Вряд ли для кого-нибудь секретом является тот факт, что компьютеры нужно защищать. Особенно если вы используете сервер на базе Windows 2000 для выхода в Интернет. Это типично для многих организаций. Windows 2000 намного проще и удобнее в настройке, чем различные версии Unix. А при должной настройке эта система не менее устойчива к взлому и стабильна. Впрочем, многие любители Unix могут с этим не согласиться, но это мое мнение. Обычно к серверу Windows 2000 подключается модем выделенной линии (или любое другое устройство), параллельно с локальной сетью. При этом организуется либо раздача соединения с Интернетом по локальной сети (Internet Connection Sharing, простейший вариант NAT), либо устанавливается прокси-сервер. Каждый из этих вариантов имеет свои плюсы и минусы, но с точки зрения гибкости управления и учета деятельности пользователей я предпочитаю второй. В любом случае нужно ясно понять – сервер придется защищать. Самое удивительное – Windows 2000 (равно как и XP) обладают богатыми встроенными возможностями по защите, и в этой статье я постараюсь вам объяснить, как ими пользоваться. Но для начала давайте вспомним базовые концепции стека протоколов TCP/IP.
Особенности стека TCP/IP
Основной протокол стека TCP/IP – это IP (Internet Protocol). Он работает на сетевом уровне и занимается доставкой пакетов. У отправителя и получателя должны существовать уникальные IP адреса, которые указываются в заголовках каждого пакета. То есть первый критерий фильтрации – мы можем пропускать пакеты только от нужных (или только к нужным) IP адресам. Это самая примитивная фильтрация.
Но помимо протокола IP в сети работают несколько других протоколов. Каждый из них добавляет в пакет свой заголовок, то есть в момент передачи по сети пакет представляет собой «слоеный пирог», где помимо данных помещены заголовки различных протоколов. Один из этих заголовков вы уже знаете – это заголовок протокола IP.
Выше протокола IP находятся протоколы транспортного уровня – это TCP (Transmission Control Protocol) и UDP (User Datagram Protocol). Обычно используется либо TCP, либо UDP. Каждый из этих протоколов тоже добавляет в пакет свой заголовок. У UDP и TCP есть своя специфика – они, в отличие от IP, уже умеют работать с сетевыми службами. Причем адресация сетевых служб происходит по адресу службы – номеру порта. Отсюда вытекает вторая возможность фильтрации – мы можем ограничивать доступ по номеру порта. При этом номер порта можно комбинировать с IP адресом – к примеру, разрешать доступ на веб-сайт сервера (стандартно TCP порт 80) только с определенных IP адресов. Учтите, что хотя номера портов для TCP и UDP похожи, это разные протоколы и номера портов у них тоже разные. Номера портов большинства служб стандартизированы, и вы можете посмотреть их в файле «services», который размещается в каталоге %systemroot%system32driversetc. %Systemroot% — это каталог, где у вас установлена Windows. Кстати,
комбинация «IP адрес» + «номер порта» называется сокетом. Сокет позволяет уникально адресовать службу в Интернете.
Когда вы обращаетесь к удаленному серверу по протоколу TCP, то происходит процесс установления связи. К примеру, вы
обратились к веб-серверу узла 192.168.1.1 (стандартно – на TCP порт 80). При этом ваш компьютер (клиент) тоже должен
выделить порт, чтобы сервер знал, куда отправлять ответ. Порт клиента выделяется случайным образом – к примеру, пусть это будет TCP 29334.
Кстати, очень полезно использовать утилиту «netstat.exe», которая входит в стандартную поставку Windows – она
показывает все текущие TCP соединения и открытые порты.
Как правило, все сетевые службы общаются через TCP или UDP. TCP сегодня используется наиболее часто. Так что практически в любом пакете вы обнаружите заголовки TCP и UDP, по которым мы и будем осуществлять фильтрацию.
Осталось упомянуть протокол ICMP (Internet Control Message Protocol). Он использует IP, но не задействует ни TCP, ни UDP. ICMP предназначен для диагностики компьютерной сети, и его, в принципе, можно разрешать с любого IP адреса на любой IP адрес. По ICMP работает утилита «ping.exe», также стандартно поставляющаяся с Windows. С помощью утилиты ping вы сможете проверить доступность любого узла в Интернете. А с помощью еще одной утилиты – tracert.exe – проверить маршрут до выбранного узла.
Теперь после небольшого теоретического введения давайте перейдем собственно к построению защиты. Я буду иллюстрировать статью английской версией операционной системы, поскольку использовать русскую версию сервера Windows 2000 я настоятельно не рекомендую. Вряд ли «база знаний» на русском языке столь же информационно наполнена, как knowledge base на английском – а ведь это именно тот ресурс, который жизненно необходим всякому уважающему себя администратору. Для непосвященных
отмечу – «knowledge base» содержит ответы практически на все вопросы, там указаны практически все ошибки Windows, а также даны рекомендации по их решению и различные советы.
Настройка брандмауэра
Первое, что мы делаем – переходим в Local Security Policy (Control Panel -> Administrative Tools).
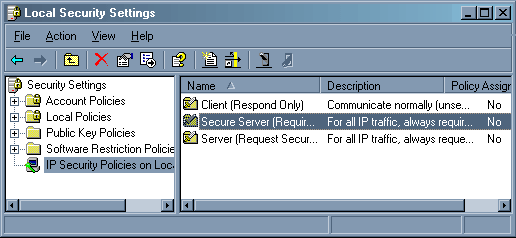
Там выбираем строчку «IP security policies…» Там уже есть три политики, но мы с вами будем создавать новую.
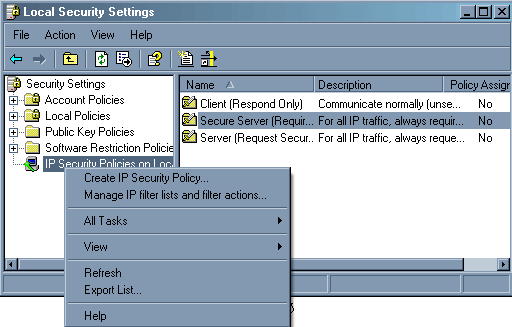
Нажимаем правую клавишу мыши на «IP security policies…», выбираем «Create IP security policy…» Запустится мастер установки IP политики.
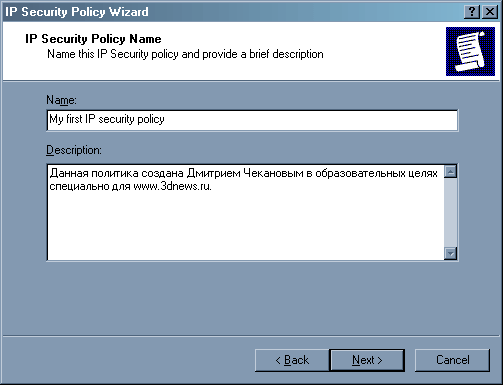
Здесь предлагается ввести название политики и ее описание. Пусть будет «My first IP security policy».
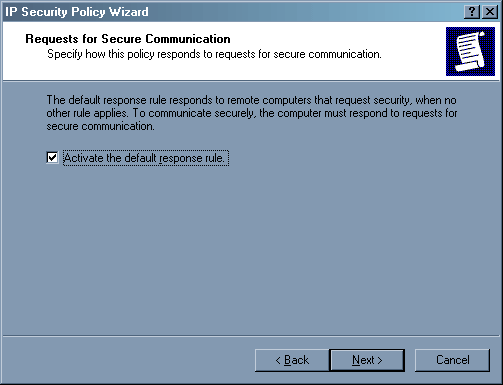
Во втором окне оставьте галочку.
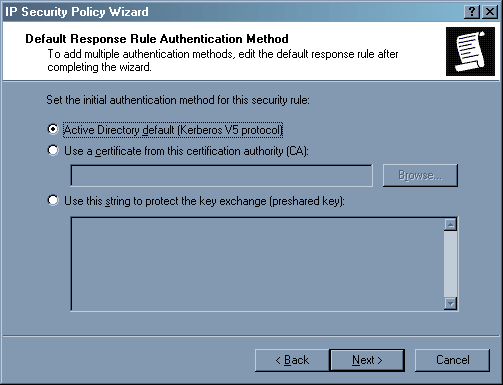
Здесь тоже ничего не трогайте, пусть все будет по умолчанию.
