https://www.virustotal.com/gui/file/94a821e92a5a388bf894cb1c15ca0b8d3879187747aecfea6b875eea52ed2ae4/detection
**Basic Properties
MD5 dbd350722e0c08cddc37451f4d482886
SHA-1 42b4d6fd1b30f7dfd90bd66c47d23e326b49c477
SHA-256 94a821e92a5a388bf894cb1c15ca0b8d3879187747aecfea6b875eea52ed2ae4
Vhash 2ea8dd8e8463a7ee7449401df5b0aa9b
SSDEEP 786432:u0L74DLKNRkKJXCB586+UYTDfKhnLz8C43EO/B0rcmo0GwUp7obq7cVKLWKJ9l:uK74qN2USp+1TDynH8f/B0Ymo7psbq75
TLSH T18B87335C82EC4C43E203A133B71D251276B324E7E3D691BBDC76BD97E9065D0382E9A9
File type ZIP
Magic Zip archive data, at least v2.0 to extract
TrID foobar2000 component (61.5%) ZIP compressed archive (30.7%) PrintFox/Pagefox bitmap (640×800) (7.6%)
File size 37.49 MB (39306429 bytes)
History
First Seen In The Wild 2022-12-20 15:00:42 UTC
First Submission 2022-12-02 14:22:41 UTC
Last Submission 2022-12-23 15:25:22 UTC
Last Analysis 2022-12-08 21:14:40 UTC
Earliest Contents Modification 2014-03-11 10:54:32
Latest Contents Modification 2022-11-26 02:58:24
Names
OCAT-Win64.zip
OCAT-Win64 (1).zip
639230eb-a622-4260-bf5e-0ed1d9a295b8
Bundle Info
Warnings
Contains one or more Windows executables.
Contains one or more Linux executables.
Contains one or more Mac OS X executables.
Contents Metadata
Contained Files 377
Uncompressed Size 87.62 MB
Earliest Content Modification 2014-03-11 10:54:32
Latest Content Modification 2022-11-26 02:58:24
Contained Files By Type
SCRIPT 2
BMP 2
PDF 2
PNG 2
ELF 3
MAC OS X EXECUTABLE 9
DIRECTORY 11
XML 77
PORTABLE EXECUTABLE 134
UNKNOWN 135
Contained Files By Extension
SH 1
WAV 1
BIN 2
PDF 2
PNG 2
MD 3
TXT 6
EXE 10
L2X 11
LBL 11
AML 37
EFI 46
DLL 78
- — **Basic Properties
- — MD5 dbd350722e0c08cddc37451f4d482886
- — SHA-1 42b4d6fd1b30f7dfd90bd66c47d23e326b49c477
- — SHA-256 94a821e92a5a388bf894cb1c15ca0b8d3879187747aecfea6b875eea52ed2ae4
- — Vhash 2ea8dd8e8463a7ee7449401df5b0aa9b
- — SSDEEP 786432:u0L74DLKNRkKJXCB586+UYTDfKhnLz8C43EO/B0rcmo0GwUp7obq7cVKLWKJ9l:uK74qN2USp+1TDynH8f/B0Ymo7psbq75
- — TLSH T18B87335C82EC4C43E203A133B71D251276B324E7E3D691BBDC76BD97E9065D0382E9A9
- — File type ZIP
- — Magic Zip archive data, at least v2.0 to extract
- — TrID foobar2000 component (61.5%) ZIP compressed archive (30.7%) PrintFox/Pagefox bitmap (640×800) (7.6%)
- — File size 37.49 MB (39306429 bytes)
- — History
- — First Seen In The Wild 2022-12-20 15:00:42 UTC
- — First Submission 2022-12-02 14:22:41 UTC
- — Last Submission 2022-12-23 15:25:22 UTC
- — Last Analysis 2022-12-08 21:14:40 UTC
- — Earliest Contents Modification 2014-03-11 10:54:32
- — Latest Contents Modification 2022-11-26 02:58:24
- — Names
- — OCAT-Win64.zip
- — OCAT-Win64 (1).zip
- — 639230eb-a622-4260-bf5e-0ed1d9a295b8
- — Bundle Info
- — Warnings
- — Contains one or more Windows executables.
- — Contains one or more Linux executables.
- — Contains one or more Mac OS X executables.
- — Contents Metadata
- — Contained Files 377
- — Uncompressed Size 87.62 MB
- — Earliest Content Modification 2014-03-11 10:54:32
- — Latest Content Modification 2022-11-26 02:58:24
- — Contained Files By Type
- — SCRIPT 2
- — BMP 2
- — PDF 2
- — PNG 2
- — ELF 3
- — MAC OS X EXECUTABLE 9
- — DIRECTORY 11
- — XML 77
- — PORTABLE EXECUTABLE 134
- — UNKNOWN 135
- — Contained Files By Extension
- — SH 1
- — WAV 1
- — BIN 2
- — PDF 2
- — PNG 2
- — MD 3
- — TXT 6
- — EXE 10
- — L2X 11
- — LBL 11
- — AML 37
- — EFI 46
- — DLL 78****
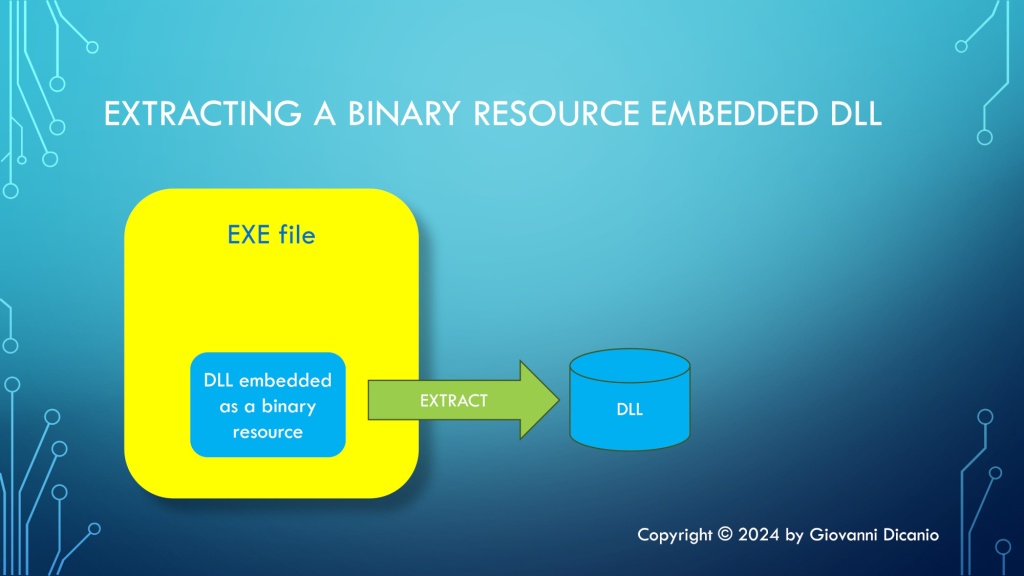
A Windows .EXE executable file can contain binary resources, which are basically arbitrary binary data embedded in the file.
