- Messages
- 4,931
- Solutions
- 138
- Reaction score
- 966
- Points
- 413
-
-
#2
Can you also tell us what procedure are you following to upgrade your windows 10 computers to 1903.
To start with, confirm that the software has been distributed to your distribution point and that the boundary that your client is in, is associated with the correct distribution point.
Check the following log files — CAS.log, ContentTransferManager.log, DataTransferService.log
dprd7
Active Member
- Messages
- 31
- Reaction score
- 0
- Points
- 6
-
Thread Starter
-
-
#3
I was using the guide you had but the only difference is I am doing a required install with times to be available and expiration times. My first couple deployments worked but out of nowhere now it is not. The software has been sent and the computer is in the boundary group but using active directory since we can’t use IP Ranges.
I also did a test last night with your guide completely and when I try to install through software center it says «The software could not be found on any server at this time which is odd».
I will look at those logs but I am kinda a newbie with reading the logs. lol
I wanted to say by the way I love the site and the guides. It is an amazing resource.
dprd7
Active Member
- Messages
- 31
- Reaction score
- 0
- Points
- 6
-
Thread Starter
-
-
#4
I am curious about the boundary groups. I have it set the domain level and all the computer are in that domain but I did notice one thing in the logs which is weird.
This is from the locationServices log
Client is not in any boundary group and ConfigMgr is no longer managing WindowsDO GPO. Set WindowsDO GPO to default values. Mode = LAN. GroupID = empty LocationServices 12/6/2019 12:14:13 PM 8800 (0x2260)
dprd7
Active Member
- Messages
- 31
- Reaction score
- 0
- Points
- 6
-
Thread Starter
-
-
#5
Update. I just noticed that my clients are saying the wrong Active Directory Site when you look at the general info for the client which is why they seem to be outside the boundary group. Anyone have any idea how this happened and how to fix it since I made no changes to my SCCM and the boundary and boundary groups are correct. Before Thanksgiving everything was fine. I could push the client and the AD site would be correct but after break if I push the client it says the wrong AD site. Please help
joe_v
Active Member
- Messages
- 31
- Reaction score
- 3
- Points
- 8
-
-
#6
Do you have Computers in a specific OU in Active Directory? Is that OU used in discovery? If you try to remote to the client system, do you see the site code that was assigned to the SCCM showing up in Configuration Management Client (under the site tab) ? Are you able to ping the client? Do you have firewall settings that might be blocking ICMP or ping?
dprd7
Active Member
- Messages
- 31
- Reaction score
- 0
- Points
- 6
-
Thread Starter
-
-
#7
My boundary is set at the top and my discovery is set to specific OUs which are within the boundary and are being discovered there. The clients have the correct Site code. I can ping them and there has been no firewall changes.
joe_v
Active Member
- Messages
- 31
- Reaction score
- 3
- Points
- 8
-
-
#8
Alright… If you do these 2 things, on one machine please try to uninstall SCCM client manually through command prompt (run as admin) by changing directory to C:\windows\ccmsetup (this is seen only if the client was installed previously on the computer) then typing ccmsetup /uninstall. Waiting for the ccmsetup in processes to complete ( in taskmanager). Then try to install in again manually.
From another machine, could you try to post the recent client.msi.log and ccmsetup.log from the C:\windows\ccmsetup.
joe_v
Active Member
- Messages
- 31
- Reaction score
- 3
- Points
- 8
-
-
#9
Also for the one where you would be doing the manual install for the sccm client on the host machine, please check the site code to see if it is showing as the right one or if it is empty. If it is empty, use the find site button and wait to see if it brings the right site code.
dprd7
Active Member
- Messages
- 31
- Reaction score
- 0
- Points
- 6
-
Thread Starter
-
-
#10
Will do that when I get a chance. Is there a way to push out software if the machine lives outside the boundary group?
joe_v
Active Member
- Messages
- 31
- Reaction score
- 3
- Points
- 8
-
-
#11
Technically, the boundary helps the client to see where to get the software from. Otherwise it won’t know where to look for the software. Please try the things i told earlier and we can try to see what the problem is.
Content Troubleshooting
This deep dive covers how to troubleshoot content location issues on the client and server-side in Configuration Manager.
Video: Content Troubleshooting Deep Dive (Full Video)
Video: Content Troubleshooting Video Timeline
Scenario 1: Succesful Content Lookup Workflow
-
Healthy ConfigMgr client.
-
The client is in a boundary.
-
There is a Distribution Point associated with the boundary group.
-
The content is distributed successfully to the DP.
-
The software / update / package is deployed to the device.
-
Enable verbose logging on the site system with the MP role and the client
Successful Content Lookup Flow
There are many moving parts when a content location request is sent to the management point and processes by a ConfigMgr client. Here are some key snippets of how this happens.
CCIStateStore::GetCIState — Client is requesting CI ModelName ScopeId_CA3F999B-7A81-43BF-912C-56E267C1E565/RequiredApplication_4894a05f-49c0-4836-a22f-50526dba27c4, Revision 1 for User: S-1-5-21-1880864260-2612682489-34998949-6112
CDownloadPayloadInfo::AddCI — CI with ModelName ScopeId_CA3F999B-7A81-43BF-912C-56E267C1E565/DeploymentType_677dac51-d2a2-4bbd-aeb0-4b845aa288cd, Version 1 is already available. Requested Model:VersionSpecific will be downloaded.
