Вы можете использовать Active Directory для безопасного хранения резервных копий ключей (паролей) восстановления BitLocker с клиентских компьютеров. Это очень удобно, если в вашей сети множество пользователей, которые используют BitLocker для шифрования данных. Вы можете настроить групповые политики в домене так, чтобы при шифровании любого диска с помощью BitLocker компьютер обязательно сохранял ключ восстановления в учетную запись компьютера в AD (по аналогии с хранением пароля локального администратора компьютера, генерируемого через LAPS).
Чтобы настроить хранение ключей BitLocker в Active Directory, ваша инфраструктура должна соответствовать следующим требованиям:
- Клиентские компьютеры с Windows 10 или Windows 8.1 с редакциями Pro и Enterprise;
- Версия схемы AD не ниже Windows Server 2012;
- Ваши ADMX файлы групповых политик должны быть обновлены до актуальных версий.
Содержание:
- Настраиваем групповую политику для сохранения ключей восстановления BitLocker в AD
- Просмотр и управления ключами восстановления BitLocker в Active Directory
Настраиваем групповую политику для сохранения ключей восстановления BitLocker в AD
Для автоматического сохранения ключей BitLocker в домене вам нужно настроить отдельную групповую политику.
- Откройте консоль управления доменными GPO (gpmc.msc), создайте новую GPO и назначьте ее на OU с компьютерами, для которых вы хотите включить автоматическое сохранение ключей BitLocker в AD;
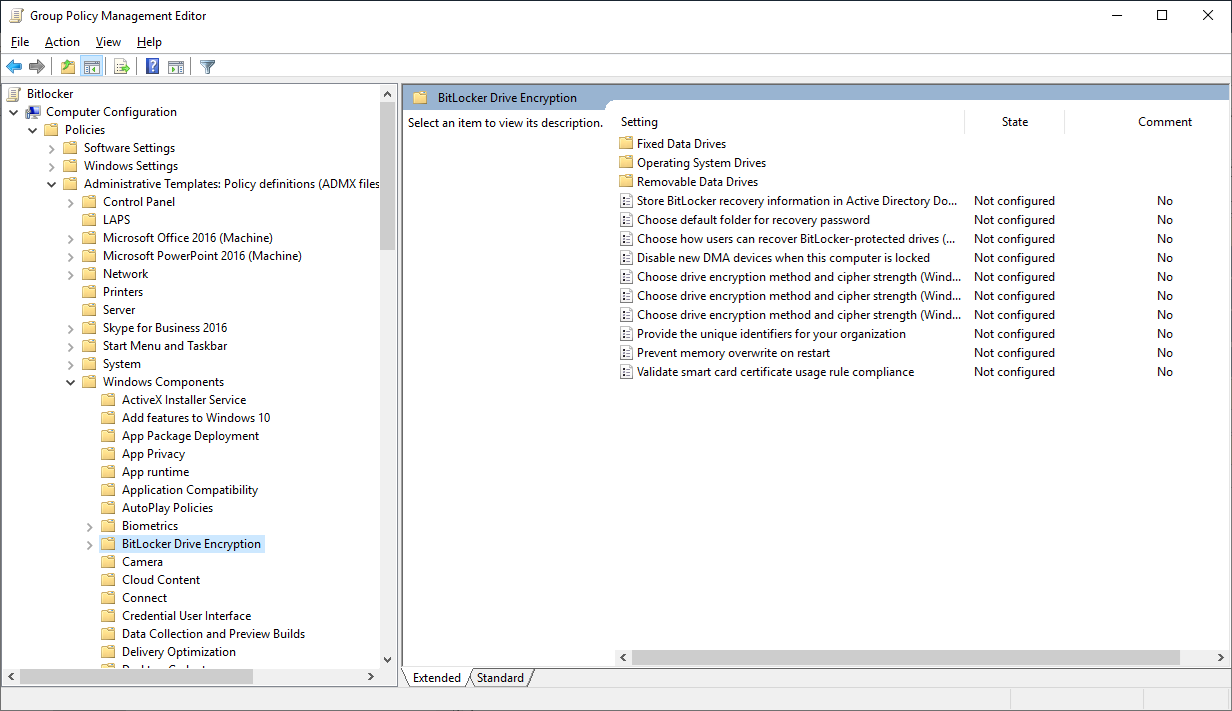
- Перейдите в следующий раздел GPO Computer Configuration -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption;
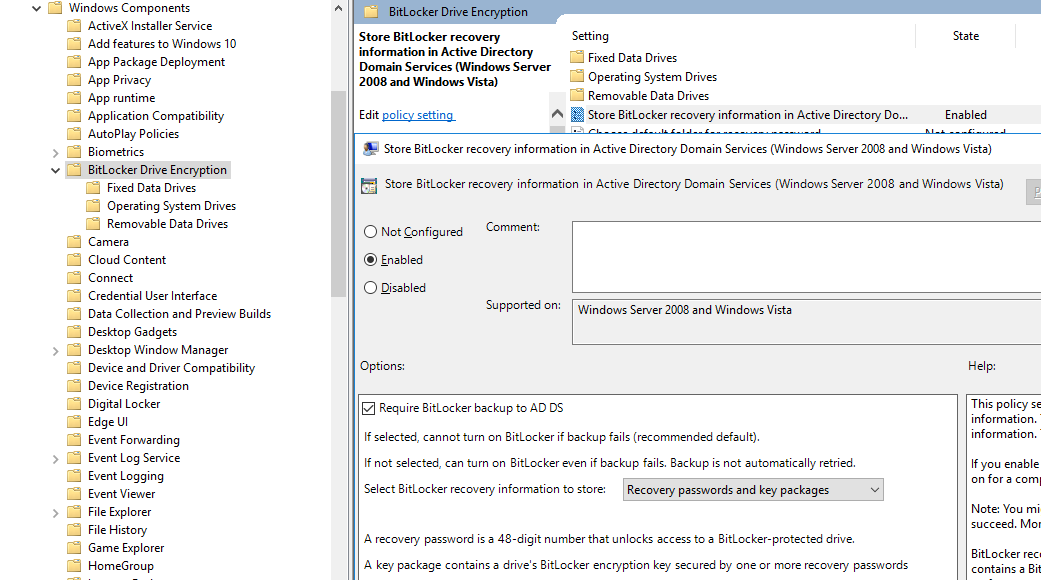
- Включите политику Store BitLocker recovery information in Active Directory Domain Services со следующими настройками: Require BitLocker backup to AD DS и Select BitLocker recovery information to store: Recovery passwords and key packages;
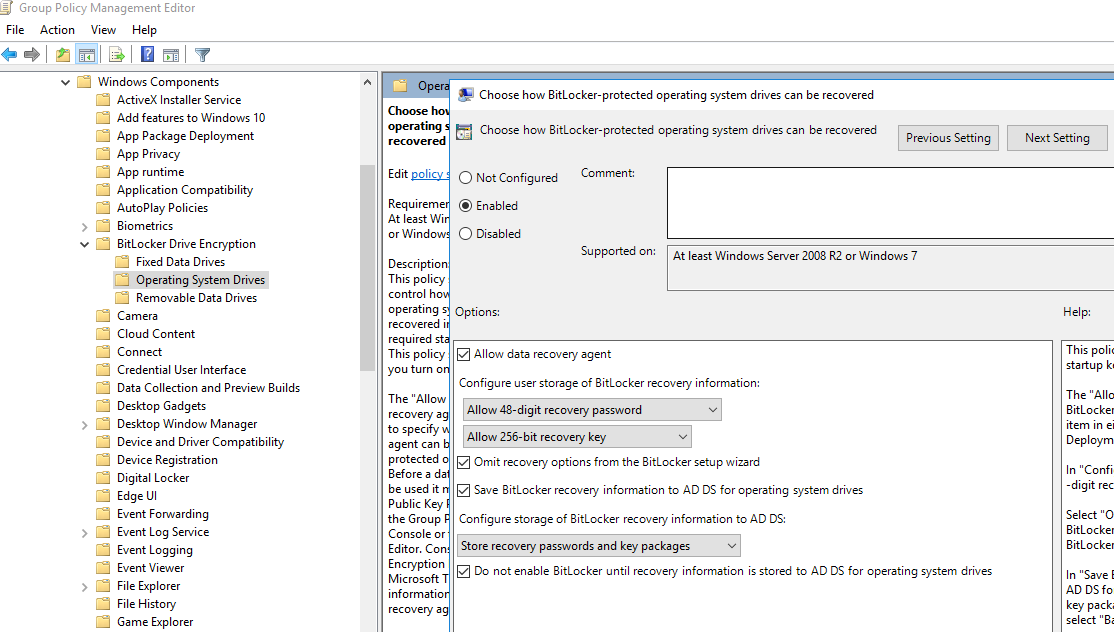
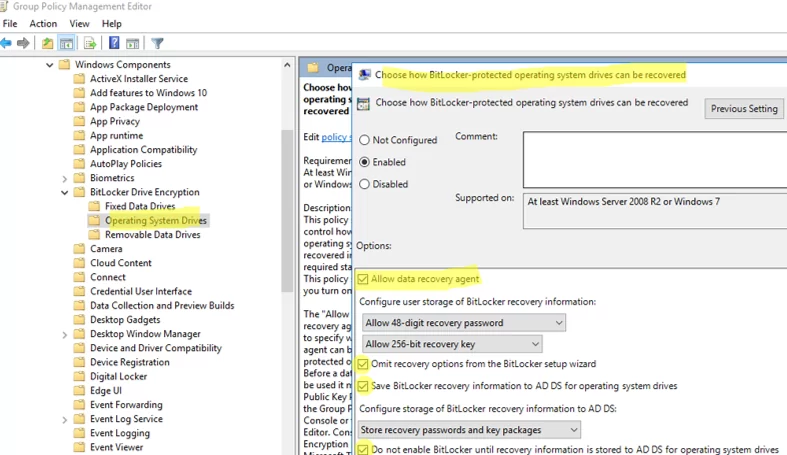
- Затем перейдите в раздел Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption -> Operating System Drives и включите политику Choose how BitLocker-protected operating system drives can be recovered. Обратите внимание, что желательно включить опцию Do not enable BitLocker until recovery information is stored to AD DS for operating system drives. В этом случае BitLocker не начнет шифрование диска, пока компьютер не сохранит новый ключ восстановления в AD (в случае мобильного пользователя придется ждать очередного подключения к домену);
- В нашем случае мы включаем автоматическое сохранение ключа BitLocker для системного диска операционной системы. Если вы хотите сохранять ключи восстановления BitLocker для съемных носителей или других дисков, настройте аналогичную политику в разделах GPO: Fixed Data Drives и Removable Data Drives. [/alert]
- Обновите настройки политик на клиентах:
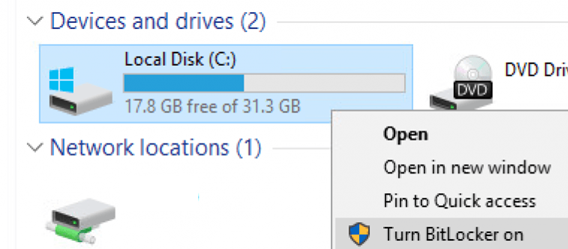
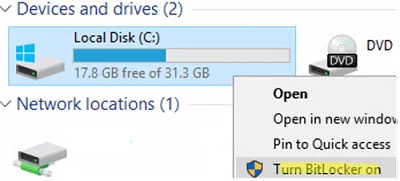
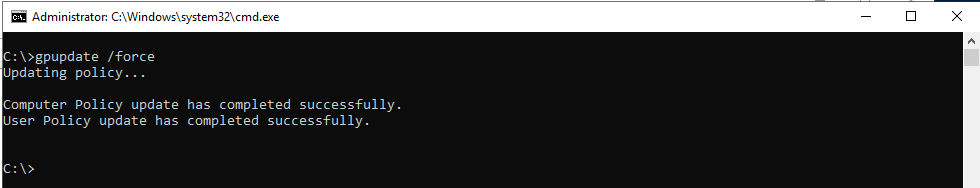
gpupdate /force - Зашифруйте системный диск компьютера с Windows 10 Pro с помощью BitLocker (Turn BitLocker on);
- Windows 10 сохранит ключ восстановления BitLocker компьютера в Active Directory и зашифрует диск.
Для одного компьютера может быть несколько паролей восстановления BitLocker (например, для разных съемных носителей).
Если диск компьютера уже зашифрован с помощью BitLocker, вы можете вручную синхронизировать его в AD. Выполните команду:
manage-bde -protectors -get c:
Скопируйте значение поля Numerical Password ID (например, 33F6F1F0-7398-4D63-C80F-7C1643044047).
Выполните следующую команду, чтобы сохранить этот ключ восстановления в учетную запись данного компьютера в AD:
manage-bde -protectors -adbackup C: -id {33F6F1F0-7398-4D63-C80F-7C1643044047}
Должно появится сообщение:
Recovery information was successfully backed up to Active Directory
Либо можно отправить в AD ключ восстановления BitLocker системного диска с помощью PowerShell:
BackupToAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId ((Get-BitLockerVolume -MountPoint $env:SystemDrive ).KeyProtector | where {$_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorId
Просмотр и управления ключами восстановления BitLocker в Active Directory
Чтобы управлять ключами восстановления BitLocker из консоли Active Directory Users and Computers (ADUC – dsa.msc), нужно установить специальные инструменты RSAT.
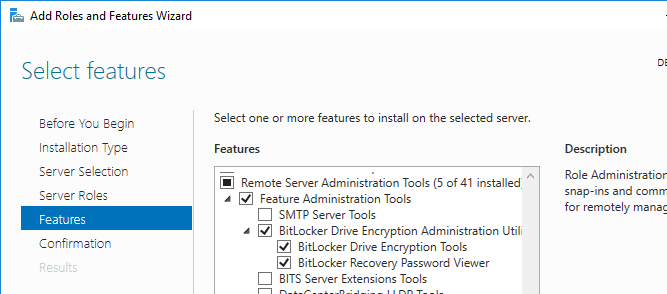
В Windows Server вы можете установить компоненты BitLocker Drive Encryption Administration Utility (содержит BitLocker Drive Encryption Tools и BitLocker Recovery Password Viewer) через Server Manager.
Или можно установить эти компоненты Windows Server с помощью PowerShell:
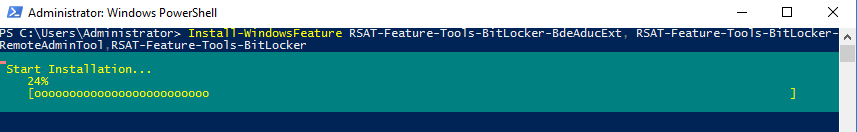
Install-WindowsFeature RSAT-Feature-Tools-BitLocker-BdeAducExt, RSAT-Feature-Tools-BitLocker-RemoteAdminTool, RSAT-Feature-Tools-BitLocker
В Windows 10 нужно установить RSAT-Feature-Tools-BitLocker из состава RSAT.
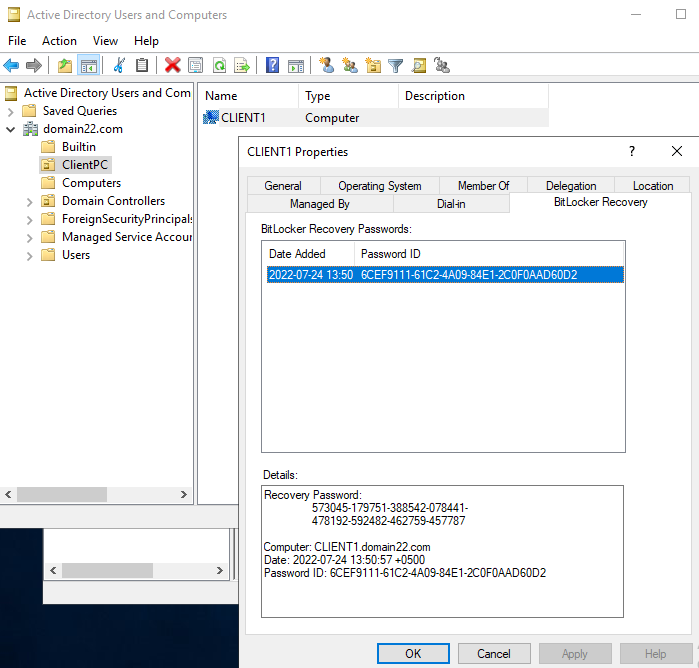
Теперь, если открыть свойства любого компьютера в консоли ADUC, вы увидите, что появилась новая вкладка BitLocker Recovery.
Здесь указано, когда создан пароль, Password ID и ключ восстановления BitLocker.
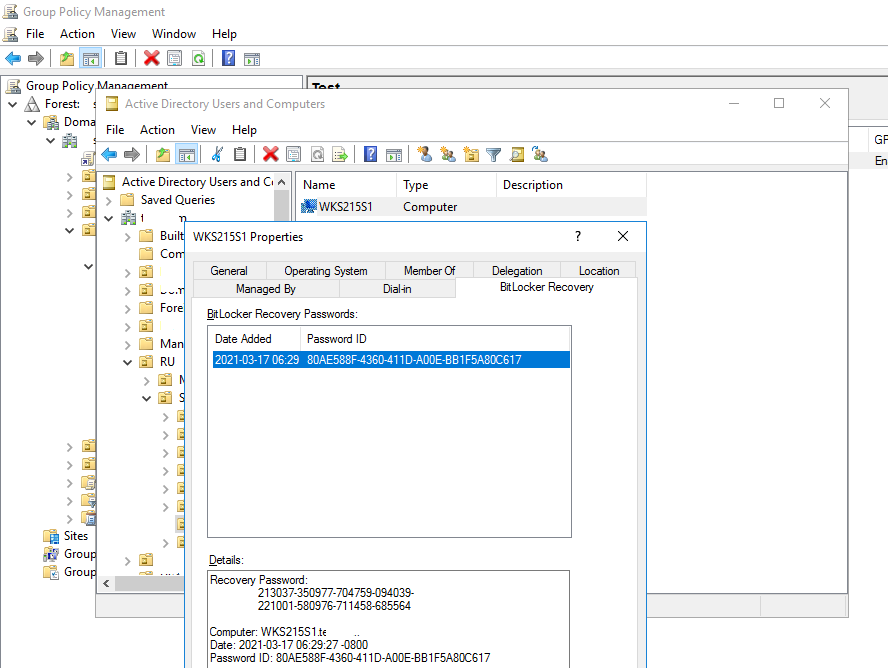
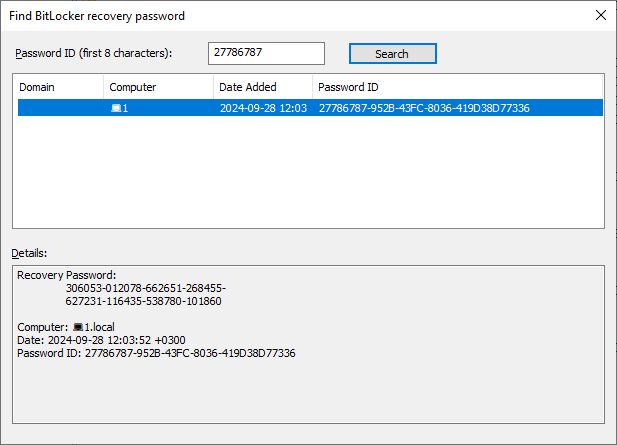
Теперь, если пользователь забыл свой пароль BitLocker, он может сообщить администратору первые 8 символов Recovery Key, которые показываются на экране его компьютера и администратор с помощью функции Action —> Find BitLocker recovery password может найти и сообщить пользователю ключ восстановления компьютера.
По умолчанию, ключи восстановления BitLocker могут просматривать только администраторы домена. В Active Directory вы можете делегировать любой группе пользователей права на просмотр ключа восстановления BitLocker на определенной OU с компьютерами. Для этого нужно делегировать права на просмотр значения атрибута msFVE-RecoveryInformation.
Итак, в этой статье мы показали, как настроить автоматическое резервное копирование ключей восстановления BitLocker в Active Directory и теперь, если пользователь забыл пароль BitLocker, вы сможете получить его и восстановить доступ к данным на устройстве пользователя.
В случае повреждения области жесткого диска с системной информацией BitLocker вы можете попробовать расшифровать данные в соответствии со статьей.
Active Directory можно использовать для хранения резервных копий ключей восстановления BitLocker рабочих станций.
Настроим групповые доменные политики GPO так, чтобы при включении шифрования с помощью BitLocker доменный ПК сохранял копию ключа восстановления в учётной записи компьютера в AD.
Системные требования:
- Клиентская ОС старше Windows 8.1 редакции Pro или Enterprise
- Версия схемы AD не ниже Windows Server 2012
- ADMX файлы групповых политик имеют актуальные версии
GPO для сохранения ключей восстановления BitLocker в AD
Создаём новую групповую политику в домене. Привязываем её к нужной организационной единице домена с рабочими станциями. Редактируем её.
Computer Configuration → Policies → Administrative Templates → Windows Components → BitLocker Drive Encryption.
Включаем политику «Store BitLocker recovery information in Active Directory Domain Services»:
- Enabled
- Require BitLocker backup to AD DS
- Select BitLocker recovery information to store: Recovery passwords and key packages
Apply.
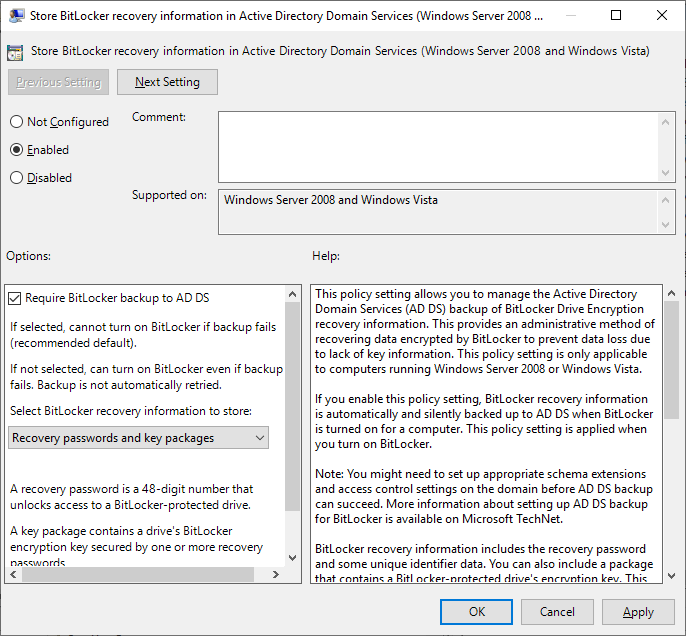
Computer Configuration → Policies → Administrative Templates → Windows Components → BitLocker Drive Encryption → Operating System Drives.
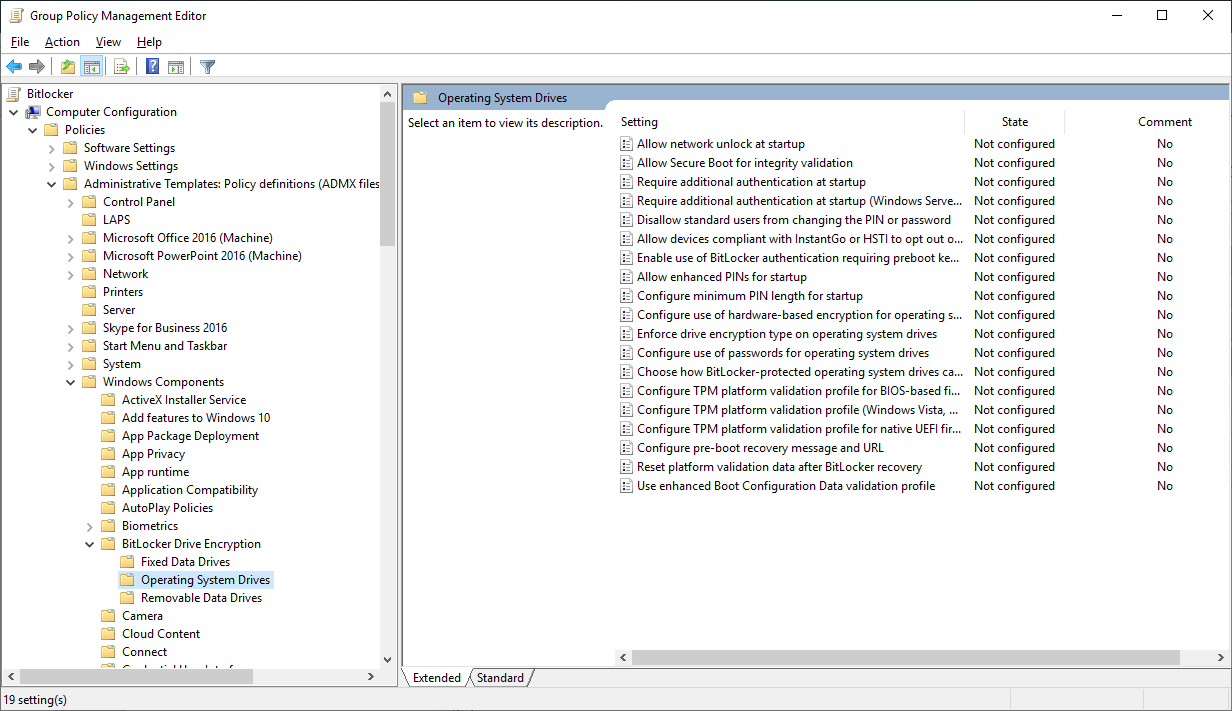
Включаем политику «Choose how BitLocker-protected operating system drives can be recovered»:
- Enabled
- Allow data recovery agent
- Configure user storage of BitLocker recovery information: указываем параметры
- Omit recovery options from the BitLocker setup wizard
- Save Bitlocker recovery information to AD DS for operating system drives
- Configure storage of BitLocker recovery information to AD DS: Store recovery passwords and key packages
- Do not enable BitLocker until recovery information is stored to AD DS for operating system drives
Параметр «Do not enable BitLocker until recovery information is stored to AD DS for operating system drives» необходим для того, чтобы BitLocker не начинал шифрование, пока не синхронизирует ключи с Active Directory.
Если необходимо включить шифрование для других дисков или съёмных носителей, необходимо настроить аналогичную политику в разделах GPO:
- Fixed Data Drives
- Removable Data Drives
Включение BitLocker на рабочей станции
Дожидаемся распространение доменных политик по сайтам домена. Обновляем групповые политики на рабочей станции:
gpupdate /force
Шифруем диск. Правой кнопкой, включить BitLocker.
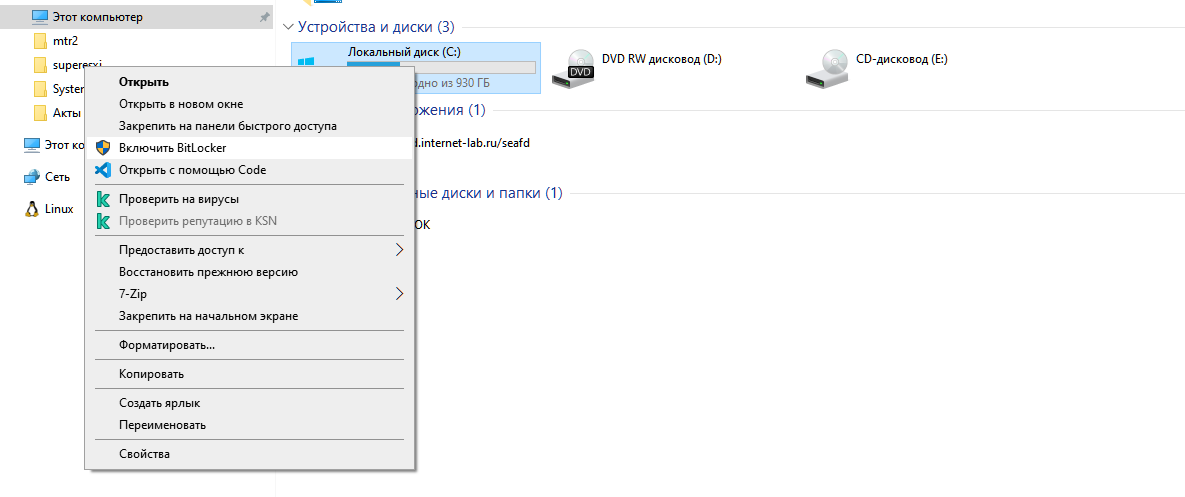
Или из панели управления: Шифрование диска BitLocker.
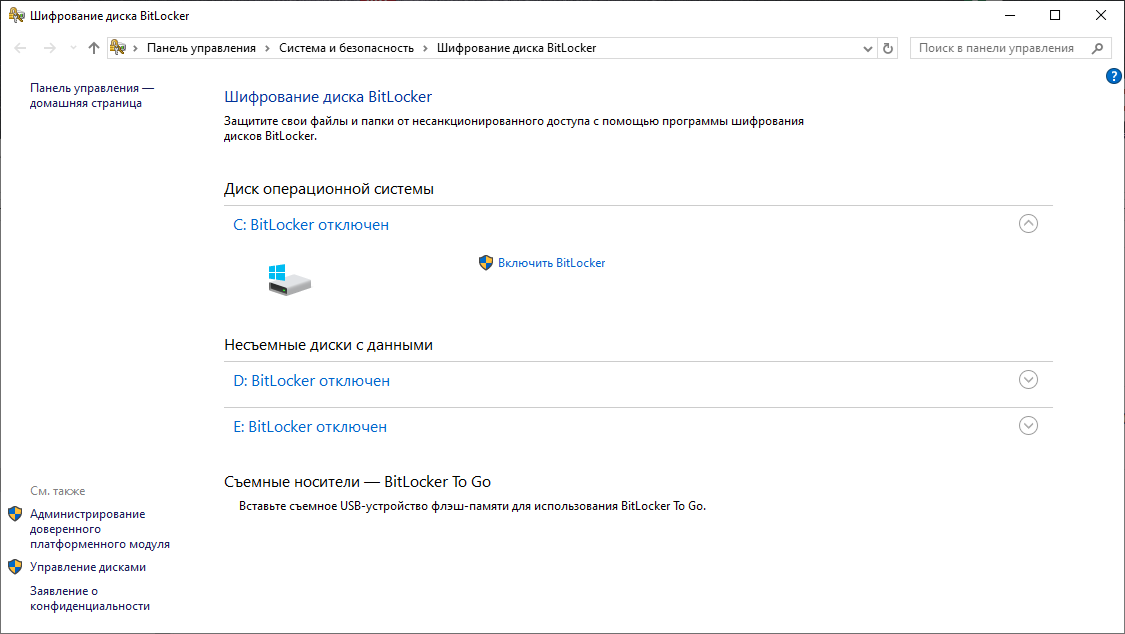
Windows сохранит ключ восстановления BitLocker компьютера в Active Directory и зашифрует диск.
Если диск уже зашифрован с помощью BitLocker, вы можете вручную синхронизировать его в AD:
manage-bde -protectors -get c:Скопируйте Numerical Password ID (например, 33F6F1F0-7398-4D63-C80F-7C1643044047). Сохраните этот ключ восстановления в AD:
manage-bde -protectors -adbackup C: -id "{ваш Numerical Password ID}"Результат: Recovery information was successfully backed up to Active Directory.
Аналогичную процедуру можно сделать через PowerShell:
BackupToAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId ((Get-BitLockerVolume -MountPoint $env:SystemDrive ).KeyProtector | where {$_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorIdУправление ключами восстановления в AD
Для работы с ключами шифрования из консоли Active Directory Users and Computers можно установить компоненты BitLocker Drive Encryption Administration Utility, которые включают в себя:
- BitLocker Drive Encryption Tools
- BitLocker Recovery Password Viewer
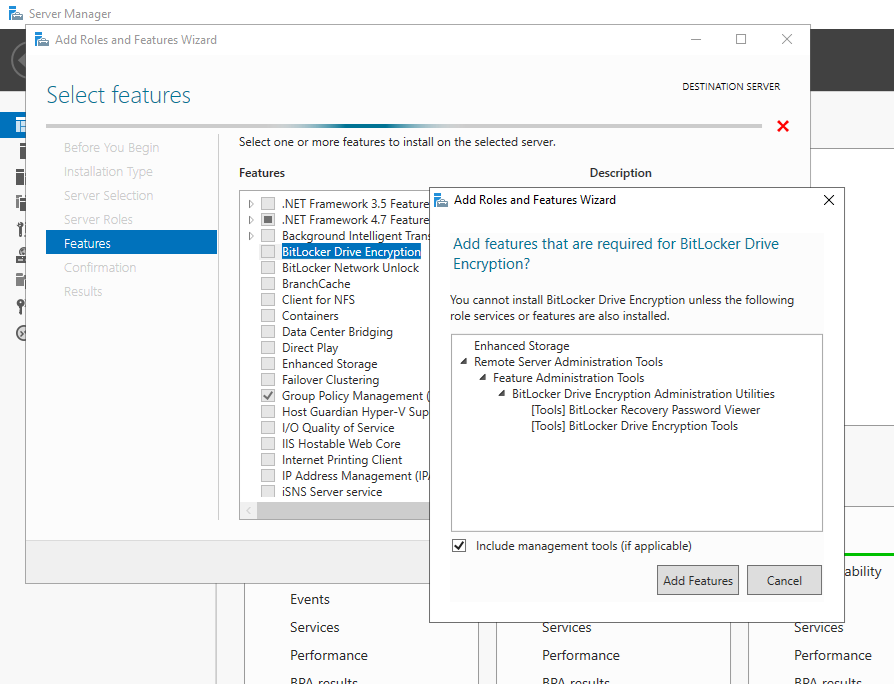
В System Manager добавляем компоненты BitLocker Drive Encryption из пакета Remote Server Administration Tools (RSAT). Потребуется перезагрузка.
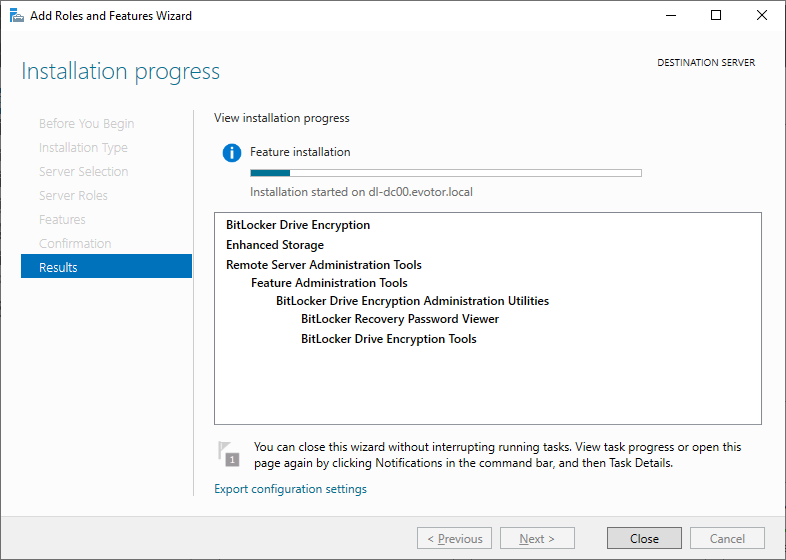
В Windows 10 можно установить RSAT-Feature-Tools-BitLocker из состава RSAT.
Компоненты также можно установить с помощью PowerShell:
Install-WindowsFeature RSAT-Feature-Tools-BitLocker-BdeAducExt, RSAT-Feature-Tools-BitLocker-RemoteAdminTool, RSAT-Feature-Tools-BitLockerОткрываем ADUC, в свойствах компьютера появилась вкладка BitLocker Recovery. Здесь можно посмотреть:
- Время создания пароля
- Password ID (Recovery Key ID, Key ID)
- Recovery Password — ключ восстановления BitLocker
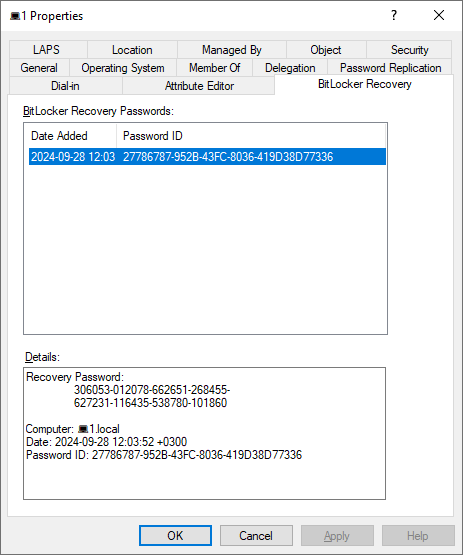
Если пользователь забудет пароль BitLocker (а он забудет), он может сообщить администратору Recovery Key ID или восемь его первых символов, которые показываются на экране его компьютера.
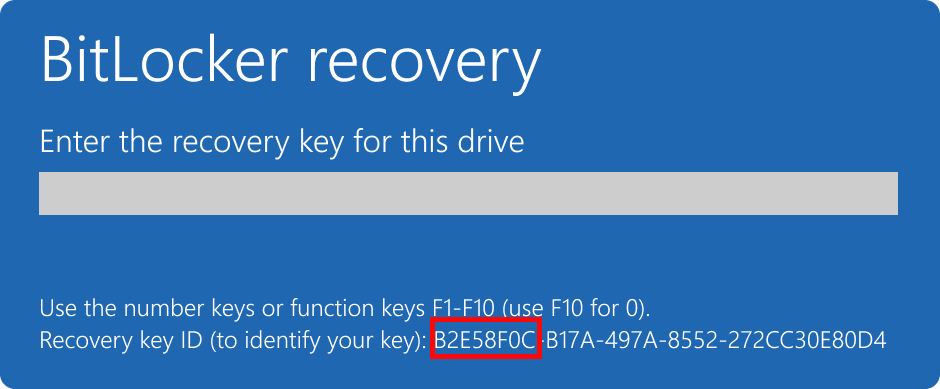
Может потребоваться указать ключ восстановления BitLocker для данных или внешних дисков, например, если пользователь забыл пароль разблокировки.
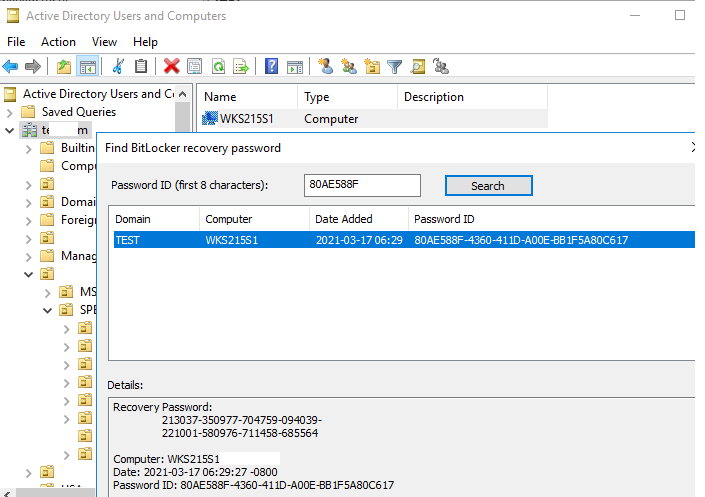
Администратор сможет найти и сообщить пользователю ключ восстановления. Делается это с помощью функции Action → Find BitLocker recovery password при клике правой кнопкой на домен.
Ссылки
Включить BitLocker без TPM