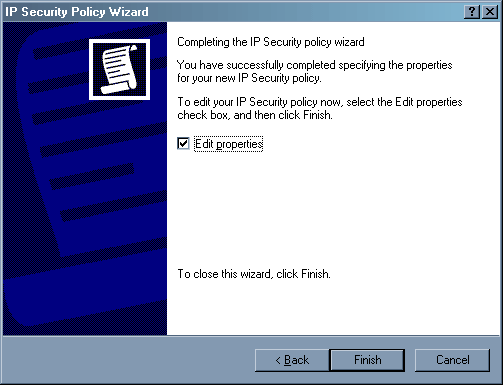
Здесь снимаем галочку – свойства политики мы отредактируем чуть позднее. Теперь в списке политики мы наблюдаем нашу. Нажимаем правую клавишу мыши на «IP security policies…», выбираем «Manage IP filter lists and filter actions…», переходим в закладку «Manage Filter Actions».
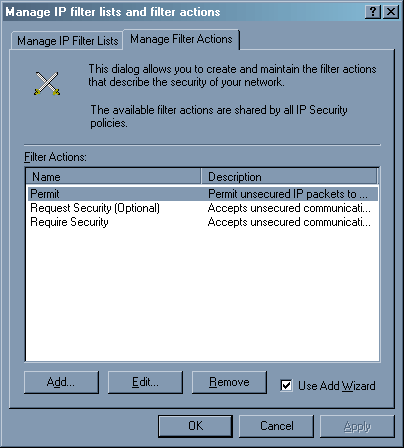
Нажимаем клавишу Add – нам нужно добавить действие «Deny». Вновь запускается мастер.
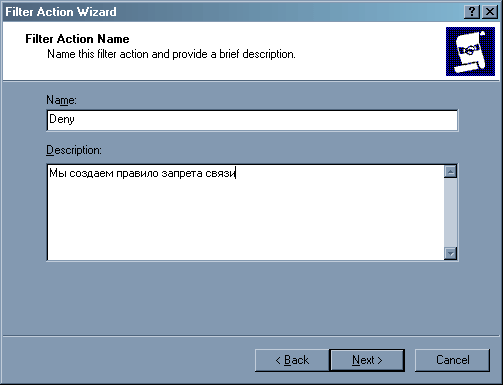
Во втором окне мы выбираем действие – «Block».
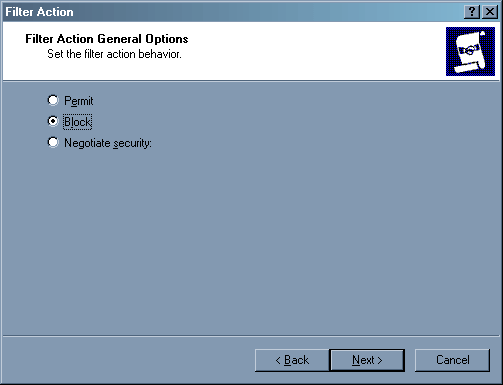
Первое правило – все, что не разрешено, должно быть запрещено. Наш подход будет следующий – мы запретим связь со всеми узлами, а потом будем потихоньку открывать то, что нам нужно. В последнем окне нажимаем клавишу «Finish», галочку «Edit Properties» помечать не нужно.
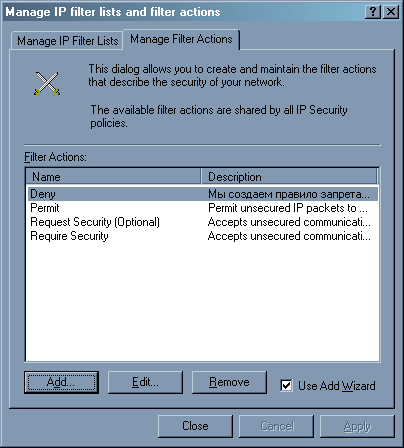
В окне действий появилось наше – «Deny». Закрываем окно и переходим к редактированию созданной нами политики (для этого достаточно нажать два раза левой клавишей мыши на ее название).
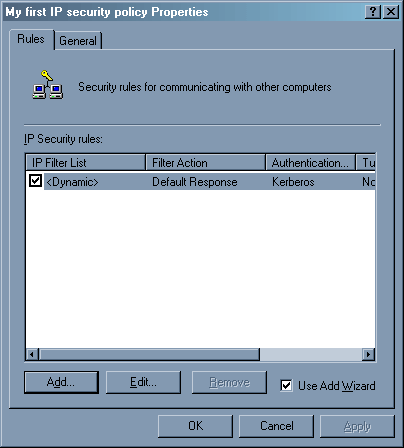
Нажимаем клавишу «Add». Сейчас мы будем изменять нашу политику. Запустится мастер.
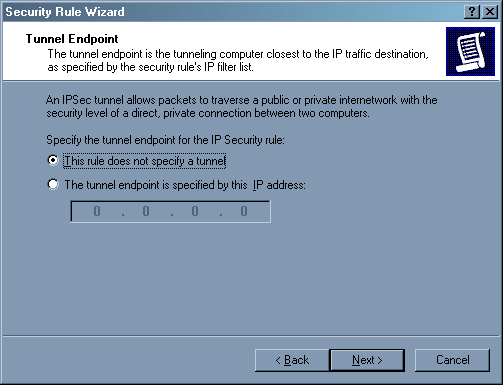
Туннель нам не нужен – нажимаем «Next».
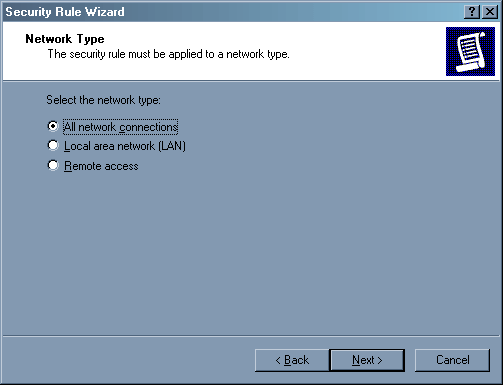
Здесь указывается, для какого соединения будет действовать правило. Если внутренняя сеть у вас имеет «левые» IP адреса, то можете сильно не мучаться и указать «All network connections», мы обеспечим доступ с внутренней сети отдельной строкой. Если выделенка у вас подключена через удаленный доступ, то можете выбрать «Remote Access», но опять же, если у вас есть несколько модемов для доступа клиентов сети к серверу по телефону, то это правило будет действовать и на них, что не всегда полезно. Так что указывайте «All network connections» и не мучайтесь.
Здесь все оставляем по умолчанию.
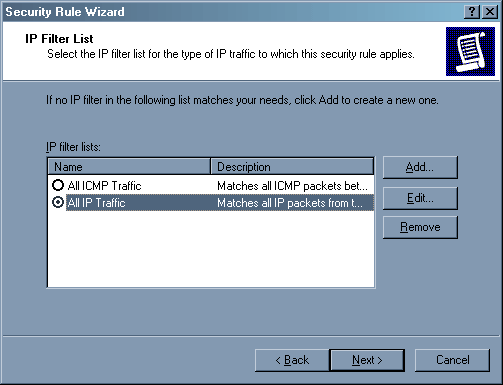
Первое что мы должны сделать – запретить все для всех. Поэтому нажимаем клавишу Add – будем добавлять фильтр. Запустится опять же мастер добавления фильтра (то же самое вы можете сделать через строчку «Manage IP filters list», нажав правую клавишу мыши на «IP security policies…» в окне «Local security settings»).
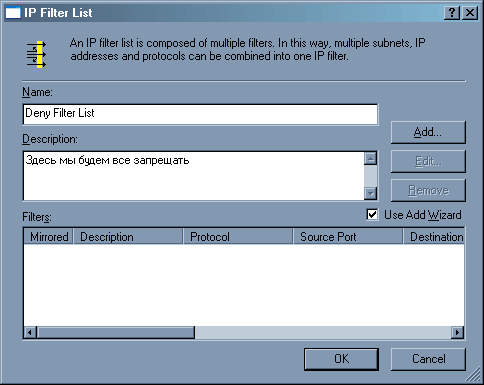
Называем фильтр «Deny Filter List» и нажимаем клавишу «Add». Вновь запускается мастер (они вам еще не надоели?).