===== CacheManager: Content for Content_8ba1768d-abc6-4e42-919d-1e421fe610f0.1 was NOT found cache. =====
ContentLocationRequest : <ContentLocationRequest SchemaVersion=»1.00″ BGRVersion=»1″ ExcludeFileList=»»><Package ID=»UID:9c93cbee-aabc-4daf-996a-4580daa09c87″ Version=»1″ DeploymentFlags=»9223372036855300962″/><AssignedSite SiteCode=»DM1″/><ClientLocationInfo LocationType=»SMSUpdate» DistributeOnDemand=»0″ UseAzure=»0″ AllowWUMU=»0″ UseInternetDP=»0″ AllowHTTP=»1″ AllowSMB=»1″ AllowMulticast=»1″ AllowSuperPeer=»1″ DPTokenAuth=»1″><ADSite Name=»Default-First-Site-Name»/><Forest Name=»CONTOSO.LOCAL»/><Domain Name=»CONTOSO.LOCAL»/><IPAddresses><IPAddress SubnetAddress=»192.168.10.0″ Address=»192.168.10.35″/></IPAddresses><Adapters><Adapter Name=»Ethernet» IfType=»6″ PhysicalAddressExists=»1″ DnsSuffix=»» Description=»Microsoft Hyper-V Network Adapter»/></Adapters><BoundaryGroups BoundaryGroupListRetrieveTime=»2021-04-28T15:00:21.637″ IsOnVPN=»0″><BoundaryGroup GroupID=»16777218″ GroupGUID=»ad36e248-a857-45e6-ab82-c179bb680b18″ GroupFlag=»0″/></BoundaryGroups></ClientLocationInfo></ContentLocationRequest>
Starting download on action (INSTALL) for Update (9c93cbee-aabc-4daf-996a-4580daa09c87)
Content Text = <Content ContentId=»9c93cbee-aabc-4daf-996a-4580daa09c87″ Version=»1″><FileContent Name=»debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab» Hash=»78A05BCA9CCA039C62C1B2D494281E72ED864BD9″ HashAlgorithm=»SHA1″ Size=»79417630″/></Content>
Submitted CTM job {C17823B5-A8A9-48F8-8375-64CFC55869CB} to download Content 9c93cbee-aabc-4daf-996a-4580daa09c87.1 under context System — ContentTransferManager
CTM job {C17823B5-A8A9-48F8-8375-64CFC55869CB} (corresponding DTS job {C54E37D3-BFDE-4629-AC82-32E6CE733750}) started download from ‘http://DEMO1.CONTOSO.LOCAL/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87’ for full content download.
DTSJob {C54E37D3-BFDE-4629-AC82-32E6CE733750} created to download from ‘http://DEMO1.CONTOSO.LOCAL:80/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87’ to ‘C:\Windows\ccmcache\1’.
UpdateURLWithTransportSettings(): NEW URL — http://demo1.contoso.local:80/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87/sccm?/debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab
Total content size from the downloaded manifest is 79417630
Creating root directory…
Directory ‘C:\Windows\ccmcache\1’ already exists.
Starting BITS job ‘{97C9975B-820F-467A-9A0D-366C70F28EEC}’ for DTS job ‘{C54E37D3-BFDE-4629-AC82-32E6CE733750}’ under user ‘S-1-5-18’.
