Lately, I have been working a lot with SSH and Windows 10, for one transitioning away from WMI for certain things, hopefully, a blog post coming on that front soon. Setting up SSH on Windows 10 is fairly simple to do, but it is one of those processes that can be wrought with missteps and misinformation from various places. As a case in point, you may receive permissions issues on a private key connecting to Windows 10. Why is this? Let’s take a look at bad owner or permissions on SSH config Windows 10 and see what this relates to.
Public key authentication with Windows 10
First of all, if you see this error mentioned in the title of the blog post, it means you are most likely attempting to configure public key authentication to access your OpenSSH installed and configured in Windows 10. Why do you want to configure public key authentication?
First of all, if you want to know how to configure Windows 10 SSH, take a look at my blog post here:
- OpenSSH Server Windows 10 Install with Public Key authentication
Also, learn about OpenSSH in general here:
- OpenSSH
Public key authentication is noted as a more secure way to authenticate to an OpenSSH server. Why is this? With public-key authentication, you have two parts of a cryptographic key that grants access. It includes both a private key and a public key. The SSH server possesses the public key of the key pair, while you as the user possess the private key. In addition to passing the physical private key file, you can also secure the private key with a password.
So, it is easy to understand how this type of authentication is much more secure. As far as the cryptographic key is concerned, an attacker can’t simply brute force the server to guess a weak, guessable, or cracked password to gain access. They have to have possession of the key and know the password if the private key is secured with one.
SSH clients have also come a long way in recognizing when there may be bad ideas in play when it comes to private key files. If the permissions contain other security permissions on the private key file other than the user that should possess those permissions, the key can be more easily compromised.
