Copilot is your AI companion
Always by your side, ready to support you whenever and wherever you need it.
These spreadsheets list the policy settings for computer and user configurations that are included in the Administrative template files delivered with the Windows operating systems specified. You can configure these policy settings when you edit Group Policy Objects.
Important! Selecting a language below will dynamically change the complete page content to that language.
-
File Name:
Windows10andWindowsServer2016PolicySettings.xlsx
You can use the filtering capabilities that are included in this spreadsheet to view a specific subset of data, based on one value or a combination of values that are available in one or more of the columns. In addition, you can click Custom in the drop-down list of any of the column headings to add additional filtering criteria within that column.
To view a specific subset of data, click the drop-down arrow in the column heading of cells that contain the value or combination of values on which you want to filter, and then click the desired value in the drop-down list. For example, to view policy settings that are available for Windows Server 2012 R2 or Windows 8.1, in the Administrative Template worksheet, click the drop-down arrow next to Supported On, and then click At least Microsoft Windows Server 2012 R2 or Windows 8.1.
What’s New?
The Administrative Template spreadsheet contains three columns that provide more information about each policy setting’s behavior related to reboots, logoffs, and schema extensions. These columns are the following:
- Reboot Required: A «Yes» in this column means that the Windows operating systems requires a restart before it applies the described policy setting.
- Logoff Required: A «Yes» in this column means that the Windows operating system requires the user to log off and log on again before it applies the described policy setting.
- Active Directory Schema or Domain Requirements: A «Yes» in this column means that you must extend the Active Directory schema before you can deploy this policy setting.
- Status: A «New» in this column means that the setting did not exist prior to Windows Server 2012 R2 and Windows 8.1. It does not mean that the setting applies only to Windows Server 2012 R2 and Windows 8.1. Refer to the column entitled «supported on» to determine to which operating system the policy setting applies.
-
Supported Operating Systems
Windows 10, Windows 2000, Windows 2000 Server, Windows 7, Windows 8, Windows 8.1, Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Vista, Windows XP
- Microsoft Excel or Excel Viewer
-
- Click the Download button to start the download.
- Do one of the following:
- To start the installation immediately, click Open.
- To copy the download to your computer for installation at a later time, click Save.
- To cancel the installation, click Cancel.
In this article, I will list all the new Windows 11 22H2 group policy settings and cover the steps to download these settings. Microsoft has released the Group Policy Settings Reference Spreadsheet for Windows 11 2022 Update (22H2) and you can use these policy settings in your setup.
The GPO settings released for Windows 11 22H2 are the files used to expose policy settings when you use the Group Policy Management Console (GPMC) to edit Group Policy Objects (GPOs). The spreadsheet lists all the 80+ Windows 11 22H2 GPO settings for computer and user configurations that are included in the administrative template files (.admx and .adml) delivered with Windows 11, version 22H2.
Microsoft will offer Windows 11 22H2 update for free to eligible Windows 10 and Windows 11 devices. When I say eligible, it means the devices to meet the Windows 11 minimum requirements will be get Windows 11 22H2 upgrade.
There are different methods to upgrade to Windows 11 22H2 and for enterprises, you can use Configuration Manager or Microsoft Intune to move to version 22H2. Have a look at the detailed guide on how to upgrade to Windows 11 version 22H2 using Configuration Manager.
Let’s look at the steps to download the group policy settings reference spreadsheet for Windows 11 (22H2). This spreadsheet shows the policy settings for computer and user configurations that come with Windows 11 2022 Update (22H2) and are part of the Administrative template files. You can configure these policy settings when you edit Group Policy Objects.
Use the following steps to download Group Policy settings reference spreadsheet for Windows 11 22H2:
The file named Windows11andWindowsServer2019PolicySettings–22H2.xlsx is included in the download. You will require Microsoft Excel to open this file and view the data. Check out how to download and install Microsoft Office 2021.
Use the Excel program to access the Windows 11 22H2 Group Policy Settings Reference Spreadsheet. Select the Administrative Templates tab and here we can see a list of new Windows 11 22H2 Group Policy Settings.
