Recent Windows Operating systems do not reply to ping requests by default. The firewall policy was set to refuse ICMP Echo Requests by default. That means you will be getting ‘Request Timed Out’ from a Windows 10 or Windows 11 PC even though it is connected and set up properly on the network. This same basic network security rule was applied on earlier Operating Systems such as Windows 8.1 and 7 too. This guide shows how to enable ping reply and make your Windows 11/10 desktop or laptop computer respond to ICMP (ping) requests from other network devices.
If the Windows 11/10 computer is in a domain network, then the global domain policy that is related to ICMP echo requests will be applied automatically by your system administrator. In this example, we consider workgroup setup where the domain setup is not available; for example, a small office or your simple home network.
Also, this guide shows how to enable incoming FTP traffic in the Windows 11/10 firewall if you are planning to make your Windows PC an FTP server by using Microsoft IIS or other FTP server programs like FileZilla FTP server.
There is a pre-built firewall rule in Windows 11/10 to enable or disable ICMP echo requests. By default it was disabled. We can enable the rule to allow ping requests in Windows OS which can reply back to other network devices in the local or external network.
To open the rule, go to the control panel by right-clicking on the start button and selecting Control Panel.
In another way, you can search for ‘control’ in Windows 11 search bar.
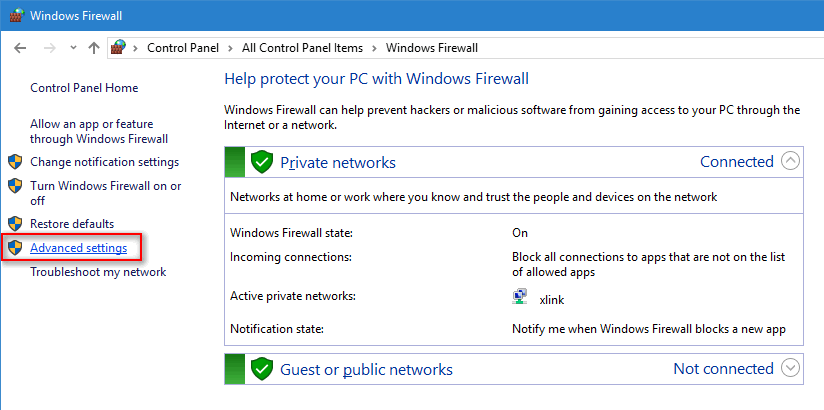
Make sure to change the view to the ‘Large Icon’ in the control panel to access Windows Firewall (or Windows Defender Firewall in Windows 11) settings quickly and easily.
Click on Advanced Settings to get the ICMP rule (incoming and outbound connections) option.
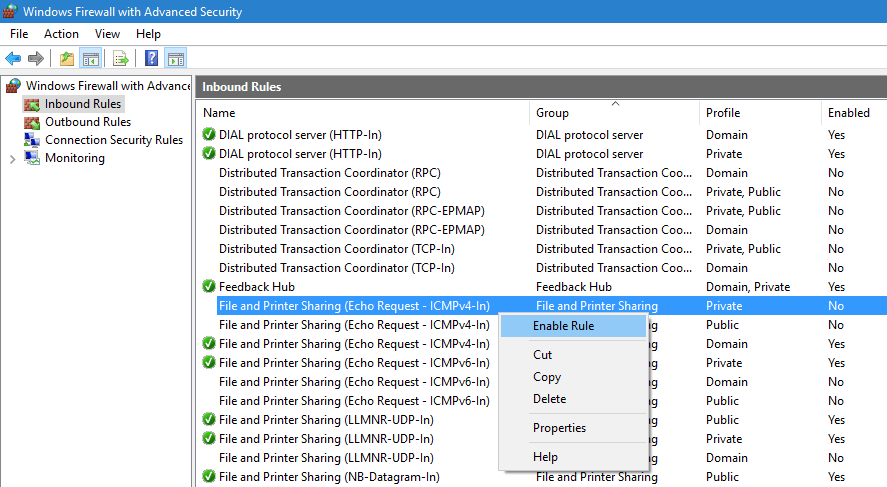
Since we are going to allow incoming ping requests, we need to open the Inbound Rules area and look for the File and Printer Sharing Echo Request –ICMPv4 rule as shown below.
