When using Windows, you might run into messages that talk about specific hard disk volumes like \Device\HarddiskVolume3. At first, these messages might seem a bit tricky to get, but actually, they’re pretty straightforward once you know what to do.
In this guide, we’ll break down what these hard disk volume references mean and show you how to figure out which drive they’re talking about in Windows 11 or Windows 10. We’ll go step by step so you can find the specific device or volume path you need to sort out any issues with file access events.
Understanding hard disk volume references
Before we get into finding hard disk volume references in Windows, let’s first get what they are and why we use them.
Also see: How to hide a drive in Windows 11
In Windows, hard disk volumes help organize data on physical hard drives. Each volume gets a unique reference, like:
- \Device\HarddiskVolume3
- \Device\HarddiskVolume4
- \Device\HarddiskVolume5
- \Device\HarddiskVolume1
- \Device\HarddiskVolume2
- \Device\HarddiskVolume6
This reference is how Windows identifies and accesses the volume’s contents.
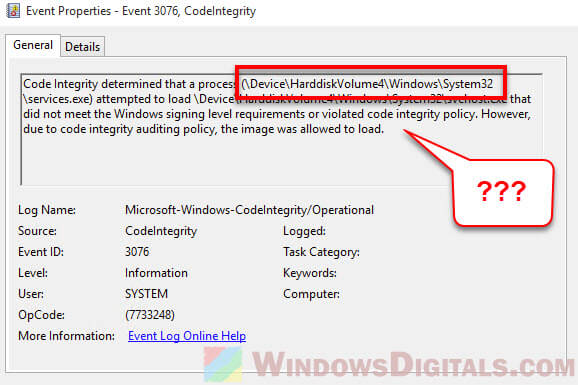
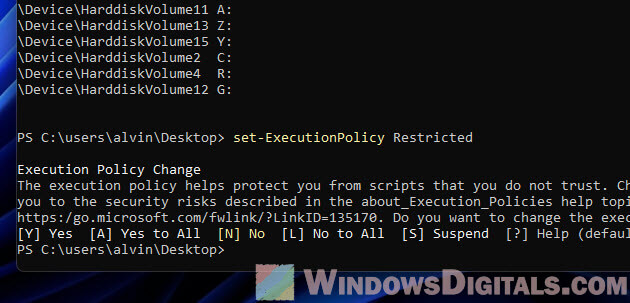
When fixing issues in Windows, you might see error messages pointing to a certain hard disk volume. Like, you could get a message saying:
\Device\HarddiskVolume3\Windows\System32\svchost.exe is missing or corrupted
This means Windows can’t find the svchost.exe file on the third hard disk volume, and you’ll need to find that volume and the file to fix the problem.
Related issue: Service Host Local System (svchost.exe) high CPU, disk, or memory usage
How to tell which drive is \Device\HarddiskVolume3 or other volumes?
Now that we know what hard disk volume references are, let’s see how to find the hard disk volume number and figure out which drive it’s pointing to in Windows 11/10.
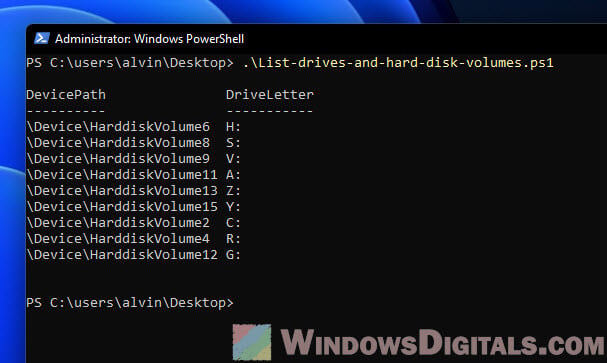
Method 1: Listing all drive letters and hard disk volume numbers using PowerShell
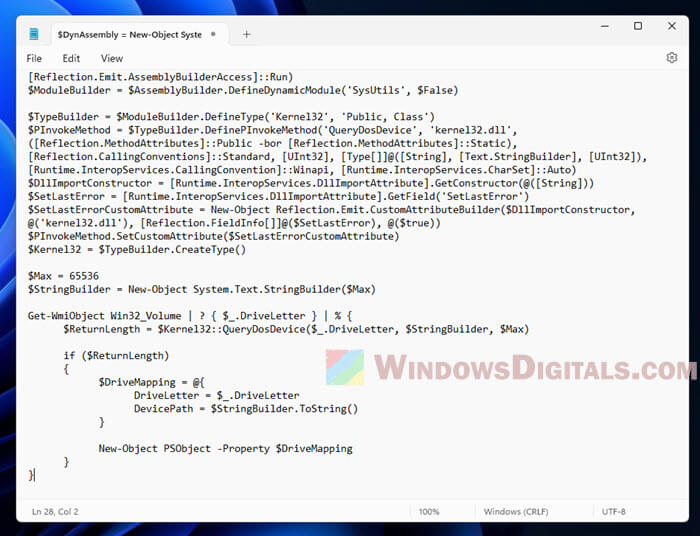
This method gives you a full list of all device names and their matching volume paths on your computer. It uses PowerShell to check the Windows Management Instrumentation (WMI) class Win32_Volume for the drive letter and then gets the device path through the QueryDosDevice function from the Kernel32 module.
To list all the drive letters and their matching hard disk volume numbers on your Windows system, do this:
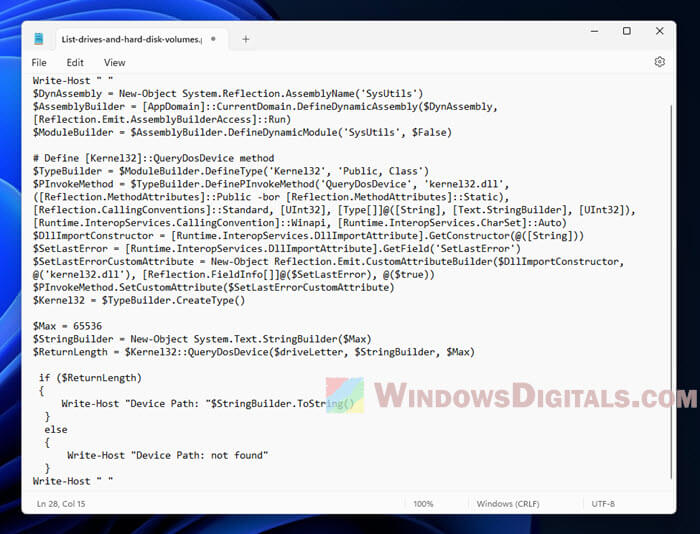
- Open Notepad and paste the following PowerShell script.
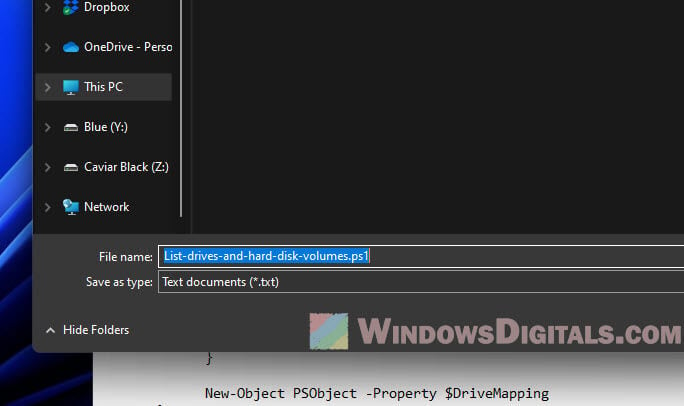
$DynAssembly = New-Object System.Reflection.AssemblyName('SysUtils') $AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly($DynAssembly, [Reflection.Emit.AssemblyBuilderAccess]::Run) $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule('SysUtils', $False) $TypeBuilder = $ModuleBuilder.DefineType('Kernel32', 'Public, Class') $PInvokeMethod = $TypeBuilder.DefinePInvokeMethod('QueryDosDevice', 'kernel32.dll', ([Reflection.MethodAttributes]::Public -bor [Reflection.MethodAttributes]::Static), [Reflection.CallingConventions]::Standard, [UInt32], [Type[]]@([String], [Text.StringBuilder], [UInt32]), [Runtime.InteropServices.CallingConvention]::Winapi, [Runtime.InteropServices.CharSet]::Auto) $DllImportConstructor = [Runtime.InteropServices.DllImportAttribute].GetConstructor(@([String])) $SetLastError = [Runtime.InteropServices.DllImportAttribute].GetField('SetLastError') $SetLastErrorCustomAttribute = New-Object Reflection.Emit.CustomAttributeBuilder($DllImportConstructor, @('kernel32.dll'), [Reflection.FieldInfo[]]@($SetLastError), @($true)) $PInvokeMethod.SetCustomAttribute($SetLastErrorCustomAttribute) $Kernel32 = $TypeBuilder.CreateType() $Max = 65536 $StringBuilder = New-Object System.Text.StringBuilder($Max) Get-WmiObject Win32_Volume | ? { $_.DriveLetter } | % { $ReturnLength = $Kernel32::QueryDosDevice($_.DriveLetter, $StringBuilder, $Max) if ($ReturnLength) { $DriveMapping = @{ DriveLetter = $_.DriveLetter DevicePath = $StringBuilder.ToString() } New-Object PSObject -Property $DriveMapping } } - Save the Notepad file as a .ps1 file, like List-drives-and-hard-disk-volumes.ps1.
