Cyberly strives to stay free, and we rely on donations to make it possible. If our content has helped you, please consider donating—your contribution helps keep the site running and allows us to keep creating valuable content.
Your support will help keep this knowledge free and accessible to everyone, now and in the future.
Donate Now
Reading Time: 3 minutes
Welcome to Cyberly’s Hydra download page. Hydra, also known as THC-Hydra, is a powerful and versatile tool designed for ethical hacking, penetration testing, and security auditing. It is widely respected in the cybersecurity community for its ability to perform fast and efficient brute force attacks on a variety of protocols and authentication systems. By downloading Hydra, you gain access to a cutting-edge tool that helps identify weak credentials and vulnerabilities, enabling you to secure your systems and networks more effectively.
What is Hydra?
Hydra is an open-source application developed to test login and password security. It supports numerous protocols such as HTTP, HTTPS, SSH, FTP, SMTP, IMAP, POP3, and many more, making it a highly adaptable solution for testing various environments. Its compatibility with diverse authentication mechanisms ensures that you can assess vulnerabilities in web applications, remote services, and network systems alike. With Hydra, ethical hackers can simulate real-world attack scenarios to identify and address potential entry points before malicious actors exploit them.
Features of Hydra
Hydra is packed with features that make it an essential tool for ethical hackers and cybersecurity professionals:
- Protocol Versatility: Supports dozens of protocols, including widely used ones like SSH, RDP, MySQL, and LDAP.
- High-Speed Performance: Employs parallelised connections to perform fast and efficient brute force attacks.
- Customisable Modules: Hydra‘s modular architecture allows users to add custom attack modules for specific use cases.
- Command-Line Interface: Offers advanced users full control over attacks through a straightforward CLI.
- Dictionary and Brute Force Attacks: Supports both dictionary-based and iterative brute force password-cracking techniques.
- Open-Source and Free: Available under the GNU General Public License, Hydra remains accessible to everyone in the ethical hacking community.
Why Use Hydra?
Hydra is designed to expose weak authentication systems by demonstrating the risks associated with poor password hygiene and inadequate security configurations. It helps organisations strengthen their defences by identifying accounts vulnerable to brute force attacks and improving their authentication mechanisms.
For businesses and individuals, Hydra is a wake-up call to adopt best practices, such as enforcing complex password policies, implementing multi-factor authentication (MFA), and continuously monitoring login attempts to detect suspicious activity.
How to Download Hydra
Hydra is an open-source tool available for free download. Follow these simple steps to obtain the latest version of Hydra:
- Visit the official GitHub repository for THC-Hydra: https://github.com/vanhauser-thc/thc-hydra.
- Download the source code or pre-compiled binaries for your operating system.
- Follow the installation instructions provided in the README file to set up Hydra on your system.
Hydra supports multiple operating systems, including Linux, macOS, and Windows, ensuring compatibility with most testing environments.
Important Note
Hydra is a tool intended for ethical hacking and cybersecurity purposes only. Its use is strictly prohibited on systems or networks where you do not have explicit permission to perform security testing. Misuse of Hydra may result in legal consequences. Always adhere to ethical guidelines and legal frameworks when using this tool.
Getting Started with Hydra
Once you have downloaded and installed Hydra, you can begin using it to conduct password security assessments. Familiarise yourself with its command-line options and experiment with different protocols to understand its capabilities. Cyberly recommends using Hydra alongside other penetration testing tools for a comprehensive evaluation of your system’s security.
Support and Resources
If you have any questions about Hydra or need assistance, explore the following resources:
- Documentation: The official GitHub page provides detailed documentation, including examples and usage guides.
- Forums: Join cybersecurity forums and communities to discuss Hydra with other professionals.
- Cyberly Tutorials: Stay tuned to Cyberly for in-depth guides and tutorials on using Hydra effectively.
Conclusion
Hydra is a cornerstone application for anyone serious about ethical hacking and cybersecurity. By identifying and addressing vulnerabilities in authentication systems, it empowers users to build more secure digital environments. Download Hydra today and take the first step towards safeguarding your systems against potential threats.
