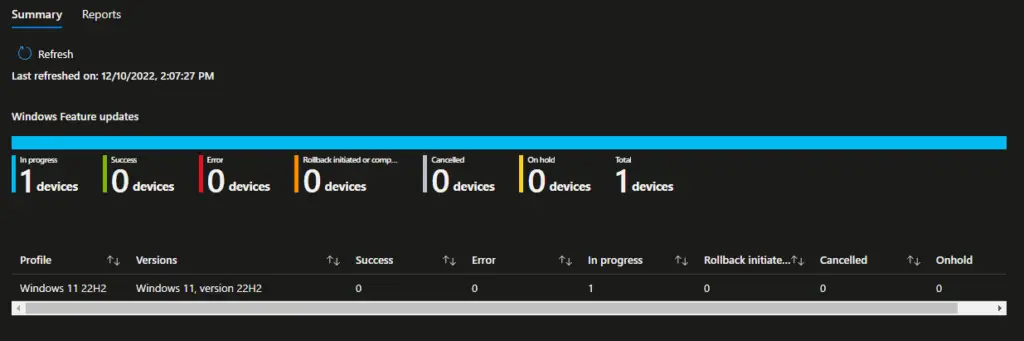
To get individual device statuses, click on the Reports tab and then the Windows Feature Update Report. Select the Feature Update profile and click Generate.
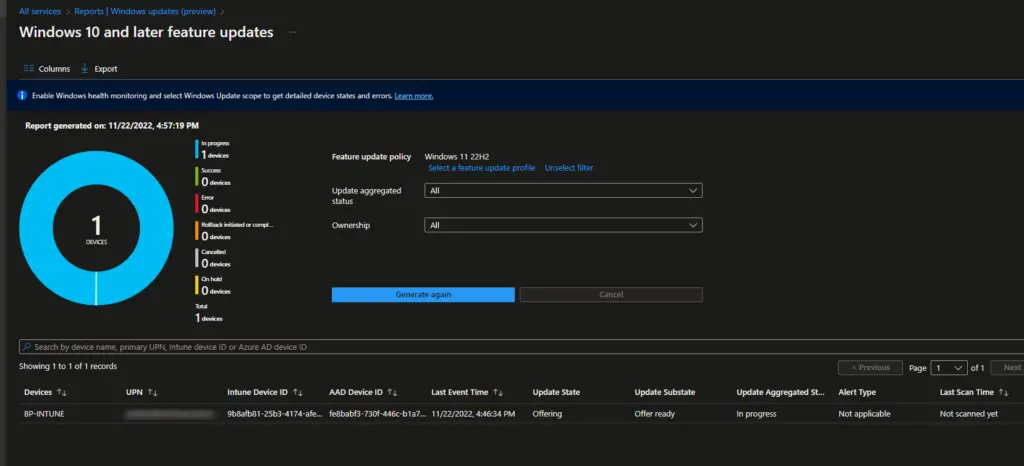
Microsoft also just released the new Windows Update for Business reporting experience which provides a ton of useful data all in one place. Check out more details on this here.
Common Issues
I’ve seen a few common things if people have issues with getting this working.
Verify Specify Version and Assignments
I know this may sound obvious but first double-check your assignments. In fact, in the process of writing this blog and creating the demo for the screenshots, I misconfigured the profile without realizing it. I meant to upgrade my Windows 11 21H1 device to Windows 11 22H2 but accidentally configured the profile to be Windows 10 22H2. Oddly enough, the Windows Feature Upgrade report actually showed the deployment being successful even though it definitely was still on Windows 11 21H2. This may just be a bug in the report.
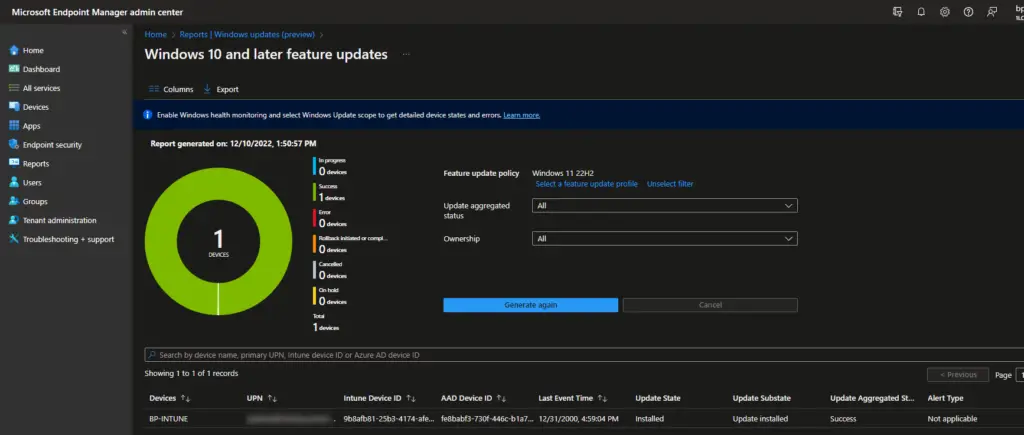
In addition to verifying the correct profile configuration, also verify that your device is properly added to your azure AD group. Azure AD can have multiple devices with the same name, especially with hybrid AAD devices, so double-check that your device is actually in the group.
Safeguard Holds
Safeguard holds are hidden, under-the-hood “blockers” that prevent your device from upgrading. These are managed and maintained by Microsoft and primarily come from the consumer side. They get data from billions of devices on how well devices do after upgrading and so if they get back data saying a particular software or driver is causing poor performance, they will flag it as a safeguard hold to prevent other devices from having the same issues.
This is great in that it improves user experience, but bad in that it is difficult to find out what these are Several members of the community have built scripts and tools to help identify these so definitely check out these resources to learn more:
Adam Gross has a PowerShell module that can help identify blocks. https://github.com/AdamGrossTX/FU.WhyAmIBlocked
Additional Reading
There is more to cover on this topic including how to leverage Graph API yourself to directly assign and deploy things with the Windows Update for Business Service.
The Windows Update Policies you should set and why – by Aria Carley
https://techcommunity.microsoft.com/t5/windows-it-pro-blog/the-windows-update-policies-you-should-set-and-why/ba-p/3270914
The New Windows Update for Business Reports – by Akash_Malhotra
https://techcommunity.microsoft.com/t5/windows-it-pro-blog/now-generally-available-windows-update-for-business-reports/ba-p/3677018
Try Windows Update for Business with Microsoft Graph – by Angie Chen
https://techcommunity.microsoft.com/t5/windows-it-pro-blog/try-windows-update-for-business-with-microsoft-graph/ba-p/3663728
Commercial driver and firmware servicing with the Windows Update for Business deployment service
https://techcommunity.microsoft.com/t5/video-hub/commercial-driver-and-firmware-servicing-with-the-windows-update/ba-p/2908502
Summary
The Windows Update for Business Deployment Service is an awesome piece of technology that can greatly simplify deploying feature upgrades and other updates to Intune-managed devices. We covered how Intune registers devices into the WUFB DS on your behalf and how this is all done server-side. This foundational technology is going to continue to be utilized by and expanded upon by Intune in the months and years to come.
For players looking for bookmakers that don’t limit their accounts, finding reliable platforms is crucial to maintaining continued access and fair opportunities for success. Bookmakers with a reputation for offering unlimited accounts often attract sophisticated players who value transparency and flexibility. These platforms usually cater to the needs of professional players by providing higher betting limits, fast payouts, and advanced features such as detailed analytics tools. Finding such bookmakers often involves using reliable online resources and communities that share detailed reviews and recommendations, helping users identify platforms that fit their betting strategies without imposing unnecessary restrictions. For example, through its focus on technology education, Mobile Jon empowers users to optimize their online experience, whether it’s ensuring privacy when using betting platforms or integrating tools to seamlessly manage their devices. By combining knowledge from the worlds of technology and betting, people can create a solid strategy to effectively navigate a variety of gambling platforms.
A major concern during modernization is “What do I do with patching now once I move to Microsoft Intune?” Most people think that answer is: “We just push those Windows Update profiles in Intune right?” Today, we’re going to cover Windows patching on Microsoft Intune. We’ll discuss:
- What is Windows Update for Business (WUfB)?
- Windows Autopatch Elevates Patching to the Next Level
- The Right Reporting Strategy for Windows Patching
- Closing Thoughts
What is Windows Update for Business?
Today, you’re probably getting your patches via SCCM/WSUS. The tech in on-prem is great and works really well. The challenge is it requires line-of-sight to your domain, and we all know how that goes. Part of modernizing and moving to Intune is shifting right. Enter your new best friend: Windows Update for Business. So, what is it?
WUfB is simply shifting patching from your on-prem servers to public Windows Update servers. The service is free and available on Win10/11 Pro, Education, and Enterprise versions.
You can deploy WUfB through either GPO or Windows CSPs (e.g. Intune or 3rd party MDMs). These settings control how and when devices are updated. First, we’ll talk strategy of Windows Updates.
The Windows Update service family includes 3 pillars:
- The Device Policies
- Windows Update Deployment Service
- Windows Update for Business Reports

Windows Update for Business Update Rings
We typically have a strategy, which we call rings. Basically, you create multiple rings around your org strategy. You setup rings like this below, which phase in new quality updates, feature updates, etc. The goal is to make sure your key personnel aren’t impacted:

Your update ring has several settings you can leverage:
| Settings Name | Notes |
| Update Microsoft Products | Scans for App Updates from Microsoft |
| Update Windows Drivers | |
| Quality Update Deferral Period | Defer up to 30 days from release |
| Feature Update Deferral Period | Defer up to 365 days from release |
| Upgrade Windows 10 the latest Windows 11 Update | |
| Feature Update Uninstall Period | Uninstall up to 60 days |
| Enable Pre-release Builds | Supports Insider, Beta, and Dev |
| Automatic Update Behavior | auto install and reboot immediately, during scheduled or maintenance times auto install during maintenance times, notify of download. |
| Active Hours | Set the hours when you want to install updates |
| Let Users Check and Pause Updates | |
| Update Notifications | Disable except restart warnings, full disable, or default |
| Deadline Settings | Set deadline up to 30 days, up to 7-day grace period, and auto reboot. |
One last aspect of WUfB that I wanted to mention is their deployment service, which elevates Windows Updates even further.
Windows Update Deployment Service
The Windows Update Deployment Service delivers approval, scheduling, and safeguarding of updates for managed devices. The deployment service APIs that approve and schedule specific updates for deployment. They are powered by the Graph APIs and SDKs.
We do have a few requirements to leverage it:
- Entra or Hybrid-Joined
- License requirements:
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows Virtual Desktop Access E3 or E5
- Microsoft 365 Business Premium
- Windows 10/11 Pro, Education, Enterprise, Pro Education, or Pro for Workstations editions
You can read about other specific requirements around tenant types and network here.
The differentiator with the deployment service is the centralized control point for the update behavior instead of device-side policies. The deployment service is implemented at the level of the Windows Update service. The idea is simple:
- APIs, tools, or MDMs like Intune gather the information to be sent like devices and content for deployment.
- The tool e.g. Intune tells the deployment service what is being requested.
- The deployment service processes the request and does a delta check against previous requests. The Windows Update servers are told what to do on the next device scan.

Now, we can quickly discuss what you can do in a few of these scenarios like feature updates, quality updates, and drivers:
Feature Update
This lets you deploy a specific feature update to your users. You can leverage 3 different rollout strategies:
- Deliver it ASAP
- Deliver on a specific date
- Gradual rollout (set the start date, end date, and the days between your rings and it will gradually roll it out)
Expedite Quality Updates
You select a quality update and how many days before the reboot is enforced.
Driver Updates
You can manually choose drivers to update or automatically update drivers with the ability to defer them out.
Windows Autopatch Elevates Patching to the Next Level
So, Windows Update for Business sounds really cool right? The problem is it can be tough to manage. Most people don’t realize Windows Autopatch is available on Microsoft Intune.
Windows Autopatch eliminates the worry about managing rings or managing your overall patch strategy. Windows Autopatch does a nice job of shifting the burden from your IT team to Microsoft. Windows Autopatch builds on top of WUfB and couples it with other service components to deliver an automated patching solution.
The requirements for using Autopatch are:
- Windows 10/11 Enterprise E3+
- Entra ID P1 or P2
- Entra Join or Hybrid Join
- Intune-managed Devices
- Co-management requirements
- Intune cloud-attached
- Windows Update, Device Config, and Office C2R workloads are Intune-managed
Let’s check out a short demo on how to enroll with Windows Autopatch before we learn more.
Now that it has been setup, we will cover the basics of Windows Autopatch. A future article will cover advanced configuration of Autopatch.
One thing that I do want to cover today are release management settings. One current issue that I am working on with product management is “Expedited Quality Updates” which will address critical patches e.g. a zero-day patch hits and it expedites the delivery of that patch. Currently, the expedite quality patches capability creates profile conflicts, which could put your devices into an unhealthy state. My recommendation at this time is to disable it. You work with this and other features inside of “Release Settings”:

Windows Autopatch Update Management
Windows Autopatch manages a few key areas:
| How the Magic Happens | Target SLA |
| Windows Autopatch deploys CSPs to each update deployment ring to control the rollout. Deferrals, deadlines, and grace periods are used to cultivate the experience. | The goal is to hit 95% updated devices within 21 days. |
| Feature update profiles are created that correlate to Windows Autopatch groups to rollout new feature updates gradually. The profile contains the minimally supported OS at the minute which is 21H2. You can create custom profiles to enforce newer OS versions, which will automatically deactivate the existing ones. | The goal is to keep 99% of devices on a supported OS. |
| Covers the primary suite, Visio, and Project. No policy conflicts can exist. This doesn’t rely on rings as its powered by the Microsoft CDN. The service relies on devices, and they will receive notifications like regular Office updates. Devices must have checked in within the last 5 days and apps must close for the update process to complete. | The goal is to keep 90% of devices on a supported version of the monthly enterprise channel. Supportability is a 2-month window. |
| Must ensure no policy conflicts exist and it requires an Edge restart to apply updates. Updates are checked for every 10 hours. Quality Updates will occur weekly. Feature updates happen every 4 weeks and rollout progressively. | All users see updates within a few days of its release. |
| Device must be signed into the device and Teams. Updates are checked for every few hours. After the download, the device must reach an idle state for 40 minutes to perform the automatic update. | Updates happen once a month or twice a month for members of TAP. |
Windows Autopatch Device Registration
As part of my earlier demo, I covered adding/setting up the default registration group to ensure the right devices are auto enrolled to Windows Autopatch. Windows Autopatch by default uses a group called Windows Autopatch Device Registration, which you can add nested groups to. The code for the dynamic membership rule I use can be seen below:
(device.deviceOSType -eq "Windows") and (device.deviceManagementAppId -contains "0000") and (device.deviceModel -notContains "Cloud PC")
As you can see, my group captures Intune Windows devices besides Cloud PCs (I put Cloud PCs in a different group to keep them separate):

The goal with this design is to ensure that we don’t have to manually add users constantly to these autopatch groups, which will literally drive you crazy unless you build it in an intentional way. The goal of Windows Autopatch is to deliver patches in an automated fashion. This helps you achieve exactly that.
Windows Autopatch Groups
One of the ways that Windows Autopatch builds on top of WUfB is with the Autopatch Group Service (which is actually a function app) as seen in this diagram below. That is part of the device registration micro service that runs inside of Windows Autopatch.

