It is crucial to lay a foundation prior to you construct a common-goal pc network. In this function you will use a selection of laptop programming languages and applications, functioning in teams with other IT specialists, or alone. Our Computer Networking & Information Method Security Program presents a degree — with both an AAT and an AAS-T option — along with 4 specialty certificates. Kelly has a degree in Pc Science and has had over 21 market and IT certifications.
Quite a few of our students are presently functioning in the networking field, and bring their knowledge to the classroom. As a complement you need to study Richard Stevens TCP/IP Illustrated, volume 1 for a additional sensible approach to TCP, UDP and IP. The data Menu of Microsoft Workplace Excel 2003 consists of some helpful commands that you have to have to know and use in your Excel jobs. A laptop or computer network is a method in which multiple computer systems are connected to every single other to share data and sources. We are going to see some of the things you can do to have a clean and efficient computer.
However there are people who do not know how to use them and that’s why I’ve prepared this introduction to computer system basics. Don has an associate’s degree in Electronic Technology and maintains certifications in A+, MCP, 2008 Server Administration and ITAA Data Security Awareness as nicely as various FEMA certifications. Our subsequent plan information session for Computer Networking & Facts Systems Security is April 13 at three p.m. in Building 16, Room 209. This pathway is employed for communication and can be established involving two or more laptop elements. Standard information of python (such as via Intro to Laptop or computer Science ) is essential.
Computer Networking requires a hands-on strategy to teaching incredibly technical material, utilizing Mininet (a network emulator) to show you how a computer network functions, what things contribute to its efficiency and how to overcome inherent limitations. NECC’s Computer Networking Certificate will give you with the capabilities vital to install, configure, and manage hardware and application utilized in local area networks (LAN). Novices can study these crucial networking concepts and technologies to discover the fundamentals of computer networking speedy.
This module supplies students with the fundamental expertise needed to succeed in networking-connected degree applications. Our diverse Computer system Networks degree prepares you for entry into this exciting field. You will also acquire understanding of wide region networks (WAN), firewalls, and wireless networking. As an applications developer your function will contain writing specifications and designing, creating, testing, implementing and from time to time supporting applications employing computer languages and development tools.
Whenever you start your computer in Safe Mode, you’ll notice a number of messages scrolling by that tell you which file Windows is loading. Unfortunately, the list can scroll by so fast that you can’t read it. Knowing which file Windows is loading is important because loading the wrong file at the wrong time can prove fatal when getting the operating system to work. Selecting the Enable Boot Logging option slows the Windows loading process considerably because the operating system records everything it loads into the NTBtLog.TXT file, located in the %SystemRoot% folder (normally C:\Windows) of your system. You can open this file using Notepad and see a list of the files that Windows loads.
Of course, all those filenames may not mean much to you. Sure, you might recognize a few of them, but for the most part, the meaning isn’t clear. Fortunately, you can check most of these filenames online. A simple Google search is enough to provide everything you need in most cases. You can also go to sites such as the ones in the following list to view information about the files:
• Program Checker: http://www.programchecker.com/
• Spyware.net: http://www.fbmsoftware.com/spyware-net/
• Software Tips & Tricks: http://www.softwaretipsandtricks.com/necessary_files/
• eConsultant: http://www.econsultant.com/windows-tasks/
You have another option for obtaining information about the individual files that load during the boot process. Because the NTBtLog.TXT file contains the full path to each of the files, you can quickly locate an individual file that Windows loaded. Right-click the file and choose Properties from the context menu. On the Digital Signature tab, you can verify the digital signature of the company that signed the file. The Details tab, provides significant information about the file that you can use for verification purposes on the many Web sites that provide this information.
The whole point of working through the NTBtLog.TXT file is to ensure that you know what’s loading and to look for potential sources of problems. In most cases, the log tells you when files haven’t loaded and tells you about errors that Windows experienced during the boot process. Although it’s perfectly normal to see some drivers fail to load, the failure of an essential driver is something you should note and fix.
Source of Information : For Dummies Windows Server 2008 All In One Desk Reference For Dummies
When it comes to troubleshooting 2008 Servers, there are some basic steps that can be performed based on problems that have been discovered. This article will cover some general steps when troubleshooting is required.
Boot Menu Options
Repair your Computer
Along with the options that are usually presented when you press F8 key, – the new option that has been introduced is Repair your Computer, provided if you have installed Windows RE locally to the server.
Safe Mode
This option starts the server with fewer drivers and services that are running on the server. This option is usually used when you are facing some issues with device drivers. As the server boots the drivers are also loaded on the screen. The list of drivers that are loaded during this process is CD, and hard disk. Services are event log, plug and play, RPC, WMI, and cryptographic.
Safe Mode with Networking
It’s like safe mode but it has the drivers for networking support. It also loads network drivers along with networking services.
Safe Mode With Command Prompt
This is command line interface if you want to run some commands with cmd.
(5)Enable Boot Logging
It is used for debugging, it will show which drivers load and failed. It is written in ntbtlog.txt file which is in windows folder.
