If you think that Kali Linux is the only OS (operating system) for hacking then you might be thinking wrong.
Why you might ask, it is because due to the overexposure to hacking in the past few years, many tools have landed in the market for Windows.
Also read- Start Learning Hacking With Kali Linux
So if you are interested in hacking but don’t want to install Linux for that, then you are at the right place because here, In this article, we have shortlisted some of the best hacking tools for Windows 10 and 11, which might help you to get started with your ethical hacking career.
These hacking tools include some of the best free hacking tools and the paid ones for hacking Wi-Fi, password cracking, Pentesting, and software related to networking with download links.
Disclaimer: All content in this article are intended for security research purpose only. Techworm does not support the use of any tool to indulge in unethical practices.
Table Of Contents
- 10 Best Hacking Tools For Windows 10, 11
- 1. Wireshark
- 2. Social-Engineer Toolkit
- 3. Aircrack ng
- 4. Metasploit
- 5. OclHashcat
- 6. Nmap
- 7. Nessus
- 8. Acunetix WVS
- 9. Maltego
- 10. John The Ripper
10 Best Hacking Tools For Windows 10, 11
1. Wireshark
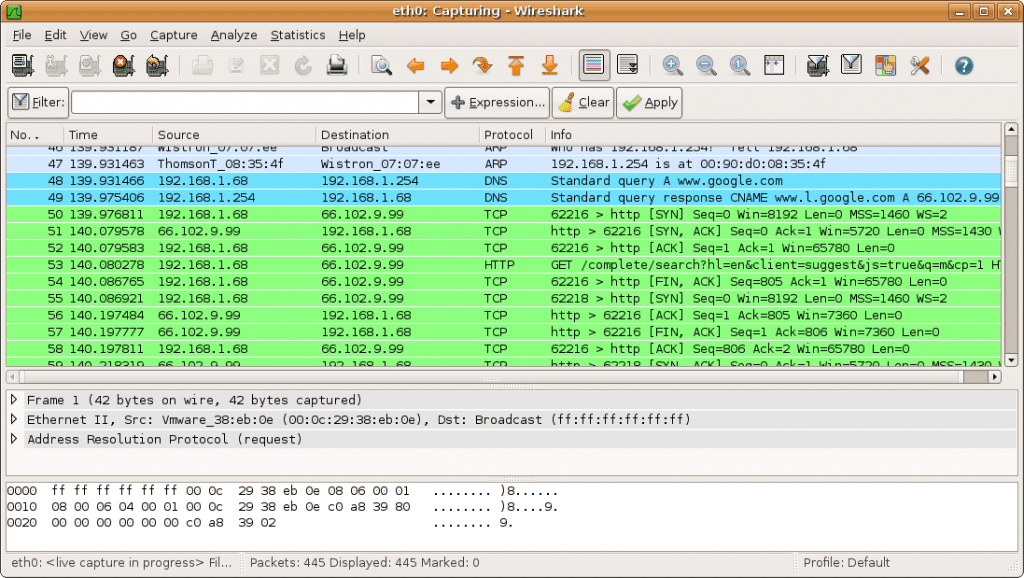
Wireshark is the networking mapping application that provides you with all the information related to what is mapping on your network and how’s that mapping.
It also provides information related to cookies, such as how many cookies are getting installed and where packets are flowing, and much more. Not only that, but You can also perform phishing, keylogging, and men-in-the-middle attacks from this tool.
It was initially named Ethereal. The hacking tool is a free and open-source tool that comes in a command-line version called TShark.
Wireshark is a GTK+-based Wireshark network protocol analyzer or sniffer, that lets you capture and interactively browse the contents of network frames. In conclusion, it works best on both Linux and Windows.
This hacking software is very famous among hackers. It offers many services, such as Spear Phishing Attack Vector, which lets you hack any social networking account on Facebook, Twitter, Gmail, etc.
It is basically used to send a fake login page to the victim so that they can enter their id and password on that page and thus get their password hacked.
The chances are high as it looks exactly like the original login page of that particular social networking site.
When a victim enters the info, that info is automatically transferred to the hacker.
It also has many other tools to study thoroughly on the internet.
Apart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows.
3. Aircrack ng
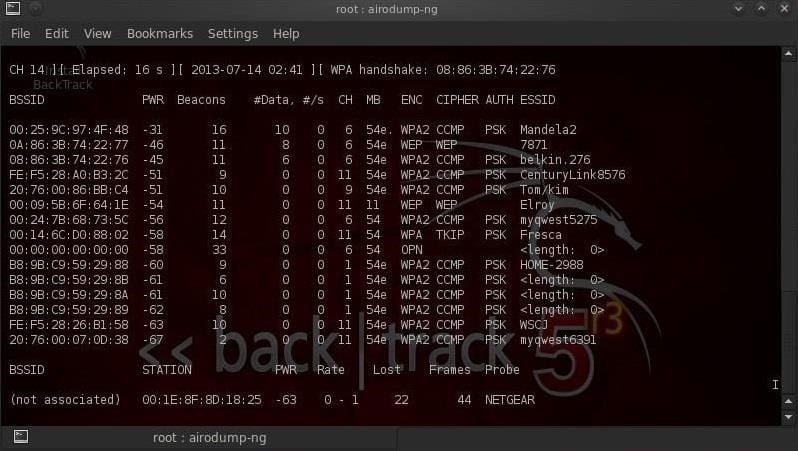
This Windows 11 wifi hacking tool is widely used for network monitoring. It is purely based on the command-line interface.
In AirCrack, you will find lots of tools that can be used for tasks like monitoring, attacking, pen testing, and cracking.
Without any doubt, this is one of the best network tools you can use to hack WIFI. This tool also supports all the WIFI versions, such as WPA/WPA2-PSK, etc. In short, this tool captures all the packets present in the network connection and converts them into the text from which we can see the passwords.
Learn How To Hack WiFi Password
4. Metasploit
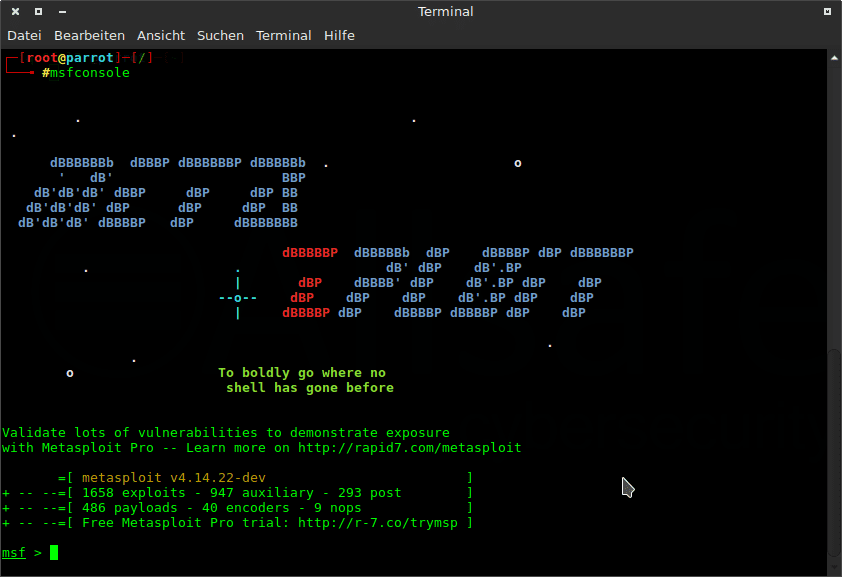
It’s a forensic tester that is used by governments as well. Metasploit allows you to remotely control any computer from anywhere and anytime in the world.
This hacking tool for windows 11 works on the principles of trojan.
Now, what is a trojan? It is software that allows remote access to any device in the world. For instance, if a trojan is installed on a particular computer, a hacker can access and control that computer from any part of the world.
This software is also used to make trojan for Android devices, which you can hack any android device using Metasploit.
5. OclHashcat
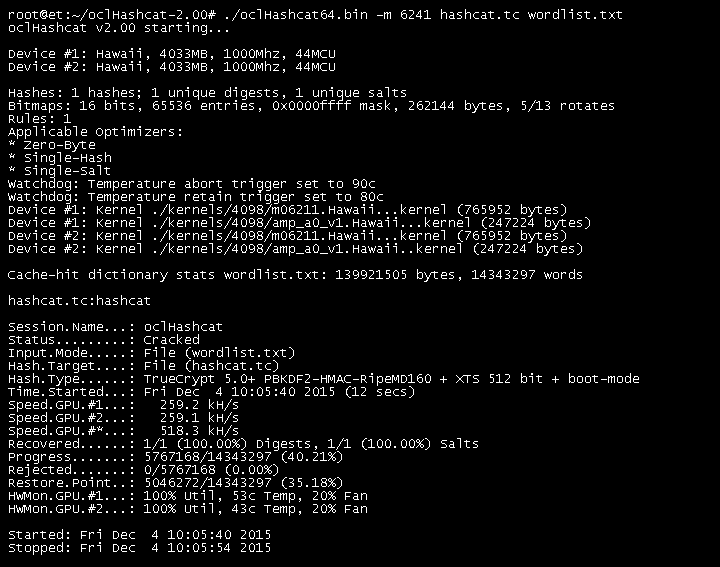
If you love password cracking, then this tool is best for you.
While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of your GPU.
It is the world’s fastest password hacking tool for windows 11 with the world’s first and only GPU-based engine.
It offers many features such as Straight, Combination, Brute-force, Hybrid Dictionary + mask, and Hybrid mask + dictionary.
6. Nmap
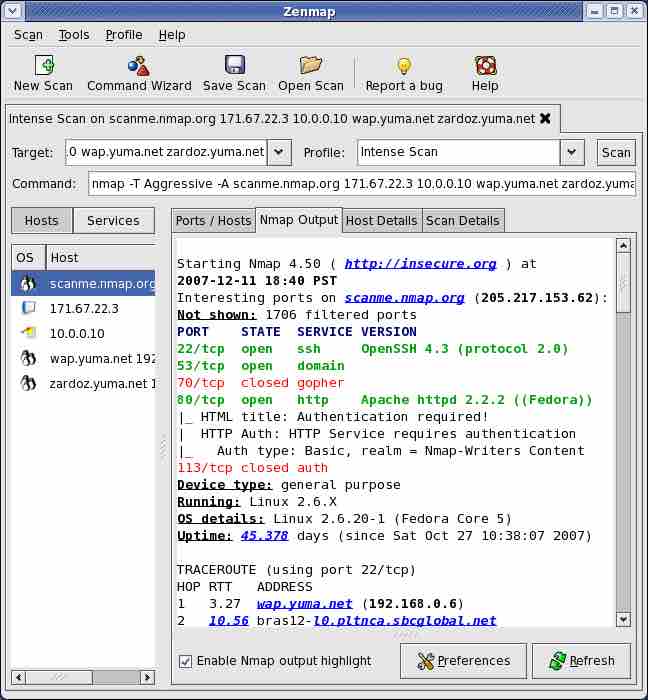
Also known as the “network mapper,” this tool successfully falls in the category of a port scanning tool.
It’s an entirely free and open-source hacking tool mainly used as a port scanner.
Not only that, but it is also used for a wide range of services such as the use of raw IP packets to determine the hosts available on a network, operating systems used by hosts, and the type of firewall used.
Platforms supported by Nmap are Windows, Linux, and OS X., So keep this in mind.
7. Nessus
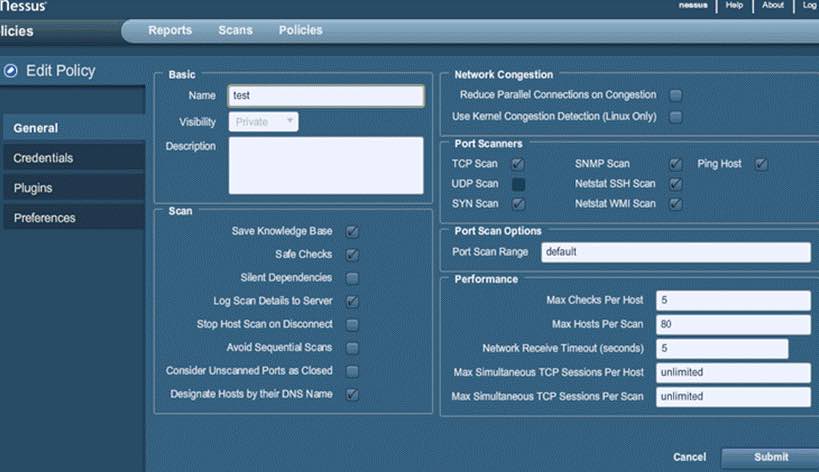
Nessus is one of the best free top security tools for windows 11. It basically works on the client-server framework.
Developed by Tenable Network Security, this tool is among the most popular vulnerability scanners in the world.
Using this tool, one can scan almost every type of vulnerability, including remote access, flaw detection, misconfiguration alert, denial of shttps://www.techworm.net/tag/securityuervices against TCP/IP stack, preparation of PCI DSS audits, malware detection, sensitive data searches, etc.
Apart from this, Nessus can also be used to scan multiple networks on IPv4, IPv6, and hybrid networks. You can even also put it into scheduled scanning mode.
8. Acunetix WVS
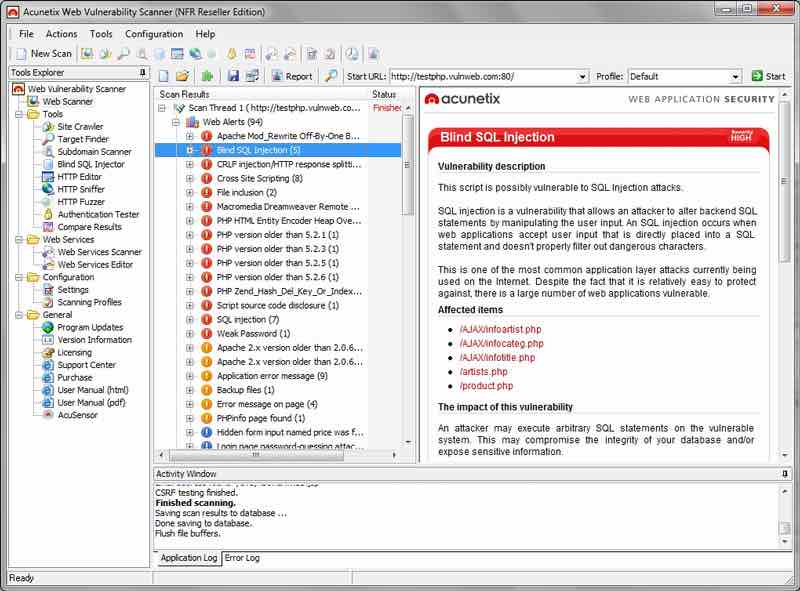
Acunetix is essentially a web vulnerability scanner (WVS) that scans and finds flaws in a website.
It’s a handy tool for most security researchers worldwide.
This multi-threaded tool mainly crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities.
It also comes up with the outstanding feature of the Login Sequence Recorder. This feature allows one to access the password-protected areas of websites.
The new AcuSensor technology used in this tool allows you to reduce the false positive rate, which is very nice, in our opinion.
9. Maltego
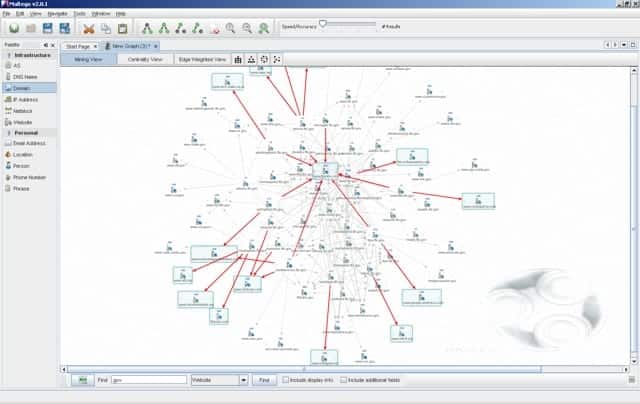
Maltego is an excellent tool for forensics. You can use it as a free hacking tool for Windows 10.
It’s an open-source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you.
On top of that, the hacking tool also excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment.
Used by many hackers, this tool is Based on Java, runs in an easy-to-use graphical interface with lots of customization options while scanning.
10. John The Ripper
John The Ripper is one of the most preferred and most trusted password cracking tools for hackers.
This is absolutely free and open-source software and distributed in the form of source code which is quite strange.
Although it is primarily written in the C programming language.
Different modules of it grant the ability to crack passwords using different encryption techniques. So if password cracking is your thing then you must go for it.
Looking for Wi-Fi hacking tool?
Read – 10 Best Wi-Fi Hacking Tools
We will advise our readers, not to opt for any online hacking tools as most of it will get you into trouble by infecting your device with malware or even getting you hacked.
Conclusion
So this was all regarding some of the best hacking tools for windows 10. If you have any better suggestions then do let us know in the comment section below, would love to hear that.
Anchit Sharma
Anchit Sharma covers evergreen explainers, how-to, tips-tricks, and lists, for Techworm. He previously wrote for GadgetsToUse and TheHackerNews.
In the ever-evolving world of cybersecurity, staying ahead of potential threats is crucial. For penetration testers and ethical hackers, having the right set of tools is essential for identifying vulnerabilities and securing systems. Windows, being a widely used operating system, is often a prime target for cyber-attacks. To help safeguard against these threats, we’ve compiled a list of the top 10 hacking tools for Windows in 2024. These tools not only enhance your security measures but also provide the necessary features for effective penetration testing and vulnerability assessment.
- What is Windows Hacking?
- Essential Tools for Windows Hacking in 2024
- 1. Metasploit Framework
- 2. Nmap
- 3. Wireshark
- 4. Cain and Abel
- 5. Aircrack-ng
- 6. John the Ripper
- 7. Hydra
- 8. Burp Suite
- 9. SQLmap
- 10. Social-Engineer Toolkit (SET)
What is Windows Hacking?