The below table lists all the new group policy settings released for Windows 11 22H2 by Microsoft. The table also lists the GPO name along with the policy path and policy description.
| Windows 11 22H2 Group Policy Settings Name | GPO Policy Path | Group Policy Description |
| Hide messages when Windows system requirements are not met | System | This policy controls messages which are shown when Windows is running on a device that does not meet the minimum system requirements for this OS version. If you enable this policy setting, these messages will never appear on desktop or in the Settings app. |
| Hide and disable all items on the desktop | Desktop | Removes icons, shortcuts, and other default and user-defined items from the desktop, including Briefcase, Recycle Bin, Computer, and Network Locations. |
| Enable App Installer | Windows Components\Desktop App Installer | This policy controls whether the Windows Package Manager can be used by users. If you enable or do not configure this setting, users will be able to use the Windows Package Manager. |
| Enable App Installer Settings | Windows Components\Desktop App Installer | This policy controls whether users can change their settings. If you enable or do not configure this setting, users will be able to change settings for the Windows Package Manager. If you disable this setting, users will not be able to change settings for the Windows Package Manager. |
| Enable App Installer Experimental Features | Windows Components\Desktop App Installer | This policy controls whether users can enable experimental features in the Windows Package Manager. If you enable or do not configure this setting, users will be able to enable experimental features for the Windows Package Manager. |
| Enable App Installer Local Manifest Files | Windows Components\Desktop App Installer | This policy controls whether users can install packages with local manifest files. If you enable or do not configure this setting, users will be able to install packages with local manifests using the Windows Package Manager. |
| Enable App Installer Hash Override | Windows Components\Desktop App Installer | This policy controls whether or not the Windows Package Manager can be configured to enable the ability override the SHA256 security validation in settings. |
| Enable App Installer Default Source | Windows Components\Desktop App Installer | This policy controls the default source included with the Windows Package Manager. |
| Enable App Installer Microsoft Store Source | Windows Components\Desktop App Installer | This policy controls the Microsoft Store source included with the Windows Package Manager. |
| Set App Installer Source Auto Update Interval In Minutes | Windows Components\Desktop App Installer | This policy controls the auto-update interval for package-based sources. |
| Enable App Installer Additional Sources | Windows Components\Desktop App Installer | This policy controls additional sources provided by the enterprise IT administrator. |
| Enable App Installer Allowed Sources | Windows Components\Desktop App Installer | This policy controls additional sources allowed by the enterprise IT administrator. |
| Enable App Installer ms-appinstaller protocol | Windows Components\Desktop App Installer | This policy controls whether users can install packages from a website that is using the ms-appinstaller protocol. |
| Configure Discovery of Designated Resolvers (DDR) protocol | Network\DNS Client | Specifies if the DNS client would use the DDR protocol. |
| Configure NetBIOS settings | Network\DNS Client | Specifies if the DNS client will perform name resolution over NetBIOS. |
| Turn off files from Office.com in Quick access view | Windows Components\File Explorer | Turning off files from Office.com will prevent File Explorer from requesting recent cloud file metadata and displaying it in the Quick access view. |
| Turn off Adobe Flash in Internet Explorer and prevent applications from using Internet Explorer technology to instantiate Flash objects | Windows Components\Internet Explorer\Security Features\Add-on Management | This policy setting turns off Adobe Flash in Internet Explorer and prevents applications from using Internet Explorer technology to instantiate Flash objects. |
| Turn off Adobe Flash in Internet Explorer and prevent applications from using Internet Explorer technology to instantiate Flash objects | Windows Components\Internet Explorer\Security Features\Add-on Management | This policy setting turns off Adobe Flash in Internet Explorer and prevents applications from using Internet Explorer technology to instantiate Flash objects. |
| Enable global window list in Internet Explorer mode | Windows Components\Internet Explorer | This setting allows Internet Explorer mode to use the global window list that enables sharing state with other applications. |
| Enable global window list in Internet Explorer mode | Windows Components\Internet Explorer | This setting allows Internet Explorer mode to use the global window list that enables sharing state with other applications. |
| Reset zoom to default for HTML dialogs in Internet Explorer mode | Windows Components\Internet Explorer | This policy setting lets admins reset zoom to default for HTML dialogs in Internet Explorer mode. If you enable this policy, the zoom of an HTML dialog in Internet Explorer mode will not get propagated from its parent page. |
| Reset zoom to default for HTML dialogs in Internet Explorer mode | Windows Components\Internet Explorer | This policy setting lets admins reset zoom to default for HTML dialogs in Internet Explorer mode. |
