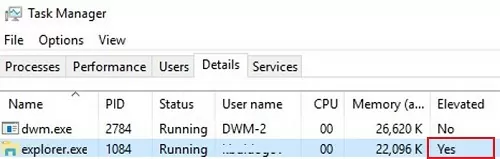
Недавно мой коллега Дмитрий с канала @winitpro_ru обновил свою классику блога про запуск проводника от имени администратора. В статье он объясняет, что это может пригодиться, например, для входа в пользовательские или системные папки без перманентного изменения списков контроля доступа (ACL).
Этот трюк в первую очередь ценен для корпоративных серверов. Дома-то можно и сторонний файловый менеджер с правами администратора запустить. Но любопытно же покопаться в вопросе!
[+] Сегодня в программе
История вопроса
Я интересуюсь этой темой ещё с завещания мистера Гейтса, написанного в 2011 году. Сейчас Дмитрий добавил в свою статью альтернативный метод, который появился уже во времена Windows 10.
Если завершить процесс
explorerи сразу же запустить его с ключом/NoUACCheck, проводник получит полные права.
Этот недокументированный ключ проводника означает «запускать без проверки контроля учетных записей». Впервые он всплыл в рамках запланированного задания CreateExplorerShellUnelevatedTask, которое автоматически создается (а также воссоздается и включается) при первой попытке запустить проводник с полными правами. Это с заметным опозданием разъяснил Рэймонд Чен.
Действительно, если в PowerShell от имени администратора выполнить kill -name explorer; explorer, полноправного процесса не получится. Вместо него из планировщика запустится explorer /nouaccheck. Экспортировав задание в XML, вы увидите, что в него заложен запуск с наименьшими доступными пользователю правами.
<Principal id="Author"> <UserId>S-1-5-21-1234567890-3333304218-166522979-1000</UserId> <LogonType>InteractiveToken</LogonType> <RunLevel>LeastPrivilege</RunLevel> </Principal>
Поскольку администратору выдается два токена (обычный и административный), запуск происходит с обычными правами. Однако, как выяснилось, этот ключ можно приспособить и для запуска с полными правами!
Запуск проводника с полными правами в Windows 10
В Windows 10 22H2 запустите PowerShell от имени администратора и выполните:
kill -name explorer; explorer /nouaccheck
Здесь kill — псевдоним командлета Stop-Process. Но учтите, что эта команда убивает процессы у всех пользователей. Чтобы прибить проводник только у себя, в PowerShell можно так:
Get-Process explorer -IncludeUserName | where UserName -match $ENV:USERNAME | Stop-Process explorer /nouaccheck
С утилитой taskkill команда будет покороче, но результат тот же — проводник запустится с правами администратора. Чтобы вернуть ему обычные права, завершите процесс и запустите explorer без ключей. Это можно сделать в диспетчере задач и даже в той же консоли.
Отличия в Windows 11
В Windows 11 я этот метод не проверял. Увидев обновление в статье Дмитрия, я решил попробовать, и… способ не сработал у меня в боевой Windows 11 23H2. И в чистой виртуальной машине тоже!
Мы списались с Дмитрием, и в рамках мозгового штурма я отслеживал запуск процессов посредством аудита, а также их завершение с помощью gflags. Выяснились любопытные нюансы.
Последовательность «убил explorer — выполнил от админа с ключом /nouaccheck » запускает цепочку действий под капотом. В игру вступают процессы wermgr (Windows Error Reporting) и winlogon. По ходу дела прибивается запущенный с полными правами процесс, а вместо него стартует новый — с обычными правами.
Детальный разбор ниже, но сразу скажу, что задание планировщика CreateExplorerShellUnelevatedTask здесь не участвует (возможно, потому что проводник уже запускается без проверки UAC).
В итоге различие между поведением Windows 10 и 11 свелось к значению параметра
AutoRestartShellиз раздела реестраHKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.
По умолчанию оно равно 1. В Windows 11 23H2 трюк работает, только если установить его равным 0. То есть не перезапускать оболочку автоматически в случае ее закрытия. Иначе winlogon всех побеждает и форсирует перезапуск с обычными правами.
Но даже с отключенным рестартом оболочки первый запуск
explorer /nouaccheckне достигает цели. Его прибивают, поэтому приходится повторять команду. Второй процесс уже выживает.
Возможно, различие в поведении разных поколений ОС является следствием изменений оболочки в Windows 11 — там ведь другой Пуск и панель задач. Кстати, иногда наблюдается побочный эффект — не работает Пуск и поиск (Win + S), некоторые сочетания клавиш (Win + D).
Запуск проводника с полными правами в Windows 11
В сравнении с Windows 10 скрипт для Windows 11 труднее запомнить наизусть:
# https://www.outsidethebox.ms/22306/ # отключение перезапуска оболочки $path = 'HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon' New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 0 -Force | Out-Null # завершение процесса только у текущего пользователя # Stop-Process -Name explorer #на терминальных серверах убьет процесс у всех Get-Process explorer -IncludeUserName | where UserName -match $ENV:USERNAME | Stop-Process explorer /nouaccheck #будет убит Start-Sleep -Seconds 1 explorer /nouaccheck #останется с полными правами # включение перезапуска оболочки New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 1 -Force | Out-Null # завершение процесса, и теперь сам перезапустится с обычными правами # Get-Process explorer -IncludeUserName | where UserName -match $ENV:USERNAME | Stop-Process
При таком раскладе для разовой задачи может быть проще обойтись блокнотом с правами админа.