Windows hacking refers to the process of exploiting vulnerabilities within the Windows operating system to gain unauthorized access or control over a system. This can involve a range of techniques, from exploiting software bugs and weaknesses to using specialized tools for password cracking, network sniffing, and social engineering. While hacking is often associated with malicious intent, ethical hacking, or penetration testing, is conducted by cybersecurity professionals to identify and fix security flaws, ultimately enhancing the security of Windows-based systems. By understanding the methods used by hackers, security experts can better defend against potential attacks and protect sensitive information.
To effectively conduct penetration testing and enhance cybersecurity measures, it is important to utilize the best tools available. Below is a list of essential tools for Windows hacking in 2024. Each tool offers unique features that can help identify vulnerabilities, recover passwords, and perform comprehensive network analysis. By mastering these tools, cybersecurity professionals can stay ahead of threats and ensure robust protection for Windows-based systems.
1. Metasploit Framework
Metasploit remains a powerful and widely-used tool for penetration testing. It offers a comprehensive framework for developing and executing exploit code against a remote target machine.
2. Nmap
Nmap is an essential tool for network discovery and security auditing. It allows hackers to scan large networks quickly, providing detailed information about active hosts and services.
3. Wireshark
Wireshark is a top-rated network protocol analyzer. It lets you capture and interactively browse the traffic running on a computer network, aiding in troubleshooting and network analysis.
4. Cain and Abel
Cain and Abel is a versatile tool for password recovery. It uses methods such as network packet sniffing, cracking various password hashes, and performing cryptanalysis attacks.
5. Aircrack-ng
Aircrack-ng specializes in WiFi network security. It focuses on monitoring, attacking, testing, and cracking WiFi networks, making it a favorite among hackers.
6. John the Ripper
John the Ripper is an open-source password security auditing and password recovery tool available for many operating systems. It’s designed to detect weak passwords and improve overall security.
7. Hydra
Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, making it a robust tool for network security professionals.
8. Burp Suite
Burp Suite is a leading toolkit for web application security testing. It provides a comprehensive solution for finding vulnerabilities in web applications through dynamic and static analysis.
9. SQLmap
SQLmap automates the process of detecting and exploiting SQL injection flaws. It helps in taking over database servers by finding and utilizing SQL vulnerabilities.
10. Social-Engineer Toolkit (SET)
SET is an open-source penetration testing framework designed for social engineering. It focuses on attacking the human element, utilizing a variety of custom attack vectors.
By mastering these tools, cybersecurity professionals can enhance their penetration testing and vulnerability assessment capabilities, ensuring robust security for their networks and systems.
10 Best Android Keylogger
7 Techniques to Change Windows Password
Wondering which software is used for hacking? What is the best software for hacking a password? We have created a list of useful hacking tools and software that will help you do your job much easier.
Ethical hacking and online security involve a lot of efforts. Many tools are used to test and keep the software secure. The same tools can also be used by hackers for exploitation. Becoming a hacker is not easy it requires many skills. You can learn a few hacking tricks from free hacking tutorials online, some really cool hacking books, and books on information security . However, Along with all the skills, you need to have the best tools to perform hacking, security threat analysis, and penetration testing.
A hacking tool is a computer program or software which helps a hacker to hack a computer system or a computer program. The existence of hacking tools has made the lives of hackers much simpler when compared to the times they did not exist. But it does not mean that if the Hacker is equipped with a good hacking tool, his entire job is smoothly done. The hacker still requires the skills of all the aspects of hacking equally well.
This tools list includes the following types of hacking tools
- Password Cracking Tools
- Wireless / WIFI Hacking Softwares
- Network Scanning Softwares
- Packet crafting tools to exploit firewall weaknesses
- Traffic Monitoring, Packet Sniffers, and Network Hacking Tools
- Rootkit Detectors to Hack Filesystem
- Vulnerability Search Tools: Fuzzers, Scanners and more
- Forensics Softwares
- Debuggers to Hack Running Applications
- Hacking Operating Systems like Kali Linux and more
- Encryption tools
- Intrusion detection software
Password Cracker Software
A password cracker software, which is often referred to as a password recovery tool, can be used to crack or recover the password either by removing the original password, after bypassing the data encryption, or by an outright discovery of the password. In the process of password cracking, a very common methodology used to crack the user password is to repeatedly make guesses for the probable password and perhaps finally hitting on the correct one. It cannot be denied that whenever we are referring to cybersecurity, passwords are the most vulnerable security links. On the other hand, if the password is too completed, the user might forget it. Password Cracker software is often used by hackers to crack the password and access a system to manipulate it. Do not unethically use this software for hacking passwords.
In the next section, you would be getting familiar with some of the popular Password Cracker tools which are used by hackers for password cracking.
Hashcat
Hashcat is a password cracker for GPU(s) and CPU(s) using OpenCL. It can run on NVDIA and AMD devices. It is a very powerful password cracking tool that is also well documented.
Ophcrack
It is a free password cracker software which is based on the effective implementation of the rainbow tables. It runs on a number of Operating Systems like Mac OS X, Unix/Linux, and Windows Operating System. It is equipped with real-time graphs for analyzing the passwords and is open-source software. Ophcrack has the capability to crack both NTLM hashes as well as LM hashes.
Medusa
Medusa is one of the best online brute-force, speedy, parallel password crackers that is available on the Internet. It has been designed by the members of the website foofus.net. It is also widely used in Penetration testing to ensure that the vulnerability of the system can be exposed and appropriate security measures can be taken against hacking.
RainbowCrack
Rainbow Crack as the name suggests, is a cracker for hashes with the Rainbow Tables. It runs on multiple operating systems such as Linux, Windows Vista, Windows XP (Windows Operating Systems). It supports both Graphical User Interface as well as Command-line Interface. It’s software that is used for password cracking by generating rainbow tables, fuzzing all the parameters.
Wfuzz
Wfuzz is a flexible tool for brute forcing Internet-based applications. It supports many features like Multithreading, Header brute-forcing, Recursion when discovering directories, Cookies, Proxy Support, hiding results, and encoding the URLs to name a few. Wfuzz is a useful tool for finding unlinked resources like scripts, directories, and servlets as well.
Fgdump
Fgdump is a powerful cracking tool. In fact, it’s much more powerful than pwdump6 as the latter has the tendency to hang whenever there is a presence of an antivirus. Fgdump has the capability to handle this problem of hanging by shutting down first. It later restarts the Antivirus software. It supports multi-threading which is very relevant in the multitasking and multi-user environment.
John The Ripper
John the Ripper is free software for password cracking which was originally designed for the Unix Operating System. At present, it can run on 15 Operating systems which include 11 different versions of UNIX, Win32, DOS, and BeOS. It has the capability to combine several password crackers into a single package which has made it one of the most popular cracking tools for hackers.
IKECrack
The objective of this security tool is to locate the valid user identities in a Virtual Public Network along with the secret key combinations. Once this is accomplished, this information can be used easily by a hacker to have access to a VPN in an unauthorized manner
Wireless Hacking Tools
Wireless Hacking Tools are those hacking tools that are used to hack into a wireless network which is usually more susceptible to security threats. One must also ensure that the network is completely secured against hacking or other malware. The list of wireless hacking tools which would be discussed now can be used to do a Penetration Testing for a Wireless Network. This is an intentional attack on a network to detect security vulnerabilities by accessing its data and functionality.
Aircrack-ng
It is a software suite specially designed for a wireless network and which operates under both the Windows and the Linux Operating System. Aircrack-ng consists of a packet sniffer, WPA cracker, and analysis tool, and a detector for the wireless Local Area Networks (802.11). The best part of this software suit is one need not install it to use it. It is a collection of files that can be easily used with a command prompt.
It is a network software suite used in 802.11 Wireless Local Area Networks. It consists of tools such as a packet sniffer, detector, and a WEP. This tool runs on both Windows and Linux Operating systems. It can work with any type of wireless network interface controller, provided the driver is supporting the raw monitoring mode.
There have been many wireless hacking tools exposed in the recent past. When a hacker hacks a wireless network, it is supposed to defeat the Wireless network’s security devices. The Wi-Fi networks i.e. the Wireless LANs are more exposed to the security threats from a hacker while compared to that of a wired network. While hackers are always more than ready to hack especially if there are weaknesses in a computer network, hacking is often a tedious and complicated procedure.
Kismet
Kismet is a wireless detector system which detects possible intrusion to an 802.11 layer2 wireless network, it is also a sniffer. There is a certain plug-in supported by Kismet which enables sniffing media like DECT. It also has the capacity to infer whether a nonbeaconing network is present or not via the data traffic in the network and a network is identified by this tool by collecting data packets passively, detecting hidden and standard named networks.
KisMAC
It is a discovery tool for a wireless network for the Mac OS X operating system. It has many features that are similar to another wireless detector tool called Kismet. This tool is meant for expert network security personnel and is not very user-friendly for the beginners
NetStumbler
NetStumbler is a hacking tool that is used in the Windows Operating system and comes with add-ons that are used to hack a wireless network. It has the capability to convert a WIFI enabled laptop on Windows OS into a network detector in an 802.11 WLAN.
Airjack
It is a powerful tool for packet injection in an 802.11 wireless network and is very useful as it has the capability to send in forged de-authentication packets. This feature is usually used by a hacker to bring down a network.
Best Network Scanning & Hacking Tools
Nmap
Nmap or Network Mapper is a free open source utility tool for network discovery and security auditing solution for you. It is a flexible, powerful, portable, and easy-to-use tool that is supported by most of the operating systems like Linux, Windows, Solaris, Mac OS, and others.
SuperScan
It is a multi-functional application that is designed for scanning TPC port. This is also a pinger and address resolver. It also has useful features like ping, traceroute, WhoIs, and HTTP requests. There is no need for installation as it is a portable application.
Angry IP Scanner
It is a fast port and IP address scanner. It is a lightweight and cross-platform application that has the capacity to scan the IP addresses in any range and also in their ports. It simply pings each IP address.
Packet Crafting To Exploit Firewall Weaknesses
Through the Packet crafting technique, an attacker capitalizes on your firewall’s vulnerabilities. Here are some packet crafting tools
Hping
Earlier Hping was used as a security tool. Now it is used as a command-line oriented TCP/IP packet analyzer or assembler. You can use this for Firewall testing, advanced port scanning, network testing by using fragmentation, TOS, and different other protocols.
Scapy
It is a powerful and interactive packet manipulation program. Scapy has the capability to decode or forge the packets of a large number of protocols at a time. One of the best features is that it can confuse the process of decoding and interpreting.
Netcat
Netcat is a simple Unix utility program. This program has the capability to read and write data across network connections and it does so by using UDP or TPC protocol. It was created as a reliable back-end tool.
Nemesis
It is command-line crafting and injecting utility tool used for network packets. This program works for both Unix and Windows operating systems. This is a well-suited tool for testing Network, Intrusion Detection System, IP Stacks, Firewalls, and many others
Socat
This is again a command-line based utility tool. It has the capability to establish two bidirectional byte streams through which it transfers data. In this tool, streams can be constructed from a large set of different data sinks.
Yersinia
Not all network protocols are powerful. In order to take advantage of the weakness of certain network protocols, Yersinia is created. It is a full-proof framework that analyzes and tests the deployed networks and systems.
Traffic Monitoring for Network-Related Hacking
These tools allow users to monitor the websites one’s children or employees are viewing. Here’s a list of some of these tools
Splunk
If you want to convert your data into powerful insights Splunk tools are the best options for you. The Splunk tools are the leading platforms for operational intelligence. It can collect any type of data from any machine in real-time.
Nagios
Nagios is the name for the industry standard in monitoring IT infrastructure. The Nagios tools help you monitor your entire IT infrastructure and have the capability to detect problems well ahead they occur. It can also detect security breaches and share data availability with stakeholders.
P0f