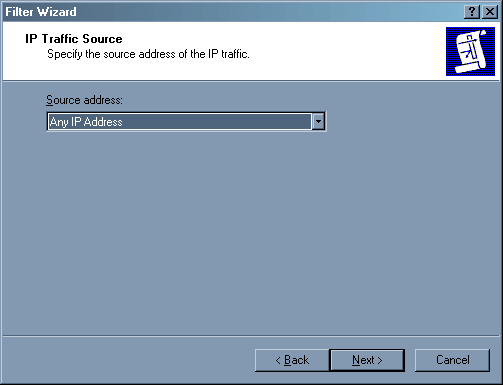
Здесь указывается источник пакета. Поскольку мы хотим запретить пакеты от всех источников, то указываем «Any IP address».
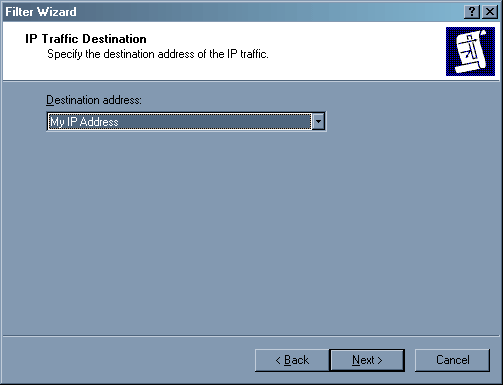
Здесь указывается адрес получателя пакета. Опять же, мы хотим запретить пакеты от всех IP источников для нашего компьютера, поэтому указываем «My IP address».
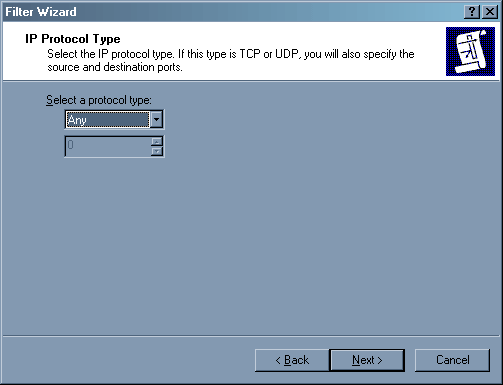
Мы запрещаем все протоколы – выбираем «Any».
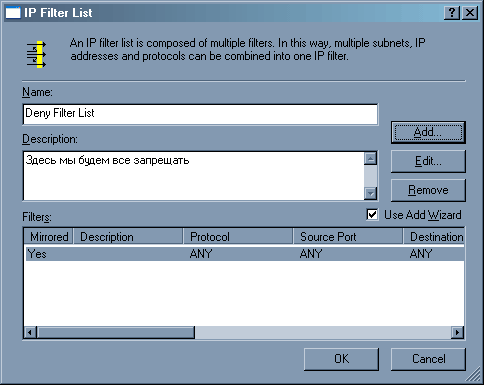
Готово – появился новый фильтр. Прекрасно, теперь нажимаем клавишу «Ok».
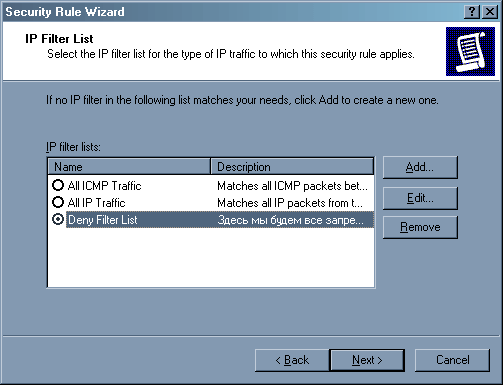
Появился новый список фильтров. Нажимаем «Next».
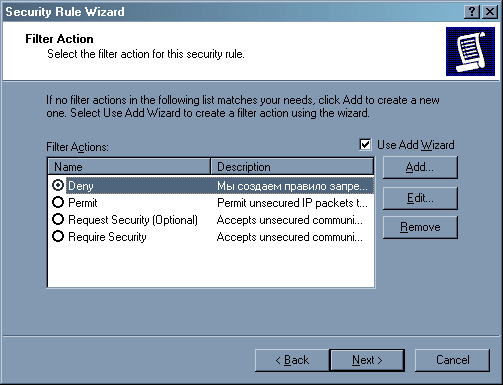
Выбираем действие – «Deny».
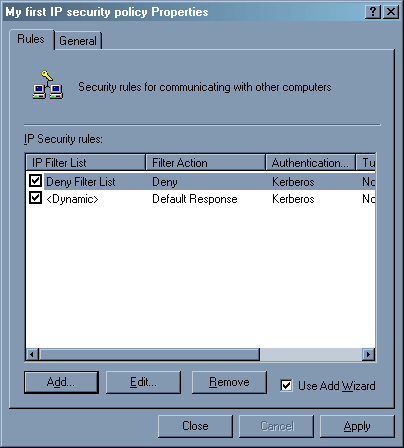
В политике появилось новое правило – запрещение всего от всех и для всех. Теперь будем разрешать. Это, пожалуй, самая трудоемкая задача.
Первоначально следует разрешить ICMP трафик от всех пользователей на нашу машину. Для этого выполним ту же операцию «Add» в окне политики, только теперь мы воспользуемся готовым списком фильтров «All ICMP traffic».
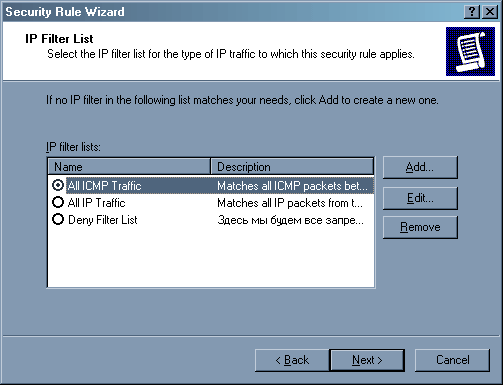
Данный фильтр разрешает ICMP пакеты с любого IP адреса на наш компьютер.
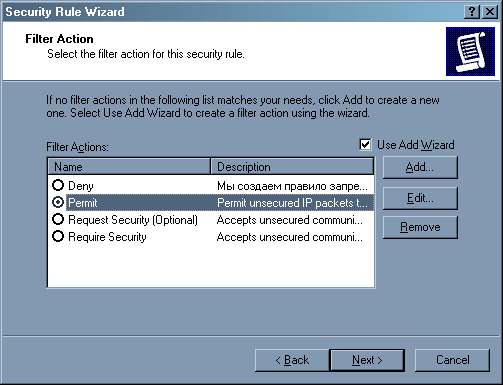
Естественно, что действие теперь будет «Permit».
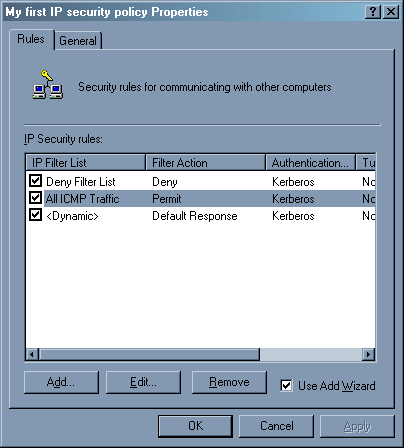
В свойствах политики добавилась еще одна строчка.
Теперь у нас не будет работать ничего, кроме ICMP протокола. Сейчас нам осталось выделить те службы, которые нам нужны, и прописать для них доступ. Лучше всего создать еще один список фильтров (к примеру, «Internet services»), добавить в него несколько строчек фильтров и право «permit». Ниже я дам строчки для самых распространенных служб, но в вашем индивидуальном случае все может быть по-другому. Следует отметить, что по умолчанию каждая служба добавляется зеркально – то есть если мы разрешаем связь от нашего компьютера к любым веб-серверам (порт 80), то будет реализовываться и обратная связь для передачи ответа веб-сервера.