Many SSH clients check for the permissions configured on the SSH private key and if these are too permissive, it will not be allowed for use to make the SSH connection. Note the following error seen when trying to SSH into a remote Windows 10 machine with wide-open permissions on the private key file:
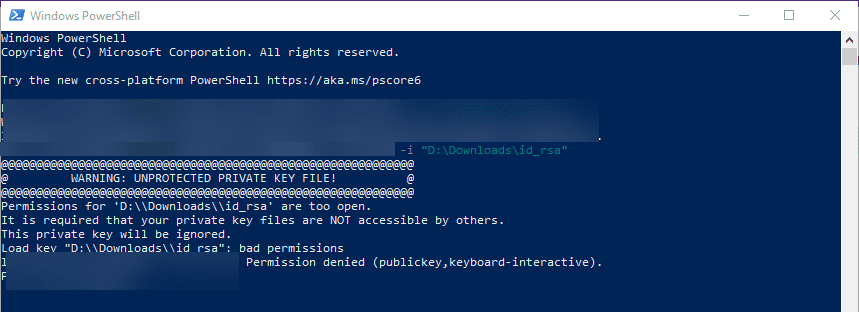
The error above states the issue: Permissions for the key file are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored.
To get past the Bad Owner or Permissions on SSH Config Windows 10 error, you need to configure three things:
- Permissions on the authorized_keys file
- Permissions on your private key file
- sshd_config file changes
Part of the process to properly configure your Windows 10 SSH session for public-key authentication is ensuring the permissions are set correctly, both on the authorized_keys file (holds public key) and the private key file that holds the private key side of your key pair. Let’s take a look at both.
When you enable OpenSSH on your Windows 10 machine, you need to create the .ssh directory in the user profile of the user you will be logging in with. This is the location OpenSSH looks to find the authorized public keys, and by extension, the paired private keys that are allowed to access the machine.
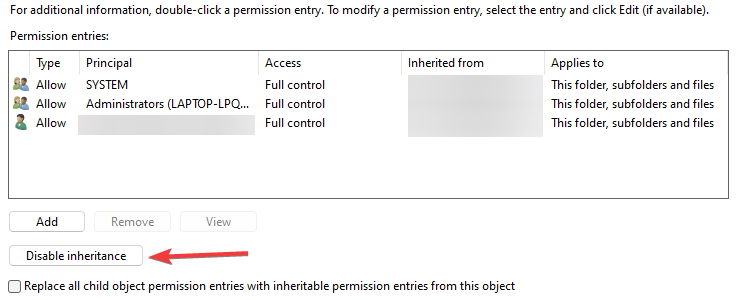
By default, when you create the directory and the authorized_keys file, it will have too many permissions assigned. As you can see, it will have the local Administrators group added to the file. Click Advanced.
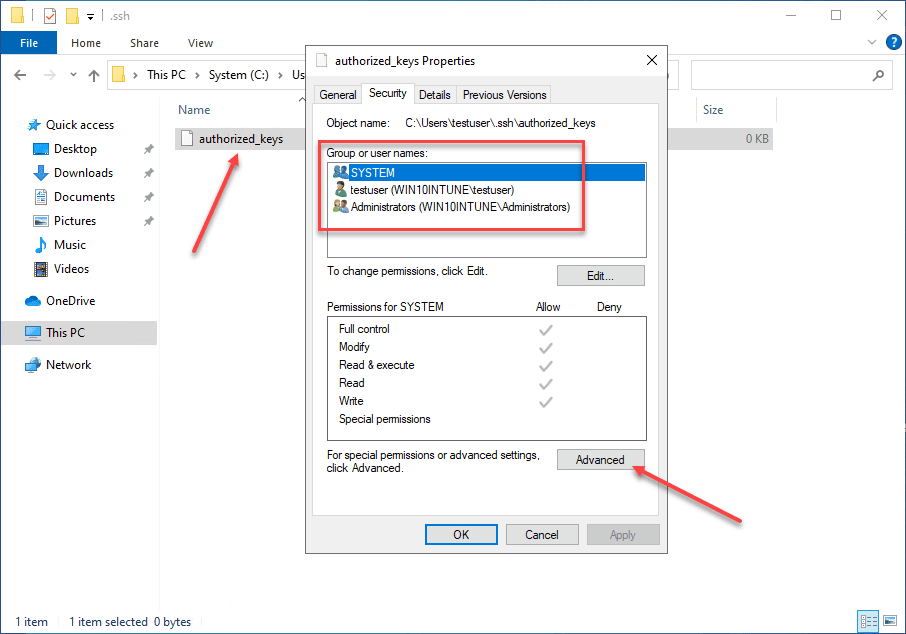
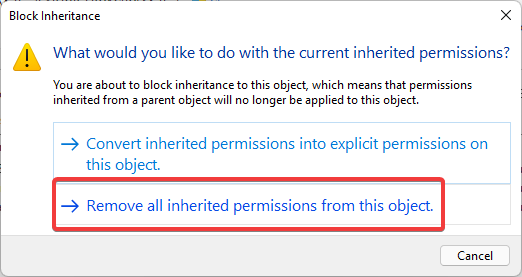
Here, we need to disable inheritance. This breaks inheritance on the folder and allows you to set explicit permissions.
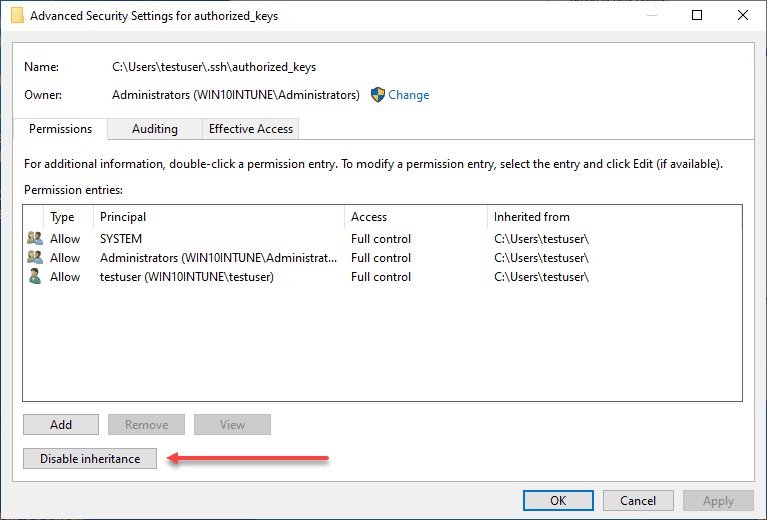
Choose the option Convert inherited permissions into explicit permissions on this object.
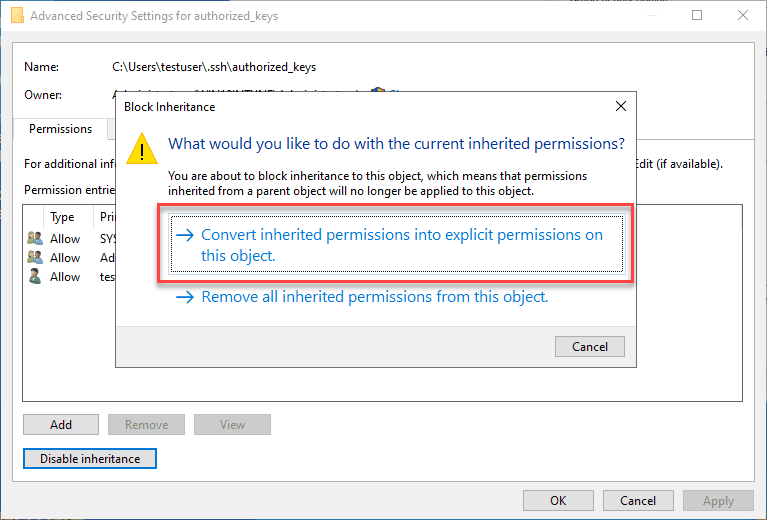
Adjust your permissions so that you only have SYSTEM and your username displayed as having permissions on the authorized_keys file.
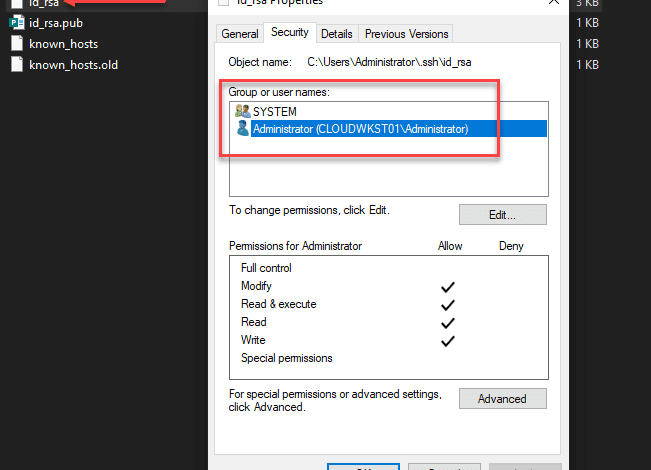
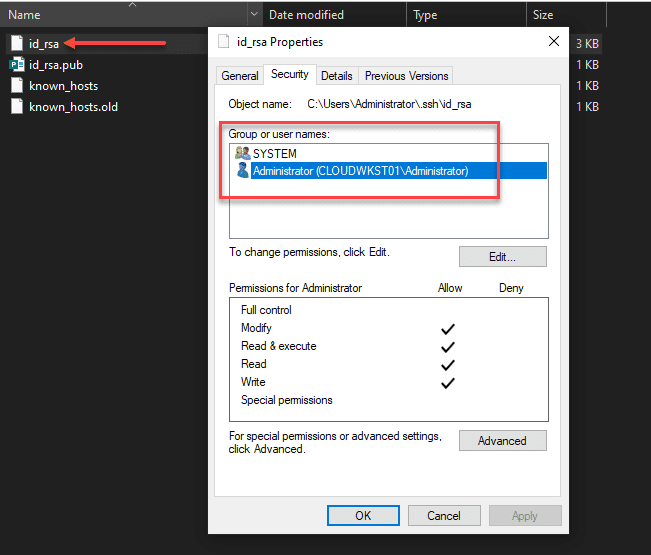
Permissions on your private key file
Now, on your private key, you need to ensure the same thing is set. The user that you are logged in with and SYSTEM are the only permissions that need to be enumerated on the private key file.
