Sometimes Windows system displays error messages regarding corrupted or missing OBJECTS.DATA files. Situations like that can occur, for example, during a software installation process. Each software program requires certain resources, libraries, and source data to work properly. Corrupted or nonexistent OBJECTS.DATA file can therefore effect in failed execution of the started process.
OBJECTS.DATA file Analysis Studio Offline Data. The file was developed by Microsoft for use with Office software. Here you will find detailed information about the file and instructions how to proceed in the event of OBJECTS.DATA related errors on your device. You can also download OBJECTS.DATA file compatible with Windows 10, Windows 10, Windows 8.1, Windows 8, Windows 7, Windows 7, Windows Vista, Windows Vista, Windows XP, Windows XP, Windows XP, Windows XP, Windows XP, Windows XP, Windows 8 devices which will (most probably) allow you to solve the problem.
Compatible with: Windows 10, Windows 10, Windows 8.1, Windows 8, Windows 7, Windows 7, Windows Vista, Windows Vista, Windows XP, Windows XP, Windows XP, Windows XP, Windows XP, Windows XP, Windows 8
User popularity
Fix OBJECTS.DATA errors
- 1 Information about OBJECTS.DATA file
- 2 Errors related to OBJECTS.DATA file
- 3 How to fix OBJECTS.DATA related errors?
- 3.1 Scanning for malicious software
- 3.2 System and driver update
- 3.3 System File Checker tool
- 3.4 System recovery
- 4 Download OBJECTS.DATA
- 4.1 List of OBJECTS.DATA file versions
File info
| General information | |
|---|---|
| Filename | OBJECTS.DATA |
| File extension | DATA |
| Type | Data |
| Description | Analysis Studio Offline Data |
| Software | |
|---|---|
| Program | Office 2010 |
| Software | Office |
| Author | Microsoft |
| Software version | 2010 |
| Details | |
|---|---|
| File size | 14835712 |
| Oldest file | 2017-04-24 |
| Latest file | 2017-05-10 |
There are various types of errors related to OBJECTS.DATA file. OBJECTS.DATA file may be located in wrong file directory on your device, may not be present in the system, or may be infected with malicious software and therefore not work correctly. Below is a list of most common error messages related to OBJECTS.DATA file. If you encounter one listed below (or similar), please consider the following suggestions.
- OBJECTS.DATA is corrupted
- OBJECTS.DATA cannot be located
- Runtime Error — OBJECTS.DATA
- OBJECTS.DATA file error
- OBJECTS.DATA file cannot be loaded. Module was not found
- cannot register OBJECTS.DATA file:
- OBJECTS.DATA file could not be loaded
- OBJECTS.DATA file doesn’t exist
OBJECTS.DATA
Application could not be started because OBJECTS.DATA file is missing. Reinstall the application to solve the problem.
OK
Problems related to OBJECTS.DATA can be addressed in various ways. Some methods are meant only for advanced users. If you don’t have confidence in your skills, we suggest consulting a specialist. Fixing OBJECTS.DATA file errors should be approached with utmost caution for any mistakes can result in unstable or unproperly working system. If you have the necassary skills, please proceed.
OBJECTS.DATA file errors can be caused by various factors, so its is beneficial to try to fix them using various methods.
Step 1: Scan your computer for any malicious software
Windows files are commonly attacked by malicious software that prevents them from working properly. First step in addressing problems with OBJECTS.DATA file or any other Windows system files should be scanning the system for malicious software using an antivirus tool.
If by any chance you don’t have any antivirus software installed on your system yet, you should do it immediately. Unprotected system is not only a source of file errors, but, more importantly, makes your system vulnerable to many dangers. If you don’t know which antivirus tool to choose, consult this Wikipedia article – comparison of antivirus software.
Step 2: Update your system and drivers.
Installing relevant Microsoft Windows patches and updates may solve your problems related to OBJECTS.DATA file. Use dedicated Windows tool to perform the update.
- Go to the Windows «Start» menu
- Type «Windows Update» in the search field
- Choose the appropriate software program (name may vary depending on your system version)
- Check if your system is up to date. If any unapplied updates are listed, install them immediately.
- After the update has been done,restart your computer in order to complete the process.
Beside updating the system, it is recommended that you install latest device drivers, as drivers can influence proper working of OBJECTS.DATA or other system files. In order to do so, go to your computer or device producer’s website where you will find information regarding latest driver updates.
Step 4: Restoring Windows system
Another approach is to restore system to previous state, before the OBJECTS.DATA file error occured. In order to restore your system, follow the instructions below
- Go to the Windows «Start» menu
- Type «System Restore» in the search field
- Start the system restore tool – it’s name may differ depending on version of the system
- The application will guide you through the process – read the messages carefully
- After the process has finished, restart your computer.
If all the above-mentioned methods failed and the OBJECTS.DATA file problem has not been resolved, proceed to the next step. Remember that the following steps are intended only for advanced users.
Download and replace OBJECTS.DATA file
The last solution is to manually download and replace OBJECTS.DATA file in appropriate folder on the disk. Select file version compatible with your operating system and click the «Download» button. Next, go to your web browser’s «Downloaded» folder and copy the downloaded OBJECTS.DATA file.
Go to the folder where the file should be located and paste the downloaded file. Below is the list of OBJECTS.DATA file example directory paths.
- Windows 10: C:\Windows\System32\wbem\Repository\
- Windows 10: C:\Windows\System32\wbem\Repository\
- Windows 8.1: C:\Windows\System32\wbem\Repository\
- Windows 8: 1: C:\Windows\System32\wbem\Repository\
- Windows 7: —
- Windows 7: —
- Windows Vista: —
- Windows Vista: —
- Windows XP: —
- Windows XP: —
- Windows XP: —
- Windows XP: —
- Windows XP: —
- Windows XP: —
- Windows 8: —
If the steps did not solve your OBJECTS.DATA file problem, you should consult a professional. A probability exists that the error(s) might be device-related and therefore should be resolved at the hardware level. A fresh operating system installation might be necessary – a faulty system installation process can result in data loss.