Within the confines of this informative tutorial, you shall embark on a path unveiling the seamless integration of BitLocker recovery keys into the esteemed realm of Windows Active Directory (AD). By adroitly adhering to the following steps, the security of your BitLocker-protected drives shall attain unparalleled fortification, as a centralized repository for imperative recovery information is established. Such a diligent undertaking ensures the safeguarding of your precious data, rendered accessible through clear and succinct guidance. Let us commence this expedition, empowering your AD with the treasured wisdom of BitLocker recovery keys.
Requirements
- For setup BitLocker in AD you need to check all requirements accordance this list:
A Trusted Platform Module (TPM) version 1.2 or newer. This feature is commonly found in most modern computers as a standard inclusion. - A BIOS/UEFI firmware that supports TPM and has it enabled. Ensure that your computer’s BIOS/UEFI settings have TPM enabled to enable smooth BitLocker functionality.
- Secure Boot enabled (if supported by your computer). Activating Secure Boot provides an additional layer of security and complements the TPM feature for enhanced data protection.
Create Policy for domain
To ensure the keys of needed storage within your domain,significant part in our instruction is make and form Group Policy which setup rule of encryption disk. Embrace the power of GPO management, which acts as the gateway to safeguarding BitLocker recovery keys centrally. To embark on this journey, open the GPO management panel.
First of all create object that you want to use in policy, for that open Windows Explorer by pressing combination of keys Win + E, next in the field above enter Control Panel\System and Security\Administrative Tools in that folder choose AD User and Computers:
In that utility create new organization unit or object that you want to apply by policy of disk encryption, for that click on the domain name choose New and Organizational Unit:
Add computer on your machine to OU:
Locating the Group Policy management system is a breeze — simply conduct a search or utilize the following command by pressing Win+R:
gpmc.msc
Next, establish a new group policy within the designated organizational unit that encompasses the computers where you desire to automatically store keys. For instance, you can apply it to the «Computer» OU. However, we can apply this for any objects in Active Directory: forest, domain, sites, OU or organizational unit all of that can be configured.
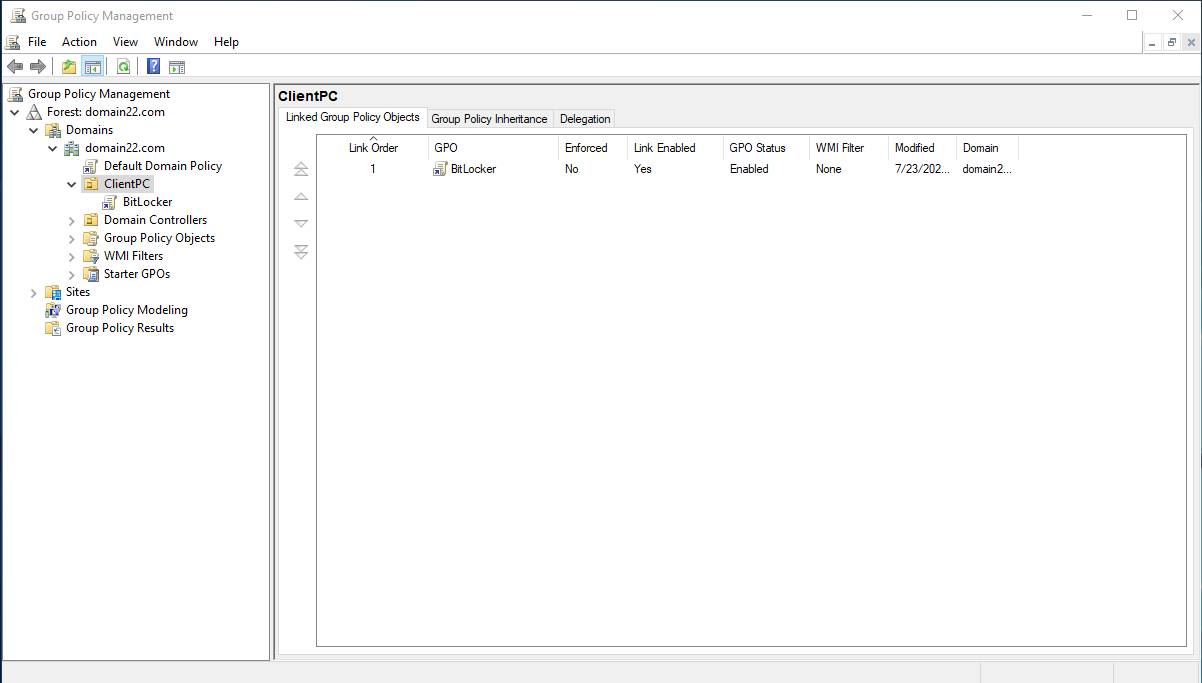
Click right mouse on the your object and choose accordance point as in the picture above:
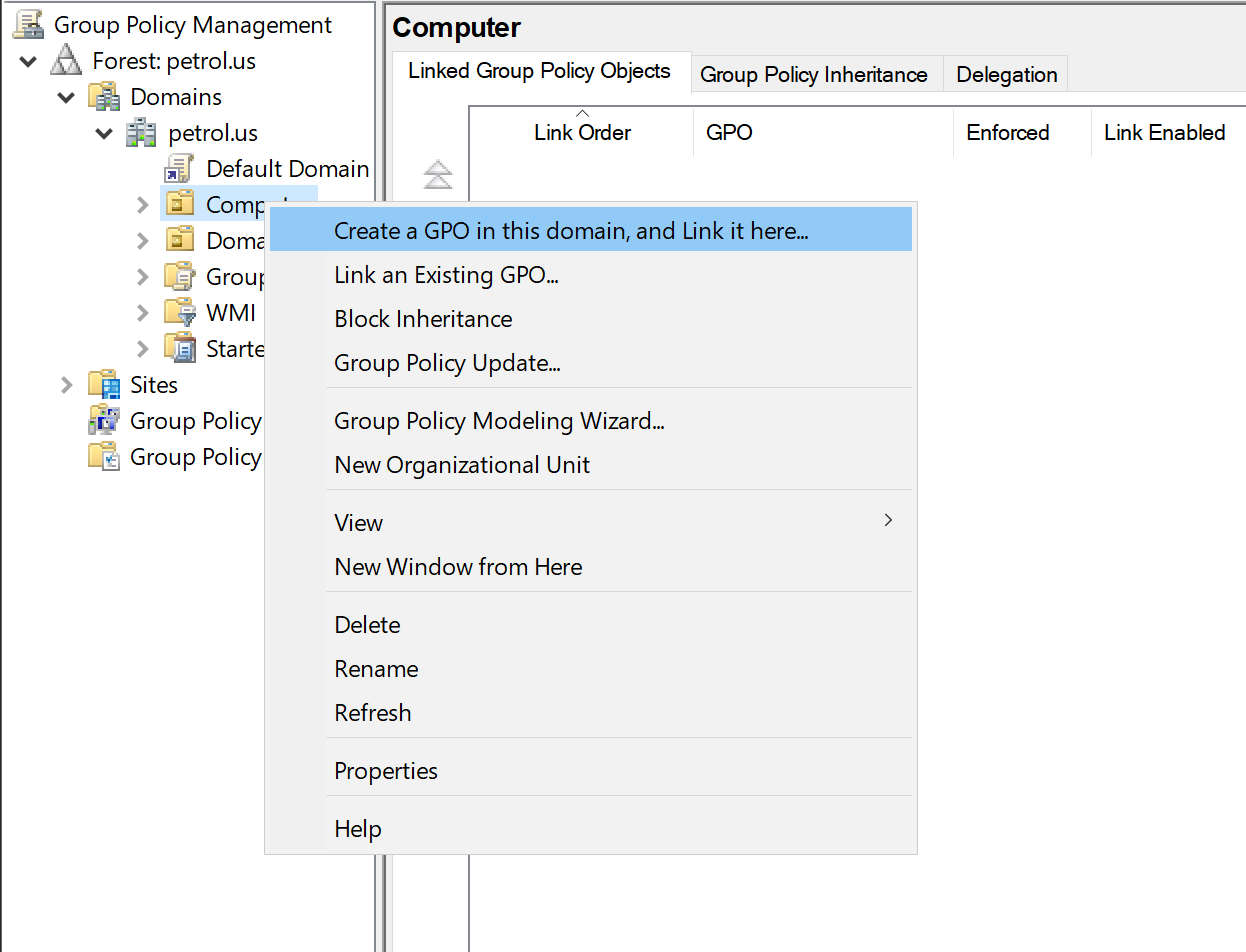
Setup GPO for domain
Begin by establishing a distinct Group Policy. Then navigate to the specified GPO section as illustrated below, and proceed to activate the Store BitLocker recovery information in AD policy option. Follow path Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption, choose that parameter and change value to Enabled.
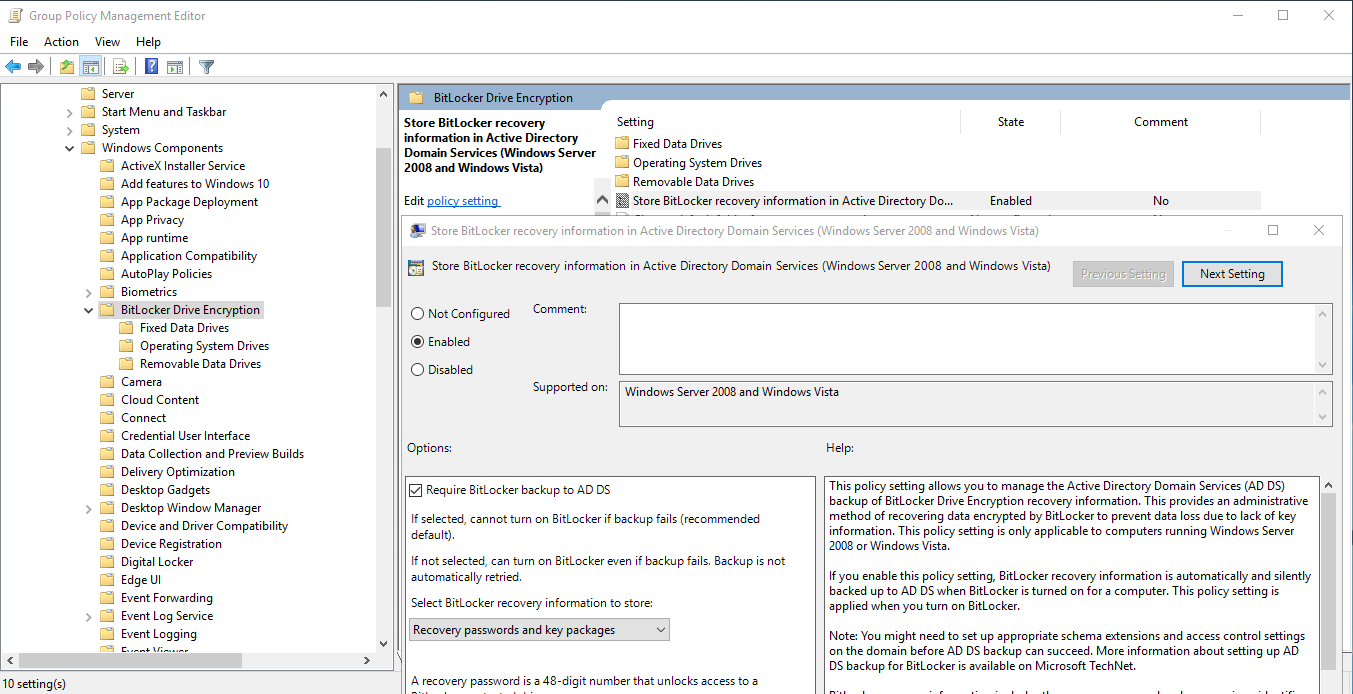
Let’s continue the installation, now you need to go to the folder just below the menu list on the left and select the second Operating folder, which there will be a file with the Store settings, opening it with a double click, go to the panel and select Enabled.
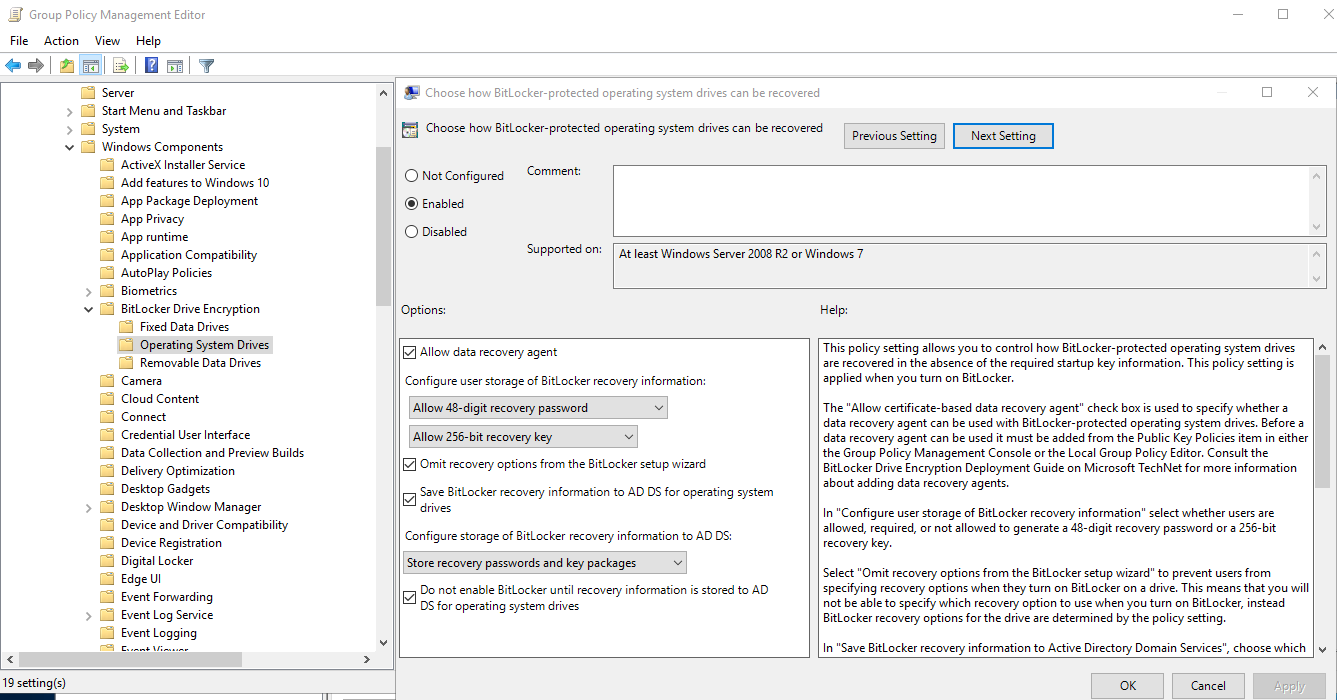
Check all box like in the screen above in options field then make sure that you chek last box due to potential issue of recovery. If you want save keys on removable device you need to choose accordance configuration file and Enabled that function.
Update policy
Next step will be update policy or rules that we configure in the step above, for that type command in the CLI and wait some time:
gpupdate /force
Managing BitLocker data in the AD
