В этой статье мы поговорим об особенностях резервного копирования контроллеров домена Active Directory, рассмотрим, как настроить автоматическое резервное копирование AD с помощью PowerShell и встроенного Windows Server Backup.
Содержание:
- Нужно ли бэкапить Active Directory?
- Как проверить дату последнего бэкапа контроллера домена Active Directory?
- Бэкап контроллера домена AD с помощью Windows Server Backup
- Резервное копирование Active Directory с помощью PowerShell
Нужно ли бэкапить Active Directory?
Одним из способов повышения отказоустойчивой и распределения нагрузки в Active Directory является развертывание дополнительных контроллеров домена. В такой среде база AD реплицируется между всеми DC и при выходе из строя любого контроллера домена не происходит полный отказ сервиса. Клиенты смогут просто переключиться на оставшиеся DC. Администратор может затем быстро развернуть новый DC на площадке, реплицировать на него базу AD с оставшихся DC, а старый контроллер домена удалить согласно инструкции.
Однако наличие дополнительных контроллеров домена не поможет в случаях когда неисправны все контроллеры домена. Например, когда все DC инфицированы или зашифрованы (например в случае перехвата учетных данных администратора домена утилитой mimikatz), повреждений в логической структуре базы данных NTDS.DIT (которая была реплицирована на все DC), или в других катастрофических сценариях.
В общем, бэкапить AD можно и нужно. Как минимум вы должны регулярно создавать резервные копии ключевых контроллеров доменов, владельцев ролей FSMO (Flexible single-master operations). Вы можете получить список контролеров домена с ролями FSMO командой:
netdom query fsmo
Как проверить дату последнего бэкапа контроллера домена Active Directory?
Можно проверить, когда создавалась резервная копия текущего контроллера домена AD с помощью утилиты repadmin:
repadmin /showbackup
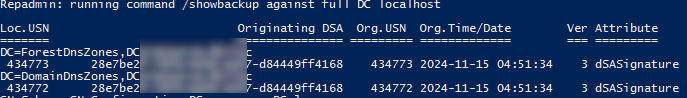
В данном примере видно, что последний раз бэкап DC и разделов AD выполнялся в 2021 году (скорее всего он не делался с момента развертывания контроллера домена).
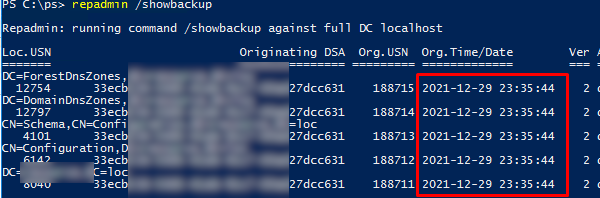
Узнать время последнего резервному копированию всех DC в домене:
repadmin /showbackup *
С помощью следующей команды можно узнать сколько раз выполнялось резервное копирование AD на конкретном DC:
(Get-ADReplicationAttributeMetadata -Object "CN=Configuration,DC=WINITPRO,DC=LOC" -Properties dSASignature -Server DC01).Version
Если ваши виртуальные контроллеры домена бэкапятся через снапшоты(см. пример с резервным копированием Hyper-V),, убедитесь что при ваша система резервного копирования обновляет в LDAP значение атрибута LastOriginatingChangeTime (содержит дату последнего резервного копирования).
Бэкап контроллера домена AD с помощью Windows Server Backup
Если у вас нет специального ПО для резервного копирования, для создания резервных копий AD можно использовать встроенный Windows Server Backup (этот компонент пришел на замену
NTBackup
).
Для резервного контроллера домена нужно создать резервную копию Состояния системы (System State). В System State бэкап попадает база Active Directory (NTDS.DIT), содержимое каталога SYSVOL с файлами групповых политик (GPO), DNS зоны, реестр, метаданные IIS, база данных службы сертификации AD CS, файлы загрузчика Windows, и другие системные файлы и ресурсы. Резервная копия создается через службу теневого копирования VSS.
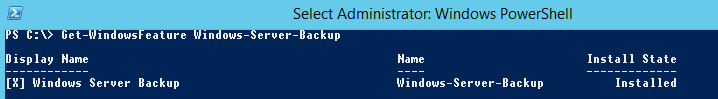
Проверьте, установлен ли компонент Windows Server Backup с помощью PowerShell командлета Get-WindowsFeature:
Get-WindowsFeature Windows-Server-Backup
Если компонент WSB отсутствует, установите его с помощью PowerShell:
Add-Windowsfeature Windows-Server-Backup –Includeallsubfeature
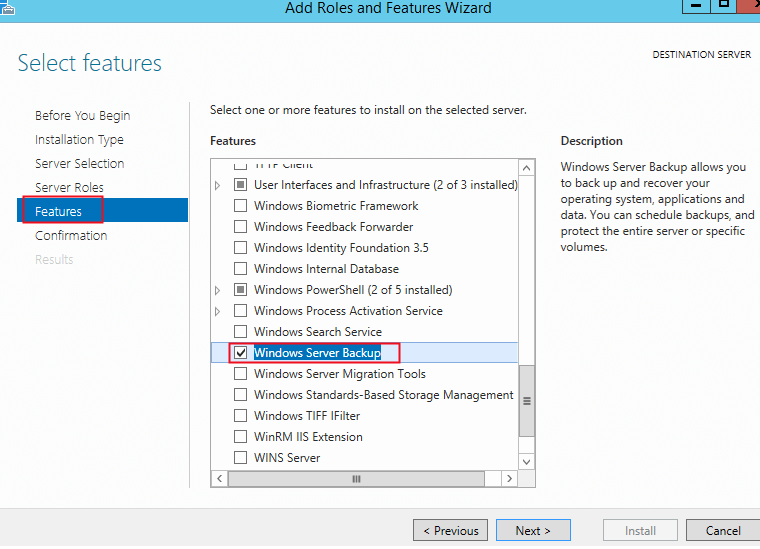
Или из Server Manager -> Features.
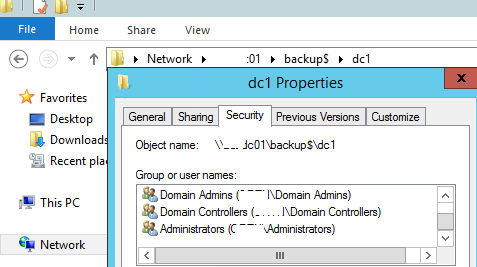
Я буду сохранять бэкап данного контроллера домена AD в сетевую папку на отдельном выделенном сервере для резервного копирования. Например, путь к каталогу будет таким
\\srvbak1\backup\dc01
. Измените NTFS разрешения на сетевой папке, чтобы права чтения-записи в каталог были только у SYSTEM, Domain Admins и Domain Controllers.
Вы можете настроить автоматическое задание резервного копирования в графической MMC оснастке Windows Server Backup (
wbadmin.msc
). Недостаток этого инструмента — новая резервная копия в каталоге WindowsImageBackup будет перезаписывать старую. Чтобы хранить копии AD от разных дат, можно автоматизировать резервное копирование с помощью консольной утилиты wbadmin.exe.
Резервное копирование Active Directory с помощью PowerShell
Для автоматизации бэкапов контроллера домена воспользуемся PowerShell скриптом. Для хранения нескольких уровней копий AD мы будем хранить каждый бэкап в отдельном каталоге с датой создания копии в качестве имени папки.
При резервном копировании в сетевую папку поддерживается только режим создания полной резервной копии. Если вы подключите диск для бэкапов как локальное устройство (например, LUN через FC или iSCSI диск), для такого устройства служба VSS будет поддерживать режим инкрементального резервного копирования.
Базовая версия PowerShell скрипта резервного копирования DC будет выглядеть так (укажите UNC путь к сетевой папке:
$path="\\srvbak1\backup\dc1\"
Import-Module ServerManager
[string]$date = get-date -f 'yyyy-MM-dd'
$TargetUNC=$path+$date
$TestTargetUNC= Test-Path -Path $TargetUNC
if (!($TestTargetUNC)){
New-Item -Path $TargetUNC -ItemType directory
}
$WBadmin_cmd = "wbadmin.exe START BACKUP -backupTarget:$TargetUNC -systemState -noverify -vssCopy -quiet"
Invoke-Expression $WBadmin_cmd
Чтобы PowerShell скрипт удалял старые резервные копии (например, старше 60 дней), можно добавить такой код:
$Period = "-60" # Количество хранимых дней.
# Вычисляем дату после которой будем удалять файлы.
$CurrentDay = Get-Date
$ChDaysDel = $CurrentDay.AddDays($Period)
# Удаление файлов, дата создания которых больше заданного количества дней
GCI -Path $TargetUNC -Recurse | Where-Object {$_.CreationTime -LT $ChDaysDel} | RI -Recurse -Force
# Удаление пустых папок
GCI -Path $TargetUNC -Recurse | Where-Object {$_.PSIsContainer -and @(Get-ChildItem -Path $_.Fullname -Recurse | Where { -not $_.PSIsContainer }).Count -eq 0 } | RI -Recurse
При резервном копировании на локально подключенный диск, можно вместо такого скрипта можно корректно удалять старые копии с помощью команды:
$KeepVersion=10
$WBadmin_cmd = " wbadmin delete backup -keepVersions:$KeepVersion -quiet"
Invoke-Expression $WBadmin_cmd
В этом случае wbadmin будет хранить только последние 10 резервных копий. Более старые будут удалены.
Запустите данный скрипт. Должна появится консоль wbadmin с информацией о процессе создании теневой копии диска:
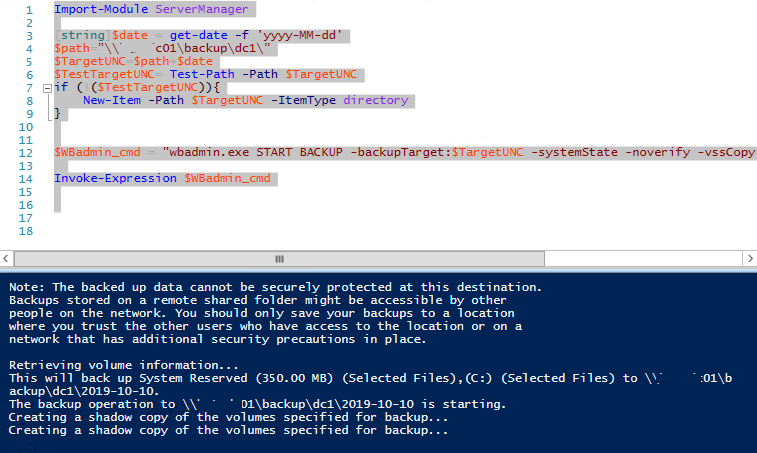
Если бэкап выполнен успешно, в логе появятся сообщения:
The backup operation successfully completed. The backup of volume (C:) completed successfully. The backup of the system state successfully completed [11/15/24 12:51 PM].
Лог бэкапа хранится в каталоге
C:\Windows\Logs\WindowsServerBackup\
.
Теперь проверьте, что дата даты последнего бэкапа DC обновлена:
repadmin /showbackup
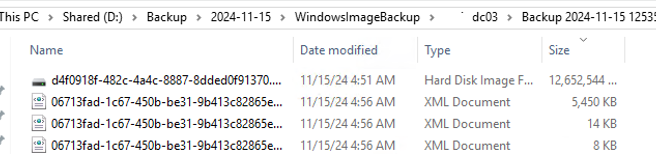
Размер каталога с резервной копией контроллера домена в сетевой папке в этом примере около 12 Гб. На выходе вы получили VHDX файл, который можно использовать для восстановления ОС через WSB, или вы можете вручную смонтировать VHDX файл и извлечь из него нужные файлы или папки.
Если на площадке имеется несколько DC, то не обязательно бэкапить их все. Для экономии места достаточно периодически бэкапить только файл базы данных AD (ntds.dit). Для этого используйте следующие команды:
$WBadmin_cmd = "wbadmin start backup -backuptarget:$path -include:C:\Windows\NTDS\ntds.dit -quiet"
Invoke-Expression $WBadmin_cmd
Размер такого бэкапа будет составлять всего 50-500 Мб в зависимости от размера базы AD.
Для автоматического выполнения бэкапа по расписанию, создайте на DC создать скрипт
c:\ps\backup_ad.ps1
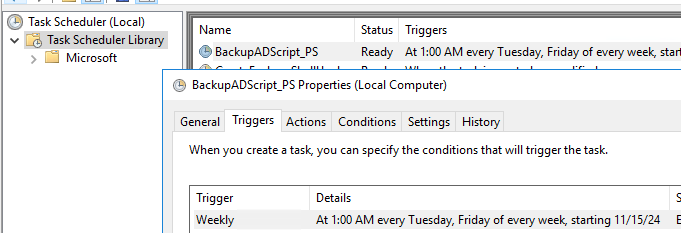
. Этот скрипт нужно запускать по расписанию через Task Scheduler. Можно создать задание планировщика из графического интерфейса или из PowerShell. Главное требование — задание должно запускать от имени SYSTEM с включенной опцией Run with highest privileges. Для бэкапа контролера домена AD три раза в неделю создайте следующее задание:
$trigger = New-ScheduledTaskTrigger -Weekly -DaysOfWeek Tuesday,Friday -At "01:00AM"
$User= "NT AUTHORITY\SYSTEM"
$Action= New-ScheduledTaskAction -Execute "PowerShell.exe" -Argument "c:\ps\backup_ad.ps1"
Register-ScheduledTask -TaskName "BackupADScript_PS" -Trigger $Trigger -User $User -Action $Action -RunLevel Highest –Force
Итак, мы настроили резервное копирование на контроллере домена AD, а в следующей статье мы поговорим о способах восстановления Active Directory из имеющейся резервной копии.
В этой статье мы посмотрим, как создать резервную копию контроллера домена Active Directory на базе Windows Server 2019. Такая резервная копия DC позволит вам восстановить как отдельные объекты AD, так и домен целиком при возникновении проблем.
Несмотря на то, что сервисы Active Directory разработаны с учетом избыточности, администратору AD нужно разработать и внедрить четкую политику резервного копирования Active Directory.
Как минимум, необходимо создавать резервную копию DC с ролями FSMO и по одному DC на каждой площадке (филиале). Конкретные рекомендации по стратегии резервного копирования сильно зависят от архитектуры вашего домена и структуры сети.
В Windows Server 2019 есть встроенный компонент Windows Server Backup, позволяющий создать резервную копию AD.
Запустите Server Manager на контроллере домена Windows Server и выберите Add Roles and Features. Затем нажмите Next несколько раз и выберите для установки компонент Windows Server Backup.
Также вы можете установить компонент WSB в Windows Server с помощью команды PowerShell:
Install-WindowsFeature -Name Windows-Server-Backup -IncludeAllSubfeature –IncludeManagementTools