File versions list
Filename
OBJECTS.DATA
System
Windows 10
File size
18333696 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | 29ca9961eadfed47ed8a68dec732b263 | |
| SHA1 | a4835aef8e0c2180fb7405f363f63d6214dedb54 | |
| SHA256 | 1139ea014b95c4049cc35e6adfdce57cf1cc01602e3ba3d9829537a3ca0efd98 | |
| CRC32 | 31a0185b | |
| Example file location | C:\Windows\System32\wbem\Repository\ |
Filename
OBJECTS.DATA
System
Windows 10
File size
22429696 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | ff65d7fa716ec306604279c4eed44535 | |
| SHA1 | 4cdf66f75399c7da44781412669974ea7956782b | |
| SHA256 | 1b579bbc1ff630a9eaba0a7687643c4f0d79a41b7422a0d9c799a0879b6164b8 | |
| CRC32 | b109fe1a | |
| Example file location | C:\Windows\System32\wbem\Repository\ |
Filename
OBJECTS.DATA
System
Windows 8.1
File size
25468928 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | f4ca89bc855182959c62e83b0fde47d2 | |
| SHA1 | cb472ff4f0651b80c1044912cec1336eaf26f0aa | |
| SHA256 | 62e58d1b0719914264333da5fdec9350838376d233886c632f6e73e3f7b6c028 | |
| CRC32 | 179fcfcc | |
| Example file location | C:\Windows\System32\wbem\Repository\ |
Filename
OBJECTS.DATA
System
Windows 8
File size
18333696 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | 6dfff7017ab46e30b05462114856392e | |
| SHA1 | dac75aa9d1f5e8c0faefcfb4a6966a9cd6e07ec1 | |
| SHA256 | b7a97ad6eb07f9ffa753845cc9310c9afd91550c283a050f628bcd966219340f | |
| CRC32 | 7bea2584 | |
| Example file location | 1: C:\Windows\System32\wbem\Repository\ |
Filename
OBJECTS.DATA
System
Windows 7
File size
14835712 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | 2e933c159e38b3422014f8eac5750967 | |
| SHA1 | 61d3be7c52b46e1a2f54c221a6d7ca484e138205 | |
| SHA256 | fa24ad50b20a45803db5a00befaf335ca26bb608633b07751fc4a94f783fc917 | |
| CRC32 | d4e3001f | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows 7
File size
14311424 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | 3ba6628bbb50967346bee98d0e9bdf8f | |
| SHA1 | e351b86079bcdd26fe7e9660e858b23bc1721b7f | |
| SHA256 | dff5efd0b4bad24810cdd070a90edb9e4ac13519a0e2f0965d61702b8cb028d8 | |
| CRC32 | 757e7a55 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows Vista
File size
23175168 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | 687d4a71e5e56f71a976b9181f6e1c7c | |
| SHA1 | 33f715c37c8db35f6f54e6304c837d414f7303db | |
| SHA256 | b923ff99f923fdc93378b6c268d8893fa48d2b5407d3d6bbafaed81c8a412188 | |
| CRC32 | af4ab42f | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows Vista
File size
23076864 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | 1e5eeb8cc3303eab04bc85cf6f769568 | |
| SHA1 | 7bc0f78c086f118422f2f8efea5e31c04601b0cd | |
| SHA256 | 631d99f1e13ee6f32f5e50ac5f1a5645903729b4626c656b25a70b2b29d85609 | |
| CRC32 | dc798280 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
4055040 bytes
Date
-0001-11-30
| File details | ||
|---|---|---|
| MD5 | 2672f6d88b957ef92674f987b3e85e03 | |
| SHA1 | 21c48e5bfa93dfc1dd9e53c28347c7ad30168f9a | |
| SHA256 | 19ca379bd6bb76fc0b58d93e59794047388f2cd5d4e14bf6736634f7f92f9ba7 | |
| CRC32 | bdfe3376 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
4055040 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | a706badf9e693cc3c7488a4fe6191573 | |
| SHA1 | 402dc89a13516d8182537b94fcf861391df7529b | |
| SHA256 | b6e6ce82e42d1c8f7b102644e3065f2971006daa1b1be2954d63dc411d9a33bd | |
| CRC32 | 30be7eef | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
5054464 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | 44601aa506a9dc72c7f4311a38f2cd82 | |
| SHA1 | dbd7dd0aff68726d117f22d686c2290f684a3b2d | |
| SHA256 | 03f785a0b0d8f18b4f034556ab2c052cc6eb0fb62fd49808ec9d085dd4936faa | |
| CRC32 | 9de70c10 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
4055040 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | b39fd09f209d9b7f2dc57325ac692472 | |
| SHA1 | 520fd398c997d067282306c0e99cb85e243da555 | |
| SHA256 | 84d8197a1418e9c0502041a0e70d3dd7fff2215db84209548b8952c8d4f08f1a | |
| CRC32 | 8c8afae3 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
4055040 bytes
Date
-0001-11-30
| File details | ||
|---|---|---|
| MD5 | ee7eec2e9d124264a6c9ee0887788b8a | |
| SHA1 | abb02d097ad00c9108e20b433371495837c01321 | |
| SHA256 | 694826478eb59c62d845a6e34f2886e3d6bfdcd7919b7d2d80df04a2d73ea32f | |
| CRC32 | 9767f226 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows XP
File size
4055040 bytes
Date
2017-04-24
| File details | ||
|---|---|---|
| MD5 | 30b57a6f6f2adf932de152ff242e3688 | |
| SHA1 | ad92008423bfef0225ec879b34c8d40d8797f395 | |
| SHA256 | ca8d51f00565e1de71860828edfad5689a3f44dc822e7ecabfdd49955b01fa87 | |
| CRC32 | 4fdc23e2 | |
| Example file location | — |
Filename
OBJECTS.DATA
System
Windows 8
File size
18333696 bytes
Date
2017-05-10
| File details | ||
|---|---|---|
| MD5 | 29ca9961eadfed47ed8a68dec732b263 | |
| SHA1 | a4835aef8e0c2180fb7405f363f63d6214dedb54 | |
| SHA256 | 1139ea014b95c4049cc35e6adfdce57cf1cc01602e3ba3d9829537a3ca0efd98 | |
| CRC32 | 31a0185b | |
| Example file location | — |
Последнее обновление: 11/27/2024
[Среднее время чтения: 4,5 мин.]
Файл OBJECTS.DATA, также известный как файл Analysis Studio Offline Data, был создан компанией CubedLabs для разработки YouTube Download & Convert 1.1.4. Файлы DATA относятся к категории типов файлов Data (Analysis Studio Offline Data).
Первая версия OBJECTS.DATA для Windows XP была представлена 10/25/2001 в Windows XP.
04/09/2008 вышла версия 1.1.4 для YouTube Download & Convert 1.1.4.
В этой короткой статье приводятся подробные сведения о файле, шаги по устранению проблем DATA с OBJECTS.DATA и список бесплатных загрузок для каждой версии, содержащейся в нашем полном каталоге файлов.
Что такое сообщения об ошибках OBJECTS.DATA?
Общие ошибки выполнения OBJECTS.DATA
Ошибки файла OBJECTS.DATA часто возникают на этапе запуска YouTube Download & Convert, но также могут возникать во время работы программы.
Эти типы ошибок DATA также известны как «ошибки выполнения», поскольку они возникают во время выполнения YouTube Download & Convert. К числу наиболее распространенных ошибок выполнения OBJECTS.DATA относятся:
- Не удается найти OBJECTS.DATA.
- OBJECTS.DATA — ошибка.
- Не удалось загрузить OBJECTS.DATA.
- Ошибка при загрузке OBJECTS.DATA.
- Не удалось зарегистрировать OBJECTS.DATA / Не удается зарегистрировать OBJECTS.DATA.
- Ошибка выполнения — OBJECTS.DATA.
- Файл OBJECTS.DATA отсутствует или поврежден.
Библиотека времени выполнения Microsoft Visual C++
Ошибка выполнения!
Программа: C:\Windows\System32\wbem\Repository\OBJECTS.DATA
Среда выполнения получила запрос от этого приложения, чтобы прекратить его необычным способом.
Для получения дополнительной информации обратитесь в службу поддержки приложения.
В большинстве случаев причинами ошибок в DATA являются отсутствующие или поврежденные файлы. Файл OBJECTS.DATA может отсутствовать из-за случайного удаления, быть удаленным другой программой как общий файл (общий с YouTube Download & Convert) или быть удаленным в результате заражения вредоносным программным обеспечением. Кроме того, повреждение файла OBJECTS.DATA может быть вызвано отключением питания при загрузке YouTube Download & Convert, сбоем системы при загрузке или сохранении OBJECTS.DATA, наличием плохих секторов на запоминающем устройстве (обычно это основной жесткий диск) или заражением вредоносным программным обеспечением. Таким образом, крайне важно, чтобы антивирус постоянно поддерживался в актуальном состоянии и регулярно проводил сканирование системы.
Как исправить ошибки OBJECTS.DATA — 3-шаговое руководство (время выполнения: ~5-15 мин.)
Если вы столкнулись с одним из вышеуказанных сообщений об ошибке, выполните следующие действия по устранению неполадок, чтобы решить проблему OBJECTS.DATA. Эти шаги по устранению неполадок перечислены в рекомендуемом порядке выполнения.