BITS compatible path: http://DEMO1.CONTOSO.LOCAL:80/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87/sccm?/debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab
BITSHelper, remote name = http://DEMO1.CONTOSO.LOCAL:80/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87/sccm?/debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab, local name = C:\Windows\ccmcache\1\debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab
Job: {C54E37D3-BFDE-4629-AC82-32E6CE733750}, Total Files: 1, Transferred Files: 0, Total Bytes: 79417630, Transferred Bytes: 262144
CContentAccessService::NotifyDownloadProgressEx — downloaded size 52480, total size 77556
The hash we are verifying is SDMPackage:<Content ContentId=»9c93cbee-aabc-4daf-996a-4580daa09c87″ Version=»1″><FileContent Name=»debcf2da-e7da-4c50-b718-fc95ffe40c9d_1.cab» Hash=»78A05BCA9CCA039C62C1B2D494281E72ED864BD9″ HashAlgorithm=»SHA1″ Size=»79417630″/></Content>
Hash verification succeeded for content 9c93cbee-aabc-4daf-996a-4580daa09c87.1 downloaded under context System
Job: {C54E37D3-BFDE-4629-AC82-32E6CE733750}, Total Files: 1, Transferred Files: 1, Total Bytes: 79417630, Transferred Bytes: 79417630
DTSJob {C54E37D3-BFDE-4629-AC82-32E6CE733750} successfully completed download. DataTransferService 4/27/2021 8:21:18 AM 2612 (0x0A34)
DTS job {C54E37D3-BFDE-4629-AC82-32E6CE733750} has completed:
CCTMJob::EvaluateState(JobID={C17823B5-A8A9-48F8-8375-64CFC55869CB}, State=Success)
Tip: You can open all content logs at once in CMTrace.exe by adding the following files: «CAS.log» «CIAgent.log» «CIDownloader.log» «CIStateStore.log» «ClientLocation.log» «CMBITSManager.log» «ContentTransferManager.log» «DataTransferService.log» «DCMAgent.log» «LocationServices.log» «StateMessage.log» «UpdatesDeployment.log»
Snippets of Location Request
Example of the management point MP_Location.log calling the stored procedure MP_GetContentDPInfo
<ServerNameList>
<ServerName LocalityEx="256" Fallback="0">DEMO1.CONTOSO.LOCAL</ServerName>
</ServerNameList>,SMSUpdate,00000000,CONTOSO.LOCAL,CONTOSO.LOCAL,<ClientLocationInfo LocationType="SMSUpdate" DistributeOnDemand="0" UseAzure="0" AllowWUMU="0" UseInternetDP="0" AllowHTTP="1" AllowSMB="1" AllowMulticast="1" AllowSuperPeer="1" DPTokenAuth="1">
<ADSite Name="DEFAULT-FIRST-SITE-NAME"/>
<Forest Name="CONTOSO.LOCAL"/>
<Domain Name="CONTOSO.LOCAL"/>
<IPAddresses>
<IPAddress SubnetAddress="192.168.10.0" Address="192.168.10.35"/>
</IPAddresses>
<Adapters>
<Adapter Name="Ethernet" IfType="6" PhysicalAddressExists="1" DnsSuffix="" Description="Microsoft Hyper-V Network Adapter"/>
</Adapters>
<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-28T15:00:21.637" IsOnVPN="0">
<BoundaryGroup GroupID="16777218" GroupGUID="ad36e248-a857-45e6-ab82-c179bb680b18" GroupFlag="0"/>
</BoundaryGroups>
</ClientLocationInfo>,<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-28T15:00:21.637" IsOnVPN="0">
<BoundaryGroup GroupID="16777218" GroupGUID="ad36e248-a857-45e6-ab82-c179bb680b18" GroupFlag="0"/>
</BoundaryGroups>)Example of a content location request from the client sent to the management point in CAS.log
<ContentLocationRequest SchemaVersion="1.00" BGRVersion="1" ExcludeFileList="">
<Package ID="UID:9c93cbee-aabc-4daf-996a-4580daa09c87" Version="1" DeploymentFlags="9223372036855300962"/>
<AssignedSite SiteCode="DM1"/>
<ClientLocationInfo LocationType="SMSUpdate" DistributeOnDemand="0" UseAzure="0" AllowWUMU="0" UseInternetDP="0" AllowHTTP="1" AllowSMB="1" AllowMulticast="1" AllowSuperPeer="1" DPTokenAuth="1">
<ADSite Name="Default-First-Site-Name"/>
<Forest Name="CONTOSO.LOCAL"/>
<Domain Name="CONTOSO.LOCAL"/>
<IPAddresses>
<IPAddress SubnetAddress="192.168.10.0" Address="192.168.10.35"/>
</IPAddresses>
<Adapters>
<Adapter Name="Ethernet" IfType="6" PhysicalAddressExists="1" DnsSuffix="" Description="Microsoft Hyper-V Network Adapter"/>
</Adapters>
<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-28T15:00:21.637" IsOnVPN="0">
<BoundaryGroup GroupID="16777218" GroupGUID="ad36e248-a857-45e6-ab82-c179bb680b18" GroupFlag="0"/>
</BoundaryGroups>
</ClientLocationInfo>
</ContentLocationRequest>Example of Content location reply from the management point to the client in the client’s CAS.log
<ContentLocationReply SchemaVersion="1.00" BGRVersion="1">
<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-27T14:21:06.263" IsOnVPN="0">
<BoundaryGroup GroupID="16777218" GroupGUID="ad36e248-a857-45e6-ab82-c179bb680b18" GroupFlag="0"/>
</BoundaryGroups>
<ContentInfo PackageFlags="0" DeploymentFlags="9223372036855300962">
<ContentHashValues/>
</ContentInfo>
<Sites>
<Site>
<MPSite SiteCode="DM1" MasterSiteCode="DM1" SiteLocality="LOCAL" IISPreferedPort="80" IISSSLPreferedPort="443"/>
<LocationRecords>
<LocationRecord LocalityEx="BOUNDARYGROUP" DPFallbackIn="PT0M">
<URL Name="http://DEMO1.CONTOSO.LOCAL/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87" Signature="http://DEMO1.CONTOSO.LOCAL/SMS_DP_SMSSIG$/9c93cbee-aabc-4daf-996a-4580daa09c87.1.tar" Capability="0"/>
<ADSite Name="Default-First-Site-Name"/>
<IPSubnets>
<IPSubnet Address="192.168.10.0"/>
<IPSubnet Address=""/>
</IPSubnets>
<Metric Value=""/>
<Version>9040</Version>
<Capabilities SchemaVersion="1.0">
<Property Name="SSLState" Value="0"/>
</Capabilities>
<ServerRemoteName>DEMO1.CONTOSO.LOCAL</ServerRemoteName>
<DPType>SERVER</DPType>
<Windows Trust="1"/>
</LocationRecord>
</LocationRecords>
</Site>
</Sites>
<RelatedContentIDs/>
</ContentLocationReply>Here’s a snippet of the download options for a software update download request in UpdatesDeploymentAgent.log
<DownloadOptions>
<Priority>Foreground</Priority>
<DPLocality>10</DPLocality>
<Timeout>
<Location>604800</Location>
<Download>86400</Download>
<PerDPInactivity>0</PerDPInactivity>
<TotalInactivity>0</TotalInactivity>
<UseBranchCache>true</UseBranchCache>
<PersistOnWriteFilterDevices>false</PersistOnWriteFilterDevices>
<OverrideServiceWindows>false</OverrideServiceWindows>
</Timeout>
</DownloadOptions>A point of interest is DPLocality flag determines how the client obtains distribution points, according to distribution point locality. Possible values are:
DP_NO_FALLBACK_UNPROTECTED
Scenario 2: Failed Content Lookup Due to Boundary Misconfiguration
-
Healthy ConfigMgr client.