Дождитесь окончания установки Windows Server Backup и нажмите Close.
Теперь в Server Manager выберите Tools -> Windows Server Backup.
В левой панели выберите Local Backup, вызовите контекстное меню и выберите Backup Schedule.
В настройках резервного копирования выберите Custom.
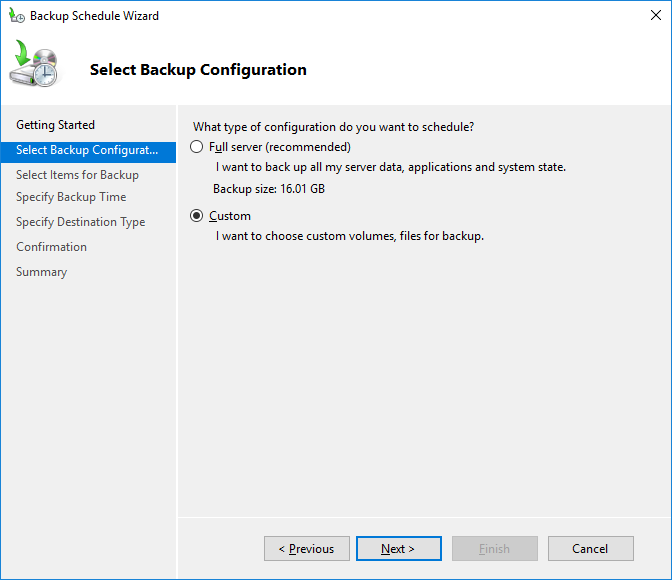
Для полного резевного копирования контоллера домена Active Directory нужно выбрать режим бэкапа System State. Такого образа вполне достаточно для восстановления контроллера домена Active Directory.
System State включает в себя:
- Базу Active Directory (ntds.dit)
- Каталог Sysvol (с объектами GPO)
- Встроенные DNS зоны со всеми записями
- Базу данных службы сертификации (Certificate Authority)
- Системные загрузочные файлы
- Реестр
- Базу данных службы компонентов (Component Services)
С помощью такого бэкапа вы сможете развернуть службы AD на том же самом сервере (не поддерживается восстановление ОС из system state backup на другом сервере). Если вы планируете восстанавливать контроллер домена на другом сервер, нужно выбрать опцию Bare metal recovery.
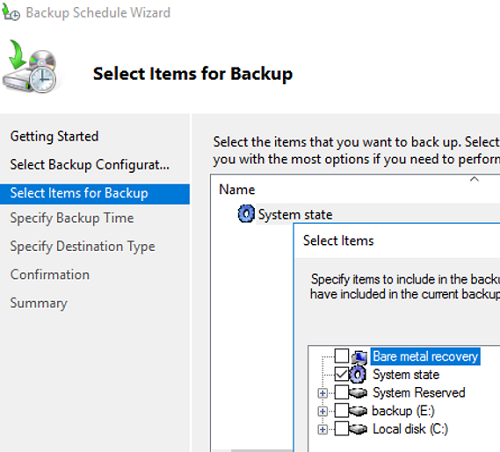
Задайте расписание резервного копирования. Например, я хочу создавать резервную копию AD ежедневно в 12:00.
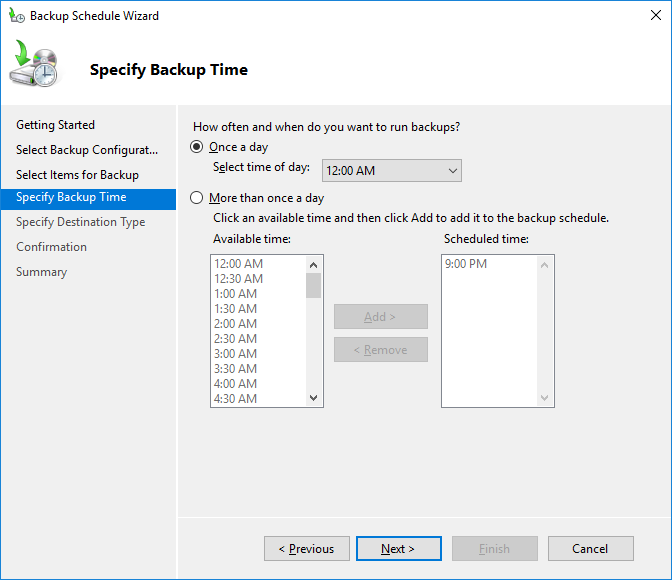
Вы можете складывать резервные копии контроллера домена на отдельный физический диск или в сетевую папку на другом сервере или NAS устройстве. Я использую выделенный диск (выберите его в качества устройства для хранения резервных копий).
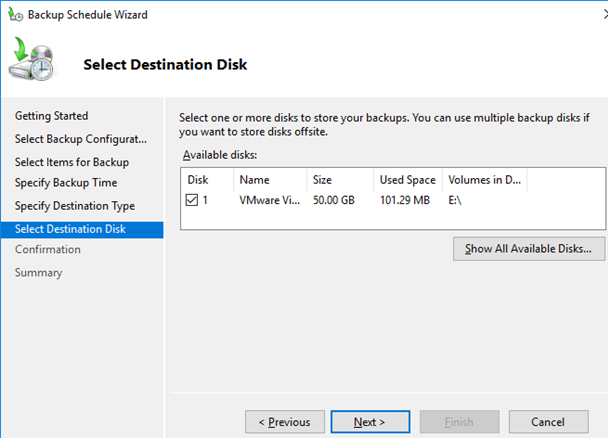
Нажмите Finish чтобы создать новое задание резервного копирования.
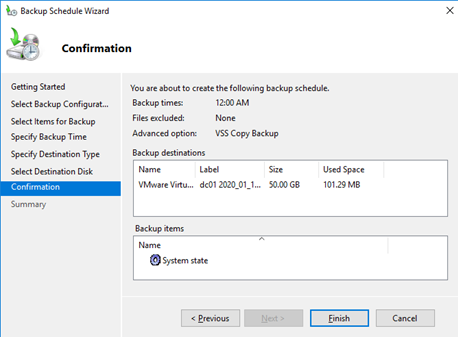
Вы можете найти созданное задание резервного копирования в Task Scheduler. Запустите taskschd.msc, перейдите в раздел Task Scheduler Library -> Microsoft -> Windows -> Backup и найдите задание Microsoft-Windows-WindowsBackup. Данное задание запускается от имени системы (аккаунта NT Authority\SYSTEM). Если вы хотите создать резервную копию DC немедленно, в настройках задания на вкладке Settings включите опцию “Allow task to be run on demand”. Сохраните изменения, щелкните ПКМ по заданию и выберите Run (или дождитесь автоматического запуска задания по расписанию).
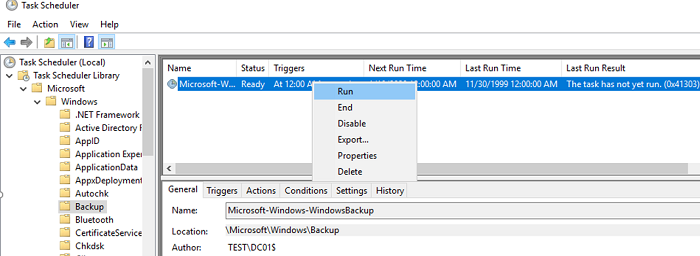
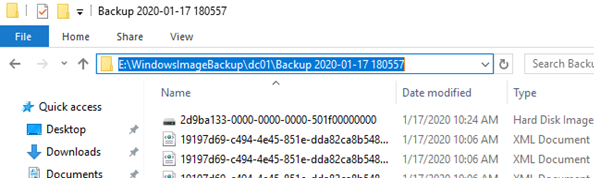
После окончания процесса резервного копирования на диске E: появится каталог с именем WindowsImageBackup. Обратите внимание на структуру каталога WindowsImageBackup. В нем содержится каталог с именем контроллера домена. В этой папке находится каталог с именем Backup и временем создания резервной копии (например, E:\WindowsImageBackup\dc01\Backup 2021-10-17 120957). Внутри этого каталога находится файл vhdx. Это виртуальных диск с образом вашего контроллера домена. Вы можете вручную подключить его через Disk Manager и получить доступ к файлам.
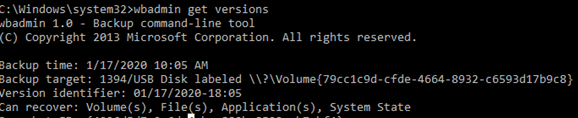
Также вы можете выполнять резервное копирование DC с помощью консольной утилиты wbadmin. Например, чтобы создать резервную копию system state сервера и сохранить ее на отдельный диск, выполните команду:
wbadmin start systemstatebackup -backuptarget:e: -quiet
В этом примере содержимое каталога WindowsImageBackup на целевом диске перезаписывается.
Список доступных резервных копий на диске можно вывести так:
wbadmin get versions
Чтобы удалить все старые резервных копии, кроме последней, выполните команду:
wbadmin delete backup -keepVersions:1
Также вы можете использовать PowerShell модуль WindowsServerBackup для создания резервной копии Active Directory на DC. Следующий PowerShell скрипт создаст резервную копию System State на указанном диске:
$WBpolicy = New-WBPolicy
Add-WBSystemState -Policy $WBpolicy
$WBtarget = New-WBBackupTarget -VolumePath "E:"
Add-WBBackupTarget -Policy $policy -Target $WBtarget
Start-WBBackup -Policy $WBpolicy
Для восстановления AD в случае аварий вам понадобится SystemState Backup в корне локального диска DC. При восстановлении AD вам нужно загрузить сервер с ролью ADDS в режиме Directory Services Restore Mode (DSRM).
Learn how to backup Active Directory with this step-by-step guide.
Table of contents:
- Active Directory Backup Best Practices
- Active Directory Full Backup VS System State Backup
- How to Install Windows Server Backup
- How to Backup Active Directory (Step by step instructions)
- Automate Backup Monitoring (Email Alerts)
Let’s dive right in.
Why it is Important to backup Active Directory
In networks that use Active Directory, it is a critical service that must be running 24/7.
If these servers crash then your business operations can be disrupted or stopped altogether. Users won’t be able to access applications, their data, and files that can make a business run. In a hybrid environment, a failed Active Directory server can even disrupt cloud services.
I have supported companies that had a failed domain controller and it affected almost everything. Employees could not access their files, applications, and even internet access was down. The worst part is they had no backups, so they had to rebuild their domain environment. It took several weeks to fully recover. It was a lot of extra work that could have been avoided if they had backups.
With the ongoing security threats, it’s a real possibility you could be hit with a virus or ransomware. With ransomware, the best protection is to ensure you have backups.
I highly recommend you backup Active Directory and that you start by reading my best practices below.
Active Directory Backup Best Practices
Tip: This first section is very important and could save you from having to restore Active Directory from a backup.
- Restoring Active Directory from a backup should be your last option for recovery.
- You should have multiple domain controllers. This will allow for a single domain controller to fail and still provide full recovery without a backup.
- To expand on the above, DO NOT rely on multiple controllers as your only source of recovery. You should absolutely still be doing a backup of Active directory. All domain controllers can fail, database corruption can occur, viruses, ransomware or some other disaster could wipe out all domain controllers. In this situation, you would need to restore it from a backup. Also backing up Active Directory is FREE so there is no reason not to do it.
- You should enable the Active Directory Recycle Bin, this will give you the ability to restore deleted objects without the need for a backup.
- Document your Active Directory environment, backup policy, and disaster recovery plans.
- Backup Active Directory at least daily, if you have a large environment with lots of changes then consider twice a day backups.
- Ensure you have an offsite backup of Active Directory. This will be explained more throughout this guide.
- Backup two domain controllers in each domain, one of those should hold the Operation master role.
Active Directory Full Backup VS System State Backup
This section will help you understand the difference between doing a full server backup and a system state backup.
Full Backup
- Backs up all server data, including applications and the operating system
- Includes the system state
- Allows for bare metal recovery – This allows for restoring to an entirely different piece of hardware. Although, it is recommended that the hardware receiving the restore have the same hardware configuration.
- If you have lots of data or 3rd party applications installed on your domain controller (not recommended) your backups will be considerably larger.
- The full backup option is best used for restoring the whole server to the same or different server. A full restore will allow you to easily re-install the operating system and use the backup to recover.
System State Backups
The system state backup includes only the components needed to restore Active Directory. The system state includes the following:
- Sysvol from the domain controller – The sysvol includes group policy objects but I still recommend you backup group policy from the GPMC.
- Active Directory database and related files
- DNS zones and records (only for Active Directory integrated DNS)
- System registry
- Com+ Class registration database
- System startup files
- The system state backup is best used for recovering Active Directory only on the same server. It cannot be used to recover a corrupt server operating system. Microsoft does not support restoring a system state backup from one computer to a second computer of a different make, model, or hardware configuration
Install Windows Server Backup
To create an Active Directory backup the Windows server backup utility needs to be installed. This utility gets a bad wrap, mostly because it is used incorrectly. It is not a solution for backing up your entire enterprise but works great for specific use cases like backing up Active Directory.
I’ve been using it for years to backup Active Directory and it works great. There are a few things to be aware of when using this utility and I’ll point those out throughout this guide.
Step 1: Open Server Manager
Step 2: Add Roles and Features
Now click on “add roles and features”
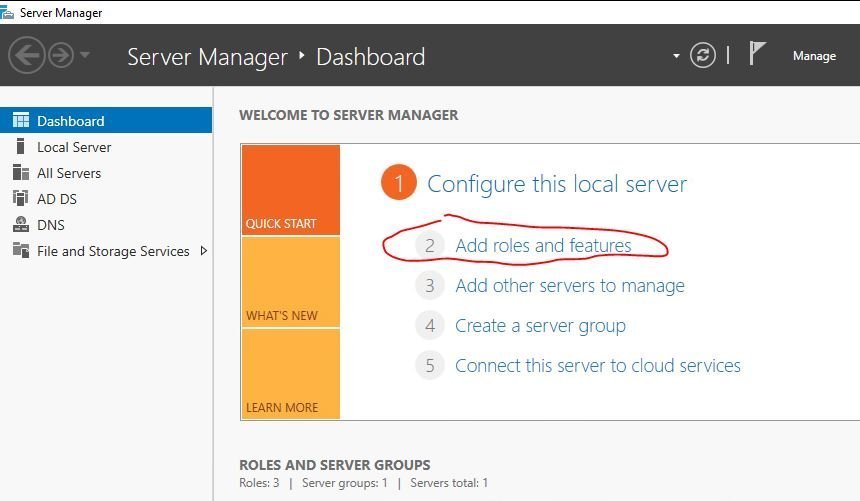
Step 3: Select Windows Server Backup
Now just click next a few times to get to the select features page. Select “Windows Server Backup” and click next.
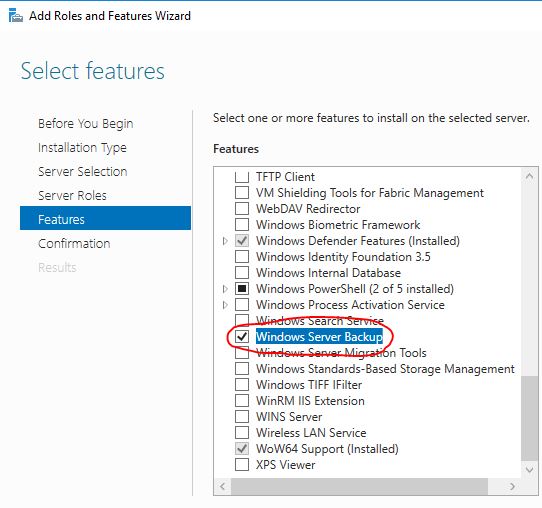
On the next screen click install. When the install is complete click close.
That completes installing the Windows server backup utility.
The next step is to configure the backup.
How to Backup Active Directory (Full Server Backup)
I prefer to use the full backup option instead of the system state backup. This option allows you to easily restore if the operating system or Active Directory becomes corrupt.
It includes the system state so you can choose to restore the entire server or just the system state.
The steps for backing up just the system state are the same you will just choose custom instead of full server.
Here are the settings that will be configured for this backup:
- Daily Backup
- 1 full backup then 14 incremental backups – Windows server backup automatically handles the full and incremental backups no additional configuration is needed.
- The backup destination will be a volume mounted as a local disk. I’m using a SAN with replication to another datacenter for disaster recovery.
- My domain controllers are virtual running in a VMWare environment.
- The domain controller is Windows Server 2016
Step 1: Create a dedicated disk for backups.
Important: When doing a full backup the disk cannot be larger than the one you are restoring to. So if the server you are backing up has a disk size of 50GB, the backup disk cannot be larger than this. The Windows backups are very efficient, the first backup is full then it will do incremental backups. I like to make the backup disk slightly smaller than the disk I’ll be backing up.
Step 2: Configure Windows Server Backup
Open the Windows Server Backup Utility
Click on “Backup Schedule” on the right-hand side
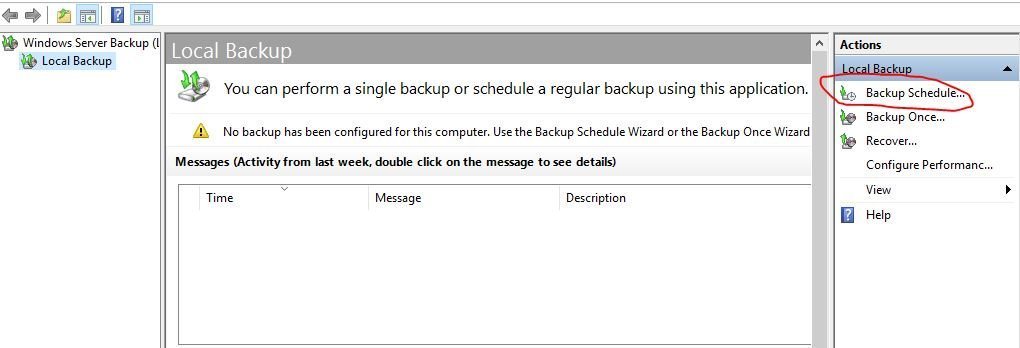
Click next on the Getting started page
Select “Full Server” and click next.
If you want to backup just the system state select “Custom”.
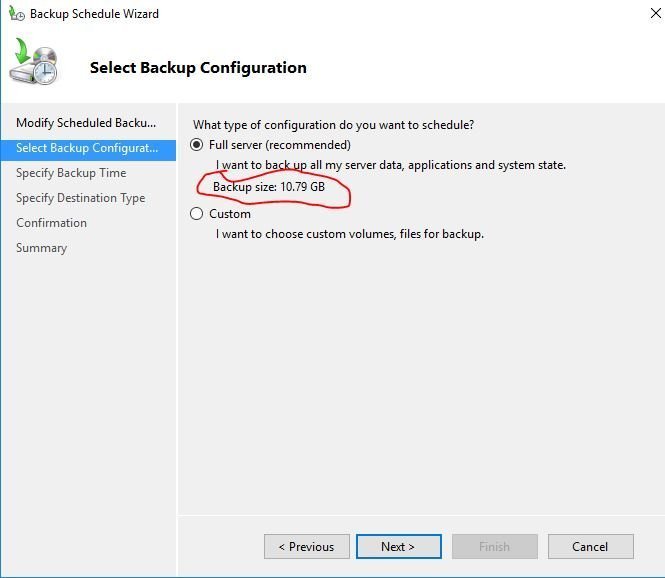
In the above screenshot, the backup configuration will tell you how large the backup size will be. Unless you have 3rd party programs and files on your domain controller the backup should be fairly small. After the first backup, it will do an incremental and only backup the changes.
Click the “Advanced settings” button
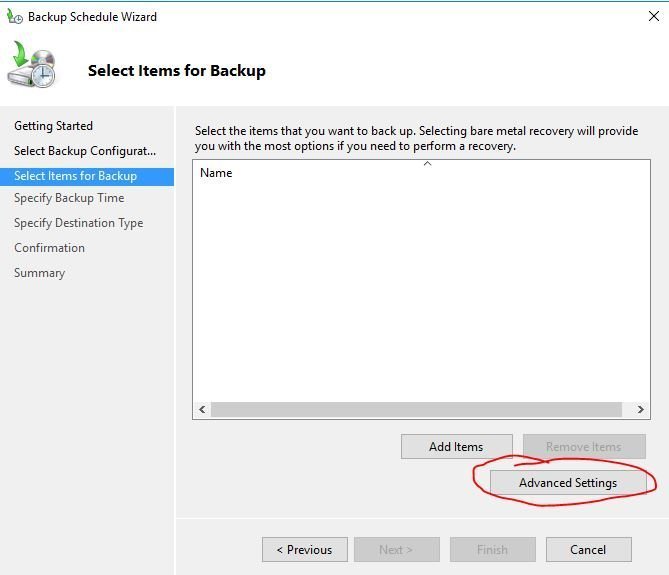
Click “VSS Settings” then select “VSS full backup”. Click OK
This is recommended if you are not using any other backup product to backup Active Directory.
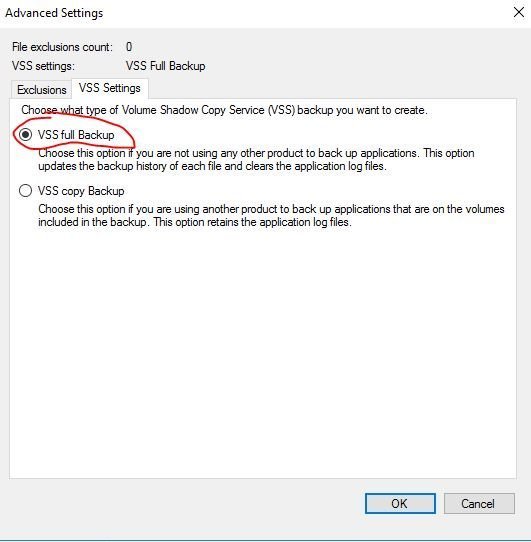
Configure the backup schedule that works best for you. In my environment, I configured a daily backup at 7:00 PM.
If you have a large environment with lots of AD changes you should consider twice a day backups.
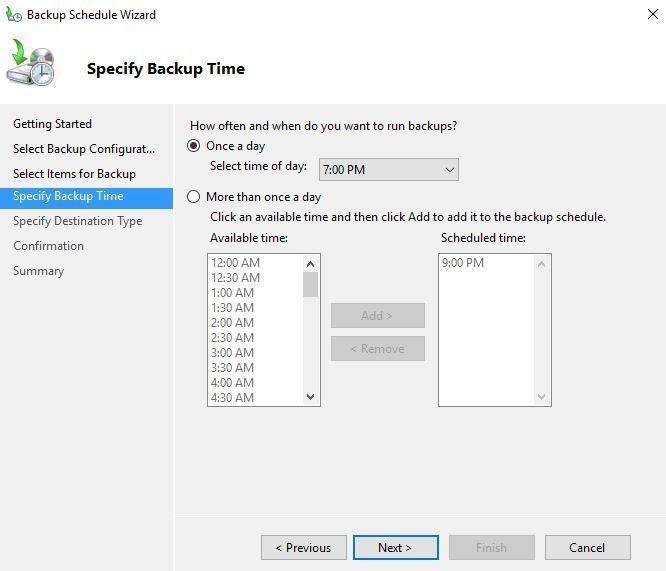
On the specify destination type screen choose “Back up to a hard disk that is dedicated for backups”.
DO NOT choose “Back up to a shared network folder” This option does not support incremental backups it will overwrite the backup each time.
Confirm backup settings and click finish.
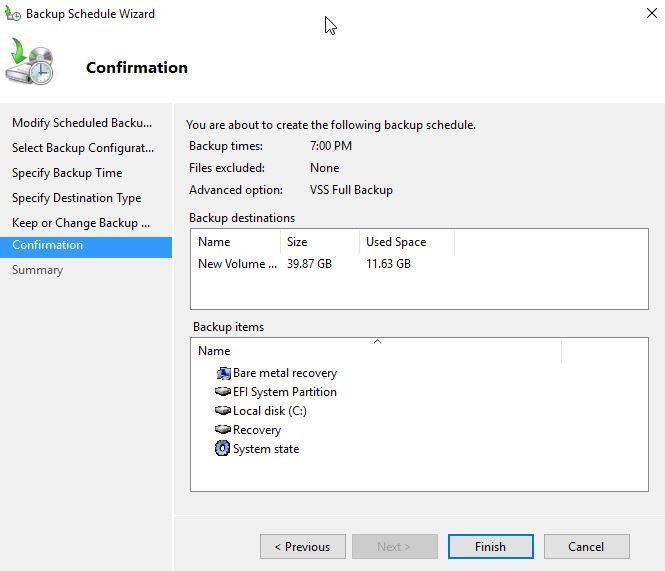
The backup configuration is complete but we need to change a few settings in the scheduled task that was created.
Task Scheduler Settings
Just type in “Task Scheduler” in the search bar and click the app.
Browse to Task Scheduler Library -> Microsoft -> Windows -> Backup
You will see the windows backup scheduled task.
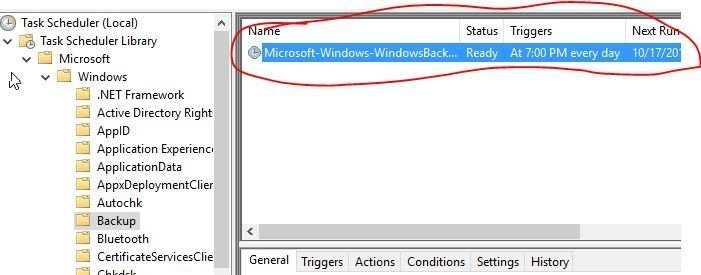
Double click on the task name to open it up.
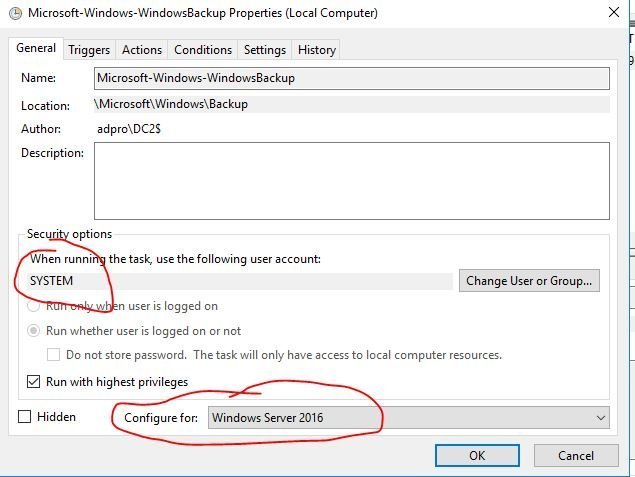
On the General screen, ensure the task is running as the SYSTEM account and change the configure for to the correct operating system. I’m running 2016 so that is what I have selected.
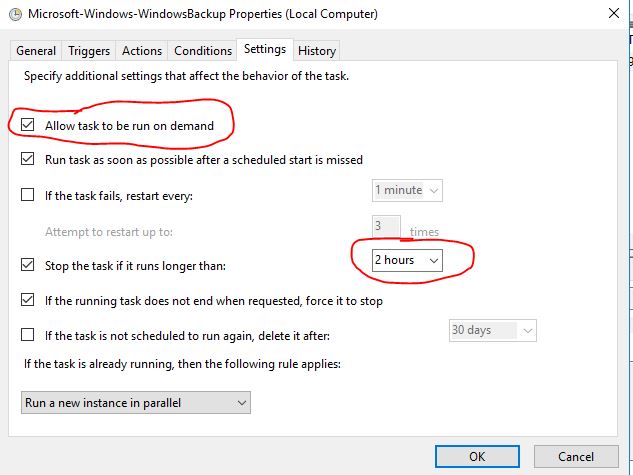
On the settings screen change the task to stop running if it runs longer than 2 hours. Also, check the box to allow the task to be run on demand.
Click OK. That completes the changes for the scheduled task.
If you want you could right click the task and run it. The backup process may cause a bit of CPU usage so you may need to wait.
The first backup will be a full backup. The next 14 backups will be incremental then it will do another full backup.
You can check the status of backups, disk space used, and much more in the backup utility.
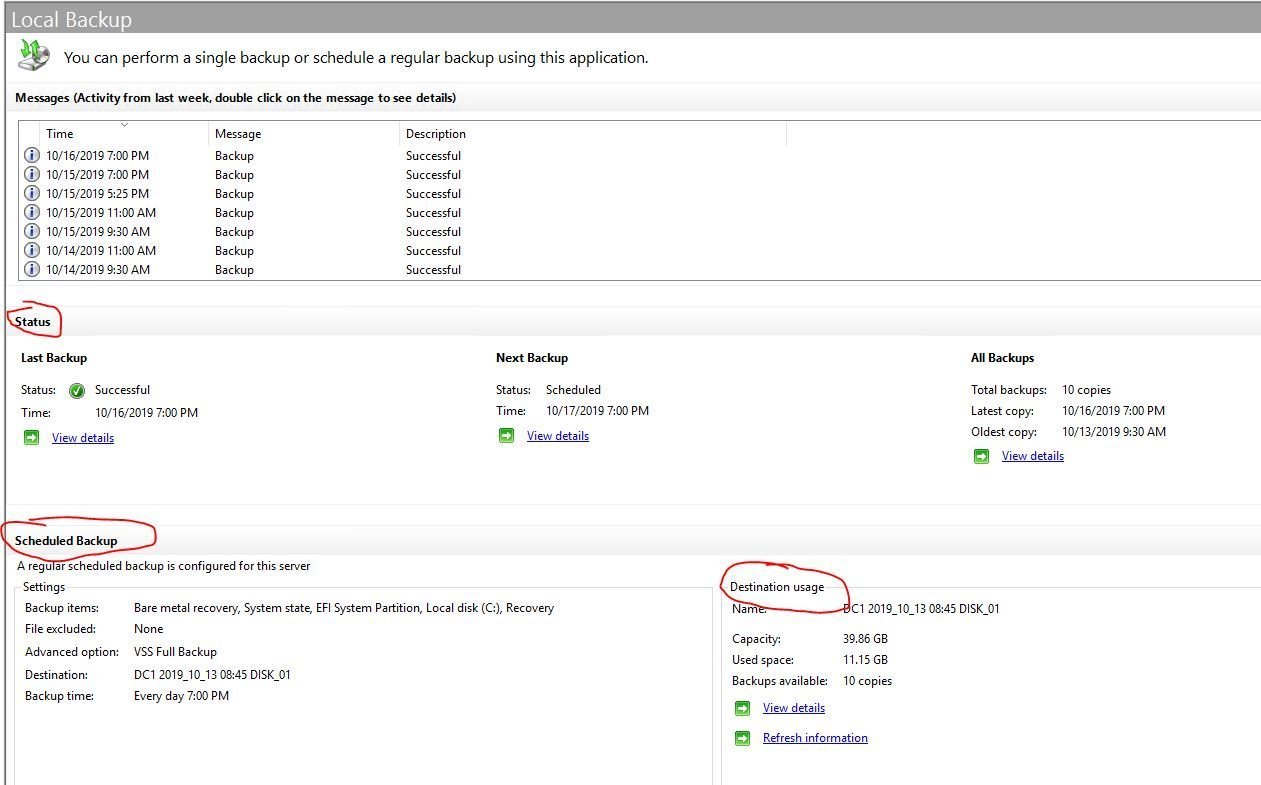
The backup configuration is complete, Active Directory will now backup on a daily basis (or whatever schedule you configured it for).
In the next section, I will show you how to easily monitor the backups.
Automate AD Backup Monitoring (Email Alerts)
In this section, I’ll show you how to get email notifications when the backup completes. This is a tested solution that I found from Microsoft and that I use in production.
To automate monitoring of the backups you will configure a scheduled task to trigger an action when event ID 4 has been logged.
Step 1: Setup PowerShell Script
The scheduled task will trigger a PowerShell script when event ID 4 is logged. The script will send an email message.
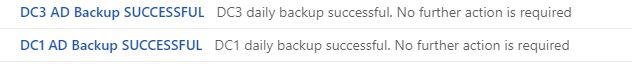
Copy the script below and paste it into a text file. Save it as AD-Backup-Success.ps1
You need to change the from address, to address and the SMTP address.
$From = "dc1@yourdomain.com" $To = "rallen@ad.activedirectorypro.com" $Subject = "DC1 AD Backup SUCCESSFUL" $Body = "DC1 daily backup successful. No further action is required" $SMTPServer = "SMTP address" $SMTPPort = "25" Send-MailMessage -From $From -to $To -Subject $Subject -Body $Body -SmtpServer $SMTPServer -port $SMTPPort
Step 2: Setup Scheduled Task
Open the scheduled task app, in the task scheduler library create a new task.
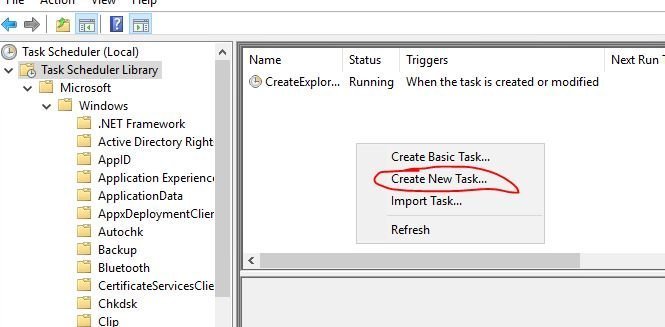
On the general screen set the following
- Name: AD Backup Success Notification
- Use the following account: SYSTEM
- Set to “Run whether user is logged on or not”
- Run with highest privileges
- Configure for: Choose your operating system
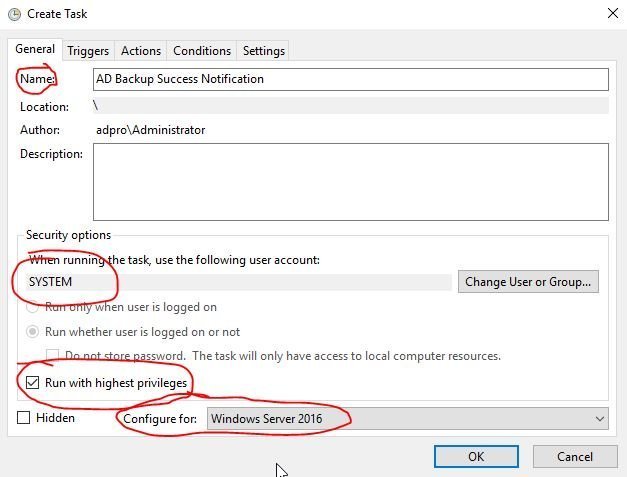
On the Triggers screen click on new and set the following:
- Begin the task: On an event
- Log: Microsoft-Windows-Backup/Operational
- Source: Backup
- Event ID: 4
On the Actions screen click new and configure the following:
- Action: Start a program
- Program/script: C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe
- Add arguments: Path to the script from step 1. Example c:\it\AD-Backup-sucess.ps1
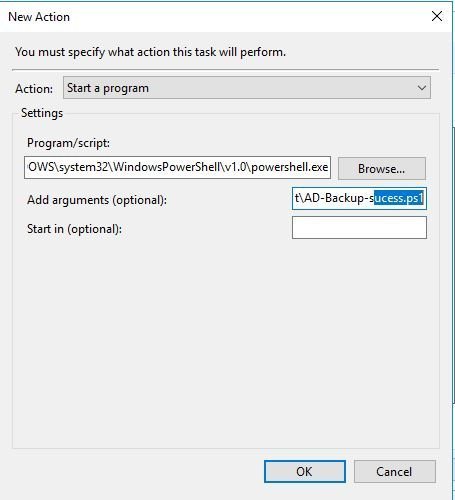
Click ok and the task setup is complete.
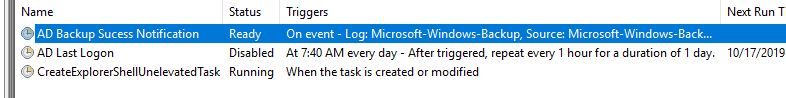
Now when the backup completes you will receive an email notification.
Summary
Active Directory is one of the most critical components in a Windows environment. It seems like everything is dependent on Active Directory or DNS and if it crashes nothing works right or at all. I’ve worked with customers that had a complete domain controller crash (all of them) and literally everything was down. Fortunately, they had backups and were able to recover the domain controllers.
With all the ransomware going around and constant threats you never know what can happen so don’t rely on multiple domain controllers as your only method for AD Backups. You definitely should have multiple domain controllers but in addition, ensure you are running backups as well. Why would you not? I just showed you a way to back them up for FREE.
Next, check out my guide on how to restore Active Directory from backup.
Resources
- Automate System State backup – Microsoft documentation
- Windows Server Backup Feature Overview
Microsoft Active Directory (AD) is the primary authentication service used by a majority of organizations worldwide (roughly 90 percent). It stores critical business information on domain controllers (DCs) like user accounts, their permissions, the number of computers in your organization’s network, etc. In other words, it’s critical infrastructure. However, many businesses still don’t understand just how important it is to back up Active Directory. If an outage were to occur, your organization would lose an estimated $100,000 per day, according to the latest research findings. While those numbers are scary, they likely represent the impact of only the most severe Active Directory recovery scenarios. Still, these figures should be reason enough for your business to take AD backup seriously.
This guide will explore the ins and outs of how to back up Active Directory Domain Controller (AD DC). Learn about the best practices, tools and methods, and how to perform different types of backups.
Why is Active Directory Backup Important?
There are several factors that can lead to Active Directory DC becoming unavailable, which includes cyber attacks, human error, natural disasters, and power outages. AD outages caused by one or a combination of these factors can have several effects on your business. Apart from the immediate financial losses we mentioned initially, your business may also experience:
- Data Losses: Without efficient Active Directory backups, your business risks losing important AD data, such as user account information, permissions, and configurations. Without these pieces of information, important business processes may be severely affected.
- Reputational Damage: Delayed recovery efforts due to a lack of AD backups may end up affecting your organization’s reputation, especially if the outage affects critical business functions and services that customers need.
- Loss of Employee Productivity: If employees can’t access the resources they need to do their work, their productivity may decrease while waiting for the restoration of your organization’s network.
Active Directory backups can help prevent all of the above by creating a copy of all the data stored in the AD that you can retrieve in case of an outage. These backups should be part of the larger recovery strategy that ensures Active Directory downtimes don’t last too long or severely affect your operations.
Tools and Methods for Active Directory Backup
Below are the steps involved in conducting a Windows Server Backup.
Full Server Backup
A full server backup, commonly referred to as a full backup, aims to restore “everything.” It creates a copy of all the volumes or partitions on the server, including all the applications and operating systems, as well as the system state.
This AD backup allows for bare metal recovery (BMR), which allows you to transfer all the recovered data from a full server backup onto a new physical server or virtual machine (VM).
To perform a full AD backup, you can use two methods:
Method 1: Using Windows Server Backup GUI
1. Log in to the server with the appropriate administrative privileges.
2. On the Windows Start menu, search for the backup utility by typing “Windows Server Backup” and click on it to launch it.