| Disable HTML Application | Windows Components\Internet Explorer | This policy setting specifies if running the HTML Application (HTA file) is blocked or allowed. If you enable this policy setting, running the HTML Application (HTA file) will be blocked. If you disable or do not configure this policy setting, running the HTML Application (HTA file) is allowed. |
| Disable HTML Application | Windows Components\Internet Explorer | This policy setting specifies if running the HTML Application (HTA file) is blocked or allowed. If you enable this policy setting, running the HTML Application (HTA file) will be blocked. If you disable or do not configure this policy setting, running the HTML Application (HTA file) is allowed. |
| Configure hash algorithms for certificate logon | System\KDC | This policy setting controls hash or checksum algorithms used by the Kerberos client when performing certificate authentication. |
| Configure hash algorithms for certificate logon | System\Kerberos | This policy setting controls hash or checksum algorithms used by the Kerberos client when performing certificate authentication. |
| Allow retrieving the Azure AD Kerberos Ticket Granting Ticket during logon | System\Kerberos | This policy setting allows retrieving the Azure AD Kerberos Ticket Granting Ticket during logon. |
| Request traffic compression for all shares | Network\Lanman Server | This policy controls whether the SMB server requests SMB client to use traffic compression for all SMB shares. If you enable this policy setting, the SMB server will by default request the SMB client to compress traffic when SMB compression is enabled. |
| Disable SMB compression | Network\Lanman Server | This policy controls whether the SMB server will disable (completely prevent) traffic compression. |
| Use SMB compression by default | Network\Lanman Workstation | This policy controls whether the SMB client uses traffic compression by default. If you enable this policy setting, the SMB client will attempt to compress traffic by default when SMB compression is enabled. |
| Disable SMB compression | Network\Lanman Workstation | This policy controls whether the SMB client will disable (completely prevent) traffic compression. |
| Allow Custom SSPs and APs to be loaded into LSASS | System\Local Security Authority | This policy controls the configuration under which LSASS loads custom SSPs and APs. If you enable this setting or do not configure it, LSA allows custom SSPs and APs to be loaded. If you disable this setting, LSA does not load custom SSPs and APs. |
| Configures LSASS to run as a protected process | System\Local Security Authority | This policy controls the configuration under which LSASS is run. If you do not configure this policy and there is no current setting in the registry, LSA will run as protected process for clean installed, HVCI capable, client SKUs that are domain or cloud domain joined devices. |
| Suppress the display of Edge Deprecation Notification | Windows Components\Microsoft Edge | You can configure Microsoft Edge to suppress the display of the notification that informs users that support of this version of Microsoft Edge ended on March 9th, 2021. If enabled, the notification will not show. If disabled or not configured, the notification will show every time Edge is launched. |
| Suppress the display of Edge Deprecation Notification | Windows Components\Microsoft Edge | You can configure Microsoft Edge to suppress the display of the notification that informs users that support of this version of Microsoft Edge ended on March 9th, 2021. If enabled, the notification will not show. If disabled or not configured, the notification will show every time Edge is launched. |
| Only allow device authentication for the Microsoft Account Sign-In Assistant | Windows Components\Microsoft account | This setting determines whether to only allow enterprise device authentication for the Microsoft Account Sign-in Assistant service (wlidsvc). By default, this setting is disabled and allows both user and device authentication. When the value is set to 1, only allow device authentication, and block user authentication. |
| Enable ESS with Supported Peripherals | Windows Components\Windows Hello for Business | While this policy is enabled on Windows 11 devices, external biometric authentication with Windows Hello will be blocked. |
| Limits print driver installation to Administrators | Printers | Determines whether users that aren’t Administrators can install print drivers on this computer. By default, users that aren’t Administrators can’t install print drivers on this computer. If you enable this setting or do not configure it, the system will limit installation of print drivers to Administrators of this computer. If you disable this setting, the system won’t limit installation of print drivers to this computer. |
| Manage processing of Queue-specific files | Printers | Manages how Queue-specific files are processed during printer installation. |
| Manage Print Driver signature validation | Printers | This policy setting controls the print driver signature validation mechanism. This policy controls the type of digital signature that is required for a print driver to be considered valid and installed on the system. |
| Manage Print Driver exclusion list | Printers | This policy setting controls the print driver exclusion list. The exclusion list allows an administrator to curate a list of printer drivers that are not allowed to be installed on the system. |
| Configure RPC listener settings | Printers | This policy setting controls which protocols incoming RPC connections to the print spooler are allowed to use. By default, RPC over TCP is enabled and Negotiate is used for the authentication protocol. |