Демо и разбор поведения в Windows 11
На видео этот же скрипт обставлен дополнительными проверками и выводом вспомогательных сообщений. Я также задействовал
- Сторонний скрипт для определения уровня целостности выполняющегося процесса. Фактически он дублирует столбцы Elevated в диспетчере задач и Integrity Level в Process Monitor.
- Мой скрипт для обработки событий аудита процессов. В событии 4688 тоже содержится информация о токене процесса (Token Elevation Type) и его уровне целостности (Mandatory Label).
/blog/wp-content/uploads/explorer-elevated-public.mp4
Для начала я отключаю перезапуск оболочки, убиваю explorer и запускаю новый с ключом /nouaccheck.
Setting AutoRestartShell = 0 AutoRestartShell : 0 Starting explorer elevated... Sunday, February 25, 2024 12:48:11 AM
Это порождает запуск двух процессов. Консольный вывод списка процессов во время этой операции не слишком точный, поэтому я опираюсь на видео и аудит.
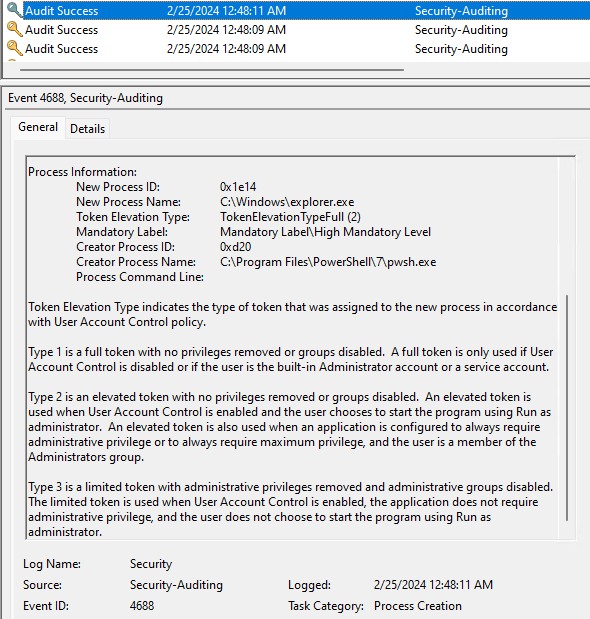
EventTime : 2024-02-25T08:48:12.3249754Z NewProcessID : 8464 NewProcessName : C:\Windows\explorer.exe ParentProcessID : 7700 ParentProcessName : C:\Windows\explorer.exe EventTime : 2024-02-25T08:48:11.2992578Z NewProcessID : 7700 NewProcessName : C:\Windows\explorer.exe ParentProcessID : 3360 ParentProcessName : C:\Program Files\PowerShell\7\pwsh.exe
Из PowerShell выполняется ИД 7700, в свою очередь из под него запускается ИД 8464. На картинке запуск процесса с ИД 7700 в графическом интерфейсе журнале событий. Идентификаторы процессов выглядят недружелюбно, но в скрипте это легко обрабатывается — [int]$id.
Тут же в дело вступает Windows Error Reporting, чей процесс wermgr.exe запускается с помощью запланированного задания.
ProviderName: Microsoft-Windows-TaskScheduler
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
2/25/2024 12:48:13 AM 100 Information Task Scheduler
started "{58c1e3bc-
9637-4830-b106-72d9
99259bc6}"
instance of the "\M
icrosoft\Windows\Wi
ndows Error Reporti
ng\QueueReporting"
task for user "NT
AUTHORITY\СИСТЕМА".
2/25/2024 12:48:13 AM 129 Information Task Scheduler
launch task "\Micro
soft\Windows\Window
s Error Reporting\Q
ueueReporting" ,
instance "%windir%\
system32\wermgr.exe
" with process ID
1600.
В результате оба процесса explorer завершаются. В скрипте я убеждаюсь в их отсутствии и снова запускаю проводник с полными правами, после чего проверяю его уровень целостности. Он высокий!
Title : Displaying Process/Primary Information ProcessName : explorer SessionId : 1 PID : 9132 TokenIntegrityLevel : HIGH_MANDATORY_LEVEL
Этому процессу соответствует запись аудита.
EventTime : 2024-02-25T08:48:16.3657996Z NewProcessID : 9132 NewProcessName : C:\Windows\explorer.exe ParentProcessID : 3360 ParentProcessName : C:\Program Files\PowerShell\7\pwsh.exe
Наконец, я возвращаю все на исходные позиции – восстанавливаю перезапуск оболочки и убиваю ее. В результате автоматически запускается процесс explorer с обычными правами (средним уровнем целостности).
Setting AutoRestartShell = 1, killing explorer. Should auto-start non-elevated... Sunday, February 25, 2024 12:48:26 AM AutoRestartShell : 1 Title : Displaying Process/Primary Information ProcessName : explorer SessionId : 1 PID : 8580 TokenIntegrityLevel : MEDIUM_MANDATORY_LEVEL
В журнале аудита видно, что родительским процессом был winlogon.