3. On the left pane of the Windows Server Backup console, you’ll see two options: “Backup Once” and “Backup Schedule.” Since we’re performing a one-time backup, select “Backup Once.”
4. Choose the “Different options” radio button and click Next.
5. You’ll then have two options; “Full server (recommended)” and “Custom.” Select the “Full server (recommended)” button, then click Next.
6. Specify your backup destination by choosing between “Local drives” or “Remote shared folder.” For simplicity, let’s choose “Local drives” for this guide. Click Next.
7. On the Confirmation Screen, ensure everything is as you want, then click “Backup” to start the backup process.
Method 2: Using Windows Server Backup Command-line Tool (wbadmin.exe)
1. Launch the Command Prompt with administrative privileges.
2. Type the following command to perform a full server backup:
wbadmin start backup -backuptarget:\<Drive_letter_to_store_backup\>: -include:\<Drive_letter_to_include\>:
3. Press Enter to execute the command.
Importance of a Full Server Backup
In the event of a catastrophic failure such as hardware malfunction, cyberattack, or natural disaster, a full server backup ensures that no matter what happens, a business has a fallback option that can restore its operations to the last backup point, minimizing the impact of data loss. Full server backups capture the entire system, including operating system files, applications, and data. This comprehensive snapshot ensures data integrity by preserving the relationships between files and their dependencies.
Backing up All Volumes/Partitions on a Server
By backing up all volumes or partitions, you ensure that all data, including system files, applications, and user data, is included in the backup. Having backups of all volumes or partitions simplifies the recovery process. Instead of restoring individual files or directories, you can restore entire volumes or partitions, reducing the time and effort required to recover from a backup.
Bare Metal Recovery Capabilities
Bare metal recovery is a backup type for restoring a server to a functional state after a catastrophic failure or when setting up a new server. BMR allows you to restore an entire server, including the operating system, system settings, applications, and data, from scratch. This is crucial in the event of hardware failure, corruption, or other disasters that render the server inoperable. BMR can significantly reduce the time required to recover a server compared to reinstalling the operating system and applications manually.
Restoring AD to a New Physical Server or Virtual Machine
Restoring Active Directory to a new physical server or virtual machine involves careful planning and execution to ensure a smooth transition without data loss or service interruptions. Below are the steps and best practices to restore AD to a new physical server or virtual machine.
- Evaluate the hardware or virtualization platform for the new server/VM to ensure it meets the requirements for running AD.
- Install the operating system (Windows Server) on the new server/VM, ensuring it is compatible with the version of AD you are restoring.
- Restore the AD to the new server/VM using most recent backup either using Windows server backup tool or third-party backup software.
- Once the new server/VM is operational and running AD, ensure that it replicates and synchronizes properly with the existing domain controllers.
- If the new server/VM is intended to replace an existing domain controller holding FSMO roles, transfer the FSMO roles (Schema Master, Domain Naming Master, RID Master, PDC Emulator, and Infrastructure Master) to the new server/VM.
- Use the “ntdsutil” or PowerShell commands to transfer the FSMO roles to the new server/VM.
- Perform thorough testing to ensure that AD functionality is restored and that users can authenticate, access resources, and perform domain-related tasks without any issues.
- Verify that Group Policies, DNS settings, and other AD-dependent configurations are functioning correctly.
- Document the steps taken during the restoration process for future reference and auditing purposes.
System State Backup
A system state backup creates a copy of just the essential components required to restore the Active Directory to a functional state. These components may include Active Directory database (NTDS), SYSVOL directory, system registry, boot files, performance monitor configuration files, etc. As such, a system state backup is very important for AD disaster recovery.
You can perform a system state backup in two ways:
Method 1: Using Windows Server Backup GUI
1. First, log in to the server with the appropriate administrative privileges.
2. On the Windows Start menu, search for the backup utility by typing “Windows Server Backup” and click on it to launch it.
3. On the left pane of the Windows Server Backup console, you’ll see two options: “Backup Once” and “Backup Schedule.” Since we’re performing a one-time backup, select “Backup Once.”
4. Choose the “Different options” radio button and click Next.
5. In the “Backup Once” page, select the “Custom” option, then click Next.
6. Under “Select Items for Backup,” click “Add Items,” then check the box next to “System State.” Click “OK.”
7. If using Windows Server 2008 R2 or Windows Server 2008, select the volumes to include in the backup. Optionally, enable system recovery to include critical volumes.
8. On the “Specify Destination Type” page, select either “Local drives” or “Remote shared folder,” then click Next. If backing up to a remote shared folder, enter the path, select access control preferences, and provide user credentials for write access.
9. For Windows Server 2008 and Server 2008 R2, choose “VSS copy backup” on the “Specify Advanced Options” page. Click “Next.”
10. Select the desired backup location on the “Select Backup Destination” screen.
11. Review the backup settings and click “Back up” to confirm and start the backup process.
Method 2: Using Windows Server Backup Command-line Tool (wbadmin.exe)
1. Launch the Command Prompt with administrative privileges by searching for “Command Prompt” in the Start menu, right-clicking it, and selecting “Run as administrator.”
2. Type the following command to initiate the system state backup, then press “Enter.”
wbadmin start systemstatebackup -backuptarget:<TargetDrive>
Replace <TargetDrive> with the destination where you want to store the backup.
Understanding System State Backup
System State Backup ensures that important system configurations, files, and databases are backed up and can be restored in case of system failure, corruption, or other issues. The Active Directory database is the most crucial component of System State backup, which contains information about the entire domain structure, including user and group policies, domain trusts, and security settings. System files, including critical operating system files, boot files, and files required for system startup and operation, are also included in a System State Backup.
Components Included in System State Backup
A System State Backup includes critical components necessary for system recovery. These components may vary slightly depending on the version of Windows Server, but they are typically the same. These components collectively ensure that critical system configurations, databases, and files are backed up.
- Active Directory Database (NTDS). This component contains the Active Directory database, which stores information about users, groups, computers, and other objects in the domain.
- System Registry. The Windows Registry stores system and application settings. System State Backup includes a snapshot of the registry, allowing for the restoration of registry settings to a previous state if necessary.
- System Files. Critical system files, including those required for system startup and operation, are included in the System State Backup. These files ensure the proper functioning of the operating system and applications.
- COM+ Class Registration Database. This component contains information about Component Object Model (COM) components and their configuration. COM+ provides a framework for building and deploying distributed applications on Windows platforms.
- Boot Files. System State Backup includes boot files required for system startup, such as the Boot Configuration Data (BCD) store, boot manager files, and other boot-related components.
- Certificate Services Database. If Certificate Services (PKI) is installed, the Certificate Services database is included. This database stores information about issued certificates, certificate revocation lists (CRLs), and other PKI-related data.
- SYSVOL Directory. SYSVOL is a shared directory which stores the server copy of the domain’s public files. It includes Group Policy settings, scripts, and other essential components for domain controllers.
- Cluster Service. In clustered environments, the System State Backup includes components related to the Cluster service, which manages high-availability clusters.
- Internet Information Services Metabase. If Internet Information Services (IIS) is installed, the IIS Metabase is included in the System State Backup. The Metabase stores configuration settings for IIS websites and applications.
- Active Directory Certificate Services. If Active Directory Certificate Services (AD CS) is installed, its database is included. This database stores information about issued certificates and other PKI-related data.
Importance of System State Backup for AD Disaster Recovery
A System State Backup includes critical components of your operating system, the AD database, and ensures that the directory structure and data integrity are preserved during recovery. In the event of a domain controller failure, System State Backup allows you to restore the entire server, including AD, to a previously known good state. System State Backup also serves as a critical component of disaster mitigation strategies, providing a reliable mechanism for restoring the AD database to a consistent and healthy state in the event of database corruption such as hardware failures, software bugs, or improper shutdowns.