| Configure RPC connection settings | Printers | This policy setting controls which protocol and protocol settings to use for outgoing RPC connections to a remote print spooler. |
| Configure RPC over TCP port | Printers | This policy setting controls which port is used for RPC over TCP for incoming connections to the print spooler and outgoing connections to remote print spoolers. |
| Always send job page count information for IPP printers | Printers | Determines whether to always send page count information for accounting purposes for printers using the Microsoft IPP Class Driver. |
| Configure Redirection Guard | Printers | Determines whether Redirection Guard is enabled for the print spooler. You can enable this setting to configure the Redirection Guard policy being applied to spooler. If you disable or do not configure this policy setting, Redirection Guard will default to being ‘enabled’. |
| Fully disable Search UI | Windows Components\Search | If you enable this policy, the Search UI will be disabled along with all its entry points, such as keyboard shortcuts, touchpad gestures, and type-to-search in the Start menu. The Start menu’s search box and Search Taskbar button will also be hidden. If you disable or don’t configure this policy setting, the user will be able to open the Search UI and its different entry points will be shown. |
| Allow search highlights | Windows Components\Search | Disabling this setting turns off search highlights in the start menu search box and in search home. Enabling or not configuring this setting turns on search highlights in the start menu search box and in search home. |
| Force Instant Dim | Windows Components\Human Presence | Determines whether Attention Based Display Dimming is forced on/off by the MDM policy. The user will not be able to change this setting and the toggle in the UI will be greyed out. |
| Do not sync accessibility settings | Windows Components\Sync your settings | Prevent the “accessibility” group from syncing to and from this PC. This turns off and disables the “accessibility” group on the “Windows backup” settings page in PC settings. |
| Remove Run menu from Start Menu | Start Menu and Taskbar | Allows you to remove the Run command from the Start menu, Internet Explorer, and Task Manager. |
| Prevent changes to Taskbar and Start Menu Settings | Start Menu and Taskbar | This policy setting allows you to prevent changes to Taskbar and Start Menu Settings. If you enable this policy setting, The user will be prevented from opening the Taskbar Properties dialog box. |
| Remove access to the context menus for the taskbar | Start Menu and Taskbar | This policy setting allows you to remove access to the context menus for the taskbar. If you enable this policy setting, the menus that appear when you right-click the taskbar and items on the taskbar are hidden, such as the Start button, the clock, and the taskbar buttons. If you disable or do not configure this policy setting, the context menus for the taskbar are available. This policy setting does not prevent users from using other methods to issue the commands that appear on these menus. |
| Prevent users from uninstalling applications from Start | Start Menu and Taskbar | If you enable this setting, users cannot uninstall apps from Start. If you disable this setting or do not configure it, users can access the uninstall command from Start |
| Remove Recommended section from Start Menu | Start Menu and Taskbar | This policy allows you to prevent the Start Menu from displaying a list of recommended applications and files. If you enable this policy setting, the Start Menu will no longer show the section containing a list of recommended files and apps. |
| Remove Recommended section from Start Menu | Start Menu and Taskbar | This policy allows you to prevent the Start Menu from displaying a list of recommended applications and files. If you enable this policy setting, the Start Menu will no longer show the section containing a list of recommended files and apps. |
| Simplify Quick Settings Layout | Start Menu and Taskbar | If you enable this policy, Quick Settings will be reduced to only having the WiFi, Bluetooth, Accessibility, and VPN buttons; the brightness and volume sliders; and battery indicator and link to the Settings app. If you disable or don’t configure this policy setting, the regular Quick Settings layout will appear whenever Quick Settings is invoked. |
| Disable Editing Quick Settings | Start Menu and Taskbar | If you enable this policy, the user will be unable to modify Quick Settings. If you disable or don’t configure this policy setting, the user will be able to edit Quick Settings, such as pinning or unpinning buttons. |
| Remove Quick Settings | Start Menu and Taskbar | This policy setting removes Quick Settings from the bottom-right area on the taskbar. |
| Remove pinned programs from the Taskbar | Start Menu and Taskbar | This policy setting allows you to remove pinned programs from the taskbar. |
| Hide the TaskView button | Start Menu and Taskbar | This policy setting allows you to hide the TaskView button. If you enable this policy setting, the TaskView button will be hidden and the Settings toggle will be disabled. |
| Hide the TaskView button | Start Menu and Taskbar | This policy setting allows you to hide the TaskView button. If you enable this policy setting, the TaskView button will be hidden and the Settings toggle will be disabled. |