Шаг 1. Восстановите компьютер до последней точки восстановления, «моментального снимка» или образа резервной копии, которые предшествуют появлению ошибки.
Чтобы начать восстановление системы (Windows XP, Vista, 7, 8 и 10):
- Нажмите кнопку «Пуск» в Windows
- В поле поиска введите «Восстановление системы» и нажмите ENTER.
- В результатах поиска найдите и нажмите «Восстановление системы»
- Введите пароль администратора (при необходимости).
- Следуйте инструкциям мастера восстановления системы, чтобы выбрать соответствующую точку восстановления.
- Восстановите компьютер к этому образу резервной копии.
Если на этапе 1 не удается устранить ошибку OBJECTS.DATA, перейдите к шагу 2 ниже.
Шаг 2. Если вы недавно установили приложение YouTube Download & Convert (или схожее программное обеспечение), удалите его, затем попробуйте переустановить YouTube Download & Convert.
Чтобы удалить программное обеспечение YouTube Download & Convert, выполните следующие инструкции (Windows XP, Vista, 7, 8 и 10):
- Нажмите кнопку «Пуск» в Windows
- В поле поиска введите «Удалить» и нажмите ENTER.
- В результатах поиска найдите и нажмите «Установка и удаление программ»
- Найдите запись для YouTube Download & Convert 1.1.4 и нажмите «Удалить»
- Следуйте указаниям по удалению.
После полного удаления приложения следует перезагрузить ПК и заново установить YouTube Download & Convert.
Если на этапе 2 также не удается устранить ошибку OBJECTS.DATA, перейдите к шагу 3 ниже.
YouTube Download & Convert 1.1.4
CubedLabs
Шаг 3. Выполните обновление Windows.
Когда первые два шага не устранили проблему, целесообразно запустить Центр обновления Windows. Во многих случаях возникновение сообщений об ошибках OBJECTS.DATA может быть вызвано устаревшей операционной системой Windows. Чтобы запустить Центр обновления Windows, выполните следующие простые шаги:
- Нажмите кнопку «Пуск» в Windows
- В поле поиска введите «Обновить» и нажмите ENTER.
- В диалоговом окне Центра обновления Windows нажмите «Проверить наличие обновлений» (или аналогичную кнопку в зависимости от версии Windows)
- Если обновления доступны для загрузки, нажмите «Установить обновления».
- После завершения обновления следует перезагрузить ПК.
Если Центр обновления Windows не смог устранить сообщение об ошибке OBJECTS.DATA, перейдите к следующему шагу. Обратите внимание, что этот последний шаг рекомендуется только для продвинутых пользователей ПК.
Если эти шаги не принесут результата: скачайте и замените файл OBJECTS.DATA (внимание: для опытных пользователей)
Если ни один из предыдущих трех шагов по устранению неполадок не разрешил проблему, можно попробовать более агрессивный подход (примечание: не рекомендуется пользователям ПК начального уровня), загрузив и заменив соответствующую версию файла OBJECTS.DATA. Мы храним полную базу данных файлов OBJECTS.DATA со 100%-ной гарантией отсутствия вредоносного программного обеспечения для любой применимой версии YouTube Download & Convert . Чтобы загрузить и правильно заменить файл, выполните следующие действия:
- Найдите версию операционной системы Windows в нижеприведенном списке «Загрузить файлы OBJECTS.DATA».
- Нажмите соответствующую кнопку «Скачать», чтобы скачать версию файла Windows.
- Скопируйте этот файл в соответствующее расположение папки YouTube Download & Convert:
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\Показать на 195 каталогов больше +
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\
Windows 10: C:\Windows\System32\wbem\Repository\ - Перезагрузите компьютер.
Если этот последний шаг оказался безрезультативным и ошибка по-прежнему не устранена, единственно возможным вариантом остается выполнение чистой установки Windows 10.
СОВЕТ ОТ СПЕЦИАЛИСТА: Мы должны подчеркнуть, что переустановка Windows является достаточно длительной и сложной задачей для решения проблем, связанных с OBJECTS.DATA. Во избежание потери данных следует убедиться, что перед началом процесса вы создали резервные копии всех важных документов, изображений, установщиков программного обеспечения и других персональных данных. Если вы в настоящее время не создаете резервных копий своих данных, вам необходимо сделать это немедленно.
Скачать файлы OBJECTS.DATA (проверено на наличие вредоносного ПО — отсутствие 100 %)
ВНИМАНИЕ! Мы настоятельно не рекомендуем загружать и копировать OBJECTS.DATA в соответствующий системный каталог Windows. CubedLabs, как правило, не выпускает файлы YouTube Download & Convert DATA для загрузки, поскольку они входят в состав установщика программного обеспечения. Задача установщика заключается в том, чтобы обеспечить выполнение всех надлежащих проверок перед установкой и размещением OBJECTS.DATA и всех других файлов DATA для YouTube Download & Convert. Неправильно установленный файл DATA может нарушить стабильность работы системы и привести к тому, что программа или операционная система полностью перестанут работать. Действовать с осторожностью.
Файлы, относящиеся к OBJECTS.DATA
Файлы DATA, относящиеся к OBJECTS.DATA
| Имя файла | Описание | Программное обеспечение (версия) | Размер файла (в байтах) | Расположение файла |
|---|---|---|---|---|
| OBJECTS.DATA | Analysis Studio Offline Data | YouTube Download & Convert 1.1.4 | 23986176 | C:\Windows\inf\ |
Другие файлы, связанные с OBJECTS.DATA
| Имя файла | Описание | Программное обеспечение (версия) | Размер файла (в байтах) | Расположение файла |
|---|---|---|---|---|
| SA.DAT | Game Data | YouTube Download & Convert 1.1.4 | 6 | C:\WINDOWS\Tasks\ |
| WmiApRpl.h | C/C++/Objective-C Header | YouTube Download & Convert 1.1.4 | 3444 | C:\Windows\System32\wbem\Performance\ |
| api-ms-win-core-sysinf… | ApiSet Stub DLL | Microsoft® Windows® Operating System (10.0.17134.12) | 12136 | C:\Users\Tester\AppData\Local\Microsoft\OneDriv… |
| diagwrn.xml | Extensible Markup Language | YouTube Download & Convert 1.1.4 | 5718 | C:\Windows\System32\Sysprep\Panther\ |
| api-ms-win-core-dateti… | ApiSet Stub DLL | Microsoft® Windows® Operating System (10.0.17134.12) | 11112 | C:\Users\Tester\AppData\Local\Microsoft\OneDriv… |
Rusty
-
-
#1
I have been recently cleaning up my hard drive and found
that one of the biggest files is
C:\WINDOWS\system32\wbem\Repository\FS\OBJECTS.DATA
which is 1.2 GIGs worth(!?)
So a few questions:
1. What does it do?
2. Is it safe to delete it?
3. How can I delete it?
TIA!
Rusty
-
-
#3
I guess I should have mentioned I already tried an extensive Google
search, and turned up very little, just a number of posts saying that
the file won’t defrag.
I hope someone in this group knows what OBJECTS.DATA is and what it does.
-
-
#4
Can I comment without register? oh, i can’t.
sorry for alterting you Rusty but I find this file ( OBJECTS.DATA) while browsing my PC by Datemodified to see what keep generating space. This file show up in my C search. But I’m running Windows10 since 2017
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
Appearance settings
- What is WMI?
- Understanding WMI Persistence
- How does a WMI persistent object look like?
- WMI Persistence Template by Matt G.
- WMI Persistence via PowerLurk by Sw4mpf0x
- WMI Persistence Detection
- What about DFIR?
- Detection Logics & Lessons Learned
- So, to summarize
- Changes to your Sysmon Config
- Some references
- EventCode 400 sample contents
- EventCode 403 sample contents
What is WMI?