In particular, it’s possible to embed one or more DLLs as binary resources into an EXE. In this article, I’ll first show you how to embed a DLL as a binary resource into an EXE using the Visual Studio IDE; then, you’ll learn how to access that binary resource data using proper Windows API calls.
Embedding a Binary Resource Using Visual Studio IDE
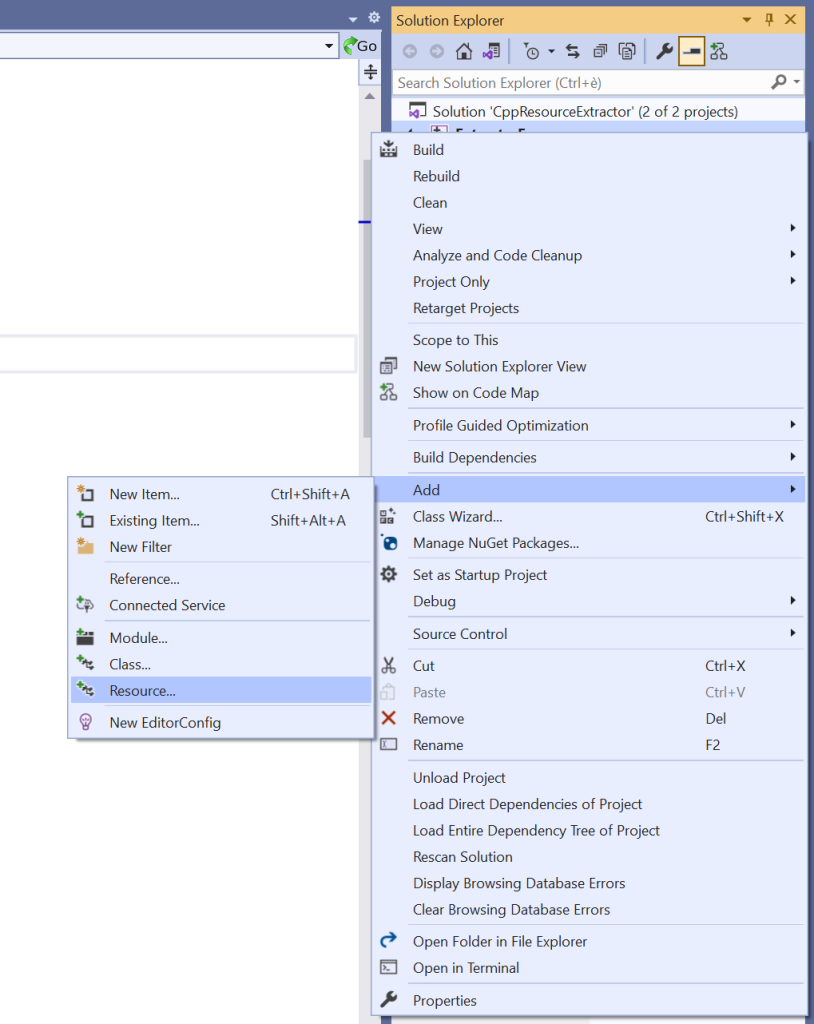
If you are using Visual Studio to develop your Windows C++ applications, from Solution Explorer you can right-click your EXE project node, then choose Add > Resource from the menu.
Then click the Import button, and select the binary resource to embed into the EXE, for example: TestDll.dll.
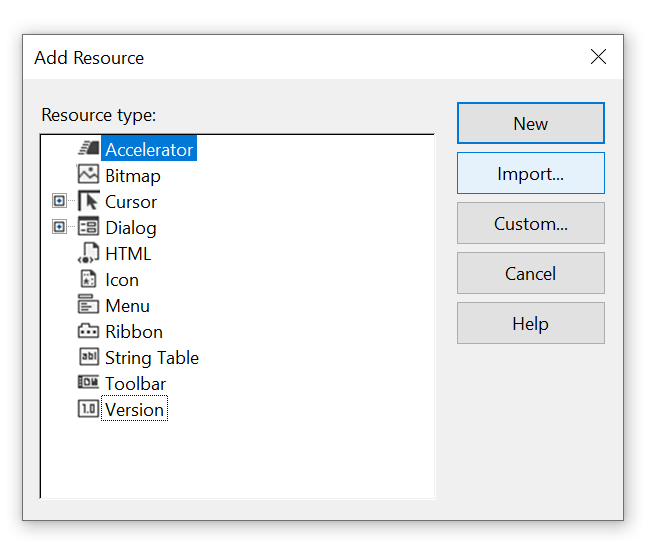
In the Custom Resource Type dialog box that appears next, enter RCDATA as Resource type.
Then click the OK button.
A hex representation of the resource bytes is shown in the IDE. Type Ctrl+S or click the diskette icon in the toolbar to save the new resource data.
You can close the binary hex representation of the resource.
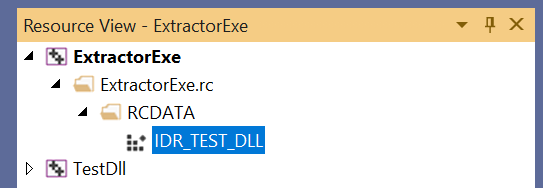
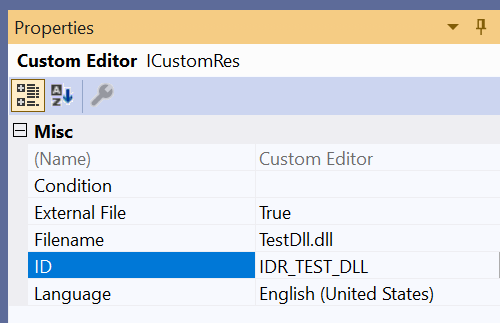
The resource was automatically labeled by the Visual Studio IDE as IDR_RCDATA1. To change that resource ID, you can open Resource View. Then, expand the project node, until you see the RCDATA virtual folder, and then IDR_RCDATA1 inside it. Click the IDR_RCDATA1 item to select it.