-
The client is NOT in a boundary.
-
There is a Distribution Point associated with the boundary group the client is NOT in.
-
The content is distributed successfully to the DP.
-
The software / update / package is deployed to the device.
-
Enable verbose logging on the site system with the MP role and the client
Notable Ways to Identity when a Client is Not in Boundary Group
If a client is not in a boundary group here are some snippets that can be helpful.
Client is not in any boundary group and ConfigMgr is no longer managing WindowsDO GPO. Set WindowsDO GPO to default values. Mode = LAN. GroupID = empty
The number of discovered DPs(including Branch DP and Multicast) is 0
In the content location request in the CAS.log, you will also notice the BoundaryGroup element doesn’t contain the fields GroupID, GroupGUID, or GroupFlag.
Tip: Search the text «ContentLocationRequest» in the CAS.log to find location requests performed on the client-side logs.
In the CAS.log here is an example of a response from the management point when the client is in no boundary group, and fallback is disabled, and no content was found.
<ContentLocationReply SchemaVersion="1.00" BGRVersion="1" ContentFlags="86016" HashAlgorithm="32780" AlgorithmPreference="4" Hash="5230AF02CF06BDD36CDD10FD13C4DF795F465E46FC47E1B1A00E44E2589AA6AD" ExcludeFileListHash="" RelatedContentID="">
<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-28T15:36:56.910"/>
<ContentInfo/>
<Sites>
<Site>
<MPSite SiteCode="DM2" MasterSiteCode="DM2" SiteLocality="FALLBACK"/>
<LocationRecords/>
</Site>
</Sites>
<RelatedContentIDs/>
</ContentLocationReply>We can compare this to the response received in the CAS.log when the content was found and the client is in a boundary group.
<ContentLocationReply SchemaVersion="1.00" BGRVersion="1">
<BoundaryGroups BoundaryGroupListRetrieveTime="2021-04-28T15:00:21.637" IsOnVPN="0">
<BoundaryGroup GroupID="16777218" GroupGUID="ad36e248-a857-45e6-ab82-c179bb680b18" GroupFlag="0"/>
</BoundaryGroups>
<ContentInfo PackageFlags="0" DeploymentFlags="9223372036855300962">
<ContentHashValues/>
</ContentInfo>
<Sites>
<Site>
<MPSite SiteCode="DM1" MasterSiteCode="DM1" SiteLocality="LOCAL" IISPreferedPort="80" IISSSLPreferedPort="443"/>
<LocationRecords>
<LocationRecord LocalityEx="BOUNDARYGROUP" DPFallbackIn="PT0M">
<URL Name="http://DEMO1.CONTOSO.LOCAL/SMS_DP_SMSPKG$/9c93cbee-aabc-4daf-996a-4580daa09c87" Signature="http://DEMO1.CONTOSO.LOCAL/SMS_DP_SMSSIG$/9c93cbee-aabc-4daf-996a-4580daa09c87.1.tar" Capability="0"/>
<ADSite Name="Default-First-Site-Name"/>
<IPSubnets>
<IPSubnet Address="192.168.10.0"/>
<IPSubnet Address=""/>
</IPSubnets>
<Metric Value=""/>
<Version>9040</Version>
<Capabilities SchemaVersion="1.0">
<Property Name="SSLState" Value="0"/>
</Capabilities>
<ServerRemoteName>DEMO1.CONTOSO.LOCAL</ServerRemoteName>
<DPType>SERVER</DPType>
<Windows Trust="1"/>
</LocationRecord>
</LocationRecords>
</Site>
</Sites>
<RelatedContentIDs/>
</ContentLocationReply>If the content is not found, you will be able to note the following line in StateMessage.log
State message(State ID : 5003) with TopicType 1702 and TopicId ScopeId_CA3F999B-7A81-43BF-912C-56E267C1E565/DeploymentType_677dac51-d2a2-4bbd-aeb0-4b845aa288cd/1 has been recorded for S-1-5-21-1880864260-2612682489-34998949-6112
Scenario 3: Download Failure Due to Content Distribution Failure
This scenario covers some of the basics in troubleshooting content that has failed to distribute to a distribution point.