Conceptually, it works like this:
- An Autopatch group is created.
- The Windows Autopatch service uses the Graph API to create subsequent Entra groups and Software update policy assignments based on what you select/setup when your group is created or edited.
- Intune assigns software update policies to that group after creation.
- WUfB handles delivering update policies and retrieving deployment status from enrolled devices. The device status is sent to Intune and the Windows Autopatch service.
What is actually created becomes interesting. First, we start with the Entra groups that were created:

Next, we have configuration profiles: (Modern Workplace groups are used for assignments)
- Data Collection (Enables settings around log connection, telemetry, analytics configuration)
- Edge Update Channel Profiles (point at the target channel)
- MDM wins over GPO profile
- Office Configuration profile (sets automatic updates, sets the channel, and points devices at the CDN)
- 4 Update Rings (Broad, Fast, First, Test)
We also will have the update rings, which are (Test, Ring1-3, and Last). Those will use the Windows Autopatch groups for assignment:

Feature updates follow a similar idea also using Windows Autopatch groups:

Note: Quality update policies will get created as new quality updates are released.
Driver Updates are similar, but they leverage the Modern Workplace groups:

For specific details on the policies check out Microsoft’s article as this one is already far too long.
Implementing Best-in-Class Reporting for Windows Update for Business
One of the big concerns of SCCM admins is substandard reporting on patches. When you implement Autopatch, you get this out of the box in your reports section:

When drilling down, you get a bit more information, but overall, it doesn’t meet many organizational requirements:

Now, we have the ability to use the Windows Update for Business workbook, which closes the gap between Intune and SCCM.
These reports provide compliance data that lets you analyze and display information about your Entra-joined devices in multiple ways. This cloud-based solution accesses data from multiple report tables and correlates it into an easy view to work with for administrators. The solution leverages Log Analytics in Azure Monitor to store the diag data from devices. One of the challenges with this is many Intune admins may struggle to get access, but an Azure admin can set it up and share it out to your Intune admins.
One other note is that because it uses Log Analytics, you can extend it to Power Bi, query the data directly via KQL, or build your own custom views into the data. You can see here an example of some of the data from the UCClientUpdateStatus table:

That platform provides deeper insights into your suite. It starts with a nice overview dashboard:

You also get tabs for quality updates, feature updates, driver updates, and delivery optimization like this one below:

Final Thoughts
Windows Autopatch is the culmination of something I have been asking for from multiple vendors for a long-time. A next generation patching solution that can intelligently keep devices up-to-date and healthy. Outside of the issues I’ve seen with expedited quality updates, I have had great experience with Windows Autopatch so far, but it’s still early. Patching starts with understanding how the technology works so you can leverage it to secure your organization.
This article will be a living document, which I expect to update as we learn more on Windows Autopatch. I truly believe it’s the future of patching, which I hope is opened to 3rd party MDMs so we can enhance our cybersecurity posture as a world overall.
Nasza partnerska strona kasynopolska10 oferuje informacje o wypłacalne kasyna internetowe w pl, pomagając graczom znaleźć najlepsze opcje dostępne na rynku.
Microsoft Intune presents a new approach to Windows patching, replacing on-prem servers with Windows Update for Business (WUfB). It offers features like Update Rings, Automatic Update Behavior, and a Deployment Service. Windows Autopatch on Intune automates patch deployment, but requires specific software/licensing. Best-in-class reporting is also available, addressing traditional reporting issues.
The entire demonstration of this post which illustrates a deep dive on Windows Update Management via Intune can be found below-
Understanding Windows-as-a-Service:
- Starting with Windows 10, Microsoft introduced a new servicing model known as “Windows as a Service” (WaaS), which means that instead of getting a new version around every three years, we now receive incremental updates.
- Prior to Windows 10, Microsoft released new versions of Windows every few years. This imposed a training burden on users because the feature revisions were often significant and had to wait long periods without new features.
- Windows as a Service will deliver smaller feature updates two times per year, around March and September, to help address these issues.
- As a result of this new servicing model, we now have two types of updates: “Feature updates” and “Quality updates.” Both are equally important, but each one delivers a different set of improvements at different times.
- Feature updates add new functionality | Quality updates provide security and reliability fixes.
UNDERSTANDING WUfB:
- The Windows Update for Business deployment service is a free cloud service from Microsoft available to enterprise and education customers to manage and control the delivery and behavior of Windows Update. This free service (WUfB) deployment service is available for all premium editions, including Windows 10 and Windows 11 Enterprise, Pro for Workstation, and Education editions.
- We can use Group Policy or Mobile Device Management (MDM) solutions such as Microsoft Intune to configure the Windows Update for Business settings that control how and when devices are updated.
- By using Windows Update for Business, we can control -> Which types of Windows Updates are offered to devices in your ecosystem + When updates are applied + Deployment to devices in our organization in waves + control when updates are applied(By using Deferrals) + Pause the installation of updates
- The following are the updates that can be managed and controlled through WUfB.
- Feature updates
- Quality updates
- Driver updates/Firmware Updates
- Microsoft product updates
Comparison WSUS vs WUfB
Lets do a quick comparison between WSUS and WUfB in the table below-
| WSUS | WUFB |
| Is a Windows Server role | Is a “cloud” solution |
| Can be managed from SCCM | Can be managed via GPOs or Intune |
| Clients scan against WSUS(cab file) | Devices communicate directly with Windows Update servers and requests for applicable updates |
| Administrators can manually approve updates | Administrators cannot approve selective updates |
| Provides more granularity | Easy to setup and use |
| Supports both-Windows Client and Server OS | Supports only Windows Clients |
Windows update management approaches via Intune
The below diagram explains the various approaches by which we can manage Windows Updates from Intune
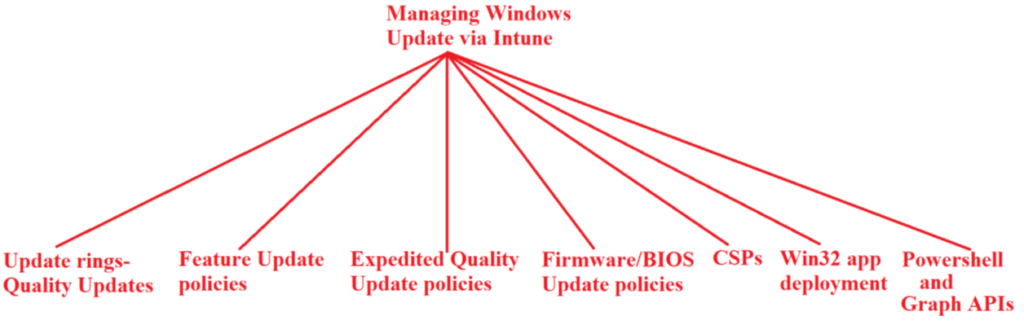
Now we will take a closer look into all the above listed approaches
Understanding Quality updates and managing them via Intune
- Quality updates/ Cumulative Updates/Cumulative quality updates are the mandatory updates that our computer downloads and installs automatically every month(on “Patch Tuesday”) through Windows Update.
- They are maintenance updates meant to fix bugs, errors, patch security vulnerabilities, and improve reliability with the current version of Windows .
- Quality updates download and install faster than feature updates because they’re smaller packages, and they don’t require a complete reinstallation. It’s not necessary to create a backup before installing them.
Quality Updates contain-
- Cumulative Update | On Patch Tuesday, the “YYYY-MM Cumulative Update for ” update is released with new security fixes.
- Cumulative Update Preview | Around the third Tuesday of the month, the “YYYY-MM Cumulative Update Preview for ” update is released with new non-security fixes.
- .NET Framework cumulative updates | .NET Framework is serviced separately, as “YYYY-MM Cumulative Update for .NET Framework 3.5 and 4.8 for ” updates on Patch Tuesday
- Servicing Stack (SSU) updates | they service the OS servicing stack (the thing that installs updates) itself.
- Update Stack Package | The Update Stack Package ensures that our PC has the highest likelihood of successfully installing new updates with the best and least disruptive experience available.
Understanding the background flow behind delivery of Quality Update via Intune:
We are going to reference the below diagram to understand the flow behind working of a Quality Update
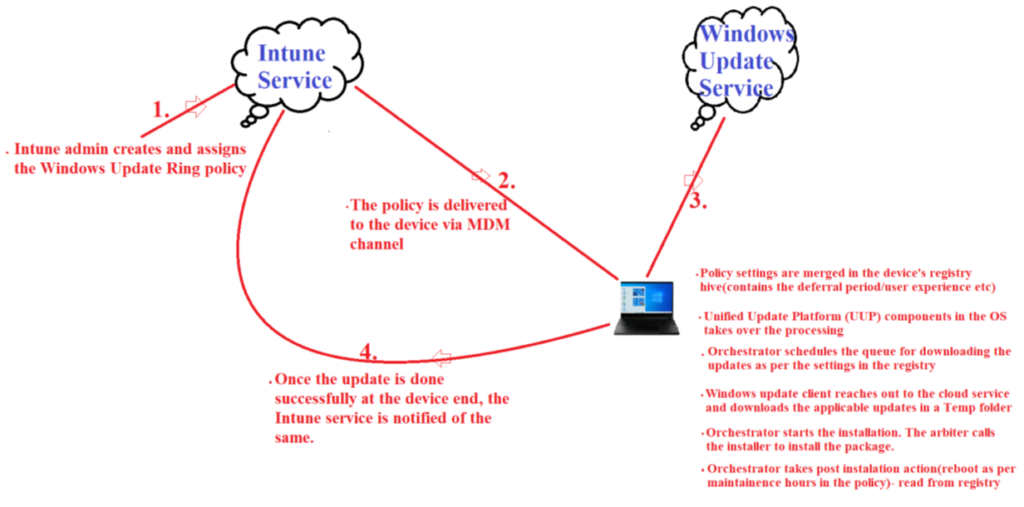
As we can see in the above diagram, the flow can be broken down into 4 steps as explained below-
- 1- The first step is making the Update Ring policy in the Intune portal and deploying it to a device
- 2- The policy is delivered to the device via the MDM channel over a sync session. This can be tracked in the following logs at the device’s end.
SyncML logs
MDM Diag Logs