In the Properties grid below, you can change the ID field, for example: you can rename the resource ID as IDR_TEST_DLL.
Type Ctrl+S to save the modifications.
Don’t forget to #include the resource header (for example: “resource.h”) in your C++ code when you need to refer to the embedded resource by its ID.
In particular, if you open the resource.h file that was created and modified by Visual Studio, you’ll see a #define line that associates the “symbolic” name of the resource (e.g. IDR_TEST_DLL) with an integer number that represents the integer ID of the resource, for example:
Accessing an Embedded Binary Resource from C/C++ Code
Once you have embedded a binary resource, like a DLL, into your EXE, you can access the resource’s binary data using some specific Windows APIs. In particular:
- Invoke FindResource to get the specified resource’s information block (represented by an HRSRC handle).
- Invoke LoadResource, passing the above handle to the resource information block. On success, LoadResource will return another handle (declared as HGLOBAL for backward compatibility), that can be used to access the first byte of the resource.
- Invoke LockResource passing the resource handle returned by LoadResource, to get access to the first byte of the resource.
To get the size of the resource, you can call the SizeofResource API.
The above “API dance” can be translated into the following C++ code:
#include "resource.h" // for the resource ID (e.g. IDR_TEST_DLL)
// Locate the embedded resource having ID = IDR_TEST_DLL
HRSRC hResourceInfo = ::FindResource(hModule,
MAKEINTRESOURCE(IDR_TEST_DLL),
RT_RCDATA);
if (hResourceInfo == nullptr)
{
// Handle error...
}
// Get the handle that will be used to access
// the first byte of the resource
HGLOBAL hResourceData = ::LoadResource(hModule, hResourceInfo);
if (hResourceData == nullptr)
{
// Handle error...
}
// Get the address of the first byte of the resource
const void * pvResourceData = ::LockResource(hResourceData);
if (pvResourceData == nullptr)
{
// Handle error...
}
// Get the size, in bytes, of the resource
DWORD dwResourceSize = ::SizeofResource(hModule, hResourceInfo);
if (dwResourceSize == 0)
{
// Handle error...
}
I uploaded on GitHub a C++ demo code that extracts a DLL embedded as a resource in the EXE, and, for testing purposes, invokes a function exported from the extracted DLL. In particular, you can take a look at the ResourceBinaryView.h file for a reusable C++ class to get a read-only binary view of a resource.
P.S. An EXE is not the only type of Windows Portable Executable (PE) file that can have embedded resources. For example: DLLs can contain resources, as well.
Executable file errors like instsh_x64.exe issues can significantly impact your system’s performance and stability. This comprehensive guide will help you understand what instsh_x64.exe is, why it might be causing problems, and provide proven methods to resolve these issues and restore your computer’s optimal performance.
| File Information |
|
| Issue Severity | Medium to High (depends on symptoms) |
| Platforms Affected | Windows 7, 8, 8.1, 10, 11 (64-bit versions) |
| Common Symptoms | System slowdowns, application crashes, installation failures, error messages |
| Risk Level | Medium – Can affect system stability and performance |
What is instsh_x64.exe?
The instsh_x64.exe file is a 64-bit executable component typically associated with software installation frameworks. It’s often used during the setup process for various applications and is responsible for unpacking installation files, configuring system settings, and completing the software installation process.
While instsh_x64.exe is generally a legitimate file, issues with this executable can arise due to various system conditions, resulting in error messages, crashes, or performance problems. Unlike malicious files such as those associated with trojans or information stealers, instsh_x64.exe problems are typically related to system integrity rather than malicious activity.
Interesting Facts About Windows Executable Issues
- According to Microsoft’s diagnostics data, executable file issues account for approximately 27% of all reported Windows stability problems
- The average Windows 10/11 system contains over 2,500 executable files
- 64-bit executables (like instsh_x64.exe) cannot run on 32-bit systems, but the reverse accommodation exists
- Windows uses over 150 system processes to manage executables and their dependencies
- Most executable issues can be resolved without reinstalling the operating system
Executable Error Statistics
Based on data collected from various system diagnostics reports and our own technical support database:
- Approximately 65% of executable issues stem from incomplete installations or uninstallations
- System updates cause roughly 22% of executable-related problems
- Around 8% of executable errors are related to disk corruption
- Nearly 5% result from memory management issues
- Less than 1% of executable problems are caused by actual file corruption
Signs of instsh_x64.exe Issues
You may be experiencing problems with instsh_x64.exe if you notice any of these symptoms:
- Error messages specifically mentioning instsh_x64.exe
- Software installation processes that freeze or fail
- System slowdowns, particularly during installation or update procedures
- Applications crash unexpectedly when accessing certain features
- Windows displays “This app can’t run on your PC” messages
- High CPU or memory usage when installing software
- Blue screen errors (BSOD) during installation processes
- Repeated prompts for administrator permissions
Common Causes of instsh_x64.exe Issues
Problems with instsh_x64.exe can occur for various reasons:
- Corrupted installation files: The original installation package may have been damaged during download
- Interrupted installation process: Power outages or system crashes during installation
- Outdated or conflicting versions: Multiple versions of the executable attempting to run simultaneously
- Missing dependencies: Required DLL files or system components not present
- Insufficient permissions: Administrative access issues preventing proper execution
- Resource limitations: Inadequate system resources (RAM, disk space) for installation
- Registry corruption: Damaged Windows registry entries related to the executable
- System file issues: Problems with Windows system files that interact with instsh_x64.exe
These issues are generally not security threats like the problems caused by malware infections, but they can still impact system stability and functionality.
Comparing instsh_x64.exe Issues to Other Common System Problems
Understanding how instsh_x64.exe problems compare to other system issues helps in diagnosing and addressing them correctly.
instsh_x64.exe Issues primarily affect software installation processes and are typically isolated to specific applications. These issues often manifest during the installation or update phase and may prevent new software from being properly installed. The problems are generally temporary and can usually be resolved by addressing the specific executable file. Most instsh_x64.exe issues affect individual applications rather than system-wide functionality.