It is a versatile passive tool that is used for OS fingerprinting. This passive tool works well in both Linux and Windows operating systems. It has the capability to detect the hooking up of the remote system whether it is Ethernet, DSL, or OC3.
Ngrep
Ngrep or network grep is a pcap-aware tool that allows you to extend hexadecimal or regular expressions in order to match it against the data loads of the packet. It can recognize IPv4/6, UDP, TCP, Ethernet, SLIP, PPP, FDDI, and many others.
Packet Sniffers To Analyze Traffic
These tools help capture and analyze incoming traffic on your website. Some of the popular ones are listed below
Wireshark
If you want to put a security system, Wireshark is the must-have security tool. It monitors every single byte of the data that is transferred via the network system. If you are a network administrator or penetration tester this tool is a must-have.
Tcpdump
Tcpdump is a command-line packet analyzer. After completing the designated task of packet capturing Tcpdump will throw the report that will contain numbers of the captured packet and packets received by the filter. The user can use flags like –v, -r, and –w to run this packet analyzer tool.
Ettercap
It is a comprehensive suite in the middle of the attack. It has the feature of sniffing the live connections and content filtering along with many other interesting tricks. It offers three interfaces, traditional command line, GUI, and Ncurses.
Dsniff
Dsniff is the collection of various tools that are used for penetration testing and network auditing. The tools like dsniff, msgsnarf, mailsnarf, webspy and urlsnarf passively monitor a network of interesting data like files, emails, passwords, and many others.
EtherApe
EtherApe is a graphical network monitor for UNIX model PCs after etherman. This interactive tool graphically displays network activity. It features a link layer and TCP/IP modes. It supports Token Ring, FDDI, Ethernet, PPP, SLIP, ISDN, and other WLAN devices.
Web Proxies: Proxies fundamentally assist in adding encapsulation to distributed systems. The client can request an item on your server by contacting a proxy server.
Paros
It is a Java-based HTTP/HTTPS proxy that helps in assessing the vulnerability of web applications. It supports both viewing and editing HTTP messages on-the-fly. It is supported by Unix and Windows systems. There are some other features as well like client certificate, spiders, proxy chaining and many others.
Fiddler
It is a free web debugging proxy tool that can be used for any browser, platforms or systems. The key features of this tool include performance testing, HTTP/HTTPS traffic recording, web session manipulation, and security testing.
Ratproxy
A passive and semi-automated application which is essentially a security audit tool. It can accurately detect and annotate problems in web 2.0 platforms.
Sslstrip
This tool is the one that demonstrates the HTTPS stripping attack. It has the capability to hijack HTTP traffic on the network in a transparent manner. It watches the HTTPS link and then redirect and maps those links into homograph-similar or look-alike HTTP links.
Rootkit Detectors To Hack File System
This is a directory and file integrity checker. It checks the veracity of files and notifies the user if there’s an issue.
AIDE (Advanced Intrusion Detection Environment)
It is a directory and file integrity checker that helps in creating a database using the regular expression rules that it finds from the config files. This tool also supports message digest algorithms and file attributes like File type, Permissions, Inode, Uid, Gid, and others.
Firewalls: Firewalls monitor and control network traffic. A firewall is the quintessential security tool used by novices and tech experts alike. Here are a few of the best ones for hackers:
Netfilter
Netfilter offers software for the packet filtering framework that works within the Linux 2.4.x and later series of the kernel. The software of Netfilter help in packet mangling including packet filtering along with network address and port translation.
PF: OpenBSD Packet Filter
It is an OpenBSD system that enables the filtering of TCP/IP traffic and also performs Network Address Translation. It also helps in conditioning and normalizing of TCP/IP traffic along with packet prioritization and bandwidth control.
Fuzzers To Search Vulnerabilities
Fuzzing is a term used by hackers for searching a computer system’s security vulnerabilities. Here is a list of a few:
Skipfish
It’s a reconnaissance web application security tool. Some of its features are dictionary-based probes and recursive crawls. A website’s sitemap is eventually annotated for security assessments.
Wfuzz
This tool is designed in such a way that it helps in brute-forcing web applications. Wfuzz can be used for finding resources but it does not play any role in finding the links to directories, servlets, scripts, and others. It has multiple injection points and allows multi-threading.
Wapiti
Wapiti is a web application vulnerability scanner that allows you to audit the security of the web applications that you are using. The scanning process is a “black-box” type and detects the vulnerabilities like file disclosure, data injection, XSS injection, and many others.
W3af
It is a web application attack and audit framework that helps in auditing any threat that the web application experiences. This framework is built on Python and is easy-to-use and can be extended. It is licensed under GPLv2.0.
Forensics
These tools are used for computer forensics, especially to sniff out any trace of evidence existing in a particular computer system. Here are some of the most popular.
Sleuth Kit
It is an open-source digital intervention or forensic toolkit. It runs on varied operating systems including Windows, Linux, OS X, and many other Unix systems. It can be used for analyzing disk images along with in-depth analysis of file systems like FAT, Ext3, HFS+, UFS, and NTFS.
Helix
This is a Linux based incident response system. It is also used in system investigation and analysis along with data recovery and security auditing. The most recent version of this tool is based on Ubuntu that promises ease of use and stability.
Maltego
It is an open-source forensic and intelligence application. It can be used for gathering information in all phases of security-related work. It saves you time and money by performing the task on time in a smarter way.
Debuggers To Hack Running Programs
These tools are utilized for reverse engineering binary files for writing exploits and analyzing malware.
GDB
GDB is a GNU Project Debugger. The unique feature of this debugger enables the user to see what is happening inside one program while it is being executed or check a program at the moment of the crash.
Immunity Debugger
It’s a powerful debugger for analyzing malware. Its unique features include an advanced user interface with a heap analysis tool and function graphing.
Other Hacking Tools: Besides the aforementioned tools, there is a myriad of hacking tools used by hackers. They don’t belong to a particular category, but are very popular among hackers nonetheless:
Netcat
It is a featured network utility tool. It has the capability to read and write data across all network connections that use TCP/IP protocol. It is a reliable back-end tool that can be easily and directly driven by other scripts and programs.
Visual Traceroute
It is a tracert or IP tracking tool that displays the path of internet packets through which it traversed to reach the specific destination. It identifies the IP address of each hop along the way it reaches the destination.
htDig
It is a complete searching and indexing system that is used for a domain or internet. It works on both Linux and Windows systems. It, however, does not replace the internet-wide search systems like Google, Infoseek, AltaVista, and Lycos.
CURL
It is a free and open-source software command-line tool that transfers data with URL syntax. It supports HTTP/HTTPS, Gopher, FTP, LDAP, POP3, and many others. It can run under a wide variety of operating systems. The recent stable version is v7.37.1.
Hacking Operating Systems
There are numerous professionals who aspire to have a career as ethical hackers. Hacking is not an easy task as it requires great insight about technology and programming. There are specific operating systems as well that are specially designed for hackers to use. These operating systems have preloaded tools and technologies that hackers can utilize to hack. This article offers a detailed overview of various operating systems that are built keeping hacking in mind. All these operating systems are unique form each other and have proved to be a great resource for hackers around the world.
Kali Linux
This is a creation of the makers of BackTrack. This is regarded as the most versatile and advanced penetration testing distribution ever created. The documentation of the software is built in an easy format to make it the most user-friendly. It is one of the must-have tools for ethical hackers that is making a buzz in the market.
SELinux
Security-Enhanced Linux or SELinux is an upstream repository that is used for various userland tools and libraries. There are various capabilities like policy compilation, policy management, and policy development which are incorporated in this utility tool along with SELinux services and utilities. The user can get the software as a tested release or from the development repository.
Knoppix
The website of Knoppix offers a free open source live Linux CD. The CD and DVD that is available contain the latest and recent updated Linux software along with desktop environments. This is one of the best tools for beginners and includes programs like OpenOffice.org, Mozilla, Konqueror, Apache, MySQL, and PHP.
BackBox Linux
It is a Linux distribution that is based on Ubuntu. If you want to perform a security assessment and penetration tests, this software is the one that you should have in your repository. It proactively protects the IT infrastructure. It has the capability to simplify the complexity of your IT infrastructure with ease as well.
Pentoo
It is a security-focused live CD that is created based on Gentoo. It has a large number of customized tools and kernels including a hardened kernel consisting of aufs patches. It can backport the Wi-Fi stack from the latest kernel release that is stable as well. There are development tools in Pentoo that have Cuda/OpenCL cracking.
Matriux Krypton
If you are looking for a distro to be used in penetration testing and cyber forensic investigation, then Matriux Krypton is the name that you can trust. This is a Debian based GNU/Linux security distribution. It has more than 340 powerful tools for penetration testing and forensics; additionally, it contains custom kernel 3.9.4.
Blackbuntu
It is free and open-source penetration testing distribution available over the internet. It is based on Ubuntu 10.10, which is designed specifically for information security training students and professionals. It is fast and stable yet a powerful tool that works perfectly for you. This software is a recommendation from most of the users.
WEAKERTH4N
It’s a great pen-testing distro comprising of some innovative pen-testing tools. The software uses Fluxbox and is built using Debian Squeeze. One of its popular features is its ability to hack old Android-based systems.
CAINE (Computer Aided Investigative Environment)
It is an Italian GNU/Linux live distribution list that was created as a project of Digital Forensic. It offers a complete forensic environment. This environment is organized in such a way that it integrates the existing software tools and software module and finally, throws the result in the form of a friendly graphical interface.
Helix
There are various versions of Helix released by e-fence that are useful for both home and business use. The Helix3 Enterprise is a cyber-security solution offered by this organization that provides an incident response. It throws live response and acquires volatile data. Helix3 Pro is the newest version in the block of Helix family products.
Encryption Tools
Times are changing and spying has become a common phenomenon everywhere. There have been increasing instances where even the governments have been found to be spying on their citizens from time to time. This is one of the prime reasons why the importance of Encryption has increased manifold. Encryption tools are very important because they keep the data safe by encrypting it so that even if someone accesses the data, they can’t get through the data unless they know how to decrypt the data. These tools use algorithm schemes to encode the data to prevent unauthorized access to encrypted data.
Some of the popular Encryption Tools will be discussed in this article:-
TrueCrypt
TrueCrypt is an open-source encryption tool that can encrypt a partition in the Windows environment (except Windows 8); it’s equipped for creating a virtual encrypted disk in a file. Moreover, it has the capability to encrypt the complete storage device. TrueCrypt can run on different operating systems like Linux, Microsoft Windows, and OSX. TrueCrypt stores the encryption keys in the RAM of the computer.
OpenSSH
OpenSSH is the short name for Open Secure Shell and is a free software suite that is used to make your network connections secured. It uses the SSH protocol to provide encrypted communication sessions in a computer network. It was designed originally as an alternative to the Secure Shell Software developed by SSH Communications Security. The tool was designed as a part of the OpenBSD project.
PuTTY
It an open-source encryption tool available on both UNIX and Windows operating systems. It is a free implementation of SSH (Secure Shell) and Telnet for both Windows as well as UNIX. The beauty of this tool is that it supports many network protocols like Telnet, SCP, rlogin, SSH, and raw socket connection. The word PuTTY has no specific meaning, however, as in UNIX tradition, tty is a terminal name.
OpenSSL
OpenSSL is an open-source encryption tool that implements the TLS and SSL protocols. OpenSSL’s core library is written in the C programming language. The fundamental cryptographic functions are implemented by it. OpenSSL versions are available for operating systems like UNIX, Solaris, Linux, and Mac OS X. The project was undertaken in 1988 with the objective of inventing free encryption tools for the programs being used on the internet.
Tor
Tor is a free encryption tool and has the capability to provide online anonymity as well as censorship resistance. Internal traffic is directed through a free network that consists of more than five thousand relays so that the user’s actual location can be hidden. It is difficult to track Internet activities like visiting websites and instant messages; the most important goal of this tool is to ensure the personal privacy of the users.
OpenVPN
Encryption is a vital part of hacking. If you want to put your hacking abilities to the test, a VPN is necessary. A VPN encrypts your devices and network information, keeping you anonymous on the Internet.