Third-Party Backup Solutions
Third-party backup solutions offer additional features and flexibility compared to native backup tools and centralized management consoles, allowing IT administrators to manage backup policies, schedules, and recovery operations across multiple servers and endpoints from a single interface. They often incorporate advanced backup techniques such as incremental backups, differential backups, and block-level backups, and typically offer granular recovery options, allowing administrators to restore individual files, folders, applications, and AD objects, such as user accounts, groups, organizational units (OUs), and Group Policy objects (GPOs), or even specific database records without having to perform a full server restore.
Below are some third-party Active Directory backup solutions, each offering unique features and capabilities to meet organizations’ diverse needs.
- Netwrix Recovery for Active Directory
- Veeam Backup & Replication
- Quest Rapid Recovery
- Acronis Backup
- NetBackup by Veritas
- Backup Exec by Veritas
- Dell (formerly Quest) Active Directory Recovery Manager
- Adaxes
Automation of Active Directory Backups
It’s important to automate AD backups as much as possible, as this ensures critical directory data is protected against data loss or corruption. Automated backups require selecting a backup solution that supports automation and setting up a backup schedule within the backup solution to automatically perform AD backups at regular intervals, e.g., daily, weekly, or at other intervals.
Active Directory Backup Best Practices
Even after you back up Active Directory, there are several things you can do to ensure that the restoration process goes smoothly. Some Active Directory backup best practices include:
- Schedule regular backups of Active Directory to ensure that you have up-to-date copies of directory data.
- Configure backup schedules to perform backups at times when AD activity is low to minimize disruptions and ensure consistent backups.
- Perform full server backups or system state backups of domain controllers, as they include critical AD components such as the AD database (NTDS.dit), system registry, SYSVOL directory, and other essential system files.
- Maintain multiple backup copies at separate locations to protect against data loss due to hardware failures, disasters, or ransomware attacks.
- Regularly verify the integrity of AD backups by performing test restores and validation checks.
- Ensure that backup files are not corrupted and can be successfully restored in case of a recovery scenario.
- Store backups both onsite and offsite for redundancy and disaster recovery purposes. Securely store backup files in encrypted and access-controlled storage locations to prevent unauthorized access or tampering.
- Choose backup solutions that offer granular recovery options, allowing you to restore individual AD objects, attributes, or containers without needing to perform a full AD restore.
- Define a backup retention policy to manage backup storage efficiently and comply with regulatory requirements.
- Monitor backup jobs regularly to ensure they complete successfully, implement alerting mechanisms to notify administrators of backup failures.
- Document backup procedures, schedules, and recovery processes to ensure consistency and facilitate troubleshooting.
- Regularly test backup and recovery processes to validate their effectiveness and identify any potential issues or shortcomings.
- Leverage Microsoft Volume Shadow Copy Service, a technology which takes manual or automatic backup copies or snapshots of computer files or volumes, even when they are in use.
Microsoft Volume Shadow Copy Service (Microsoft VSS)
Microsoft Volume Shadow Copy Service is a technology in Microsoft Windows operating systems which allows taking manual or automatic backup copies or snapshots of computer files or volumes, even when they are in use. These snapshots can be used for creating consistent backups of data, allowing users to restore files to previous versions or recover from data loss situations.
VSS operates at the block level of the file system and creates a point-in-time copy, or shadow copy, of the volume on which the data resides. This copy is made while the system continues to write to the original volume. It ensures data consistency by temporarily freezing the state of the volume, capturing a snapshot, and then allowing ongoing write operations to resume. VSS is commonly used by many backup solutions to create backups of data without needing to take systems offline or interrupt ongoing operations.
The primary components of VSS include.
- VSS Service: This is a Windows service responsible for managing the shadow copy creation process. It coordinates the activities of various VSS components.
- VSS Requestor: This is an application or service that initiates the process of creating or restoring a shadow copy.
- VSS Writer: This is a component within applications or services that maintain data on the volume. Writers ensure that data is in a consistent state before a shadow copy is created.
- VSS Provider: This is a system component that interacts directly with the volume and creates the shadow copies.
Recommended Backup Strategy for Active Directory
A comprehensive backup strategy for Active Directory is important; it not only safeguards against data loss but also ensures quick recovery in case of corruption, accidental deletions, or malicious attacks. Below, we outline a recommended backup strategy tailored specifically for Active Directory environments. Below is our recommended backup strategy for Active Directory.
Understand Business Requirements for AD backup
Evaluate the organization’s AD environment to understand its complexity, size, and criticality. Identify the number of domains, domain controllers, forests, and any specialized configurations or integrations. Define clear goals and objectives for AD backup. These may include minimizing downtime, meeting regulatory requirements, and supporting disaster recovery efforts. Document detailed requirements for AD backup, including below.
- Frequency of backups (e.g., daily, weekly)
- Types of backups (e.g., full, incremental)
- Storage requirements (e.g., on-premises, cloud)
- Encryption and security measures
- Backup retention policies
- Monitoring and reporting capabilities
- Integration with existing backup infrastructure
- Disaster recovery procedures
Determine Recovery Point Objective (RPO) and Recovery Time Objective (RTO)
Consider the impact of system downtime on the business. How much revenue would be lost per hour of downtime? What are the potential costs associated with data loss? Assess the technical capabilities of your backup and recovery infrastructure. Some backup solutions may offer faster recovery times or more frequent backups than others.
Recovery Point Objective (RPO)
RPO refers to the acceptable amount of data loss in the event of a disaster or outage. Determine how frequently data needs to be backed up to meet business requirements. For example, if the RPO is one hour, it means that in the event of a failure, the organization can afford to lose up to one hour’s worth of data changes.
Recovery Time Objective (RTO)
RTO refers to the maximum acceptable downtime for a system or service in this case AD. Determine how quickly systems or services need to be restored after a failure. Factors to consider include the time it takes to detect the failure, initiate the recovery process, and restore operations. For example, if the RTO is four hours, it means that systems should be restored and operational within four hours of a failure.
Consider the cost implications of achieving specific RPOs and RTOs. More aggressive RPOs and RTOs typically require more sophisticated and expensive backup and recovery solutions. Document the agreed-upon RPOs and RTOs in your disaster recovery plan.
Backup Frequency and the 3-2-1 Backup Rule
How often you should perform backups of your data refers to the backup frequency. Consider how frequently your data changes. Data that changes frequently may require more frequent backups to minimize data loss in the event of a disaster. The RPO is the terminology that determines the maximum acceptable amount of data loss. Backup frequency should be aligned with the RPO to ensure that backups capture changes within the acceptable window. Assess your storage capacity and available resources for performing backups. More frequent backups may require additional storage space and computational resources.
The 3-2-1 backup rule is a best practice for data backup and disaster recovery. It suggests creating multiple copies of your data and storing them in different locations to ensure redundancy and protection against various failure scenarios.
3: Maintain at least three copies of your data. This includes the original data and two backup copies.
2: Store the backup copies on at least two different types of storage devices or media. For example, you might use a combination of external hard drives, network-attached storage, tape drives, or cloud storage.
1: Keep at least one backup copy in a different physical location from the primary data and other backups or offsite. This provides protection against disasters such as fires, floods, or theft that could affect all copies stored in the same location.
When determining backup frequency and implementing the 3-2-1 backup rule, it is important to regularly review and adjust your backup strategy based on changes in data volume, business needs, and technological advancements. Regular testing of backups is also important to ensure their reliability and effectiveness in restoring data when needed.
Choosing a Secure Backup Storage Solution
It’s important to do your research when selecting a backup storage solution. Below are some considerations.