DLL Errors involve issues with dynamic link library files that multiple programs share. Unlike executable problems, DLL errors tend to impact multiple applications simultaneously since many programs may depend on the same DLL file. These errors often occur during normal program operation rather than specifically during installation. DLL issues typically require different resolution methods, focusing on library registration or replacement.
Driver Problems affect hardware functionality rather than software installations. These issues impact device operation and may cause hardware to function improperly or not at all. Driver problems require specific troubleshooting related to hardware compatibility and often need manufacturer-provided solutions. Unlike instsh_x64.exe issues, driver problems persist regardless of what software is being used.
System File Corruption represents broader damage to core Windows components. This type of problem affects the entire operating system rather than specific installation processes. System file corruption generally causes widespread stability issues across multiple aspects of Windows. These problems usually require more comprehensive repair approaches like SFC scans or system restore operations.
The primary advantage in dealing with instsh_x64.exe issues is their relatively contained nature – they typically don’t spread to other system components and can often be resolved by focusing on the specific installation process that’s utilizing this executable.
Method 1: Basic Troubleshooting Steps
Begin with these fundamental steps that can resolve many instsh_x64.exe issues:
- Restart your computer to clear any temporary issues in memory
- Check for Windows Updates by going to Settings > Update & Security > Windows Update
- Ensure you have sufficient disk space (at least 10GB free) for installation processes
- Temporarily disable antivirus software that might be interfering with the installation process
- Run the installation as administrator by right-clicking the installer and selecting “Run as administrator”
Method 2: Using Trojan Killer for System Repair
Trojan Killer includes advanced system repair capabilities that can resolve executable file issues:
- Download and install Trojan Killer from the official website
- Launch the application with administrator privileges
- Navigate to the System Tools section and select System Repair
- Run a system scan to identify issues with executable files
- Select and repair the detected issues related to instsh_x64.exe
- Restart your computer to apply the changes
Method 3: Windows System File Checker
Microsoft’s built-in System File Checker can repair corrupted system files:
- Open Command Prompt as administrator (right-click Start > Command Prompt (Admin))
- Run the command:
sfc /scannow - Wait for the process to complete (this may take several minutes)
- Restart your computer if problems are found and fixed
According to Microsoft Support, System File Checker can identify and repair corrupted or missing system files that might be affecting executable operations.
Method 4: Clean Installation of the Software
If the problem persists, try a complete reinstallation:
- Uninstall the problematic software through Control Panel > Programs > Uninstall a program
- Use a cleanup utility to remove leftover files and registry entries
- Restart your computer to complete the removal process
- Download a fresh copy of the software from the official source
- Install the software using administrator privileges
Method 5: Check for Disk Errors
Disk corruption can cause executable file issues:
- Open Command Prompt as administrator
- Type the command:
chkdsk C: /f /r(where C: is your system drive) - Press Y if prompted to schedule the check for the next restart
- Restart your computer to allow the disk check to run
- Wait for the process to complete (may take 1-2 hours for large drives)
Method 6: Windows Reset or Repair Install
For persistent issues, consider using Windows recovery options:
- Go to Settings > Update & Security > Recovery
- Under “Reset this PC,” click “Get started”
- Choose “Keep my files” to preserve your personal data
- Follow the on-screen instructions to complete the process
If you’re considering a complete system reset, you might want to read our article on whether a factory reset removes all system issues to understand the implications.
Preventing instsh_x64.exe Issues
To avoid future problems with executable files like instsh_x64.exe:
- Always download software from official sources
- Keep Windows and all applications updated
- Maintain at least 20% free disk space on your system drive
- Regularly perform system maintenance using tools like Trojan Killer
- Create system restore points before major software installations
- Use a reliable internet connection when downloading software
- Close unnecessary applications before installing new software
- Keep system drivers updated, especially for storage controllers
Good system maintenance practices also help prevent other issues like those discussed in our guide on system restore options.
Technical Details of Windows Executable Files
For advanced users and IT professionals, here are some technical details about Windows executable files:
- File Format: Windows PE (Portable Executable) format with specific headers and sections
- Architecture: Specifically designed for x64 (64-bit) Windows environments
- Dependencies: Often relies on Windows API functions and various system DLLs
- Registry Impact: May create entries in HKLM\SOFTWARE and HKCU\SOFTWARE sections
- File System: Typically operates with specific permissions requirements in protected directories
- Common Locations: Usually found in C:\Program Files\, C:\Program Files (x86)\, or application-specific directories
More technical information about executable file structures can be found in Microsoft’s documentation on the PE format.
Frequently Asked Questions
Is instsh_x64.exe a virus or malware?
No, instsh_x64.exe is typically a legitimate executable file used by various software installation frameworks. It’s not inherently malicious. However, like any system file, it could potentially be impersonated by malware. If you suspect this might be the case, perform a thorough system scan with Trojan Killer. Legitimate instsh_x64.exe files are usually digitally signed by their publisher and located in appropriate installation directories. Be suspicious if you find this file in unusual locations such as the Temp folder or your Documents directory, especially if you’re experiencing other symptoms of malware infection like unexpected system behavior or network activity.
Why does instsh_x64.exe cause high CPU usage?
High CPU usage by instsh_x64.exe is usually normal during active installation processes, as the executable is unpacking files, updating registry settings, and configuring application components – all resource-intensive tasks. This high usage should be temporary and limited to the installation duration. However, if instsh_x64.exe continues to consume excessive CPU resources after installation is complete or when no installation is in progress, this indicates a problem. The issue might be an installation that failed to complete properly, leaving the process running in the background, or possibly a conflict with another application. In rare cases, persistent high CPU usage could indicate the executable has been compromised or duplicated by unwanted software.
What happens if I delete instsh_x64.exe?
Manually deleting instsh_x64.exe is not recommended as this file is typically needed for software installation processes. If you delete it while an installation is in progress, that installation will fail and may leave your system in an inconsistent state with partially installed software. If the file is currently not being used by any active installation, deleting it might prevent future installations or updates for certain applications. The better approach is to address any issues with the file rather than deleting it. If you’ve already deleted the file and are experiencing problems, reinstalling the affected software from an official source should restore the proper version of the file. Always use proper uninstallation methods rather than manually deleting system files.
Can Windows Updates fix instsh_x64.exe problems?