Log Files for Troubleshooting Content Distribution in ConfigMgr
Records details about package creation, compression, delta replication, and information updates. It can also include other activities from the distribution manager component. For example, installing a distribution point, connection attempts, and installing components. For more information on other functionality that uses this log, see Service connection point and OS deployment.
Records the actions of the SMS_Executive component that is responsible for sending content from a primary site to a remote distribution point.
Example of Error if the Source Folder Doesn’t Exist or the Site Server Doesn’t Have Access
The source directory \\demo3\Sources\Applications\Igor Pavlov\7-Zip (x64) — MSI Install\aad16824-5471-4dd8-ae69-f71167d7051d\ doesn’t exist or the SMS service cannot access it, Win32 last error = 2
Failed to take snapshot of one or more contents in package DM300013
Scenario 4: Download Failure Due to Invalid Content
The fix for this type of scenario may be as simple as performing an ‘update content’ or ‘redistribute’ the content which is failing. Other times you may have to validate antivirus exclusions on your endpoints and servers. Using the log files to identify what type of error is occurring will be key to resolving the issue and determine where the issue lies.
Example of Error if the Hash of the Downloaded File Does Not Match the Expected Hash
Failed to do hash verification with preference : 4. Try to verify at next hash algorithm
Download failed for content Content_ebb608a6-a6a7-4384-b168-63a0f446b7fb.1 under context S-1-5-21-1880864260-2612682489-34998949-6112, error 0x80091007
The above log files and lines would be helpful from the client when determining if there is a hash mismatch issue. It is good to note that the hash mismatch may not be due to a corrupt file in the Content Library, but it is still worth investigating. This can also commonly be due to Antivirus on the endpoint which lacks the prover exclusions for example.
Example of Error if a File is Missing from the Content Library When a Client Requests It
[CCMHTTP] ERROR: URL=http://DEMO4.CONTOSO.LOCAL:80/SMS_DP_SMSPKG$/Content_ac0256aa-503f-48f1-bfa0-972d685cf50d.1, Port=80, Options=224, Code=0, Text=CCM_E_BAD_HTTP_STATUS_CODE
Successfully queued event on HTTP/HTTPS failure for server ‘DEMO4.CONTOSO.LOCAL’.
Error sending DAV request. HTTP code 404, status ‘Not Found’
GetDirectoryList_HTTP(‘http://DEMO4.CONTOSO.LOCAL:80/SMS_DP_SMSPKG$/Content_ac0256aa-503f-48f1-bfa0-972d685cf50d.1’) failed with code 0x800705b4.
Error retrieving manifest (0x800705b4).
2021-04-29 02:25:19 192.168.10.22 PROPFIND /SMS_DP_SMSPKG$/Content_ac0256aa-503f-48f1-bfa0-972d685cf50d.1 — 80 CONTOSO\DEMO4CLIENT$ 192.168.10.38 SMS+CCM+5.0 — 404 0 0 1704 2
Log Files for Troubleshooting
The Content Access service. Maintains the local package cache on the client.
Records details about the process of remediation and compliance for compliance settings, software updates, and application management.
Records details about configuration item definition downloads.
Records changes in state for configuration items, such as compliance settings, software updates, and applications.
Records tasks that are related to client site assignment.
Records information for Background Intelligent Transfer Service (BITS) jobs on the device.
ContentTransferManager.log
Schedules the Background Intelligent Transfer Service (BITS) or Server Message Block (SMB) to download or access packages.
Records all BITS communication for policy or package access.
Records high-level information about the evaluation, conflict reporting, and remediation of configuration items and applications.
Records the client activity for locating management points, software update points, and distribution points.
Records details about software update state messages that are created and sent to the management point.
Records details about deployments on the client, including software update activation, evaluation, and enforcement. Verbose logging shows additional information about the interaction with the client user interface.
Records location request and reply activity from clients.
Built-in IIS logging — useful for all IIS based ConfigMgr roles. Log location and name may vary.
Meet the Patch My PC Team!: ()
Scenario 1 — What happens on a successful content lookup in SCCM: ()
Review valid boundary, boundary group, and content distribution: () How to Enable Verbose Logging in ConfigMgr/SCCM Client: ()
Client logs for content location request in SCCM: ()
Review Client Log Files CAS.log CIAgent.log CIDownloader.log CIStateStore.log ClientLocation.log CMBITSManager.log ContentTransferManager.log DataTransferService.log DCMAgent.log LocationServices.log StateMessage.log UpdatesDeployment.log : ()
CCIStateStore::GetCIState — Client is requesting CI ModelName: ()
===== CacheManager: Content for Content_{guid} was NOT found cache. =====: ()
Client location request in CAS.log ContentLocationRequest: ()
Review MP_Location.log on the management point and the stored procedure MP_GetContentDPInfo: ()
DataTransferService.log creating a bits download request: ()
Review downloaded update in the CCMCache folder: ()
Review the MP_GetContentDPInfo stored procedure in the ConfigMgr database: ()
Scenario 2 — Boundary Groups Misconfigured: ()
Client is not in a boundary group in SCCM: ()
Attempt application install in SCCM when the client isn’t in boundary group: ()
Application installed fails with error code 0x87D00607 in SCCM/ConfigMgr: ()
Enable fallback for content in the configuration manager site: ()
Troubleshooting content distribution failures in Configuration Manager (SCCM): ()
Content corruption in SMSContentLib directory: ()
Tip: The Fallback=»0″ or Fallback=»1″ controls if fallback is allowed. To learn more about fallback see this .
