The genuine armsvc.exe file is a software component of Adobe Acrobat by .
Armsvc.exe is an executable file that belongs to Adobe Acrobat, a group of software and web services created by Adobe, to create, view, modify and print files in the Portable Document Format (PDF). This process automatically updates Acrobat on a periodic basis. This is not a critical Windows component and should be removed if known to cause problems. Adobe Acrobat comes bundles with Reader (formerly Acrobat Reader), a freeware tool that can view, print and annotate PDF files; Acrobat (formerly Acrobat Exchange), a paid software that can create PDF documents; and Acrobat.com, a file hosting service. Adobe Systems Incorporated is an American software giant that develops software products for web design, video editing, web hosting, image editing, servers, as well as formats such as Flash and PDF. The company was established in 1982 by Charles Geschke and John Warnockin and is currently headquartered in San Jose, California.
ArmSvc stands for Adobe Acrobat Automatic Update Service
The .exe extension on a filename indicates an executable file. Executable files may, in some cases, harm your computer. Therefore, please read below to decide for yourself whether the armsvc.exe on your computer is a Trojan that you should remove, or whether it is a file belonging to the Windows operating system or to a trusted application.
Click to Run a Free Scan for armsvc.exe related errors
Armsvc.exe file information

The process known as Adobe Acrobat Update Service or Acrobat Update Service belongs to software Adobe Acrobat Update Service or Adobe Refresh Manager or Adobe Reader XI or Adobe Reader X or Adobe Common File Installer or Adobe Acrobat Reader DC or Adobe Reader XI MUI or Acrobat Update Service by Adobe Systems (www.adobe.com) or Adobe (www.adobe.com).
Description: Armsvc.exe is not essential for Windows and will often cause problems. Armsvc.exe is located in a subfolder of «C:\Program Files\Common Files» or sometimes in a subfolder of the user’s profile folder—primarily C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\ or C:\Program Files (x86)\Common Files\Adobe\ARM\UserName.0\.
Known file sizes on Windows 10/11/7 are 81,088 bytes (15% of all occurrences), 82,128 bytes and 22 more variants.
It is the AdobeARMservice service: Adobe Acrobat Updater keeps your Adobe software up to date.
The program has no visible window. It is not a Windows core file. The file has a digital signature. The application can be uninstalled in the Control Panel.
Therefore the technical security rating is 25% dangerous, but you should also take into account the user reviews.
Uninstalling this variant:
In case you experience problems using armsvc.exe, you can do the following:
1) uninstall the program using the Control Panel ⇒ Uninstall a Program ⇒ Adobe Refresh Manager or Adobe Reader XI
2) turn to the software developer, Adobe, for advice
3) look for a new, improved version.
Recommended: Identify armsvc.exe related errors
- If armsvc.exe is located in a subfolder of «C:\Program Files», the security rating is 34% dangerous. The file size is 83,984 bytes (50% of all occurrences) or 63,960 bytes.
The file is not a Windows system file. The armsvc.exe file is digitally signed. The program is not visible.Uninstalling this variant:
In case you experience problems using armsvc.exe, you can do the following:
1) uninstall the program using the Control Panel ⇒ Uninstall a Program ⇒ Adobe Refresh Manager
2) turn to the software developer, Adobe, for advice
3) look for a new, improved version.
Important: Some malware camouflages itself as armsvc.exe, particularly when located in the C:\Windows or C:\Windows\System32 folder. Therefore, you should check the armsvc.exe process on your PC to see if it is a threat. We recommend Security Task Manager for verifying your computer’s security. This was one of the Top Download Picks of The Washington Post and PC World.
Best practices for resolving armsvc issues
A clean and tidy computer is the key requirement for avoiding problems with armsvc. This means running a scan for malware, cleaning your hard drive using 1cleanmgr and 2sfc /scannow, 3uninstalling programs that you no longer need, checking for Autostart programs (using 4msconfig) and enabling Windows’ 5Automatic Update. Always remember to perform periodic backups, or at least to set restore points.