Yes, Windows Updates can sometimes resolve instsh_x64.exe issues, particularly if the problem stems from outdated system components that this executable interacts with. Microsoft regularly includes fixes for common system file behaviors and dependencies in their updates. Updates to the Windows Installer service, which often works in conjunction with files like instsh_x64.exe, can address known bugs affecting installation processes. Additionally, Windows feature updates may include completely refreshed versions of core system components that installation frameworks depend on. However, Windows Updates won’t fix issues if the root cause is a corrupted application-specific file or a third-party software conflict. For these cases, you’ll need to use more targeted solutions like reinstalling the specific software or using system repair tools.
Does reinstalling Windows completely fix all executable file issues?
Reinstalling Windows does resolve most executable file issues, including problems with instsh_x64.exe, but it’s an extreme solution that should be considered only after trying less disruptive methods. A Windows reinstallation effectively resets all system files to their default state, eliminating any corruption or inconsistencies in the operating system components. However, this approach has significant drawbacks: you’ll need to reinstall all your applications, reconfigure your settings, and possibly restore your data from backups. Less drastic alternatives like using Windows’ built-in repair options (sfc /scannow, DISM tools), performing an in-place upgrade, or using the “Reset this PC” feature with the “Keep my files” option can often fix executable issues while preserving your applications and data. Always ensure you have comprehensive backups before attempting any system-level repair methods.
Advanced Technical Analysis of Windows Installation Executables (For IT Professionals)
This section provides in-depth technical information about installation executables like instsh_x64.exe, their operation, and troubleshooting methodologies for IT professionals and system administrators.
PE File Structure Analysis
Windows executable files like instsh_x64.exe follow the Portable Executable (PE) format structure:
// Simplified PE Header structure relevant to installation executables
struct PEHeader {
// DOS MZ Header (marks file as executable)
IMAGE_DOS_HEADER dosHeader; // Begins with "MZ" signature
// PE Signature "PE\0\0" and File Header
DWORD peSignature; // PE\0\0 (0x50450000)
IMAGE_FILE_HEADER fileHeader;
// Optional Header (contains important addressing information)
IMAGE_OPTIONAL_HEADER64 optionalHeader; // 64-bit specific format
// Section Headers (define code, data, resource sections)
IMAGE_SECTION_HEADER sectionHeaders[]; // Multiple sections
};
// Common sections found in installation executables
Sections:
- .text (Contains executable code)
- .data (Initialized data)
- .rdata (Read-only data, string constants)
- .rsrc (Resources like icons, dialogs, version info)
- .reloc (Base relocation information)
Common Installation Framework Architectures
Advanced understanding of how installation frameworks function:
| Component | Function | Common Issues |
|---|---|---|
| Bootstrap Executable | Initial small executable that launches the main installer | Permission problems, corruption during download |
| Extraction Module | Unpacks compressed installation files | Disk space issues, incomplete downloads |
| Installation Engine | Core logic for file copying and configuration | DLL dependencies, version conflicts |
| Registry Handler | Manages registry modifications | Permission issues, registry corruption |
| UI Manager | Handles installation interface | Display driver issues, resource limitations |
Diagnostic Commands for Executable Analysis
System administrators can use these commands to diagnose executable file issues:
# Get detailed information about running instsh_x64.exe processes tasklist /fi "imagename eq instsh_x64.exe" /v # Check file integrity and signature sigcheck -a -h C:\path\to\instsh_x64.exe # View file dependencies depends.exe C:\path\to\instsh_x64.exe # Check for open handles to the file handle.exe instsh_x64.exe # Monitor real-time file system and registry access procmon.exe /filter "Process Name" "is" "instsh_x64.exe" # Check loaded modules within the process listdlls.exe [PID of instsh_x64.exe process] # Analyze process memory usage vmmap.exe [PID of instsh_x64.exe process]
Registry Keys Associated with Installation Executables
Common registry locations that affect installation executables:
# Windows Installer configuration HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer # Component registration HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs # File associations HKLM\SOFTWARE\Classes\.exe HKLM\SOFTWARE\Classes\exefile # Application compatibility settings HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags # Installation locations HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*
Error Code Analysis
Common Windows error codes associated with installation executable failures:
| Error Code | Description | Typical Resolution |
|---|---|---|
| 0x80070005 | Access Denied | Run as administrator, check permissions |
| 0x80070570 | File cannot be accessed (corruption) | Redownload installer, check disk |
| 0x8007064C | Insufficient disk space | Free up disk space, clean temporary files |
| 0x80070643 | Installation failed during execution phase | Check logs, verify prerequisites |
| 0x80070652 | Installation already in progress | End existing installer processes, restart |
Recovery Scripts
PowerShell script for diagnosing and repairing common executable issues:
# PowerShell script to diagnose and repair common installation executable issues # Save as RepairInstaller.ps1 and run as administrator # Check system file integrity Write-Host "Checking system file integrity..." -ForegroundColor Green sfc /scannow | Out-Null # Reset Windows Installer service Write-Host "Resetting Windows Installer service..." -ForegroundColor Green Stop-Service -Name msiserver -Force Start-Service -Name msiserver # Clear Windows Installer cache Write-Host "Clearing Windows Installer cache..." -ForegroundColor Green Remove-Item "$env:WINDIR\Installer\$*.TMP" -Force -ErrorAction SilentlyContinue # Reset Windows Update components Write-Host "Resetting Windows Update components..." -ForegroundColor Green Stop-Service -Name wuauserv -Force Stop-Service -Name bits -Force Stop-Service -Name cryptsvc -Force # Clear Windows Update cache Remove-Item "$env:WINDIR\SoftwareDistribution\*" -Recurse -Force -ErrorAction SilentlyContinue # Restart services Start-Service -Name wuauserv Start-Service -Name bits Start-Service -Name cryptsvc Write-Host "Basic system repairs completed. Please restart the computer." -ForegroundColor Green
These technical details provide system administrators and IT professionals with the information needed to better understand, diagnose, and resolve issues with installation executables like instsh_x64.exe in their environments.
Conclusion
Issues with instsh_x64.exe can range from minor inconveniences to significant system problems that prevent software installation. By understanding the nature of these executable files and following the troubleshooting steps outlined in this guide, most issues can be effectively resolved without requiring extensive technical knowledge.
Regular system maintenance, careful software installation practices, and using reliable system utilities like Trojan Killer can help prevent most executable file issues before they impact your system. If you continue to experience persistent problems with instsh_x64.exe or other system files, consider consulting with a professional technical support service for personalized assistance.
Remember that addressing system file issues promptly helps maintain your computer’s performance, stability, and security over time.