In order to effectively manage and configure BitLocker on client computers, it is imperative to install the required components on the server. By doing so, you gain the capability to oversee and fine-tune BitLocker settings, ensuring optimal security and encryption for the client machines:
After successfully installing the component, a server restart is essential to complete the setup. Once the server is up and running, navigate to the Control Panel for AD users and components. Access the properties of the PC, where you will now find a new tab labeled «BitLocker Recovery.» Within this tab, you gain the privilege to view the encryption key, providing essential insight into the BitLocker encryption status and recovery options for the PC.
In the event of a user encountering login difficulties, the domain administrator possesses the capability to retrieve the encryption key from the domain. Armed with this key, the user can effortlessly log in without any impediments. This seamless recovery process ensures swift access and minimizes potential disruptions caused by login complications, guaranteeing a smooth user experience.
In case a user encounters login issues, the administrator holds the ability to retrieve the encryption key from the domain. With this key in hand, the user can effortlessly log in without facing any hindrance. This seamless recovery process ensures swift access and minimizes any potential disruptions caused by login complications.
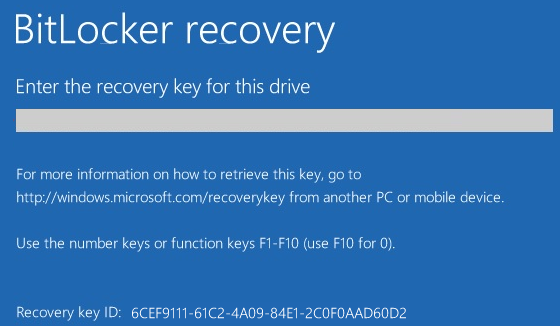
The recovery key can be conveniently located by utilizing the initial 8 characters, as demonstrated in our example, «6CEF9111.» Employing this shortened representation allows for a quick and straightforward retrieval of the full recovery key, ensuring efficient recovery in case of any critical events or issues:
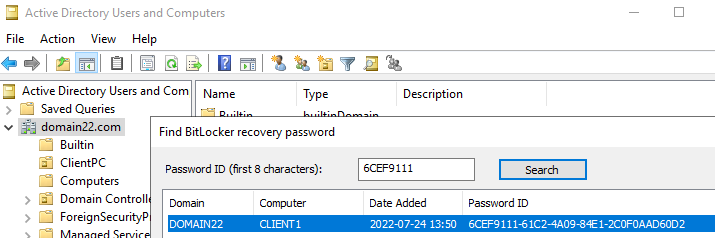
To ensure utmost security, exclusive access to the BitLocker key is granted solely to the domain administrator. Nevertheless, if needed, permissions can be adjusted to provide other domain users with access to the BitLocker key. This flexibility enables a controlled and well-managed approach to granting key retrieval rights, thus empowering the appropriate personnel to access and manage the BitLocker recovery process as required.
BitLocker encryption disk
By clicking on the disk in the target machine choose point with Turn on:
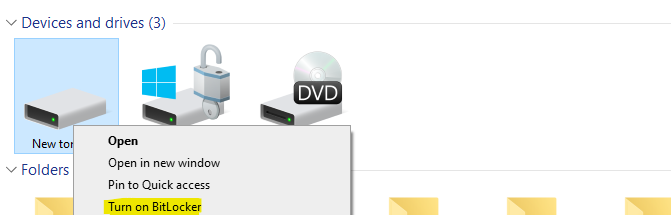
Once your key is securely stored in the domain, BitLocker automatically initiates the encryption process for the drive. This streamlined approach ensures seamless data protection.
Moreover, you have the flexibility to utilize multiple BitLocker passwords on a single PC, each associated with different portable flash drives. This versatile feature allows for convenient and tailored data encryption for various storage devices.
Is disk encrypted?
If you encrypted your disk before that step, then you need to know their ID and add them to the system storage for recovery purposes:
manage-bde -protectors -get c:
By executing this command, you gain access to the comprehensive details of the BitLocker encryption protectors associated with the specified drive. Replace «c:» with the letter corresponding to the specific drive you wish to inquire about. Upon running the command in either Command Prompt or PowerShell, pertinent information like recovery passwords, recovery keys, or TPM protectors (depending on the encryption method employed for that drive) will be displayed.
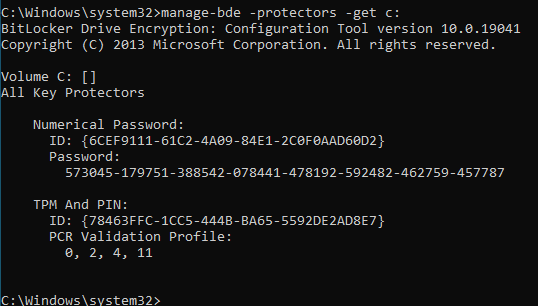
In that process we need to retrieve a ID (e.g., 6CEF9111-61C2-4A09-84E1-2C0F0AAD60D2).
To continue, follow the setup instructions and proceed to enter the next command in the provided interface. This pivotal step ensures the seamless progression of the configuration process, unlocking the full potential of BitLocker encryption.:
manage-bde -protectors -adbackup C: -id {6CEF9111-61C2-4A09-84E1-2C0F0AAD60D2}