It is an open-source tool for the implementation of virtual private network techniques so that secure site-to-site or point-to-point connections using routers or bridges are possible, also remote access is possible. OpenVPN offers the users a secure authentication process by using secret keys which are pre-shared.
Stunnel
Stunnel is a multi-platform open-source tool that is used to ensure that both the clients and the servers get secured encrypted connections. This encryption software can operate on a number of operating system platforms like Windows as well as all operating systems which are UNIX-like. Stunnel depends upon a distinct library like SSLeay or OpenSSL to implement the protocols (SSL or TLS)
KeePass
KeePass is an open-source as well as a free password management tool for Microsoft Windows as well as unofficial ports for operating systems such as iOS, Linux, Android, Mac OS X, and Windows Phone. All the usernames, passwords, and all other fields are stored by KeePass in a secured encrypted database. This database, in turn, is protected by a single password.
Intrusion Detection System And The IDS Tools
An Intrusion Detection System is a software application or a device that is equipped to do network or system monitoring activities for any malicious threats and sends reports to the management station. Intrusion detection tools can help in identifying potential threats that can be dangerous for the system or the network.
Snort
It is an open-source Network Intrusion System as well as a Network Intrusion Prevention System which is free for all to use. It was created in 1988 by Martin Roesch. It has the capability to perform packet logging and analysis of real-time traffic on networks that are using the internet protocol.
NetCop
NetCop is an advanced intrusion detection system which is available practically everywhere. NetCop makes use of a specific method to classify the spyware. This is because there are several software programs which intrude your privacy and which have a different kind of capabilities. NetCop gives a distinct threat level to each program, thus classifying the threats.
Hacking Vulnerability Exploitation Tools
A tool that identifies whether a remote host is vulnerable to a security attack and tries to protect the host by providing a shell or other function remotely is called a Vulnerability Exploitation tool. Here is a list of some o the popular ones:
Metasploit
Metasploit was released in the year 2004 and it was an instant hit in the world of computer security. Metasploit provides data on the vulnerabilities in the security system and it helps in conducting penetration testing too.
Sqlmap
It is a penetration testing tool that is available as an open-source. Its goal is to automate the detection and exploitation process of the injection flaws in SQL and to take over the database servers.
Sqlninja
The main objective of this tool is to access a vulnerable DB server; it’s used for pen testing so that the procedure of controlling a DB server can be automated when the vulnerability of an SQL injection has been tracked.
Social Engineer Toolkit
This toolkit also known as SET was designed by TrustedSec. The tool comes as an open-source code and is Python driven. It is used for conducting Penetration Testing around Social Engineer.
NetSparker
It is a web-based security scanner that has an exploitation engine to confirm the security vulnerabilities and makes the user concentrate on the elimination of security threats with its False-Positive free feature.
BeEF
BeEF is the short term for The Browser Exploitation Framework. It is a tool for penetration testing which concentrates on a web browser and thus accesses the actual security position of the environment it’s targeting.
Dradis
Dradis stands for Direction, Range, and Distance. It is an open-source vulnerability scanner or application which provides the facility of information sharing effectively, especially during assessing the security of the system in a central repository.
Vulnerability Scanners
The scanners which assess the vulnerability of a network or a computer to security attacks are known as Vulnerability Scanners. The tools might function differently, however, all of them aim to provide an analysis of how vulnerable the system or a network is. Here is a list of the best ones:
Nessus
Nessus is the world’s most popular vulnerable scanner topping the list in the years 2000, 2003, and in the year 2006 survey on security tools. It’s free to use a vulnerability scanner for personal use in the non-enterprise environment.
OpenVAS
This scanner is tipped by many to be the most advanced vulnerability scanner in the world and is a powerful and comprehensive tool for scanning as well as providing solutions for vulnerability management. It is free software and is maintained daily.
Nipper
It is a parser for network infrastructure and its full form is Network Infrastructure Parser. This open-source scanner helps with features like auditing, configuring, and managing devices for network infrastructure as well as managing the computer networks.
QualysGuard
It is a vulnerability management scanner that provides solutions for vulnerability management by applications through the web. Designed by Qualys Inc., it’s available on demand. It helps the users by analyzing their vulnerability status.
Nexpose
Vulnerability management is one of the best security practices to protect the system or a network from security threats. Nexpose is a vulnerability management scanner which does different kind of vulnerability checks where there’s a risk in IT security.
Web Vulnerability Scanners
While vulnerability scanners are meant for your system, the web vulnerability scanners assess the vulnerability of web applications. It identifies the security vulnerabilities that your app might have by conducting various tests.
Burp Suite
Burp Suite is a tool for conducting the security test of web-based applications. It has a collection of tools that work together and conduct the entire process of testing with an objective to find as well as exploit the vulnerabilities in the security.
Webscarab
It is a testing tool for web security applications and has been written in Java and thus is operating system independent. It acts as a proxy and lets users change web requests by web browsers and web server replies. Webscarab often records the traffic to conduct a further review.
Nikto
It is a scanner for web servers and is available as an open-source. It conducts detailed testing for several items against the web servers which include testing of more than 6700 files or programs which can be dangerous. It also tests for version specific problems of the web servers.
W3af
This tool exposes more than 200 potential vulnerabilities and thus minimizes security threats to your websites. It’s written in the programming language Python. W3af has both a console user interface as well as a graphical user interface.
How to Protect Against Hacking Attacks?
It’s important to have reliable antivirus software if you want to protect your devices and data against different types of hacking attacks.
If you’re looking for the best antivirus software to protect yourself and those around you, there are several excellent antivirus software programs out there, such as Bitdefender, McAfee, Kaspersky, Avira, Avast, hack Snapchat on android, and Malwarebytes.
All of this top-notch antivirus software offers protection against all sorts of malware, including viruses, ransomware, Trojans, worms, rootkits, and more. Here’s a comprehensive video that covers the top antivirus software available on the market these days.
In 2020, Bitdefender and Kaspersky are perhaps the best antivirus software out there. We think both of these software offers top-notch anti-malware protection without putting a burden on system performance. However, according to CimaTech, Bitdefender has a slight edge over Kaspersky.
No matter which product you choose, it’s equally important that you practice safe online habits when you browse or shop online.
Can you think of more tools? Please share it with me in the comments.
Legacy / Removed Tools Archive
Below is a list of tools that were listed on this page earlier but no longer available. They are either dead or removed by owners.
L0phtCrack
L0phtCrack which is now known as L0phtCrack6 is a tool that tests the strength of a password given, as well as to recover lost passwords on the Microsoft Windows platform. Thus it is a tool for both password recovery as well as auditing the password. It uses techniques such as Rainbow tables, brute-force, and dictionary to recover passwords.
Brutus
Brutus is one of the most flexible and free password crackers which operates remotely. It is popular also because of its high speed and operates under operating systems such as Windows 2000, Windows NT, and Windows 9x. Currently, it does not operate under the UNIX operating system. Brutus was initially designed to check network devices like routers for common as well as default passwords.
THC Hydra
Every password security study has revealed that the biggest security weaknesses are passwords. THC Hydra is a tool for cracking logins and it is flexible as it supports various protocols. It is very fast and at the same time, new modules can be easily added. Hydra can run on operating systems like Solaris 11, OSX, Windows, and Linux.
Cain And Abel
Cain and Abel often referred to like Cain, is a tool for recovering the password in the Windows platform. It has the capability to recover various kinds of passwords using techniques such as cracking the password hashes by using brute-forcing, dictionary attacks, cryptanalysis attacks and packet sniffing in the network.
InSSIDer
InSSIDer is a network scanner that is used in a Wi-Fi network for the Windows Operating System as well as the Apple OS X. It has been developed by MetaGeek, LLC. It is used to collect information from both software and a wireless card and is useful in selecting the availability of the best wireless channel. It also shows those Wi-Fi network channels which overlap with each other.
Firesheep
In order to log into a website, a user has submitted details like his or her username and password. The server validates this data and sends back a “cookie”. The websites usually encrypt the password, however, it does not encrypt other details which leave the cookie exposed to hacking threats which are also known as HTTP session hijacking. Firesheep has a packet sniffer that can intercept the cookies which are encrypted from Social Media sites like Twitter and Facebook and come with the Firefox web browser. Firesheep is available for both the Windows and Mac OS X operating system. It would also run on the Linux platform in the new future.
KARMA
KARMA is an attack tool that takes advantage of the probing techniques that is used by a client of a WLAN. The station searches for a Wireless LAN in the list of preferred network and it is then that it makes the SSID open for an attacker who is listening. The disclosed SSID is used by KARMA for the impersonation of a valid WLAN and attracts the station to the listening attacker.
WepLab
The WebLab is a tool that teaches about the weaknesses of a WEP, how a WEP works, and how it is used to break a wireless network which is WEP protected. It has the features of a WEP Security Analyzer.
SSL/TLS Security Test By High-Tech Bridge
This free online service performs a detailed security analysis and configuration test of SSL/TLS implementation on any web server for compliance with NIST guidelines and PCI DSS requirements, as well as for various industry best-practices.
Encase
Encase is the fastest and most comprehensive network forensic solution available in the market. It is created following the global standard of forensic investigation software. It has the capability of quickly gathering data from a wide variety of devices.
Ping.eu
It is the tracing tool that helps the user to know the time that the data packets took to reach the host. This is an online application where you just need to place the hostname or IP address and fetch the result.
Backtrack 5r3
This operating system is built keeping the savviest security personnel in mind as the audience. This is also a useful tool even for the early newcomers in the information security field. It offers a quick and easy way to find and also update the largest database available for the security tools collection to date.
Bugtraq
It is one of the most stable and comprehensive distributions. It offers stable and optimal functionalities with the stable manager in real-time. It is based upon 3.2 and 3.4 kernels Generic that is available in both 32 and 64 Bits. Bugtraq has a wide range of tools in various branches of the kernel. The features of the distribution vary as per your desktop environment
NodeZero
This is regarded as the specialist tool that is specifically designed for security auditing and penetration testing. It is a reliable, stable, and powerful tool to be used for this purpose and is based on the current Ubuntu Linux distribution. It is a free and open-source system that you can download from the website.
Samurai Web Testing Framework
It is a live Linux environment that is designed in such a way that it functions as a web pen-testing environment. The software CD contains tools and programs that are open source and free. The tool selection is based on the ones that the company themselves use for the security of their IT infrastructure.
DEFT
DEFT is a distribution that is created for computer forensics. It can run in a live stream on the system without corrupting the device. The system is based on GNU/Linux and the user can run this live using a CD/DVD or USB pen drive. DEFT is now paired with DART, which is a forensic system.
Secunia PSI
It is free computer security software which scans software on a computer system. It tracks those third-party/non-Microsoft programs which require security updates to protect your computer against hackers and cyber-criminals.
Retina
Retina, with more than 10,000 deployments, is one of the most sophisticated vulnerability scanners in the market. It aids in efficient identifications of IT vulnerability and is also available as a standalone application as well. It essentially identifies weaknesses in the configuration and missing patches.
Websecurify
Website security is a crucial factor for both personal as well as organization websites. The prime goal should be to detect the vulnerability of your website before an intruder detects it. Web security is a testing tool for website security and can be used to detect the vulnerability of your webs
Ethical hacking is a territory less explored! The idea of breaking into a system to keep your and others’ system secure is noble. If you too are looking for getting a headstart, this is the guide for you. We have compiled a list of the best ethical hacking tools and software that will be helpful in your learning journey.