- Run the
List-drives-and-hard-disk-volumes.ps1script in PowerShell to see all the drive letters and their hard disk volume paths on your Windows 11 or Windows 10 system.
Recommended resource: Run CMD, PowerShell, or Regedit as SYSTEM in Windows 11
To run the List-drives-and-hard-disk-volumes.ps1 script in PowerShell, just follow these steps:
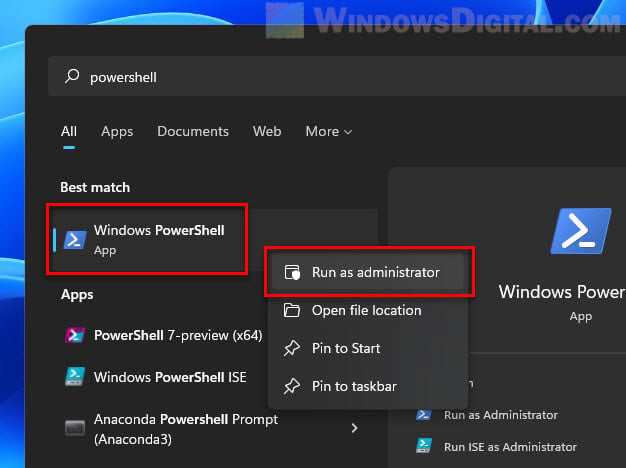
- Open PowerShell as an admin by right-clicking the Start button, picking “Windows PowerShell (Admin)” or “Windows Terminal (Admin)” if you’re using Windows Terminal, and saying “Yes” to the User Account Control (UAC) prompt.
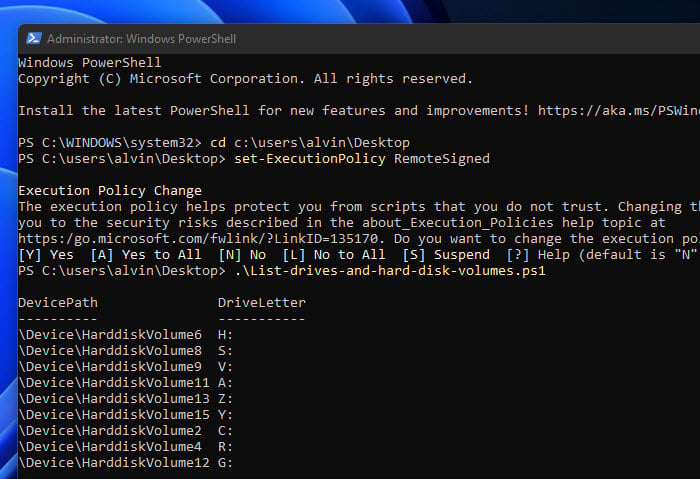
- If needed, change the execution policy by typing
Set-ExecutionPolicy RemoteSigned
and hitting Enter. Say
Yto confirm. This lets you run scripts you’ve made or downloaded as long as they’re signed by someone trustworthy. - Go to where you saved the script using the
cdcommand. For example, if it’s on the Desktop, typecd C:\Users\username\Desktop
and press Enter. Swap in your actual Windows username.
- To run the script, type
.\List-drives-and-hard-disk-volumes.ps1
and hit Enter. You’ll see the device names and their paths for all drives on your computer.
- It’s a good idea to set the execution policy back to its default after running the script by typing
Set-ExecutionPolicy Restricted
You need admin rights to run the script since it touches on system info.
Useful tip: How to merge two drives in Windows 11
Here’s a deeper look at what the script does:
- It makes a dynamic assembly named ‘SysUtils’ and sets up a method to call the
QueryDosDevicefunction from the Kernel32 module. - The
StringBuilderobject’s max length is set to 65536 to hold the device path info. - Then it uses
Get-WmiObjectto ask theWin32_Volumeclass for drive letter details, only keeping results that have a drive letter. - For each drive letter, it calls the
QueryDosDevicefunction with the drive letter as input. The function returns the device path string’s length, which is then put into an object that has both the drive letter and device path. - Last, it shows the device letter and path for each drive.
Similar problem: Hard drive doesn’t show up after clone in Windows 11
Method 2: Getting the hard disk volume number from a specific drive letter using PowerShell
This method lets you find the device path for a specific drive letter using a similar approach as Method 1. But instead of listing all device names and their paths, it asks you for a drive letter and gives back its device path.
To see the device path for a specific drive letter, use this PowerShell script:
- Open Notepad and paste in the PowerShell script below.
$driveLetter = Read-Host "Enter Drive Letter:" Write-Host " " $DynAssembly = New-Object System.Reflection.AssemblyName('SysUtils') $AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly($DynAssembly, [Reflection.Emit.AssemblyBuilderAccess]::Run) $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule('SysUtils', $False) $TypeBuilder = $ModuleBuilder.DefineType('Kernel32', 'Public, Class') $PInvokeMethod = $TypeBuilder.DefinePInvokeMethod('QueryDosDevice', 'kernel32.dll', ([Reflection.MethodAttributes]::Public -bor [Reflection.MethodAttributes]::Static), [Reflection.CallingConventions]::Standard, [UInt32], [Type[]]@([String], [Text.StringBuilder], [UInt32]), [Runtime.InteropServices.CallingConvention]::Winapi, [Runtime.InteropServices.CharSet]::Auto) $DllImportConstructor = [Runtime.InteropServices.DllImportAttribute].GetConstructor(@([String])) $SetLastError = [Runtime.InteropServices.DllImportAttribute].GetField('SetLastError') $SetLastErrorCustomAttribute = New-Object Reflection.Emit.CustomAttributeBuilder($DllImportConstructor, @('kernel32.dll'), [Reflection.FieldInfo[]]@($SetLastError), @($true)) $PInvokeMethod.SetCustomAttribute($SetLastErrorCustomAttribute) $Kernel32 = $TypeBuilder.CreateType() $Max = 65536 $StringBuilder = New-Object System.Text.StringBuilder($Max) $ReturnLength = $Kernel32::QueryDosDevice($driveLetter, $StringBuilder, $Max) if ($ReturnLength) { Write-Host "Device Path: "$StringBuilder.ToString() } else { Write-Host "Device Path: not found" } Write-Host " " - Save it as a .ps1 file, like Get-device-path-from-drive-letter.ps1.
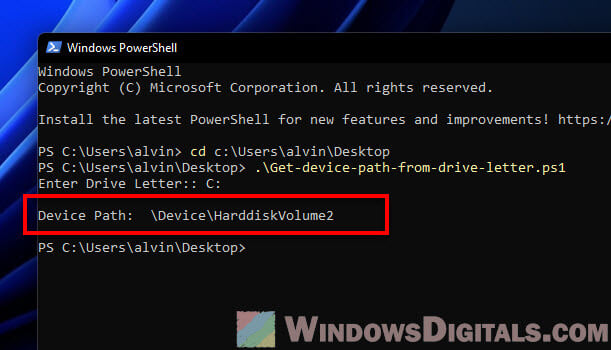
- Run the
Get-device-path-from-drive-letter.ps1script in PowerShell. When asked, type the drive letter you want the device path for.
For how to run the .ps1 PowerShell script you’ve made, just follow the steps in the method above.
Here’s what the script does:
- Like Method 1, it creates ‘SysUtils’ and sets up a way to use the
QueryDosDevicefunction from the Kernel32 module. - It asks for a drive letter with the
Read-Hostcommand. Remember to enter it without the backslash (like “C:”, not “C:\”). - The
StringBuilderobject’s max length is set to 65536, so it can hold the device path info. - Then it calls
QueryDosDevicewith the input drive letter. If it works, it returns the length of the device path string. - If
QueryDosDeviceworks out, the script shows the device path for the drive letter. If not, it says the device path wasn’t found.
One final note
One more thing to remind you is that although these methods do help you track down disk volume paths and drive letters, you have to know that the volume numbers can sometimes change. For instance, plugging in a new hard disk drive or SSD, creating a new partition, etc. can sometimes shuffle the numbers. When things don’t go as planned, double-check the volume paths and drive letters again to make sure you are working with the correct volume.
Having this issue several times for our users.
Something makes the windows profile corrupt so they got logged in as a temporary profile.
Log Name: Application
Source: Microsoft-Windows-User Profiles Service
Date: 3/27/2012 8:46:56 AM
Event ID: 1530
Task Category: None
Level: Varning
Keywords:
User: SYSTEM
Computer: idg000578.idg.local
Description:
Windows har upptäckt att din registerfil fortfarande används av andra program eller servrar. Filen tas nu bort ur minnet. Programmen eller tjänsterna som använder registerfilen kanske inte fungerar korrekt efter detta.