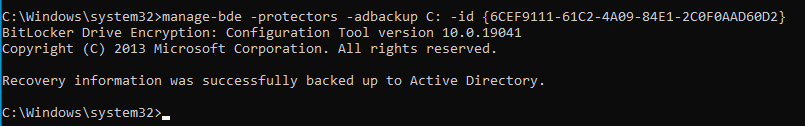
With this command, the specified key will be securely backed up in Active Directory, ensuring the enhanced protection and recovery of your encrypted drive.
Result
This tutorial has empowered you to implement and manage BitLocker with confidence, enhancing data security and enabling swift recovery measures within the AD environment. As a result, your organization is now equipped to safeguard critical data, reinforcing data protection strategies and mitigating potential risks effectively.
You can use Active Directory to securely store backups of BitLocker recovery keys (passwords) from client computers. It is very convenient if you have multiple users using BitLocker to encrypt their data. You can configure Group Policies in your domain so that when encrypting any drive with BitLocker, the computer will save the recovery key in its computer object account in AD (like storing a local computer administrator password generated using LAPS).
To configure storing BitLocker keys in Active Directory, your infrastructure must meet the following requirements:
- Client computers running Windows 10 or Windows 8.1 with Pro and Enterprise editions;
- AD schema version: Windows Server 2012 or higher;
- Your GPO ADMX files must be updated to the latest versions.
Contents:
- How to Configure Group Policy to Store BitLocker Recovery Keys in AD?
- How to View and Manage BitLocker Recovery Keys in Active Directory?
How to Configure Group Policy to Store BitLocker Recovery Keys in AD?
To automatically save (backup) BitLocker recovery keys to the Active Directory domain, you need to configure a special GPO.
- Open the Domain Group Policy Management console (
gpmc.msc), create a new GPO and link it to an OU with the computers you want to enable automatic BitLocker key saving in AD; - Go to Computer Configuration -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption;
- Enable the Store BitLocker recovery information in Active Directory Domain Services policy with the following settings: Require BitLocker backup to AD DS and Select BitLocker recovery information to store: Recovery passwords and key packages;
- Then go to Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption -> Operating System Drives and enable the policy Choose how BitLocker-protected operating system drives can be recovered. Note that it is recommended to check Do not enable BitLocker until recovery information is stored to AD DS for operating system drives. If you check the option, BitLocker will not start drive encryption until the computer saves a new recovery key in AD (if you are a mobile user, you will have to wait for the next connection to the domain network);
- In our case, automatic saving of a BitLocker key is enabled for the operating system drive. If you want to save BitLocker recovery keys for external media devices or other drives, configure a similar policy in these GPO sections: Fixed Data Drives and Removable Data Drives;
- Update Group Policy settings on the clients:
gpupdate /force - Encrypt the system drive of your computer running Windows 10 Pro using BitLocker (Turn BitLocker on);
- Windows 10 will save the BitLocker recovery key for the computer in Active Directory and encrypt the drive.
You may have multiple BitLocker recovery passwords for a single computer (for example, for different removable devices).
If a computer disk is already encrypted using BitLocker, you can manually sync in AD. Run the command:
manage-bde -protectors -get c:
Copy the Numerical Password ID value (for example, 22A6A1F0-1234-2D21-AF2B-7123211335047).
Run the command below to save the recovery key to the current computer’s AD account:
manage-bde -protectors -adbackup C: -id {22A6A1F0-1234-2D21-AF2B-7123211335047}
