Для централизованной настройки параметров получения и установки обновлений на рабочих станциях и серверах Windows можно использовать групповые политики. В этой статье мы рассмотрим базовые параметры GPO, которые позволяют управлять установкой обновлений на компьютерах, получающих обновления от локального сервера WSUS или напрямую с серверов Windows Update в интернете.
Содержание:
- Настройка параметров получения обновлений клиентам WSUS через GPO
- Назначить групповые политики WSUS на OU с компьютерами
- Применение групповых политик Windows Update на клиентах
- GPO для получения и установки обновлений Windows Update через Интернет
Настройка параметров получения обновлений клиентам WSUS через GPO
Если у вас развернут собственный сервер обновлений Windows Server Update Services (WSUS), вы должны настроить рабочие стации и сервера в вашем домене AD для получения обновлений с него (а не с серверов Microsoft Update через Интернет).
В нашем случае мы хотим создать две разные политики установки обновлений для рабочих станций и серверов. Для этого откройте консоль управления WSUS (
wsus.msc
) на сервере и создайте в разделе Computers -> All Computers две группы компьютеров:
- Workstations
- Servers
Затем перейдите в раздел настройки сервера WSUS (Options), и в параметре Computers измените значение Use Group Policy or registry setting on computers (Использовать на компьютерах групповую политику или параметры реестра).
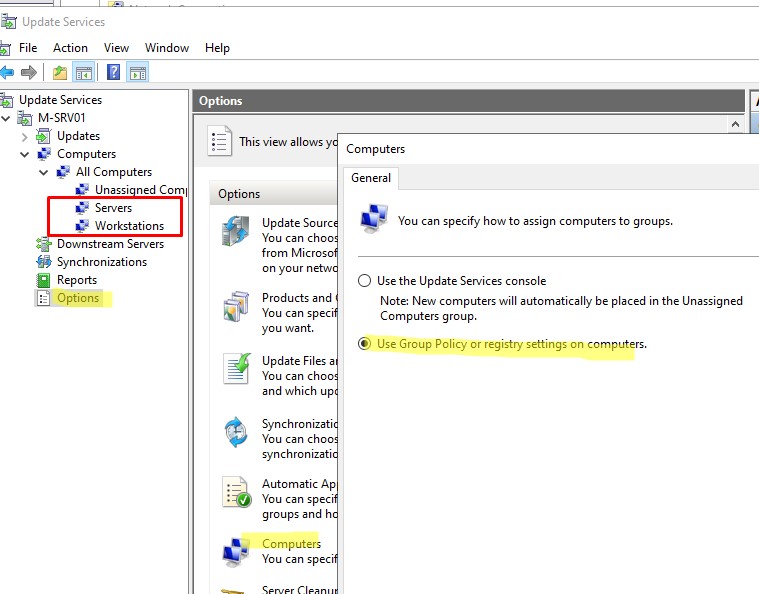
Эта опция включает client side targeting для клиентов WSUS (таргетинг на стороне клиента). Благодаря этому вы сможете автоматически распределить компьютеры по группам обновлений в консоли WSUS по специальной метке в реестре клиента (такая метка создается через GPO или напрямую в реестре.
Теперь откройте консоль управления доменные групповыми политиками (Group Policy Management) и создайте две новые групповые политики: ServerWSUSPolicy и WorkstationWSUSPolicy.
Начнем с описания серверной политики ServerWSUSPolicy.
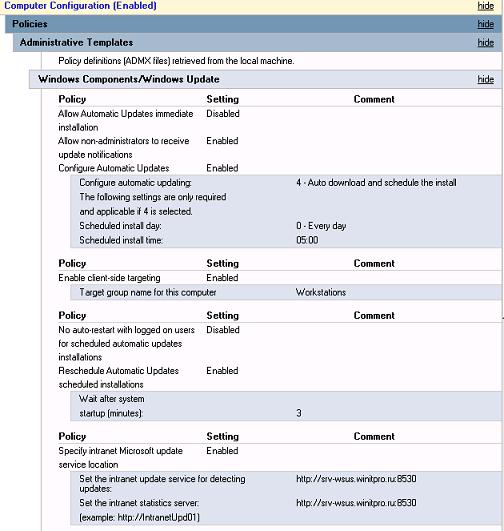
Настройки параметров службы обновлений Windows, находятся в разделе GPO: Computer Configuration -> Policies-> Administrative templates-> Windows Component-> Windows Update (Конфигурация компьютера -> Административные шаблоны -> Компоненты Windows -> Центр обновления Windows).
Мы хотим, чтобы продуктивные сервера не устанавливали обновления автоматически и не перезагружались без подтверждения администратора. Для этого настроим GPO так, чтобы сервера автоматически скачивали доступные обновления, но не устанавливали их. Администраторы будут запускать установку обновлений вручную (из панели управления или с помощью модуля PSWindowsUpdate) в согласованные окна обслуживания.
Настроим следующие параметры политики:
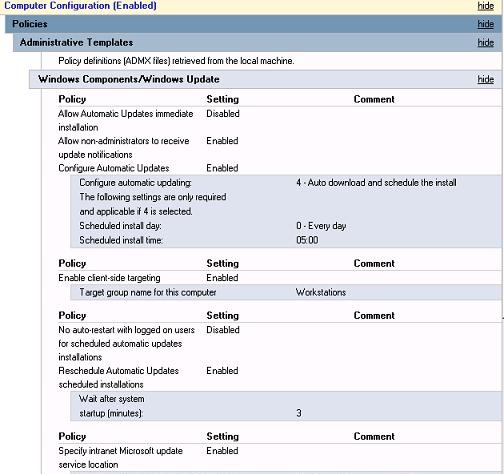
- Configure Automatic Updates (Настройка автоматического обновления):
Enable
.