INFORMATION —
2 user registry handles leaked from \Registry\User\S-1-5-21-1606980848-1645522239-682003330-500:
Process 2004 (\Device\HarddiskVolume2\Windows\System32\winlogon.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-500
Process 2028 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\Rtvscan.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-500\Software\Symantec\Symantec Endpoint Protection\AV\Custom Tasks
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»Microsoft-Windows-User Profiles Service» Guid=»{89B1E9F0-5AFF-44A6-9B44-0A07A7CE5845}» />
<EventID>1530</EventID>
<Version>0</Version>
<Level>3</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime=»2012-03-27T06:46:56.185206800Z» />
<EventRecordID>16864</EventRecordID>
<Correlation />
<Execution ProcessID=»936″ ThreadID=»2588″ />
<Channel>Application</Channel>
<Computer>idg000578.idg.local</Computer>
<Security UserID=»S-1-5-18″ />
</System>
<EventData Name=»EVENT_HIVE_LEAK»>
<Data Name=»Detail»>2 user registry handles leaked from \Registry\User\S-1-5-21-1606980848-1645522239-682003330-500:
Process 2004 (\Device\HarddiskVolume2\Windows\System32\winlogon.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-500
Process 2028 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\Rtvscan.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-500\Software\Symantec\Symantec Endpoint Protection\AV\Custom Tasks
</Data>
</EventData>
</Event>
Din profil kan inte läsas in, så du har loggats in med datorns standardprofil.
INFORMATION — Åtkomst nekad.
Windows har upptäckt att din registerfil fortfarande används av andra program eller servrar. Filen tas nu bort ur minnet. Programmen eller tjänsterna som använder registerfilen kanske inte fungerar korrekt efter detta.
INFORMATION —
59 user registry handles leaked from \Registry\User\S-1-5-21-1606980848-1645522239-682003330-2237:
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\MSF\Registration\Listen
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Internet Settings
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\TrustedPeople
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\TrustedPeople
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\TrustedPeople
Process 2028 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\Rtvscan.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Symantec\Symantec Endpoint Protection\AV\Custom Tasks
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Root
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Root
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Root
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\Shell
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Explorer
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Explorer
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Explorer
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\My
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\My
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\My
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\trust
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\trust
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\trust
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\CA
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\CA
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\CA
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\Shell\Bags\1\Desktop
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Disallowed
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Disallowed
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\Disallowed
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Policies\Microsoft\SystemCertificates
Process 312 (\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\Windows Live\WLIDSVC.EXE) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\SmartCardRoot
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\SmartCardRoot
Process 2448 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\ProtectionUtilSurrogate.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\SystemCertificates\SmartCardRoot
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows NT\CurrentVersion
Process 1668 (\Device\HarddiskVolume2\Program Files (x86)\Symantec\Symantec Endpoint Protection\SmcGui.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows NT\CurrentVersion
Process 2676 (\Device\HarddiskVolume2\Windows\explorer.exe) has opened key \REGISTRY\USER\S-1-5-21-1606980848-1645522239-682003330-2237\Software\Microsoft\Windows\CurrentVersion\HomeGroup\Printers
#1
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Сентябрь 2019 — 02:10
Аналогично: есть ли в системе вирусы, и особенно кейлоггеры?
https://cloud.mail.ru/public/QUwr/3hcNLK7y7
- Наверх
#2
Dr.Robot
Dr.Robot
- Helpers
- 3 343 Сообщений:
Poster
Отправлено 29 Сентябрь 2019 — 02:10
1. Если Вы подозреваете у себя на компьютере вирусную активность и хотите получить помощь в этом разделе,
Вам необходимо кроме описания проблемы приложить к письму логи работы трёх программ — сканера Dr. Web (или CureIt!, если антивирус Dr. Web не установлен на Вашем ПК), Hijackthis и DrWeb SysInfo. Где найти эти программы и как сделать логи описано в Инструкции. Без логов помочь Вам не сможет даже самый квалифицированный специалист.
2. Если у Вас при включении компьютера появляется окно с требованием перечислить некоторую сумму денег и при этом блокируется доступ к рабочему столу,
— попытайтесь найти коды разблокировки здесь https://www.drweb.com/xperf/unlocker/
— детально опишите как выглядит это окно (цвет, текст, количество кнопок, появляется ли оно до появления окна приветствия Windows или сразу же после включении компьютера);
— дождаться ответа аналитика или хелпера;
3. Если у Вас зашифрованы файлы,
Внимание! Услуга по расшифровке файлов предоставляется только лицензионным пользователям продуктов Dr.Web, у которых на момент заражения была установлена коммерческая лицензия Dr.Web Security Space не ниже версии 9.0, Антивирус Dr.Web для Windows не ниже версии 9.0 или Dr.Web Enterprise Security Suite не ниже версии 6.0. подробнее.
Что НЕ нужно делать:
— лечить и удалять найденные антивирусом вирусы в автоматическом режиме или самостоятельно. Можно переместить всё найденное в карантин, а после спросить специалистов или не предпринимать никаких действий, а просто сообщить название найденных вирусов;
— переустанавливать операционную систему;
— менять расширение у зашифрованных файлов;
— очищать папки с временными файлами, а также историю браузера;
— использовать самостоятельно без консультации с вирусным аналитиком Dr. Web дешифраторы из «Аптечки сисадмина» Dr. Web;
— использовать дешифраторы рекомендуемые в других темах с аналогичной проблемой.
Что необходимо сделать:
— прислать в вирусную лабораторию Dr. Web https://support.drweb.com/new/free_unlocker/?keyno=&for_decode=1 несколько зашифрованных файлов и, если есть, их не зашифрованные копии в категорию Запрос на лечение. Дожидаться ответа на Вашу почту вирусного аналитика и далее следовать его указаниям ведя с ним переписку по почте. На форуме рекомендуется указать номер тикета вирлаба — это номер Вашего запроса, содержащий строку вида [drweb.com #3219200];
4. При возникновении проблем с интернетом, таких как «не открываются сайты», в браузерах появляются картинки с порно или рекламным содержанием там, где раньше ничего подобного не было, появляются надписи типа «Содержание сайта заблокировано» и пр. нестандартные уведомления необходимо выложить дополнительно к логам из п.1 лог команды ipconfig
Для этого проделайте следующее:
- Зайдите в меню Пуск на Рабочем столе, вызовите в нем окно команды Выполнить…
- В появившемся окне наберите cmd и нажмите клавишу <Enter>. Появится черное окно консоли (интерпретатора команд).
- Напишите в этом черном окне команду ipconfig /all>»%userprofile%\ipc.log» и нажмите клавишу <Enter>, затем наберите там же команду explorer.exe /select,»%userprofile%\ipc.log» и нажмите клавишу <Enter>, нужный файл будет показан в Проводнике Windows.
- Приложите этот файл к своему сообщению на форуме.
Чтобы не сделать ошибок в написании команд, можно скопировать эти команды отсюда и последовательно вставлять в черное окно консоли путем выбора пункта Вставить из меню, появляющегося при нажатии правой кнопки мыши в черном окне консоли.
- Наверх
#3
RomaNNN
RomaNNN
- Posters
- 6 001 Сообщений:
Ковальски
Отправлено 29 Сентябрь 2019 — 16:59
Куча непонятных либ сомнительной репутации, скринсейверы, активаторы. Сложно сказать, есть ли тут малварь, либо это просто левые либы от чего-то.