Download Hydra Now: https://github.com/vanhauser-thc/thc-hydra
Take control of your system’s security with Hydra and Cyberly! Together, we can make the digital world a safer place.
Disclaimer: This post may contain affiliate links. If you make a purchase through one of these links, Cyberly may earn a small commission at no extra cost to you. Your support helps us continue providing free tutorials and content. Thank you!
Skip to content
Navigation Menu
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
Appearance settings
Repository files navigation
THC-HYDRA-windows
Description
The THC-HYDRA tool compiled for Windows
Features
- Latest
9.1version (2020-07-29) - Compiled for
x64only from version 9.1, older releases were compiled forx86so they should work onx86andx64platforms - Compiled with SSH, MySQL, PostgreSQL and RDP optional modules
- Embedded Cygwin DLLs
Usage
- Download the whole archive
- Extract it and run
hydra.exe - Profit
Prerequisites
- Microsoft Visual C++ 2008 Redistributable Package (more info here)
Older versions
- Browse the release section to find some old versions
Disclaimer & licence
The very same as mentioned on https://github.com/vanhauser-thc/thc-hydra.
I don’t own anything on THC brand or hydra, neither am I affiliated or working on the project.
Last but not least, antivirus softwares might report some binaries as hacktools or even malwares: this is a known and common issue. If you don’t trust this compilation, just don’t download it.
Credits
- The Hackers Choice «THC» https://github.com/vanhauser-thc/thc-hydra
THC Hydra — утилита для UNIX-терминала, предназначенная для тестирования безопасности серверов, локальных сетей, веб-приложений. Имеет открытый исходный код, легко компилируется практически под любые актуальные операционные системы. То есть существует также THC Hydra для Windows, Mac OS, Android. Программа включена в базовую сборку Kali Linux. Установка в Kali NetHunter тоже возможна (без GUI).
Возможности программы
Утилита поддерживает проведение взлома через брутфорс (не по хэшу, а именно перебором ключей по словарю). Главное же её преимущество — это поддерживаемые сетевые протоколы. Их более 50, включая Rlogin, RSH, Subversion и даже XMPP. И программа может работать в параллельном режиме, выполняя взлом сразу с нескольких компьютеров (в том числе с задействованием GPU-вычислений) или по нескольким сетевым протоколам одновременно.
Основные возможности приложения:
- доступ к защищенным локальным сетям (как через Ethernet, так и WiFi);
- доступ к LAN по заданному диапазону портов;
- восстановление пароля к зашифрованным файлам/пакетам;
- взлом веб-серверов;
- взлом почтовых сервисов (включая Gmail, с возможностью обхода ограничений по капче);
- составление собственного словаря на основе заданной ключевой фразы.
Также THC Hydra Linux может дистанционно взламывать специфические локальные сети (в которых установлены только игровые консоли или торговые автоматы с дистанционным управлением). Утилита работает через терминал, но для неё выпустили массу неофициальных GUI (самый популярный Xhydra).
Результаты брутфорса можно экспортировать в log-файл. Это позволит выполнить взлом сети в несколько попыток (начинать всё сначала каждый раз не потребуется).
Варианты использования программы
С помощью Hydra можно восстановить забытый пароль к файлу или WiFi. Она работает заметно быстрее других приложений для брутфорса, может задействовать одновременно вычисления как на CPU, так и GPU (обязательно требуется установка проприетарного драйвера последней версии).
Скачать THC Hydra актуальной версии бесплатно можно на нашем сайте.

THC Hydra – это приложение, которое в консольном режиме может производить тестирование на предмет безопасности беспроводных и проводных сетей.
Описание программы
Программа лишена пользовательского интерфейса и работает при помощи командной строки.