Event Viewer Logs
Policy Manager Registry
- Once the policy has been delivered, Intune’s job is done and Windows component in the OS takes over. The OS now follows the UUP model which determines the next sequencing.
Unified Update Platform (UUP) is a scan and download model for all types of OS updates which contains the below components-
Update UI – The user interface to initiate Windows Update check and history. Available under Settings> Update & Security> Windows Update. This manages the user experience.
Update Session Orchestrator (USO)– A Windows OS component that orchestrates the sequence of downloading and installing various update types from Windows Update. There is a service which runs for this component and it does the update scheduling
- 3- As per the policy received from Intune, which is now merged in the machine’s registry- the Orchestrator schedules the scan, verifies admin policies for download, starts the download. There are 4 components in the Operating System take over the proceedings from here, i.e. Update Agent, Windows Update Arbiter, Windows Update client and Orchestrator.
Update Agent, which is a component of the OS(a DLL) is downloaded when an update is applicable. It generates a list of payloads that are to be downloaded by the machine.
Windows Update Arbiter works as a deployment manager that calls different installers. The arbiter evaluates the manifest and tells the Windows Update client to download files.
Windows Update client reaches out to the cloud service and downloads files in a temporary folder.
Orchestrator starts the installation and restarts the machine(as per policy if applicable).
- 4- Once the update is done successfully at the device end, the Intune service is notified of the same.
More details on this section can be found in our official documentation https://learn.microsoft.com/en-us/windows/deployment/update/windows-update-overview
Troubleshooting- Quality Updates using logs and Registry
If we have encountered any issue while delivering Quality update via Intune, then we can use the below block diagram as a troubleshooting approach.
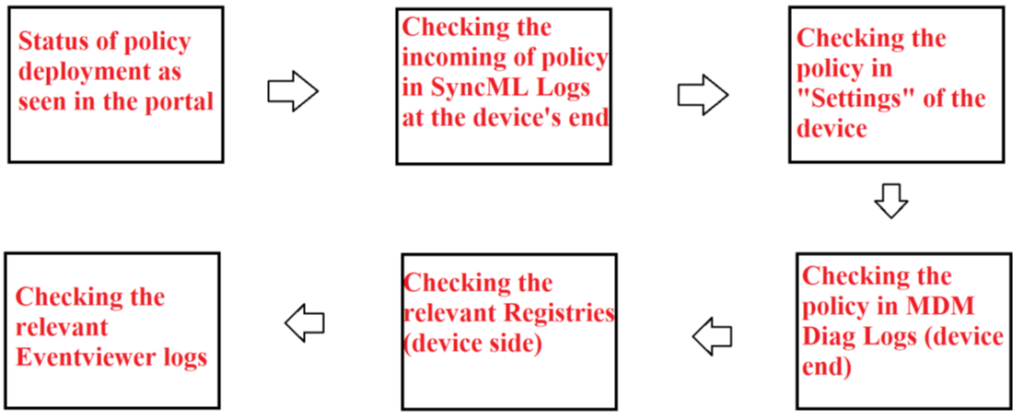
Now lets use the above block diagram as a reference and look at the troubleshooting approach.
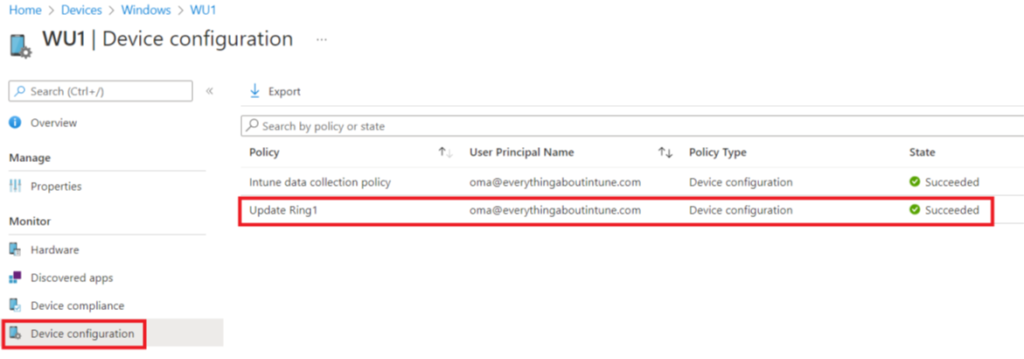
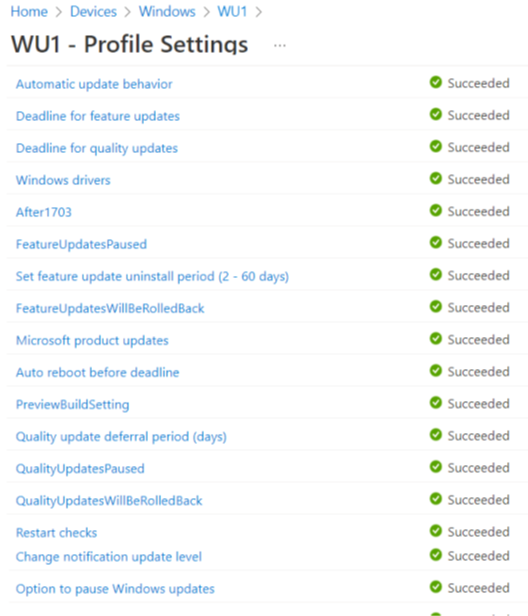
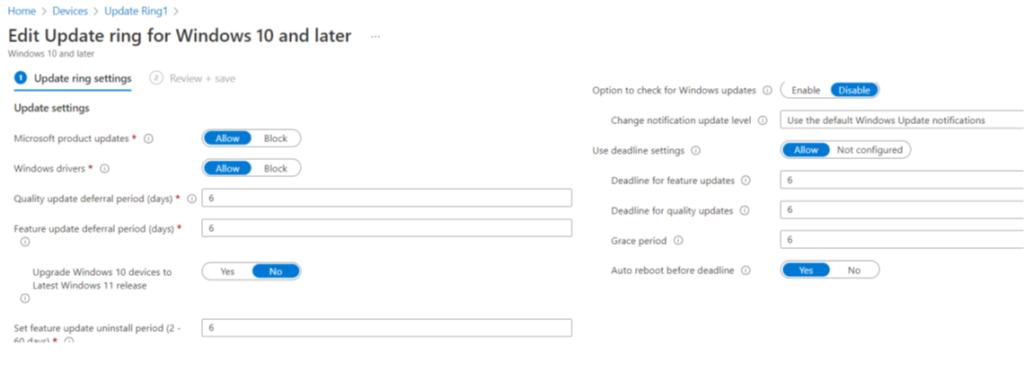
- The first step of troubleshooting is to verify the status of the policy delivery from the Intune console as shown below
- Now if we take a SyncML trace at the device end, we can see the policy getting delivered via Intune as shown below
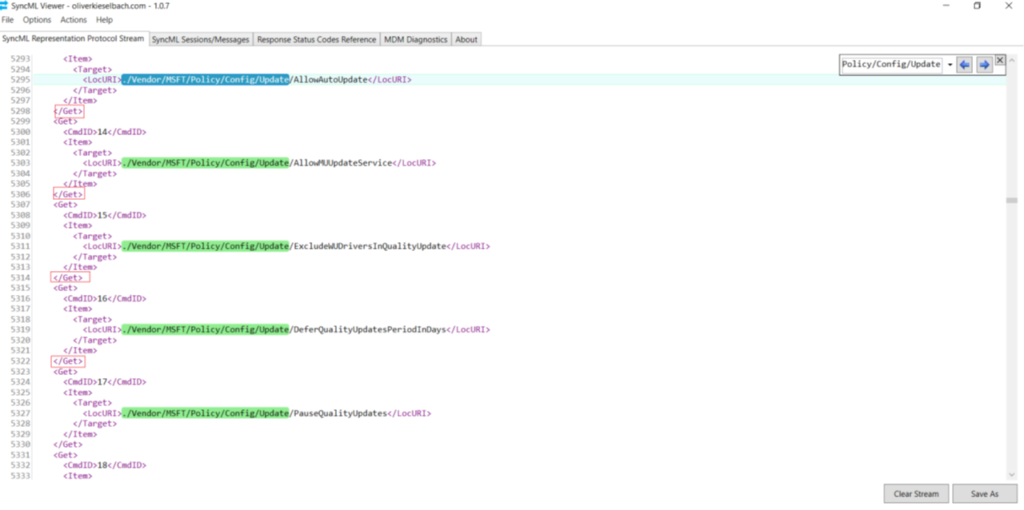
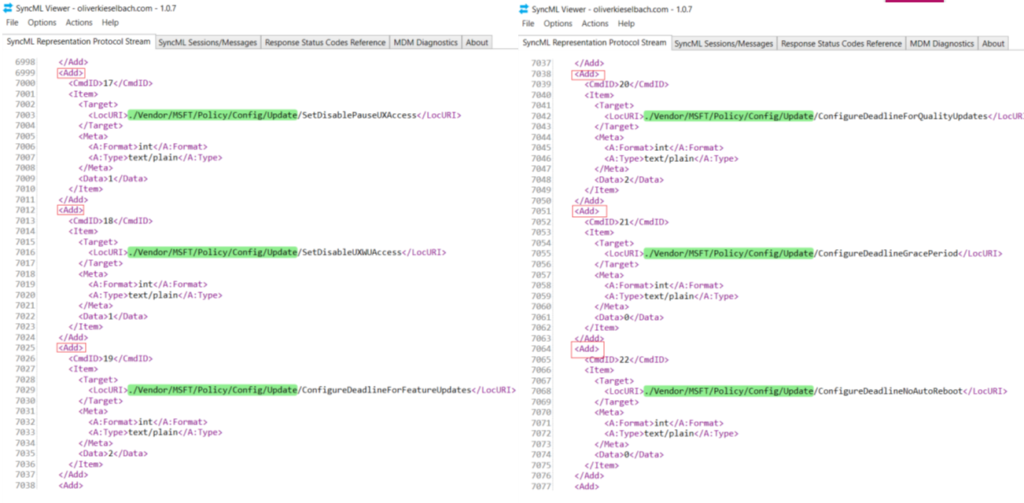
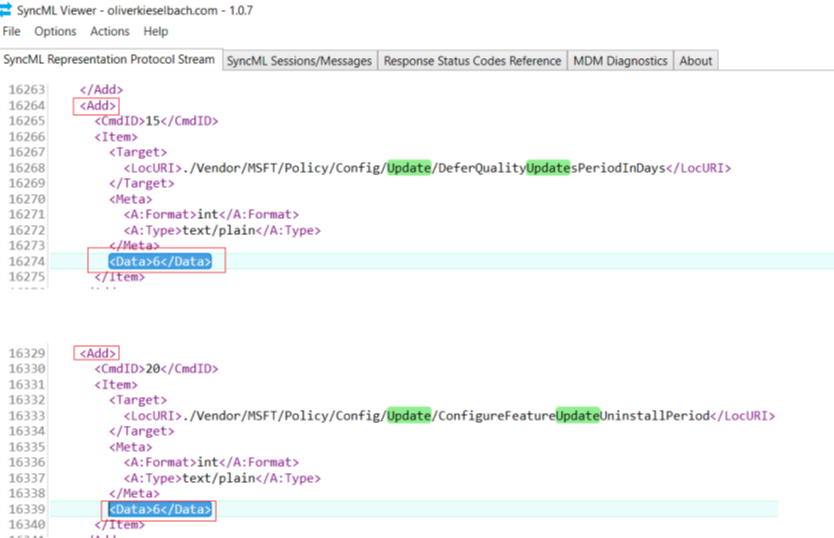
- We see that the settings in the policy correspond with the settings that is getting delivered to the device(in the SyncML trace)
- We will also be able to see ‘Updates’ as a managed workload in settings under the Device Management section.
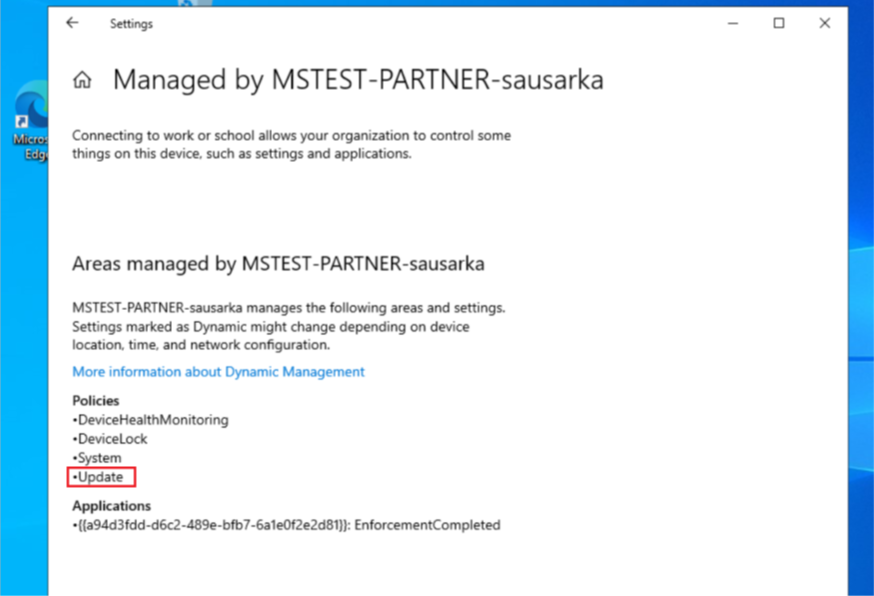
- As per the settings in the policy, we should see a message stating that the update settings in the device is being managed and the option to Pause an update should be blocked(if selected in the policy)
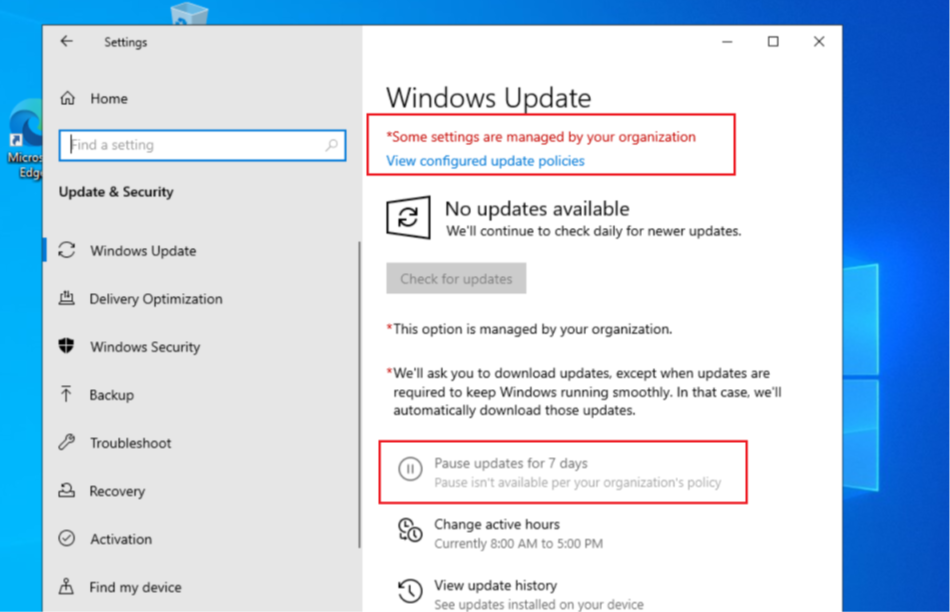
The UI also shows the specific settings related to Windows Update which are being managed by the MDM
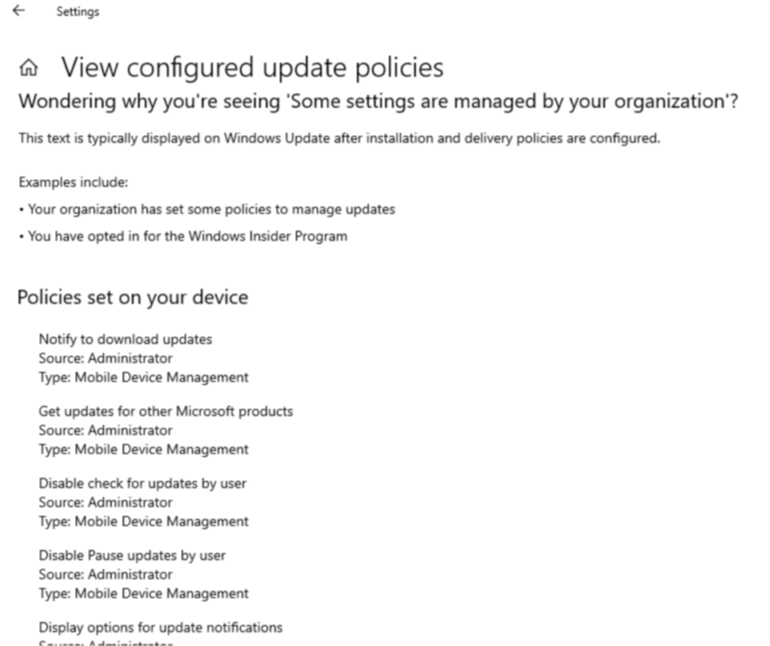
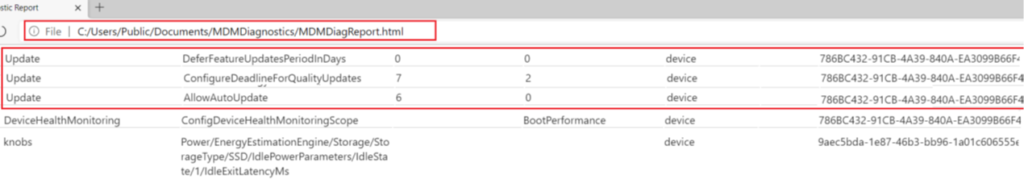
- We can also see the settings as per the policy in the MDM diag logs to confirm that the same has been delivered to the device successfully.
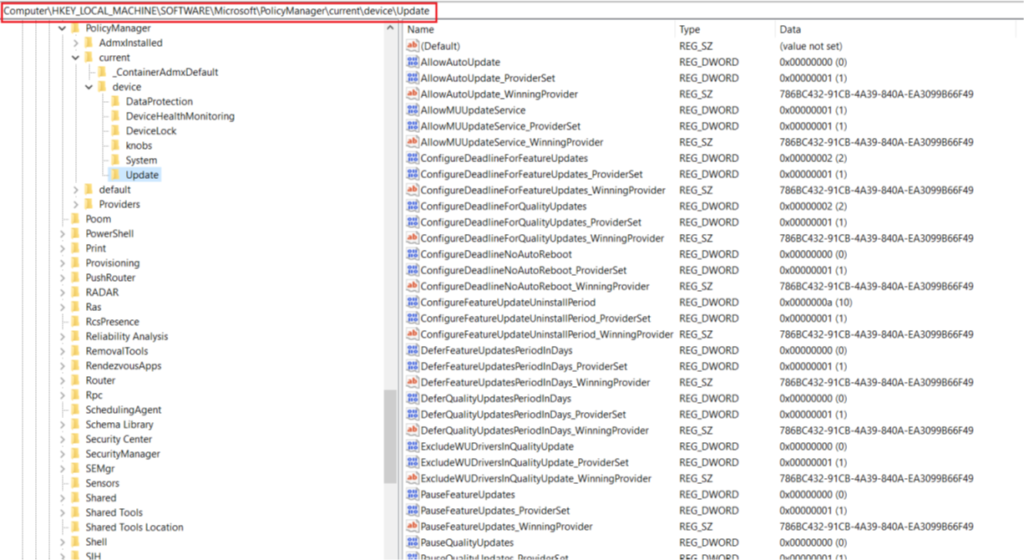
- Now the next place to check while troubleshooting is the registry. All the policies delivered from Intune reside in the ‘Policy Manager’ node, hence as shown below we are going to check the entries in the ‘update’ hive which should correspond with the settings in the policy
- Now the next part of troubleshooting is checking the eventviewer logs. All the policies deployed from Intune are going to be logged in which has been referenced below
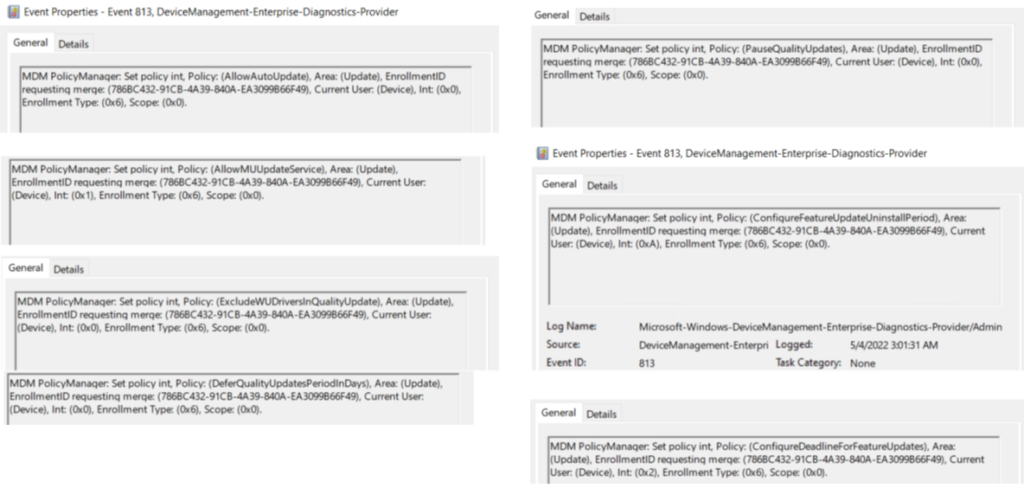
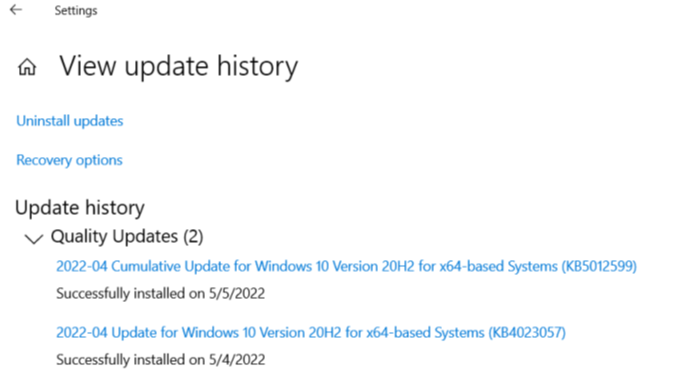
- If an update has been successfully installed in the device via Intune, it will show in the ‘Update History’ section of the UI
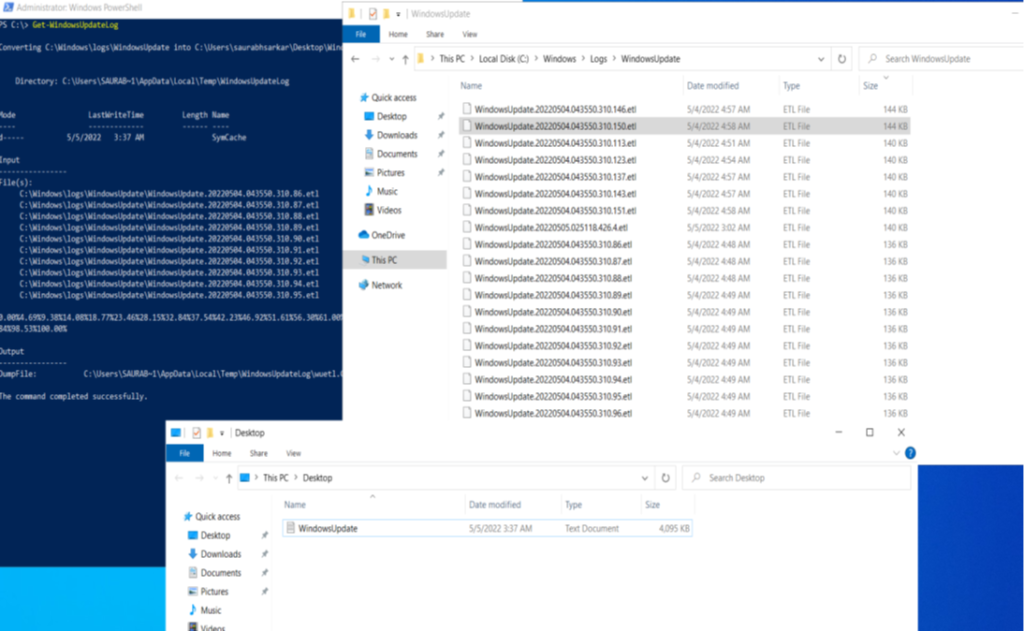
- The next place for logging is the Windows update logs present in C:\WINDOWS\Logs\WindowsUpdate which contains all the update logs in form of .etl
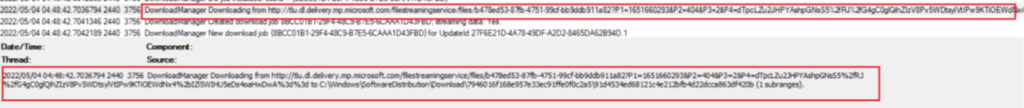
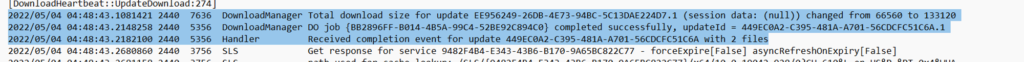
- As shown below, in the .etl file we can see the download request creation for the download of the update, update getting downloaded from Windows Update endpoint in the cloud, the total size of the file downloaded etc
Understanding Feature updates and managing them via Intune
Background of Feature Updates:
- On Windows, features updates are technically new versions of the OS, which are available twice a year. These updates typically include new features/visual improvements.
- Feature updates are bigger in size than quality updates. The download size can be close to 3GB, depending upon the OS version and hence they take longer to apply
- Intune supports setting a feature level to any version that remains in support at the time we create the policy and the device updates to the version of Windows specified in the policy.
- A device that already runs a later version of Windows remains at its current version. By freezing the version, the devices feature set remains stable during the duration of the policy.
- A device won’t install an update when it has a safeguard hold for that Windows version.
- While the feature version remains static, devices can continue to install quality and security updates that are available for their feature version.
The feature updates policy brings devices to a specified Windows version and freezes it. This means, even if the device might be eligible to update to the next OS version, the same will be blocked. So essentially with Feature updates policy we can select the Windows feature update version that you want devices to remain at, in our organization
Requirement:
Editions:
- Windows 10/11 Pro | Enterprise | Education
- Have Telemetry turned on, with a minimum setting of Required.
License:

Telemetry:
- One of the other requirement for Feature update to work is setting up of the Telemetry in the device. The telemetry in the device should be Turned ON and set to Required so that the device can send the relevant data to DSS. The telemetry can be turned ON by sending a Device Config policy from Intune or a CSP as documented below-
- https://learn.microsoft.com/en-us/mem/intune/protect/windows-10-feature-updates
- https://learn.microsoft.com/en-us/mem/intune/configuration/device-restrictions-windows-10#reporting-and-telemetry
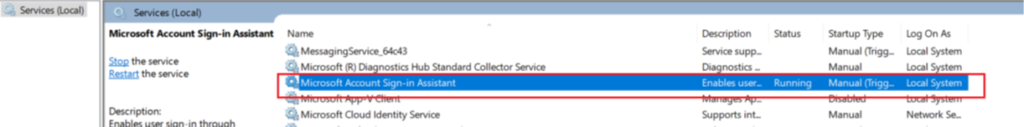
Microsoft Account Sign-In Assistant (wlidsvc):
- The Microsoft Account Sign-In Assistant (wlidsvc) must be able to run. By default, the service is set to Manual (Trigger Start), which allows it to run when needed.
Understanding the background flow behind delivery of Feature Update via Intune:
Now we are going to reference the below diagram to understand the flow behind working of a Feature Update policy via Intune.
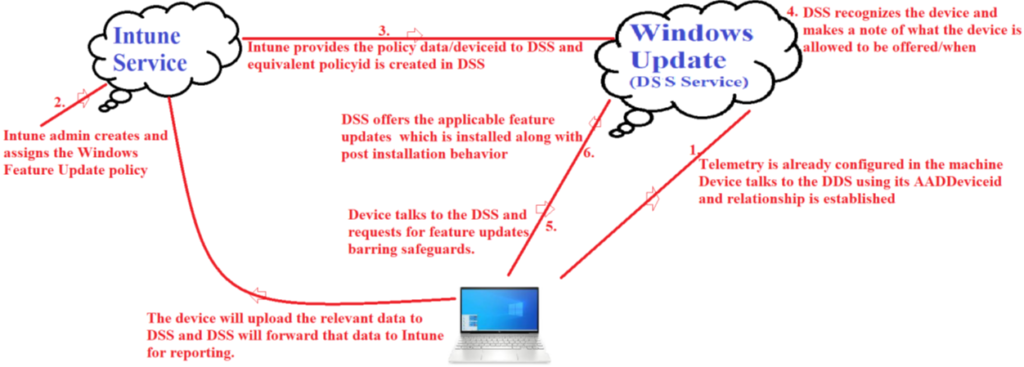
As we can see in the above diagram, the flow can be broken down into 7 steps as explained below-
- 1- DSS service(Deployment Scheduling Service) is a cloud service that runs in the backend. We must first configure the telemetry using CSPs or policies in the Windows devices. Device leverages its AAD deviceid and establishes a relationship with DSS so that it can send all its update related data to DSS.
- Once the client has been enabled to do that, device will start sending all its windows update related data to DSS.DSS and the Device become friends!
- 2- Now in the 2nd step the Intune admin creates a Feature Update policy at the Intune portal
- 3- Intune has the ability of talking to the DSS service. Intune gives the feature update policy(made by the Intune admin) with policyid to DSS
- Creating a Feature Update Policy in Intune creates an equivalent DSS Policy – for every Feature Update Policy ID, there should be a DSS Policy ID.
- Intune will take the policy data + device ID and hand it over to DSS. We can check and confirm that the AAD Device ID has been added to the DSS Policy assignment list, thus offering the update to the device
- The policy given by Intune service to DSS contains all the relevant information- like the feature to which the device should be blocked the update behavior etc
- 4- DSS recognizes the device as DSS and device are already friends from earlier!.
- 5- Now when the device talks to DSS, DSS can monitor and administer the update progress of the device as per the policy it has already received. The device requests for updates from the DSS service barring the safeguard holds
- 6- DSS will offer the applicable feature updates as per the policy body it had already received from Intune.
- 7- it will download/install the relevant feature update applicable from DSS along with post installation behavior which the device is to follow
- 8- The device will upload the relevant data to DSS. And DSS will forward that data to Intune for reporting. The major heavy lifting is done by DSS and not Intune
Important
Feature Updates(unlike the Update Ring policy,) does not deploy PolicyCSP towards the device.
We will not see anything in the Eventviewer/SyncML/MDM Diag logs at the device’s end.
We will not see registry keys in the ‘policy’ node being updated while using Feature Updates.
The communication happens between Intune and Windows Update Service
The Feature Update policy needs to be deployed to Device Groups (and not User Groups)
Troubleshooting- Feature Updates using logs and Registry
Now we are going to reference the below diagram while troubleshooting any Feature Update related issues via Intune
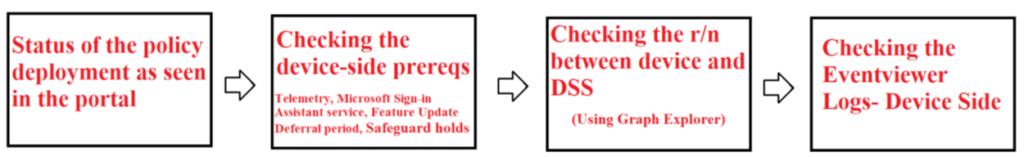
- The first step is to check the status of the policy for Telemetry as viewed in the Intune portal. This is a pre-requisite
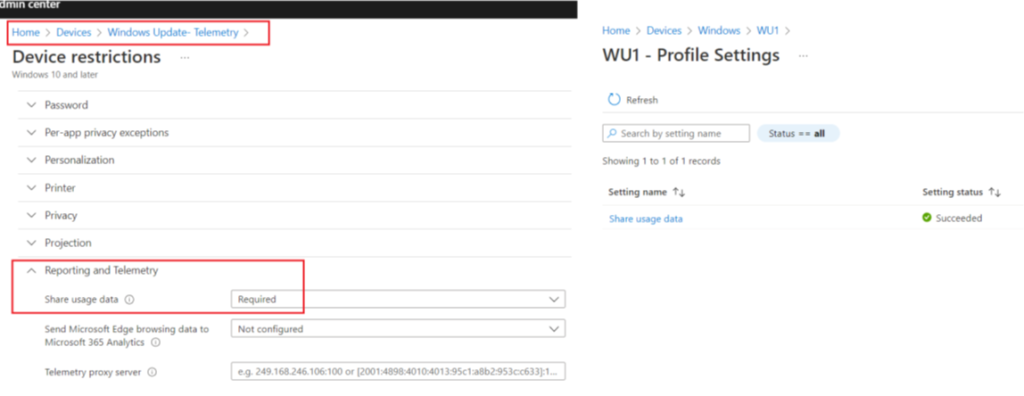
- If the above policy for turning on the Telemetry is delivered to the device, the below registry gets updated accordingly.
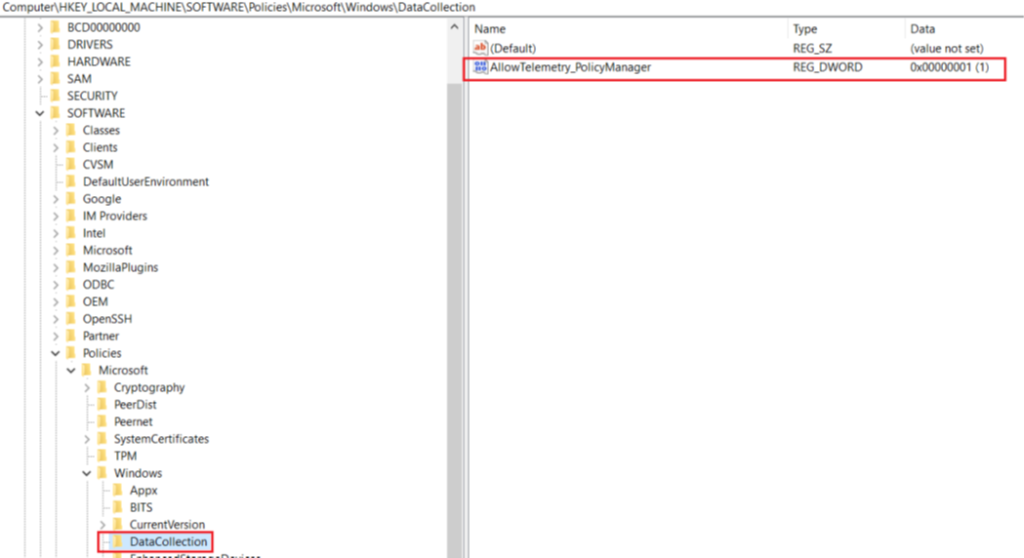
- The next step is to ensure that the Microsoft Account Sign-In Assistant service is running in the device.
- The deferral period in the Update ring policy should be set to 0 days. The same should reflect in the registry as shown below
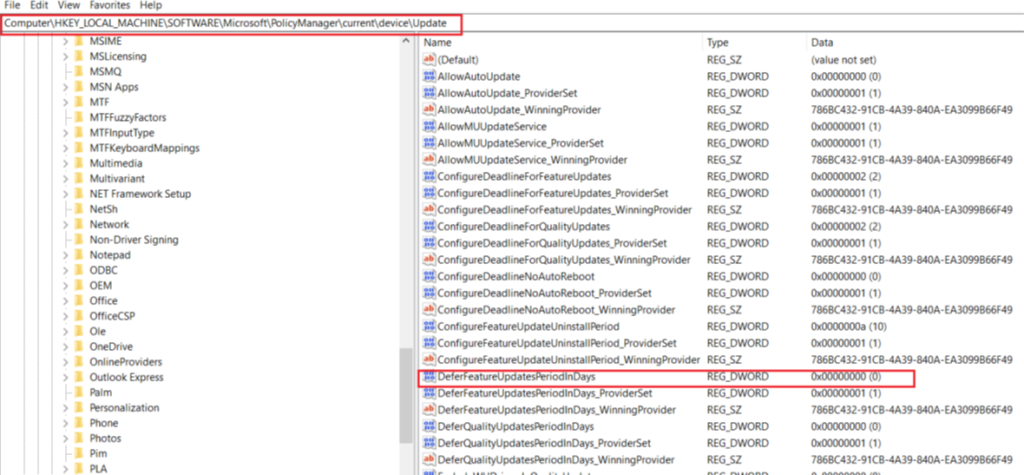
Note- The above value is set in the Windows Update ring policy
- We have to check and make sure that the value of ‘GStatus’ should be non-zero
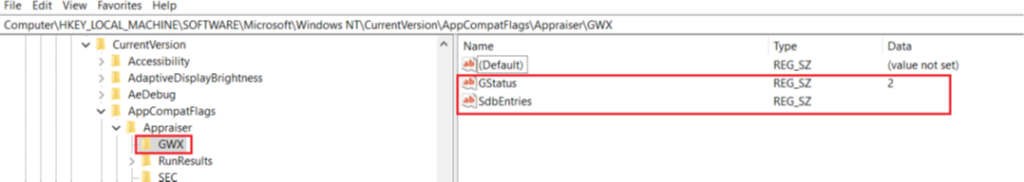
- The next step is to check for any safeguard hold in the operating system
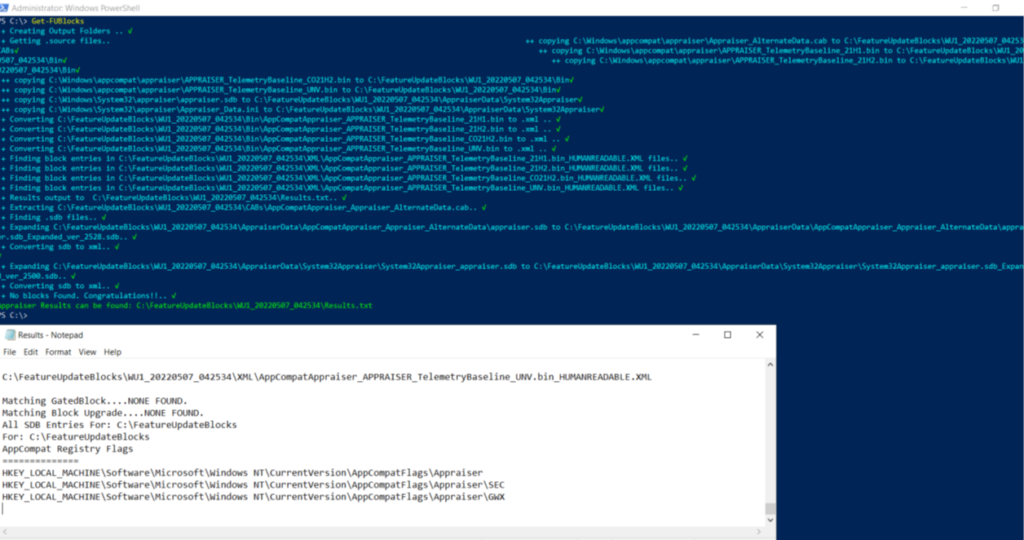
We can run the below Powershell commands while troubleshooting a client for Safeguard holds.
Install-Module –Name FU.WhyAmIBlocked
Import-Module FU.WhyAmIBlocked
Get-FUBlocks
https://www.asquaredozen.com/2020/07/26/demystifying-windows-10-feature-update-blocks/
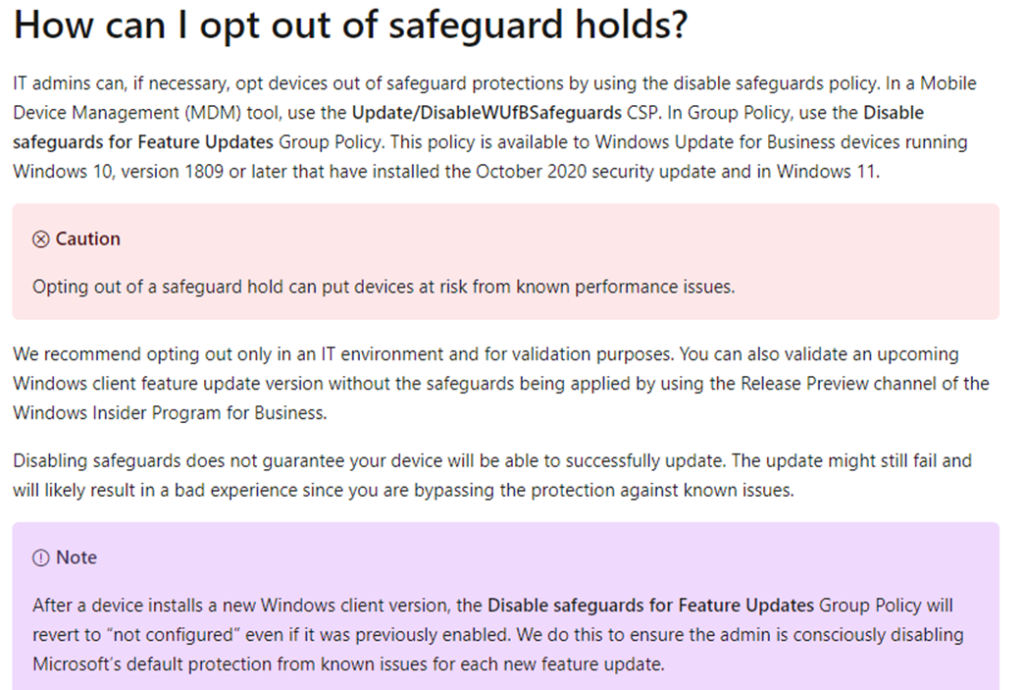
- Even though its not recommended, the below official doc shows how we can opt out of Safeguard Holds from a device.
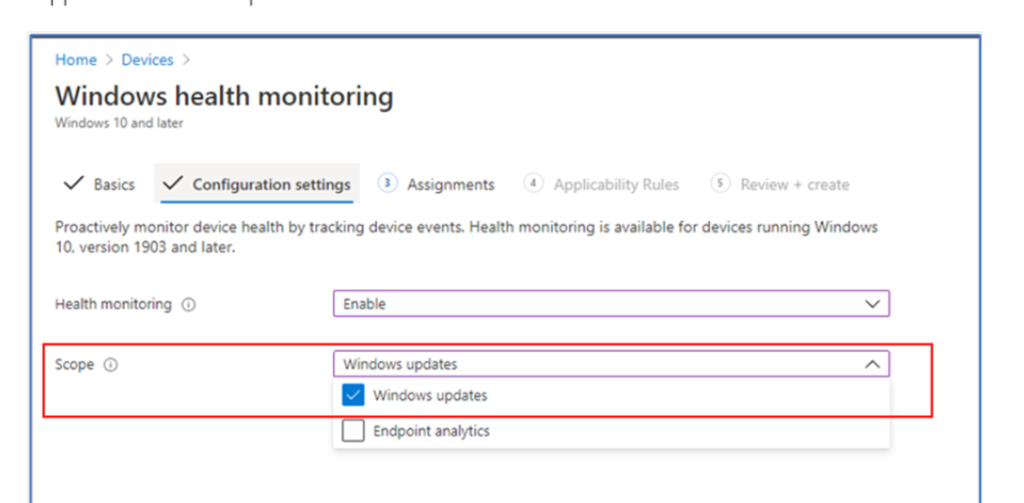
- Now need to enable Windows Health Monitoring and in its scope add Windows updates
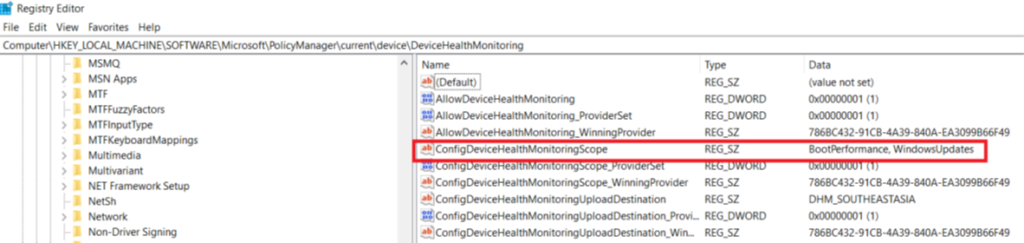
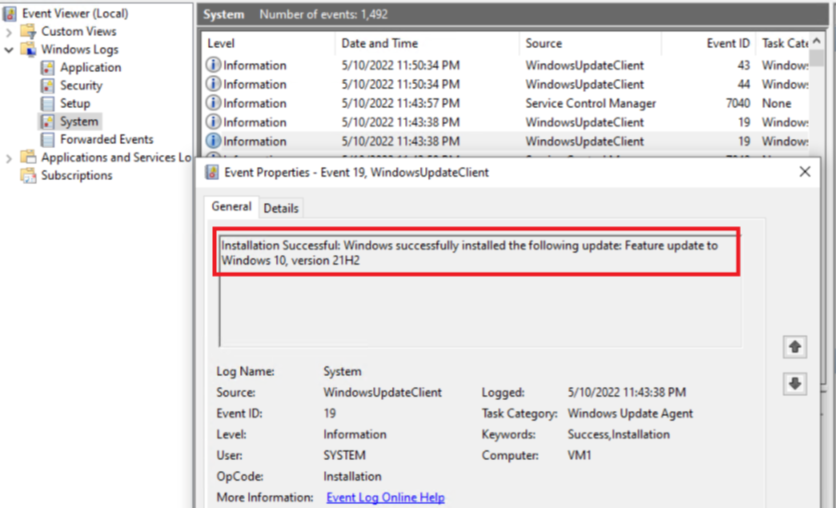
- The next place to check is the device side ‘System’ logs which is going to capture any events for Feature Update installation
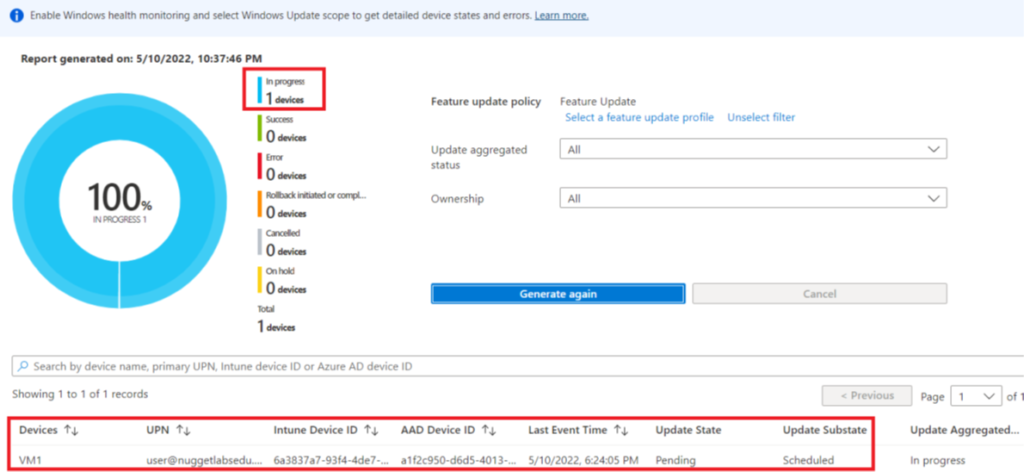
- The last place to check for, is the Windows Update report for the relevant Feature Update policy.
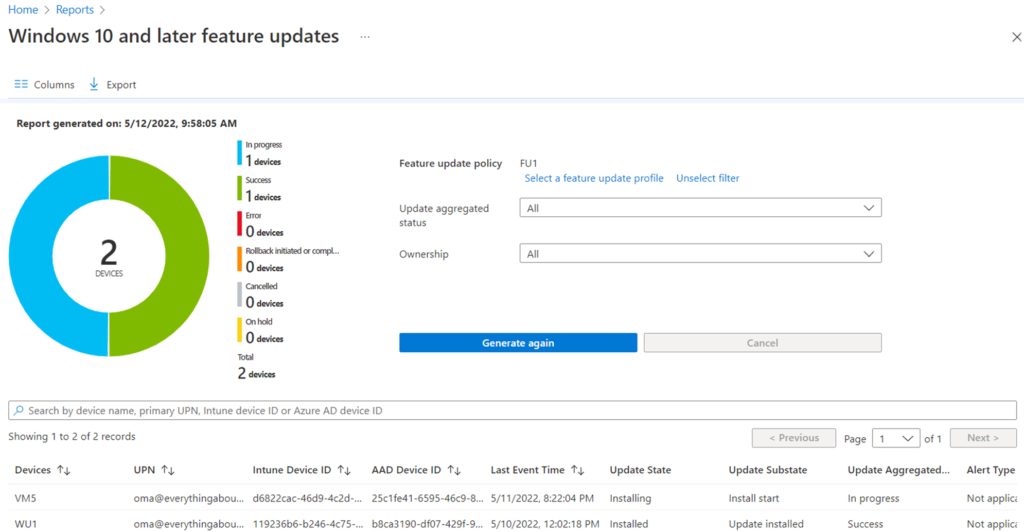
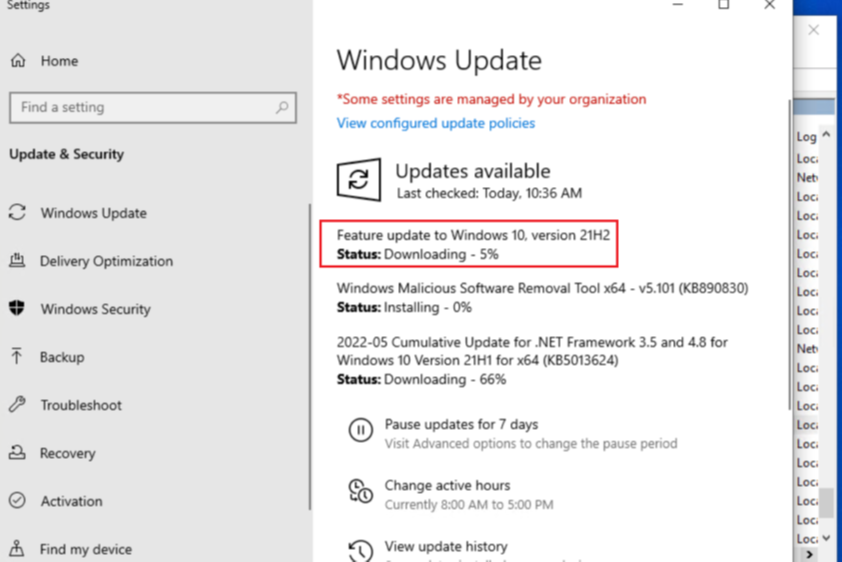
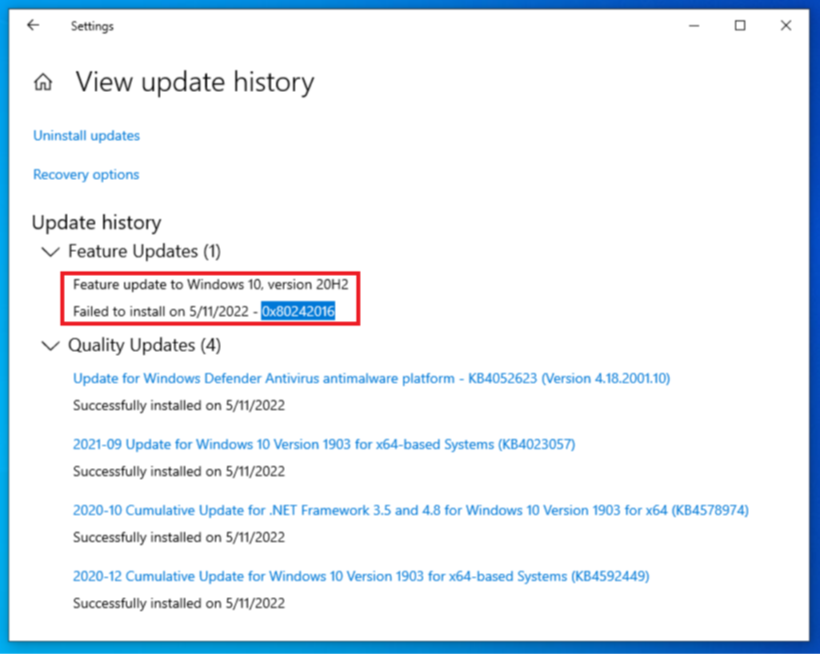
- If the device got the correct Feature Update delivered but the installation failed, along with the Windows update logs, we can also see the same in the below UI
Windows Update + Autopilot
- During an Autopilot deployment, only critical driver updates and Windows Zero Day updates get installed during OOBE. Feature updates cannot be applied during the Autopilot out of box experience (OOBE).
- The policies apply at the first Windows Update scan after a device has finished provisioning, which is typically a day.
The below documentation explains some more background on this topic.
Windows Update + Co-management