EventTime : 2024-02-25T08:48:26.4698992Z NewProcessID : 8580 NewProcessName : C:\Windows\explorer.exe ParentProcessID : 820 ParentProcessName : C:\Windows\System32\winlogon.exe
Конец!
Я благодарю за помощь в подготовке материала участников чата @winsiders — Nirai Charged Pulse и Андрея Шубина.
You may want to open File Explorer as Administrator to modify files you have no access to. Those can be files created under a different user account, or some system file you want to play with. In such a situation, you may find that you have no permission to access the file or folder. Running Windows 11 File Explorer as Admin solves the issue.
In order to address issues within a document or access system files for troubleshooting purposes, you may need to run File Explorer elevated. This could be necessary for making significant changes to system files or saving files to protected locations.
If you prefer to maintain control over your workflow without depending on a system administrator to provide elevated permissions, you can manually run File Explorer as an administrator. In modern versions of Windows, File Explorer typically operates with limited privileges as a security measure. Even attempting to run the executable file C:\Windows\explorer.exe as Administrator through the right-click menu does not result in privilege escalation: It will ultimately return to its default permissions.
But this guide will show on how to run Windows 11 Explorer elevated, i.e. with administrative privileges. Note that will require you to terminate
To open Windows 11 File Explorer with administrator rights, do the following.
- Right-click the Start button in the taskbar and select Run from the menu.
- In the Run dialog, type
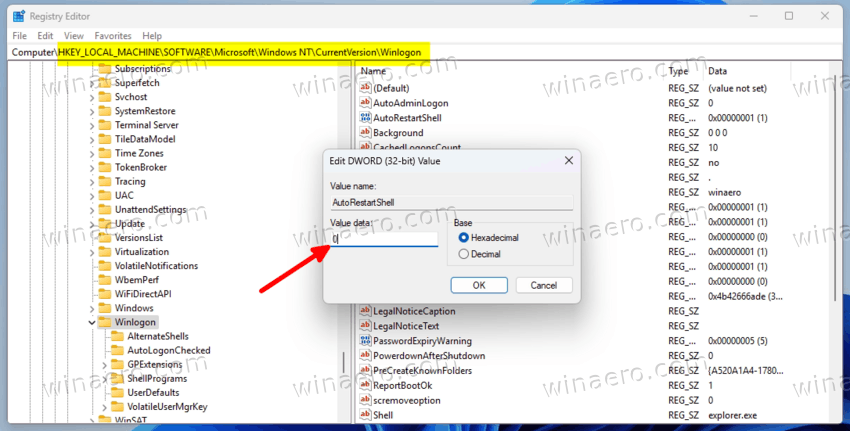
regeditand press the Enter key. - Navigate to the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon key.
- Double-click the AutoRestartShell DWORD value, and change its data from 1 to 0.
- Press Ctrl + Shift + Esc on the keyboard to open the Task Manager.
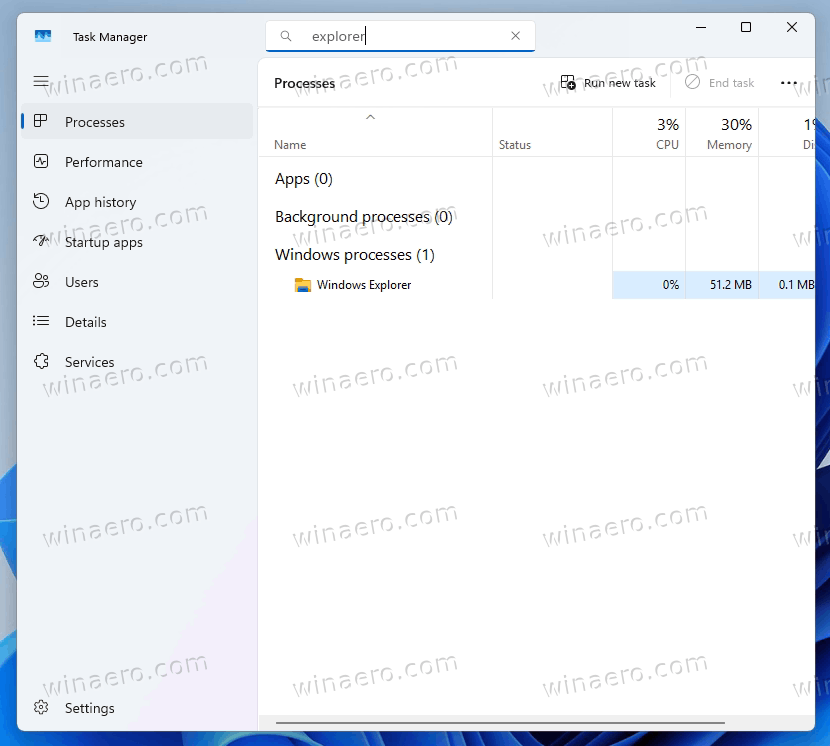
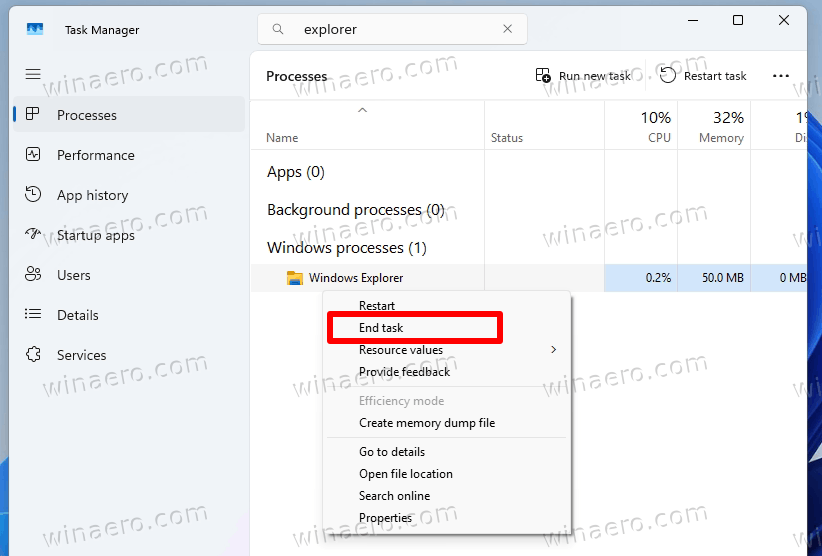
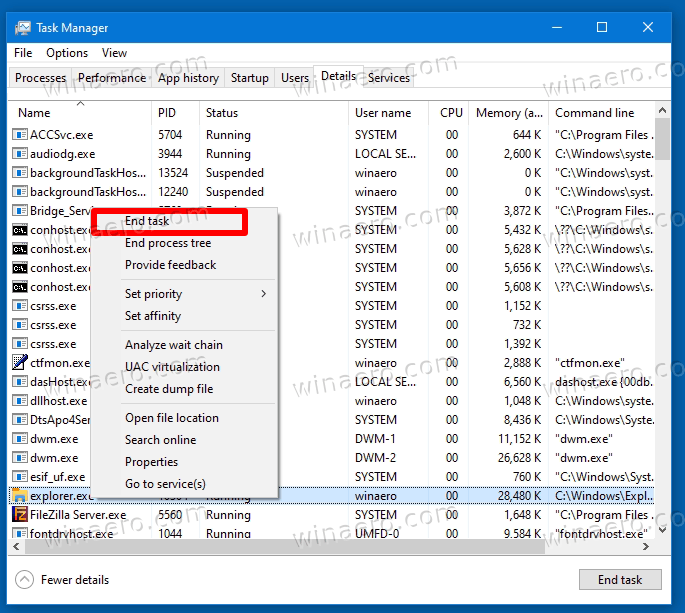
- In Task Manager, find the explorer process, and right-click it.
- Select End task from the menu, and click OK to confirm. This will stop the Explorer process, so the taskbar and desktop will disappear.
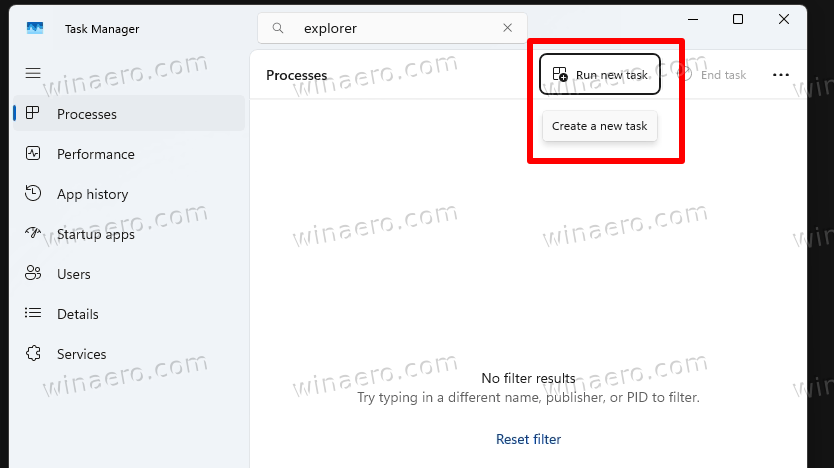
- Now in Task Manager, click on Run new task.
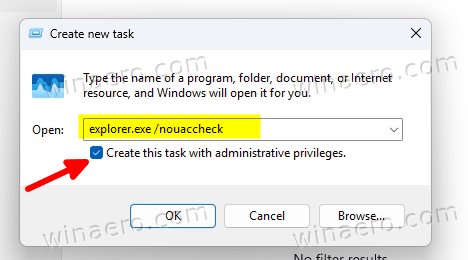
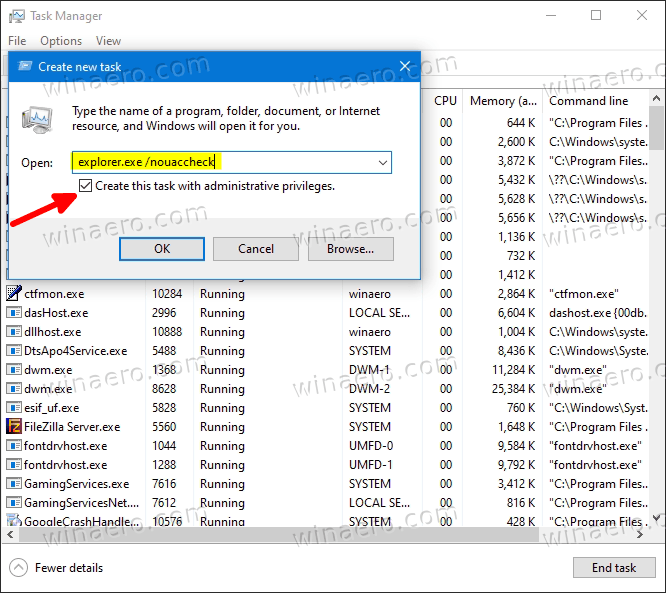
- In the Create new task dialog, type explorer.exe /nouaccheck.