WMI is Microsoft’s implementation of WBEM (Web Based Enterprise Management) which is based on CIM and allows for the remote management of multiple system components in Windows environments. WMI is used on a daily basis by sysadmins across large domains due to its flexibility and scalability. Easy to deploy, scripts that leverage WMI can be seen everywhere. Unfortunately, as with everything that is widely deployed, has “remote” capabilities and runs on “windows”: the dark force is strong around it (just for fun: MS17-010).
It is known that WMI can be abused in many ways to either gather information, make changes and create persistence mechanisms. An excellent article by Matt Graeber (@mattifestation) called Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor was an eye opener for many of us in the cybersec world. We knew this was possible, but forgot how flexible it was. The main strength of WMI persistence is its stealthiness and effectiveness. When a command is executed by WMI as a result of “evil” the only thing you will see is WmiPrvse.exe as the process. Distinguishing a valid system action from an invalid one is very hard under these circumstances. In other words, WMI persistence defeats non-repudiation!
What I will cover here are different methods for detecting WMI persistence that you could leverage within your network to hunt for this treat.
Understanding WMI Persistence
First, rather than re-inventing the wheel, I will link here below the sources that I consulted to learn more about WMI:
- Matt Graeber’s article (mentioned above)
- Pentestarmoury article “Creeping on Users with WMI Events” by Sw4mp_f0x. He also developed PowerLurk (see below)
- Permanent WMI Subscriptions
- Derbycon 2015 presentation by Matt
How does a WMI persistent object look like?
Let’s use two scripts that allow us to easily create a malicious persistence without having to do it step by step (have a look at the PS files to understand all the bits and pieces involved), namely:
- PowerLurk by Sw4mp_f0x
- WMI Persistence Template Gist by Matt G.
- Alternatively, you can also use an adaptation of Matt’s work by n0pe-sled WMI-Persistence.ps1
WMI Persistence Template by Matt G.
We tweaked some of the parameters in the script to make sure the timer event launches every minute and that no cleanup is performed at the end. After launching it, we can inspect the newly created Event Consumers/Filters/Bindings as follows:
EventFilter
Get-WmiObject -Namespace root\subscription -Class __EventFilterResult:
__GENUS : 2
__CLASS : __EventFilter
__SUPERCLASS : __IndicationRelated
__DYNASTY : __SystemClass
__RELPATH : __EventFilter.Name="TimerTrigger"
__PROPERTY_COUNT : 6
__DERIVATION : {__IndicationRelated, __SystemClass}
__SERVER : W10B1
__NAMESPACE : ROOT\subscription
__PATH : \\W10B1\ROOT\subscription:__EventFilter.Name="TimerTrigger"
CreatorSID : {1, 5, 0, 0...}
EventAccess :
EventNamespace : root/cimv2
Name : TimerTrigger
**Query : SELECT * FROM __TimerEvent WHERE TimerID = 'PayloadTrigger'**
QueryLanguage : WQL
PSComputerName : W10B1EventConsumer
Get-WmiObject -Namespace root\subscription -Class __EventConsumerResult:
[snip]
__GENUS : 2
__CLASS : CommandLineEventConsumer
__SUPERCLASS : __EventConsumer
__DYNASTY : __SystemClass
__RELPATH : CommandLineEventConsumer.Name="ExecuteEvilPowerShell"
__PROPERTY_COUNT : 27
__DERIVATION : {__EventConsumer, __IndicationRelated, __SystemClass}
__SERVER : W10B1
__NAMESPACE : ROOT\subscription
__PATH : \\W10B1\ROOT\subscription:CommandLineEventConsumer.Name="ExecuteEvilPowerShell"
**CommandLineTemplate : powershell.exe -NoP -C "iex ([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String((Get-ItemProperty -Path HKLM:\SOFTWARE\PayloadKey -Name PayloadValue).PayloadValue)))"**FilterToConsumerBinding
Get-WmiObject -Namespace root\subscription -Class __FilterToConsumerBindingResult:
[snip]
__NAMESPACE : ROOT\subscription
**__PATH : \\W10B1\ROOT\subscription:__FilterToConsumerBinding.Consumer="CommandLineEventConsumer.Name=\"ExecuteEvilPowerShell\"",Filter="__EventFilter.Name=\"TimerTrigger\""**
**Consumer : CommandLineEventConsumer.Name="ExecuteEvilPowerShell"**
CreatorSID : {1, 5, 0, 0...}
DeliverSynchronously : False
DeliveryQoS :
**Filter : __EventFilter.Name="TimerTrigger"**As we can observe, this persistence is based off a Timer intrinsic Event type. If you launched it and head to C:\ you will see the payload_result.txt file as per the script:
$TimerArgs = @{
IntervalBetweenEvents = ([UInt32] 6000) # 6000 ms == 1 min
SkipIfPassed = $False
TimerId = $TimerName
}
$Payload = {
# Prep your raw beacon stager along with Invoke-Shellcode here
"Owned at $(Get-Date)" | Out-File C:\payload_result.txt
}Let’s look at the persistent registry key generated by the script via Invoke-WmiMethod -Namespace root/default -Class StdRegProv -Name CreateKey -ArgumentList @($HiveVal, $PayloadKey) (creating the Registry Key) & Invoke-WmiMethod -Namespace root/default -Class StdRegProv -Name SetStringValue -ArgumentList @($HiveVal, $PayloadKey, $EncodedPayload, $PayloadValue) (storing the payload value inside the key)
PS C:\Windows\system32> Get-ItemProperty 'HKLM:\SOFTWARE\PayloadKey'
PayloadValue : DQAKACAAIAAgACAAIwAgAFAAcgBlAHAAIAB5AG8AdQByACAAcgBhAHcAIABiAGUAYQBjAG8AbgAgAHMAdABhAGcAZQByACAAYQBsAG8AbgBnACAAdwBpAHQAaAAgAEkAbgB2AG8AawBlAC0AUwBoAGUAbABsAGMAbwBkAGUAIABoAGUAcgBlAA0ACgANAAoAIAAgACAAIAAiAE8AdwBuAGUAZAAgAGEAdAAgACQAKABHAGUAdAAtAEQAYQB0AGUAKQAiACAAfAAgAE8AdQB0AC0ARgBpAGwAZQAgAEMAOgBcAHAAYQB5AGwAbwBhAGQAXwByAGUAcwB1AGwAdAAuAHQAeAB0AA0ACgA=
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\PayloadKey
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE
PSChildName : PayloadKey
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\RegistryAlternatively:

We can observe the BASE64 ciphered payload (hold on to this, as it will become one of our detection artifacts later).