Should you experience an actual problem, try to recall the last thing you did, or the last thing you installed before the problem appeared for the first time. Use the 6resmon command to identify the processes that are causing your problem. Even for serious problems, rather than reinstalling Windows, you are better off repairing of your installation or, for Windows 8 and later versions, executing the 7DISM.exe /Online /Cleanup-image /Restorehealth command. This allows you to repair the operating system without losing data.
To help you analyze the armsvc.exe process on your computer, the following programs have proven to be helpful: ASecurity Task Manager displays all running Windows tasks, including embedded hidden processes, such as keyboard and browser monitoring or Autostart entries. A unique security risk rating indicates the likelihood of the process being potential spyware, malware or a Trojan. BMalwarebytes Anti-Malware detects and removes sleeping spyware, adware, Trojans, keyloggers, malware and trackers from your hard drive.
Other processes
skypehost.exe steam.exe hostappserviceupdater.exe armsvc.exe googleupdate.exe igfxtray.exe rpbrowserrecordplugin.dll wltrysvc.exe nvscpapisvr.exe utorrent.exe plugin-container.exe [all]
What Is Armsvc.exe & Should You Disable It?
In the ever-evolving landscape of Windows operating systems and software applications, users frequently encounter various processes running in the background. One such process that often raises questions is armsvc.exe. While the filename can seem innocuous, it is imperative to understand its purpose, origin, functionality, and whether it should remain enabled on your computer.
Understanding Armsvc.exe
Armsvc.exe is a process related to the Microsoft Windows operating system, specifically concerning the Universal Windows Platform (UWP) apps. It is a component of the Microsoft Application Registration and Management Service, which assists in managing and registering applications within the Windows ecosystem. The executable file is typically located in the C:WindowsSystem32 directory.
The primary role of armsvc.exe relates to background tasks associated with how UWP apps interact with the Windows service. This includes tasks like licensing, provisioning, and updating applications, ensuring that users have the latest features and are compliant with licensing rules. The service is an integral part of the Microsoft Store’s ecosystem, providing essential backend support for apps sourced from the store.
How Does Armsvc.exe Work?
When you install an app through the Microsoft Store, armsvc.exe ensures that the application is registered correctly. It manages tasks such as:
- Licensing Verification: It checks if the user holds a valid license for the application.
- Application Updates: It facilitates the downloading and installation of updates.
- Provisioning: It configures application settings and preferences when an app is newly installed.
- Subscription Management: It tracks the subscription status and manages paid applications.
The operations conducted by armsvc.exe occur silently in the background, meaning that you typically won’t see its direct effects. However, implications of its functions are felt when an application is not updated or when it experiences licensing issues.
Should You Disable Armsvc.exe?
The question of whether to disable armsvc.exe implies a need for careful consideration, as disabling any critical system service could lead to unintended consequences.
There are several things to consider before making a decision:
-
Safety and Security: Generally,
armsvc.exeis not a malicious process. It is a legitimate file originating from Microsoft. However, like many processes, it can be mimicked by malware. If you notice unusual behavior or if your antivirus software flags the file, it might be worth performing a thorough virus scan or checking the file’s location. The legitimatearmsvc.exeshould only be located inC:WindowsSystem32. -
Impact on Applications: Disabling
armsvc.exewill directly impact how UWP apps function. Without this service, apps may fail to update, leading to bugs and security vulnerabilities in outdated applications. Additionally, users may experience issues with using Microsoft Store features, such as purchasing applications or utilizing premium features that require compliance checks. -
Resource Consumption: If you’re concerned about system performance, it is essential to evaluate whether
armsvc.exeis indeed consuming significant system resources. Users sometimes report that certain applications (or their background services) can lead to high CPU and memory usage. If you notice such problems, you may decide to disable the service temporarily until you can determine the cause. -
Alternatives: If you are intent on disabling
armsvc.exe, consider whether you can achieve the same results through other means, such as configuring application settings to disable automatic updates or notifications, which can give you more control without completely disabling a necessary service.