3 – Auto download and notify for install
(Автоматически загружать обновления и уведомлять об их готовности к установке) – клиент автоматически скачивает новые обновлений и оповещает об их наличии; - Specify Intranet Microsoft update service location (Указать размещение службы обновлений Майкрософт в интрасети): Enable. Set the intranet update service for detecting updates (Укажите службу обновлений в интрасети для поиска обновлений):
http://srv-wsus.winitpro.ru:8530
, Set the intranet statistics server (Укажите сервер статистики в интрасети):
http://srv-wsus.winitpro.ru:8530
– здесь нужно указать адрес вашего сервера WSUS и сервера статистики (обычно они совпадают); - No auto-restart with logged on users for scheduled automatic updates installations (Не выполнять автоматическую перезагрузку при автоматической установке обновлений, если в системе работают пользователя):
Enable
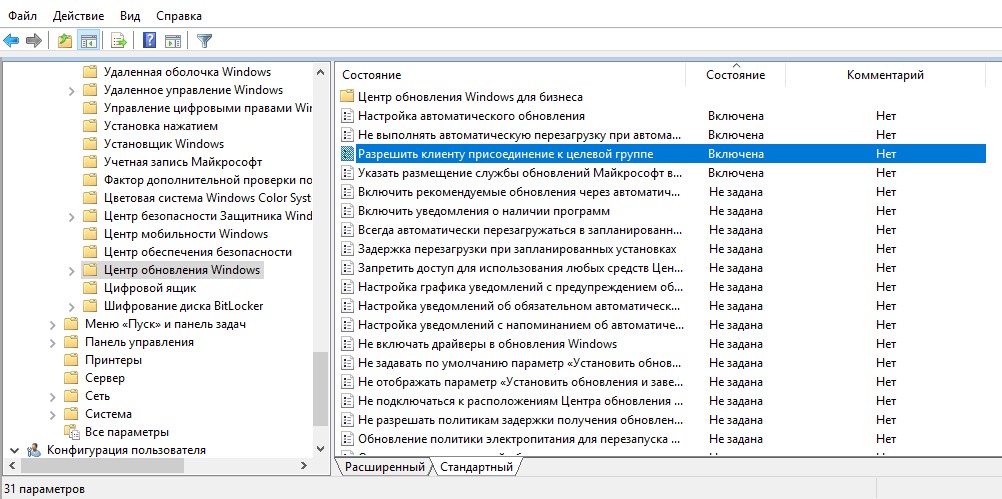
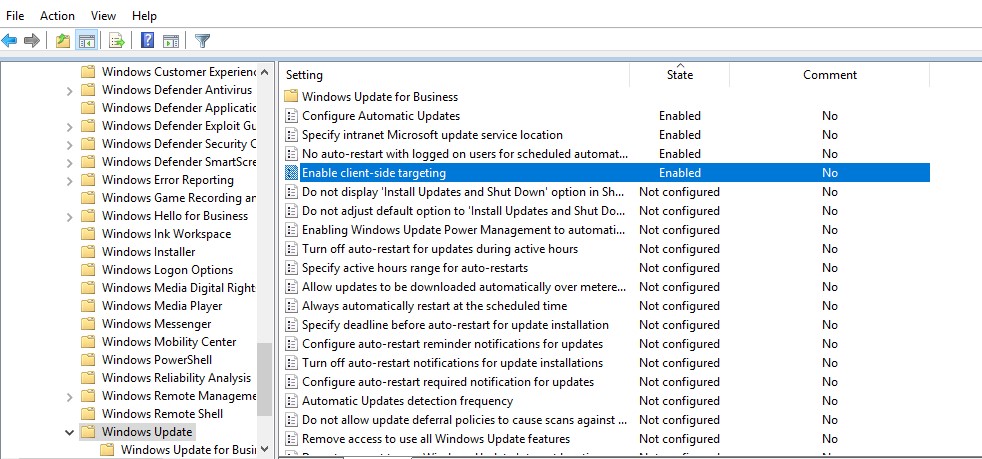
– запретить автоматическую перезагрузку при наличии сессии пользователя; - Enable client-side targeting (Разрешить клиенту присоединение к целевой группе):
Enable
. Target group name for this computer (Имя целевой группы для данного компьютера):
Servers
– в консоли WSUS отнести клиенты к группе Servers
Для рабочих станций мы хотим включить автоматическую загрузку и установку Windows Update сразу после получения новых обновлений. Компьютеры после установки обновлений должны перезагружаться автоматически в нерабочее время (с предварительным предупреждением пользователей).
В настройках WorkstationWSUSPolicy указываем:
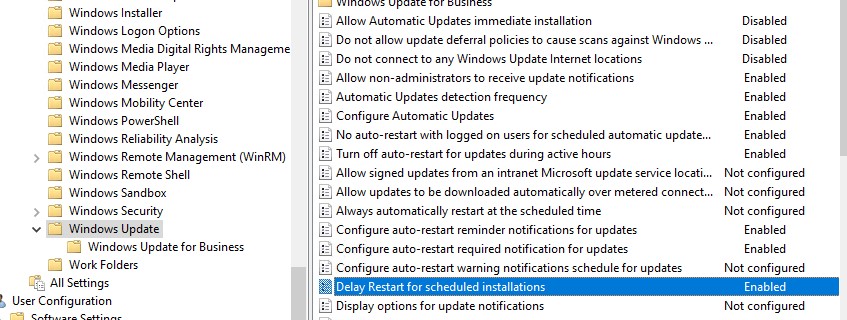
- Allow Automatic Updates immediate installation (Разрешить немедленную установку автоматических обновлений):
Disabled
— запрет на немедленную установку обновлений при их получении; - Allow non-administrators to receive update notifications (Разрешить пользователям, не являющимся администраторами, получать уведомления об обновлениях):
Enabled
— отображать не-администраторам предупреждение о появлении новых обновлений и разрешить их ручную установку; - Configure auto-restart reminder notifications for updates и Configure auto-restart warning notifications schedule for updates – показывать пользователям уведомления о перезагрузке
- Configure Automatic Updates:
Enabled
. Configure automatic updating:
4 — Auto download and schedule the install
. Scheduled install day:
0 — Every day
. Scheduled install time:
05:00
– при получении новых обновлений клиент скачивает в локальный кэш и планирует их автоматическую установку на 5:00 утра; - Enable client-side targeting:
Workstations
– в консоли WSUS отнести клиента к группе Workstations; - No auto-restart with logged on users for scheduled automatic updates installations:
Disabled
— система автоматически перезагрузится через 5 минут после окончания установки обновлений; - Specify Intranet Microsoft update service location: Enable. Set the intranet update service for detecting updates:
http://srv-wsus.winitpro.ru:8530
, Set the intranet statistics server:
http://srv-wsus.winitpro.ru:8530
–адрес WSUS сервера. - Включите опции Do not allow update deferral policies to cause scans against Windows Update (ссылка) и Do not connect to any Windows Update Internet locations. Это позволит предотвратить обращение клиента к серверам Windows Update в интернете.