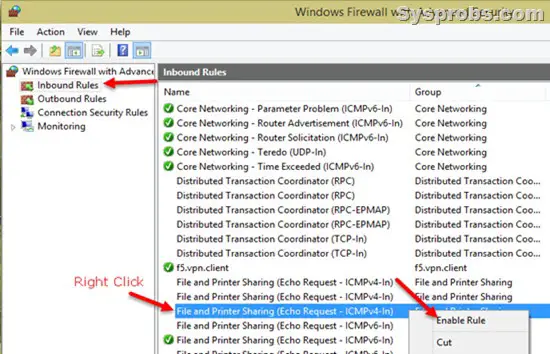
Once you enabled the Echo Request for ICMPv4 which is for IP v4, then your Windows 10 or Windows 11 computer will respond to ping requests.
You will see ‘Private’, ‘Public’ and ‘Domain’ network profiles in the advanced Firewall security settings while enabling or creating rules. Windows OS have each rule for every network profile. You have to enable the only profile which is related to your current connection.
For example, if you are at home or office local network, then the connection mostly will be in ‘Private’ or ‘Domain’ network profile. Therefore enable the Echo Request rule for these profiles only.
If you connect the same laptop to any public Internet network (like a coffee shop or airport Wi-Fi), Windows 11 will treat it as the public network profile. In this case, your computer will not respond to ping requests which come from the Internet to your computer, because the Echo Request rule is not enabled for the ‘Public’ network profile. Hence, it is essential to not enable unwanted firewall rules for public network profile.
Allow Ping Requests in Windows 11 by Command Prompt
You can also allow the Ping (ICMP Echo requests) by using the command prompt. It will modify the firewall rules. Using the command prompt will be handier to do the task quicker than the GUI. Also, it will be useful to execute these commands remotely when you are connected through a command prompt or on the Windows server core versions.
To enable ping requests for IPV4, execute the following command as administrator. Make sure to open the command prompt (CMD) as run as administrator.
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=allowDisable Ping Reply in Windows 10/11:
Visit the same control panel settings and disable the rule (for private or domain network profile). Now the Windows computer will not respond to ping requests from the connected network devices.
Here is the command to disable the ping in the command prompt.
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=blockEnable Incoming FTP Traffic in Windows 11/10/8.1 Firewall
Once you set up an FTP server on a Windows computer, then you must enable inbound FTP traffic in the firewall settings. You can follow the same methods below in Windows 11, even though screenshots are taken on Windows 10.
1) Open the control panel and Windows Firewall.
2) Click on ‘Allow an App or feature through Windows Firewall’. It may have a different option in Windows 8.1 or older versions, but you will find a similar option.
Assuming that you already installed IIS and enabled the FTP server, the firewall settings will automatically detect the FTP server application and list it out in the field.
Click on ‘Change Settings’ and choose ‘FTP Server’. Select the network profile currently the computer is connected, press OK to complete the steps.
3) Another Method: Manually Create The Policy and Allow
If you could not succeed with the above method or are not able to see the FTP server app in the programs list of firewall settings, you can manually create an inbound rule and allow particular FTP ports (20 and 21).
4) In the Control panel Firewall settings, click on Advanced settings.
5) We need to create a new inbound rule to allow FTP traffic. This can be done by allowing particular port numbers in incoming traffic. If you do not have any third party personal firewall programs, this step will ensure that incoming FTP traffic is enabled on the computer even though the Windows firewall is on.
To create a new inbound rule in Windows 10/11 computer, click on Inbound Rules and ‘New Rule’.
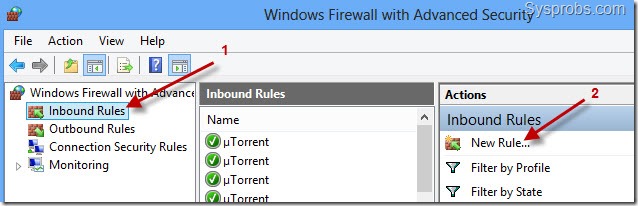
6) Select ‘Port’ as the rule type on the next screen.