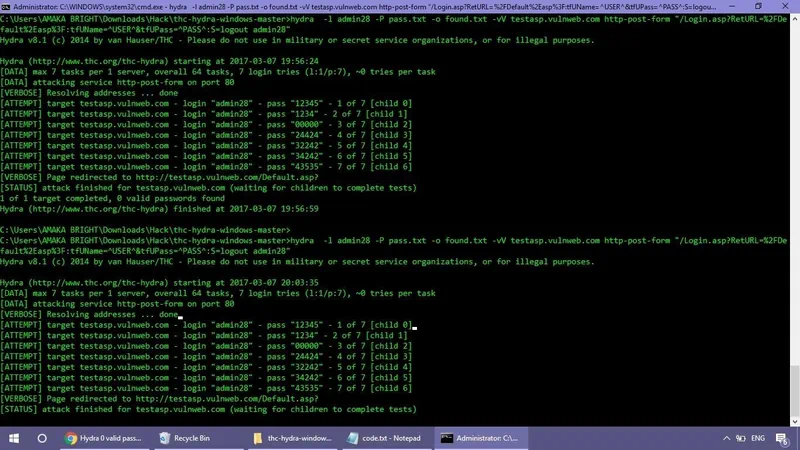
Приложение распространяется на бесплатной основе, соответственно, какая-либо активация не требуется.
Как установить
Установка тоже не нужна. Достаточно скачать приложение, затем запустить его:
- Обращаемся к разделу загрузки и при помощи прямой ссылки производим скачивание.
- Двойным левым кликом запускаем исполняемый файл, который отмечен на прикреплённом ниже скриншоте.
- Если понадобится, утверждаем доступ к полномочиям администратора.
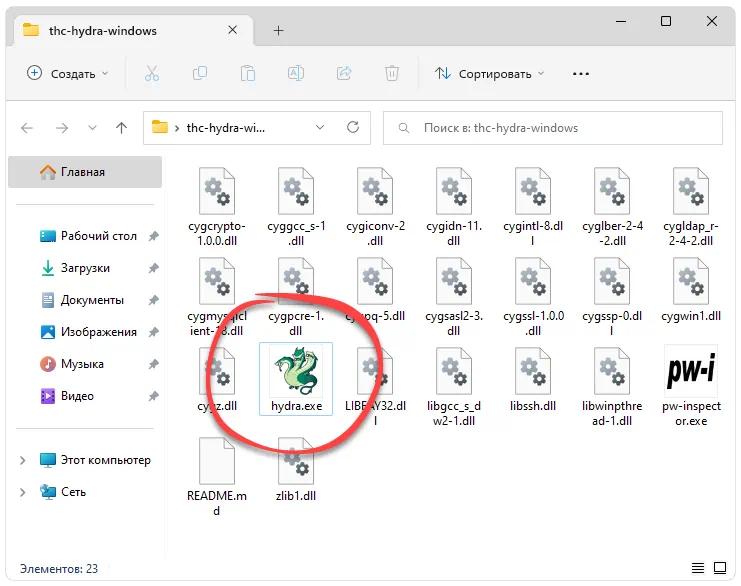
Как пользоваться
Работа с ПО сводится к вводу специальных операторов, а также просмотру полученного результата. Присутствует собственная справка, но лучше всего перейти на YouTube и посмотреть какой-нибудь обучающий ролик по теме.
Достоинства и недостатки
Переходим к разбору сильных, а также слабых сторон приложения для тестирования безопасности сетей.
Плюсы:
- широкий набор возможностей для тестирования безопасности сетей;
- присутствует встроенная справка.
Минусы:
- нет русского языка;
- отсутствует пользовательский интерфейс.
Скачать
Загрузить программу можно при помощи прикрепленной ниже кнопки.
| Язык: | Английский |
| Активация: | Бесплатно |
| Разработчик: | The (Freeworld) Hacker’s Choice |
| Платформа: | Windows XP, 7, 8, 10, 11 |
THC Hydra v8.5
This is the Windows app named thc-hydra whose latest release can be downloaded as hydrav9.2.zip. It can be run online in the free hosting provider OnWorks for workstations.
Download and run online this app named thc-hydra with OnWorks for free.
Follow these instructions in order to run this app:
— 1. Downloaded this application in your PC.
— 2. Enter in our file manager https://www.onworks.net/myfiles.php?username=XXXXX with the username that you want.
— 3. Upload this application in such filemanager.