<file path="C:\windows\system32\rtvcvfw64.dll" size="246272" links="1" ctime="28.09.2012 23:45:18.000" atime="28.09.2019 09:52:21.242" wtime="28.09.2012 23:45:18.000" buildtime="28.09.2012 23:45:17.000"> <attrib archive="true" value="20" /> <hash sha1="fae178bae65161fc77d9184ee487a0ca8df5298e" sha256="a126f29f665ba1b94392165cdcc6ffa0fdbfc330f5dde12dcaecd4c371b22681" /> <arkstatus file="unsigned, pe64, dll" cert="unsigned" cloud="unknown" type="unknown" /> </file> <file path="C:\windows\system32\wuaueng2.dll" size="2651648" links="1" ctime="05.06.2019 00:57:25.515" atime="05.06.2019 00:57:25.515" wtime="05.06.2019 00:57:25.515" buildtime="14.03.2018 20:53:37.000"> <attrib archive="true" value="20" /> <hash sha1="d6e6132e2bb3f1abf50434df07638db05a22caa1" sha256="a109e915864c25b02eb02cc7edc57bd616b1d53d57085c6623235fac2de295a8" /> <arkstatus file="unsigned, pe64, dll" cert="unsigned" cloud="unknown" type="unknown" /> <verinfo company="Microsoft Corporation" descr="Windows Update Agent" origname="wuaueng.dll" version="7.6.7601.24085 (win7sp1_ldr.180314-0600)" product_name="Microsoft® Windows® Operating System" product_version="7.6.7601.24085" file_version_num="7.6.7601.24085" product_version_num="7.6.7601.24085" /> </file> <file path="C:\Windows\SysWOW64\Branded.scr" size="8174592" links="1" ctime="05.06.2019 05:03:18.692" atime="05.06.2019 05:06:24.935" wtime="10.10.2011 10:00:00.000" buildtime="19.05.2006 05:13:29.000"> <attrib archive="true" value="20" /> <hash sha1="86276aa730467b78d9993c6a0653b5dfee37f40d" sha256="7601401ee34b4440a5b69d660f276025327b986647c8d929b15f6009ddbb46b3" /> <arkstatus file="unsigned, pe32" cert="unsigned" cloud="unknown" type="unknown" /> <verinfo company="Microsoft Corporation" descr="Windows Energy Screen Saver" origname="ssBranded" version="6.0.5384.4 (winmain_beta2.060518-1455)" product_name="Microsoft® Windows® Operating System" product_version="6.0.5384.4" file_version_num="6.0.5384.4" product_version_num="6.0.5384.4" /> </file> <file path="C:\Windows\SysWOW64\Euphoria.scr" size="513024" links="1" ctime="05.06.2019 05:03:18.879" atime="05.06.2019 05:06:25.138" wtime="10.10.2011 10:00:00.000" buildtime="24.06.2010 08:17:06.000"> <attrib archive="true" value="20" /> <hash sha1="c7301237b4fed80fdd6b5664a46fbf3653e0acd7" sha256="18c5363e589729830cb83e6e4f2c6d14706be74f31fac830537ad9669407ae67" /> <arkstatus file="unsigned, pe32" cert="unsigned" cloud="unknown" type="unknown" /> </file> <file path="C:\windows\oinstall.exe" size="10149360" links="1" ctime="28.09.2019 04:26:33.130" atime="28.09.2019 04:26:33.130" wtime="14.12.2018 12:39:08.568" buildtime="14.12.2018 12:38:35.000"> <attrib archive="true" value="20" /> <hash sha1="b8ffb78f56c9b35aa79bc8121c216669f99b0a75" sha256="ca991b9b7ccfb19218ec4d0b58cec38b9b373be5e4e35ad28946b54343132ca6" /> <arkstatus file="pe32" cert="root_not_trusted" cloud="unknown" type="unknown" /> <verinfo company="" descr="Office 2013-2016 C2R Install" origname="" version="" product_name="Office 2013-2016 C2R Install" product_version="" file_version_num="6.4.9.0" product_version_num="6.4.9.0" /> <certinfo timestamp="14.12.2018 12:39:04.000"> <item subject="CN=WZTeam" issuer="CN=WZTeam" thumbprint="648384a4dee53d4c1c87e10d67cc99307ccc9c98" sn="8ac1a3101349c28a4d33947cfcd07662" from="02.11.2016 22:47:06.000" to="01.01.2040 03:59:59.000" /> </certinfo> </file>
Смущает детект-диагностика на подмену тела на целую кучу процессов, это в системе что-то явно нестандартное.
<detects>
<item object="EncoderServer.exe:2540" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2540\Device\HarddiskVolume1\MSI Afterburner\RivaTuner Statistics Server\EncoderServer.exe" id="b7a1268d5335ff14e30ccf481ed041fdd27c5a63" />
<item object="lsass.exe:652" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\652\Device\HarddiskVolume2\Windows\System32\lsass.exe" id="efd72f6cb0412c19f936e3d8c294be41b2e5c11f" />
<item object="RAVCpl64.exe:2596" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2596\Device\HarddiskVolume2\Program Files\Realtek\Audio\HDA\RAVCpl64.exe" id="c0e3ae8d2386f6a464c953ea8d91556c47359d47" />
<item object="smss.exe:288" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\288\Device\HarddiskVolume2\Windows\System32\smss.exe" id="72b72ba971bcc0373817994772b9f87ce7fdbc33" />
<item object="svchost.exe:472" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\472\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="cb36c0d33d9e2365f5605af875293ac4890208cd" />
<item object="explorer.exe:2216" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2216\Device\HarddiskVolume2\Windows\explorer.exe" id="a36c63ef27b4b927d85353397eabbae42e98921b" />
<item object="svchost.exe:320" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\320\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="4a9f57c7c05c70ca157a13f271fd8936147c1821" />
<item object="wininit.exe:532" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\532\Device\HarddiskVolume2\Windows\System32\wininit.exe" id="d8c2688c2c0285a669140d4ac8585834189ec67e" />
<item object="NVDisplay.Container.exe:1176" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1176\Device\HarddiskVolume2\Program Files\NVIDIA Corporation\Display.NvContainer\NVDisplay.Container.exe" id="775624a31612010dc2368f2c12f285b707e66fab" />
<item object="winlogon.exe:624" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\624\Device\HarddiskVolume2\Windows\System32\winlogon.exe" id="47c61285d51acf10502be473389adf10b9fb1edb" />
<item object="RAVCpl64.exe:2596" threat="PROC:CERT.Grey" type="unknown_malware" path="\Process\2596\Device\HarddiskVolume2\Program Files\Realtek\Audio\HDA\RAVCpl64.exe" id="ba04ac01385c7e8ab2b99e4502ae9d8a5409c236" />
<item object="services.exe:600" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\600\Device\HarddiskVolume2\Windows\System32\services.exe" id="133dc8db852e656f79124ca449c9b0c98b176c15" />
<item object="svchost.exe:168" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\168\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="04b01501aa86d5c85c975671484ee29f71313078" />
<item object="svchost.exe:1052" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1052\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="d6f8243c0569f15f4ade32ad693673d891cecaa4" />
<item object="lsm.exe:668" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\668\Device\HarddiskVolume2\Windows\System32\lsm.exe" id="42a0096b71e0ab7312e114306b9f1ef96a602c37" />
<item object="svchost.exe:764" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\764\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="a1a6bd50f4b2f45cddceaadbde6ab14cd29b5587" />
<item object="NVDisplay.Container.exe:824" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\824\Device\HarddiskVolume2\Program Files\NVIDIA Corporation\Display.NvContainer\NVDisplay.Container.exe" id="71c20bc15d9d4f206b849ae748b8dcd73e2cdf8a" />
<item object="wmpnetwk.exe:3056" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\3056\Device\HarddiskVolume2\Program Files\Windows Media Player\wmpnetwk.exe" id="4093bbe9a1d1095d920a7340f901e69f296a4e51" />
<item object="OriginWebHelperService.exe:1776" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1776\Device\HarddiskVolume2\Program Files (x86)\Origin\OriginWebHelperService.exe" id="8463b958f8abd6943a693261c33bb35157626964" />
<item object="svchost.exe:876" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\876\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="79db0a9677edd4e29c60c94daebbe79ac485a654" />
<item object="svchost.exe:1144" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1144\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="a02f8f95f6f649bf4504b435353775a47ac50f18" />
<item object="taskhost.exe:2044" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2044\Device\HarddiskVolume2\Windows\System32\taskhost.exe" id="7a20e5f569951775c763ac106b85c2ea782319fd" />
<item object="svchost.exe:980" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\980\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="2a4c4a037995e09f33bebc92813e6d8b18988978" />
<item object="spoolsv.exe:1448" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1448\Device\HarddiskVolume2\Windows\System32\spoolsv.exe" id="2e2c1b59c8749aae83dc03a509ac68c22b7273af" />
<item object="RTSSHooksLoader64.exe:2572" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2572\Device\HarddiskVolume1\MSI Afterburner\RivaTuner Statistics Server\RTSSHooksLoader64.exe" id="c7649123ac1e4759dd2cf95670eb611974602528" />
<item object="svchost.exe:1488" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1488\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="9ad0574f61c38fcb2d32697dd3f1166270dc48fc" />
<item object="OfficeClickToRun.exe:1640" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1640\Device\HarddiskVolume2\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" id="4d205d269f79d2da01b70254fa57d4e182a2d401" />
<item object="svchost.exe:1700" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1700\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="a6567920ca5c3a549980636d68eb1e4295413914" />
<item object="NvTelemetryContainer.exe:1744" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1744\Device\HarddiskVolume2\Program Files (x86)\NVIDIA Corporation\NvTelemetry\NvTelemetryContainer.exe" id="0d8c470385c60aca1fcc2874dd1d22faaba51988" />
<item object="RTSS.exe:1292" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1292\Device\HarddiskVolume1\MSI Afterburner\RivaTuner Statistics Server\RTSS.exe" id="ce74a04efe2bdab975a8e331326d99642d9ee766" />
<item object="taskeng.exe:2036" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2036\Device\HarddiskVolume2\Windows\System32\taskeng.exe" id="5fbdc4e4d42f18ba4e919e2ff0f179778e6ee395" />
<item object="dwm.exe:2200" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\2200\Device\HarddiskVolume2\Windows\System32\dwm.exe" id="c4b3b0f24bb641a4bc39f5f7498f36fd9bb48f68" />
<item object="svchost.exe:1164" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\1164\Device\HarddiskVolume2\Windows\System32\svchost.exe" id="359d25a41b06f6dabf626d21b44665903b45054f" />
<item object="TrustedInstaller.exe:4532" threat="PROC:HollowedProcess.EP" type="unknown_malware" path="\Process\4532\Device\HarddiskVolume2\Windows\servicing\TrustedInstaller.exe" data="C:\Users\аа\AppData\Local\Temp\dwsF3CA.exe " id="bbab2a2e09656405599182298301a7523c09bdeb" />
<item object="CommandLineTemplate" threat="WMI:SUSPICIOUS.Data" type="unknown_malware" path="\WMI\root\subscription\CommandLineEventConsumer{266c72e5-62e8-11d1-ad89-00c04fd8fdff}\CommandLineTemplate" data="cscript KernCap.vbs" id="d1a1dc314166b80a99c7b13c6a593d7499c1680b" />
</detects>
Если есть два способа, простой и сложный, то выбирай сложный, так как он проще простого способа, который тоже сложный, но ещё и кривой.