- In case of Co-managed scenarios, feature updates policies might not immediately take effect on devices when we newly configure the Windows Update policies workload to Intune. This delay is temporary but can initially result in devices updating to a later feature update version than is configured in the policy.
- Monitor the report for the policy. To do so, go to Reports > Windows Updates > Reports Tab > Feature Updates report. Select the policy you created and then generate the report.
- Devices that have a state of ‘OfferReady’ or later, are enrolled for feature updates and protected from updating to anything newer than the update we specified in the policy.
- With devices enrolled for updates and protected, we can safely change the Windows Update policies workload from Configuration Manager to Intune
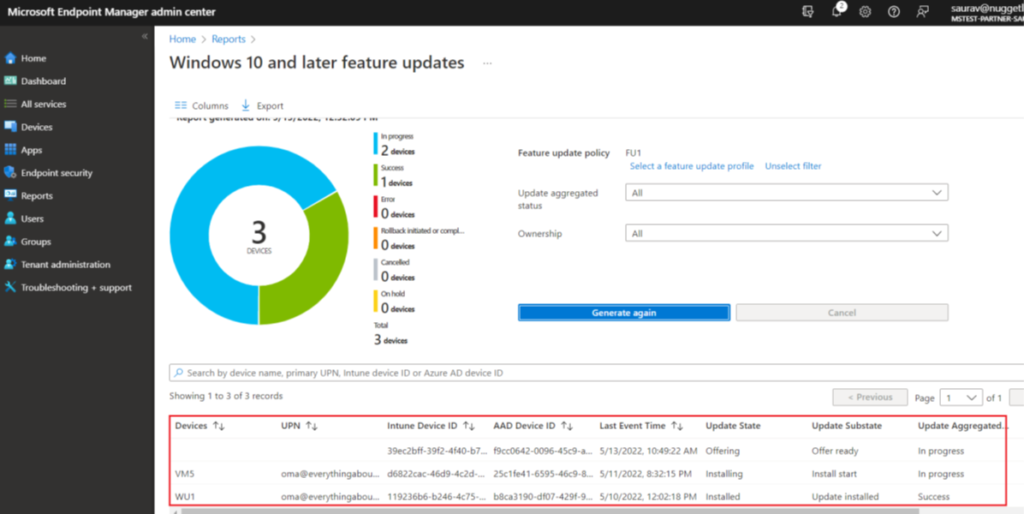
- The official document from Microsoft explains the above scenario in detail
- https://learn.microsoft.com/en-us/mem/intune/protect/windows-10-feature-updates#limitations-for-feature-updates-for-windows-10-and-later-policy
Removing a Feature Update
- When a device is no longer assigned to any feature update policies, Intune waits 90 days to unenroll that device from feature update management and to unenroll that device from the deployment service.
- This delay allows time to assign the device to a different policy and ensure that in the meantime the device doesn’t receive a feature update that wasn’t intended.
Understanding Expedited updates and managing them via Intune
- By using expedited updates, we can speed installation of quality updates(like an out-of-band security update for a zero-day flaw.) This is the ‘Fast Lane’ – extremely useful if you want to deploy a hotfix quickly. We might expedite a specific update to mitigate a security threat when your normal update process wouldn’t deploy the update for some time.
- Not all updates can be expedited. Only Windows 10/11 security updates that can be expedited are available to deploy with Quality updates policy.
- To speed installation, expedite updates uses available services, like WNS and push notification channels, to deliver the message to devices that there’s an expedited update to install.
- This process enables devices to start the download and install of an expedited update as soon as possible, without having to wait for the device to check in for updates.
- When a restart is required to complete installation of the update, the policy helps to manage the restart.
- In the policy, we can configure a period that users must restart a device before the policy forces an automatic restart.
Only devices that need the update, receive the expedited update. Windows Update evaluates the build and architecture of each device, and then delivers the version of the update that applies.
Expedite update policies ignore and override any quality update deferral periods for the update version we deploy
Understanding the background flow behind delivery of Expedited Update via Intune:
- We are going to reference the below flow diagram to understand the background behind working of an Expedited update.
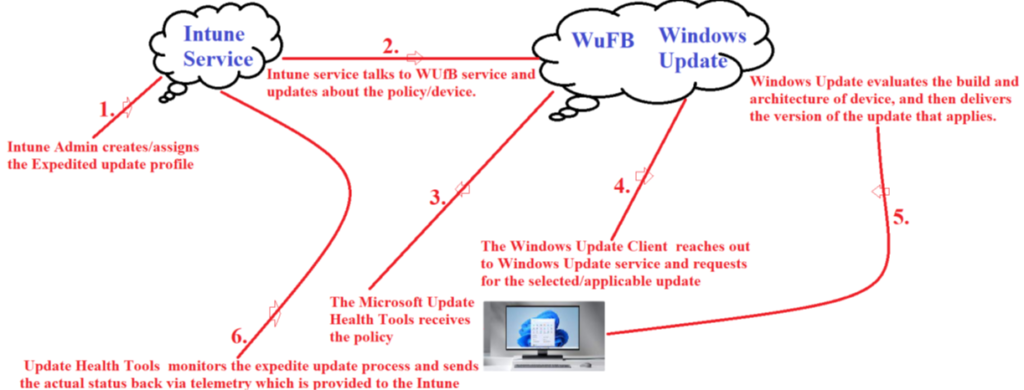
As we can see in the above diagram, the flow can be broken down into 6 steps as explained below-
- 1- Intune Admin creates/assigns the Expedited update profile
- 2- Intune service talks to WUfB service and updates about the policy/device. This communication can be tracked in the service side logs
- 3-WNS sends a Push Notification to deliver the message to devices that there’s an expedited update to install, instead of waiting for the regular Windows Update client sync. The Microsoft Update Health Tools receives the policy
- 4- The Windows Update Client service(running in the device) reaches out to Windows Update service in cloud and requests for the selected/applicable update
- 5-Windows Update evaluates the build and architecture of each device, and then delivers the version of the update that applies which is in accordance with the policy created by the admin. The update is downloaded and installed in the machine
- 6-Microsoft Update Health Tools sends the status back via telemetry which is provided to the Intune service for reporting
Troubleshooting- Expedited Updates using logs and Registry
- The first thing to check while troubleshooting is the Update Ring policy at the portal. The Notification Level should be set to default and it should NOT be Turned Off
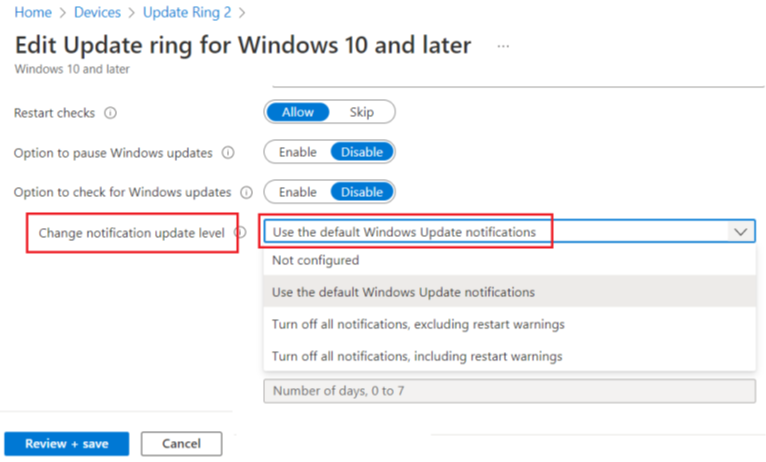
- The Windows update Health Tool should be installed in the machine
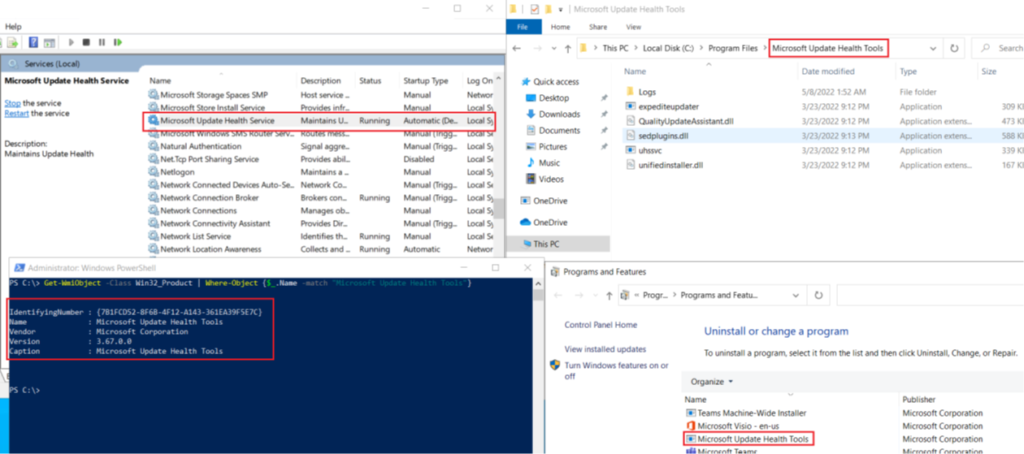
- We can view from it from the control panel and check its version from Powershell. We have to also ensure that its corresponding service should also be running in the device as shown below
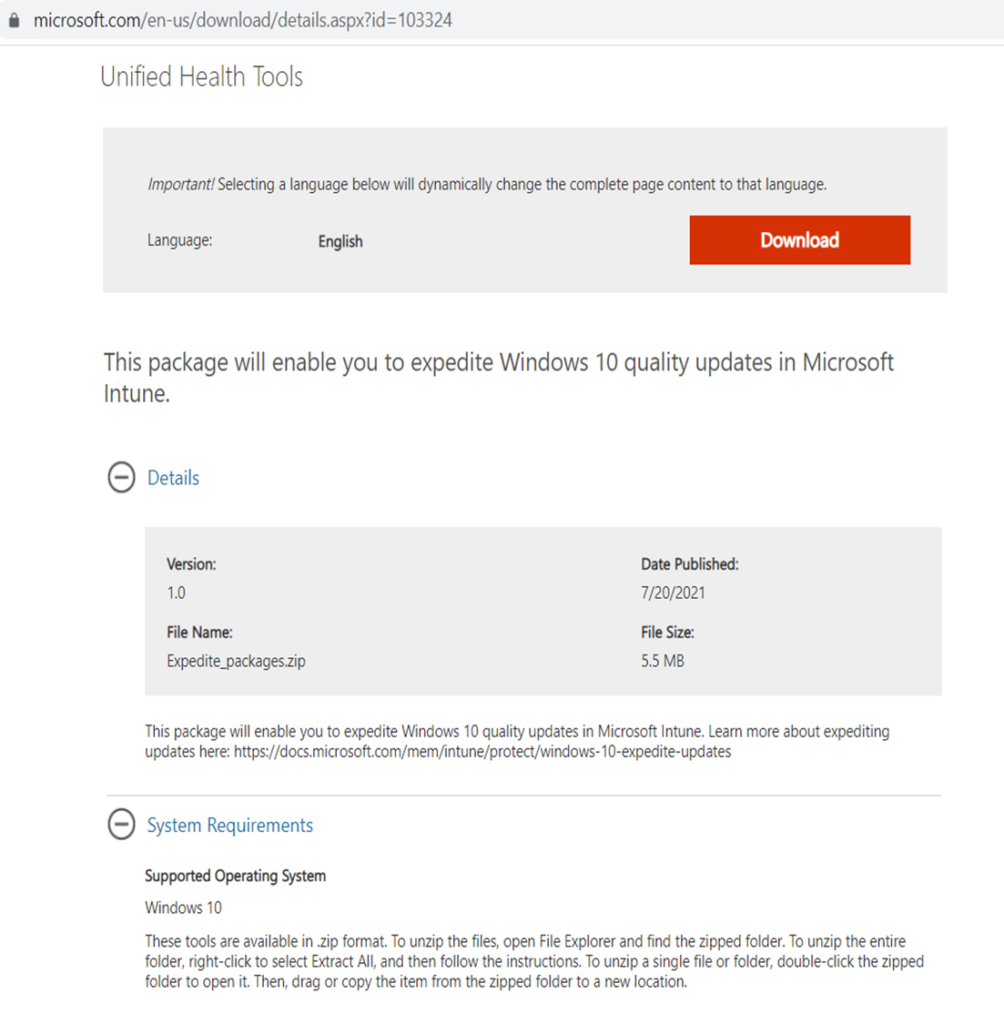
- If the Windows Update Health Tool is not present in the machine, we have an option of deploying the same from Intune. We can download it from our official website as shown below
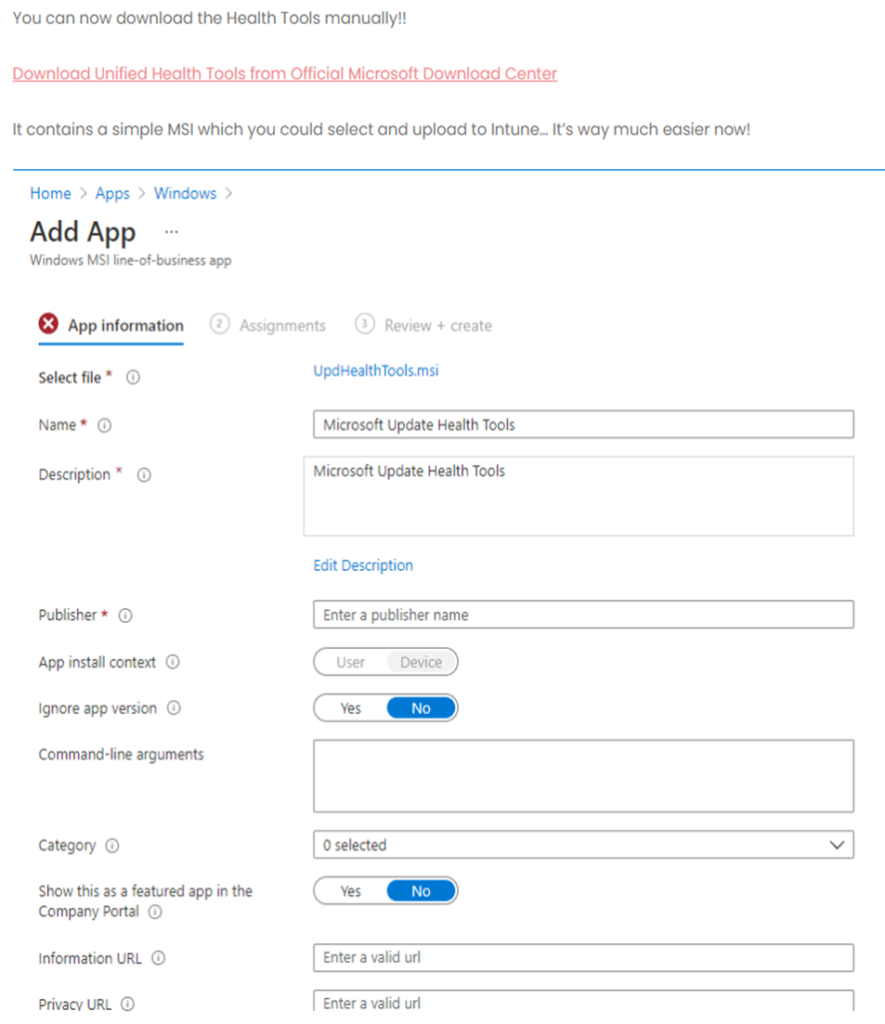
- The above downloaded tool is in the format of .msi, so it can be deployed from Intune as a LOB app.
- Alternatively, we can also deploy the below Powershell script which is going to install the relevant module and download the kb for Windows Update Health Tool
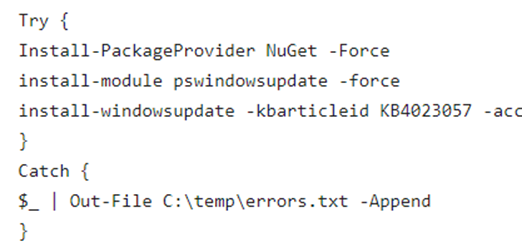
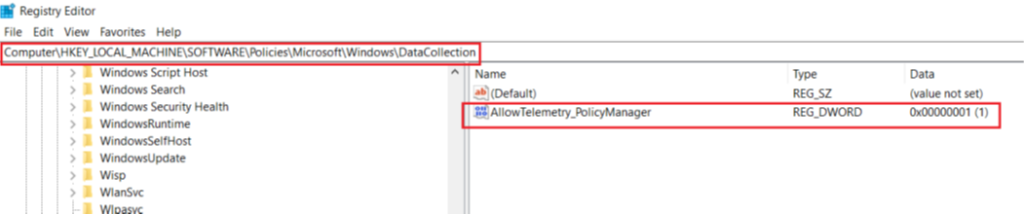
- We should also check and ensure that the registry which enables the device to send its Telemetry to Windows Service is also set correctly as shown below
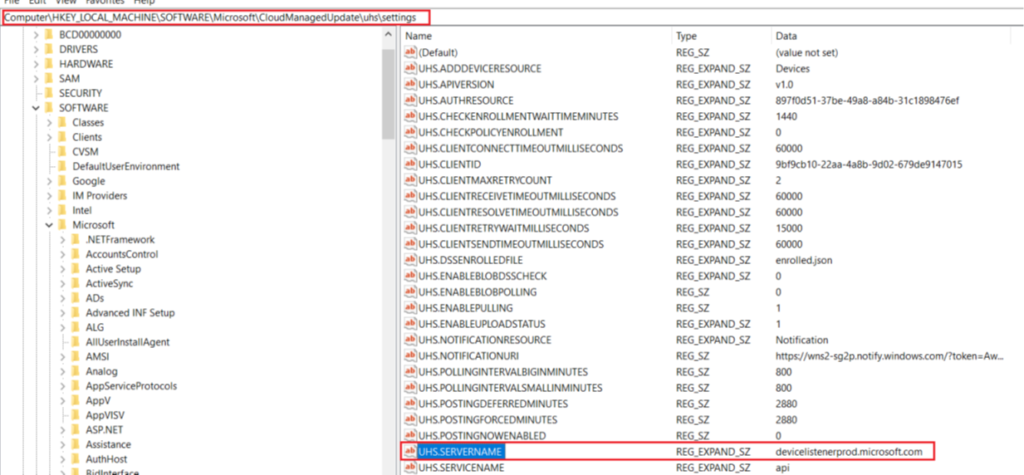
- The next thing to check is the ‘UHS.SERVERNAME’ key in the below registry key, which should point to the relevant Microsoft endpoint.
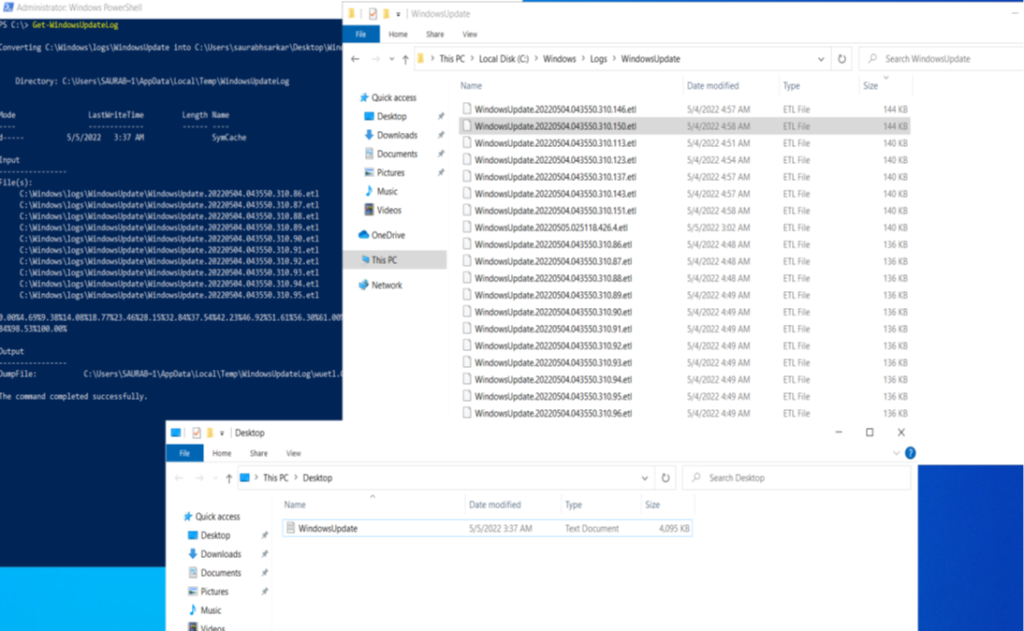
- The next location to check for is the Windows Update logs which is going to capture the download and installation of the Expedited Updates
- The last thing to check for, is the reporting for the policy that we have created in the portal.
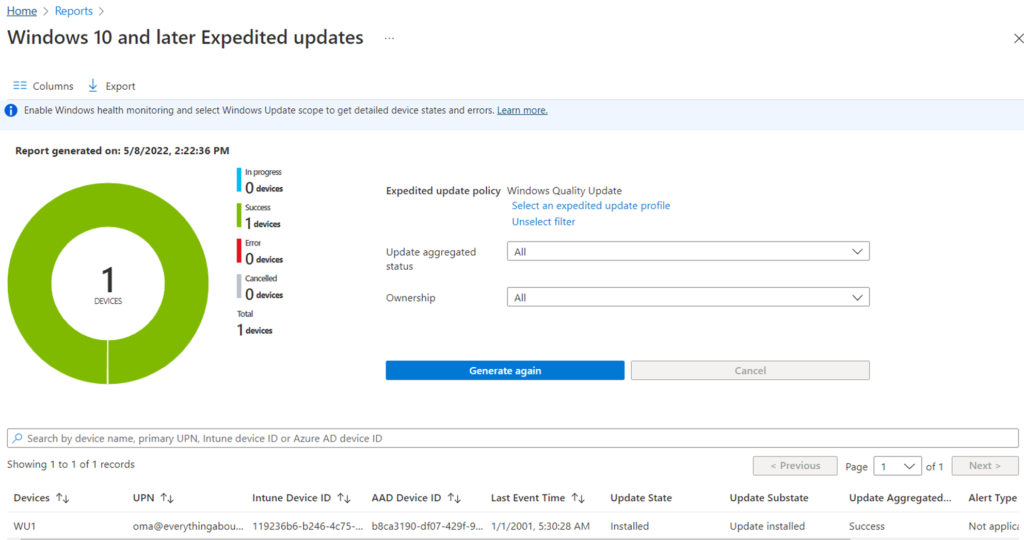
Key Pointers:
- Enabling and Configuring Health Monitoring/Telemetry and making sure the Update Health Tools are installed.
- Making sure that the Update notification settings are Not disabled
- Making sure that the user has all the needed License in place (Intune and Windows)