sshd_config file changes
Now that we have the permissions set correctly on the authorized_keys file and the private key, we need to make sure the sshd_config file is configured correctly. We need to make three changes for this to work correctly:
Below, I have uncommented the PubeyAuthentication yes stanza. Then, we have commented out the PasswordAuthentication yes and Match Group administrators configuration.
PubkeyAuthentication yes
#PasswordAuthentication yes
#Match Group administrators
# AuthorizedKeysFile __PROGRAMDATA__/ssh/administrators_authorized_keysBe sure to restart your OpenSSH SSH Server service on your Windows 10 machine after making these changes to the sshd_config file. Once the changes are in place, you should be able to connect to the machine via SSH.
Wrapping Up
Connecting to Windows 10 via SSH is a great way to make secure connections to Windows 10 when public-key authentication is used. It can also be a great way to use solutions like Ansible to connect to your Windows 10 boxes remotely.
Brandon Lee
Brandon Lee is the Senior Writer, Engineer and owner at Virtualizationhowto.com, and a 7-time VMware vExpert, with over two decades of experience in Information Technology. Having worked for numerous Fortune 500 companies as well as in various industries, He has extensive experience in various IT segments and is a strong advocate for open source technologies. Brandon holds many industry certifications, loves the outdoors and spending time with family. Also, he goes through the effort of testing and troubleshooting issues, so you don’t have to.
Starting from Windows 10 build 1809, Windows has a native SSH client that is based on the OpenSSH port.
If you try to connect to some host from a Windows command-line prompt (CMD) or PowerShell using the ssh command, you may receive the error as follows:
Bad owner or permissions on
C:\\Users\\<username>/.ssh/config
This short note shows how to fix the permissions on all the files under the C:\\Users\\<username>/.ssh folder.
Right-click on the .ssh folder and select “Properties“.
Go to the “Security” tab and click on “Advanced“:
Click on “Disable inheritance“:

Choose the option “Remove all inherited permissions permissions from this object“:

Remove all users and groups except SYSTEM and your user, check the box “Replace all child object permission entries with inheritable permission entries from this object” and click on “OK“:

The correct owners and permissions on the C:\\Users\\<username>/.ssh folder should look like this:

The “Bad owner or permissions on C:\\Users\\<username>/.ssh/config” error should be resolved now and you should be able run the ssh command without any issues.
Was it useful? Share this post with the world!
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
SSH is commonly used by network administrators to control systems, and issues such as Bad owner or permissions on SSH config occur seldom.
Fixing this problem is rather straightforward, but it is one of those processes rife with blunders and misinformation from multiple sources.
But what if someone who did not know how to fix this problem encountered it? Here are some fixes that might help you.
What is SSH used for?
SSH connections have been used to secure a variety of communications and administrative or management duties between a local workstation and a remote host.
Among other things, SSH is used to control routers, server hardware, virtualization platforms, operating systems (OSes), and file transfer programs.
A related problem is the Unable to establish host authenticity but this guide will help you fix it quickly.
Now, let’s see how we can fix bad owner or permissions on SSH config with the solutions below.
How can I fix bad owner or permissions on SSH config?
1. Change permission
- Open Windows Explorer and locate your .ssh folder. It is usually located in
C:\Users\ - Right-click the .ssh folder and click Properties.
- Find and click the Security tab and then click Advanced.
- Click Disable Inheritance.
- A warning popup will appear. Click Remove all inherited permissions from this object.
- Click OK to close the Advanced Security Settings for .ssh window.
- You will notice that all users will be removed. On the same window, click the Add button.
- Next, click Select a principal to bring up the Select Users or Groups window.
- Click Advanced.
- Click the Find Now button. A list of user results should appear.
- Select your user account.
- Then click OK.
- Microsoft’s hotpatching for Windows Server 2025 to be subscription-based starting July
- Fix: An Error Occurred While Loading a Higher Quality Version of This Video
- iTunesMobileDevice.dll is Missing From Your Computer [Solved]
- SYNSOACC.DLL Could Not Be Located: How to Fix in Cubase
2. Using commands
- First, type in
chown $USER ~/.ssh/config - After that, type in
chmod 644 ~/.ssh/config
What is the difference between telnet and SSH?
Telecommunications and Networks are abbreviated as Telnet, and it is a networking protocol best known for the UNIX platform.
Telnet is credited as being the first Internet, having been created as a method of remote control for managing mainframe computers from remote terminals when the Internet originally opened in 1969.
While there is no official fix for bad owner or permissions on the SSH config problem, many users have reported that removing inherited permissions has worked for them.
Additionally, there are numerous lines of commands that might fix the issue and are available on the web and in the forums.
The fix for a bad owner or permissions on the SSH config problem can vary in steps depending on the process type.
If you are experiencing ssh_exchange_identification connection closed by host issues, read this article.
Let us know whether you were able to fix the bad owner or permissions on the SSH config in the comments section below.
Farhad Pashaei
As a technophile, Farhad has spent the last decade getting hands-on experience with a variety of electronic devices, including smartphones, laptops, accessories, wearables, printers, and so on.
When he isn’t writing, you can bet he’s devouring information on products making their market foray, demonstrating his unquenchable thirst for technology.
Ошибка Bad owner or permissions сообщает что у конфигурационного файла слишком много прав, а точнее очень много источников имеют к нему доступ. Поэтому наша задача сделать доступным этот файл только для одного пользователя.
Для этого нужно перейти в папку где находится файл config:
C:\Users\*ИМЯ_ПОЛЬЗОВАТЕЛЯ*\.sshКликнуть правой кнопкой мыши по файлу config.
В появившемся окне выбрать пункт «Свойства».
Далее выбрать вкладку безопасность.
Нажать на кнопку «Дополнительно» (внизу окна)
В появившемся окне сначала нажать кнопку «Отключить наследования» и в окне подтверждения выбрать опцию «Удалить все унаследованные разрешения из этого объекта»