You will see this message:
Recovery information was successfully backed up to Active Directory
Or you can backup the BitLocker recovery key for your system drive to Active Directory using PowerShell:
BackupToAAD-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId ((Get-BitLockerVolume -MountPoint $env:SystemDrive ).KeyProtector | where {$_.KeyProtectorType -eq "RecoveryPassword" }).KeyProtectorId
How to View and Manage BitLocker Recovery Keys in Active Directory?
To manage BitLocker recovery keys from the Active Directory Users and Computers snap-in (ADUC, dsa.msc), you must install the Remote Server Administration Tools (RSAT).
In Windows Server, you can install the BitLocker Drive Encryption Administration Utility feature using Server Manager (it contains BitLocker Drive Encryption Tools and BitLocker Recovery Password Viewer) .
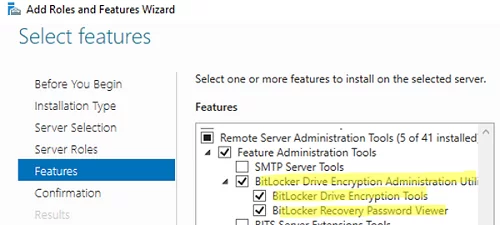
Or you can install these Windows Server features using PowerShell:
Install-WindowsFeature RSAT-Feature-Tools-BitLocker-BdeAducExt, RSAT-Feature-Tools-BitLocker-RemoteAdminTool, RSAT-Feature-Tools-BitLocker
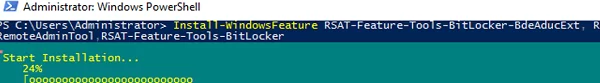
In Windows 10 you have to install RSAT-Feature-Tools-BitLocker from RSAT.
Now, if you open the properties of any computer in the ADUC console, you will see a new BitLocker Recovery tab.
Here you can view when a password was created, get the Password ID and the BitLocker recovery key.
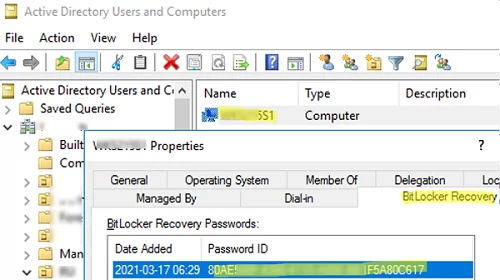
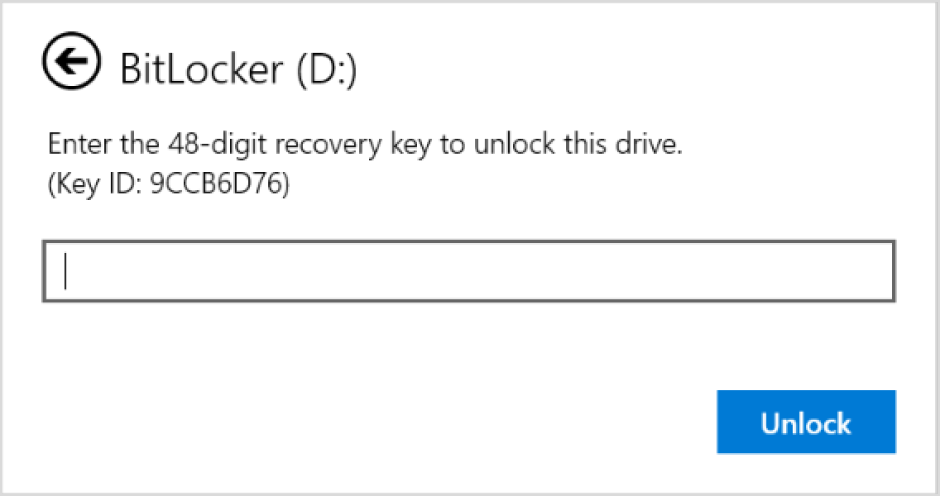
Then if a user forgets his BitLocker password, he can tell the first 8 symbols of the recovery key displayed on the computer screen to the administrator, and the administrator can find the recovery key of the computer in ADUC using Action —> Find BitLocker recovery password and tell it to the user. The recovery password (48-digit number) will help to unlock a Bitlocker-protected drive.
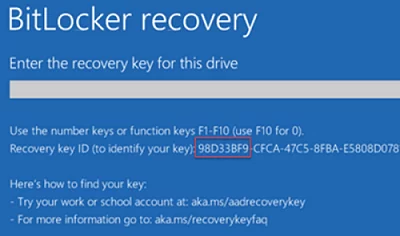
By default, only domain administrators can view BitLocker recovery keys. In Active Directory, you can delegate permissions to view BitLocker recovery keys in a specific OU to any user group. To do it, delegate the permission to view msFVE-RecoveryInformation attribute value.
So, in this article, we have shown how to configure an automatic backup of BitLocker recovery keys in Active Directory. If a user forgets the BitLocker password, you can get it and restore access to the data on the user’s device.
If the BitLocker system information area of the hard drive is damaged, you can try to decrypt the data according to this article.
,
This guide contains step-by-step instructions on how to force Windows to automatically store BitLocker recovery keys and passwords to Active Directory (AD), on any domain computer you enable the BitLocker protection.
If you want to protect your domain laptops and desktop PCs from unauthorized access, e.g. in case of theft, a good practice is to enable BitLocker encryption on all such computers, especially those used outside of your premises.
But since manually managing BitLocker recovery keys in a business environment is difficult, in this guide we’ll see how you can force Windows to back up recovery keys and passwords to AD when you enable the BitLocker protection on a domain-joined computer, and how to view BitLocker data (ID & Password) in AD when required. This process ensures that recovery keys are stored securely, making them easily accessible to administrators when needed.
How to Automatically Back up BitLocker Recovery Keys & Passwords to Active Directory.
To automatically save the BitLocker recovery keys/passwords to Active Directory (AD):
Part 1. Configure Active Directory to Store BitLocker Data.
Step 1. Install BitLocker Drive Encryption Features.
1. On AD Domain Server, open Server Manager and click Add Roles and features.