How to Disable Armsvc.exe
If you thoroughly understand the implications and still wish to proceed, here’s how to disable armsvc.exe:
-
Using the Windows Services Management Console:
- Press
Windows + Rto open the Run dialog box. - Type
services.mscand hit Enter. - Scroll through the list and find the «Microsoft Application Registration Service».
- Right-click on it, and choose «Properties».
- In the «Startup type» dropdown menu, select «Disabled».
- Click «OK» and restart your computer.
- Press
-
Using Task Manager:
- Open Task Manager by right-clicking on the taskbar and selecting «Task Manager».
- Click on the «Services» tab.
- Find the
armsvc.exeservice, right-click it, and choose «Stop».
-
Via Windows Settings:
- Open the Settings app by pressing
Windows + I. - Go to «Privacy».
- In the «Activity history» or app permissions, you can manage what apps are allowed to run or track, thereby limiting the interactions.
- Open the Settings app by pressing
Troubleshooting Issues Related to Armsvc.exe
Users may encounter various issues related to armsvc.exe. Here are some common problems and their respective fixes:
-
High CPU or Memory Usage: If you notice
armsvc.exeor associated UWP apps consuming excessive resources, consider updating the applications, as previous versions may have bugs affecting performance. Additionally, check for Windows updates that might improve system stability. -
Application Not Launching: If an application fails to start or update, try restarting the
armsvc.exeservice. Utilize the methods outlined above to restart the service, and then attempt to launch the application again. -
Frequent Crashes of UWP Apps: When UWP apps crash frequently, it could be related to licensing issues. Check if your Microsoft account is correctly signed in and synced. You might also consider re-registering the apps via PowerShell with the following command:
Get-AppxPackage | Foreach {Add-AppxProvisionedPackage -Online -PackagePath $_.InstallPath -SkipLicense} -
Malware Concerns: If there’s any suspicion that
armsvc.exemay not be legitimate—due to unusual behavior or location—immediately run a full antivirus scan. Use tools like Windows Defender or third-party software to ensure your system is free of malware.
Conclusion
armsvc.exe is an essential component of the Windows operating system, specifically for managing UWP apps from the Microsoft Store. Disabling it, while possible, can lead to a cascade of issues regarding app functionality, automatic updates, and licensing management.
Understanding its role can assist users in making an informed decision about whether to allow it to run in the background. If you’re dealing with performance issues, rather than disabling it outright, you might consider troubleshooting the root causes or limiting resource-heavy UWP apps individually.
For most users wanting seamless application management and consistent updates, it’s advisable to keep armsvc.exe enabled. However, if you’re equipped with the knowledge of its implications and the potential for troubleshooting, you can make the best decision for your computing environment. Your choice should depend on a balance between security, performance, and usability.
*7-day Free Trial w/Credit card, no charge upfront or if you cancel up to 2 days before expiration; Subscription price varies per region w/ auto renewal unless you timely cancel; notification before you are billed; 30-day money-back guarantee; Read full terms and more information about free remover.
Armsvc.exe is a sophisticated new malware threat of the Trojan horse type. Armsvc.exe uses disguise to trick its victims and then begins to covertly execute various malicious processes in the attacked system.

Malware comes in numerous varieties and shapes. However, there are not many online threats that can match the crafty and cunning nature of an infection from the Trojan horse type. The Armsvc.exe Trojan is one such threat and if you are reading this, you have most likely become a victim of its harmful activities. It is highly recommended to remove this Trojan and rid your system of it, because if you don’t do that in time, a lot of malicious effects may take place on your computer. What we have in mind here is the ability of the Trojan to cause severe data and software corruption, to insert different viruses like Spyware or Keyloggers and even Ransomware threats and to provide the hackers with total remote access to your entire computer. Fortunately, there is a way to safely eliminate Armsvc.exe Trojan and our team has already prepared a removal guide on that. We have selected some proven steps, which will assist you to manually identify the harmful Trojan files and delete them even if your antivirus is not able to fully clean up the infection. However, we would encourage you to follow them only after you carefully familiarize yourself with the specifics of this malicious software group because dealing with infections like Armsvc.exe Trojan may require all of your attention and understanding.