| Do not allow WebAuthn redirection | Windows Components\Remote Desktop Services\Remote Desktop Session Host\Device and Resource Redirection | This policy setting lets you control the redirection of web authentication (WebAuthn) requests from a Remote Desktop session to the local device. This redirection enables users to authenticate to resources inside the Remote Desktop session using their local authenticator (e.g., Windows Hello for Business, security key, or other). |
| Disable Cloud Clipboard integration for server-to-client data transfer | Windows Components\Remote Desktop Services\Remote Desktop Connection Client | This policy setting lets you control whether data transferred from the remote session to the client using clipboard redirection is added to the client-side Cloud Clipboard. |
| Service Enabled | Windows Components\Windows Defender SmartScreen\Enhanced Phishing Protection | This policy setting determines whether Enhanced Phishing Protection in Microsoft Defender SmartScreen is in audit mode or off. |
| Notify Malicious | Windows Components\Windows Defender SmartScreen\Enhanced Phishing Protection | This policy setting determines whether Enhanced Phishing Protection in Microsoft Defender SmartScreen warns your users if they type their work or school password into one of the following malicious scenarios: into a reported phishing site, into a Microsoft login URL with an invalid certificate, or into an application connecting to either a reported phishing site or a Microsoft login URL with an invalid certificate. |
| Notify Password Reuse | Windows Components\Windows Defender SmartScreen\Enhanced Phishing Protection | This policy setting determines whether Enhanced Phishing Protection in Microsoft Defender SmartScreen warns your users if they reuse their work or school password. |
| Notify Unsafe App | Windows Components\Windows Defender SmartScreen\Enhanced Phishing Protection | This policy setting determines whether Enhanced Phishing Protection in Microsoft Defender SmartScreen warns your users if they type their work or school passwords in Notepad, Winword, or M365 Office apps like OneNote, Word, Excel, etc. |
| Device Control | Windows Components\Microsoft Defender Antivirus\Features | Enable or Disable Defender Device Control on this machine. Note: You must be enrolled as E3 or E5 in order for Device Control to be enabled. |
| Select Device Control Default Enforcement Policy | Windows Components\Microsoft Defender Antivirus\Device Control | Default Allow: Choosing this default enforcement, will Allow any operations to occur on the attached devices if no policy rules are found to match. |
| Define Device Control evidence data remote location | Windows Components\Microsoft Defender Antivirus\Device Control | Define evidence file remote location, where Device Control service will move evidence data captured. |
| Control whether or not exclusions are visible to Local Admins. | Windows Components\Microsoft Defender Antivirus | This policy setting controls whether or not exclusions are visible to Local Admins. |
| Select the channel for Microsoft Defender monthly platform updates | Windows Components\Microsoft Defender Antivirus | Enable this policy to specify when devices receive Microsoft Defender platform updates during the monthly gradual rollout. |
| Select the channel for Microsoft Defender monthly engine updates | Windows Components\Microsoft Defender Antivirus | Enable this policy to specify when devices receive Microsoft Defender engine updates during the monthly gradual rollout. |
| Select the channel for Microsoft Defender daily security intelligence updates | Windows Components\Microsoft Defender Antivirus | Enable this policy to specify when devices receive Microsoft Defender security intelligence updates during the daily gradual rollout. |
| Configure time interval for service health reports | Windows Components\Microsoft Defender Antivirus\Reporting | This policy setting configures the time interval (in minutes) for the service health reports to be sent from endpoints. |
| CPU throttling type | Windows Components\Microsoft Defender Antivirus\Scan | This policy setting determines whether the maximum percentage CPU utilization permitted during a scan applies only to scheduled scans, or to both scheduled and custom scans (but not real-time protection). |
| Disable gradual rollout of Microsoft Defender updates. | Windows Components\Microsoft Defender Antivirus\MpEngine | Enable this policy to disable gradual rollout of Defender updates. Current Channel (Broad): Devices set to this channel will be offered updates last during the gradual release cycle. |
| Enable MPR notifications for the system | Windows Components\Windows Logon Options | This policy controls the configuration under which winlogon sends MPR notifications in the system. If you enable this setting or do not configure it, winlogon sends MPR notifications if a credential manager is configured. If you disable this setting, winlogon does not send MPR notifications. |
Along with new Windows 11 22H2 GPO settings, the ADMX templates for Windows 11 22H2 are also available for download. To install these new Windows 11 22H2 ADMX templates, refer to my guide on how to download and install Administrative Templates for Windows 11.
Follow the below steps to download Administrative Templates (.admx) for Windows 11 22H2:
Microsoft has released a special spreadsheet which covers all Group Policy options for Windows 10 version 1803, known as «April 2018 Update». This document is useful for all Windows 10 users, especially for those who are is using Windows 10 Home. As you may already know, the Home edition doesn’t include the Local Group Policy Editor app (gpedit.msc), so having a list of Registry parameters you can apply is a must-have thing.