2. Select Role-based or feature based installation and click Next.

3. At ‘Server Selection’ options, select your Domain Server and click Next.

4. Click Next at Server Roles.
5a. On Features window, select the BitLocker Drive Encryption and…

5b. …then select Add features to install all features required for BitLocker drive encryption along with management tools.

5c. Click Next again to proceed.

6. Finally click Install to install the BitLocker Drive Encryption features.

8. When the feature installation is completed, click Finish and restart the server.

Step 2. Create a new GPO to Store BitLocker keys in AD.
After performing the above steps, proceed to configure Active Directory to automatically backup the BitLocker keys/passwords from domain computers to AD, via a Group Policy.
1. Open Server Manager and from the Tools menu open the Group Policy Management.
2. In Group Policy Manager, either edit the default domain policy or create a new Group Policy for the entire domain or just for the OU that contains the Computers you want to store BitLocker keys in AD.*
* Note: In this example we create a new GPO for the «Workstations» OU which contains all the domain computers where the BitLocker encryption is enabled.
3. Right-click and select Create a GPO in this domain, and Link it here…

4. Name the new GPO as «Store BitLocker keys in Active Directory» and click OK.

5. Now Edit the created GPO.

6a. Go to Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption.
6b. Now open the Store BitLocker Recovery information in Active Directory Domain Services policy.

6c. Set the policy to Enabled, leave the default options Require BitLocker backup to AD DS & Recovery passwords and key packages selected, and click Apply > OK.

7a. Then, go to Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives.
7b. Open the policy Choose how BitLocker-protected system drives can be recovered.

7c. Enable the policy and then check the option Do not enable BitLocker until recovery information is stored in AD DS for operating system drives to prevent users from enabling BitLocker unless the computer is connected to the domain and the backup of BitLocker recovery information to AD DS succeeds. When done, click OK.

8. Close all the Group Policy Management windows.
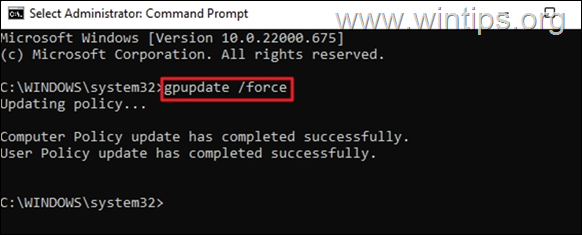
9. Finally, open Command Prompt as Administrator and give the following command to apply the new policy in both the server and the workstations (or restart the workstations):
- gpupdate /force
Step 3. Turn On BitLocker on Workstations.
If you haven’t already enabled BitLocker on client computers, do the following:*
* Note: If you have already enabled BitLocker on clients, then follow the steps in this guide to manually backup the recovery keys and passwords in AD: How to Store Manually the BitLocker keys in Active Directory (AD).
1. Login to client machines, with a user that have Local Administrator rights on the machine.
2. Navigate to Control Panel and open BitLocker Drive Encryption.

3. Click Turn On BitLocker next to C: drive (aka «OS drive»), and follow the on-screen instructions to encrypt it.

4. A message will now appear telling you if you’re ready to encrypt the drive. At this point, check the Run BitLocker system check box and click Continue to ensure that the machine can read the recovery data before encrypting the drive. Then, click Restart now.

5. After restarting, Windows will start encrypting the drive and the BitLocker Recovery key and password will be automatically stored automatically in AD.
6. Finally, proceed to verify that the recovery key and password are stored on the computer’s object in AD by following the instructions below.
Part 2. View BitLocker Recovery Keys and Passwords in AD (Active Directory).
After applying the above steps, you’ll be able to retrieve the stored BitLocker keys in AD, using one of the following ways:
A. Using Computer Properties in Active Directory.
1. Open Active Directory Users and Computers.
2. Right-click on the computer object that you want to view the stored recovery key and choose Properties.
3. Then select the BitLocker Recovery tab to see the Recovery ID and the Recovery Password under the ‘Details’ field.

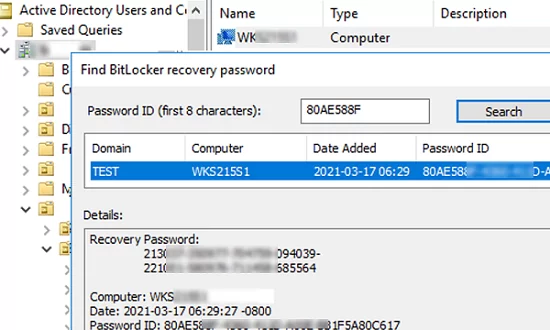
B. Using ‘Find BitLocker Password’ option.
If you know the Recovery ID (identifier):
1. Open Active Directory Users and Computers.
2. Right-click on the domain name and select Find BitLocker Password.

3. Type the first eight (8) characters of the Recovery ID of the computer that you want to see the BitLocker recovery key and click Search.

That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).