Table of Contents
We have listed the best tools for hacking for Windows and Linux in this article. These hacking tools will help you in conducting security research that can be beneficial for you and your organization. Go ahead and download the best hacking tool which suits your requirements.
Note: We do not endorse or promote any illegal activities associated with these applications. Instead, our aim is to provide valuable insights into the best hacking software for beginners.
1. Metasploit

Metasploit stands as one of the most exceptional hacking tools available for your PC download. The framework’s cross-platform support ensures seamless compatibility across Mac OS X, Linux, and Windows systems. Whether you’re an experienced security expert or a novice honing ethical hacking skills, Metasploit empowers users with a powerful toolset for conducting penetration testing and thorough security assessments.
Features:
- Open-source pen-testing framework, implemented in Ruby.
- Pivotal in recognizing and exploiting security vulnerabilities.
- Enables evasion of detection systems and executes comprehensive security vulnerability scans.
- Facilitates remote attacks and effective network enumeration.
- Ideal for ethical hacking practices and the development of security testing tools.
- Provides capability for website replication, aiding in phishing and social engineering simulations.
2. Nmap

Nmap stands out as one of the finest hacking tools available for PC download, especially during the reconnaissance phase of ethical hacking. As a powerful network security mapper, Nmap excels in discovering services and hosts within a network, enabling the creation of comprehensive network maps.
Features:
- Capable of probing computer networks, host discovery, and OS detection.
- Script extensibility allows advanced vulnerability detection and adaptation to network conditions.
- Acts as a security scanner, port scanner, and network exploration tool.
- Supports cross-platform operation on Mac, Linux, and Windows.
- Ideal for network inventory, monitoring, and vulnerability assessment.
Also Read: 16 Best Hacking Websites for Free
3. Acunetix WVS