Trojan infections – real nightmare for the users’ computers!
Trojan horse infections can be extremely troublesome. We really aren’t exaggerating because if a malicious script like Armsvc.exe is inside your computer, all of your data, as well as your system and your safety could be exposed to great risks. What malicious things can a Trojan horse do? Well, the options the hackers can choose from are not just one or two. They can program the script to act as a backdoor for other infections like Ransomware, spyware and different viruses. They can also use Armsvc.exe Trojan to gain complete remote access to your computer and turn it into a bot. Very often, with the help of the Trojan, the hackers are able to secretly collect passwords, login credentials, banking details, credit or debit card numbers and perform various crimes such as online fraud, blackmail, and theft.
Usually, most of the victims are not aware of the contamination and it takes them time to figure out that the malware is secretly operating on their machine. This is because Trojans often lack some visible symptoms and try to remain hidden for as much time as possible, while they perform the malicious deeds they have been programmed for. Unfortunately, by the time they are revealed, major damage is caused to the infected machine and the victims often have to face the malicious consequences that appear almost out of the blue.
SUMMARY:
| Name | Armsvc.exe |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Crashes and system errors as well as changed Internet and browser settings are oftentimes the main signs that there’s a Trojan horse infection in the computer. |
| Distribution Method | Usually, hackers who create Trojan viruses disguise their malware as something users would be tempted to download and then upload it to pirate file-sharing/torrent sites or send it via spam emails. |
| Detection Tool |
Some threats reinstall themselves if you don’t delete their core files. We recommend downloading SpyHunter to remove harmful programs for you. This may save you hours and ensure you don’t harm your system by deleting the wrong files. |
Please follow all the steps below in order to remove Armsvc.exe!
How to remove Armsvc.exe
- First, click the Start Menu on your Windows PC.
- Type Programs and Settings in the Start Menu, click the first item, and find Armsvc.exe in the programs list that would show up.
- Select Armsvc.exe from the list and click on Uninstall.
- Follow the steps in the removal wizard.
What we suggest you do first is, check the list of programs that are presently installed on the infected device and uninstall any rogue software that you find there:
- From the Start Menu, navigate to Control Panel ->>> Programs and Features ->>> Uninstall a Program.
- Next, carefully search for unfamiliar programs or programs that have been installed recently and could be related to Armsvc.exe.
- If you find any of the programs suspicious then uninstall them if they turn out to be linked to Armsvc.exe.
- If a notification appears on your screen when you try to uninstall a specific questionable program prompting you to just alter it or repair it, make sure you choose NO and complete the steps from the removal wizard.
Remove Armsvc.exe from Chrome
- Click on the three dots in the right upper corner
- Go to more tools
- Now select extensions
- Remove the Armsvc.exe extension
- Once you open Chrome, click on the three-dots icon to open the browser’s menu, go to More Tools/ More Options, and then to Extensions.
- Again, find the items on that page that could be linked to Armsvc.exe and/or that might be causing problems in the browser and delete them.
- Afterwards, go to this folder: Computer > C: > Users > *Your User Account* > App Data > Local > Google > Chrome > User Data. In there, you will find a folder named Default – you should change its name to Backup Default and restart the PC.
- Note that the App Data folder is normally hidden so you’d have to first make the hidden files and folders on your PC visible before you can access it.
How to get rid of Armsvc.exe on FF/Edge/etc.
- Open the browser and select the menu icon.
- From the menu, click on the Add-ons button.
- Look for the Armsvc.exe extension
- Get rid of Armsvc.exe by removing it from extensions
If using Firefox:
- Open Firefox
- Select the three parallel lines menu and go to Add-ons.
- Find the unwanted add-on and delete it from the browser – if there is more than one unwanted extension, remove all of them.
- Go to the browser menu again, select Options, and then click on Home from the sidebar to the left.
- Check the current addresses for the browser’s homepage and new-tab page and change them if they are currently set to address(es) you don’t know or trust.