7) You can leave ‘TCP’ selected and in ports number enter 20 and 21 (20,21). FTP (File Transfer Protocol) uses port numbers 20 and 21 for data transfer and command control, click here to view more information.
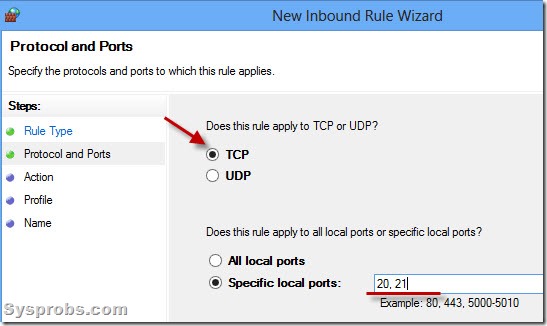

9) Depending on the network connection you are connected to, select the connection type where the particular rule should be applied. You can select all three (Domain, Private and Public) if you are not sure which one to select.
10) Provide a name for the rule, for example, ‘FTP’. This rule name will show under incoming rules in firewall advanced settings. We can easily modify or disable it later by this name.
If you want to block incoming FTP traffic later, you can simply right-click on it and disable the rule.
Also, you can enable the FTP inbound traffic in Windows 10/11 firewall by command prompt with simple commands which are explained at the Microsoft site here.
With the steps outlined in this guide, you will be able to enable ping reply and FTP packets on your Windows 11/10 computer without completely disabling the Firewall.
Echo request (a.k.a. ICMP packets or ping) serves to discover whether or not the network device is present on the network (LAN or WAN). It can be used to ping computers, laptops, servers (including website hosting ones), network printers, routers, etc. However, the ping response should be enabled in advance for the network device to be able to reply. Otherwise, you will get Request timed out instead of response.
Unfortunately the majority of users go and disable Windows Firewall when they want to allow ICMP response to have Ping command working. They forget about the fact that the Firewall protects their PC from hack and malware and it is a must when working in public networks. Here is how to do the right way.
- Press Win+R.
- Type wf.msc.
- Hit Enter:
- Click on the Advanced settings link in the left part of the window:
- Select Inbound Rules in the left pane.
- Enable the rule named: File and printer sharing
Note, that you can allow pings for Private, Public and Domain types of network independently. If you have separate rules preinstalled for each type, enable those you need. Otherwise you can double-click the rule to call its properties, go to the “Advanced” tab and specify network profiles:
Now your PC will respond to ICMP packets when pinged from another device. Just like this:
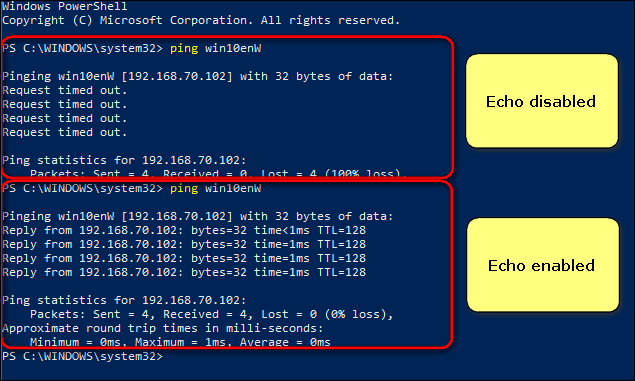
Hope, this will be helpful to you.
By default, the built-in Windows Defender Firewall blocks all inbound ICMP traffic. As a result, if you try to ping the Windows host from a different device, the computer will not respond to the ICMP echo request (with the Request timed out description). In this article, we’ll look at how to enable or disable host network connectivity checks (ICMP echo requests) using the ping command on Windows 10/11 and Windows Server 2022/2019/2016.

You can use the graphical MMC snap-in, the command line, and the PowerShell console to manage the rules of the Windows Firewall. Let’s look at all three ways of enabling and disabling ICMP rules in the firewall.
How to Allow Ping in Windows Firewall
Search for Firewall in the quick search bar and open the Windows Defender Firewall with Advanced Security snap-in (or press Win+R and run the wf.msc command).