Enable Low Resolution Video
Useful to keep the resolution 640*480 mode. Useful to troubleshoot graphical resolutions that are set higher.
Last Known Good Configuration
If you made any changes to the server and then that server is not logging you into Windows, try this option. This is useful if you have installed any drivers and after reboot you are unable to login.
Directory Services Restore Mode
This is used only in Active Directory servers. Used to restore AD using methods (Authoritative and Non-authoritative.)
Debugging Mode
This mode is widely used by developers.
Disable Automatic Restart on System Failure
As the name suggests, for any errors observed the server will reboot and you can control that with this option.
Disable Driver Signature Enforcement
With this option you can allow non signed drivers to load in server system; however the recommendation would be to use the signature drivers wherever possible.
(12)Starts Windows Normally
If by mistake, you press F8 and want to start Windows in normal mode than please press this option.
What is Windows Recovery Environment?
Actually RE is the part of Windows 2008 Media, to use this feature boot from CD. You need to install and repair your computer. It checks for integrity of hardware, drivers, etc.
Tools Section
Reliability Monitor
It has been introduced in Windows 2008 Server; it indicates system performance based on hardware, windows and other failures.
Event Viewer
Event viewers can give to lots of information. There are three critical logs that are available in 2008 server:
- Application Logs – Where application related information is written
- Security Logs – Where security information is noted down
- System log – Where system components write the vent for E.g. hardware
MSconfig
This utility provides system configuration information, you can use which mode (e.g.-diag.) Mode needs to be used for troubleshooting.
Windows Server Event Logs
who restarted windows server
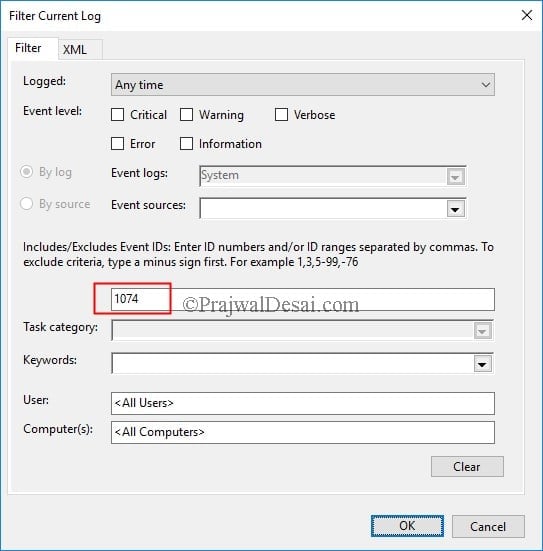
log in to the server. The below steps work on Windows Server 2008, 2008 R2 and Server 2012 R2. Launch the Event Viewer (type eventvwr in run). In the event viewer console expand Windows Logs. Click on System and in the right pane click Filter Current Log.

In the Filter Current log box, type 1074 as the event ID. This will filter the events and you will see events only with ID 1074.
The process C:\Windows\System32\RuntimeBroker.exe (CORPAD) has initiated the restart of computer CORPAD on behalf of user PRAJWAL\sccmadmin for the following reason: Other (Unplanned)
Reason Code: 0x5000000
Shutdown Type: restart
Who Logged In
You’re looking for events with the event ID 4624—these represent successful login events. You can see details about a selected event in the bottom part of that middle-pane, but you can also double-click an event see its details in their own window.
Reboot/Shutdown, force Shutdown Event Logs :
- Event ID 1074: “The process X has initiated the restart / shutdown of computer on behalf of user Y for the following reason: Z.” Indicates that an application or a user initiated a restart or shutdown.
- Event ID 1076: “The reason supplied by user X for the last unexpected shutdown of this computer is: Y.” Records when the first user with shutdown privileges logs on to the computer after an unexpected restart or shutdown and supplies a reason for the occurrence.
- Event ID 6005: “The event log service was started.” This is synonymous to system startup.
- Event ID 6006: “The event log service was stopped.” This is synonymous to system shutdown.
- Event ID 6008: “The previous system shutdown was unexpected.” Records that the system started after it was not shut down properly.
- Event ID 6009: Indicates the Windows product name, version, build number, service pack number, and operating system type detected at boot time.
- Event ID 6013: Displays the uptime of the computer. There is no TechNet page for this id.
- Event ID 7036 telling you that various services “entered the stopped state.” As the machine starts up again, you will see more 7036s announcing that services are entering the running state.