Group Policy is a way to configure computer and user settings for devices which are joined to Active Directory Domain Services (AD) as well as local user accounts. It controls a wide range of options and can be used to enforce settings and change the defaults for applicable users. Local Group Policy is a basic version of Group Policy for computers not included in a domain. The Local Group Policy settings are stored in the following folders:
C:\Windows\System32\GroupPolicy
C:\Windows\System32\GroupPolicyUsers.
If you are running Windows 10 Pro, Enterprise, or Education edition, you can use the Local Group Policy Editor app to configure the options with a GUI.
- Open your favorite web browser.
- Navigate to the following page: Download Group Policy Settings Reference Spreadsheet Windows 1803
- Click on the download button.
- Open the downloaded Windows10andWindowsServer2016PolicySettings-1803.xlsx file with Microsoft Excel or LibreOffice Calc.
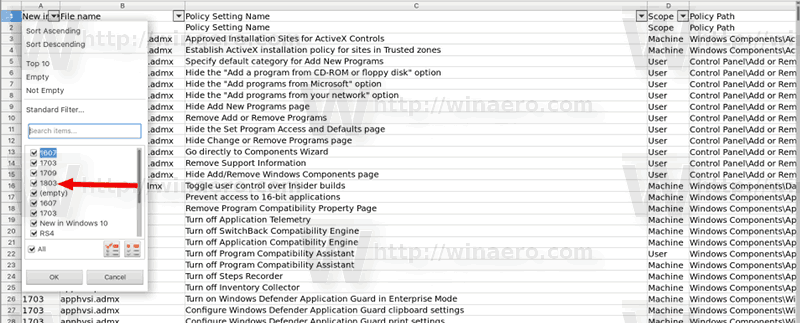
The spreadsheet lists the policy settings for computer and user configurations that are included in the Administrative template files delivered with the Windows operating systems specified. You can configure these policy settings when you edit Group Policy Objects.
You can use the filtering capabilities that are included in this spreadsheet to view a specific subset of data, based on one value or a combination of values that are available in one or more of the columns. In addition, you can click Custom in the drop-down list of any of the column headings to add additional filtering criteria within that column.
To view a specific subset of data, click the drop-down arrow in the column heading of cells that contain the value or combination of values on which you want to filter, and then click the desired value in the drop-down list. For example, to view policy settings that are available for Windows Server 2012 R2 or Windows 8.1, in the Administrative Template worksheet, click the drop-down arrow next to Supported On, and then click At least Microsoft Windows Server 2012 R2 or Windows 8.1.
Related articles.
- How To See Applied Group Policies in Windows 10
- See Applied Windows Update Group Policies in Windows 10
- Apply Group Policy to All Users Except Administrator in Windows 10
- Apply Group Policy to a Specific User in Windows 10
- Reset All Local Group Policy Settings at once in Windows 10
That’s it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won’t take a lot from you, but it will help us grow. Thanks for your support!
Let’s quickly check the details of the Windows 10 22H2 Group Policy Settings. The latest Windows 10 22H2 includes new security features for enterprise, more productivity-focused features, with every new release of the Windows version, group policy settings are updated to enhance the work experience.
Microsoft recommend that you begin targeted deployments of Windows 10, version 22H2 in your organization to validate that your apps, devices, and infrastructure work as expected with the new release.
Windows 10, version 22H2 (Windows 10 2022 Update) is a scoped release focused on quality improvements to the overall Windows experience in existing feature areas such as quality, productivity, and security.
For devices running Windows 10, versions 20H2, 21H1, or 21H2, you can take advantage of an enablement package for a fast, easy installation experience.

There are different methods to upgrade to Windows 10 22H2. As per Microsoft, Windows 10 22H2 availability can vary depending on the device and WUfB policy configured from Intune. You can also use the SCCM Windows Servicing option to upgrade to Windows 10 22H2 version.
- Windows 11 22H2 Group Policy Settings list Download
- Download Windows 10 Administrative Templates for All Versions
Download Windows 10 22H2 Group Policy Settings Reference Spreadsheet
This spreadsheet lists the policy settings for computer and user configurations included in the ADMX files delivered for Windows 10 2022 Update (Version 22H2). You can configure these policy settings when you edit Windows 10 22H2 Group Policy Objects.
Group Policy settings reference spreadsheet for Windows 10, version 22H2
- To download Group Policy settings reference spreadsheet for Windows 10 22H2, Select the link. You’ll be redirected to the Download Center details page.
- On the download page that opens, Validate the Windows version details. Click on the Download button.

Here you will get the Windows10andWindowsServer2019PolicySettings–22H2.xlsx. You can use the filtering capabilities. In addition, you can click Custom in the drop-down list of any of the column headings to add additional filtering criteria within that column.