- We should ensure that there are no legacy old gpo’s interfering and the device is not pointing to WSUS like an example
Deploying an Update (specific patch/kb) as Win32app
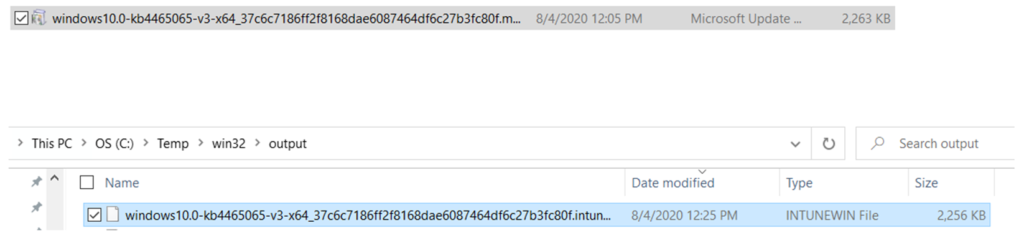
- If we wish to deploy a specific kb to a device via Intune, we have the option of deploying it as a Win 32 app.
- We would have to Download the kb(in .msi/.msu format)>Convert it into .intunewin format>Deploy the same from the portal
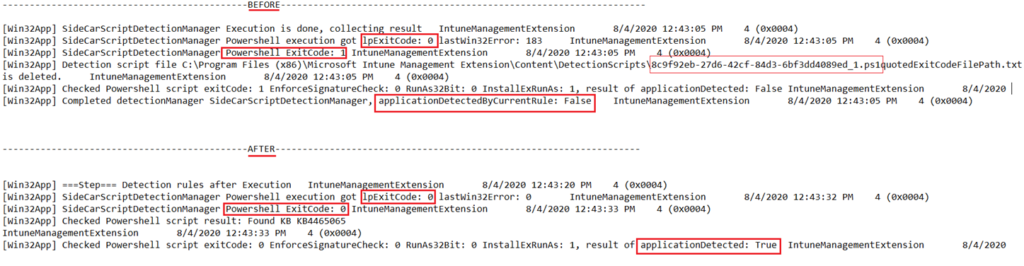
- Once the same is deployed, we can check the IME logs and track its flow of installation, as shown below
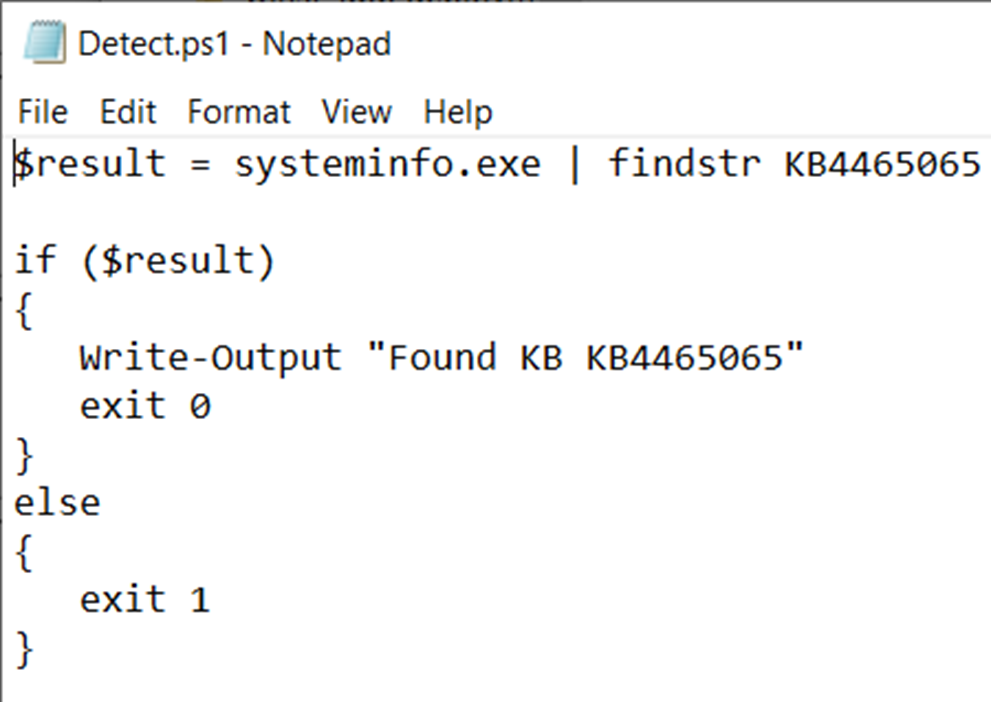
- We can use the below PowerShell script for reference, (in the Detection logic) while deploying the kb in form of win32 app
Managing Windows Updates using CSPs:
- If there is any setting that is not present in the Intune UI, we always have the option of directly targeting the setting which is exposed in form of CSP by the operating system via OMA-URIs
- The below list shows the CSPs related to Windows Update which can be targeted.
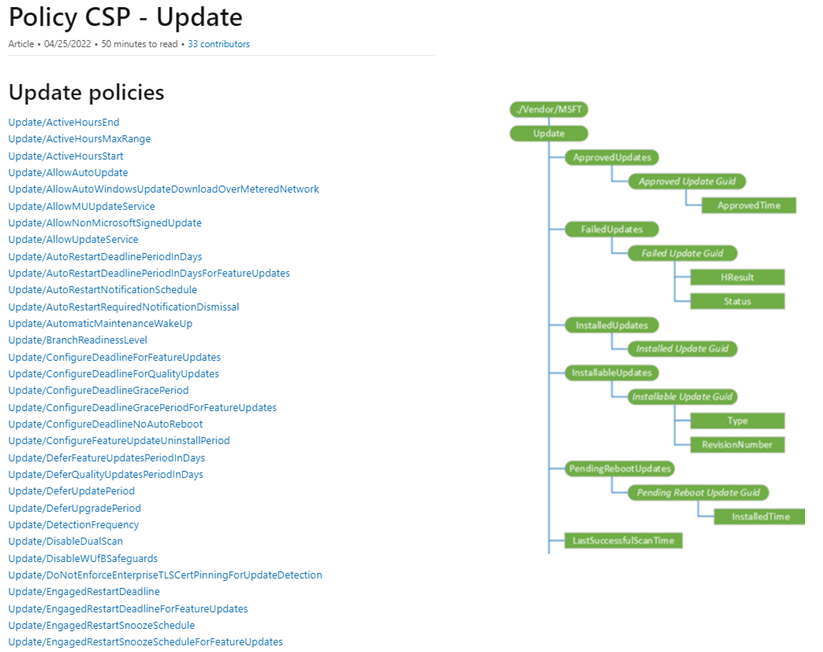
Official documentation for the same can be found below-
https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update
More information on this topic can be found https://www.petervanderwoude.nl/post/managing-windows-update-for-business-on-windows-10-via-oma-dm/
Deploying an Update using Powershell Modules:
- The below official document from Microsoft explains how we can use the PowerShell modules for managing Windows Update
https://techcommunity.microsoft.com/t5/windows-it-pro-blog/powershell-for-the-windows-update-for-business-deployment/ba-p/2437208
Deploying an Update using Graph APIs:
- The below official document from Microsoft explains how we can use the Graph APIs for managing Windows Update
https://techcommunity.microsoft.com/t5/windows-it-pro-blog/public-preview-of-microsoft-graph-apis-to-manage-windows-updates/ba-p/2302751
Deploying Driver and Firmware updates:
Background:
- Microsoft has released a new deployment service for driver and firmware updates, which gives us visibility into the drivers hosted in Windows Update that are a match for your enterprise devices and offering you control over both the selection of individual updates and the scheduling of update deployments to devices from Windows Update.
- IT admins can access the deployment service in Intune by creating Driver Update Policies and assigning devices to them. Once a device is under the purview of such a policy, the deployment service allows Windows Update to make its selection decisions, but the results are sent to the admin for review and action instead of simply offering the drivers to the device..
Using this policy, the admins can review available content and then make approval decisions on a per driver basis.
The Drivers are not offered by default – Only after a driver is approved by the admin, it is deployed to the device.
Understanding the background flow behind delivery of Drivers and Firmware via Intune:
- We are going to reference the below diagram to understand the delivery of firmware/drivers via Intune
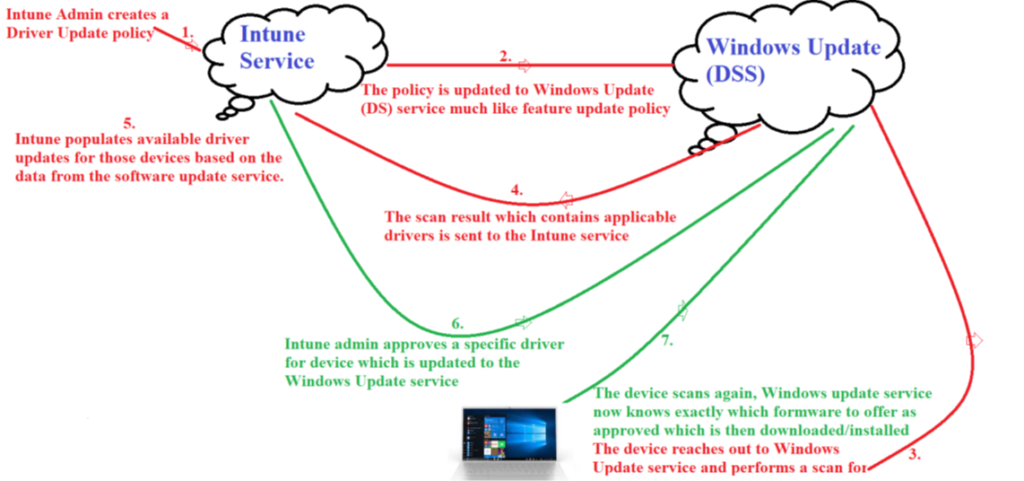
As we can see in the above diagram, the flow can be broken down into 7 steps as explained below-
- 1- Intune Admin creates a Driver Update policy in the Intune portal. The same needs to be targeted to a device group
- 2- The policy is updated in Windows Update (DSS) service much like feature update policy. The policy body and deviceid is provided to DSS by Intune
- 3-The device reaches out to Windows Update service and performs a scan for Firmwares and Drivers. This is a normal scan performed by the Windows Update client in the device wherein the device is discovering the applicable firmware updates.
- 4-The scan result which contains the applicable drivers is sent to the Intune service
- 5-Intune populates available driver updates for those devices based on the data from the software update service.We can see all the drivers and firmwares that are applicable for the devices
- 6-Intune Admin approves the selected driver updates The admin can approve and schedule the deployment on pre-driver basis. The admin has the ability of select a particular driver amongst the list of applicable drivers for the machines. Intune admin approves a specific driver for device which is updated to the Windows Update service
- 7-Now when the device scans again, Windows update service knows exactly which firmwares to offer as approved already by the admin
- Other applicable drivers are not offered to the device(even though they are applicable). The device only gets the firmwares/drivers which are trusted and approved the admin
- The device installs the firmwares/drivers offered to it and the inventory is updated
Using Win32 app deployment approach for Driver updates:
- If we wish to deploy a specific driver, we can use the Win32 app approach to do the same. We would have to package the driver to .intunewin file and then we can deploy the same. The below blog sheds some light onto the process.
https://thinkdeploy.blogspot.com/2019/03/deploying-thinkpad-bios-updates-with.html
Endpoint Manager simplifies upgrades to Windows 11:
Via Intune, now the process of upgrading a device to Windows 11 is simplified. As shown in the screenshot below, the same can be selected in the Intune policy itself.
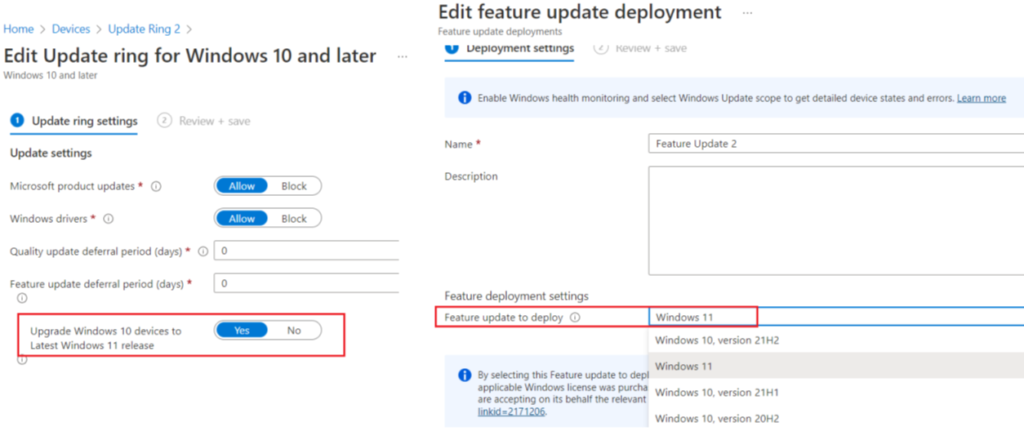
The below official document from Microsoft sheds more light into the process.
https://techcommunity.microsoft.com/t5/microsoft-endpoint-manager-blog/endpoint-manager-simplifies-upgrades-to-windows-11/ba-p/2771886?fbclid=IwAR07_y3TGo3KUD84Ybk2QvRxNBLiwtjjaS3DY6ast-5cC082CRxh9xwbv3E
Reminder:
Intune delivers policies, not the updates.
Windows Update for Business is a separate component from Intune. Intune defines an Update schedule for Windows UpdatesWe dont have an option of selectively deploying patches(by creating baselines) from Intune (like we do with SCCM)
Best Practices:
- Using rings incrementally. so that if anything goes wrong with Ring1, we have the ability to pause the subsequent prod rings
- Efficient use of Deferral, Deadline and Grace period
- Using Expedite Updates when updates are to be deployed faster than normal schedule.