- Turn off auto-restart for updates during active hours –
Enabled
. Отключить авто перезагрузку после установки обновлений в рабочее время (задать интервал рабочего времени в политике Active Hours Start и Active Hours End. Например, с 8 AM до 5 PM)
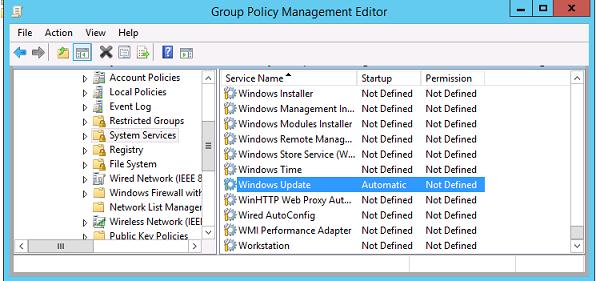
В обеих GPO включите принудительный запуск службы Windows Update (
wuauserv
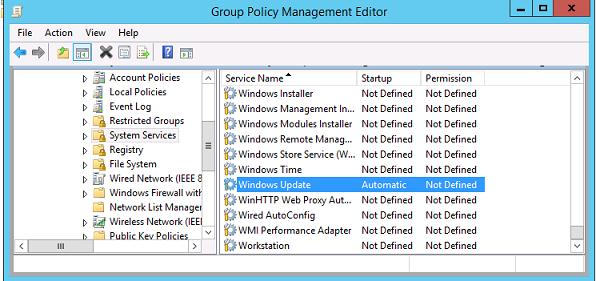
) на компьютерах. Для этого в разделе Computer Configuration -> Policies-> Windows Setings -> Security Settings -> System Services найдите службу Windows Update и задайте для нее автоматический запуск (Automatic).
Назначить групповые политики WSUS на OU с компьютерами
Затем в консоли управления GPO прилинкуйте созданные вами политики к соответствующим контейнерам (подразумевается что для серверов и рабочих станций в AD созданы отдельные контейнеры OU).
Совет. Мы рассматриваем лишь один довольно простой вариант привязки политик WSUS к клиентам. В реальных организациях возможно привязать одну политику WSUS на все компьютеры домена (GPO с настройками WSUS вешается на корень домена), разнести различные виды клиентов по разным OU (как в нашем примере – мы создали разные политики WSUS для серверов и рабочих станций). В больших распределенных доменах можно привязывать различные WSUS сервера к сайтам AD, или же назначать GPO на основании фильтров WMI, или скомбинировать перечисленные способы.
Щелкните в консоли GPMC по нужному OU, выберите пункт меню Link as Existing GPO и привяжите нужную политику WSUS.
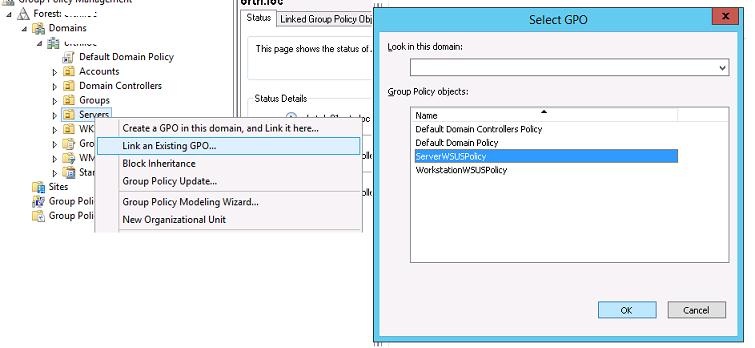
Совет. Также привяжите серверную политику WSUS к OU Domain Controllers.
Аналогично назначьте политику для компьютеров на OU с рабочими станциями.
Применение групповых политик Windows Update на клиентах
Дождитесь применения новых настроек GPO на клиентах или обновите их вручную:
gpupdate /force
Чтобы с клиента ускорить процесс регистрации и сканирования состояния на сервере WSUS, выполните команды:
$updateSession = new-object -com "Microsoft.Update.Session"; $updates=$updateSession.CreateupdateSearcher().Search($criteria).Updates
wuauclt /reportnow
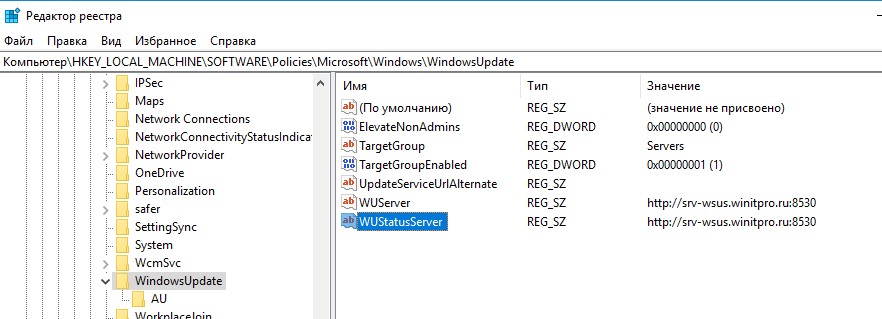
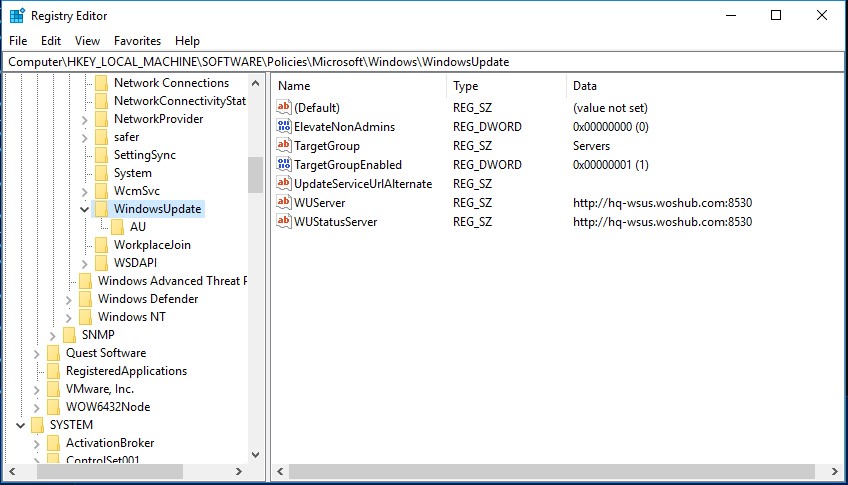
Все настройки Windows Update, которые мы задали групповыми политиками должны появится на клиентах в ветке реестре HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate.