Now let’s throw in that juicy iex keyword to the Splunk mix and see what it comes up with:
Query: WmiPrvse OR powershell AND "iex" (NOT *google* NOT splunk NOT TargetImage=*powershell* NOT TargetImage=*wmiprvse* NOT TargetImage=*chrome* NOT TargetImage=*vmware* NOT EventCode=600) | reverse | table _time, EventCode, Message
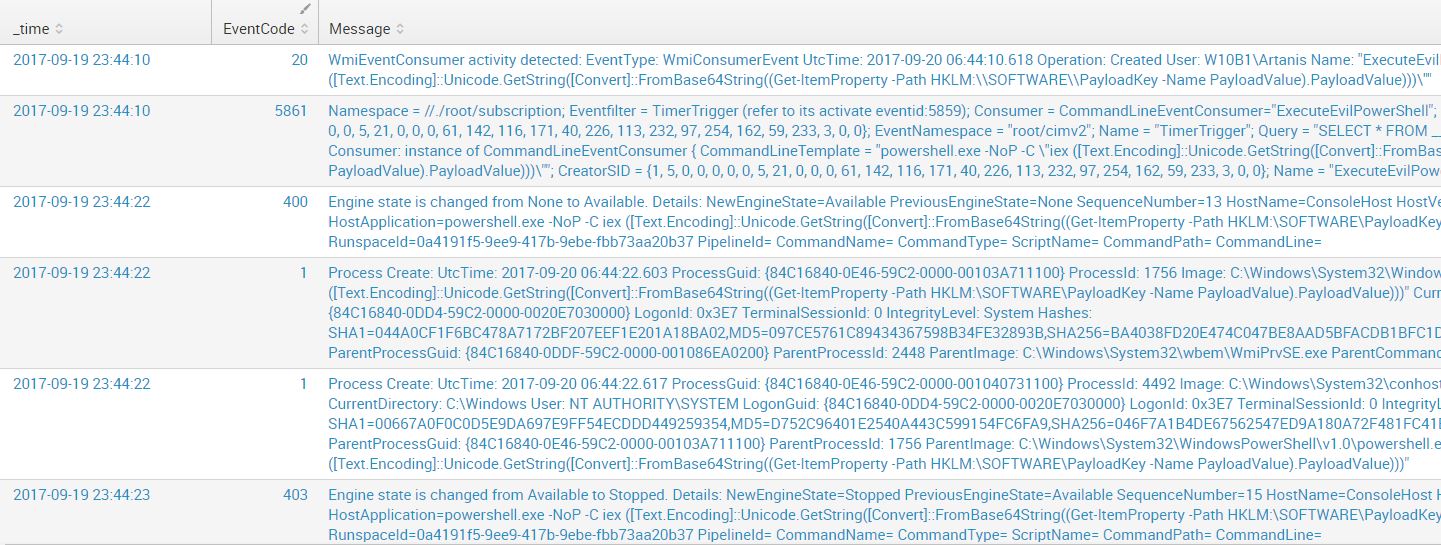
We start observing some other interesting events popping up here. Disregarding Sysmon EventCode 20 (belongs to the new 6.10 version) which will be dissected later, we can see 5861 (Source: Microsoft-Windows-WMI-Activity/Operational), 400 (Source: Windows Powershell / Message: Engine state is changed from None to Available)1 and 403 (Source: Windows Powershell / Message: Engine state is changed from Available to Stopped)2. All of them are standard Windows Events, I haven’t “enabled” anything in particular here. I’m just farming what the OS already gives you by default.
The interesting thing about all these events is that they all reveal the powershell code used as payload: powershell.exe -NoP -C iex ([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String((Get-ItemProperty -Path HKLM:\SOFTWARE\PayloadKey -Name PayloadValue).PayloadValue))) ― ―
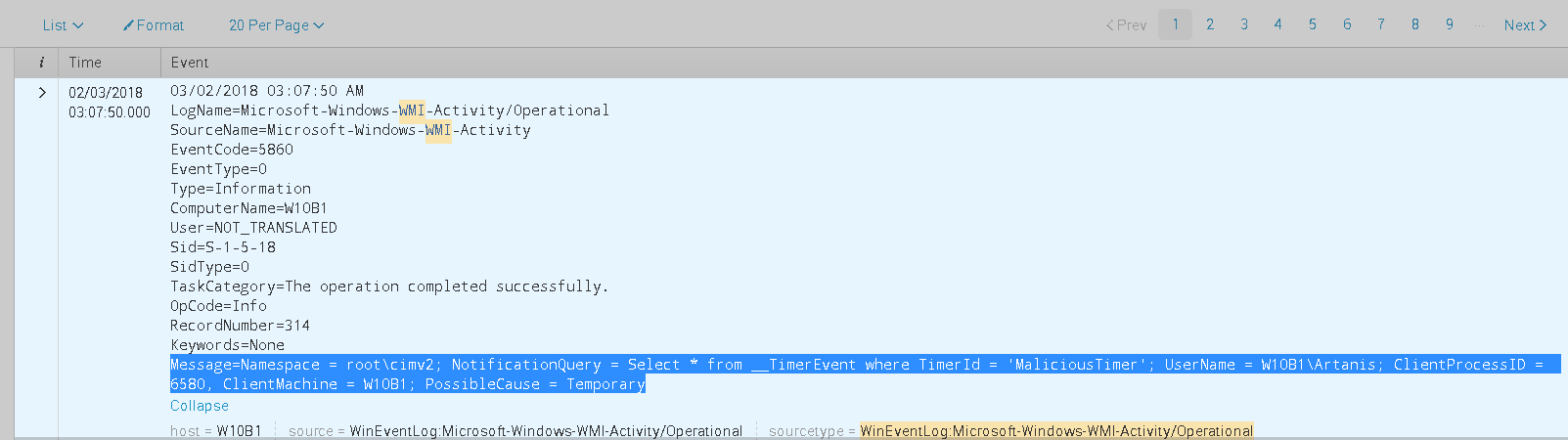
Most interesting of them all is Event 5861, which is giving us a lot of information about the persistence, namely the Binding itself.
WMI Persistence via PowerLurk by Sw4mpf0x
We can reproduce the same Timer Triggered Event as above with more ease with this great script which allows for a lot of flexibility.
Register-MaliciousWMIEvent -EventName MaliciousWMIEvent -LocalScriptBlock {Invoke-Expression -Command "cmd /c calc.exe"} -Trigger Interval -IntervalPeriod 60 -TimerId MaliciousTimerthis will simply start calc every 60 seconds and we can see the timer event
__GENUS : 2
__CLASS : __IntervalTimerInstruction
__SUPERCLASS : __TimerInstruction
__DYNASTY : __SystemClass
__RELPATH : __IntervalTimerInstruction.TimerId="MaliciousTimer"
__PROPERTY_COUNT : 3
__DERIVATION : {__TimerInstruction, __EventGenerator, __IndicationRelated, __SystemClass}
__SERVER : W10B1
__NAMESPACE : ROOT\cimv2
__PATH : **\\W10B1\ROOT\cimv2:__IntervalTimerInstruction.TimerId="MaliciousTimer"**
IntervalBetweenEvents : 60000
SkipIfPassed : False
TimerId : MaliciousTimer
PSComputerName : W10B1Let’s go ahead and remove it though:
Get-WMIObject -Namespace root\Subscription -Class __FilterToConsumerBinding | Remove-WmiObject -Verbose
Get-WMIObject -Namespace root\Subscription -Class __EventFilter | Remove-WmiObject -Verbose
Get-WMIObject -Namespace root\Subscription -Class __EventConsumer | Remove-WmiObject -Verbose
Get-WmiObject -Class __IntervalTimerInstruction | Remove-WmiObject -VerboseWe can do many more things, but this post is mainly about how to detect such sneaky persistence mechanisms, so let’s go ahead and grab our majestic free install of Splunk Enterprise with a 60 day trial and let’s make use of our best friend Sysmon the Great.
WMI Persistence Detection
For the purposes of this test, I’ve used a “log all” approach with Sysmon, you can find a sample config file here (Threat Hunting Ecosystem as a Code is my next project, don’t look at it yet, it’s ugly!)