Acunetix is undoubtedly one of the best ethical hacking tools for Windows and Linux. As a fully automated web application security testing tool, it boasts the capability to detect and report on more than 4500 web vulnerabilities, including all variants of SQL Injection and XSS. The tool’s extensive support for JavaScript, HTML5, and single-page applications allows it to effectively audit complex authenticated applications. Acunetix also offers advanced Vulnerability Management features, enabling risk prioritization based on data through a consolidated view. Its integration with other platforms and tools makes it a comprehensive solution for ethical hackers, ensuring robust security assessment and reporting.
Features:
- Fully automated ethical hacking tool for web application security testing.
- Integrates scanner results into other platforms and tools for a comprehensive view.
- Prioritizes risks based on data through a consolidated view.
- Offers advanced Vulnerability Management features.
- Scalable and fast, capable of crawling hundreds of thousands of pages without interruptions.
- Integrates with popular WAFs and Issue Trackers to aid in the SDLC.
- Available as both an On-Premises and Cloud solution for convenience.
4. Wireshark

Wireshark is undoubtedly one of the best hacking software for beginners if you need to analyze data packets and perform deep inspections of various protocols. This powerful packet analyzer offers live captures and offline analysis, allowing you to identify and address security issues and general networking problems effectively. Wireshark is a versatile and indispensable tool for anyone involved in network analysis and security assessment.
Features:
- Cross-platform support on Linux, Windows, and Mac OS X.
- Enables exporting analysis results to various file formats such as XML, PostScript, CSV, and Plaintext.
- User-friendly GUI and TTY-mode TShark utility for browsing captured network data.
- Decodes gzip files on the fly and decrypt various protocols like IPsec, ISAKMP, SSL/TLS, etc.
- Supports up to 2000 different network protocols for extensive network analysis.
- Available for free as open-source software.
5. Nessus Vulnerability Scanner

Nessus offers a powerful and widely recognized vulnerability scanner. Developed by Tenable Network Security, Nessus efficiently detects critical bugs and vulnerabilities on various systems.
Features:
- Detects unpatched services, misconfigurations, and weak passwords (default and common).
- Performs remote vulnerability scanning, password dictionary attacks, and denial of service attacks.
- It supports a variety of platforms such as Windows 7 and 8, Mac OS X, and popular Linux distros such as Debian, Ubuntu, and Kali Linux, etc.
- Nessus serves various user types with different editions like Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud.
Also Read: 8 Types of Ethical Hacking You Should Know About
6. Maltego

Maltego is undeniably one of the best hacking software for beginners if you need a powerful tool dedicated to link analysis and data mining. It offers multiple versions to suit different needs, from the free Community edition to the advanced Maltego XL. Whether you are a security professional or an ethical hacker, Maltego provides valuable insights into network weaknesses and abnormalities, making it an invaluable tool for analyzing and visualizing complex data.
Features:
- Supports Windows, Linux, and Mac OS, catering to different operating systems.
- Performs real-time information gathering and data mining.
- Presents data in graphical formats, making it easy to read and interpret.
- Library of transforms for data discovery from open sources.
7. Intruder

Intruder is a highly recommended hacking tool, especially for companies of all sizes. As a fully automated scanner, it excels at finding cybersecurity weaknesses in your digital estate and providing insights on risk assessment and remediation.
Features:
- Offers over 9,000 security checks, making enterprise-grade scanning accessible to all.
- Identifies missing patches, misconfigurations, and common web app issues.
- Integrates with Slack, Jira, and major cloud providers for seamless collaboration.
- A valuable tool for companies seeking efficient and comprehensive vulnerability scanning to enhance their cybersecurity posture.
8. John The Ripper

John the Ripper is one of the best tools for hacking for Windows and Linux, especially for password cracking. This open-source tool is highly effective in detecting weak UNIX passwords and can be utilized on Windows, DOS, and Open VMS.
Features:
- Performs dictionary attacks and tests various encrypted passwords.
- Utilizes brute force technology to decipher passwords and various algorithms.
- Auto-detects encryption type for intelligent password testing.
Also Read: What is Ethical Hacking?
9. Invicti (formerly Netsparker)

Invicti is undoubtedly a great hacking tool, especially for web application security scanning. This web application security scanner is equipped with unique Proof-Based Scanning Technology, ensuring dead accurate vulnerability detection, including SQL Injection and Cross-site Scripting in web applications and APIs.
Features:
- Requires minimal configuration for user-friendliness and efficiency.
- Seamless integration with SDLC, bug tracking systems, etc., through REST API.
- Capable of identifying URL rewrite rules and custom 404 error pages.
- Fully scalable solution, scanning up to 1,000 web applications within 24 hours.
- Available as both Windows software and online SAAS solution for flexibility and convenience.
10. CANVAS

CANVAS by Immunity is a powerful and comprehensive ethical hacking tool that offers a wide range of exploits and an automated exploitation system for penetration testers and security professionals. With over 800 exploits available, it provides robust and reliable exploit development capabilities.
Features:
- Enables users to take screenshots and download passwords from remote systems.
- Allows modification of files and escalation of privileges for administrator access.
- Integrates an alternative to Nmap called scanand for efficient port scanning in mid to large networks.
- Supports custom exploit development and a shellcode generator for enhanced flexibility.
11. Aircrack

Aircrack-ng is undoubtedly one of the best hacking tools to download for your PC, especially for assessing and securing Wi-Fi network security. This versatile tool offers a range of command-line utilities dedicated to activities like attacking, monitoring, testing, and cracking Wi-Fi networks. Aircrack-ng supports multiple platforms, including Windows, OS X, Linux, Free BSD, NetBSD, OpenBSD, Solaris, and eComStation 2, making it widely accessible to ethical hackers.
Features:
- Performs WEP and WPA2-PSK key cracking using FMS attacks, PTW attacks, and dictionary attacks.
- Allows exporting data to text files for convenient analysis and reporting.
- Checks Wi-Fi cards and driver capabilities for compatibility and optimization.
- Ideal for monitoring Wi-Fi security, performing replay attacks, and detecting fake access points.
- Trustable and widely recognized ethical hacking tool in the market.
Also Read: 20 Best WiFi Hacking Tools for PC
12. Wapiti

Wapiti is a powerful and free web application vulnerability scanner that helps identify security weaknesses in web applications. Its automatic detection feature scans for various vulnerabilities like cross-site scripting (XSS), SQL injection, and more.
Features:
- Automatic detection of web application vulnerabilities.
- Manual testing features for in-depth analysis.
- Comprehensive reporting of security issues.
- Integration capabilities with other security tools.
- Targets various vulnerabilities, including XSS, SQL injection, and more.
13. Angry IP Scanner

Angry IP Scanner (ipscan) is a great choice as hacking software if you need a fast and user-friendly network scanner. As an open-source and cross-platform tool, it efficiently scans IP addresses and ports, making it popular among network administrators, enterprises, banks, and government agencies worldwide.
Features:
- Supports IP range, random IPs, or files in different formats for scanning.
- Provides an extensible interface with multiple data fetchers for enhanced functionality.
- Over 29 million downloads, testifying to its popularity and reliability.
- Requires no installation, making it a hassle-free hacking tool for PC users.
14. Ettercap

Ettercap is a wonderful hacking tool if you need a powerful network security tool for man-in-the-middle attacks on a LAN. As a free and open-source tool, Ettercap offers a wide range of features, including sniffing live connections, content filtering on the fly, and active and passive dissection of multiple protocols.
Features:
- Enables network and host analysis for enhanced security auditing.
- Capable of conducting man-in-the-middle attacks, password sniffing, and web traffic interception.
- Supports DNS spoofing, ARP poisoning, and SSH/HTTPS tunneling for advanced penetration testing.
- A versatile and essential tool for ethical hackers and security professionals.
Also Read: 15 Best WiFi Hacking Apps For Android (2023)
15. NetStumbler

NetStumbler is a great hacking tool, especially if you need a reliable wireless network scanner for Windows. As a free and open-source tool, NetStumbler allows scanning and displaying information about wireless networks in the area, including network names, SSIDs, channels, and encryption types.
Features:
- Supports 802.11b, 802.11a, and 802.11g WLANs for efficient detection.
- Capable of detecting rogue access points for enhanced security assessment.
- Integrated support for a GPS unit, providing comprehensive network analysis and tracking.
- Ideal for verifying network configurations, locating areas with poor coverage, and detecting wireless interference.
- A valuable tool for security professionals and hobbyists interested in wireless network scanning and analysis.
16. sqlmap

sqlmap is one of the best hacking software for beginners if you need a powerful penetration testing tool for detecting and exploiting SQL injection flaws in various database management systems. As an open-source tool, sqlmap offers full support for a wide range of database systems, including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, and many more.
Features:
- Supports direct database connection without passing via SQL injection by providing credentials and server details.
- Allows enumeration of users, password hashes, privileges, databases, tables, and columns.
- Automatic recognition of password hash formats and support for dictionary-based cracking.
- Provides the ability to dump database tables, search for specific data, and download/upload files.
- Supports out-of-band stateful TCP connections, enabling interactive command prompts or Meterpreter sessions.
17. OpenVAS

OpenVAS is undoubtedly one of the best hacking tools to download for your PC if you need a comprehensive vulnerability scanner. Developed and driven forward by Greenbone since 2006, OpenVAS is a full-featured tool that can perform both unauthenticated and authenticated testing, making it highly effective in identifying vulnerabilities.
Features:
- Includes a powerful internal programming language for customizable vulnerability tests.
- Obtains vulnerability tests from a feed with a long history and daily updates.
- Part of the Greenbone Community Edition, along with other open-source modules.
- A powerful and reliable tool for security professionals and ethical hackers seeking to identify and address vulnerabilities in their systems.
Also Read: 28 Best Hacking E-books Every Beginner Should Know About
18. SQLNinja

SQLNinja is a powerful and specialized ethical hacking tool designed to exploit SQL Injection vulnerabilities on web applications that use Microsoft SQL Server as their backend database. Its primary objective is to provide remote access to the vulnerable DB server, even in hostile environments.
Features:
- Automates the process of taking over a DB server when a SQL Injection vulnerability is found.
- Tests database schema and fingerprints remote databases for assessment.
- Performs brute force attacks using word lists for penetration testing.
- Supports direct shell and reverse shell access for versatile exploitation.
19. SolarWinds