Если у вас есть локальная сеть с «левыми» адресами, то нужно прописать для нее доступ – открываем все протоколы с адресов 192.168.1.0 маска 255.255.255.0 (к примеру) до «My IP address». Для этого можете создать отдельный фильтр «My LAN».
А теперь перейдем к заполнению наиболее часто используемых служб (если у вас есть дополнения, то присылайте их автору (dch@3dnews.ru)).
1. Запросы DNS сервера.
Разрешаем 53 порт получателя (destination port address) протокола UDP от нашего компьютера к любому компьютеру. Вместо любого компьютера можно указать DNS сервер провайдера.
2. Веб-трафик.
Открываем порт TCP 80 получателя от нашего компьютера к любому компьютеру.
3. FTP-трафик.
Открываем порты TCP 20 и TCP 21 получателя от нашего компьютера к любому компьютеру.
4. SMTP трафик (для отправки писем).
Открываем порт TCP 25 получателя от нашего компьютера к любому компьютеру (можно вместо любого компьютера указать SMTP сервер провайдера).
5. POP3 трафик (для приема писем).
Открываем порт TCP 110 получателя от нашего компьютера к любому компьютеру (или к POP3 серверу провайдера).
6. IMAP трафик (для приема писем).
Открываем порт TCP 143 получателя от нашего компьютера к любому компьютеру (или к IMAP серверу провайдера).
7. ICQ трафик.
Зависит от сервера ICQ, обычно TCP порт 5190 получателя от нашего компьютера к любому компьютеру (или к серверу ICQ).
Ну а сейчас пришла пора тестирования – нажимаем правую клавишу мыши на название нашей политики и указываем «Assign».
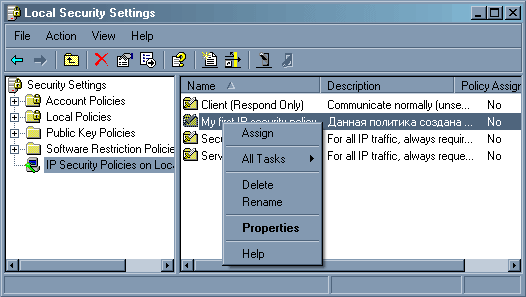
После этого вы можете наслаждаться результатом.
Заключение
После изучения данной статьи вы сможете самостоятельно настроить брандмауэр, используя встроенные в Windows
2000/XP средства безопасности. Брандмауэр позволяет повысить безопасность компьютерной сети и ограничить доступ к службам, которые вы желаете открыть только для внутренней сети. Помните, что главное правило – все что не разрешено, должно быть запрещено.
Дополнение
Доброе время суток…
В целом, задачу можно решить значительно проще:
I. Если сервер используется только для доступа в Интернет (и возможно для хостинга веб)
1.1 Отключаем на «внешнем» интерфейсе биндинг всего кроме TCP/IP
1.2 Включаем ICS(AutoNAT outside)
1.3 смотрим netstat -na
1.4 отключаем ненужные сервисы последовательно
1.5 повторяем 1.3 и 1.4 до отсутствия в 1.3 результате открытых портов на «внешнем» интерфейсе
1.6 наслаждаемся результатом
II. Если сервер используется для MSSQL, 1C, хранения финансовых отчетов и т.п. и к нему подключили Интернет.
1.1 Отключить Интернет от сервера
1.2 Уволить админа
1.3 Поставить отдельный сервер
1.4 Перейти к пункту 1)
III. Лирическое отступление:
Брандмауэры 2-го уровня (не умеющие анализировать содержимое пакетов) и не использующие понятия «внешний» и «внутренний» интерфейс к применению не пригодны (как минимум
сами по себе). Под «внешним» подразумевается интерфейс, подключенный к Интернет и имеющий «реальный» адрес. Встроенный в Win2k/XP данные возможности имеет, но настраивается намного сложнее, чем любой другой. В тоже время, существует достаточное число внешних продуктов, который распостраняются бесплатно (либо условно-бесплатно) и обладают значительно более удобным интерфейсом, а в отдельных случаях (Conseal PC firewall) и гораздо более правильной реализацией. К сожалению, на данный момент, на рынке отсутствуют продукты, которые могли бы создавать приемлемую Security Policy автоматически. Таким образом, для среднего пользователя Сети Интернет, большинство из продуктов либо не дадут результата, либо будут препятствовать работе. Не говоря о том, что обойти брандмауэр 2-го уровня довольно просто. Для этого даже не надо знать как оно работает, — уже существуют готовые программы для spoofing (IP and MAC). Приведенный в статье пример настройки вообще не содержит упоминаний о применении правил к интерфейсам, а так же того, что для разных интерфейсов (внешнего и внутреннего) необходимы _разные_ правила. Общий же тон статьи может создать впечатление мнимой простоты и ложной защишенности у начинающего пользователя. Что есть неправильно, с моей точки зрения. Опыт работы показывает, что 90% попыток пользователя настроить брандмауэр, основываясь на информации, почерпнутой из указаний «нажать сюда, потом сюда» заканчивается проблемами с доступом в Сеть и звонками пользователя в Службу поддержки провайдера.
Все вышеизложенное является моим личным мнением и никоим образом не является официальным мнением моего работодателя.
Мнение сформировано 7-ю годами администрирования в ISP.
----------- With best, Peter Lavee
Если Вы заметили ошибку — выделите ее мышью и нажмите CTRL+ENTER.
When it comes to cybersecurity, one question that often arises is whether or not older operating systems like Windows 2000 have built-in firewalls. It’s a common misconception that Windows 2000 does not have a firewall, but the reality is quite surprising.
Windows 2000 does indeed come with a basic firewall called Internet Connection Firewall (ICF). While it may not have all the advanced features of modern firewalls, it still provides a level of security by blocking unwanted incoming traffic from the internet. So, if you’re still using Windows 2000, it’s important to know that you have some level of protection against potential threats.
Yes, Windows 2000 does have a built-in firewall called Internet Connection Firewall (ICF). It provides basic protection against unauthorized access to your computer by filtering incoming and outgoing network traffic. However, it lacks advanced features like application-based filtering and advanced packet inspection. For enhanced security, it is recommended to use a third-party firewall solution.

Introduction: Windows 2000 Firewall
Windows 2000, released in February 2000, is an operating system developed by Microsoft. During its time, it was one of the most popular operating systems used by individuals and businesses alike. With the constant threat of cyberattacks and the importance of data security, one might wonder if Windows 2000 had a built-in firewall to protect against network vulnerabilities. In this article, we will explore the presence of a firewall in Windows 2000 and its capabilities in safeguarding the system.
Understanding Firewall Technology
Before diving into whether Windows 2000 has a firewall or not, let’s understand what a firewall is and how it functions. A firewall is a network security device that monitors incoming and outgoing network traffic based on predetermined security rules. Its primary purpose is to act as a barrier between internal networks and external networks, such as the internet, to prevent unauthorized access and potential threats.
Firewalls can work in different ways, but the most common ones are packet-filtering firewalls and application-level gateways (ALGs) or proxies. Packet-filtering firewalls examine the headers and content of network packets to determine whether they should be allowed or blocked based on preconfigured rules. ALGs, on the other hand, inspect the data at the application layer and can make more informed decisions about which traffic to allow or block.
Now that we have a basic understanding of firewalls, we can explore whether Windows 2000 has such capabilities.
Windows 2000 and the Lack of a Built-in Firewall
Unfortunately, Windows 2000 does not come with a built-in firewall. At the time of its release, the concept of firewalls was gaining traction, but it was not a standard feature in operating systems. Windows 2000 primarily focused on providing a robust and stable platform for businesses and individuals to carry out their computing needs.
However, despite the lack of a built-in firewall, there were external firewall solutions available in the market that could be installed on Windows 2000 systems. These third-party firewall applications provided the necessary network security features to protect against unauthorized access, malware, and other network threats.
It’s worth mentioning that some versions of Windows 2000, such as the Windows 2000 Server family, did include limited firewall capabilities. These firewall features were more oriented towards isolating and securing different network segments within an organization rather than providing comprehensive protection against external threats.