- Place a check mark for the Create this task with administrative privileges option, and click OK.
Done! The Explorer will now run as Administrator. Here is how can you be sure of this.
Check if Explorer runs elevated
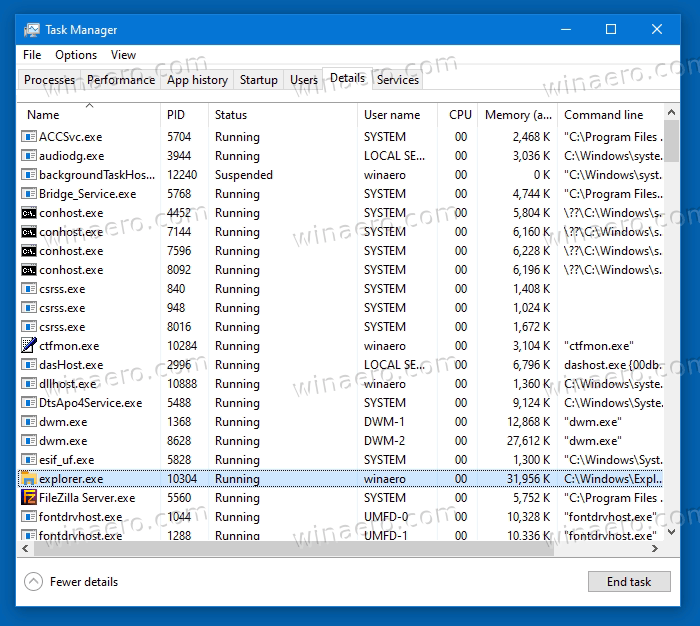
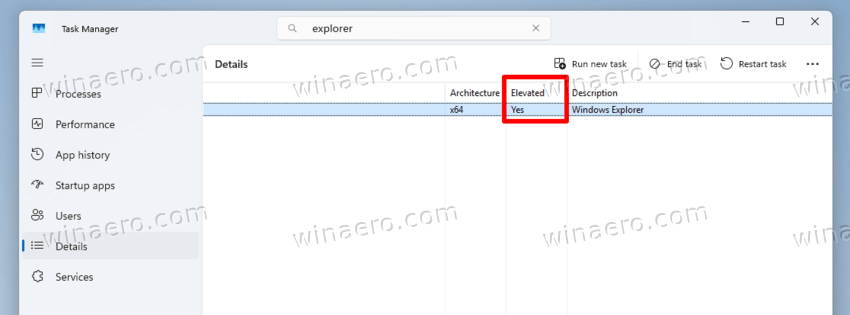
In Task Manager, switch to the Details tab.
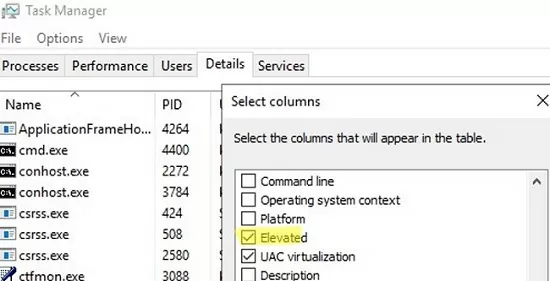
Now, right-click any column in the process grid, and choose Select columns from the menu.
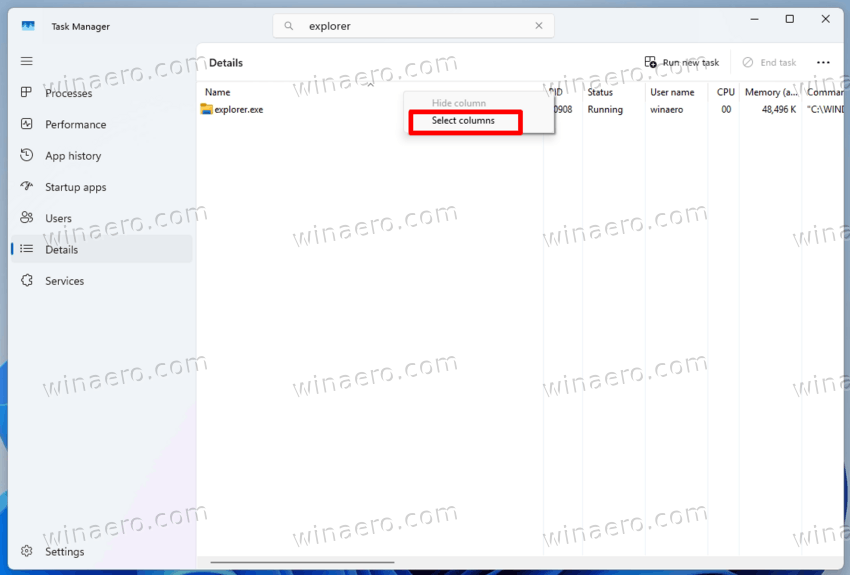
In the list of available columns, enable the Elevated option, and click OK.