SolarWinds offers a top-notch security information and event management (SIEM) solution to improve your security posture and demonstrate compliance effectively. With centralized log collection and normalization, it ensures comprehensive monitoring and threat detection.
Features:
- Centralized log collection and normalization for comprehensive monitoring.
- Intuitive dashboard and user interface for a user-friendly experience.
- Built-in file integrity monitoring to enhance security measures.
- Simple and affordable licensing for a cost-effective solution.
- A lightweight and ready-to-use SIEM solution to improve security and compliance, making it an essential hacking tool for your PC.
20. Burp Suite

Burp Suite is undoubtedly one of the best hacking tools to download for your PC, particularly for web application security testing. With three distinct editions available, including the free Community edition, it caters to different needs and budgets. Burp Suite excels as a web vulnerability scanner, offering advanced and essential manual tools for security testing.
Features:
- Available in three editions: Community (free), Professional (starting at $399 per user/per year), and Enterprise (starting at $3999/year).
- Offers scan scheduling and repeating for efficient security testing.
- Utilizes out-of-band techniques (OAST) for accurate vulnerability detection.
- Provides detailed custom advisories for reported vulnerabilities and CI integration.
- Capable of detecting over 3000 web application vulnerabilities for comprehensive scanning.
- Suitable for both beginners and experienced manual testers, offering cutting-edge scanning logic. 14. Superscan 4.0
21. Nikto Website Vulnerability Scanner

Nikto is undeniably one of the best hacking tools to download for your PC, especially for web server scanning and vulnerability testing. As an open-source tool, Nikto is capable of identifying over 6700 potentially dangerous files and checks for outdated versions and version-specific problems on web servers.
Features:
- Supports various file formats for report saving, including text, XML, HTML, NBE, and CSV.
- Full HTTP proxy support for versatile scanning capabilities.
- Can be used on systems with basic Perl installation, including Windows, Mac, Linux, and UNIX.
- Capable of executing dictionary-based brute force attacks for comprehensive testing.
- Exports result in plain text, CSV, or HTML files for easy analysis and reporting.
Also Read: 16 Best Game Hacking Apps for Android
22. Kismet

Kismet stands as one of the best ethical hacking tools to download for your PC, especially for testing wireless networks, hacking wireless LANs, or wardriving. This versatile tool acts as a sniffer and wireless network detector, passively identifying networks, collecting packets, and detecting non-beaconing and hidden networks through data traffic analysis.
Features:
- Passively identifies networks and collects packets, detecting hidden networks through data traffic analysis.
- Supports raw monitoring mode with various wireless cards.
- Works with 802.11a, 802.11b, 802.11g, and 802.11n traffic.
- Compatible with Linux, FreeBSD, NetBSD, OpenBSD, Mac OS X, and offers a client for Microsoft Windows.
- This hacking tool is completely free to use.
Navigating the realm of ethical hacking can be an exhilarating journey, especially for beginners looking to sharpen their cybersecurity skills. Throughout this tech blog, we have highlighted the best hacking software for beginners, emphasizing their legal and responsible use. As you embark on your ethical hacking endeavors, always uphold the principles of legality, ethics, and integrity. Stay curious, stay responsible, and keep exploring the dynamic world of cybersecurity.
Время на прочтение11 мин
Количество просмотров107K