For scenario 4, we delete a file directly from the FileLib and modify a file directly in the FileLib. We will cover the in a future video. This builds off of scenario 3 by showing specific failure scenarios.





i have a client in our dmz that the client installed but i only have machine policy and user policy. this machine is also my MP in the dmz. i do have other systems installing and reporting back fine. just this system is giving me issues for some reason. i included a few of the logs files where the errors are showing.
ccmsetup.log
Could not retrieve value for MDM_ConfigSetting . Error 0x80041010 ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Updating MDM_ConfigSetting.ClientHealthStatus with value 1 ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Failed to get MDM_ConfigSetting instance, 0x80041010 ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Updating MDM_ConfigSetting.ClientDeploymentErrorCode with value 0 ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Failed to get MDM_ConfigSetting instance, 0x80041010 ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
[5.00.8790.1025] Params to send ‘5.0.8790.1025 Deployment [DP] https://PRI02.xxx.net/SMS_DP_SMSPKG$/xxx00002’ ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
A Fallback Status Point has not been specified and no client was installed. Message with STATEID=’400′ will not be sent. ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Failed to send status 400. Error (87D00215) ccmsetup 6/8/2020 1:59:50 PM 7476 (0x1D34)
Successfully deleted the ccmsetup service ccmsetup 6/8/2020 1:59:55 PM 7476 (0x1D34)
Deleted file C:Windowsccmsetupccmsetup.xml ccmsetup 6/8/2020 1:59:55 PM 7460 (0x1D24)
Task ‘Configuration Manager Client Upgrade Task’ does not exist ccmsetup 6/8/2020 1:59:55 PM 7460 (0x1D24)
Could not retrieve value for MDM_ConfigSetting . Error 0x80041010 ccmsetup 6/8/2020 1:59:55 PM 7460 (0x1D24)
Removed temporary download directory. ccmsetup 6/8/2020 1:59:55 PM 7460 (0x1D24)
CcmSetup is exiting with return code 0 ccmsetup 6/8/2020 1:59:55 PM 7460 (0x1D24)
locationservices.log
Instance of CCM_WindowsDOClientConfig doesn’t exist in WMI LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
This device is not enrolled into Intune. LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
This device is not externally managed. LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
Current AD site of machine is xxx LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
Current AD site of machine is xxx LocationServices 6/16/2020 4:59:05 PM 1860 (0x0744)
Received reply of type PortalCertificateReply LocationServices 6/16/2020 4:59:05 PM 1552 (0x0610)
The reply from location manager contains 0 certificates LocationServices 6/16/2020 4:59:05 PM 1552 (0x0610)
Updating portal certificates LocationServices 6/16/2020 4:59:05 PM 1552 (0x0610)
There are no certificates available to install LocationServices 6/16/2020 4:59:05 PM 1552 (0x0610)
1 assigned MP errors in the last 10 minutes, threshold is 5. LocationServices 6/16/2020 4:59:05 PM 5024 (0x13A0)
Hey folks, here with a quick post today in response to a question about ConfigMgr client deployment in the WinAdmins Community the other day. The question was posed in regards to alternative ways to deploy the CM client without using Client Push, because Client Push is bad and no one should use it for various reasons. The common answer is to use some form of startup script, such as the ConfigMgr Client Health Script by Anders Rødland, or the ConfigMgr Client Startup Script by Jason Sandys. However, there’s another method that can be used in environments where using scripts like this is not desirable for one reason or another: software update based client deployment. Microsoft documents this use here, however, I feel that their method could be made a bit more flexible.
WARNING: This post will go over directly setting registry items that are normally configured via Group Policy administrative templates, which may or not be 100% supported. It works it theory and in practice, but be forewarned, your mileage may vary, etc.