- Наверх
#4
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Сентябрь 2019 — 21:31
Куча непонятных либ сомнительной репутации, скринсейверы, активаторы. Сложно сказать, есть ли тут малварь, либо это просто левые либы от чего-то.
Отправить на исследование?
- Наверх
#5
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 04 Октябрь 2019 — 03:37
- Наверх
#6
Ivan Korolev
Ivan Korolev
- Virus Analysts
- 1 430 Сообщений:
Poster
Отправлено 04 Октябрь 2019 — 09:30
Вышлите на анализ, посмотрим.
- Наверх
#7
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 05 Октябрь 2019 — 02:52
Branded —#8877024
OInstall — #8877026
Euphoria — #8877027
rtvcvfw64 — #8877028
wuaueng2 — #8877030
детект-диагностика на подмену тела на целую кучу процессов
Это тоже всё рекомендуется выслать?
- Наверх
#8
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 10 Октябрь 2019 — 14:48
- Наверх
#9
Ivan Korolev
Ivan Korolev
- Virus Analysts
- 1 430 Сообщений:
Poster
Отправлено 11 Октябрь 2019 — 17:43
- Наверх
#10
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 12 Октябрь 2019 — 02:49
А что делать с подменой тела?
- Наверх
#11
RomaNNN
RomaNNN
- Posters
- 6 001 Сообщений:
Ковальски
Отправлено 15 Октябрь 2019 — 20:09
Нашли зацепку. Нужен полный дамп (Full dump) памяти системы.
Как его сделать: https://forum.drweb.com/index.php?showtopic=327797#entry830484 (см. «Как выполнить «ручной» BSOD»)
Дамп будет лежать в C:\Windows\MEMORY.DMP. Его пожать в архив и выложить куда-нибудь на облако, ссылку в личку.
Сообщение было изменено RomaNNN: 15 Октябрь 2019 — 20:14
Если есть два способа, простой и сложный, то выбирай сложный, так как он проще простого способа, который тоже сложный, но ещё и кривой.
- Наверх
#12
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 16 Октябрь 2019 — 01:41
Обновил отчёты, т. к. устанавливались дополнительные программы.
https://cloud.mail.ru/public/5NWG/5j3BNaoLe
- Наверх
#13
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 28 Октябрь 2019 — 10:24
Сколько примерно времени нужно для анализа дампа?
- Наверх
#14
RomaNNN
RomaNNN
- Posters
- 6 001 Сообщений:
Ковальски
Отправлено 28 Октябрь 2019 — 23:54
Сколько примерно времени нужно для анализа дампа?
Как только, так сразу
Попробуйте пока попробовать с последней сброкой сисинфо (по ссылке из ответа робота). Там были некоторые доработки, которые могли повлиять.
Сообщение было изменено RomaNNN: 28 Октябрь 2019 — 23:59
Если есть два способа, простой и сложный, то выбирай сложный, так как он проще простого способа, который тоже сложный, но ещё и кривой.
- Наверх
#15
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Октябрь 2019 — 01:56
Имеете в виду, собрать отчёт другой утилитой? Собрал вроде.https://cloud.mail.ru/public/H1rF/27hFA4sCc
- Наверх
#16
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Октябрь 2019 — 04:16
Хотя зачем? Посмотрел адреса, они же ведь скачиваются из одного источника.
- Наверх
#17
Konstantin Yudin
Konstantin Yudin
- Dr.Web Staff
- 19 563 Сообщений:
Смотрящий
Отправлено 29 Октябрь 2019 — 10:16
Да, но утилита по ссылке обновляется постоянно, на той неделе 6 раз обновлял. Там практически реалтайм как только что то новое придумываем, чиним или малварь какая то появляется.
With best regards, Konstantin Yudin
Doctor Web, Ltd.
- Наверх
#18
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Октябрь 2019 — 10:40
Всё равно не понятно, как по одной и той же ссылке могут скачиваться разные версии утилит.
- Наверх
#19
RomaNNN
RomaNNN
- Posters
- 6 001 Сообщений:
Ковальски
Отправлено 29 Октябрь 2019 — 10:58
Всё равно не понятно, как по одной и той же ссылке могут скачиваться разные версии утилит.
Разные — никак. Ссылка ведет на хранилище с файлом, файл скачивался старый, его обновили, теперь скачивается новый
Если есть два способа, простой и сложный, то выбирай сложный, так как он проще простого способа, который тоже сложный, но ещё и кривой.
- Наверх
#20
Smart_D15
Smart_D15
- Posters
- 669 Сообщений:
Advanced Member
Отправлено 29 Октябрь 2019 — 11:01
- Наверх
-
-
#1
Привет, коллеги.
При запуске migration assistant получаю ошибку, кто-нибудь сталкивался с подобным? Как решили проблему?
2024-06-11 07:47:36.363Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Deleting directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:47:42.486Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Successfully deleted directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:47:42.487Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::~PythonUpgradeRunnerExtractor: Successfully cleaned up temporary directory C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:53:34.378Z| migration-assistant-23179725| I: MAInit: stdout successfully changed to UTF-8 mode
2024-06-11 07:53:34.401Z| migration-assistant-23179725| W: SetMALocale: UI language id of machine 1049 is not supported.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| W: SetMALocale: Migration Assistant will use English locale.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| I: MAInit: Setting export wait count value as: 36000.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.402Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.402Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: ParseCommandLineOptions: MA launched without passing command line parameters.
2024-06-11 07:53:34.410Z| migration-assistant-23179725| I: MAInit: Initializing Migration Assistant…
2024-06-11 07:53:34.414Z| migration-assistant-23179725| I: LoadCurrentUserProfile: Successfully loaded user profile for username.
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: MAInit: Ctrl handler successfully set.
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: SanityCheckAdminPrivilege: Launching user retrieved successfully: ‘domain\username’
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: SanityCheckAdminPrivilege: Process has admin privilege.
2024-06-11 07:53:34.494Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {6ABA1091-7FFA-4342-91BC-D92A489B26E2}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {36A7C7D1-03E4-487E-9AAC-773CF118B4D8}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {84920751-2BCC-4924-A34B-31D4BAAD586C}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: Product {4B44FA5F-D350-4CD3-8FB9-B48C71F445AF} installed with UpgradeCode {869AA968-0000-FFFF-0011-110011001100}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {7E776B22-715F-40C2-9A29-878664F3D94D}
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\deployment.node.type] file is [embedded]
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for rhttpproxy.ext.port2
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\rhttpproxy.ext.port2] file is [443]
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[rhttpproxy.ext.port2] : Value=[443]
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.499Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.499Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:53:34.505Z| migration-assistant-23179725| I: Entering function: RetrieveVpxdServiceAccountUser
2024-06-11 07:53:34.505Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Query EnumProcesses with array of size: 1024
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: No. of processes: 160
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process image file name for process id:4 with error: 1060.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\smss.exe, process id: 368
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:480 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\wininit.exe, process id: 544
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:556 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\winlogon.exe, process id: 584
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\services.exe, process id: 652
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\lsass.exe, process id: 660
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 736
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 780
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\LogonUI.exe, process id: 856
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\vmacthlp.exe, process id: 876
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:884 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 932
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 956
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1020
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 444
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 452
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\spoolsv.exe, process id: 1180
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1212
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1232
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\DesktopCentral_Agent\bin\dcagentservice.exe, process id: 1252
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\mqsvc.exe, process id: 1384
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\DesktopCentral_Agent\bin\dcondemand.exe, process id: 1392
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 1432
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe, process id: 1516
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1244
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe, process id: 1460
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\vmtoolsd.exe, process id: 1152
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\python\PythonService.exe, process id: 1120
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\VSSVC.exe, process id: 2076
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 2092
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\Zabbix Agent\zabbix_agentd.exe, process id: 2152
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\VeeamVssSupport\VeeamGuestHelper.exe, process id: 2276
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\ProgramData\VMware\vCenterServer\runtime\vmware-psc-client\bin\wrapper\wrapper.exe, process id: 2488
2024-06-11 07:53:34.513Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:2520 with error: 5.
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 2568
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmafdd\vmafdd.exe, process id: 2600
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 2732
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe, process id: 2804
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmdird\vmdird.exe, process id: 2260
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmcad\vmcad.exe, process id: 3364
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmdns\vmdnsd.exe, process id: 3384
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\VMware Identity Services\VMwareIdentityMgmtService.exe, process id: 3580
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 3604
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\ProgramData\VMware\vCenterServer\runtime\VMwareSTSService\bin\wrapper.exe, process id: 3732
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 3748
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 3800
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmon\vmon.exe, process id: 1964
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 3784
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 4184
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4236 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\rhttpproxy\rhttpproxy.exe, process id: 4332
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 4348
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 5020
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 5028
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 1912
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 2724
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 1484
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 1476
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4724 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4536 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4780 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4764 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4900 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4892 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5232 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5088 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5332 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4908 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6128 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:3260 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6088 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6084 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5340 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmon\vapi\vmon-vapi-provider.exe, process id: 6768
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 6752
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 3592
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 6844
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5544 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4796 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\Kaspersky Lab\NetworkAgent\klnagent.exe, process id: 7976
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\msdtc.exe, process id: 7384
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\Kaspersky Lab\NetworkAgent\vapm.exe, process id: 7348
2024-06-11 07:53:34.515Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:7064 with error: 5.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4916 with error: 5.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vpxd\vpxd.exe, process id: 9548
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: RetrieveLogonAsUserFromProcessName: Service account is running on [NT AUTHORITY\СИСТЕМА], isLocalSystem: [1]
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: RetrieveVpxdServiceAccountUser: Default VPXD service account detected.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: Leaving function: RetrieveVpxdServiceAccountUser
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:54:07.001Z| migration-assistant-23179725| I: ValidateVcAdminCredentials: Successfully validated VC credentials for Host:localhost, Port:443, TunnelPath:, User:Administrator@vsphere.local.