Затем нажимаете «Ок» и подтверждаете что файл будет доступен только владельцу.
Теперь нужно добавить разрешения для текущего пользователя. На вкладке «Безопасность» нажимаем кнопку «Изменить».
В появившемся окне нажимаем кнопку «Добавить», далее в новом окне нажимаем кнопку «Дополнительно».

В появившемся окне нажимаем поиск, а в таблице с результатами выбираем вашего текущего пользователя Windows (кликнуть по нему 2 раза или выбрать его и нажать «Ок»).


Нажимаем «Ок» во всех открытых окнах, оставляя только окно «Разрешение для группы config» и для нового пользователя в разделе «Разрешение для группы» выбираем чекбокс «Полный доступ» в колонке «Разрешить».

Нажимаем «Ок» во открытых окнах.
Проблема должна быть решена. Теперь к файлу config есть доступ только у текущего пользователя Windows.
This article helps to solve a Bad owner or permissions on .ssh/config issue occurring on a Windows 10 machine when using a terminal emulator like cmder.
Using cmder on a Windows 10 development machine, I noticed issues after I recently added a new user account to the system. It caused permission issues due to the way inheritance of ownership was being handled.

Resolve ‘Bad Owner or Permission on .ssh/config’ issues on Windows 10
To resolve, I did the following to fix up the permission issues that cause a `Bad owner or permissions on C:\\Users\\Peter/.ssh/config` from occurring each time I tried to connect to a remote host within cmder:
Fixing the ‘Bad owner or permissions on .ssh/config’ Issue
Follow these steps in the Windows 10 GUI to resolve the permission issues:
- Locate your .ssh folder. It is usually located in C:\Users\ e.g. C:\Users\Peter.
- Go to this location with Windows Explorer.
- Right click the .ssh folder and click ‘Properties’.
- Find and click the ‘Security’ tab.
- Then click ‘Advanced’.
- Click ‘Disable Inheritance’, click OK.
- A warning popup will appear. Click ‘Remove all inherited permissions from this object’.
Disable Inherited permissions on Windows 10 for a folder.
- Click ‘OK’ to close the ‘Advanced Security Settings for .ssh’ window.
- You will notice that all users will be removed. Let’s add the owner back. On the same window, click the ‘Edit’ button.
- Next, click ‘Add’ to bring up the Select Users or Groups window.
- Click ‘Advanced’, then click the ‘Find Now’ button. A list of user results should appear.
- Select your user account. In my case, I selected user ‘Peter’.
- Then click OK (approximately three times) to close all windows.
Once all that is done, close and open the cmder app again and attempt to connect to a remote SSH host. Hopefully your set up is fixed and the ‘Bad owner or permissions on .ssh/config’ error prompt is gone.