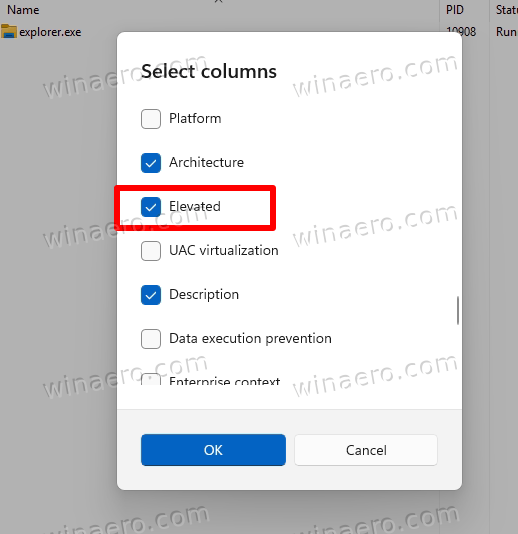
You will now clearly see in the Task Manager that Explorer runs as Administrator, and it has Yes in the newly added column.
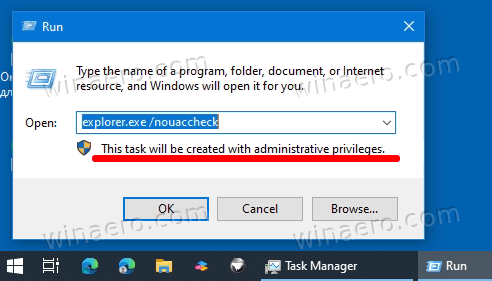
Also, if you now press Win + R to open the Run dialog, you will see a new text message telling that anything you launch will run with administrative privileges.
Keep in mind that now you have all explorer.exe processes running as Administrator. This includes the taskbar, new folder windows — everything. It will also launch all apps (EXE, CMD files) as administrator too. So it is not a good idea to keep with high privileges all the time, as you can accidentally modify or remove a file that was not supposed to be accessed by the regular user.
The same procedure can be done in Windows 10, but it doesn’t require preliminary Registry editing. The latter is new to Windows 11 only. Here are some details.
In Windows 11 version 23H2, Microsoft has done changes to how explorer.exe starts with administrator rights. With 23H2 and above, Windows 11 controls the launch of Explorer with an administrator token and kills the running process, and instead launches a new one with normal rights. The undocumented explorer.exe /nouaccheck argument disables the check, but in order to make it work, you have to restart the automated shell restart in the Registry. But Windows 10 doesn’t perform the automated shell restart, so you can omit the Registry editing.
How to Launch Explorer Elevated in Windows 10
To open Explorer as administrator (elevated) on Windows 10, do the following.
- Open the Task Manager (
taskmgr.exe), and go to the Details tab. - Find explorer.exe in the list of processes and click on End task. The taskbar and desktop will flash and disappear.
- Again in the Task Manager, select menu > File > Run New Task.
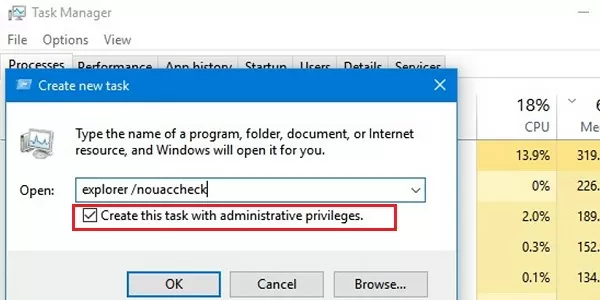
- In the new task box, type
explorer.exe /nouaccheck. - Now enable the Create this task with administrative privileges option.
- Click OK. This will start the Explorer process with administrator rights (as admin).
You are done!
As you see, there is no much difference between the Windows 11 and 10. Only a small Registry modification is required in case of Windows 11 23H2.
Here’s a final suggestion. Once you finish working with File Explorer running elevated, sign out from Windows and sign in back again. This will reload your user account session and will run the Explorer shell as usual, without administrative privileges. I don’t recommend you running it with high access rights for a long period of time, as it a security risk for your OS.
That’s it.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won’t take a lot from you, but it will help us grow. Thanks for your support!