2024-06-11 07:54:07.103Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Deleting directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:54:07.114Z| migration-assistant-23179725| E: RemoveDirectoryAndContents: Failed to delete directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir, Error: 2
2024-06-11 07:54:07.114Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::ExtractPythonAndUpgradeRunner: Extracting python msi.
2024-06-11 07:54:33.710Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::ExtractPythonAndUpgradeRunner: Installing upgrade runner msi.
2024-06-11 07:54:38.325Z| migration-assistant-23179725| I: InstallVC2015Redist: VC redistributable already present on this setup.
2024-06-11 07:54:38.432Z| migration-assistant-23179725| I: GetNumHosts: Aggregated host count: 37
2024-06-11 07:54:38.444Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 100
2024-06-11 07:54:38.450Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 200
2024-06-11 07:54:38.454Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 245
2024-06-11 07:54:38.458Z| migration-assistant-23179725| I: GetInventorySize: Inventory size retrieved. Hosts:37, VMs:245
2024-06-11 07:54:38.458Z| migration-assistant-23179725| I: wmain: Inventory size retrieved. Num of Hosts: 37, Num of VMs: 245
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: RunPreMigrationChecks: Running Prechecks…
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: LaunchUpgradeRunnerPreUpgradePhase: Changed the status of pre-upgrade checks to: RUNNING
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: Entering function: LaunchUpgradeRunnerCommon
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_URL
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_URL’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: //127.0.0.1:443/sso-adminserver/sdk/vsphere.local
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_URL] = ‘//127.0.0.1:443/sso-adminserver/sdk/vsphere.local’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_VERSION
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_VERSION] = ‘6.5’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_PASSWORD
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_PASSWORD’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_PASSWORD] = ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_URL
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VC_URL’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: //127.0.0.1:443
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_URL] = ‘//127.0.0.1:443’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_USERNAME
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_USERNAME’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: Administrator@vsphere.local
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_USERNAME] = ‘Administrator@vsphere.local’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VPXD_SA_USER
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VPXD_SA_USER’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was:
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VPXD_SA_USER] = »
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VPXD_SA_PASSWORD
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VPXD_SA_PASSWORD’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VPXD_SA_PASSWORD] = ***
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_SSL_THUMBPRINT
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VC_SSL_THUMBPRINT’ is not a json object
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Json was:
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_SSL_THUMBPRINT] = »
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_VERSION
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_VERSION] = ‘6.5’
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property MIGRATION_TYPE
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘MIGRATION_TYPE’ is not a json object
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Json was: embedded
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [MIGRATION_TYPE] = ’embedded’
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property USER_OPTIONS
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [USER_OPTIONS] with json object
2024-06-11 07:54:38.465Z| migration-assistant-23179725| I: CreateShortSymbolicLink: Symbolic link ‘C:\migDBC6.tmp’ created for path ‘C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir’.
2024-06-11 07:54:38.466Z| migration-assistant-23179725| I: LaunchUpgradeRunnerCommon: File C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json does not exist.
2024-06-11 07:54:38.466Z| migration-assistant-23179725| I: Entering function: LaunchProcAndMonitorStatus
2024-06-11 07:54:38.468Z| migration-assistant-23179725| I: LaunchProcAndMonitorStatus: Launching «»C:\migDBC6.tmp\PFiles\VMware\CIS\python\python.exe» «C:\migDBC6.tmp\PFiles\VMware\CIS\cis_upgrade_runner\UpgradeOrchestrator.py» —mode=requirements —configFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json» —logDir=»C:\Users\username\AppData\Local\Temp\vcsMigration» —locale=en —outputFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json»» in «C:\migDBC6.tmp\PFiles\VMware\CIS\python\»
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: LaunchProcAndMonitorStatus: Launched process with pid 14424 tid 16272
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: Entering function: MonitorStatusFile
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: MonitorStatusFile: Started execution of process
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Other process terminated with 1, exiting
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: MonitorStatusFile: Process exited with a non-zero exit code; no status monitoring so assuming failure
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: called parse callback 0 times
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: No need to wait for process to complete
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Process’s job tree still hasn’t terminated, waiting
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Wait on process’s job tree has completed: 0
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: Leaving function: MonitorStatusFile
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: LaunchProcAndMonitorStatus: Failure detected while monitoring status file
2024-06-11 07:55:36.889Z| migration-assistant-23179725| W: LaunchProcAndMonitorStatus: Job still alive, terminating
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: Leaving function: LaunchProcAndMonitorStatus
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: LaunchUpgradeRunnerCommon: Failed to run pre-upgrade phase: «C:\migDBC6.tmp\PFiles\VMware\CIS\python\python.exe» «C:\migDBC6.tmp\PFiles\VMware\CIS\cis_upgrade_runner\UpgradeOrchestrator.py» —mode=requirements —configFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json» —logDir=»C:\Users\username\AppData\Local\Temp\vcsMigration» —locale=en —outputFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json»
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: RemoveDirectoryIfEmpty: Successfully deleted empty directory C:\migDBC6.tmp.
2024-06-11 07:55:36.890Z| migration-assistant-23179725| I: LaunchUpgradeRunnerCommon: Successfully deleted file: C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json
2024-06-11 07:55:36.890Z| migration-assistant-23179725| I: Leaving function: LaunchUpgradeRunnerCommon
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.netdump’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vsan-health’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.rbd’: Export disk req [20 MB], Export time estimate [3 mins] and Import time estimate [2 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.rhttpproxy’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.sps’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [10 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vpxd’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.sso’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vmafd’: Export disk req [1536 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.ngc’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.is’: Export disk req [1024 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.common_upgrade’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘upgrade_framework’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Database settings: Type=»
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: VC machine/cert parameters. AppNetPnid: [], CertIPs: [], CertFQDNs: [].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: SSO machine/cert parameters. AppNetPnid: [vcenter.vsphere.local], CertIPs: [], CertFQDNs: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: VMAFD cert parameters. AppNetPnid: [vcenter.vsphere.local], CertIPs: [], CertFQDNs: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Retrieved infra node address: [127.0.0.1] and sso.sts.url [https://vcenter.vsphere.local/sts/STSService/vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Setting AppNetPnid to [vcenter.vsphere.local]
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Certificate values retrieved IP Addresses: [] DNS Names: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: LaunchUpgradeRunnerPreUpgradePhase: Changed the status of pre-upgrade checks to: FINISHED
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: RunPreMigrationChecks: Upgrade Runner prechecks returned status: 1603
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vcdb
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.netdump
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vsan-health
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.rbd
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.rhttpproxy
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.sps
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vpxd
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.sso
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vmafd
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.ngc
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.is
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.common_upgrade
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component upgrade_framework
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Parsed 1 error messages.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Error messages: Error: Internal error occurs during VMware vCenter Server Database pre-upgrade checks.
Resolution: Please search for these symptoms in the VMware Knowledge Base for any known issues and possible resolutions. If none can be found, collect a support bundle and open a support request.
2024-06-11 07:55:37.096Z| migration-assistant-23179725| I: CreateEmptyZipFile: Successfully created empty zip file
-
-
#2
ну вроде написано что локаль не нравится
-
-
#3
почему то еще с версии vsphere 4.4 все мои попытки честно, плавно мигрировать / обновиться на новый вцентр сводились к тому что он либо обновлялся с косяками или вообще не обновлялся. Поскольку distributed switch не было и инфра не особо большая то ставил всегда с нуля и загонял кластеры заново
-
-
#4
Привет, коллеги.
При запуске migration assistant получаю ошибку, кто-нибудь сталкивался с подобным? Как решили проблему?2024-06-11 07:47:36.363Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Deleting directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:47:42.486Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Successfully deleted directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:47:42.487Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::~PythonUpgradeRunnerExtractor: Successfully cleaned up temporary directory C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:53:34.378Z| migration-assistant-23179725| I: MAInit: stdout successfully changed to UTF-8 mode
2024-06-11 07:53:34.401Z| migration-assistant-23179725| W: SetMALocale: UI language id of machine 1049 is not supported.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| W: SetMALocale: Migration Assistant will use English locale.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| I: MAInit: Setting export wait count value as: 36000.
2024-06-11 07:53:34.401Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.402Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.402Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:53:34.403Z| migration-assistant-23179725| I: ParseCommandLineOptions: MA launched without passing command line parameters.
2024-06-11 07:53:34.410Z| migration-assistant-23179725| I: MAInit: Initializing Migration Assistant…
2024-06-11 07:53:34.414Z| migration-assistant-23179725| I: LoadCurrentUserProfile: Successfully loaded user profile for username.