So let’s go ahead and create a new TimerEvent and see what our logs come up with. We shall use the following search:
LogName=Microsoft-Windows-WMI-Activity/Operational AND NOT EventCode=5858 AND NOT "sysmon"-
First thing we notice is that Windows already comes with a default “WMI-Event Detector” which is Event Id 5860 in the Microsoft-Windows-WMI-Activity/Operational Log
-
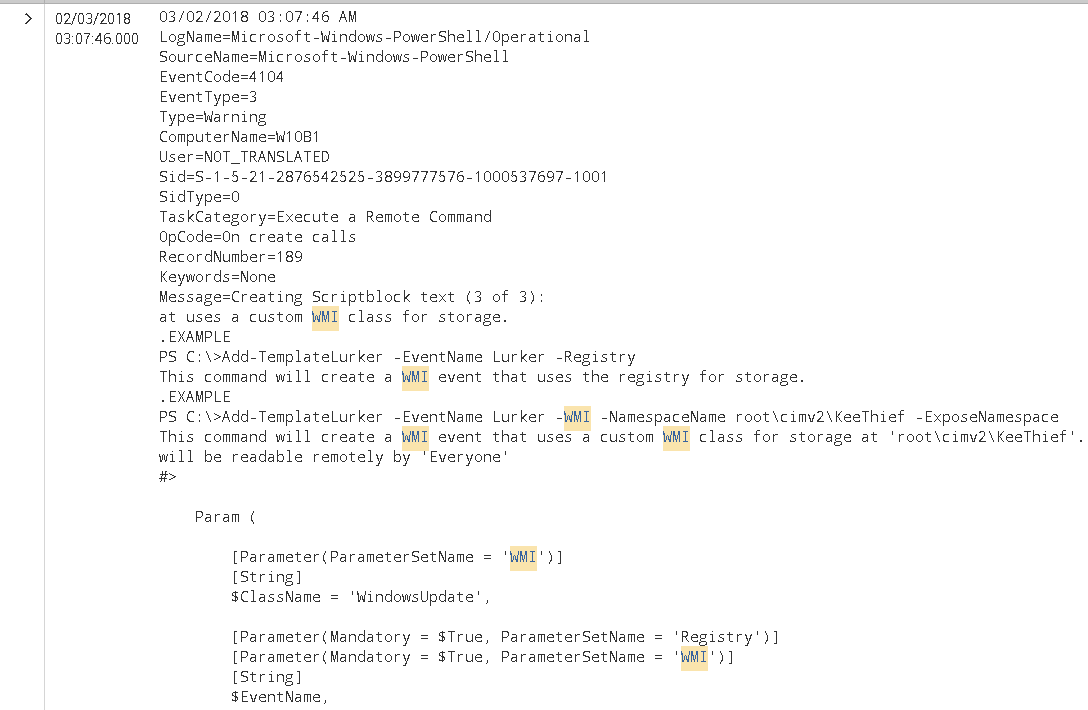
Second, becase I am running Powershell v5, Script Block Auditing is enabled by default, hence, the malicious script was also captured:
-
We also notice via another Event Id 5860 that some application with the Process Id 2024 issued a query to the WMI provider:
Who is this guy?
PS C:\WINDOWS\system32> Get-Process -Id 2024
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
425 20 22676 21804 174.56 2024 0 Sysmon64 The only problem we noticed here is that, for Timer-based WMI Events, sysmon wasn’t generating any logs. So you need to monitor Windows Event Id 5859/5861 if you want to catch those. ― ―
What would happen if we create a script event consumer?
$script = @’
Set objFSO=CreateObject("Scripting.FileSystemObject")
outFile="c:\test\log.txt"
Set objFile = objFSO.CreateTextFile(outFile,True)
objFile.Write "%TargetInstance.ProcessName% started at PID %TargetInstance.ProcessId%" & vbCrLf
objFile.Close
‘@
Register-MaliciousWmiEvent -EventName CalcMalicious -PermanentScript $script -Trigger ProcessStart -ProcessName notepad.exe -ScriptingEngine VBScript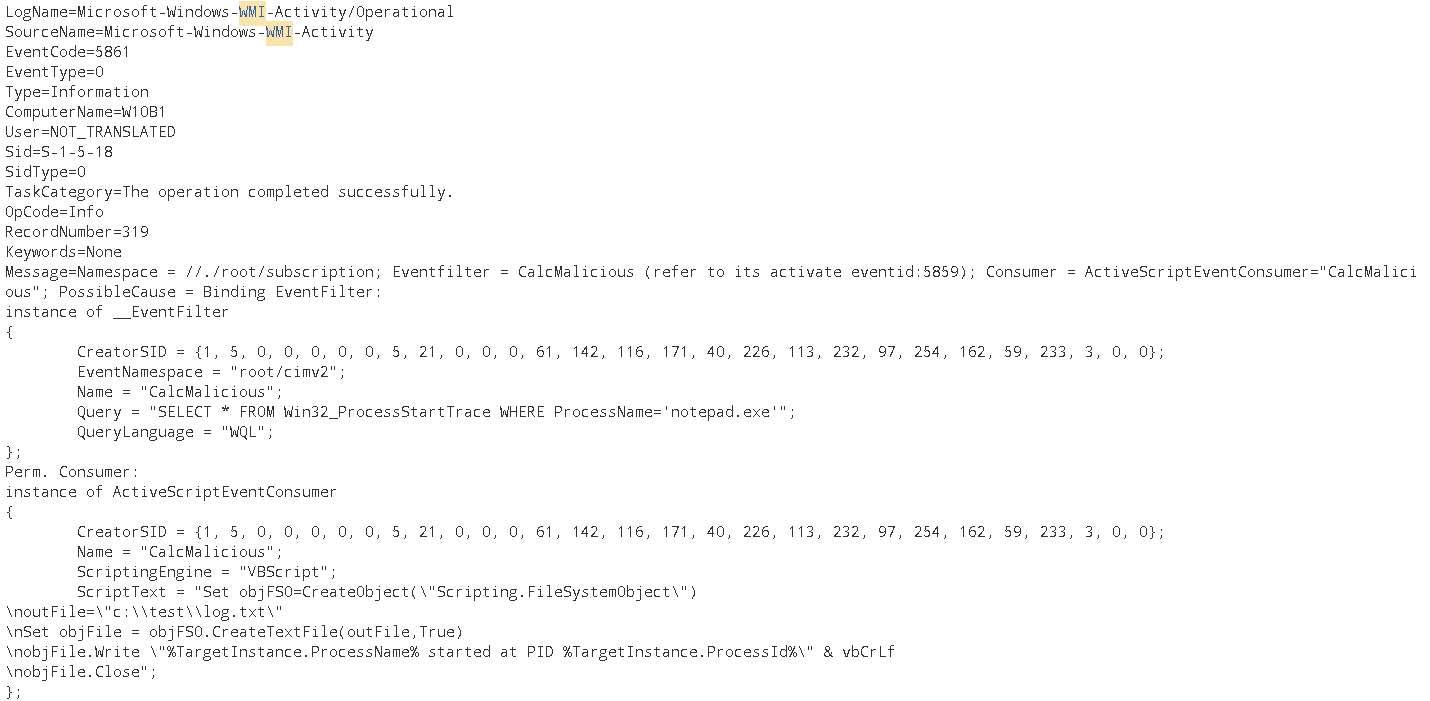
As we can observe, this pretty handy Windows Event Id 5861 provides all the information pertaining to the FilterToConsumerBinding, the EventConsumer and EventFilter
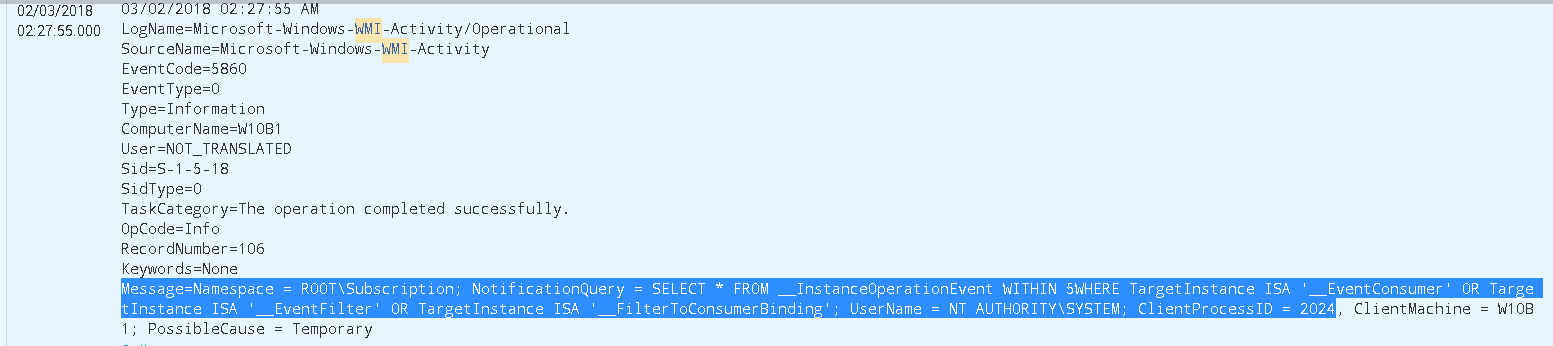
We also observe Windows Event Id 5859 showing the EventFilter which is effectively registered in the NotificationQueue:
LogName=Microsoft-Windows-WMI-Activity/Operational
SourceName=Microsoft-Windows-WMI-Activity
EventCode=5859
EventType=0
Type=Information
ComputerName=W10B1
User=NOT_TRANSLATED
Sid=S-1-5-18
SidType=0
TaskCategory=The operation completed successfully.