Prerequisites
- At least one active Software Update Point in your ConfigMgr site
- Updates classification enabled in SUP configuration
- Software update based client installation option enabled
- ConfigMgr site published to Active Directory
- Since software update based deployment does not support custom installation parameters, it must be able to discover the CM site information from AD
Configuration
Microsoft’s recommendation is to configure a Group Policy Object using the Windows Update admin template, similar to the following:
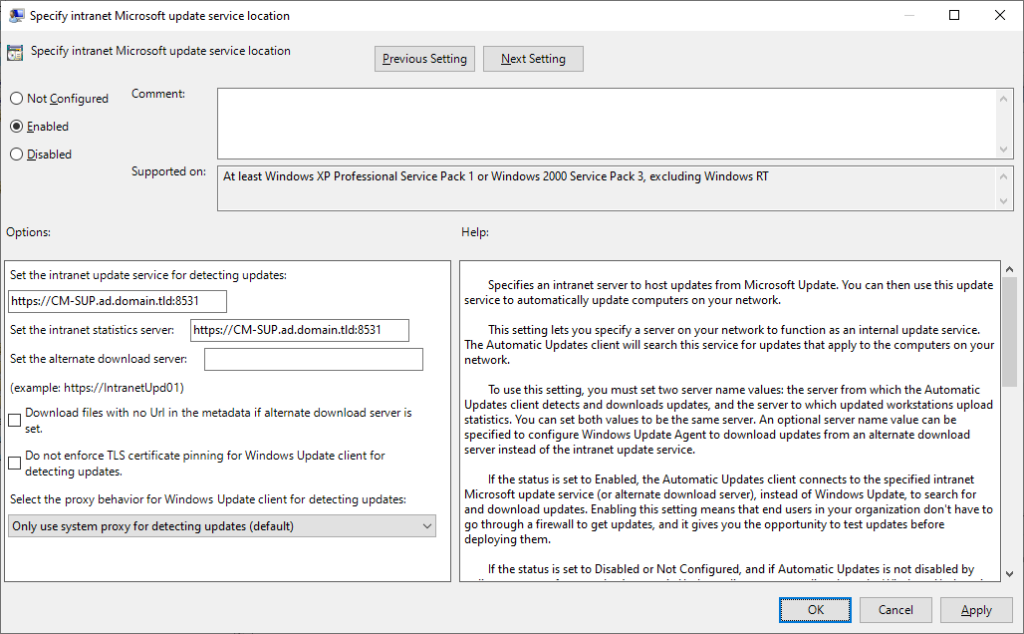
This seems pretty simple, but now you need to think about where it is linked. This setting should not be configured via Group Policy on CM-managed clients, so we need a way for it to no longer apply once the client is installed. Aha, I’ll use a WMI filter!
|
select Name from Win32_service where Name = ‘ccmexec’ |
But that will filter on computers with the service, not without, and I don’t think it’s quick and easy to make a “not” version of that query. Welcome to the stage, Group Policy Preferences, and Item Level Targeting!
Instead of using the admin template, create 3 new computer registry preferences, as follows (replace “https://CM-SUP.ad.domain.tld:8531” with your top-level Software Update Point URL):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
Hive: HKLM Key Path: SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate Value Name: WUServer Value Type: String Value Data: https://CM—SUP.ad.domain.tld:8531 Hive: HKLM Key Path: SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate Value Name: WUStatusServer Value Type: String Value Data: https://CM—SUP.ad.domain.tld:8531 Hive: HKLM Key Path: SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU Value Name: UseWUServer Value Type: DWORD Value Data: 1 |
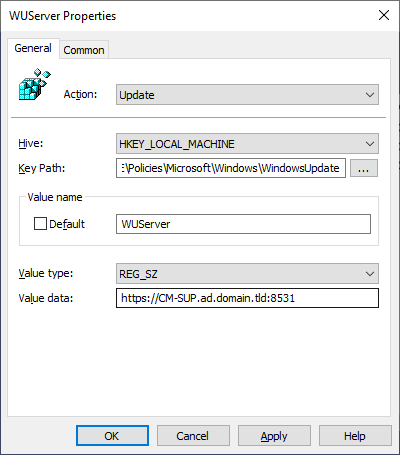
Next, configure each of these preferences with Item Level Targeting:
|
Item Type: Registry Match Item Options: Is Not Match Type: Key Exists Hive: HKEY_LOCAL_MACHINE Key Path: SYSTEM\CurrentControlSet\Services\CcmExec |
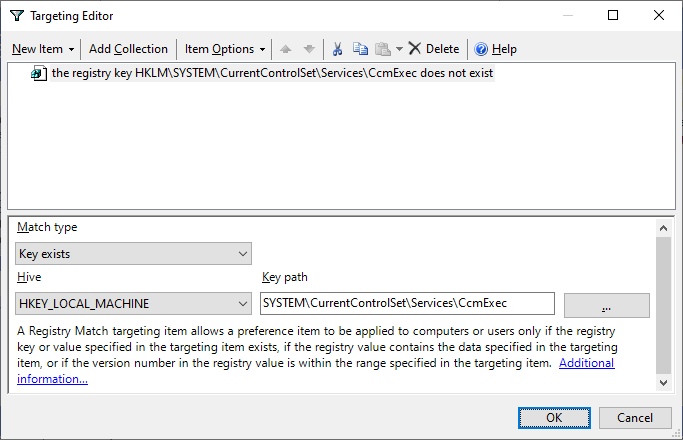
Once this GPO is configured, link it to an OU containing computer objects that you want to target, and when they next scan for updates, they will only be offered the ConfigMgr client, and become managed!