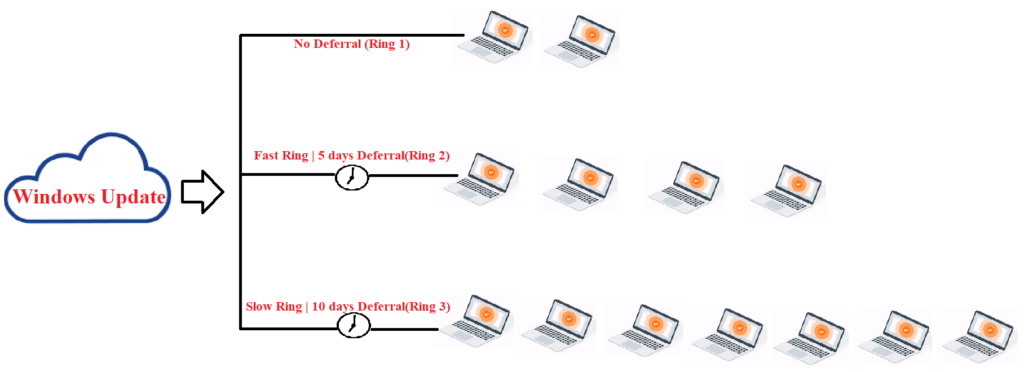
- Ring 1 which has zero deferral can be used for testing. This can be targeted to a small set of test devices to see the behavior of the devices post patching.
- Ring 2 with a 5 day deferral can be used for patching the local IT. This would be our pilot set of devices.
- Ring 3 with 10 days deferral can be used for patching the rest of the devices in our organization.
- Using an incremental approach of Rings like above provides us a very good control. If there is a patch released by Microsoft which causes any anomaly, we can identify the same in Ring1/Ring2 itself and pause the Ring 3 until that is remediated (internally or by Microsoft in form of a fix), hence our prod devices remain unaffected
I hope this blog was helpful in understanding the basics and background of Windows update management via Intune