Настройки из этой ветки можно экспортировать в REG файл и использовать его для переноса настроек WSUS на другие компьютеры, на которых нельзя задать параметры обновления с помощью GPO (компьютеры в рабочей группе, изолированных сегментах, DMZ и т.д.)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"WUServer"="http://srv-wsus.winitpro.ru:8530"
"WUStatusServer"="http://srv-wsus.winitpro.ru:8530"
"UpdateServiceUrlAlternate"=""
"TargetGroupEnabled"=dword:00000001
"TargetGroup"="Servers"
"ElevateNonAdmins"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000000 –
"AUOptions"=dword:00000003
"ScheduledInstallDay"=dword:00000000
"ScheduledInstallTime"=dword:00000003
"ScheduledInstallEveryWeek"=dword:00000001
"UseWUServer"=dword:00000001
"NoAutoRebootWithLoggedOnUsers"=dword:00000001
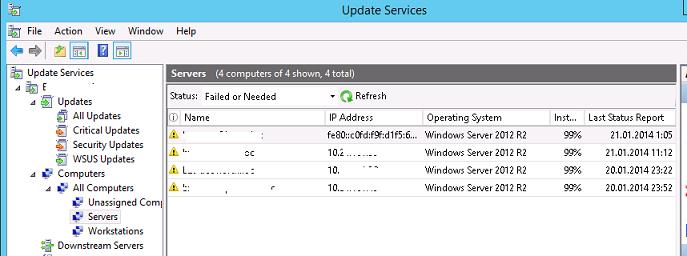
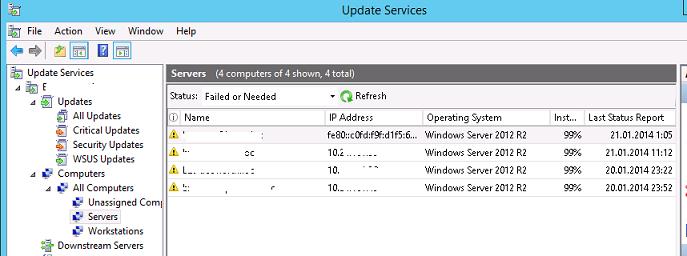
Через некоторое время все клиенты появятся в назначенных группах компьютеров в консоли WSUS. Здесь будут видны имена компьютеров, IP адреса, версии ОС, процент их пропатченности и дата последнего сканирования.
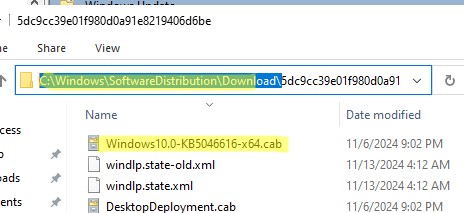
Клиенты скачивают CAB файлы обновлений в каталог
%windir%\SoftwareDistribution\Download
. Логи сканирования, загрузки и установки обновлений можно получить из файлов WindowsUpdate.log.
GPO для получения и установки обновлений Windows Update через Интернет
Если у вас отсутствует собственный сервер WSUS, вы можете использовать рассмотренные выше групповые политики для настройки параметров получения и установки обновлений на компьютеры из интернета (с серверов Windows Update).
В этом случае задайте в Not configured все параметры GPO, которые задают получение обновлений с WSUS:
- Specify Intranet Microsoft update service location: Not set
- Target group name for this computer: Not Set
- Do not allow update deferral policies to cause scans against Windows Update: Disabled
- Do not connect to any Windows Update Internet locations: Disabled
Такоие настройки GPO позволяет вам управлять тем, как компьютеры скачивают и устанавливают обновления Windows.
Estimated reading time: 4 minutes
Mastering Windows Update Management with Group Policy
Managing Windows Updates via Group Policy (GPO) remains a cornerstone for IT admins in 2025, especially with Windows 11 24H2 and Server 2022 dominating. Whether you’re delaying feature updates, enforcing patch schedules, or integrating with Intune, this guide dives into every step, tool, and trick to keep your systems current and secure. From local setups to domain-wide policies, we’ve got the details—plus PowerShell alternatives and cloud options.
Step 1: Access Group Policy Editor
For standalone PCs or domain controllers, GPO is your friend. Here’s how to start:
Local Machine: Press Win + R, type gpedit.msc, and hit Enter. Works on Windows 11 Pro/Enterprise or Server 2022.
Domain: On a domain controller, open Group Policy Management (GPMC) via Server Manager > Tools, then create or edit a GPO (e.g., “Windows Update Policy”).
Note: Link the GPO to an OU (e.g., “Workstations”) in GPMC for domain-wide effect. Use gpupdate /force to apply changes instantly.
Step 2: Configure Update Policies
Navigate to: Computer Configuration > Administrative Templates > Windows Components > Windows Update > Manage end user experience. Key settings:
- Configure Automatic Updates: Set to “4 – Auto download and schedule the install.” Pick a day/time (e.g., Sunday 3 AM). Options: 2 (notify), 3 (auto download, notify), 4 (schedule), 5 (user choice).
- Specify intranet Microsoft update service location: For WSUS, enter your server (e.g.,
http://wsus.company.local:8530) in both fields. - Defer feature updates: Under
Windows Update for Business, set “Select when Feature Updates are received” to 180 days—keeps you off bleeding-edge builds like 24H2’s early bugs. - No auto-restart with logged-on users: Enable to avoid midday reboots—critical for servers.
Pro Tip: Use Get-GPOReport -Name "Windows Update Policy" -ReportType HTML in PowerShell to audit settings.
Step 3: Test and Troubleshoot
Force an update check: wuauclt.exe /detectnow (still works in 2025, despite deprecation rumors). Check Event Viewer under Applications and Services Logs > Microsoft > Windows > WindowsUpdateClient for errors—Event ID 19 means success.
Common Fix: If updates fail, reset the client with net stop wuauserv, delete C:\Windows\SoftwareDistribution, then net start wuauserv.
Alternative: PowerShell for GPO
For scripting fans, manage policies with PowerShell:
# Requires GroupPolicy module
Import-Module GroupPolicy
$policy = "Windows Update Policy"
$gpo = Get-GPO -Name $policy
Set-GPRegistryValue -Name $policy -Key "HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU" -ValueName "AUOptions" -Type DWord -Value 4
Set-GPRegistryValue -Name $policy -Key "HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU" -ValueName "ScheduledInstallDay" -Type DWord -Value 1 # SundayNotes: Run on a DC as admin. Adjust “Value” for other options (e.g., 2 for notify).