Third-Party Firewall Solutions for Windows 2000
Although Windows 2000 itself did not offer a built-in firewall, there were several third-party firewall solutions available in the market that were compatible with the operating system. These firewall applications provided an additional layer of security for Windows 2000 users, helping safeguard their systems from external threats.
Some popular third-party firewall solutions for Windows 2000 included ZoneAlarm, Norton Personal Firewall, and McAfee Personal Firewall. These software solutions allowed users to define and manage security policies, monitor network activity, and provide essential protection against unauthorized access attempts.
Third-party firewall software played a crucial role in enhancing the security posture of Windows 2000 systems, offering an effective way to protect sensitive data and maintain network integrity.
The Importance of Firewalls in Modern Operating Systems
While Windows 2000 may not have had a built-in firewall, modern operating systems, including Windows, now come equipped with robust firewall capabilities. These firewalls are designed to protect against various network threats, including malware, hacking attempts, and unauthorized access.
Firewall technology has evolved significantly over the years, and modern firewalls now offer advanced features such as intrusion detection and prevention, deep packet inspection, and application-aware filtering. These features provide enhanced protection to both individual users and organizations, helping safeguard valuable assets and data.
In addition to built-in firewalls, there are still numerous third-party firewall solutions available in the market that offer additional layers of security and customization options.
Exploring Different Dimensions of Windows 2000 Firewall
Now that we have explored the absence of a built-in firewall in Windows 2000, let’s delve into different dimensions where firewall technology can be relevant.
The Significance of Firewalls in Network Security
When it comes to network security, firewalls play a crucial role in protecting networks against unauthorized access and potential threats. The presence of a firewall adds an additional layer of defense, acting as a barrier between internal networks and the outside world.
Firewalls can help prevent unauthorized access, block malicious traffic, and detect and mitigate potential attacks. By carefully configuring firewall rules and policies, network administrators can enhance the security posture of their systems and reduce the risk of security breaches.
Firewalls are particularly important for organizations that handle sensitive data, such as personally identifiable information (PII) or financial records. They create a barrier that can help prevent data breaches, keeping sensitive information protected from unauthorized individuals or organizations.
Types of Firewalls: Packet-Filtering and Application-Level Gateways
Firewalls can be classified into different types based on their working mechanisms and capabilities. Two common types of firewalls are packet-filtering firewalls and application-level gateways (ALGs).
Packet-filtering firewalls examine the headers and content of network packets and make decisions on whether to allow or block them based on predefined rules. This type of firewall is often fast and efficient but may not provide granular control over specific applications or protocols.
ALGs, also known as proxies, work at the application layer of the network stack. They can inspect the data within network packets and make more informed decisions about which traffic to allow or block. ALGs offer more advanced filtering capabilities and can provide tighter security controls.
Organizations should carefully consider their network security requirements and choose the appropriate type of firewall that aligns with their needs.
Implementing Firewalls in a Multi-Layered Security Approach
Firewalls are just one component of a comprehensive security strategy. To establish a robust security posture, organizations should adopt a multi-layered security approach that includes various security measures, such as antivirus software, intrusion detection and prevention systems (IDPS), and secure network configurations.
By integrating firewalls with other security solutions, organizations can create a strong defense against potential threats. Firewalls can work in conjunction with IDPS to detect and prevent malicious activities, while antivirus software can scan for and eliminate known malware.
Additionally, maintaining up-to-date security patches, conducting regular vulnerability assessments, and educating users about best security practices are all essential components of a comprehensive security approach.
The Influence of Firewalls on Compliance and Regulations
Firewalls are not only essential for enhancing network security but also play a significant role in ensuring compliance with industry regulations and standards. Many regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS), require organizations to have firewalls in place as part of their security measures.
Compliance with such regulations is crucial for organizations to maintain the trust of their customers and partners. Failure to meet regulatory requirements could result in severe consequences, including financial penalties, legal complications, and damage to a company’s reputation.
By implementing firewalls and adhering to industry standards, organizations can demonstrate their commitment to data security and protect their digital assets.
Conclusion
Although Windows 2000 did not come with a built-in firewall, it remains an important milestone in the evolution of operating systems and network security. The absence of a built-in firewall led to the popularity of third-party firewall solutions for Windows 2000 users, providing the necessary protection against network vulnerabilities.
Today, firewalls are considered a fundamental component of modern operating systems, including Windows, as they provide a crucial layer of defense against malicious activities and unauthorized access attempts. By deploying firewalls in a multi-layered security approach, organizations can create a robust security posture and protect valuable assets and data from potential threats.
Windows 2000 Firewall: Explained
- Windows 2000 does not have a built-in firewall feature.
- The operating system was released in 2000, before the widespread adoption of firewalls.
- However, third-party firewall software can be used to provide firewall protection on Windows 2000.
In the early 2000s, firewalls were not commonly included in operating systems like Windows 2000. The focus at that time was on network security and protection was mainly provided by external hardware firewalls. Windows 2000 was designed to provide a secure and reliable operating system, but it did not include a built-in firewall feature.
However, users had the option to install third-party firewall software that was compatible with Windows 2000. These software applications provided the necessary firewall protection by monitoring network traffic and blocking potentially harmful connections.
Key Takeaways
- Windows 2000 does have a built-in firewall feature.
- The firewall in Windows 2000 is called Internet Connection Firewall (ICF).
- ICF is designed to protect your computer from unauthorized access.
- You can enable or disable ICF through the Control Panel.
- ICF is not as advanced as modern firewalls and may have limitations.
Frequently Asked Questions
In this section, we will answer some common questions about the presence of a firewall in Windows 2000.
1. Is there a built-in firewall in Windows 2000?
Yes, Windows 2000 does have a built-in firewall called Internet Connection Firewall (ICF).
ICF provides protection against unauthorized access to your computer from the internet. It monitors incoming and outgoing network traffic and allows you to define security settings for different types of connections.
2. How do I enable the firewall in Windows 2000?
To enable ICF in Windows 2000, follow these steps:
- Open the Control Panel.
- Double-click on the «Network and Dial-up Connections» icon.
- Right-click on the network connection that you want to enable the firewall for and select «Properties».
- In the «Properties» window, go to the «Advanced» tab.
- Check the box that says «Protect my computer and network by limiting or preventing access to this computer from the internet».
- Click «OK» to save the changes.
Once enabled, the firewall will start protecting your computer from unauthorized access.
3. What kind of protection does the Windows 2000 firewall provide?
The Windows 2000 firewall provides basic protection by blocking unsolicited incoming traffic from the internet. It helps prevent hackers from gaining access to your computer and compromising your data.
However, it is important to note that the Windows 2000 firewall may not be as robust as modern firewalls available today. It is recommended to use a more advanced third-party firewall solution for enhanced security.
4. Can I customize the firewall settings in Windows 2000?
Yes, you can customize the firewall settings in Windows 2000. You can define specific rules to allow or block certain types of incoming or outgoing network traffic.
To customize the firewall settings, follow these steps:
- Open the Control Panel.
- Double-click on the «Network and Dial-up Connections» icon.
- Right-click on the network connection that the firewall is enabled for and select «Properties».
- In the «Properties» window, go to the «Advanced» tab.
- Click on the «Settings» button under the «Internet Connection Firewall» section.
- In the «Services» tab, you can add or remove specific services that you want to allow or block through the firewall.
- In the «Protocols» tab, you can add or remove specific protocols that you want to allow or block through the firewall.
- Click «OK» to save the changes.
By customizing the firewall settings, you can have more control over the network traffic that is allowed or blocked by the firewall.
5. Can I disable the firewall in Windows 2000?
Yes, you can disable the firewall in Windows 2000, but it is not recommended unless you have another firewall solution in place to protect your computer.
To disable the firewall, follow these steps:
- Open the Control Panel.
- Double-click on the «Network and Dial-up Connections» icon.
- Right-click on the network connection that the firewall is enabled for and select «Properties».
- In the «Properties» window, go to the «Advanced» tab.
- Uncheck the box that says «Protect my computer and network by limiting or preventing access to this computer from the internet».
- Click «OK» to save the changes.
Remember to enable another firewall solution if you choose to disable the Windows 2000 firewall.