- Choose backup solutions that support encryption both in transit and at rest. This ensures that your data is protected from unauthorized access, whether it’s being transferred over the network or stored on backup media.
- Implement access controls to restrict who can access and manage backups. Use strong authentication mechanisms such as multi-factor authentication (MFA) and role-based access control (RBAC) to prevent unauthorized access.
- If using on-premises storage solutions, ensure that physical access to backup servers and storage devices is restricted to authorized personnel only. Consider using locked server rooms or data centers with strict access controls.
- Choose backup solutions that offer redundancy and fault tolerance to ensure high availability of your data. Implementing redundant storage architectures such as RAID or distributed storage systems helps mitigate the risk of data loss due to hardware failures.
- Store backup copies offsite or in a different geographical location to protect against local disasters such as fires, floods, or theft. Consider using cloud-based backup solutions or rotating backup media to offsite locations regularly.
Implementing Backup Testing Procedures
Implementing backup testing procedures ensures the reliability and effectiveness of your backup and recovery strategy. These objectives may include verifying backup integrity and assessing recovery time. Consider the below points when implementing backup testing procedures.
- Create detailed test plans that outline the specific scenarios, procedures, and criteria for testing backups. Include information such as the types of backups to be tested, the frequency of testing, and the expected outcomes.
- Establish a schedule for conducting backup tests regularly. Consider testing both incremental and full backups. Test various recovery scenarios, including full system restores, individual file restores, and application-specific restores.
- Evaluate whether the recovery time objectives are met and identify any bottlenecks or inefficiencies in the recovery process.
- Test the backup scheduling, notification mechanisms, and error handling procedures.
- Document the results of backup tests, including any issues encountered, deviations from expected outcomes, and areas for improvement.
- Ensure that backup testing procedures remain aligned with organizational goals and industry best practices.
- Monitor backup performance metrics, such as backup success rates and recovery times, to identify trends and potential issues proactively.
How Netwrix Can Help
While native Windows tools offer basic backups, Netwrix Recovery for Active Directory, part of the Netwrix AD security and ITDR solutions portfolio, empowers organizations to achieve a more robust AD disaster recovery strategy. Key features include:
- Recovery of deleted user and computer objects, fully reanimated with all attributes restored
- Quick and flexible rollback of unwanted changes to any recorded state
- DNS rollback and recovery to any recorded state, preventing spoofing and data loss due to accidental change or malicious attack
- Domain controller backup and automated AD forest recovery
- Customizable snapshot scheduling to meet recovery point objectives (RPOs)
- Role-based Access Control (RBAC)
Conclusion and Recommendations
Active Directory is a critical component of many organizations’ IT infrastructure, managing permissions and access to network resources. Ensuring that you have a backup strategy for AD can prevent the issues that might arise from data loss, corruption, or accidental deletion.
Importance of Crafting a Comprehensive Backup Strategy
An effective backup strategy involves a thorough analysis of your organization’s data to prioritize backup efforts. This includes identifying the most critical data, understanding its frequency of change, and considering regulatory compliance requirements. In crafting such a strategy, it’s important to implement a combination of regular and consistent backups using varied methods such as full, incremental, and differential backups. This approach ensures that the latest data is continuously and securely captured, minimizing potential data loss.
Recommendations for Protecting AD Infrastructure
Protecting your AD infrastructure requires a multi-layered approach that encompasses technical measures, comprehensive policies, and continuous vigilance. Regularly reviewing and updating your security strategy in line with evolving threats and best practices is vital for maintaining a secure and resilient AD environment. By implementing the recommendations below, organizations can strengthen the security posture of their Active Directory infrastructure and better protect against potential threats and vulnerabilities.
- Use strong access controls and role-based access.
- Keep AD servers and OS up to date with patches.
- Monitor and audit AD activity for suspicious changes.
- Implement multi-factor authentication for added security.
- Deploy network security measures like firewalls and antivirus software.
- Back up AD data regularly and test the recovery plan.
- Educate staff on security best practices and potential risks.
- Leverage built-in AD security features like Kerberos and BitLocker.
- Segregate and secure AD administration duties and tools.
- Consider advanced security solutions like Privileged Access Management (PAM) and SIEM systems for added protection.
Importance of Regular Reviews and Update of Backup Strategy
Your current backup strategy might cover all the essentials as of now, but with the rapid rate of digital transformation, will it still be as effective six months down the line? Regularly reviewing and updating your backup strategy ensures that it remains relevant and adaptable to the evolving needs and challenges of your organization. Embrace changes in technology, business requirements, and industry best practices to stay ahead of potential threats. You can mitigate the risk of data loss and operational disruptions.
FAQ
How do I back up my Active Directory?
You can back up Active Directory by performing a full server backup or system state backup. To do this, you can either use the Windows Server GUI or command-line tool.
How many types of backup are there in Active Directory?
There are two main ways you can backup Active Directory: full server backup and system state backup.
How do I back up Active Directory users and computers?
You cannot backup Active Directory users and computers (ADUC); it is a tool to manage AD objects. AD users and computers will back up when you perform a full server backup, however.
How do I back up Azure Active Directory?
AD provides backup features for only object-related backups and only for 30 days. There are other Azure Backup features for several other tasks, but not for backing up Azure AD.
How do I back up the Active Directory 2008?
You can use the Windows Server Backup feature to back up Active Directory 2008.
How do I recover Active Directory without backup?
While challenging, it is possible to recover AD without backup. You can leverage several options including the Active Directory Recycle Bin if enabled, rebuilding the AD environment, or using third-party object recovery tools.
How do I restore Active Directory backup in Windows 2003?
Boot into Directory Services Restore Mode (DSRM ), open the command prompt, and use the Ntdsutil.exe utility to perform an authoritative restore from a recent backup.
How do I restore Active Directory backups?
You can either do this manually or with the help of third-party recovery tools. Manually, you must boot into DSRM on the domain controller.
What are the three types of backups?
Below are three main types of backups.
Full Backup: A full backup captures an entire dataset, including all selected files, folders, databases, or systems.
Incremental Backup: Incremental backups only capture changes made since the last backup, whether it was a full back up or an incremental backup.
Differential Backup: Differential backups capture changes made since the last full backup.Unlike incremental backups, which only capture changes since the last backup (whether full or incremental), differential backups capture changes since the last full backup.
What are the four types of backup systems?
The four types of backup systems include full, incremental, differential, and copy backup.
What is a full backup?
A full backup, also known as a full server backup, creates a copy of AD data, including the state system, with the aim of restoring AD to its original functionality.
What is a backup method?
A backup AD method refers to how you choose to perform the backup, with there being two primary ways. You can either use the Windows Server Manager or the command-line tool.
What is the best practice for Active Directory backup?
There are several best practices for Active Directory Backup you can implement, including backing up AD regularly, testing to ensure you can restore the backups, and enforcing stringent security measures on the storage.
Where are Active Directory backups stored?
The storage location for AD backups depends on your preference. You can choose to store the backups on local drives, cloud storage, external drives, etc.
Director of Product Management at Netwrix. Kevin has a passion for cyber security, specifically understanding the tactics and techniques attackers use to exploit organizations environments. With eight years of experience in product management, focusing on Active Directory and Windows security, he’s taken that passion to help build solutions for organizations to help protect their identities, infrastructure and data.
Active Directory is one of the most important components in any Windows network. Having no AD backup strategy could put your organization at risk. We provide a step-by-step guide on how to backup Active Directory running on Windows Server.
Technology Advisor | Cybersecurity Evangelist
Updated: November 30, 2024