Logon Type:
This is a valuable piece of information as it tells you HOW the user just logged on:
|
Logon Type |
Description |
| 2 | Interactive (logon at keyboard and screen of system) |
| 3 | Network (i.e. connection to shared folder on this computer from elsewhere on network) |
| 4 | Batch (i.e. scheduled task) |
| 5 | Service (Service startup) |
| 7 | Unlock (i.e. unnattended workstation with password protected screen saver) |
| 8 | NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with “basic authentication”) See this article for more information. |
| 9 | NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. |
| 10 | RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) |
| 11 | CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network) |
Impersonation Level: (Win2012 only)
From MSDN
| Anonymous | Anonymous COM impersonation level that hides the identity of the caller. Calls to WMI may fail with this impersonation level. |
| Default | Default impersonation. |
| Delegate | Delegate-level COM impersonation level that allows objects to permit other objects to use the credentials of the caller. This level, which will work with WMI calls but may constitute an unnecessary security risk, is supported only under Windows 2000. |
| Identify | Identify-level COM impersonation level that allows objects to query the credentials of the caller. Calls to WMI may fail with this impersonation level. |
| Impersonate | Impersonate-level COM impersonation level that allows objects to use the credentials of the caller. This is the recommended impersonation level for WMI calls. |
New Logon:
The user who just logged on is identified by the Account Name and Account Domain. You can determine whether the account is local or domain by comparing the Account Domain to the computer name. If they match, the account is a local account on that system, otherwise a domain account.
- Security ID: the SID of the account
- Account Name: Logon name of the account
- Account Domain: Domain name of the account (pre-Win2k domain name)
- Logon ID: a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
- Logon GUID: Supposedly you should be able to correlate logon events on this computer with corresonding authentication events on the domain controller using this GUID. Such as linking 4624 on the member computer to 4769 on the DC. But the GUIDs do not match between logon events on member computers and the authentication events on the domain controller.
Process Information:
- Process ID is the process ID specified when the executable started as logged in 4688.
- Process Name: identifies the program executable that processed the logon. This is one of the trusted logon processes identified by 4611.
Содержание
Просмотр системного журнала
Если в работе Windows 2008 появляется какая-то нестабильность, или появляются ошибки запуска\установки приложений, то это может быть связано с появлениями ошибок в самой операционной системе. Все системные ошибки и предупреждения можно найти в «Журнале системы«. В нем сохраняется информация о событиях, записываемых системными компонентами Windows.
Для просмотра и сохранения системного журнала нужно выполнить шаги:
Открыть «Диспетчер сервера«. Этот пункт меню можно найти нажав на кнопку «Пуск«, затем нажав правой кнопкой мыши на «Компьютер«:

В диспетчере сервера выбрать «Диспетчер сервера» -> «Диагностика» -> «Журналы Windows» -> «Система«
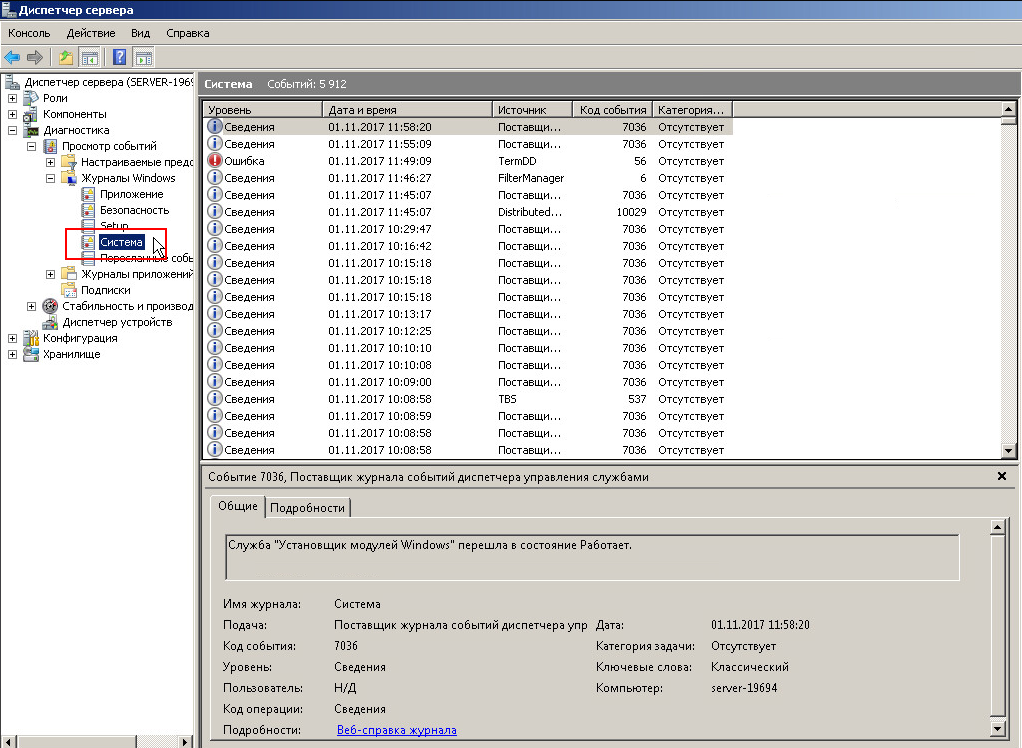
Экспорт журнала
Системный журнал в полном объеме можно экспортировать для последующего изучения путем нажатия на ссылку «Сохранить события как…«

После нажатия ссылки «Сохранить события как…» нужно выбрать путь и имя файла для сохраняемого журнала.

Готово