Cloud Option: Intune Integration
For hybrid or cloud-first setups, Intune’s taking over GPO’s role:
Setup: In Intune (intune.microsoft.com), go to Devices > Windows > Update Rings. Create a ring, set feature update deferral (180 days), and assign to an Azure AD group.
Bonus: Add a Compliance Policy to flag non-updated devices—email alerts beat manual checks.
Best Practices
- Stagger Updates: Use multiple GPOs (e.g., “Test Group,” “Production”) to roll out patches in waves.
- Monitor: WSUS Reporting or Intune’s dashboard—aim for 95% compliance.
- Security: Enable “Do not connect to Windows Update Internet locations” to force internal sources.
FAQ
Q: Does GPO work with Windows 11 Home?
A: No, Home lacks gpedit.msc—upgrade to Pro or use registry hacks.
Q: Can WSUS and Intune coexist?
A: Yes, but avoid overlap—set Intune to “Windows Update for Business only” if WSUS is primary.
Q: Why defer updates?
A: Early builds (e.g., 24H2) often have bugs—180 days lets Microsoft patch them.
Glossary
- GPO: Group Policy Object—rules applied to users/devices in Active Directory.
- WSUS: Windows Server Update Services—local update server.
- Intune: Microsoft’s cloud MDM for device management.
- VSS: Volume Shadow Copy Service—used by updates for consistency.
Next Steps: See our Windows Server Backup Guide for recovery prep.
Group Policies allow centrally configuring Windows Update settings that determine how updates are received and installed on workstations and servers in a domain network. In this article, we’ll look at the basic GPO options that you can use to manage Windows Update settings on computers that receive updates from an intranet WSUS server or directly from Windows Update servers on the Internet.
Contents:
- Configure Windows Update GPO Settings for WSUS Clients
- Assign the Windows Update GPOs to the WSUS Clients
- Applying Windows Update Group Policy to Client Computers
- Configure Clients to Receive Updates from the Internet via GPO
Configure Windows Update GPO Settings for WSUS Clients
Once you have installed the local Windows Server Update Services (WSUS) host, configure the workstations and servers in your Active Directory to receive updates from it (instead of from Microsoft Update servers over the Internet).
In our example, we want to create two different update installation policies for workstations and servers. To do this, open the WSUS management console (wsus.msc) on the server and create two computer groups under the Computers -> All Computers section.
- Workstations
- Servers
Then open the WSUS Options and in the Computers parameter, change the value to Use Group Policy or registry setting on computers.
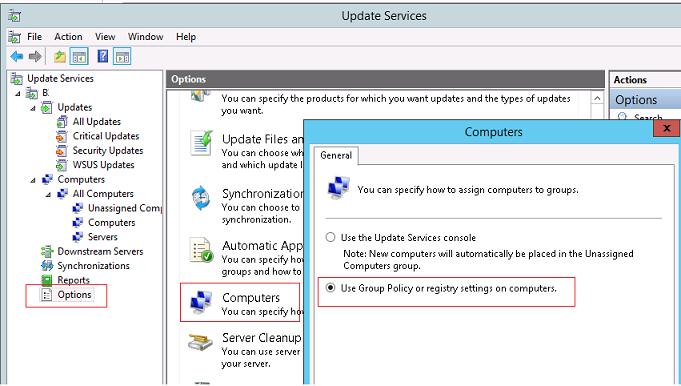
This option enables client-side targeting for WSUS clients. This allows computers to be automatically assigned to update groups using a special registry parameter that contains the WSUS computer group name (this registry parameter is set by GPO or by direct registry modification).
Then open the Group Policy Management console (gpmc.msc) and create two new GPOs: ServerWSUSPolicy and WorkstationWSUSPolicy.
Let’s start with the description of the server update policy, named ServerWSUSPolicy.
The settings for the Windows Update service are located in this GPO section: Computer Configuration -> Policies –> Administrative Templates -> Windows Component-> Windows Update.
The server update policy should prevent production servers from automatically installing updates or restarting without the administrator’s approval. Let’s configure the GPO so that the servers automatically download available updates, but do not install them. During scheduled maintenance windows, administrators can manually initiate the installation of updates (from the Settings app or using the PSWindowsUpdate module).
Configure the following policy options:
- Configure Automatic Updates:
Enable.3 – Auto download and notify for install– client automatically downloads new updates and notifies about them; - Specify Intranet Microsoft update service location:
Enable. Set the intranet update service for detecting updates:http://hq-wsus.woshub.com:8530, Set the intranet statistics server:http://hq-wsus.woshub.com:8530– set the address of the local WSUS server and the statistics server (they are usually the same) - No auto-restart with logged on users for scheduled automatic updates installations:
Enable– disable the automatic restart if there are active user sessions - Enable client-side targeting:
Enable. Target group name for this computer:Servers– assign clients to the Servers group in the WSUS console.
For workstations, we want to enable Windows Update to automatically download and install new updates as they become available. Users’ computers should be automatically rebooted (with user notification) after installing updates during non-working hours.
Configure the following settings in the WorkstationWSUSPolicy GPO:
- Allow Automatic Updates immediate installation
Disabled—prevent updates from being installed as soon as they are received; - Allow non-administrators to receive update notifications
Enabled— show non-admin users a notification about new updates and allow manual installation; - Configure auto-restart reminder notifications for updates and Configure auto-restart warning notifications schedule for updates:
Enabled– display reboot notifications to users - Configure Automatic Updates:
Enabled. Configure automatic updating:4 — Auto download and schedule the install. Scheduled install day:0 — Every day. Scheduled install time:05:00AM– client downloads new updates and schedules them to install automatically at 5:00 am; - Enable client-side targeting:
Workstations– this will assign the client to the Workstations group in the WSUS console; - No auto-restart with logged on users for scheduled automatic update installations:
Disabled - Specify Intranet Microsoft update service location:
Enabled. Set the intranet update service for detecting updates:http://hq-wsus.woshub.com:8530, Set the intranet statistics server:http://hq-wsus.woshub.com:8530</emcode– is the address of the internal WSUS server. - Enable Do not allow update deferral policies to cause scans against Windows Update (so-called Dual Scan) and Do not connect to any Windows Update Internet locations. This prevents the client from contacting Windows Update servers on the Internet.