Active Directory (AD) is a Microsoft proprietary directory service developed for Windows domain networks. It was first introduced in Windows Server 2000 for centralized domain management.
Active Directory (AD) is included in all versions of Windows Server since 2000. It is a central component for managing network resources, user accounts, and security in a Windows-based environment. AD enables administrators to organize and control access to resources such as computers, printers, applications, and user data across an organization. It ensures centralized authentication and authorization, simplifying identity management and enhancing security.
Active Directory provides centralized authentication and authorization, making it easier to manage user identities and permissions. It supports key services such as Group Policy (for managing settings across devices and users) and Single Sign-On (SSO), allowing users to access multiple systems with a single login. Additionally, it integrates seamlessly with other Microsoft services like Exchange and SharePoint.
Directory Structure
The AD directory structure is hierarchical and consists of several core components:
- Domains: A domain is the fundamental unit of AD. It contains objects such as users, computers, and groups. Domains share a common directory database and security policies.
- Organizational Units (OUs): These are containers within a domain used to organize objects. OUs can mirror a company’s organizational structure, making it easier to apply policies and delegate administrative tasks.
- Trees: A tree is a collection of one or more domains grouped together in a contiguous namespace. For example, sales.company.com and hr.company.com might be part of the same tree.
- Forest: A forest is the top level of the AD hierarchy. It consists of one or more domain trees that share a common schema and global catalog but do not necessarily share a contiguous namespace.
- Global Catalog: This is a searchable index that contains a partial replica of all objects in the AD forest. It enables quick searches for objects across domains.
Active Directory simplifies network management, improves security, and enhances user experience. Its hierarchical structure allows for efficient organization. Its integration into Windows Server enables its access rights management services to be easily embedded into a wide range of Windows-compatible systems.
Do you need to back up the active directory?
Active Directory is one of the most important components in any Windows network. Having no backup strategy whatsoever could put the entire organization at risk. Its best practice is to have multiple active directory domain controllers with fail-over functionalities so that when one fails, you would still be able to recover even without a backup. However, having multiple domain controllers is not enough justification to not do a backup. You should still be doing a backup of the active directory whether you have multiple domain controllers or not. Multiple domain controllers can fail at once, accidental or deliberate deletion of all the accounts or critical organizational units (OU) can occur, entire database corruption can occur, viruses, and ransomware or some other disaster could wipe out all domain controllers. In such a situation, you would need to restore it from a backup. This is why you need to backup.
You probably don’t need to back up every single domain controller, to get a good backup of the AD. You only really should have to back up one of the domain controllers. If your domain controller crashes, your network and by extension, business activities come to a halt. Although active directory services are designed with high redundancy (if you deployed several DCs in your network). It’s therefore important to develop and implement a clear active directory backup policy. If you have multiple DCs running, you need to back up at least one of them. The ideal DC to backup should be the one running the Flexible Single Master Operation (FSMO ) role. With a good backup and recovery strategy implementation, your organization can easily recover after your domain controllers crash.
If the Active Directory Domain Controller (AD DC) becomes unavailable for whatever reason, then users cannot log in and systems cannot function properly, which can cause disruption to business activities. That’s why backing up your Active Directory is important. In this article, we will show you how to backup an Active Directory domain controller running on Windows Server 2019. Before we begin we will take a look at a concept known as System State backup and how it affects Active Directory data.
System State backup
Microsoft Windows Server offers the possibility to perform a ‘Full’ backup or a ‘System State’ backup. A Full backup makes a copy of the system drives of a physical or a virtual machine, including applications, operating systems, and even the System State. This backup can be used for bare metal recovery—this allows you to easily reinstall the operating system and use the backup to recover.
System State backup on the other hand creates a backup file for critical system-related components. This backup file can be used to recover critical system components in case of a crash. Active Directory is backed up as part of the System State on a domain controller whenever you perform a backup using Windows Server Backup, Wbadmin.exe, or PowerShell. For the purpose of this guide, we will be using System State backup because it allows us to backup only the components needed to restore Active Directory. However note that Microsoft does not support restoring a System State backup from one server to another server of a different model, or hardware configuration. The System State backup is best suited for recovering Active Directory only on the same server.
As described later in this guide, Windows Server Backup must be installed through features in Server Manager before you can use it to back up or recover your server. The type of backup you select for your domain controllers will depend on the frequency of changes to Active Directory and the data or applications that might be installed on the domain controller. The bare minimum you need to back up to protect essential Active Directory data on a domain controller is the System State. The System State includes the following list plus some additional items depending on the roles that are installed:
- Domain controller: Active Directory DC database files (NTDS.DIT), boot files & system protected files, COM+ class registration database, registry, system volume (SYSVOL)
- Domain member: Boot files, COM+ class registration database, registry
- A machine running cluster services: Additionally backs up cluster server metadata
- A machine running certificate services: Additionally backs up certificate data
In addition, System State backups will back up Active Directory-integrated DNS zones but will not back up file-based DNS zones. File-based DNS zones must be backed up as part of a volume-level backup, such as a critical volume backup or full server backup. All the above backup types can be run manually on-demand, or they can be scheduled using Windows Server Backup. You can use either Windows Server backup or Wbadmin.exe to perform a System State backup of a domain controller to back up Active Directory. Microsoft recommends using either a dedicated internal disk or an external removable disk such as a USB hard disk to perform the backups.
Backup operators do not have the privileges required to schedule backups. You must have administrative rights to be able to schedule a System State backup or restore. A System State backup is particularly important for disaster recovery purposes as it eliminates the need to reconfigure Windows back to its original state before the system failure occurred. It is important that you always have a recent backup of your System State. They may require you to perform regular System State backups to increase your level of protection. We recommended that you perform System State backups before and after any major change is made to your server.
Before going ahead with the backup process, you need to take note of the following initial steps:
- It is important that you have the necessary amount of storage space to accommodate the backup you are about to perform.
- If you’re going to be backing up while the applications that produce the data are still running (which is usually the case), you need to configure the Volume Shadow Copy Service, also known as Volume Snapshot Service (VSS) on the drive for the backup to be successful. This service helps to create backup copies or snapshots of computer files or volumes, even when they are in use.
- You need to install the Windows Server Backup feature if you haven’t done this yet. Windows Server 2019 just like previous editions, comes with the Windows Server Backup feature that helps to perform Active Directory database backups and restores. Now we will go through the above steps in detail.
Configure the Volume Shadow Copy Service (VSS)
It is important to ensure that the AD database is backed up in a way that preserves database consistency. One way to preserve consistency is to back up the AD database when the server is in a powered-off state. However, backing up the Active Directory server in a powered-off state may not be a good idea if the server is operating in 24/7 mode.
For this reason, Microsoft recommends the use of Volume Shadow Copy Service (VSS) to back up a server running Active Directory. VSS is a technology included in Microsoft Windows that can create backup copies or snapshots of computer files or volumes, even when they are in use. VSS writers create a snapshot that freezes the System State until the backup is complete to prevent modifying active files used by Active Directory during a backup process. In this way, it is possible to back up a running server without affecting its performance. For this guide, we are going to show you how to change the Shadow Copy size limit configuration on the volume where we are going to store the AD database.
1. Press a combination of Win+X on your keyboard to open the Disk Manager. Select the partition where the server is installed, then right-click on it and click on Properties.