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: MAInit: Ctrl handler successfully set.
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: SanityCheckAdminPrivilege: Launching user retrieved successfully: ‘domain\username’
2024-06-11 07:53:34.416Z| migration-assistant-23179725| I: SanityCheckAdminPrivilege: Process has admin privilege.
2024-06-11 07:53:34.494Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {6ABA1091-7FFA-4342-91BC-D92A489B26E2}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {36A7C7D1-03E4-487E-9AAC-773CF118B4D8}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {84920751-2BCC-4924-A34B-31D4BAAD586C}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: Product {4B44FA5F-D350-4CD3-8FB9-B48C71F445AF} installed with UpgradeCode {869AA968-0000-FFFF-0011-110011001100}
2024-06-11 07:53:34.495Z| migration-assistant-23179725| I: GetProductCodeFromUpgradeCode: No products found for UpgradeCode {7E776B22-715F-40C2-9A29-878664F3D94D}
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\deployment.node.type] file is [embedded]
2024-06-11 07:53:34.496Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for rhttpproxy.ext.port2
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\rhttpproxy.ext.port2] file is [443]
2024-06-11 07:53:34.497Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[rhttpproxy.ext.port2] : Value=[443]
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.498Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.499Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.499Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:53:34.505Z| migration-assistant-23179725| I: Entering function: RetrieveVpxdServiceAccountUser
2024-06-11 07:53:34.505Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Query EnumProcesses with array of size: 1024
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: No. of processes: 160
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process image file name for process id:4 with error: 1060.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\smss.exe, process id: 368
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:480 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\wininit.exe, process id: 544
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:556 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\winlogon.exe, process id: 584
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\services.exe, process id: 652
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\lsass.exe, process id: 660
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 736
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 780
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\LogonUI.exe, process id: 856
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\vmacthlp.exe, process id: 876
2024-06-11 07:53:34.512Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:884 with error: 5.
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 932
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 956
2024-06-11 07:53:34.512Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1020
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 444
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 452
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\spoolsv.exe, process id: 1180
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1212
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1232
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\DesktopCentral_Agent\bin\dcagentservice.exe, process id: 1252
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\mqsvc.exe, process id: 1384
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\DesktopCentral_Agent\bin\dcondemand.exe, process id: 1392
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 1432
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe, process id: 1516
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 1244
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe, process id: 1460
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\vmtoolsd.exe, process id: 1152
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\python\PythonService.exe, process id: 1120
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\VSSVC.exe, process id: 2076
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 2092
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\Zabbix Agent\zabbix_agentd.exe, process id: 2152
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\VeeamVssSupport\VeeamGuestHelper.exe, process id: 2276
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\ProgramData\VMware\vCenterServer\runtime\vmware-psc-client\bin\wrapper\wrapper.exe, process id: 2488
2024-06-11 07:53:34.513Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:2520 with error: 5.
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 2568
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmafdd\vmafdd.exe, process id: 2600
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 2732
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe, process id: 2804
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmdird\vmdird.exe, process id: 2260
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmcad\vmcad.exe, process id: 3364
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmdns\vmdnsd.exe, process id: 3384
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\VMware Identity Services\VMwareIdentityMgmtService.exe, process id: 3580
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 3604
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\ProgramData\VMware\vCenterServer\runtime\VMwareSTSService\bin\wrapper.exe, process id: 3732
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 3748
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 3800
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmon\vmon.exe, process id: 1964
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 3784
2024-06-11 07:53:34.513Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\svchost.exe, process id: 4184
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4236 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\rhttpproxy\rhttpproxy.exe, process id: 4332
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 4348
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 5020
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 5028
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 1912
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 2724
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 1484
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 1476
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4724 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4536 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4780 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4764 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4900 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4892 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5232 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5088 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5332 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4908 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6128 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:3260 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6088 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:6084 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5340 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vmon\vapi\vmon-vapi-provider.exe, process id: 6768
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 6752
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\jre\bin\java.exe, process id: 3592
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\conhost.exe, process id: 6844
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:5544 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4796 with error: 5.
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\Kaspersky Lab\NetworkAgent\klnagent.exe, process id: 7976
2024-06-11 07:53:34.514Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Windows\System32\msdtc.exe, process id: 7384
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files (x86)\Kaspersky Lab\NetworkAgent\vapm.exe, process id: 7348
2024-06-11 07:53:34.515Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:7064 with error: 5.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| E: GetProcessHandleFromProcessName: Failed to get process handle for process id:4916 with error: 5.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetProcessHandleFromProcessName: Process name: \Device\HarddiskVolume2\Program Files\VMware\vCenter Server\vpxd\vpxd.exe, process id: 9548
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: RetrieveLogonAsUserFromProcessName: Service account is running on [NT AUTHORITY\СИСТЕМА], isLocalSystem: [1]
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: RetrieveVpxdServiceAccountUser: Default VPXD service account detected.
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: Leaving function: RetrieveVpxdServiceAccountUser
2024-06-11 07:53:34.515Z| migration-assistant-23179725| I: GetInstallParameter: Retrieving the data for vmdir.domain-name
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetPdtConfigDirPath: ENV_VMWARE_CFG_DIR directory path is C:\ProgramData\VMware\vCenterServer\cfg
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetInstallDefaultsDirPath: install-defaults directory path is C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetFileContents: Contents from [C:\ProgramData\VMware\vCenterServer\cfg\install-defaults\vmdir.domain-name] file is [vsphere.local]
2024-06-11 07:53:34.517Z| migration-assistant-23179725| I: GetInstallParameter: PropertyName=[vmdir.domain-name] : Value=[vsphere.local]
2024-06-11 07:54:07.001Z| migration-assistant-23179725| I: ValidateVcAdminCredentials: Successfully validated VC credentials for Host:localhost, Port:443, TunnelPath:, User:Administrator@vsphere.local.
2024-06-11 07:54:07.103Z| migration-assistant-23179725| I: RemoveDirectoryAndContents: Deleting directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir
2024-06-11 07:54:07.114Z| migration-assistant-23179725| E: RemoveDirectoryAndContents: Failed to delete directory: C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir, Error: 2
2024-06-11 07:54:07.114Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::ExtractPythonAndUpgradeRunner: Extracting python msi.
2024-06-11 07:54:33.710Z| migration-assistant-23179725| I: PythonUpgradeRunnerExtractor::ExtractPythonAndUpgradeRunner: Installing upgrade runner msi.
2024-06-11 07:54:38.325Z| migration-assistant-23179725| I: InstallVC2015Redist: VC redistributable already present on this setup.
2024-06-11 07:54:38.432Z| migration-assistant-23179725| I: GetNumHosts: Aggregated host count: 37
2024-06-11 07:54:38.444Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 100
2024-06-11 07:54:38.450Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 200
2024-06-11 07:54:38.454Z| migration-assistant-23179725| I: GetNumVMs: Aggregated vm count: 245
2024-06-11 07:54:38.458Z| migration-assistant-23179725| I: GetInventorySize: Inventory size retrieved. Hosts:37, VMs:245
2024-06-11 07:54:38.458Z| migration-assistant-23179725| I: wmain: Inventory size retrieved. Num of Hosts: 37, Num of VMs: 245
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: RunPreMigrationChecks: Running Prechecks…
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: LaunchUpgradeRunnerPreUpgradePhase: Changed the status of pre-upgrade checks to: RUNNING
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: Entering function: LaunchUpgradeRunnerCommon
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_URL
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_URL’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: //127.0.0.1:443/sso-adminserver/sdk/vsphere.local
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_URL] = ‘//127.0.0.1:443/sso-adminserver/sdk/vsphere.local’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_VERSION
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_VERSION] = ‘6.5’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_PASSWORD
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_PASSWORD’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_PASSWORD] = ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_URL
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VC_URL’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: //127.0.0.1:443
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_URL] = ‘//127.0.0.1:443’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property SSO_USERNAME
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘SSO_USERNAME’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: Administrator@vsphere.local
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [SSO_USERNAME] = ‘Administrator@vsphere.local’
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VPXD_SA_USER
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VPXD_SA_USER’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was:
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VPXD_SA_USER] = »
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VPXD_SA_PASSWORD
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VPXD_SA_PASSWORD’ is not a json object
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: GetJsonProperty: Json was: ***
2024-06-11 07:54:38.463Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VPXD_SA_PASSWORD] = ***
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_SSL_THUMBPRINT
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘VC_SSL_THUMBPRINT’ is not a json object
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Json was:
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_SSL_THUMBPRINT] = »
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property VC_VERSION
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [VC_VERSION] = ‘6.5’
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property MIGRATION_TYPE
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Property ‘MIGRATION_TYPE’ is not a json object
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: GetJsonProperty: Json was: embedded
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [MIGRATION_TYPE] = ’embedded’
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Handling property USER_OPTIONS
2024-06-11 07:54:38.464Z| migration-assistant-23179725| I: JsonResolveProperty: Substituting [USER_OPTIONS] with json object
2024-06-11 07:54:38.465Z| migration-assistant-23179725| I: CreateShortSymbolicLink: Symbolic link ‘C:\migDBC6.tmp’ created for path ‘C:\Users\username\AppData\Local\VMware\Migration-Assistant\PythonURExtractDir’.