- Turn off auto-restart for updates during active hours –
EnabledDisable automatic restart after installing updates during working hours (set the working time interval in theActive Hours StartandActive Hours Endoptions. For example, from 8 AM to 5 PM
Force the Windows Update service (wuauserv) to start automatically on domain computers in both GPOs. To do this, go to Computer Configuration -> Policies-> Windows Settings -> Security Settings -> System Services, find the Windows Update service, and set it to start automatically.
Assign the Windows Update GPOs to the WSUS Clients
Then link the policies you have created to the appropriate containers (OUs) in the GPO management console (It is assumed that separate Organizational Units are created in AD for server and workstation objects).
Tip. We considered only one fairly simple strategy for linking WSUS update policies to clients. In real-world organizations, it is possible to link a single WSUS policy to all domain computers (GPO with WSUS settings attached to a domain root) or to distribute different types of clients across different OUs (as in our example, we have created different WSUS policies for the server and the workstations.). In large distributed domains, you may want to link different WSUS servers to AD sites, link GPOs based on WMI filters, or use a combination of the above methods.
In the Group Policy Management console, click on the required OU, select Link an Existing GPO, and select ServerWSUSpolicy.
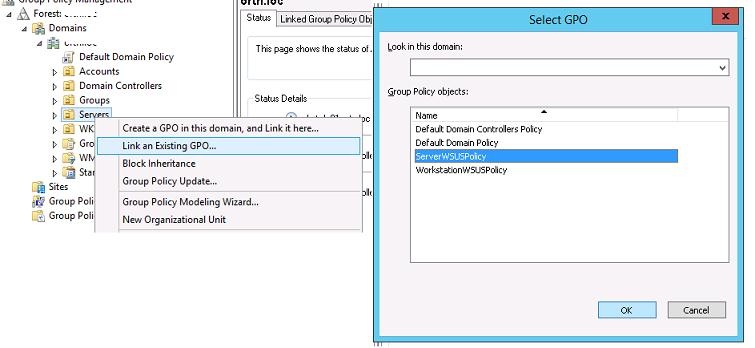
Tip. Also, link the WSUS server policy to the Domain Controllers OU.
Similarly, assign the Workstation Update policy to the OU containing the users’ computers.
Applying Windows Update Group Policy to Client Computers
Wait for the new GPO settings to be applied to the clients, or update them manually:
gpupdate /force
To force the clients to check in and report their status to the WSUS server, run:
$updateSession = new-object -com "Microsoft.Update.Session"; $updates=$updateSession.CreateupdateSearcher().Search($criteria).Updates
wuauclt /reportnow
Any Windows Update settings set through Group Policy should appear on the client in the registry key HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate. This reg key can be exported to a REG file and used to apply WSUS update settings to other computers that cannot be configured via GPO (computers in workgroups, isolated segments, DMZ, etc.)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"WUServer"="http://hq-wsus.woshub.com:8530"
"WUStatusServer"="http://hq-wsus.woshub.com:8530"
"UpdateServiceUrlAlternate"=""
"TargetGroupEnabled"=dword:00000001
"TargetGroup"="Servers"
"ElevateNonAdmins"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000000 –
"AUOptions"=dword:00000003
"ScheduledInstallDay"=dword:00000000
"ScheduledInstallTime"=dword:00000003
"ScheduledInstallEveryWeek"=dword:00000001
"UseWUServer"=dword:00000001
"NoAutoRebootWithLoggedOnUsers"=dword:00000001
After a while, clients will appear in their assigned computer groups in the WSUS console. Here you can see computer names, IP addresses, OS versions, the percentage of assigned patches they have installed, and the date of the last scan.
Client computers download the CAB update files to the %windir%\SoftwareDistribution\Download directory. The WindowsUpdate.log files provide detailed logs of how the client scans for updates against WSUS, downloads, and installs them.
If you encounter error 0x80244010 when getting updates on clients, try changing the frequency of checking for updates on the WSUS server using the Automatic Update detection frequency policy option.
Configure Clients to Receive Updates from the Internet via GPO
Suppose you don’t have an intranet WSUS server. In that case, you can use the GPO settings discussed above to configure the settings for automatically receiving and installing updates on client computers from the Internet (from Windows Update servers).
In this case, set any GPO parameters that set receiving updates from WSUS to Not Configured:
- Specify Intranet Microsoft update service location:
Not Configured - Target group name for this computer:
Not Configured - Do not allow update deferral policies to cause scans against Windows Update:
Disabled - Do not connect to any Windows Update Internet locations:
Disabled
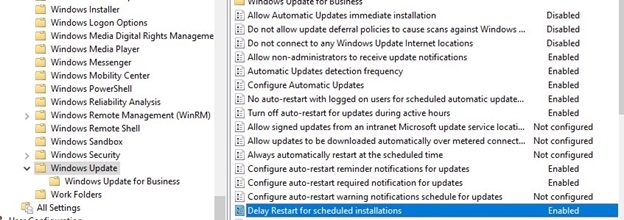
These GPO settings control how your domain computers download and install Windows updates from Microsoft Internet Update servers.
In this tutorial, we’ll show you how to configure Windows updates using Group Policy so you can keep your system as secure and up-to-date as possible.
We’ve stressed the importance of keeping your systems up to date countless times on this blog and even looked at different ways of managing your updates. But today, we’re going to look at how you can set up automatic Windows updates using Group Policy, also referred to as GPO. In this tutorial, we’ll just be focusing on Windows 10, and although the process for Windows Server will be similar, we’ll address that operating system in a separate tutorial in the future.
NOTE: You can find many other tutorials and articles on Group Policy here.
Before you get started…
To successfully complete this tutorial, you will need the following:
- To be registered on the Jotelulu platform and to have logged in.
- A Windows Server with AD DS installed.
- A user account with administrator privileges.
Creating a Windows Update Policy Using GPO
To create a Group Policy, you will need to first open Server Manager, click on the Tools menu and select Group Policy Management (1).
NOTE: You can also open the Group Policy Management window by running “GPMC.MSC”.

Next, find the domain that you wish to work on and expand the tree structure until you find the organisational unit (OU) to which your new update policy will apply (2).
Once you have found it, right-click on the Delegation and click on Create a GPO in this domain, and Link it here… (3).

At this point, a window will appear in which you need to give a name to the new GPO (4). Take your time to pick a suitable name. In the future, you may have quite a lot of GPOs. So, try to name it something descriptive and easy to understand so that you can find it in the future. For the purposes of this tutorial, we’ve named it «Windows Update Policy».