Select Inbound Rules in the left pane and find the File and Printer Sharing (Echo Request – ICMPv4-In) rule. As you can see, the rules for both ICMPv4 and ICMPv6 are available here for both the Domain and the Private network profiles. All of these rules are disabled by default.
You can turn on a firewall rule by right-clicking on it and selecting Enable Rule.

You can remotely check the availability of this computer using the ping command. Now Windows Firewall is not blocking ICMP requests and you can see that the remote host is accessible over the network.

By default, this rule allows ICMP echo requests from any source on the local network. If you want to restrict the list of computers that are allowed to send ICMP requests, or allow ICMP ping for external IP addresses, you can edit the existing rules.
- Open the properties of the firewall rule and go to the ‘Scopes’ tab;
- As you can see, the rule allows ICMP replies for all hosts on the Local subnet;
- You can edit the list of accepted IP addresses in Remote IP Address;
- This is where you can add specific IP addresses, ranges of IP addresses, or subnets.
You can enable and disable the Windows Defender firewall rule from the command line.. Open the elevated cmd prompt or PowerShell console. To allow ICMPv4 ping for all network profiles, run the command:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv4-In)" new enable=yes
You should see the following message:
Updated 2 rule(s).
Ok.

You must also enable the ICMP rule for the IPv6 protocol if it is used in your network communications:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv6-In)" new enable=yes
Separate cmdlets for managing Windows Firewall rules are available in the built-in NetSecurity PowerShell module. To allow ICMP ping for all profiles, run the following commands:
Enable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv4-In)" Enable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv6-In)"
Disable ICMP Ping in Windows Firewall
You can disable ICMP echo request rules from the Windows Defender Firewall graphical console. Select all the rules in the list (by holding down the CTLR key), right click and select Disable Rule.

It is also possible to disable the ICMP ping rules from the command prompt:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv4-In)" new enable=no netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv6-In)" new enable=no
Or with PowerShell:
Disable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv4-In)" Disable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv6-In)"
Cyril Kardashevsky
I enjoy technology and developing websites. Since 2012 I’m running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.
By default, the Windows Firewall with Advanced Security blocks ICMP Echo Requests (Pings) from the network. In this post, we will show you how to allow Pings (ICMP Echo requests) through your Windows Firewall using Command Prompt or via the Windows Firewall with Advanced Security UI.
Should I enable ICMP?
For many network administrators, they consider the Internet Control Message Protocol (ICMP) a security risk, and therefore as a security measure, should have ICMP always be blocked at the firewall. In as much as ICMP is widely known to have some security issues associated with it, and for just that reason, ICMP should be blocked; it’s still no reason to block all ICMP traffic!
What ICMP types should I allow?
Apart from Type 3 and Type 4 – the only essential ICMP traffic you need to allow in and out of your firewall on your Windows 10/11 PC, everything else is either optional or should be blocked. Bear in mind that to send ping requests, you need to allow type 8 OUT and type 0 IN.
Generally, the way the ping command works amongst other network tools, is simply by sending special packets known as Internet Control Message Protocol (ICMP) Echo Requests to a target device, and then wait for that receiving device to respond and send back an ICMP Echo Reply packet. This action of pinging, apart from testing whether a network-connected device is active, it also measures the response time and outputs the result for you to review.
We can allow Pings (ICMP Echo requests) through your Firewall on Windows 10 or Windows 11 PC in either of two ways. We’ll explore this topic under the methods outlined below as follows.
Note: If you have a third-party security software with its own firewall installed on your system or just another type of dedicated third-party firewall program installed, you’ll need to open ports in that firewall instead of the in-built Windows Firewall.
1] Allow Pings (ICMP Echo requests) through Firewall on Windows PC via Windows Firewall with Advanced Security UI
To allow Pings (ICMP Echo requests) through Firewall on Windows PC via Windows Firewall with Advanced Security user interface, do the following:
- Click Start or press the Windows key on the keyboard.
- Type windows firewall, and then select Windows Defender Firewall from the top of the search result.
- Click the Advanced settings link on the left side of the Control Panel window that opens.
- In the left pane, right-click Inbound Rules and choose New Rule.
- In the New Inbound Rule window, select Custom.
- Click Next.