I Exposed a Windows 2000 Machine to the Internet… Here’s What Happened
In summary, Windows 2000 does not come with a built-in firewall. This means that if you are using Windows 2000, you will need to implement additional security measures to protect your system from potential threats.
It is important to remember that Windows 2000 is an older operating system and may not have the same level of security features as more recent versions of Windows. Therefore, if you are still using Windows 2000, it is highly recommended to upgrade to a newer operating system that includes a firewall or to install a third-party firewall solution to enhance the security of your system.

A firewall can block network traffic between your computer and other devices.
Microsoft Windows 2000 provides a couple of different built-in methods for controlling inbound network traffic. Many of these methods run as a process or executable under the credentials of a user account (a «user mode» process). TCP/IP filtering, commonly referred to as the «Windows 2000 firewall,» is built in to the lower-level functions of the operating system (a «kernel mode» process). As a kernel-mode process, TCP/IP filtering works regardless of the user logged into the system. However, you cannot easily determine what traffic is being filtered and you may wish to disable the functionality altogether.
Step 1
Log in to the computer with a user account that is a member of the local «Administrators» group.
Step 2
Left-click on «Start,» «Settings» and «Control Panel,» and then double-click «Network and Dial-up Connections.»
Step 3
Right-click the network interface where you wish to disable the firewall (typically your Local Area Connection), and then left-click «Properties.»
Step 4
In the «Components checked are used by this connection» box, left-click «Internet Protocol (TCP/IP)» and then left-click the «Properties» button.
Step 5
In the «Internet Protocol (TCP/IP) Properties» dialogue box, left-click on the «Advanced» button.
Step 6
Left-click the «Options» tab.
Step 7
Left-click on «TCP/IP filtering,» and then left-click the «Properties» button.
Step 8
De-select the «Enable TCP/IP Filtering (All adapters)» check box, and then click «OK» on the «TCP/IP Filtering Properties» box.
Step 9
Click «OK» or «Close» on all the Network Properties windows you’ve just opened. TCP/IP filtering is now disabled.
When it comes to the world of computer security, one question that often arises is whether Windows 2000 has a firewall. It might surprise you to know that Windows 2000 does indeed come with a built-in firewall. This essential security feature provides protection against unauthorized access and helps keep your computer and network safe from potential threats.
The firewall in Windows 2000 acts as a barrier between your computer and the outside world, monitoring incoming and outgoing network traffic. It helps prevent unauthorized access by filtering and blocking potentially harmful data packets. With the Windows 2000 firewall in place, you can have peace of mind knowing that your system is better protected against potential cyber threats.
Yes, Windows 2000 does have a built-in firewall. It is called Internet Connection Firewall (ICF). The ICF helps protect your computer from unauthorized access and potential threats from the internet. It is designed to secure your system by blocking unwanted traffic to and from your computer. However, it is recommended to upgrade to a newer version of Windows, as Windows 2000 is no longer supported by Microsoft and may have security vulnerabilities.

Understanding the Firewall Capabilities of Windows 2000
When it comes to the security of an operating system, a firewall plays a crucial role in protecting it from unauthorized access and malicious attacks. Windows 2000, released by Microsoft in February 2000, is an operating system that is still in use in some organizations. However, many users are skeptical about whether Windows 2000 has a built-in firewall or not. In this article, we will explore the firewall capabilities of Windows 2000 and discuss the various aspects related to its security.
Understanding Firewall Basics
Before diving into the specifics of Windows 2000’s firewall capabilities, it is important to understand the basics of a firewall. A firewall acts as a barrier between a trusted internal network and an untrusted external network, controlling the incoming and outgoing network traffic based on predefined security rules. It monitors the network packets, examines their contents, and blocks or allows them based on the defined ruleset.
A firewall can be either hardware or software-based. Hardware firewalls are typically standalone devices that are placed between the local network and the internet, whereas software firewalls are installed directly on the operating system. Windows 2000 includes a software-based firewall known as the Internet Connection Firewall (ICF), which provides basic network protection.
Now, let’s delve into the specifics of Windows 2000’s built-in firewall and its capabilities.
The Internet Connection Firewall (ICF)
The Internet Connection Firewall (ICF) was introduced in Windows 2000 as a basic firewall solution for home and small office environments. It provides a level of protection against unauthorized access from the internet by filtering incoming network traffic. However, it is important to note that ICF is not enabled by default in Windows 2000 and needs to be manually configured.
ICF operates by inspecting the packets coming from the internet and comparing them against a set of predefined rules. It allows users to define custom rules to allow or block specific types of traffic based on protocols, ports, or IP addresses. By default, ICF blocks all unsolicited inbound traffic, which adds an extra layer of security to the operating system.
While ICF provides basic inbound protection, it does not offer comprehensive outbound protection. This means that outbound network traffic is not filtered by default, allowing any application on the system to connect to the internet without restrictions. It is recommended to use additional security measures like antivirus software and regular patching to ensure the overall security of Windows 2000.
Advanced Firewall Options
For users and organizations requiring more advanced firewall capabilities, Windows 2000 also supports third-party firewall solutions. These solutions offer more granular control over inbound and outbound network traffic and provide features such as application-level filtering, intrusion detection, and virtual private network (VPN) support.
By integrating a third-party firewall solution with Windows 2000, users can enhance the overall security posture of their systems. These solutions often offer centralized management, reporting, and monitoring abilities, giving users greater visibility and control over their network security.
Software Firewalls
Software firewalls are a popular choice for enhancing the security of Windows 2000. They provide an additional layer of protection by offering features such as advanced packet filtering, intrusion prevention, and application-level controls.
Some notable software firewall solutions compatible with Windows 2000 include Norton Internet Security, ZoneAlarm, and Comodo Firewall. These solutions offer customizable security rules, real-time monitoring, and proactive threat detection to safeguard the operating system against evolving cyber threats.
Choosing a software firewall solution depends on the specific requirements and preferences of the user or organization. It is essential to select a reputable and regularly updated firewall solution to ensure optimal protection.
Hardware Firewalls
On the other hand, hardware firewalls are standalone devices that provide network-wide protection. They are typically deployed at the edge of the network, acting as the first line of defense against incoming threats from the internet.
Hardware firewalls offer advanced security features such as deep packet inspection, VPN support, and network address translation (NAT). They are capable of handling high volumes of network traffic and provide centralized management capabilities for network-wide security policies.
Examples of hardware firewall solutions suitable for Windows 2000 environments include Cisco ASA, SonicWall TZ series, and Fortinet FortiGate appliances.
Conclusion
In conclusion, Windows 2000 does have a built-in firewall solution called the Internet Connection Firewall (ICF), which provides basic protection against unauthorized access from the internet. However, ICF is not enabled by default and requires manual configuration. For those in need of more advanced firewall capabilities, third-party software or hardware firewalls can be integrated with Windows 2000 to enhance the overall security of the operating system.
Windows 2000 Firewall: An Important Security Feature
Windows 2000, a popular operating system introduced by Microsoft, does have a built-in firewall. This firewall acts as a protective barrier between your computer and external threats, such as hackers, viruses, and malware. It plays a crucial role in safeguarding your system from unauthorized access and potential risks.
The Windows 2000 firewall provides basic security features that are essential for any computer user. It monitors incoming and outgoing network traffic, filters data packets based on specified rules, and blocks any suspicious or potentially harmful connections. This helps prevent unauthorized access to your computer and ensures that your personal information remains secure.
Although the Windows 2000 firewall is a beneficial security measure, it is important to note that it may not be as robust as the firewalls in more modern operating systems. If you are using Windows 2000, it is advisable to regularly update your operating system and install the latest security patches to enhance the effectiveness of the firewall and protect your system from new threats.
Key Takeaways:
- Yes, Windows 2000 has a built-in firewall.
- The firewall in Windows 2000 is called Internet Connection Firewall (ICF).
- ICF provides basic protection by blocking unauthorized access to your computer.
- ICF does not provide advanced features like application-level filtering.
- You can enable or disable ICF through the Windows 2000 Control Panel.
Frequently Asked Questions
In this section, we will address some common questions regarding the presence of a firewall in Windows 2000.