Once you have entered a name, click on OK (5).

The next step is to configure your new Group Policy. Find your policy in the tree on the left-hand side of the screen, right-click on it and click on Edit… (6).

At this point, the Group Policy Management Editor will open. The purpose of this GPO is to update the Windows devices within a given delegation. So, expand the following path on the left-hand side of the screen: Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update (7).

Once you have done this, make sure that Windows Update is highlighted in the left-hand pane (8). Then, in the right-hand pane, double-click on the setting called Configure Automatic Updates (9).
At this point, a window will appear where you will configure your updates. First, click on the radio button next to «Enabled» (10). Then, select an option from the drop-down menu below «Configure automatic updating (11). We recommend choosing «7 – Auto Downloading, Notify to Install, Notify to Restart».
Next, mark the checkbox next to «Install during automatic maintenance» (12).
Then, you need to select when and how often you want your devices to update (13):
- Scheduled install day (how often updates are installed).
- Scheduled install time (at what time updates are installed).
You should also mark the checkbox «Install updates for other Microsoft products» (14) in order to update other software packages like Office, Visual Studio, etc.
Finally, to apply your changes, click on Apply (15) and OK (16).

Back in the Group Policy Management Editor, you should now see that Configure Automatic Updates is «Enabled» (17).

Congratulations! You’ve just created a policy to apply automatic updates to all devices within an Organisational Unit (OU).
Summary
As you’re probably tired of hearing by now, keeping all your network devices updated is a critical task and can consume quite a lot of time. That’s why it’s definitely worth taking the time to automate them whenever possible.
In this short tutorial, we’ve shown how you can minimise your workload and set up Windows Updates using Group Policy (GPO). It’s a really quick and easy task once you know the steps to follow, but if you come up against any problems, don’t hesitate to contact us so we can help you.
Meanwhile, check out our other tutorials to learn more about a range of topics, including configuring Windows features, deploying network services and much, much more!
Thanks for choosing Jotelulu!
I am still pretty early in my journey of learning how to manage Windows 10 Pro updates, but I am a little encouraged to find that there are several setting in Group Policy that are not available in the UI. If it works as expected (and documented), at least with build 1709, you have these capabilities:
- Extend maximum Active Hours from 12 to 18
- Schedule updates e.g. during the night; can even restrict to certain days of the week and/or weeks of the month
- Prevent restarts if a user is logged on
The two key article on this are Build deployment rings for Windows 10 updates and Walkthrough: use Group Policy to configure Windows Update for Business (currently only updated to version 1607).
Manage device restarts after updates has valuable info on group policy settings and the corresponding registry keys for gaining control over restarts.
Even if the machine is not domain-joined, if it’s Pro, you can set these values directly in the registry. Configure Automatic Updates using Registry Editor is a reference of all registry settings.
Group Policy Setup
To see these features in Group Policy Management, you’ll have to install the latest Administrative Templates (.admx) for group policy. The 1709 templates are here.
Loosely following the “Build deployment rings” article above, I decided to create three policies:
- Windows 10 Update – Common Settings (uses WMI to target Windows 10 computers)
- Windows 10 Update – Broad Ring (uses WMI to target Windows 10 computers)
- Windows 10 Update – Fast IT Ring (applies only to my own management computer)
Note If you set your Windows 10 WMI filter to
select * from Win32_OperatingSystem Where Version like '10.%'
it will also include (and apply these policies to) Windows Server 2016. This filter forces it to apply to Windows 10 clients only:
select * from Win32_OperatingSystem Where Version like '10.%' and ProductType='1'
I’ll post my current settings in each policy below.
Windows 10 Update – Common Settings
Note that Allow Telemetry must be at least 1 for any of this to work, and Automatic updating must be 4 for scheduled updates to work. I’m doing 3am updates every day, don’t restart if someone is logged on, use an 18-hour Active Hours window of 6am to midnight, and block preview builds.
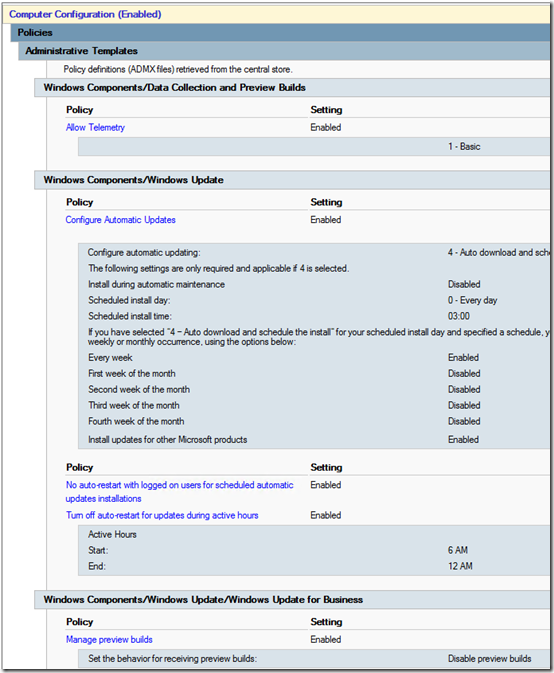
Update April 9, 2018 4/9/2018 If you use WSUS, under Windows Components > Windows Update, enable “Do not allow update deferral policies to cause scans against Windows Update” per Susan Bradley’s recommendation here. See more info in this TechNet article. The setting has no effect if you’re not using WSUS.
Update May 26, 2020 It turns out that “Turn off auto-restart for updates during active hours” has no effect when “No auto-restart with logged on users” is enabled (see the instructions in the GPO itself). I have now disabled “Turn off auto-restart for updates during active hours.” This allows machines to automatically reboot after installation of updates, as long as no one is logged in. Paired with a script that automatically logs off users each evening, this works pretty well to get Windows 10 machines patched without further intervention.
Windows 10 Update – Broad Ring
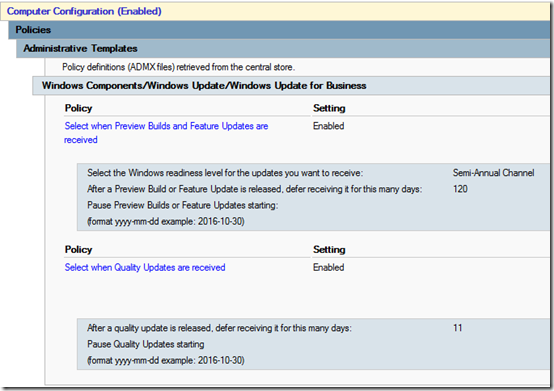
Yes, 11 days, thinking that if an update comes out on Tuesday, I want it installed on Saturday.