- On the Does this rule apply to all programs or specific programs? page, make sure the radio button is selected for All programs.
- Click Next.
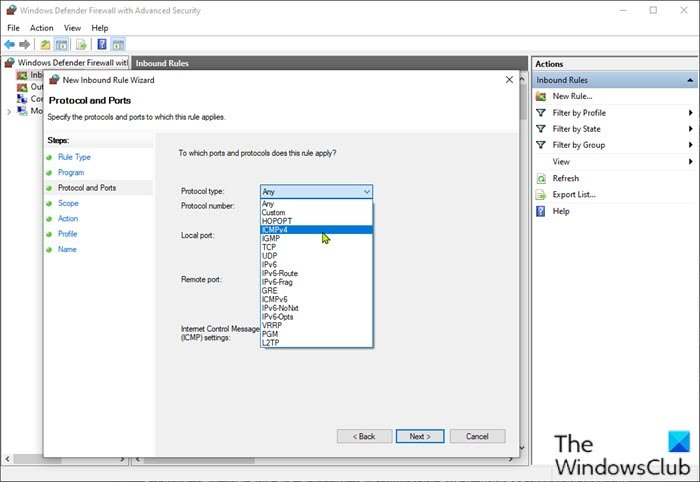
- On the To which ports and protocol does this rule apply? page, click the Protocol type drop-down, and select ICMPv4.
- Click the Customize button.
- In the Customize ICMP Settings window, select the Specific ICMP types option.
- In the list of ICMP types, enable Echo Request.
- Click OK.
- Back on the To which ports and protocol does this rule apply? page, click Next.
- On the page that appears, select the radio button for Any IP address option for under the Which local IP addresses does this rule apply to? and Which remote IP addresses does this rule apply to? sections.
If you want, you can configure specific IP addresses to which your PC will respond to a ping request. Other ping requests are ignored.
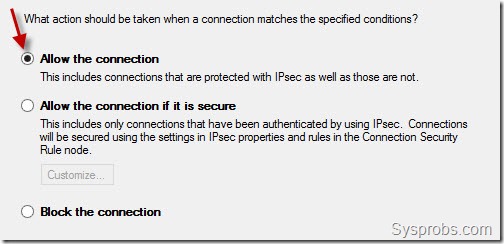
- On the What action should be taken when a connection matches the specified conditions? page, make sure the radio button is selected for Allow the connection option.
- Click Next.
- On the When does this rule apply page, check/uncheck the available options per your requirement.
- Click Next.
- At the final screen, you need to give your new rule a name, and optionally provide a description. It’s recommended to add ICMPv4 to the rule name to differentiate from the ICMPv6 rule that you will create also.
- Click the Finish button.
Now, you can go ahead and create the ICMPv6 rule by repeating the steps above, but this time at the To which ports and protocol does this rule apply? page, click the Protocol type drop-down, and select ICMPv6 instead.
- Exit Windows Defender Firewall when done.
If at anytime you want to disable the rule, open Windows Firewall with Advanced Security Control Panel, select Inbound Rules on the left, and locate the rules you created in the middle pane, right-click the rule and choose Disable. These rules can also be deleted – but it’s best just disabling the rules instead, so you can easily and quickly re-enable them without recreating them.
2] Allow Pings (ICMP Echo requests) through Firewall on Windows PC using Command Prompt
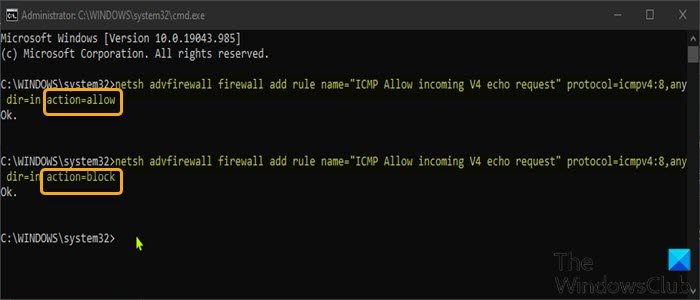
This is the fastest way to create an exception for ping requests on Windows 11/10.