OpCode=Info
RecordNumber=321
Keywords=None
Message=Namespace = //./root/CIMV2; NotificationQuery = SELECT * FROM Win32_ProcessStartTrace WHERE ProcessName='notepad.exe'; OwnerName = S-1-5-21-2876542525-3899777576-1000537697-1001; HostProcessID = 972; Provider= WMI Kernel Trace Event Provider, queryID = 0; PossibleCause = PermanentAnd one other small but important piece of information is the presence of Event Id 5857 which is telling us who the provider is (an executable) whose task is to carry out the actions determined in the EventConsumer class:
LogName=Microsoft-Windows-WMI-Activity/Operational
SourceName=Microsoft-Windows-WMI-Activity
EventCode=5857
EventType=0
Type=Information
ComputerName=W10B1
User=NOT_TRANSLATED
Sid=S-1-5-18
SidType=0
TaskCategory=The operation completed successfully.
OpCode=Info
RecordNumber=322
Keywords=None
Message=ActiveScriptEventConsumer provider started with result code 0x0. HostProcess = wmiprvse.exe; ProcessID = 972; ProviderPath = %SystemRoot%\system32\wbem\scrcons.exeLet’s commit that to memory for a second: %SystemRoot%\system32\wbem\scrcons.exe. What the event is telling us is the executable in charge of running our script. Riding the Google brave horses I was able to obtain good answers from the Internet Elders: https://msdn.microsoft.com/en-us/library/aa940177(v=winembedded.5).aspx Here it says that these are the handlers for common event consumers:
Scrcons.exe. ActiveScriptEventConsumer
Smtpcons.dll. SMTPEventConsumer
Wbemcons.dll. CommandLineEventConsumer, NTEventLogEventConsumer, LogFileEventConsumerSo essentially, even if you are NOT monitoring for either Sysmon Events 19, 20 & 21 or Windows native Events in the WMI/Operational space Ids 5857, 5859, 5860 & 5861, you can still detect the presence of potentially malicious WMI persistence by leveraging the event consumer handlers listed above. Let’s ask Sysmon for Scrcons.exe
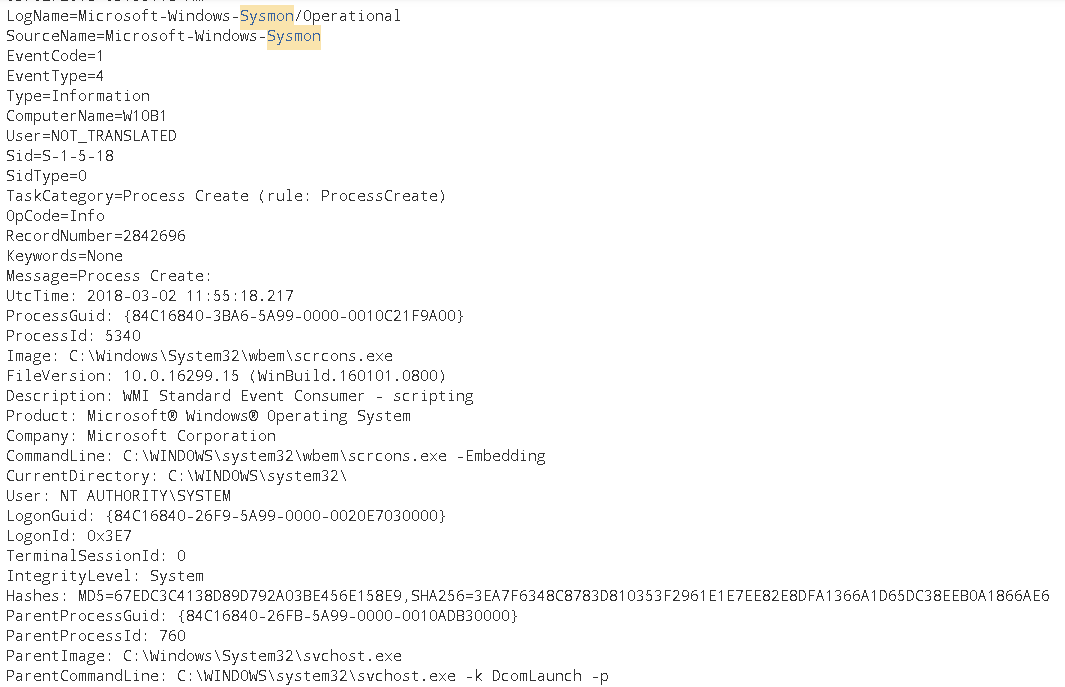
Now what a surprise! you would be expeting that WmiPrvse.exe would start scrcons.exe, instead it’s this regular non-profit bloke svchost.exe. Sysmon is even providing us with the name Description: WMI Standard Event Consumer - scripting
Looking for further clues of scrcons.exe returns a Sysmon Event Id 11 (File Created) event where our little friend created a file.
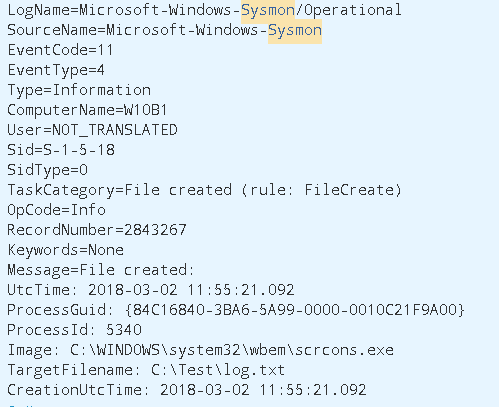
If we were expecting to see this file, written to disk by wscript.exe we will be disappointed ― ―
This time though, Sysmon seems to have noticed that a malicious event subscription was created and here we have it:
Get-WinEvent -FilterHashtable @{logname="Microsoft-Windows-Sysmon/Operational";id=20} | Select-Object -ExpandProperty Message
WmiEventConsumer activity detected:
EventType: WmiConsumerEvent
UtcTime: 2018-03-02 14:17:53.442
Operation: Created
User: W10B1\Artanis
Name: "CalcMalicious"
Type: Script
Destination: "Set objFSO=CreateObject(\"Scripting.FileSystemObject\")\noutFile=\"c:\\test\\log.txt\"\nSet objFile = objFSO.Cre
ateTextFile(outFile,True)\nobjFile.Write \"%TargetInstance.ProcessName% started at PID %TargetInstance.ProcessId%\" & vbCrLf\no
bjFile.Close"If you are using Sysmon events to monitor for WMI event subscriptions, you only need to capture the results of Event Id 19 as it will display the event consumer which is were the juicy information is that allows us to discriminate benign from malicious.