1. Is there a built-in firewall in Windows 2000?
No, Windows 2000 does not have a built-in firewall feature. Unlike its successors, such as Windows XP and later versions, Windows 2000 does not come with a native firewall solution.
However, third-party firewall applications can be installed and used on Windows 2000 to enhance its security and protect the system from unauthorized access.
2. What are the alternatives for a firewall in Windows 2000?
If you are using Windows 2000 and want to add a firewall for protection, there are various third-party firewall applications available in the market. Some popular choices include ZoneAlarm, Norton Personal Firewall, and McAfee Personal Firewall.
These applications provide similar functionalities to native firewalls and can help safeguard your Windows 2000 system from unauthorized access and network threats.
3. Why doesn’t Windows 2000 have a built-in firewall?
Windows 2000 was released before the concept of built-in firewalls became widespread. During that time, firewalls were often considered separate security measures and were not integrated into operating systems by default.
It was only with the release of Windows XP and subsequent versions that Microsoft started including a built-in firewall as a standard security feature.
4. Is it safe to use Windows 2000 without a firewall?
No, it is not safe to use Windows 2000 without a firewall, especially if you are connected to the internet or a network with external access. Without a firewall, your system is more vulnerable to unauthorized access, malware attacks, and other security threats.
It is highly recommended to install and enable a third-party firewall to protect your Windows 2000 system from potential risks.
5. How do I install a third-party firewall on Windows 2000?
To install a third-party firewall on Windows 2000, follow these steps:
1. Research and choose a reliable third-party firewall application.
2. Download the installation file from the official website of the firewall provider.
3. Run the installation file and follow the on-screen instructions to install the firewall application.
4. Once installed, configure the firewall settings according to your preferences and security requirements.
5. Regularly update the firewall software to ensure it remains effective against the latest threats.
In summary, Windows 2000 does not have a built-in firewall. This means that users need to take extra precautions to protect their system from unauthorized access and potential security threats.
However, it is possible to install a third-party firewall software on Windows 2000 to enhance the system’s security. These firewall programs can provide advanced protection by monitoring and filtering network traffic entering and leaving the computer, helping to prevent unauthorized access and malicious attacks.
-
-
#1
OK, I know Windows 2000 is not vintage, but it is unsupported by its vendor, which is something. :lookroun:
I happen to use Windows 2000 as my main OS in my main home PC workstation, and I am happy with it. I use the server version, which I run as a standard non-privileged user, and I RDP to localhost as Administrator whenever some administrative task is required — by that precaution alone I’m already opting-out of 90% of Windows viruses and malware.
The problem, in my view, is that Windows 2000 is no longer receiving security patches from Microsoft, so I am vulnerable through the LAN connection (not that there is malware in my LAN that I know of, but a guest with a laptop could ruin my W2k machine, and that would be bad).
So I think it’s time for me to install a software firewall in my Windows 2000 machine, to protect it from eventual threats which may pop up in my local ethernet network. In my XP laptop I use the built-in Windows firewall, which I find to be exactly what I need and I like it (it’s light on resources, non-obtrusive, maintenance-free, and it just works).
However, a software firewall needs to install a packet filter in the form of a windows driver, running in kernel space, and it is therefore a «delicate» piece of software which can potentially destabilize the whole system. So I need advise and I would like to hear people’s experiences with software firewall products compatible with W2K, to choose wisely.
My preference would be a firewall-only product (no antivirus or extra functionality), which is light in resources and the more stable the better.
For Windows 2000, I know of ZoneAlarm, which has a mixed reputation: it works, but it is also known to cause BSOD sometimes. I use this machine daily and I have not had a BSOD since about 2005 (and then I exchanged the stock PSU for a expensive brand one, and no BSODs since then).
What do you, fellow forum members, recommend as a software firewall for Windows 2000?
Last edited:
-
-
#2
I used ZoneAlarm back in the day. There are a lot of versions though I remember that.
-
-
#3
Well, I have been using Tiny Personal Firewall for years with no ill effects. You can find the last freeware vesion here
At that link is a comment about Kerio and Tiny being one and the same, with a link to a later last free version of Kerio. I think the free version of Tiny is 2.0.15 and the Kerio says it’s 2.15 so they may be the same.
-
-
#4
ZoneAlarm used to be good but in the later versions I used it screwed up so many things my tech friends and I all stopped using it. Just became bloated and unstable. I’m heard good things about Tiny Personal Firewall. I actually liked BlackIce back in the day but that wasn’t free.
What are you trying to stop though? Is your system connected directly to the internet and hosting things/open or is it just a workstation behind another firewall/router and mostly protected anyway? The average true firewall only protects you from the network traffic connections, not necessarily the content. That’s a some what large misunderstanding of what they do and a false sense of security. A firewall configured to allow server traffic through (whether http, ftp, etc) just allows it no matter the content or attack inside. If you’re looking for a content based firewall then you’re really looking for more of an IDS/Intrusion Detect (or Prevention) System. That will scan the packets for known signatures of attacks or malicious payloads and either alert you iDs or drop the packet iPs.
For the most part just having one of the all in one routers (firewall, switch, router combo) between your system and your modem/high speed internet is good enough for a firewall for port blocking/masking your internal systems.
The more advanced and better option but more resources intensive would be building yourself a nice router/firewall computer to filter the traffic.
The software you might be able to use also to detect packets could be Snort, there’s also a product/port (this has been years ago .. I don’t know the latest development status) called snort in-line which is the IPS version (actively blocks things it thinks are attacks).
I guess the main thing to remember (and you’re probably a tech so my apologies for probably preaching to the choir) but you can’t secure a system from the user. No matter how good your security applications are, it won’t protect someone that connects to a website or clicks «yes» on any software pop-ups on the net 
-
-
#5
One of the problems with Windows/2000 is that you don’t know what the security holes are.
For example there is a disclosed security hole in the RDP protocol (which you use) in almost all later versions of Windows. As Microsoft no longer publish details of security holes in Windows/2000 you don’t know if its there or not. I would assume it is, so how is your fire wall going to help as you have the RDP ports open.
-
-
#6
Actually barythrin hit the nail on the head. If you’re sitting behind a router that has NAT turned on (which 99.999% of them do), then you don’t need a firewall on your local PC to protect you from the internet. A firewall in that situation would only be pertinent if you’re afraid of other devices/people on YOUR network trying to get into the PC or if you’re trying to control outbound connection.
-
-
#7
Give Tiny or Kario a shot. I dumped Zonealarm for Kario at one point in another life.
Last edited:
-
-
#9
Actually barythrin hit the nail on the head. If you’re sitting behind a router that has NAT turned on (which 99.999% of them do), then you don’t need a firewall on your local PC to protect you from the internet. A firewall in that situation would only be pertinent if you’re afraid of other devices/people on YOUR network trying to get into the PC or if you’re trying to control outbound connection.
I am looking for replicating in Windows 2000 the built-in Windows-firewall experience of Windows XP . I don’t want to scan/block incoming «content», I just want to block network access to several ports/services my Windows 2000 machine has open by default.
Yes, I’m behind a NAT router which acts as a firewall keeping my Windows 2000 machine out of reach from the public Internet. But as I said, a guest with an infected laptop hooked up to my LAN could ruin my Windows 2000 machine. As a matter of fact, I myself could prepare a «specially crafted» infected Windows laptop which I guarantee would infect any Windows machine in the same LAN segment which is six or more months behind on Windows-updates AND has the built-in Windows-firewall disabled. That is the scenario I want to be protected from (not that I expect nasty guests at home, but you know the sorry state in which non-techies keep their Windows laptops they use to carry around, don’t you?).
One of the problems with Windows/2000 is that you don’t know what the security holes are.
For example there is a disclosed security hole in the RDP protocol (which you use) in almost all later versions of Windows. As Microsoft no longer publish details of security holes in Windows/2000 you don’t know if its there or not. I would assume it is, so how is your fire wall going to help as you have the RDP ports open.
I am worried about remote root exploits in Windows 2000, that’s what I want the personal software firewall for. My Windows 2000 only allows RDP connections from administrative users (it is not deployed as a full-fledged terminal server) and I very much doubt that you can exploit RDP without first successfully login in through terminal services — the vulnerability in RDP most probably is that a sniffer could impersonate or man-in-the-middle an ongoing RDP connection; and that requires much more sophistication and determination on the part of the attacker than a casual infected laptop from a guest connected to your home LAN.