- Home
- Blog
-
How to Analyze Windows Executable Files Using PEStudio?
/
/
Windows has been the most widely used operating system for several decades. However, it’s more prone to malware infection too. Undeniably, most malware authors target Windows platforms more than any other platforms. It’s the prime responsible for Windows machine owners to keep their Windows machines safe from nasty malware programs. Well, we have been keep discussing the safety of Windows and other platforms on thesecmaster.com several times. We keep doing this as much as we can. In this post, we will be covering another unique topic, how to analyze Windows executable files using PEStudio.
PEStudio is a popular tool used by malware analysts and reverse engineers to analyze and detect anomalies in Windows portable executable (PE) files like EXEs and DLLs. This comprehensive guide will explain what PEStudio is, how to download and install it, overview its key features, and provide a step-by-step walkthrough to investigate Windows executable files using PEStudio.
Before we jump into analyzing the EXE and DLL Files Using PEStudio, let’s see some of the background about the file structure of Windows files, what the PE header means, and what information you should look in a file to analyze it.
The Structure of Windows Executable File
In essence, Windows executable files follow the portable executable (PE) format, which is the standard binary interface for Windows operating systems. The PE format is fundamentally composed of the following:
Image Source: Wikipedia
PE Header
The PE header contains metadata and pointers that are necessary for the operating system to load and execute the executable properly. It is like a table of contents describing the structure of the executable. Some key attributes stored in the header include:
-
Machine Type – Specifies the required CPU architecture such as x86, x64, ARM etc. This determines whether the code is 32-bit or 64-bit.
-
Number of Sections – Indicates the total number of sections in the executable code/data. This helps locate all sections.
-
Timestamp – Contains the build timestamp of when the executable was compiled. Malware often modifies this to make it look legitimate.
-
Pointer to Symbol Table – Stores pointers to debugging symbols used for crash dumps and debugging.
-
Optional Header – An optional header containing further metadata like target OS version, subsystem, entry point address, image, and memory sizes, etc.
-
Section Table – Contains details on each section like name, virtual address, raw data size, file pointer, permissions, etc.
-
Data Directories – Has pointers to extended tables like import, export, relocation, debug directories, etc.
The header thus contains instructions for the OS loader on how to map the executable to memory and call the entry point to start execution. This is the most prominent as an invalid header can interrupt launching the executable.
Sections
The sections segment contains distinct blocks of code and data that make up the executable. Each section is separate and can have specific memory access permissions. Standard sections include:
-
.text – Contains the executable program code. Has read and execute permissions.
-
.data – Contains statically allocated program data that needs to be initialized. Has read, write permissions.
-
.rdata – Read-only data like constants and string literals. Read permission only.
-
.rsrc – Contains resources like icons, images, strings etc. embedded in the executable.
-
.reloc – Relocation table for pointers that need to be fixed up when loaded at a different base address.
Malware often hides additional malicious code and data inside new sections appended to the executable.
Import Address Table (IAT)
The IAT contains the list of DLLs and functions that are imported from external libraries for use by the executable at runtime. Entries in IAT have pointers to the memory address of imported functions.
Export Address Table (EAT)
The EAT contains a table of functions exported by the executable that can be called by external programs and libraries. It is used to expose a public API from a DLL.
Resources
This data directory contains Windows resources embedded in the executable like icons, images, strings, dialog boxes, menus, etc. Resources are stored in binary format and can be analyzed for suspicious hidden data.
Overlay
The overlay is a special section that contains any additional data appended at the end of the executable file. Malware can use overlay to piggyback extra malicious executable code or files into a benign host program.
This overall structure of Windows PE files enables portability and interoperability across different Windows versions. But malware can misuse various components for nefarious purposes.
What is the Role of PE Header in Executable Files?
The Portable Executable (PE) header of Windows executable files contains crucial metadata and pointers that are necessary for the operating system to load and execute the program correctly.
Machine Type
This 2-byte field specifies the CPU architecture for which the executable is targeted – x86, x64, ARM etc. This determines whether the executable is 32-bit or 64-bit. Running a 32-bit EXE on a 64-bit Windows can trigger compatibility modes.
Number of Sections
This 2-byte value indicates the total number of sections in the executable code/data. Based on this, the loader can locate and load all the sections.
Timestamp
The 4-byte timestamp indicates the date and time when the executable was built. However, malware often modifies the timestamp to make it look like the file was created a long time ago to avoid suspicion.
Pointer to Symbol Table
This 4-byte field contains the file offset where the symbol table is located. Symbols store debugging information used for crash dumps and reverse engineering. Stripping symbols is a common obfuscation technique.
Optional Header
This contains additional metadata about the executable structure like the magic number, target OS version, address of entry point, image base address, size of code/initialized data, linker version etc. The optional header may be malformed or manipulated by malware.
Section Table
The section table has an entry for each section header, indicating its name, memory permissions, virtual address, size of raw data, file pointer, etc. Suspicious sections can reveal hidden payloads.
Data Directories
This table contains pointers to extended tables, including the import, export, resource, relocation, debug directories etc, which contain further details on various executable components.
Thus we see the PE header instructs the OS loader on how to map the executable to memory and execute it correctly based on the target platform, entry points, sections, resources, etc. PE headers are prime targets for malware to manipulate executables.
What Information Should You Look for in an Executable File?
When analyzing Windows executable files, you should keep note of these key aspects in the file. They are:
Entropy
Entropy measures the randomness and complexity of data in a file. Encrypted and compressed files have high entropy. Malware often uses packers and crypters leading to high entropy. Normal native executables have entropy of 6.8 or less. Entropy greater than 7.2 indicates likely obfuscation or compression.
Strings
String extraction reveals human-readable plaintext strings contained in the executable. Strings may expose IP addresses, URLs, file paths, and unique identifiers used by malware. Many malware families can be identified by their distinctive strings.
Imports
The import table reveals external DLLs and API functions used by the executable. Malware often imports Windows DLLs like kernel32, advapi32, and networking-related APIs. Functions used for injection, anti-debugging, and persistence indicate malicious intent.
Exports
The export table contains functions exposed by the executable for external use. Suspicious exports may start a malicious activity when called by other programs. Malware experts decoy benign functions to hide their true purpose.
Resources
Resource sections store icons, images, metadata, etc., used by the executable. Malware can conceal payloads, custom fonts, and executable code inside resource sections obfuscated via encryption or unconventional formats.