Detects suspicious starts of explorer.exe that use the /NOUACCHECK flag that allows to run all sub processes of that newly started explorer.exe without any UAC checks
Sigma rule (View on GitHub)
1title: Explorer NOUACCHECK Flag
2id: 534f2ef7-e8a2-4433-816d-c91bccde289b
3status: test
4description: Detects suspicious starts of explorer.exe that use the /NOUACCHECK flag that allows to run all sub processes of that newly started explorer.exe without any UAC checks
5references:
6 - https://twitter.com/ORCA6665/status/1496478087244095491
7author: Florian Roth (Nextron Systems)
8date: 2022-02-23
9modified: 2022-04-21
10tags:
11 - attack.defense-evasion
12 - attack.t1548.002
13logsource:
14 category: process_creation
15 product: windows
16detection:
17 selection:
18 Image|endswith: '\explorer.exe'
19 CommandLine|contains: '/NOUACCHECK'
20 filter_dc_logon:
21 - ParentCommandLine: 'C:\Windows\system32\svchost.exe -k netsvcs -p -s Schedule'
22 - ParentImage: 'C:\Windows\System32\svchost.exe' # coarse filter needed for ID 4688 Events
23 condition: selection and not 1 of filter_*
24falsepositives:
25 - Domain Controller User Logon
26 - Unknown how many legitimate software products use that method
27level: high
- Bypass UAC Using DelegateExecute
- Bypass UAC Using SilentCleanup Task
- Bypass UAC via CMSTP
- Bypass UAC via WSReset.exe
- Function Call From Undocumented COM Interface EditionUpgradeManager
If you noticed a strange task with the name “CreateExplorerShellUnelevatedTask” in Task Scheduler in Windows 10, Windows 11 or Windows Server operating system, this article will help you in understanding what is this unusual task present in Task Scheduler and is it safe to delete or disable this task?
Table of Contents
- CreateExplorerShellUnelevatedTask Present in Windows Task Scheduler
- What is CreateExplorerShellUnelevatedTask in Task Scheduler in Windows?
- CreateExplorerShellUnelevatedTask Causing High CPU Usage in Windows Server
- How to Disable CreateExplorerShellUnelevatedTask in Task Scheduler in Windows?
Recently an AskVG reader contacted me regarding this issue. He found this suspicious task automatically created in Task Scheduler in his Windows 11 device.
Task Scheduler is a system tool which comes built-in with all Windows versions. You can use Task Scheduler to schedule important tasks or set reminders. Windows also use Task Scheduler to perform system related tasks on regular intervals.
You can also check whether the CreateExplorerShellUnelevatedTask option is present in your Windows device with the help of following steps:
1. Press WIN+R keys together to launch RUN dialog box, type taskschd.msc and press Enter. It’ll open Task Scheduler.
2. Now in right-side pane, you’ll see list of all tasks system created as well as user created.
Now you can check whether the CreateExplorerShellUnelevatedTask is present in your computer system.
Following screenshot shows the CreateExplorerShellUnelevatedTask present in one of our Windows 11 machines:

Name: CreateExplorerShellUnelevatedTask
Author: ExplorerShellUnelevated
Status: Enabled
Action: Start a program – C:\WINDOWS\explorer.exe /NoUACCheck
What is CreateExplorerShellUnelevatedTask in Task Scheduler in Windows?
Now you might be wondering what is this weird CreateExplorerShellUnelevatedTask doing in your Windows device?
Here is the answer:
Some people think that “CreateExplorerShellUnelevatedTask” task was created by 3rd party software such as CCleaner, etc or by some malware but that’s not true.
CreateExplorerShellUnelevatedTask is a system task created by Windows to prevent users and apps from running Windows Explorer process elevated. If the user or a program tries to run the Explorer elevated, the task is run to launch the Explorer unelevated.
Here is a comment from “frank_song” at official Microsoft TechNet forum about CreateExplorerShellUnelevatedTask presence:
The CreateExplorerShellUnelevatedTask task prevents Explorer from running elevated. Any attempt to start Explorer with elevation switch seems to get intercepted by Windows and a CreateExplorerShellUnelevatedTask task is created and run instead. Because the task is configured to run with the lowest privileges, Explorer never gets run with elevation. When Explorer is executed with the ‘/nouaccheck’ switch the CreateExplorerShellUnelevatedTask task is ignored and Explorer is launched conventionally, it’s elevated status inherited from the process that started it. I suggest you disable it for a test.
So CreateExplorerShellUnelevatedTask is not suspicious. In fact, it’s a legit task created by Windows and you don’t need to worry about it.
CreateExplorerShellUnelevatedTask Causing High CPU Usage in Windows Server
At TechNet forum, the topic starter faced problems with this system task. He was facing high CPU usage problem due to this task in his Windows Server 2016 device.
If you are also facing issues related to this task in your Windows computer, you can safely disable this task with the help of steps given below.
How to Disable CreateExplorerShellUnelevatedTask in Task Scheduler in Windows?
1. Press WIN+R keys together to launch RUN dialog box, type taskschd.msc and press Enter. It’ll open Task Scheduler.
2. Now look for “CreateExplorerShellUnelevatedTask” in right-side pane.
3. Right-click on the task and select Disable option.

That’s it. It’ll immediately disable the task.
In future, if you decide to re-enable the task, right-click on the task and select Enable option.
PS: Advanced users can also use following direct command to disable the task using command-line tools such as Command Prompt or PowerShell:
SchTasks /Change /Disable /TN CreateExplorerShellUnelevatedTask
Also Check:
[Fix] Can’t Create Tasks to Display Messages in Task Scheduler in Windows 8 and Later
How to Import (Restore) All Tasks in Bulk Using Task Scheduler in Windows?
How to Import / Export (Backup / Restore) Tasks Using Task Scheduler in Windows?
You are here: Home » Windows 10 » What is “CreateExplorerShellUnelevatedTask” in Task Scheduler in Windows?