— 4. Start any OS OnWorks online emulator from this website, but better Windows online emulator.
— 5. From the OnWorks Windows OS you have just started, goto our file manager https://www.onworks.net/myfiles.php?username=XXXXX with the username that you want.
— 6. Download the application and install it.
— 7. Download Wine from your Linux distributions software repositories. Once installed, you can then double-click the app to run them with Wine. You can also try PlayOnLinux, a fancy interface over Wine that will help you install popular Windows programs and games.
Wine is a way to run Windows software on Linux, but with no Windows required. Wine is an open-source Windows compatibility layer that can run Windows programs directly on any Linux desktop. Essentially, Wine is trying to re-implement enough of Windows from scratch so that it can run all those Windows applications without actually needing Windows.
SCREENSHOTS
thc-hydra
DESCRIPTION
Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system. There are already several login hacker tools available, however, none does either support more than one protocol to attack or support parallelized connects. It was tested to compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS. However the module engine for new services is very easy so it won’t take a long time until even more services are supported. Via the command line options you specify which logins to try, which passwords, if SSL should be used, how many parallel tasks to use for attacking, etc. PROTOCOL is the protocol you want to use for attacking, e.g. ftp, smtp, http-get or many others are available.
Features
- For researchers and security consultants
- This tool is for legal purposes only
- It was tested to compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS.
- Currently this tool supports several protocols
- If you want the ssh module, you have to setup libssh (not libssh2!) on your system
- Supports mobile systems based on Linux, MacOS or QNX
Programming Language
C
This is an application that can also be fetched from https://sourceforge.net/projects/thc-hydra.mirror/. It has been hosted in OnWorks in order to be run online in an easiest way from one of our free Operative Systems.
Download Windows & Linux apps
- Linux apps
- Windows apps
-
1
- Eclipse Tomcat Plugin
- The Eclipse Tomcat Plugin provides
simple integration of a tomcat servlet
container for the development of java
web applications. You can join us for
discussio… - Download Eclipse Tomcat Plugin
-
2
- WebTorrent Desktop
- WebTorrent Desktop is for streaming
torrents on Mac, Windows or Linux. It
connects to both BitTorrent and
WebTorrent peers. Now there’s no
need to wait for… - Download WebTorrent Desktop
-
3
- GenX
- GenX is a scientific program to refine
x-ray refelcetivity, neutron
reflectivity and surface x-ray
diffraction data using the differential
evolution algorithm…. - Download GenX
-
4
- pspp4windows
- PSPP is a program for statistical
analysis of sampled data. It is a free
replacement for the proprietary program
SPSS. PSPP has both text-based and
graphical us… - Download pspp4windows
-
5
- Git Extensions
- Git Extensions is a standalone UI tool
for managing Git repositories. It also
integrates with Windows Explorer and
Microsoft Visual Studio
(2015/2017/2019). Th… - Download Git Extensions
-
6
- eSpeak: speech synthesis
- Text to Speech engine for English and
many other languages. Compact size with
clear but artificial pronunciation.
Available as a command-line program with
many … - Download eSpeak: speech synthesis
- More »
Linux commands
-
1
- aarch64-linux-gnu-gdc-5
- gdc — A GCC-based compiler for the D
language … - Run aarch64-linux-gnu-gdc-5
-
2
- aarch64-linux-gnu-gdc
- gdc — A GCC-based compiler for the D
language … - Run aarch64-linux-gnu-gdc
-
3
- crlutil
- crlutil — List, generate, modify, or
delete CRLs within the NSS security
database file(s) and list, create,
modify or delete certificates entries in
a particul… - Run crlutil
-
4
- crm
- Use crm online using onworks.net
services. … - Run crm
-
5
- g.tempfilegrass
- g.tempfile — Creates a temporary file
and prints it�s file name. KEYWORDS:
general, support, scripts … - Run g.tempfilegrass
-
6
- g.versiongrass
- g.version — Displays GRASS GIS version
info. Optionally also prints build or
copyright information. KEYWORDS:
general, support, citing, copyright,
version, lic… - Run g.versiongrass
- More »