Windows 10 Update – Fast IT Ring
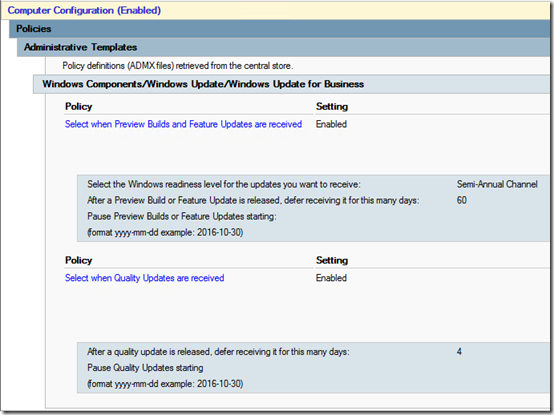
Not dropping to Semi-Annual (Targeted) as recommend by Microsoft; just getting the Semi-Annual Channel after 60 days instead of 120 and quality updates after 4 days.
Client View
After setting up and applying the policies, it takes awhile (20-30 minutes?) until the Settings app reflects the change. The Active hours option disappears:
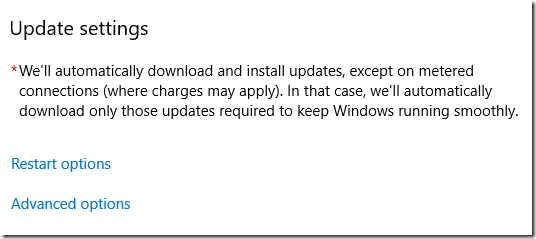
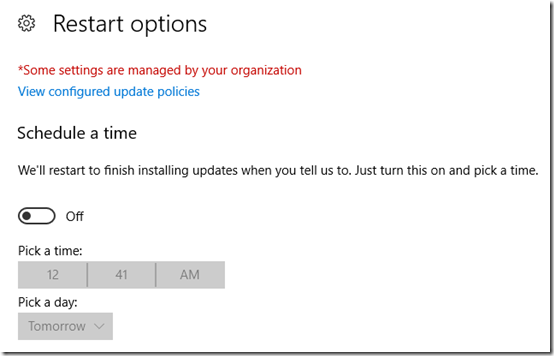
Restart options shows the time, but gives the option to change the schedule:
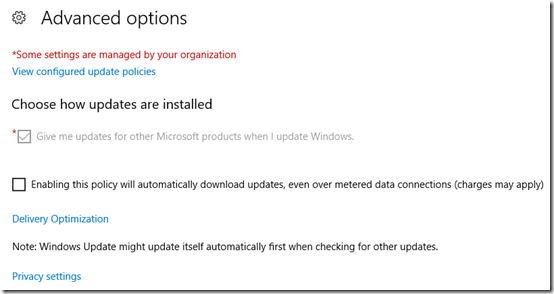
Advanced options was originally showing the 120- and 11-day values, grayed out. Maybe they will return once updates have installed.
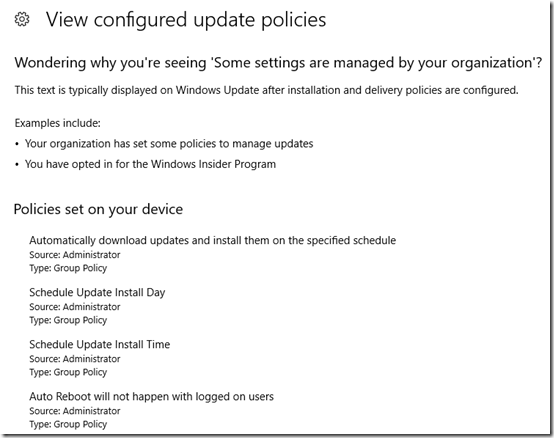
View configured update policies shows what settings are coming from Group Policy, but not what the values are:
I left my computer logged on last night. It apparently installed updates overnight, but the restart was blocked by policy. I see this now:
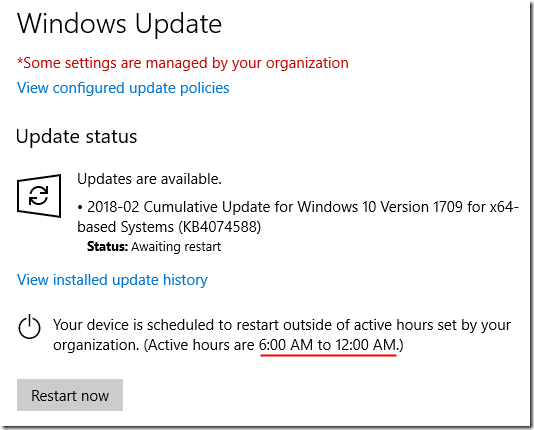
Registry values
Most of the settings wind up in HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate and the AU subkey. Here’s what those keys look like in a domain-joined Windows 10 1709 machine (paste to a .reg file if you want to import). This list does not include “Do not allow update deferral policies to cause scans against Windows Update” as it was created for a non-WSUS environment.
Update May 26, 2020 This now shows a Windows 10 1909 machine with the SetActiveHours option disabled. See details above.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate] "DeferFeatureUpdates"=dword:00000001 "BranchReadinessLevel"=dword:00000020 "DeferFeatureUpdatesPeriodInDays"=dword:00000078 "PauseFeatureUpdatesStartTime"="" "DeferQualityUpdates"=dword:00000001 "DeferQualityUpdatesPeriodInDays"=dword:0000000b "PauseQualityUpdatesStartTime"="" "ManagePreviewBuilds"=dword:00000001 "ManagePreviewBuildsPolicyValue"=dword:00000000 "DisableDualScan"=dword:00000001 "SetActiveHours"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU] "NoAutoRebootWithLoggedOnUsers"=dword:00000001 "NoAutoUpdate"=dword:00000000 "AUOptions"=dword:00000004 "ScheduledInstallDay"=dword:00000000 "ScheduledInstallTime"=dword:00000003 "ScheduledInstallEveryWeek"=dword:00000001 "AllowMUUpdateService"=dword:00000001