To allow Pings (ICMP Echo requests) through Firewall on Windows PC using Command Prompt, do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type cmd and then press CTRL + SHIFT + ENTER to open Command Prompt in admin/elevated mode.
- In the command prompt window, type or copy and paste the command below and hit Enter to create the ICMPv4 exception.
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=allow
- To create the ICMPv6 exception, run the command below:
netsh advfirewall firewall add rule name="ICMP Allow incoming V6 echo request" protocol=icmpv6:8,any dir=in action=allow
Changes takes effect immediately without system reboot.
- To disable ping requests for the ICMPv4 exception, run the command below:
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=block
- To disable ping requests for the ICMPv6 exception, run the command below:
netsh advfirewall firewall add rule name="ICMP Allow incoming V6 echo request" protocol=icmpv6:8,any dir=in action=block
If at anytime you want to disable a rule but have forgotten the name of the rule, you can run the command below to see a list of all rules:
netsh advfirewall firewall show rule name=all
That’s it on how to allow Pings (ICMP Echo requests) through Windows Firewall!
Read: Unable to Ping IP on Windows 11
What is ICMP attack?
An ICMP attack (also referred to as a Ping flood attack), is a common Denial-of-Service (DoS) attack in which a threat actor maliciously attempts to overwhelm a targeted device with ICMP echo-requests (pings).
Встроенный брандмауэр Windows в целях безопасности по умолчанию блокирует входящий ICMP трафик как в десктопных Windows 10/11, так и в Windows Server. Это означает, что вы не сможете удаленно проверить доступность компьютера с помощью стандартной команды
ping
, т.к. она будет отвечать о превышении интервала ожидания запроса (
Request timed out
) для ICMP Echo-Reply. Если вы хотите сделать возможной проверку доступности хостов Windows по протоколу ICMP из системы мониторинга или вручную из командной строки, можно разрешить ответы на ICMP эхо-запросы.
Чтобы разрешить отправку ответов на запросы по протоколу ICMP, нужно включить предустановленные правила в брандмауэре Windows.
- Откройте оснастку управления Windows Defender Firewall with Advanced Security, выполнив команду
wf.msc - Перейдите в раздел Inbound Rules
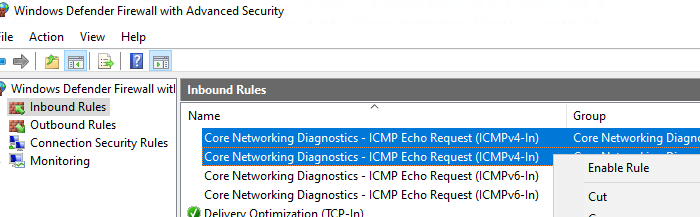
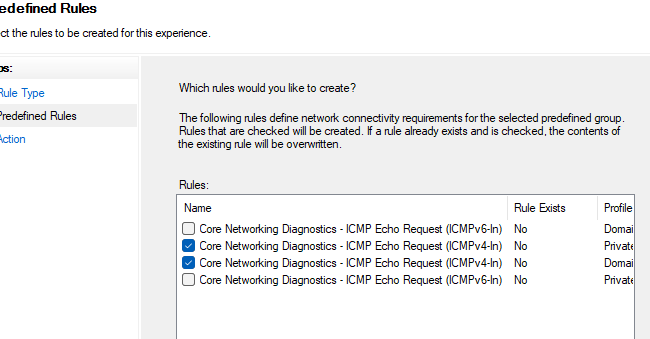
- Найдите правило Core Network Diagnostics – ICMP Echo Request (ICMPv4-In) и включите его.
- В моем случае есть два правила с этим именем. Одно для частного и общедоступного сетевого профиля Windows, и второе для доменного. Я включил их оба. Можно также включить правило, разрешающее ICMP ответы для IPv6 протокола (если используется).
Есть также другое правило File and Printer Sharing (Echo Request – ICMPv4-In), которое также разрешает компьютеру отвечать на эхо-запросы
ping
.
Попробуйте пропиговать ваш компьютер и убедитесь, что теперь он отвечает на ICMP запросы.