File Explorer process always runs with minimal (non-elevated) privileges in Windows. Even if you click the C:\Windows\explorer.exe executable file and try to start it in the ‘Run as administrator’ mode, it will not elevate privileges. In this article, we will look at a simple trick to run File Explorer on Windows with elevated privileges (as administrator).
Contents:
- Running the File Explorer Process on Windows as an Administrator
- Fix: You Don’t Have Permission to Access Folder
Running the File Explorer Process on Windows as an Administrator
To run the Windows Explorer process with elevated privileges, you will first need to kill the unprivileged explorer.exe process.
- Open the Windows Task Manager (
taskmgr.exe), go to the Details tab, find a kill theexplorer.exeprocess (End task); - Then in Task Manager select -> File -> Run New Task -> run the command:
explorer.exe /nouaccheck(make sure that the Create this task with administrative privileges option is enabled); - This will start the File Explorer process with administrator privileges. How can you be sure of this?
- On the Details tab, right-click the title of the process list and choose Select Columns;
- Check the Elevated option;
- Now you can see that the explorer.exe process is running in privileged mode (
Elevated=Yes).
You can also run the elevated explorer.exe process from the PowerShell console (be sure to run powershell.exe as an administrator):
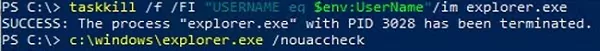
- Kill the running low-privileged explorer.exe process:
taskkill /f /FI "USERNAME eq $env:UserName"/im explorer.exe - Run the privileged explorer.exe:
c:\windows\explorer.exe /nouaccheck - The new explorer process will inherit the elevated access token that is used to run the powershell.exe console.
(NO|UAC|CHECK)
You can create the following BAT file on your desktop to quickly run File Explorer with administrator privileges:
taskkill /f /FI "USERNAME eq %USERNAME%" /im explorer.exe
start c:\windows\explorer.exe /nouaccheck
Changes related to running explorer.exe with administrative privileges have been introduced in build Windows 11 23H2. In this build, Windows 11 detects when you start Explorer with an administrator token, kills the running process, and starts a new one with non-elevated permissions instead.
In order to disable this behavior, you must modify the AutoRestartShell parameter in the registry:
$path = 'HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon'
New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 0 -Force | Out-Null
Windows will still kill the elevated process when you run the following command for the first time:
taskkill /f /FI "USERNAME eq $env:UserName" /im explorer.exe ; c:\windows\explorer.exe /nouaccheck
But if you start it again, the privileged explorer.exe will survive. 👌
When you have finished your task, remember to allow the Explorer shell to restart:
New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 1 -Force | Out-Null
taskkill /f /FI "USERNAME eq $env:UserName" /im explorer.exe
Fix: You Don’t Have Permission to Access Folder
Let’s have a look at a common scenario where an Explorer process with administrator privileges can be particularly useful
In some cases, you may need to open the system or other users’ profile folders or edit protected system files by using Explorer running as an account that has been added to the local Administrators group (or even under the built-in Windows administrator). If you try to open such a directory or file in the current Explorer context, a User Account Control (UAC) warning window will appear, asking you to grant access and elevate privileges.
For example, try using Explorer to open the system directory C:\Windows\System32\Config. The UAC prompt should appear, informing you that you are not allowed to access the directory:
You don’t currently have permission to access this folder. Click Continue to permanently get access to this folder.
If your account has local administrator permissions, you can use UAC to elevate privileges by clicking Continue.
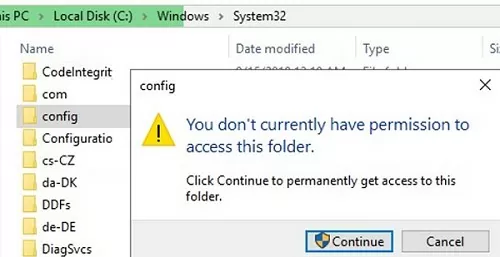
When you click Continue, UAC temporarily elevates the privileges of your explorer.exe process and grants your account Full Control NTFS permissions on the folder.
Known issues with this approach:
After performing such an operation, your account will be explicitly added to the NTFS folder permissions. Even though you only wanted to view the contents of the directory, not change its ACL! If this Windows Server host is managed by more than one administrator, then the folder ACL will be constantly increasing. This is because, when accessing the folder, any administrator will change the directory ACL.
This behavior of File Explorer causes major problems when managing shared folders on Windows Server file servers. As a workaround, many Windows administrators prefer to manage NTFS permissions on shared network folders via a UNC path (\\mun-fs01\docs\) rather than locally. In this case, there is no need to elevate permissions when accessing the shared folder. Accordingly, NTFS ACLs won’t be modified.
This pop-up UAC notification becomes annoying if you are actively managing system files or shared folders. To avoid completely disabling UAC in Windows, you can temporarily run File Explorer as an administrator.
Be sure to restart explorer.exe in Normal mode when you have finished working with protected or user folders.
This trick of running the Windows Explorer process with elevated privileges works in Windows Server 2016/2019/2022 as well as in all builds of Windows 10/11.
In early Windows 10 builds, the launch of the elevated explorer.exe process was blocked by the built-in CreateExplorerShellUnelevatedTask scheduler task.