-
-
#10
ISA Server is a full fledged product which turns a Windows 2000 Server installation into a firewall appliance. That’s not a personal software firewall a-la Windows XP.
-
-
#11
Well, I have been using Tiny Personal Firewall for years with no ill effects. You can find the last freeware vesion here
At that link is a comment about Kerio and Tiny being one and the same, with a link to a later last free version of Kerio. I think the free version of Tiny is 2.0.15 and the Kerio says it’s 2.15 so they may be the same.
Thanks a lot for the pointers. I’ve downloaded both Tiny 2.0 and Kerio 2.15. I will try them as soon as I have done a full system backup of my Windows 2000 machine.
-
-
#13
I guess the main thing to remember (and you’re probably a tech so my apologies for probably preaching to the choir) but you can’t secure a system from the user. No matter how good your security applications are, it won’t protect someone that connects to a website or clicks «yes» on any software pop-ups on the net
It’s tough to figure out how a good product for something like say a grandmother on the internet.
Well, if the system is up-to-date with security updates (in order to be protected against root exploits), and the user is running with least-privilege then you can secure the system from the user. You cannot secure the user’s *profile* from the user, but the *system* will most likely stay secured (barring an unpatched local root exploit, of course).
-
-
#14
I used ZoneAlarm with Windows 2000 from about 2004 right up until I switched to Windows 7 six months ago. I can’t recall ever having a problem with it. It’s simple and unobtrusive, and the way it handles per-program internet access is very nice.
Version 7.0.483 is the last one that works on Windows 2000 (download it from oldversion.com), but anything from 6.1 on is good.
-
-
#16
I very much doubt that you can exploit RDP without first successfully login in through terminal services — the vulnerability in RDP most probably is that a sniffer could impersonate or man-in-the-middle an ongoing RDP connection; and that requires much more sophistication and determination on the part of the attacker than a casual infected laptop from a guest connected to your home LAN.
It looks from :-
http://thehackernews.com/2012/03/poc-windows-rdp-vulnerability-exploit.html
thats its a fully flesge gaping exploitable hole, requiring no logon or authentication…
-
-
#17
It looks from :-
http://thehackernews.com/2012/03/poc-windows-rdp-vulnerability-exploit.html
thats its a fully flesge gaping exploitable hole, requiring no logon or authentication…
The hacker who made the vulnerability public only managed to BSOD the vulnerable remote Windows machines. He hinted at the possibility of a remote root exploit, but his proof of concept did no such a thing, but only a Denial-Of-Service type of attack.
The words of the hacker: http://aluigi.org/adv/termdd_1-adv.txt
The DoS attack in action: http://www.youtube.com/watch?v=DjKFP9KEeUA
«We continue to watch the threat landscape and we are not aware of public proof-of-concept code that results in remote code execution»: http://blogs.technet.com/b/msrc/archive/2012/03/16/proof-of-concept-code-available-for-ms12-020.aspx
It’s a serious problem, nonetheless, for Windows 2000.
—
Edit to add: Oh, damnit! —> «A remote code execution vulnerability exists in the way that the Remote Desktop Protocol accesses an object in memory that has been improperly initialized or has been deleted. An attacker who successfully exploited this vulnerability could run arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.» And: «For systems running supported editions of Windows XP and Windows Server 2003, a remote unauthenticated attacker could exploit this vulnerability by sending a sequence of specially crafted RDP packets to the target system.»
A truly remote root exploit, then: http://technet.microsoft.com/en-us/security/bulletin/ms12-020
Last edited:
-
-
#18
The problem is that you still don’t KNOW if either of the above apply to Windows/2000. Because its no longer supported Microsoft doesn’t report discovered security holes, and you can’t patch them. Whilst there are not many folks using Windows/2000 there are many more on XP. Ealier this year we had this from Microsoft:-
In a blog posting from Easter Monday, Microsoftie Stella Chernyak reminded everyone that in regard to Windows XP (all versions) and Office 2003 (all versions and modules), «on April 8, 2014, we will officially end support for these versions of Windows and Office.»
so in under two years time on my 36th wedding aniversary Windows/XP this laptop will become totally unsupported. I wonder how many XP systems will still be in use then. I expect many more than there ever were Windows/2000 desktops….
-
-
#19
The problem is that you still don’t KNOW if either of the above apply to Windows/2000. Because its no longer supported Microsoft doesn’t report discovered security holes, and you can’t patch them.
There is no official word from Microsoft linking that vulnerability to W2k, but it sure is affected.
so in under two years time on my 36th wedding aniversary Windows/XP this laptop will become totally unsupported. I wonder how many XP systems will still be in use then. I expect many more than there ever were Windows/2000 desktops….
I also have WinXP/Office2003 on my work laptop, and for now I refuse to upgrade (it works quite faster than many brand new laptops with Windows 7 and Office 2007 and multigigabytes of RAM).
—
Going back to my Windows 2000 workstation, these are the ports I have open in it:
(Also, I have two ports open for eMule, and one for BitTorrent (which are the only three ports open to the public Internet through NAT), but I am not running those programs right now.)
The processes which are using those ports are:
tcp/21 —> I have the FTP server «ServUDaemon» running on the W2k system. This will be kept open.
tcp/22 —> I have the SSH server from Cygwin running. This will be kept open.
tcp/135 —> NetBIOS port. This one I probably want it closed.
udp/137 —> NetBIOS port. This one I probably want it closed.
udp/138 —> NetBIOS port. This one I probably want it closed.
tcp/139 —> NetBIOS port. This one I probably want it closed.
tcp/445 —> NetBIOS port. Currently in use from my Linux laptop with the «smbfs» samba client. This will be kept open.
tcp/902 —> VMware Server 1.x remote connection. This one I probably want it closed, but open on the loopback adapter.
tcp/912 —> VMware Server 1.x remote connection. This one I probably want it closed, but open on the loopback adapter.
tcp/1025 —> Microsoft Windows Task Scheduler. This one I probably want it closed, but open on the loopback adapter.
udp/1026 —> that’s the SSH server from Cygwin, again. I don’t know why is it messing with this port, but I will probably keep it as is.
tcp/3052 —> That’s the SQL Server 2000 (MSDE) instance used by Veritas Backup Exec 9.0. This one I probably want it closed, but open on the loopback adapter.
tcp/3210 —> That’s the «Poweroff» program, I used it in the past to be able to do remote shutdowns of the Windows 2000 machine from a Linux host with no GUI. I will uninstall this program, because I now have the SSH server from Cygwin running and that will do its jobs for remote shutdowns.
tcp/3389 —> Remote Desktop service. This will be kept open.
tcp/3527 —> Veritas Backup Exec Server 9.0. I may keep this open to play with it.
tcp/6101 —> Veritas Backup Exec Name Service. I may keep this open to play with it.
tcp/6106 —> Veritas Backup Exec Server 9.0. I may keep this open to play with it.
tcp/10000 —> Veritas Backup Exec Remote Agent. I may keep this open to play with it.
tcp/45925 —> The Administrative GUI console for the FTP server. It’s only listening on the loopback adapter, so everything is fine as it is.
-
-
#20
The problem is that you still don’t KNOW if either of the above apply to Windows/2000. Because its no longer supported Microsoft doesn’t report discovered security holes, and you can’t patch them. Whilst there are not many folks using Windows/2000 there are many more on XP. Ealier this year we had this from Microsoft:-
In a blog posting from Easter Monday, Microsoftie Stella Chernyak reminded everyone that in regard to Windows XP (all versions) and Office 2003 (all versions and modules), «on April 8, 2014, we will officially end support for these versions of Windows and Office.»
so in under two years time on my 36th wedding aniversary Windows/XP this laptop will become totally unsupported. I wonder how many XP systems will still be in use then. I expect many more than there ever were Windows/2000 desktops….
And those folk will probably be using them without many issues at all. Happens with any OS. If folk find it useful and doing whats needed they generally don’t just drop it because MS has officially dropped support for it. It usually puts a lively community into action.