There is definitely a lot of confusion about how Group Policies interact with, control, and affect Software Update Management (SUM) on ConfigMgr clients. At the outset of this post (or series of posts), I don’t even know exactly what’s going to happen with some of the different settings and combinations that I’m going to try and then document.
The Windows Update Agent
The Windows Update Agent (WUA) is the key Windows component that handles both update scanning and update application to a system — this is the same whether the system uses Microsoft Updates from the web, WSUS, or ConfigMgr for updates. Because ConfigMgr actually uses WSUS, these two methods have a few things in common, specifically, the actual delivery of the update catalog to the clients. In both cases, this comes straight from WSUS and thus the use of the same group policy setting(s). Additionally, there are other settings in group policy that effect how the WUA agent behaves which I intend to explore.
Domain Group Policies vs. Local Group Policies.
As their names imply, domain group polices originate from the domain and local group policies originate on the local system. A common misconception is that local group policies are simply local registry edits in one of the above policy keys. This is not true; although you may get the desired result, this is not a true local group policy. To edit a local group policy, you must open the local group policy editor: gpedit.msc. Also note that domain group policies overwrite settings defined in a local group policy without prejudice on a setting by setting basis. Thus, only settings actually configured in the domain group policy will trump those defined in the local group policy; settings defined in a local group policy and not in the domain group policy will be left unaffected.
Why is the local vs. domain distinction important? Because ConfigMgr uses local group policies to configure the Windows Update settings on all managed clients. The clear implication here is that if you have any Windows Update settings in a domain group policy, they will overwrite those that ConfigMgr sets. The settings in the screenshot below were configured by the ConfigMgr agent in my lab environment and viewed using gpedit.msc.
So what happens if we do have a domain group policy and how can we troubleshoot this? It depends on which settings are applied in the domain group policy.
Setting the Server
The first setting to test is the actual update server. First, I’ll set it to the same value that ConfigMgr sets it to.
First a gpupdate /force and then initiate a Software Update Scan Cycle from the ConfigMgr agent Control Panel applet and check wuahandler.log on the client.
So far so good. Next, let’s set the domain group policy to point to another server and see what happens.
Another gpupdate /force, initiate a Software Update Scan Cycle again, and finally check wuahandler.log.
Egregious FAIL!
Notice what the log file says here: “Group policy settings were overwritten by a higher authority”. From this it is apparent that ConfigMgr checks to make sure that the WSUS settings do match up with those that it expects, namely the server location, and if they don’t it “gracefully” stops processing.
One of the first things I tried way back when at a customer site was to trick the process by overwriting the values directly in the registry. As many folks know, all of the group policies contained in the Administrative Templates section ultimately just set registry values (see What Is Administrative Templates Extension? for more information). The Windows Updates settings are in this section and thus update specific registry values located in HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate; note that the WUA will not automatically notice that you’ve updated the values manually so you must restart the Automatic Updates service to make them effective.
So what are the results? As you may (or may not) expect, everything worked. Of course, as soon as group policy decides to refresh, you’re back at square one.
One thing I learned in testing and verifying the above was that if the Windows Update server is set to a name that either does not resolve or is not a valid WSUS server, Windows Update is not a happy camper and neither is the ConfigMgr agent. It took multiple stops and starts of the Automatic Updates service and the SMS Agent Host once a valid update server is set for everything to work as expected again. It seems that if Windows Update has any kind of error connecting to the configured update server, the ConfigMgr agent refuses to do anything as far as software updates go — the wuahandler.log will show an initial error message but then will not show anything else until the problem is corrected, which as I just mentioned, took restarting both services. If I was patient, I think things might sort themselves out eventually, but restarting the services expedited the process.
XP: Keep Your Computer Up To Date
Another thing I noticed on my XP test client is that if there are no policies applied, either local or domain, and Windows Update has not been manually configured, then the “Keep your computer up to date” notification icon is displayed along with the associated balloon message. This is the default state of all Windows XP systems in my experience.
As soon as a Windows Update policy is applied though, including the ConfigMgr local group policy for Windows Updates, the icon and balloon are removed. This can be seen in the WindowsUpdate.log.
Windows 7: Action Center
The (nearly) equivalent behavior in Windows 7 is handled by the Action Center as seen below. However, getting rid of this message is not the same as in XP. The Action Center is a completely separate component from Windows Update and thus its messages are not generated by the WUA itself. To get rid of this message, you must set the “Configure Automatic Updates” setting; the local group policy set by ConfigMgr for Windows Updates is not sufficient. By default (in my testing at least), this setting is already set on the component at install time to “Auto download and schedule the install” and so you don’t actually need to do anything. If for some reason it’s not set though, just use a group policy to set it (local or domain).
If you set the “Configure Automatic Updates” setting to anything other than the default “Auto download and schedule the install” including disabling it, the Action Center will show the following message:
The Action Center itself is way beyond the scope of this blog, but I did dig up a few links for reference:
This blog post is long enough now so I’ll continue in another post tomorrow (hopefully). Next up is looking at the other “Configure Automatic Updates” settings and how they affect Software Updates in ConfigMgr as well as actually stopping the WUA service (i think we can all guess what happens when we do that).