This spreadsheet lists the policy settings for computer and user configurations that are included in the Administrative template files (.admx and .adml) delivered with Windows 10, version 22H2. The policy settings included in this spreadsheet also cover Windows 10 (version 21H2), Windows Server 2019, Windows Server 2016, Windows 10, or earlier windows versions.
- New Group Policy Settings Available in Different Versions of Windows 10
- List of Intune Administrative Template Settings| User | Device
The following Windows 10 22H2 Group Policy Settings lists for computer and user configurations are included in the Administrative template files (.admx and .adml) delivered with Windows 10 22H2. The list includes only the new policies added.
| Location | Policy Path | Windows 10 22H2 Policy Setting Name | Group Policy Descriptions |
| Machine | MS Security Guide | Configure RPC packet level privacy setting for incoming connections | The Windows 10 22H2 Group Policy setting controls whether packet level privacy is enabled for RPC for incoming connections. By default packet level privacy is enabled for RPC for incoming connections. |
| Machine | MS Security Guide | Manage processing of Queue-specific files | The Windows 10 22H2 Group Policy Manages how Queue-specific files are processed during printer installation. At printer installation time a vendor-supplied installation application can specify a set of files of any type to be associated with a particular print queue. The files are downloaded to each client that connects to the print server. |
| Machine | Printers | Configure Redirection Guard | The Windows 10 22H2 Group Policy Determines whether Redirection Guard is enabled for the print spooler. |
| Machine | Start Menu and Taskbar | Show or hide “Most used” list from Start menu | If you enable the Windows 10 22H2 Group Policy setting you can configure Start menu to show or hide the list of user’s most used apps regardless of user settings. Selecting “Show” will force the “Most used” list to be shown and user cannot change to hide it using the Settings app. |
| Machine | Windows Components\Internet Explorer | Enable global window list in Internet Explorer mode | This setting allows Internet Explorer mode to use the global window list that enables sharing state with other applications. The setting will take effect only when Internet Explorer 11 is disabled as a standalone browser. |
| Machine | Windows Components\Internet Explorer | Hide Internet Explorer 11 retirement notification | The Windows 10 22H2 Group policy setting allows you to manage whether the notification bar reminder that Internet Explorer is being retired is displayed. By default, the Notification bar is displayed in Internet Explorer 11. |
| Machine | Windows Components\Microsoft Defender Antivirus | Control whether or not exclusions are visible to Local Admins. | The Windows 10 22H2 Group Policy setting controls whether or not exclusions are visible to Local Admins. For end users (that are not Local Admins) exclusions are not visible whether or not this setting is enabled. |
| Machine | Windows Components\Search | Allow search highlights | Disabling this setting turns off search highlights in the taskbar search box and in search home. Enabling or not configuring this setting turns on search highlights in the taskbar search box and in search home. |
| Machine | Windows Components\Tenant Restrictions | Cloud Policy Details | This setting enables and configures the device-based tenant restrictions feature for Azure Active Directory. |
| User | AutoSubscription | Enable auto-subscription | The Windows 10 22H2 Group Policy Controls the list of URLs that the user should be auto-subscribed to |
| User | Start Menu and Taskbar | Show or hide “Most used” list from Start menu | If you enable this policy setting you can configure Start menu to show or hide the list of user’s most used apps regardless of user settings. Selecting “Show” will force the “Most used” list to be shown and user cannot change to hide it using the Settings app. Selecting “Hide” will force the “Most used” list to be hidden and user cannot change to show it using the Settings app. |
| User | Start Menu and Taskbar\Notifications | Turn on multiple expanded toast notifications in action center | The Windows 10 22H2 Group policy setting turns on multiple expanded toast notifications in action center. |
| User | Windows Components\Internet Explorer | Enable global window list in Internet Explorer mode | This setting allows Internet Explorer mode to use the global window list that enables sharing state with other applications. The setting will take effect only when Internet Explorer 11 is disabled as a standalone browser. |
| User | Windows Components\Internet Explorer | Hide Internet Explorer 11 retirement notification | This policy setting allows you to manage whether the notification bar reminder that Internet Explorer is being retired is displayed. By default the Notification bar is displayed in Internet Explorer 11. |
Download ADMX Templates for Windows 10 22H2
Administrative Templates files are divided into .admx files and language-specific .adml files for use by Group Policy administrators. The changes implemented in these files let administrators configure the same set of policies using two languages.
Administrators can configure policies using language-specific .adml files and language-neutral .admx files.Administrative Templates (.admx) for Windows 10, version 22H2 are natively accessible via the C:\Windows\PolicyDefinitions\ folder in Windows.