2. Go to the Shadow Copies tab and then click on Enable as shown on the image below.
3. In the next window, click Yes to confirm that you want to enable shadow copies as shown below.

4. After confirmation, you’ll see a restore point created in the selected partition. Click on Settings to continue.
5. In the Settings screen shown below, under Maximum size, select No limit. Once completed click the OK button, and that does it for this section—configure the Volume Shadow Copy Service (VSS).
Install the Windows Server backup feature
Windows Server Backup is a utility provided by Microsoft with Windows Server 2008 and later editions. It replaced the NTBackup utility which was built into the Windows Server 2003. Windows Server Backup is a feature that is installable in Windows Server 2019 just like in other previous editions. So if you haven’t used the backup feature yet, you will likely have to install it first. The way to install this feature is through the Server Manager.
1. Open the Server Manager console as shown in the image below.

2. Go to Local Server >> Manage tab >> and click on the Add Roles and Features as seen in the image below. This will open the Add Roles and Features Wizard.

3, In the Select installation type screen, select the Role-based or feature-based installation option and click Next.

4. In the next screen called Select destination server, you will be required to select the server on which you want to install roles and features. Windows will automatically display the server pool. In this case, we are going to select the local server, which is WD2K19-DC01-mylablocal.

5. In the Select server roles screen, you are required to select the roles to install on the server. Since we are installing a feature, you can ignore this section and continue to the next screen. Click Next to continue.

6. In the Select features screen below, scroll down to the Windows Server Backup feature, and select it as seen in the image below. Click Next to continue.

7. In the Confirm installation selections screen, make sure that the Windows Server Backup feature is on the screen and click on the Install button to begin the installation.

The Windows Server Backup feature will begin to install on your local server. Once the installation is completed, click the Close button to close the console.

Backup the Active Directory database
1. Now go to the Server Manager and click on Tools >> Windows Server Backup, in order to open it. You can also open this console by running the command wbadmin.msc on the Windows Run (Ctrl+R). Once it opens up, you’ll be able to see the scheduled and last backup status (unless this is the first time you’re doing this.)

2. Once the server backup opens, click on Backup Once to initiate a manual AD database backup. Although you can also create automatic scheduled backups by clicking Backup schedule, for this guide we are going to create a manual backup.

3. Under Backup Options select Different options and click on the Next button This option is used where there is no scheduled backup.

4. In the Select Backup Configuration screen, you have two options:
-
- Full Server backs up all server data, applications, and System State
- Custom lets you choose what you want to back up.
Since we just want to back up the active directory, we choose the second option. So select Custom and click Next.

5. In the Select Items for Backup screen, specify the items that you want to include in the backup. In this backup, we are going to choose the System State Backup item. To do this, click on the Add items button >> select System State option >> and click on the Ok button to complete the process.


6. Now we are going to enable the Volume Shadow Copy Service for this backup item. Doing this prevents AD data from being modified while the backup is in progress. To enable VSS, click on Advanced Settings >> VSS Settings >> Select VSS Full Backup, and click Ok. The VSS Full Backup is the recommended option if it is your first backup, and you are not using any third-party backup tool. This option allows you to create a backup of all the files. It is also the preferred method for incremental backups, as it does not affect the sequence of backup.


7. In the next screen, you would need to specify the backup destination type — Local drives or Remote shared folder. For the purpose of this demonstration, we are using a local hard drive to store the backup. So choose Local drives and click Next.

8. In the Select Backup Destination screen you can choose the actual partition where you want to store the backup. Once you are done, click Next to proceed to the next screen.

9. The Confirmation screen lets you double-check that all backup parameters are correctly configured. Once you are good to go, click the Backup button. The backup should take some time depending on the size of the domain controller server. Once the backup is successfully completed, you can close the Backup Wizard.

If you closed the Backup Wizard without waiting for the last message status, the backup will continue to run in the background. You can also confirm the status and completion results of the backup from the webadmin console (or Windows Server Backup Feature). The console will display a message with information from this backup (and others).
Active Directory backup automation
There are a number of tools available to manage backup and restore functions for applications or entire disks and these can help you save time with backing up Active Directory. Such systems can also be used to replicate and migrate the objects in a domain controller.
ManageEngine AD360 (FREE TRIAL)
An example of an Active Directory backup system can be found in ManageEngine AD360.
The Standard edition of this bundle includes a tool called RecoveryManager Plus. The advantage of this tool is that it is integrated into a package of tools to manage Active Directory, so you get all of your AD management systems in one console.

AD360 is able to manage both cloud and on-premises implementations of Active Directory. This is a software bundle and you install it on Windows Server. It is also available from the marketplace of AWS and Azure – these are not SaaS platforms but software packages that you run in your cloud account space.
Why do we recommend it?
ManageEngine AD360 is a collection of many Active Directory-related tools offered by ManageEngine – there are seven in total. Among this list is ADAudit Plus package, which provides controls that prevent unauthorized changes to AD objects. Another unit, ADManager Plus lets you assess, improve, and monitor the efficiency and security of user accounts. Recovery Manager Plus is another component and this manages the backup of Active Directory instances.
Who is it recommended for?
ManageEngine AD360 is a comprehensive package of everything you will need to manage and control Active Directory. The package is very large and you might not need all of the components. If you are only interested in the backup and recovery services of AD360, you might prefer to just buy RecoveryManager Plus.
Pros:
- Dramatically improves the usability of Active Directory, making routine tasks easier to perform and automate
- Can monitor changes across both local and cloud-based AD environments
- Supports SSO and MFA, great for securing your access management with multiple layers of authentication
- Extensive 60-day trial period
Cons:
- Can take time to fully explore the entire platform
The best way to understand the Active Directory backup capabilities of AD360 is to access it on a 30-day free trial.
ManageEngine 360
Start 30-day FREE Trial
Active Directory backup FAQs
Is it necessary to backup Active Directory?
It is very important to backup Active Directory. The system won’t back itself up without your intervention. However, there is a native backup system built into Windows Server, which makes the process of saving a copy of Active Directory easy.
What are the different types of backup in Active Directory?
You can run a full backup to take a copy of the entire Active Directory database and then repeat this process periodically on a schedule to create rollback points. This is the system that is available in the native backup service in Windows Server, which is called Volume Shadow Copy Service (VSS). It is more efficient to take periodical full backups and then perform incremental or differential backups more frequently. These just extract the objects that have changed since the last backup and so are much quicker and take up less space. However, you need a third-party tool to implement these strategies because they are not available in Windows Server VSS.
How does Windows Server backup work?
Windows Server Backup uses a method called Volume Shadow Copy Service (VSS). this gives you the option to backup the operating system and all of the contents of the disk This is called a Bare Metal Backup and it will copy everything on the computer, not just Active Directory. The other option is called System State Backup. This copies important system files as well as the items you select. This is the option to choose in order to back up Active Directory.
Conclusion
We have explained in detail how to back up the Active Directory using the Windows Server backup. We used the manual “Backup Once” approach, but of course, you can also configure a “Backup Schedule,” to run periodic AD backup tasks.
As already mentioned, the Windows Server Backup feature is an easy to use free tool that is bundled in most Windows Server OS, and it can work with VSS to perform Full or System State backups. However, there are also lots of third party Active Directory backup tools out there that you can use. In fact, almost every enterprise-level backup service should be capable of backing up Active Directory with little to no difficulty. The difference between all those tools lies mostly in the way some of them provide more capabilities, especially when it comes to backing up and restoring the Active Directory.