Можно включить правила Windows Firewall, разрешающие ответы на эхо-запросы ICMP с помощью такой команды PowerShell:
Set-NetFirewallRule -Name CoreNet-Diag-ICMP4-EchoRequest-In -enabled True
Если нужно ограничить список IP подсетей или хостов, которым разрешено отправлять ответы на ICMP запросы, выполните команду:
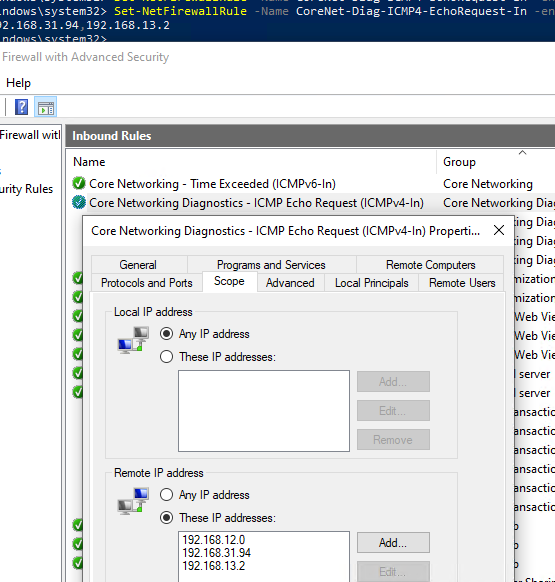
Set-NetFirewallRule -Name CoreNet-Diag-ICMP4-EchoRequest-In -enabled True -RemoteAddress 192.168.12.0,192.168.31.94
Откройте свойства правила в Windows Firewall и проверьте, что теперь правило разрешающие ICMP ответы будет работать только для указанных IP/подсетей.
Если в файрволе отсутствует (удалено) правило для входящих ICMP запросов, можно создать его из командной строки:
netsh advfirewall firewall add rule name="Allow_ICMPv4_Echo" protocol=icmpv4:8,any dir=in action=allow
Другой пример PowerShell команды, которое создаст правило файервола, разрешающего ping для всех хостов в локальной сети:
New-NetFirewallRule -DisplayName "Allow_ICMPv4_Echo" -Direction Inbound -Protocol ICMPv4 -IcmpType 8 -RemoteAddress localsubnet -Action Allow
Если нужно заблокировать ответы на ICMP эхо-запрос независимо от того, какие правила включены, создайте запрещающее правило, которое будет иметь более высокий приоритет:
New-NetFirewallRule -DisplayName "Block_ICMPv4_Echo" -Direction Inbound -Protocol ICMPv4 -IcmpType 8 -RemoteAddress localsubnet -Action Block
Чтобы разрешить ответы на ICMP ping на всех компьютерах в сети, можно включить правило Windows Firewall с помощью доменной групповой политики .
- Откройте редактор доменных GPO (
gpmc.msc
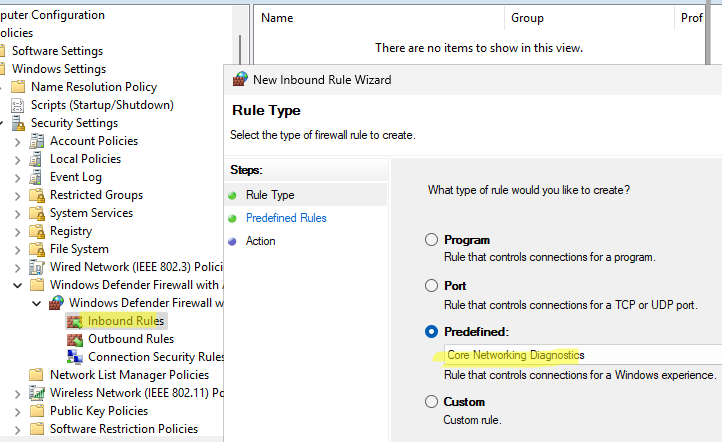
), создайте или отредактируйте имеющуюся GPO и назначьте ее на целевую OU или корень домена. - Перейдите в раздел Computer Configuration -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security -> Inbound rules
- Создайте новое правило, выберите Predefined rule типа Core Networking Diagnostics
- Укажите какие правила ICMP Echo request нужно включить.
- На следующем шаге вы берите Allow the connection.