Sections
Section names, virtual addresses, sizes, and flags can indicate anomalies. Malware appends new sections with read/execute permissions to store malicious payloads. Gaps in virtual vs raw sizes are suspicious.
Overlay
The overlay portion can contain appended malicious scripts, PE files, shell codes, etc. Overlay malware is a common trick to bundle a malicious PE inside a benign host.
Compiler Info
Linker version, compiler toolchain, timestamp, etc., reveal inconsistencies that make the executable look fabricated/fake. Malware often modifies the compiler info to pose as legitimate programs.
PE Header
Key header values like machine type, subsystem, claimed linker version, etc. should match across sections. Incorrect values are tell-tale signs of manipulation.
VirusTotal
VirusTotal checks against dozens of antivirus scanners. Detection by multiple engines indicates a high probability of malware. VirusTotal can also identify known malicious signatures.
What is PEStudio? What are Its Key Features? How Does it Help Analyzing Windows Executable Files?
PEStudio is a lightweight and portable malware analysis tool developed by Wintor to analyze and investigate the properties of executable files, particularly Windows PE (Portable Executable) files. It can process EXE, DLL, OCX, SYS, MUI, CPL, and other PE file formats. PEStudio parses the PE header and displays various metadata fields. It also scans the executable using static analysis techniques to identify anomalies that may indicate the presence of malware.
PeStudio serves as a valuable solution for software developers, security researchers, and malware analysts, offering them the ability to identify potential problems in executable files before releasing them to the public or deploying them in live environments. With PeStudio, users can conduct efficient and straightforward analyses, swiftly pinpointing any issues present in their files.
Video Creator:
The tool is frequently used by:
-
Malware analysts – To reverse engineer malware samples, understand their capabilities, and extract IOCs.
-
Software developers – To validate EXE and DLL files before release for any malformed headers, insecure functions, etc.
-
Security engineers – To vet files and strengthen the security of systems.
Some of the key capabilities of PEStudio include:
-
Parsing PE file headers
-
Dump embedded resources like icons, images, etc.
-
Detect packers and protectors
-
Scan imports, strings, and bytecode for suspicious indicators
-
Integrate with VirusTotal
-
YARA scanner
-
Disassembler
-
Import reconstructor
PEStudio has a free and paid professional version. The free version contains all the major features required for malware analysis.
Features of PEStudio
Pestudio offers a range of powerful features for analyzing Windows executable files:
-
Dependency Analysis: It shows the libraries and functions used by the file.
-
VirusTotal Integration: It checks the file against VirusTotal’s database for malware scan results.
-
File Verification: It verifies if the file has been modified since its last signing or verification.
-
Imports and Exports Analysis: It provides information about the functions and libraries used by the file.
-
Resource Analysis: It examines the file’s images, icons, and graphical elements.
-
String Analysis: It searches for suspicious or malicious strings in the file.
-
Bytecode Analysis: It detects potential security risks and malicious activity in the file’s bytecode.
-
Digital Signature Analysis: It verifies the authenticity and integrity of the file’s digital signature.
How Does it Help Analyzing Windows Executable Files?
PEStudio is an awesome tool with tons of features. It helps analyze the Windows executables in various ways.
In-depth PE Header Analysis
PEStudio parses the entire PE header and displays the values of all fields like machine type, compilation timestamp, target OS version, subsystem, entry point address, claimed linker version, etc.
This provides visibility into any anomalies in the header values that are tell-tale signs of tampering by malware. For instance, if the linker version is suspicious or the subsystem doesn’t match the rest of the file, it indicates manipulation.
Detailed Section Reporting
PEStudio extracts all the sections from the executable and reports extensive details – name, virtual address, size, entropy, permissions etc. It can detect additional sections appended by malware to conceal payloads.
It also detects gaps between raw file size and the virtual memory size of sections. Large discrepancies indicate the allocation of memory for malicious activities.
Resource Analysis
Resources like icon images, version info strings, manifests, etc. are parsed and displayed. Malware frequently hides files, custom fonts, and other suspicious resources using encryption or unconventional formatting. PEStudio helps uncover them.
Imported Function Scanning
PEStudio extracts the import table and lists all DLLs and APIs imported by the executable. It detects imports of blacklisted/banned APIs that are often used by malware. Examples – LoadLibrary, InternetConnect, CreateRemoteThread, etc.
String Extraction
ASCII and Unicode strings present in the file are extracted for analysis. Strings may contain IP addresses, URLs, bot command and control names, launch commands, etc., which are key IOCs.
YARA Scanning
PEStudio has integrated a YARA engine that scans the executable against known YARA rules to identify malware families. Getting a YARA match provides insights into the sample’s purpose.
Anomaly Detection
Various static scan checks are run to detect anomalies in the structure, metadata, sections, APIs, strings, etc. that deviate from normal. Multiple anomalies increase the likelihood the file is malicious.
Packer Detection
PEStudio checks for signatures of known packers and protectors like UPX, MPRESS, Themida, etc. which are frequently used to obfuscate malware. Being able to unpack the file is the first step in the analysis.
VirusTotal Integration
The file hash is checked against VirusTotal database to see detection rates. The high number of detections by antivirus engines indicates likely malware. VT results provide reputation context.
Import Reconstructor
If the executable imports have been reconstructed or wiped by the malware, PEStudio has tools to help recover and rebuild them for analysis.
Disassembler
The disassembler shows the executable assembly code of sections like .text to analyze the inner workings through reverse engineering.
Download and Install PEStudio
PEStudio can be downloaded from the official website https://www.winitor.com. Follow these steps to download and install the latest version:
-
Go to the link https://www.winitor.com/download
-
There is a free and professional version available.
-
The file can be downloaded as per your browser settings and can be installed directly without any hassle
-
The latest version, as the date of this post, is 9.53
How to Analyze Windows Executable Files Using PEStudio?
Once the PEStudio is ready to use, it’s time to analyze Windows executable files.
Now let’s go through a practical example of analyzing a malicious EXE sample using PEStudio to understand its workflow. Just for this demo, we have downloaded an executable file called from VirusTotal. You can do this with your suspected file.
-
Launch the PEStudio application from the start menu.
-
You will see the main viewer window with various tabs for different analysis sections.
-
Click on the “Open” button on the top left or simply drag and drop the sample file into the viewer.
-
PEStudio will automatically start analyzing the sample.
You can start recording each one of these sections for your analysis.