Follow the below steps to download Administrative Templates (.admx) for Windows 10 22H2:
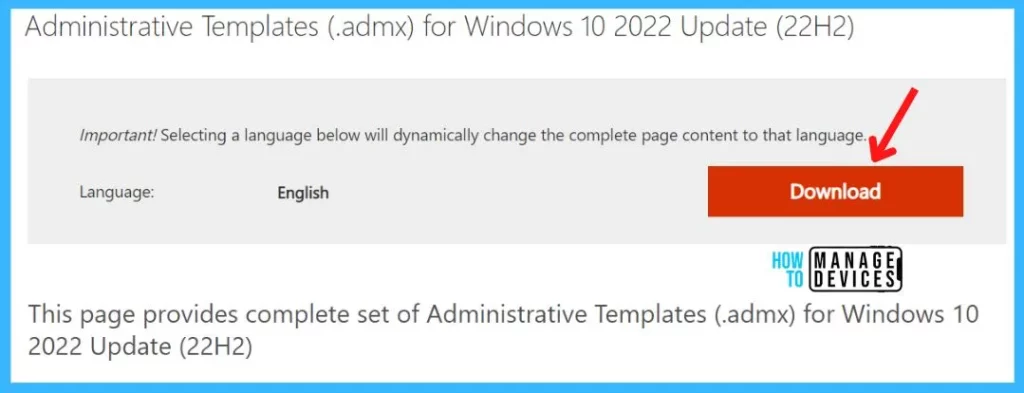
- To Download Administrative Templates (.admx). Click on the link ADMX for Windows 10, version 22H2
- You’ll be redirected to the Download Center details page for your device.
- On the download page that opens, Validate the Windows version details. Click on the Download button
Once you completed downloading an *.MSI file for Windows 10 22H2. You need to extract the files and follow the steps as described Download Windows 11 Administrative Templates.
Author
Posted by: kurtsh | May 15, 2016
These spreadsheets list the policy settings for computer and user configurations that are included in the Administrative template files delivered with the Windows operating systems specified. You can configure these policy settings when you edit Group Policy Objects.
You can use the filtering capabilities that are included in this spreadsheet to view a specific subset of data, based on one value or a combination of values that are available in one or more of the columns. In addition, you can click Custom in the drop-down list of any of the column headings to add additional filtering criteria within that column.
To view a specific subset of data, click the drop-down arrow in the column heading of cells that contain the value or combination of values on which you want to filter, and then click the desired value in the drop-down list. For example, to view policy settings that are available for Windows Server 2012 R2 or Windows 8.1, in the Administrative Template worksheet, click the drop-down arrow next to Supported On, and then click At least Microsoft Windows Server 2012 R2 or Windows 8.1.
What’s New?
The Administrative Template spreadsheet contains three columns that provide more information about each policy setting’s behavior related to reboots, logoffs, and schema extensions. These columns are the following:
- Reboot Required: A «Yes» in this column means that the Windows operating systems requires a restart before it applies the described policy setting.
- Logoff Required: A «Yes» in this column means that the Windows operating system requires the user to log off and log on again before it applies the described policy setting.
- Active Directory Schema or Domain Requirements: A «Yes» in this column means that you must extend the Active Directory schema before you can deploy this policy setting.
- Status: A «New» in this column means that the setting did not exist prior to Windows Server 2012 R2 and Windows 8.1. It does not mean that the setting applies only to Windows Server 2012 R2 and Windows 8.1. Refer to the column entitled «supported on» to determine to which operating system the policy setting applies.
Contents include:
- TP4 Policy Settings Spreadsheet.xlsx
- Windows 10 ADMX spreadsheet.xlsx
- Windows 8.1 Update and Windows Server 2012 R2 Update 1 .xlsx
- Windows Server 2016 TP5 policy settings spreadsheet.xlsx
- WindowsServer2003SP2GroupPolicySettings.xls
- WindowsServer2008andWindowsVistaSP1GroupPolicySettings.xlsx
- WindowsServer2008R2andWindows7GroupPolicySettings.xlsx
- WindowsServer2012andWindows8GroupPolicySettings.xlsx
- WindowsServer2012R2andWindows8.1GroupPolicySettings.xlsx
- WindowsServer2012R2UpdateGroupPolicySettings.xlsx
- WindowsVistaGroupPolicySettings.xls
Get the entire package here:
- DOWNLOAD: Group Policy Settings Reference for Windows and Windows Server
http://www.microsoft.com/en-us/download/details.aspx?id=25250