2024-06-11 07:54:38.466Z| migration-assistant-23179725| I: LaunchUpgradeRunnerCommon: File C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json does not exist.
2024-06-11 07:54:38.466Z| migration-assistant-23179725| I: Entering function: LaunchProcAndMonitorStatus
2024-06-11 07:54:38.468Z| migration-assistant-23179725| I: LaunchProcAndMonitorStatus: Launching «»C:\migDBC6.tmp\PFiles\VMware\CIS\python\python.exe» «C:\migDBC6.tmp\PFiles\VMware\CIS\cis_upgrade_runner\UpgradeOrchestrator.py» —mode=requirements —configFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json» —logDir=»C:\Users\username\AppData\Local\Temp\vcsMigration» —locale=en —outputFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json»» in «C:\migDBC6.tmp\PFiles\VMware\CIS\python\»
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: LaunchProcAndMonitorStatus: Launched process with pid 14424 tid 16272
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: Entering function: MonitorStatusFile
2024-06-11 07:54:38.484Z| migration-assistant-23179725| I: MonitorStatusFile: Started execution of process
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Other process terminated with 1, exiting
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: MonitorStatusFile: Process exited with a non-zero exit code; no status monitoring so assuming failure
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: called parse callback 0 times
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: No need to wait for process to complete
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Process’s job tree still hasn’t terminated, waiting
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: MonitorStatusFile: Wait on process’s job tree has completed: 0
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: Leaving function: MonitorStatusFile
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: LaunchProcAndMonitorStatus: Failure detected while monitoring status file
2024-06-11 07:55:36.889Z| migration-assistant-23179725| W: LaunchProcAndMonitorStatus: Job still alive, terminating
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: Leaving function: LaunchProcAndMonitorStatus
2024-06-11 07:55:36.889Z| migration-assistant-23179725| E: LaunchUpgradeRunnerCommon: Failed to run pre-upgrade phase: «C:\migDBC6.tmp\PFiles\VMware\CIS\python\python.exe» «C:\migDBC6.tmp\PFiles\VMware\CIS\cis_upgrade_runner\UpgradeOrchestrator.py» —mode=requirements —configFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json» —logDir=»C:\Users\username\AppData\Local\Temp\vcsMigration» —locale=en —outputFile=»C:\Users\username\AppData\Local\Temp\UpgradeRunnerPreupgradeOutput.json»
2024-06-11 07:55:36.889Z| migration-assistant-23179725| I: RemoveDirectoryIfEmpty: Successfully deleted empty directory C:\migDBC6.tmp.
2024-06-11 07:55:36.890Z| migration-assistant-23179725| I: LaunchUpgradeRunnerCommon: Successfully deleted file: C:\Users\username\AppData\Local\Temp\UpgradeRunnerInput.json
2024-06-11 07:55:36.890Z| migration-assistant-23179725| I: Leaving function: LaunchUpgradeRunnerCommon
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.netdump’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vsan-health’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.rbd’: Export disk req [20 MB], Export time estimate [3 mins] and Import time estimate [2 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.rhttpproxy’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.sps’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [10 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vpxd’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.sso’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.vmafd’: Export disk req [1536 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.ngc’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.is’: Export disk req [1024 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘com.vmware.common_upgrade’: Export disk req [10 MB], Export time estimate [1 mins] and Import time estimate [1 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParseExportEstimatesFromPreUpgradeOutput: Component ‘upgrade_framework’: Export disk req [0 MB], Export time estimate [0 mins] and Import time estimate [0 mins].
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Database settings: Type=»
2024-06-11 07:55:36.891Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: VC machine/cert parameters. AppNetPnid: [], CertIPs: [], CertFQDNs: [].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: SSO machine/cert parameters. AppNetPnid: [vcenter.vsphere.local], CertIPs: [], CertFQDNs: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: VMAFD cert parameters. AppNetPnid: [vcenter.vsphere.local], CertIPs: [], CertFQDNs: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Retrieved infra node address: [127.0.0.1] and sso.sts.url [https://vcenter.vsphere.local/sts/STSService/vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Setting AppNetPnid to [vcenter.vsphere.local]
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParsePreUpgradeOutput: Certificate values retrieved IP Addresses: [] DNS Names: [vcenter.vsphere.local].
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: LaunchUpgradeRunnerPreUpgradePhase: Changed the status of pre-upgrade checks to: FINISHED
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: RunPreMigrationChecks: Upgrade Runner prechecks returned status: 1603
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vcdb
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.netdump
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vsan-health
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.rbd
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.892Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.rhttpproxy
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.sps
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vpxd
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.sso
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.vmafd
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.ngc
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.is
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component com.vmware.common_upgrade
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Processing pre-upgrade for component upgrade_framework
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: No mismatch to process.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Parsed 1 error messages.
2024-06-11 07:55:36.893Z| migration-assistant-23179725| I: ParseErrorsWarningsFromPreUpgradeOutput: Error messages: Error: Internal error occurs during VMware vCenter Server Database pre-upgrade checks.
Resolution: Please search for these symptoms in the VMware Knowledge Base for any known issues and possible resolutions. If none can be found, collect a support bundle and open a support request.
2024-06-11 07:55:37.096Z| migration-assistant-23179725| I: CreateEmptyZipFile: Successfully created empty zip file
может версии не поддерживаются ? Это с какой на какую ?
-
-
#5
может версии не поддерживаются ? Это с какой на какую ?
Это с виндового вицентра 6.5 на 7.0 (пробовал и на 6.7).
почему то еще с версии vsphere 4.4 все мои попытки честно, плавно мигрировать / обновиться на новый вцентр сводились к тому что он либо обновлялся с косяками или вообще не обновлялся. Поскольку distributed switch не было и инфра не особо большая то ставил всегда с нуля и загонял кластеры заново
Я вот тоже, пару дней погуглил, уже развернул с нуля. Есть потом способ в Veeam плавно все задачи переделать? Если в каждой джобе перевыбрать из новой сферы он же наверняка не продолжит инкременты делать, начнет фулы?
Локаль пробовал поменять на англ, там сейчас русская винда 12r2
-
-
#6
Это с виндового вицентра 6.5 на 7.0 (пробовал и на 6.7).
Я вот тоже, пару дней погуглил, уже развернул с нуля. Есть потом способ в Veeam плавно все задачи переделать? Если в каждой джобе перевыбрать из новой сферы он же наверняка не продолжит инкременты делать, начнет фулы?
Локаль пробовал поменять на англ, там сейчас русская винда 12r2
Поставь с нуля vcenter. С винды на vcsa херово переезжает. ЕМНИП можно в виме сделать рескан бэкапов или инвентаризацию что то такое или это map backup называется — не помню. Он подтянет старые и начнет туда дописывать.
-
-
#7
Поставь с нуля vcenter. С винды на vcsa херово переезжает. ЕМНИП можно в виме сделать рескан бэкапов или инвентаризацию что то такое или это map backup называется — не помню. Он подтянет старые и начнет туда дописывать.
С нуля развернул vcsa. Рескан бэкапов, емнип, нужен при переносе в другой репозиторий. Сейчас переношу хосты и переделываю задачи вима (надо перевыбрать вм из новой сферы). Он их автоматом не находит
Verfasst von: mountainbrother — 20. März 2012
Description:
Windows detected your registry file is still in use by other applications or services. The file will be unloaded now. The applications or services that hold your registry file may not function properly afterwards.
DETAIL –
2 user registry handles leaked from \Registry\User\S-1-5-21-2890941510-4003794996-2168266983-5128:
Process 2696 (\Device\HarddiskVolume2\Windows\System32\winlogon.exe) has opened key \REGISTRY\USER\S-1-5-21-2890941510-4003794996-2168266983-5128
Process 996 (\Device\HarddiskVolume2\Windows\System32\svchost.exe) has opened key \REGISTRY\USER\S-1-5-21-2890941510-4003794996-2168266983-5128\Printers\DevModePerUser
http://support.microsoft.com/kb/947238
here is a workaround , but not the solution for the Problem:
A. Click Start | Run and type „msconfig“ (no quotes) and press enter.
B. Click services from the tab, check the check box of „Hide All Microsoft
Service“, and then click „Disable all“
C. Click Startup from the tab, then click „Disable all“
D. Click „OK“ and follow the instructions to Restart Computer, after rebooting if
you get a prompt dialog of System Configuration, please check the check box in the
dialog and click „OK“.
As a temporary work around we have carried out the following.
Disable the „User Profile Service“.
Reboot.
Log on with local admin account.
Remove the problematic profiles.
Remove reference to the specific problematic profiles from registry at:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
Log off
Log on with local admin account.
Set „User profile Service“ to start automatically.
Reboot
Log back on as problematic account and changes have been saved
We found 0ut after days of monitoring that the source of the error is the Antivirussolution.
The realtimescanner was to slow for the svchost.exe and so the profile service crash
After Deinstallation from the Scanner everythink works great again.
Now i search for a good Terminalserver Antivirsoltion
This entry was posted on 20. März 2012 um 07:29 and is filed under Allgemein.
You can follow any responses to this entry through the RSS 2.0 feed.
You can leave a response, oder trackback from your own site.