-
Overview Section
-
Entropy
-
Compilation timestamp
-
Subsystem
-
Sections
-
Initial bytes
-
VirusTotal detection
-
-
PE Header
-
Machine
-
Magic
-
Linker version
-
Subsystem
-
Address of Entry Point
-
-
Sections
-
5 sections: .text, .data, .reloc, .rsrc, .vmp0
-
.text – Executable code, Permissions: READ, EXECUTE
-
.data – Initialized data, Permissions: READ, WRITE
-
.rsrc – Resources like icons, images, and Permissions: READ
-
No obvious anomalies in section names, addresses and sizes
-
-
Imports
-
Imports msvcrt.dll, kernel32.dll, advapi32.dll, user32.dll – system DLLs commonly used by malware
-
No imports from blacklisted DLLs
-
Suspicious API imports:
-
InternetOpenUrlA – Makes HTTP/FTP requests
-
InternetReadFile – Reads web content
-
WriteProcessMemory – Writes to another process memory area
-
CreateRemoteThread – Executes code in another process
-
Likely capabilities – make web requests, inject code, download payloads
-
-
-
Exports
-
Exports 3 functions: InitApp, DeInitApp, RegisterRoutines
-
InitApp likely initializes malware components
-
DeInitApp cleans up traces
-
RegisterRoutines registers malicious code to be triggered
-
-
Resources
-
Contains 1 icon resource – image used for icon displayed for EXE
-
Nothing suspicious identified
-
-
Strings
-
Contains IP address – potential C2 server
-
Contains file paths to write data – %APPDATA%\log.txt
-
Overall indicates – outbound connection, log file written
-
-
VirusTotal
-
Detections by antivirus vendors as malicious
-
-
YARA Rules
-
Matching YARA Rules
-
-
Packer Detection
-
Type or name of Packer
-
-
Anomalies
Let’s see this with the help of an example.
How to Analyze Windows Executable Files Using PEStudio?
Step 1. Analyze the Main Tab
1. PE studio has identified the file hashes, file size, etc.2. It shows the entropy value of the file, entropy is nothing but a value that shows the encryption, packing, and obfuscation of a sample file. Its value varies from 0-8, typically, malware samples will have an entropy value above 7.2. In this case, entropy is 7.996, which says this can be a malware file.3. PeStudio also displays the first bytes of the file in hexadecimal format, like ‘4D 5A’ in the example image. These initial bytes are crucial as they confirm that the file is Windows Executable. The first bytes in a file’s header follow a specific pattern depending on the file type. While we often identify files by their extensions like ‘.exe’, the operating system recognizes them by the byte pattern in the header. For Windows executables, this pattern is always ‘4D 5A’ in hexadecimal, which corresponds to ‘MZ’ in ASCII.4. It shows which tool was used to build this file in the ‘tooling’ property. Here we can see Innosetup is used.5. The subsystem shows if the file is GUI or command-line-based. Most of the ransomware files will be the command-line type.6. The compiler stamp is the date that shows the sample compilation time. Attackers can purposefully change the date in the past or future as per their requirement.7. Our file is a 32-bit executable file that uses GUI and is created using Innosetup. We can also see the file compilation date is 1992, which can be an attacker tactic.
Step 2. Analyze Virus Total Tab
1. PEStudio shows the rating of the file in virus total as well.2. In this case, we can see that the file is marked malicious by 48 vendors in virus total.
Step 3. Analyze Indicator Tab
1. ‘Indicator’ tab shows any indicators of suspicious activity.2. This section shows imports, strings, or sections within the sample file which is considered suspicious by the tool.3. In the displayed image, PeStudio has identified several indicators and ranked them on a scale from 1 to 3, where 1 indicates a highly confident malicious indicator.4. Following this indicator, the tabs below tabs show other parts of the sample file. We can do our analysis as per the requirement.
Step 4. Analyze Sections Tab
1. Another notable tab is the ‘section’ where we can see different types of names.2. Generally, the commonly seen names start with a dot for example text, data, rdata, etc.3. In some cases we can find unusual names which need to be investigated further. In our case, we didn’t find any.4. In this tab we can see two values raw address and virtual address. The raw address is the space of the section within the binary, and the virtual address shows the size of the section once it is loaded into memory.5. The difference in a few bytes between raw and virtual address is normal however, a large gap can indicate the presence of a payload. That is if the space occupied by the section in the raw address is zero or the file ratio is zero, and the file is taking a huge space in memory is suspicious, this might be where the malicious code is present.6. The file ratio shows the space each section takes in the binary.7. We may find images, cursor data, and other details in the resource file which can be something hidden by the attacker. Using resource hacker tools might help in revealing more information.
Step 5. Analyze Library Tab
1. The ‘library’ section shows the name of any shared libraries used in the executable file.2. This tab shows all the DLL(Dynamic link library) which are imported by the malware and also shows if they are malicious or not.
Step 6. Analyze Imports Tab
1. The Imports tab in PeStudio contains the list of functions/API imported by the malware, also known as the Import Address Table (IAT). When you click on the Blacklist tab, PeStudio will sort the APIs and move all the blacklisted functions to the top.2. This tab will help in understanding how the malware behaves after compromising the host.3. The ‘group’ column provides information about the type of activity each API is related to.4. The ‘imports’ tab shows the functions imported from the libraries mentioned above, if anything suspicious is observed, PE studio will mark it suspicious. In our case, we can’t observe any.
Step 7. Analyze Strings Tab
1. The strings section will extract all the strings within the binary.2. Strings may contain IP addresses or file names, paths, commands, etc. Strings can show you if there was any network activity present.3. The ‘overlay’ tab shows additional files that are required to execute its task. In this case, innosetup is required.4. Some files might have a certification section. This is important as it will help in verifying the authenticity of the file.
Conclusion
To summarize, PEStudio is a feature-rich static analysis tool for investigating Windows executable files for anomalies and signs of malware. It parses the PE format and scans using techniques like YARA rules, Import-Export parsers, String analysis, Disassembler, etc., to detect suspicious capabilities and payloads. The interactive GUI and detailed reports simplify malware analysis and help extract key indicators of compromise. PEStudio provides immense value for threat researchers, malware analysts, SOC teams, and cybersecurity professionals to analyze advanced threats and strengthen enterprise defenses.
We hope this post helped in understanding what PEStudio is, how to download it, and how to analyze Windows executable files using PEStudio. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.