Все таргетированные хакерские атаки начинаются с разведки. Социальные инженеры, красные команды и отдельные пентестеры также собирают информацию о своих целях перед тем, как перейти к активным действиям. Им помогают десятки инструментов и хаков. Под катом ссылки на некоторые из них.
Пост состоит из 8 объемных разделов:
-
метапоисковики и поисковые комбайны;
-
инструменты для работы с дорками;
-
поиск по электронной почте и логинам;
-
поиск по номерам телефонов;
-
поиск в сети TOR;
-
поиск по интернету вещей, IP, доменам и поддоменам;
-
поиск данных об уязвимостях и индикаторов компрометации;
-
поиск по исходному коду.
В этом списке собраны инструменты, которые члены нашей команды используют в работе. И все же, эта подборка пригодится не только пентестерам, но и разработчикам, журналистам, HR, маркетологам и всем, кто много ищет в интернете. Знания — это сила. Используйте их во благо.
Как в случае инструментов для анализа зловредов или компьютерной криминалистики, я распределил инструменты на группы для удобства, в соответствии со своими представлениями о прекрасном. Список наверняка неполон, а некоторые ссылки вполне могли бы находиться в других разделах. Поскольку речь идет о поиске, в подборку не вошли многочисленные сканеры и другие инструменты для активного исследования компьютерных сетей, за исключением тех, что умеют в пассивный поиск по открытым источникам.
Метапоисковики и поисковые комбайны
Онлайн-сервисы
-
Hopain Tools, Inteltechniques, IntelligenceX, Aware OSINT Tools — представляют собой стартовые страницы для десятков поисковых систем общего и специального назначения. Все они явно ориентированы на OSINT.
-
Fagan Finder — панель с десятками поисковиков по библиотекам, архивам и базам данных.
-
Dogpile, iZito, zapmeta — метапоисковики, которые агрегируют результаты из Google, Yandex, Bing и других популярных поисковых систем и выводят на одну страницу.
-
Metaosint — поисковик по поисковым системам. Предоставляет удобный интерфейс для поиска других инструментов.
-
Synapsint — метапоисковик с возможностью поиска по IP, SSL, ASN, CVE, email и телефонным номерам.
-
ThatsThem — комбинированный поисковик по именам, адресам, телефонам, адресам электронной почты и IP.
-
Carrot2 — поисковик со встроенным алгоритмом кластеризации текста. Автоматически объединяет в группы тематически связанные источники.
-
Isearchfrom — имитирует поисковые запросы к Google из различных стран. Помогает понять, как региональные ограничения влияют на поисковую выдачу.
-
Answerthepublic — англоязычный поисковик, который выдает распространенные поисковые запросы по заданному словосочетанию.
Утилиты
-
C — поиск из командной строки в 106 источниках.
-
SpiderFoot — инструмент для автоматизации поисковых запросов и экспорта результатов в CSV, JSON, GEXF. Заточен под задачи red team. Снабжен встроенным веб-интерфейсом.
-
Query-Server — инструмент для отправки поисковых запросов в Google, Yahoo, Bing, Ask, DuckDuckGo, Baidu, Exalead, Quora, Parsijoo, Dailymotion, Mojeek и Youtube и записи результатов в CSV, JSON или XML.
-
Recon-ng — фреймворк для разведки по открытым источникам. Позволяет искать практически все от логинов, номеров телефонов и адресов, до файлов с бухгалтерской отчетностью, попавших в открытый доступ. Внешне напоминает Metasploit Framework.
-
Querytool — инструмент OSINT, основанный google-таблицах. Предназначен для сложного поиска людей, адресов электронной почты, файлов и многого другого.
-
Maltego Community Edition — это бесплатная версия OSINT-инструмента для сбора информации из Whois, поисковых систем, социальных сетей и выявления корреляций между людьми, адресами электронной почты, логинами, компаниями, веб-сайтами, доменами и т. д.
-
sn0int — фреймворк для сбора и полуавтоматической обработки информации о поддоменах, IP-адресах, скомпрометированных учетных записях, телефонных номерах и профилях в социальных сетях.
-
theHarvester — консольная утилита для сбора информации для реддтиминга. Позволяет выполнять активную и пассивную разведку при помощи различных поисковых систем. Собирает имена, адреса электронной почты, IP-адреса, поддомены и URL-адреса.
-
ReconSpider — краулер для поиска IP-адресов, электронных писем, веб-сайтов, организаций и поиска информации из разных источников.
-
Mr.Holmes — инструмент сбора информации о доменах, именах и телефонных номерах пользователя с помощью общедоступных источников и Google Dorks.
-
Datasploit — инструмент OSINT, который можно найти в Kali или BlackArch Linux. Предназначен для сбора данных по определенному домену, электронной почте, имени пользователя или номеру телефона и сохранения отчетов в текстовых файлах, HTML и JSON.
-
YaCy — децентрализованная поисковая система с открытым исходным кодом. Позволяет развернуть собственный поисковик.
Инструменты для работы с дорками
Онлайн-сервисы
-
Google Hacking Database — пополняемый каталог дорков со встроенным поиском.
-
Dorksearch — поисковая система со встроенным конструктором дорков.
-
Bug Bounty Helper — еще один онлайн-конструктор google dorks для поиска «деликатных» страниц.
Утилиты
-
pagodo — автоматизирует поиск потенциально уязвимых веб-страниц при помощи дорков из вышеупомянутой Google Hacking Database.
-
Grawler — PHP-утилита с веб-интерфейсом для автоматизации использования Google Dorks, очистки и сохранения результатов поисковой выдачи.
-
DorkScout — еще один инструмент для автоматизации поиска с использованием дорков. Написан на Golang.
-
oxDork — утилита для поиска уязвимостей и неправильных конфигураций веб-серверов.
-
ATSCAN SCANNER — предназначен для поиска с использованием дорков и массового сканирования веб-ресурсов на уязвимости.
-
Fast Google Dorks Scan — автоматизированный инструмент для сбора информации о конкретном веб-сайте при помощи дорков.
-
SiteDorks — готовый набор поисковых запросов для Google, Bing, Ecosia, DuckDuckGo, Yandex, Yahoo и так далее. Включает 527 веб-сайтов.
Поиск по электронной почте и логинам
Онлайн-сервисы
-
Snusbase — индексирует информацию из утечек и дает доступ к поиску по скомпрометированным адресам электронной почты, логинам, именам, IP-адресам, телефонам и хешам паролей.
-
have i been pwned? — поисковик по утечкам данных. Позволяет проверить, в каких инцидентах участвовал конкретный адрес электронной почты.
-
Hunter и Skymem — поиск корпоративных email-адресов по URL.
-
whatsmyname — поиск учетных записей в различных сервисах по логину. В основе сервиса лежит общедоступный JSON.
-
User Searcher — бесплатный инструмент, который поможет найти пользователя по логину на более чем 2 тыс. веб-сайтов.
-
CheckUserNames, Instant Username Search, Namecheckr, peekyou, usersearch — онлайн-сервисы для поиска аккаунтов пользователя по логину.
Утилиты
-
Infoga — инструмент, для сбора информации об учетных записях по электронной почте из общедоступных источников (поисковые системы, серверы ключей PGP, Shodan) и проверяющий, не произошла ли утечка электронной почты, с помощью API haveibeenpwned.com.
-
Holehe OSINT — проверяет, привязана ли электронная почта к учетным записям на таких сайтах, как twitter, instagram, imgur. Поддерживает более 100 порталов. Использует функцию восстановления пароля.
-
Mailcat — ищет адреса электронной почты по нику у 22 почтовых провайдеров.
-
WhatBreach — инструмент OSINT, упрощающий задачу обнаружения утечек, в которых участвовал конкретный адрес электронной почты. Умеет загружать общедоступные базы данных.
-
h8mail и pwnedOrNot — инструменты для поиска паролей от скомпрометированных адресов электронной почты в общедоступных базах данных.
-
Sherlock — инструмент для поиска аккаунтов в социальных сетях по логину пользователя.
-
Snoop Project — инструмент для поиска по логинам. По уверениям разработчика охватывает более двух с половиной тысяч сайтов.
-
Maigret — собирает досье на человека логину, проверяя аккаунты на двух с половиной тысячах сайтов и собирая всю доступную информацию с веб-страниц. Ключи API не требуются. Форк Sherlock.
-
Social Analyzer — API, интерфейс командной строки и веб-приложение для анализа и поиска профилей человека на более чем 1 тыс. сайтов.
-
NExfil — python-утилита для поиска профилей по имени пользователя на 350 веб-сайтах.
-
SPY — еще один быстрый поисковик по именам аккаунтов, работает с 210 сайтами.
-
Blackbird — инструмент для поиска аккаунтов по логину в социальных сетях.
-
Marple — упрощает поиск по логину через общедоступные поисковые системы от Google до Torch и Qwant.
-
GHunt — модульный инструмент для сбора данных о google-аккаунтах.
-
UserFinder — инструмент для поиска профилей по имени пользователя.
Поиск по номерам телефонов
Утилиты
-
Moriarty — утилита для реверсивного (обратного) поиска по телефонным номерам. Позволяет найти владельца, получить ссылки, страницы социальных сетей и другую связанную с номером информацию.
-
Phomber — выполняет поиск по телефонным номерам в интернете и извлекает все доступные данные.
-
PhoneInfoga — известный инструмент для поиска международных телефонных номеров. Сначала выдает стандартную информацию, такую как страна, регион, оператор связи по любому международному телефонному номеру, а затем ищет его следы в поисковых системах, чтобы помочь идентифицировать владельца.
-
kovinevmv/getcontact — утилита для получения информации из баз приложения GetContact (не подходит для парсинга, позволяет выполнить только ограниченное число запросов).
Поиск в сети TOR
Онлайн-сервисы
-
IACA darkweb tools — стартовая страница для двух десятков поисковых систем, работающих с TOR и доступных из обычного веба.
-
Ahmia.fi — еще один поисковик по сети TOR. Выделяется открытым исходным кодом.
-
SearchDemon, Phobos, Tor66, ExcavaTOR, Raklet, SeИtoЯ, Torch, OnionLand Search — поисковые системы, работающие внутри сети TOR.
-
Exonera Tor — база данных IP-адресов, которые были частью сети Tor. Поисковик отвечает на вопрос, работал ли ретранслятор Tor на этом IP-адресе в выбранную дату.
-
Relay Search — веб-приложение для обнаружения ретрансляторов и мостов Tor, предоставляющее информацию о том, как они настроены. Имеет открытый исходный код.
Утилиты
-
TorBot — удобный Onion краулер. Собирает адреса и названия страниц с кратким описанием, получает адреса электронной почты с сайтов, проверяет, активны ли ссылки, и сохраняет отчеты в JSON. Может быть запущен в Docker.
-
VililantOnion — Onion краулер с поддержкой поиска по ключевым словам.
-
Katana-ds — Python-инструмент для автоматизации поиска с использованием Google Dorks и с поддержкой TOR.
-
OnionSearch — скрипт Python3 для автоматизации поиска в зоне .onion через общедоступные сервисы.
-
Devils Eye — это инструмент OSINT для поиска в Darkweb. Не требует установки TOR. Также может искать в сети i2p.
Поиск по интернету вещей, IP, доменам и поддоменам
Онлайн-сервисы
-
Shodan — знаменитая поисковая система для сбора информации об устройствах, подключенных к интернету.
-
Censys Search, GreyNoise, ZoomEye, Netlas, CriminalIp — аналогичные Shodan поисковые системы, ориентированные на IoT.
-
Buckets by Grayhatwarfar — база данных с общедоступным поиском по открытым AWS Buckets, Azure Blobs, Digital Ocean Spaces.
-
Public buckets — поиск общедоступных бакетам AWS S3 & Azure Blob.
-
macaddress.io, MAC Vendor Lookup, maclookup.app — определяют производителя устройства по MAC-адресу, OUI или IAB.
-
CIRT, Default Password Lookup, Router Password, Open Sez Me — поиск по базам данных паролей, установленных по умолчанию на различных устройствах.
-
sitereport.netcraft — выдает комплексную сводку по регистрационным данным и технологиям, используемым на веб-сайте.
-
IPVoid — набор инструментов для исследования IP-адресов: проверка по черным спискам, Whois, поиск по DNS, пинг.
-
who.is, DomainDossier, whois.domaintools — поиск по регистрационным данным и Whois.
-
DNSDumpster — инструмент для исследования доменов, который может обнаруживать хосты, связанные с доменом.
-
ip-neighbors — определяет местоположение сервера, и имена хостов, которые делят с ним IP-адрес.
-
ShowMyIP — массовый поиск IP-адресов, позволяет проверять до 100 IP-адресов одновременно. Выдачу можно загрузить сохранить в .csv-файл.
-
MX Toolbox — еще один многофункциональный инструмент, позволяющий искать по доменному имени, IP-адресу или имени хоста.
-
DNSViz — это набор инструментов для анализа и визуализации системы доменных имен. Имеет открытый исходный код.
-
infosniper, ip2geolocation, ip2location, ipfingerprints, whoismind — поисковики, которые позволяют найти приблизительное географическое местоположение IP-адреса, а также другую полезную информацию, включая интернет-провайдера, часовой пояс, код города и т. д.
-
webmeup, openlinkprofiler, Meet Link Explorer — поиск по обратным ссылкам.
-
RapidDNS — инструмент для DNS-запросов, который упрощает поиск поддоменов или сайтов с одним и тем же IP-адресом.
-
CTSearch, crt — поиск по SSL/TLS сертификатам, выпущенным для конкретного домена.
Утилиты
-
IVRE — фреймворк для сетевой разведки. Альтернатива Shodan, ZoomEye, Censys и GreyNoise.
-
OWASP Amass — сетевой сканер с функцией поиска информации в открытых источниках. Агрегирует информацию из десятков различных поисковых систем и баз данных.
-
Infoooze — инструмент OSINT на базе NodeJs. Объединяет в себе сканер портов и поддоменов, поиск DNS-поиск URL-сканер, поиск в Whois и еще ряд инструментов.
-
Automater — утилита для поиска URL, IP-адресов и хешей MD5, предназначенная для упрощения работы ИБ-аналитиков. Установлена в Kali Linux по умолчанию.
-
Raccoon — инструмент, созданный для разведки и сбора информации с упором на простоту. Использует Nmap для сканирования портов и ряд пассивных методов поиска данных, чтобы собрать всестороннюю информацию о цели.
-
Mitaka — предназначена для поиска IP-адресов, MD5, ASN и биткойн-адресов.
-
Photon — сканер для работы с информаций из открытых источников. Предназначен для сканирования конкретных веб-сайтов в поисках (pdf, png, xml и т. д.), ключей, поддоменов и многого другого. Экспортирует полученные данные в JSON.
-
AttackSurfaceMapper — сканер с функциями поиска по открытым источникам. Ищет поддомены и связанные с ними IP-адреса.
-
HostHunter — использует методы разведки по открытым источникам для сопоставления IP-адресов с именами хостов. Выгружает результаты поиска в CSV или TXT-файлы.
-
Subfinder — модульный инструмент для обнаружения поддоменов при помощи методов пассивной разведки. Предназначен для багхантеров и пентестеров.
-
Sublist3r — предназначен для поиска поддоменов с использованием OSINT.
-
WASP Amass — выполняет сетевое картирование при помощи информации из открытых источников.
-
Anubis — еще одна утилита для обнаружения поддоменов и сбора информации о них из открытых источников.
-
DOME — скрипт python, выполняющий активное и/или пассивное сканирование для получения поддоменов и поиска открытых портов.
-
Belati — инструмент для сбора общедоступных данных и документов с веб-сайтов Вдохновлен Foca и Datasploit.
Поиск данных об уязвимостях и индикаторов компрометации
Онлайн-сервисы
-
MITRE CVE — поисковик, база данных и общепринятый классификатор уязвимостей.
-
NIST NVD — поиск по официальной американской правительственной базе данных об уязвимостях.
-
GitHub Advisory Database — база данных уязвимостей, включающая CVE и рекомендации по безопасности.
-
CVEDetails, osv.dev, VulDB, maltiverse — еще ряд источников данных об уязвимостях и индикаторах компрометации.
-
opencve.io — поисковик CVE со встроенными оповещениями о новых угрозах.
-
security.snyk.io и Mend Vulnerability Database, Vulncode-DB — базы данных уязвимостей с открытым исходным кодом.
-
Cloudvulndb — проект, который аккумулирует уязвимости и проблемы безопасности поставщиков облачных услуг.
-
Vulnerability Database — система для поиска информации об актуальных угрозах.
-
Rapid7 — DB — база данных, которая содержит детали более чем 180 тыс. уязвимостей и 4 тыс. эксплойтов. Все эксплойты включены в Metasploit.
-
Exploit DB — CVE-совместимый архив общедоступных эксплойтов и уязвимого программного обеспечения.
-
sploitus — поисковик по эксплойтам и хакерским инструментам.
Поиск по исходному коду
Онлайн-сервисы
-
Searchcode — поиск реальных примеров функций, API и библиотек на 243 языках в GitHub, GitLab, Bitbucket, GoogleCode и других хранилищах исходного кода.
-
Sourcegraph — быстрый и функциональный поисковик по open-source репозиториям. Имеет selfhosted-версию.
-
HotExamples — поиск примеров кода open-source проект. Позволяет увидеть на одной странице примеры использования того или иного класса или метода из нескольких проектов.
-
Libraries.io — поиск по 4 690 628 пакетам в 32 пакетных менеджерах.
-
RepoSearch — поиск исходного кода в репозиториях SVN и GitHub.
-
grep.app — поиск по содержимому Git. Полезен для поиска строк, связанных с уязвимостями индикаторами компрометации и вредоносными программами.
-
Search from Cyber_detective — поиск в 20 репозиториях с открытым исходным кодом при помощи дорков.
-
PublicWWW — позволяет найти любой буквенно-цифровой фрагмент, в том числе куски HTML, JavaScript, CSS-кода в коде веб-страниц.
-
NerdyData — поиск веб-сайтов, использующих определенные технологии.
Утилиты
-
Gitrob — инструмент, помогающий находить потенциально конфиденциальные файлы, помещенные в общедоступные репозитории на Github. Клонирует репозиторий, перебирает историю коммитов, помечает подозрительные файлы и выводит результаты в веб-интерфейс.
-
Github Dorks — утилита для поиска с использованием дорков через GitHub Search API. Написан на Python.
-
gitGraber — инструмент для мониторинга GitHub и оперативного поиска конфиденциальных данных, например, кредов от Google, Amazon (AWS), Paypal, Github, Mailgun, Facebook, Twitter, Heroku, Stripe, Twilio.
-
github-search — коллекция консольных инструментов для исследования Github.
-
TheScrapper — предназначен для поиска адресов электронной почты и учетных записей социальных сетей в исходном коде веб-сайта.