What happens if we instead create a CommandLine Event Subscription instead of a Script based one? The command would look like this with PowerLurk:
Register-MaliciousWmiEvent -EventName LogCalc1 -PermanentCommand “cmd.exe /c msg Artanis This is Persistence!” -Trigger ProcessStart -ProcessName calculator.exeThis time, instead of scrcons.exe we shall see wbemcons.dll as the event handler, and instead of a process being a child of another process we shall see WmiPrvse.exe loading wbemcons.dll. In all my experimental hunts I can assure you that the presence of wbemcons.dll being loaded as a module by WmiPrvse.exe is extremely rare, so do pay attention to those if you are not monitoring WMI/Operational native Windows events.
I will leave it as an exercise to the reader to investigate which events are generated by creating a CommandLine Event Consumer.
What about DFIR?
It happens to be the case that any permanent event subscription gets written to a WMI database file called OBJECTS.DATA that can be located here:
- C:\Windows\System32\wbem\Repository\OBJECTS.DATA
- C:\Windows\System32\wbem\Repository\FS\OBJECTS.DATA
It turns out that the information pertaining WMI event subscriptions can be located there in plain text. The file has a binary format and its structure, AFAIK, is undocumented. However, there are a few out there that were brave enough to come up with some cool python scripts that make use of The Sword of RegEx The Great and Meticulous that allow for parsing of these files, namely:
- https://github.com/darkquasar/WMI_Persistence (developed by me)
- https://github.com/davidpany/WMI_Forensics (David Pany script)
- https://github.com/fireeye/flare-wmi (a few scripts by FireEye analysts)
So even if you are (well… luckily after reading this post “were”) not collecting any WMI telemetry data in your environment, you can still go out there and hunt for these threats by collecting all the OBJECTS.DATA files in your hosts. The scripts listed above allow for easy parsing of a folder full of these files so the heavy lifting will be on the collecting side of things 
Detection Logics & Lessons Learned
You may think that WMI fileless persistence and malware execution mechanisms are a very low risk threat thus spending business cycles into creating a detection for this drops way down the list of priorities. It is, however, an extremely easy to detect tactic and if your priority list is not packed with threat scenarios like this one then you are not putting together a proper list!
We all know looking at detailed TTPs is a tedious process, but only by adopting a systemic approach you will be able to extend your detection & prevention surface. It’s an ants work, mixed with that of a dragon ― ―
So, to summarize
| Monitor | Detect | Suited for |
|---|---|---|
| Sysmon Event Id 11 (File Write) where “Image” is “C:\WINDOWS\system32\wbem\scrcons.exe”. | Suspicious files written by the script event consumer handler | Environments with Sysmon monitoring |
| Sysmon Event Id 1 where “ParentImage” is C:\Windows\System32\svchost.exe AND Image is “C:\WINDOWS\system32\wbem\scrcons.exe”. Alternatively Windows Security Log Event ID 4688 (Process Created) can also be monitored. | Instances of an Active Script Event Consumer WMI Persistence | When you are not monitoring Windows native WMI/Operational events OR,when a malicious actor disabled native windows event logging and you have another technology in place (for example EDR) |
| Sysmon Event Id 7 where “Image” is C:\Windows\System32\wbem\WmiPrvSE.exe AND “ImageLoaded” contains “wbemcons.dll”. | Instances of an Active CommandLine Event Consumer Persistence | When you are not monitoring Windows native WMI/Operational events,OR,when a malicious actor disabled native windows event logging and you,have another technology in place (for example EDR) |
| Windows Event Id 5859 in WMI-Activity/Operational | Suspicious Event Consumers | Environments with no Sysmon monitoring using solely native Windows Events OR for Intrinsic Timer Events (Sysmon doesn’t catch those!) |
| Windows Event Id 5861 in WMI-Activity/Operational | Suspicious Event Filters | Environments with no Sysmon monitoring using solely native Windows Events OR for Intrinsic Timer Events (Sysmon doesn’t catch those!) |
Hopefully in my next post I will resume the Mimikatz one and then I will jump into Meterpreter detections 
Changes to your Sysmon Config
We will add a tag for the new event that has a pretty tight condition: it will only collect WMI events when they are created. This way, the FP ratio is reduced to a minimum, but as a trade off you need to be really paying attention and treat Alarms pertaining to these events as critical always.
<!--SYSMON EVENT ID 19,20,21 : WMIEvent-->
<WmiEvent onmatch="include">
<Operation condition="is">Created</Operation>
</WmiEvent>Some references
- Malware using WMI Persistence: WMIGhost / Actors: APT29POSHSPY
- Yeap, cryptominers WMI’ing the sh!@# out of Browsers
- This dude man! mattifestation
- List of modules involved in each WMI event https://msdn.microsoft.com/en-us/library/aa940177(v=winembedded.5).aspx
- https://msdn.microsoft.com/en-us/library/aa392282(v=vs.85).aspx This explains how to create an NTEventLogEventConsumer class and how to setup one of its properties (insertionstrings) to a string. It also does this via MOF and compiling the MOF. The MOF then is embedded in OBJECTS.DATA. WMIPers is not parsing the “_EventConsumer” for these events very well, must look into that. The interesting thing though is that you could store anything in those “strings”, why not a payload?
- https://msdn.microsoft.com/en-us/library/aa393016(v=vs.85).aspx Ability to register EventConsumers and EventFilters can be restricted by setting the EventAccess attribute of the EventFilter instance.
arrivederci my friends, wine and fettuccine awaits!
EventCode 400 sample contents
09/19/2017 11:44:22 PM
LogName=Windows PowerShell
SourceName=PowerShell
EventCode=400
EventType=4
Type=Information
ComputerName=W10B1
TaskCategory=Engine Lifecycle
OpCode=Info
RecordNumber=56
Keywords=Classic
Message=Engine state is changed from None to Available.
Details:
NewEngineState=Available
PreviousEngineState=None
SequenceNumber=13
HostName=ConsoleHost
HostVersion=5.1.14393.206
HostId=9ebd19fb-d695-44ec-a9b1-51d48db8b1ef
HostApplication=powershell.exe -NoP -C iex ([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String((Get-ItemProperty -Path HKLM:\SOFTWARE\PayloadKey -Name PayloadValue).PayloadValue)))
EngineVersion=5.1.14393.206
RunspaceId=0a4191f5-9ee9-417b-9ebe-fbb73aa20b37
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine=EventCode 403 sample contents
09/19/2017 11:44:23 PM
LogName=Windows PowerShell
SourceName=PowerShell
EventCode=403
EventType=4
Type=Information
ComputerName=W10B1
TaskCategory=Engine Lifecycle
OpCode=Info
RecordNumber=57
Keywords=Classic
Message=Engine state is changed from Available to Stopped.
Details:
NewEngineState=Stopped
PreviousEngineState=Available
SequenceNumber=15
HostName=ConsoleHost
HostVersion=5.1.14393.206
HostId=9ebd19fb-d695-44ec-a9b1-51d48db8b1ef
HostApplication=powershell.exe -NoP -C iex ([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String((Get-ItemProperty -Path HKLM:\SOFTWARE\PayloadKey -Name PayloadValue).PayloadValue)))
EngineVersion=5.1.14393.206
RunspaceId=0a4191f5-9ee9-417b-9ebe-fbb73aa20b37
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine=Tags:
threat hunting, hunting, wmi, windows management instrumentation, backdoor, persistene, siem, ioc, splunk, elk, darkquasar, volatility