If using MS Edge/IE:
- Start Edge
- Select the browser menu and go to Extensions.
- Find and uninstall any Edge extensions that look undesirable and unwanted.
- Select Settings from the browser menu and click on Appearance.
- Check the new-tab page address of the browser and if it has been modified by “Armsvc.exe” or another unwanted app, change it to an address that you’d want to be the browser’s new-tab page.
How to Delete Armsvc.exe
- Open task manager
- Look for the Armsvc.exe process
- Select it and click on End task
- Open the file location to delete Armsvc.exe
- Access the Task Manager by pressing together the Ctrl + Alt + Del keys and then selecting Task Manager.
- Open Processes and there try to find a process with the name of the unwanted software. If you find it, select it with the right button of the mouse and click on the Open File Location option.
- If you don’t see a “Armsvc.exe” process in the Task Manager, look for another suspicious process with an unusual name. It is likely that the unwanted process would be using lots of RAM and CPU so pay attention to the number of resources each process is using.
- Tip: If you think you have singled out the unwanted process but are not sure, it’s always a good idea to search for information about it on the Internet – this should give you a general idea if the process is a legitimate one from a regular program or from your OS or if it is indeed likely linked to the adware.
- If you find another suspicious process, open its File Location too.
- Once in the File Location folder for the suspicious process, start testing all of the files that are stored there by dragging them to our free online scanner available below.
-
Each file will be scanned with up to 64 antivirus programs to ensure maximum accuracy
This scanner is free and will always remain free for our website’s users.
This file is not matched with any known malware in the database. You can either do a full real-time scan of the file or skip it to upload a new file. Doing a full scan with 64 antivirus programs can take up to 3-4 minutes per file.
Drag and Drop File Here To Scan
Analyzing 0 s
Each file will be scanned with up to 64 antivirus programs to ensure maximum accuracy
This scanner is based on VirusTotal’s API. By submitting data to it, you agree to their Terms of Service and Privacy Policy, and to the sharing of your sample submission with the security community. Please do not submit files with personal information if you do not want them to be shared.
- If the scanner finds malware in any of the files, return to the Processes tab in the Task Manager, select the suspected process, and then select the End Process option to quit it.
- Go back to the folder where the files of that process are located and delete all of the files that you are allowed to delete. If all files get deleted normally, exit the folder and delete that folder too. If one or more of the files showed an error message when you tried to delete them, leave them for now and return to try to delete them again once you’ve completed the rest of the guide.
How to Uninstall Armsvc.exe
- Click on the home button
- Search for Startup Apps
- Look for Armsvc.exe in there
- Uninstall Armsvc.exe from Startup Apps by turning it off
- Now you need to carefully search for and uninstall any Armsvc.exe-related entries from the Registry. The easiest way to do this is to open the Registry Editor app (type Regedit in the windows search field and press Enter) and then open a Find dialog (CTRL+F key combination) where you have to type the name of the threat.
- Perform a search by clicking on the Find Next button and delete any detected results. Do this as many times as needed until no more results are found.
- After that, to ensure that there are no remaining entries lined to Armsvc.exe in the Registry, go manually to the following directories and delete them:
- HKEY_CURRENT_USER/Software/Random Directory.
- HKEY_CURRENT_USER/Software/Microsoft/Windows/CurrentVersion/Run/Random
- HKEY_CURRENT_USER/Software/Microsoft/Internet Explorer/Main/Random
Is Armsvc.exe dangerous?
Threats like Armsvc.exe and Smss.exe tend to appear fully legitimate or generally harmless-looking files, links, emails messages, images, applications, audio or video files. This way, they can purposely trick the users into clicking on them without having a clue about the danger. One tap on the well-camouflaged payload is usually enough to activate the exploit kit, where the malware is inserted. This ability of the Trojans is what the hackers love the most. They frequently use various tricky transmitters such as malicious links, attachments, too-good-to-be-true offers, “you won a prize” messages, aggressive popping boxes or some free applications and installers to infect the users and break through their system.
That’s why users have a major role in the prevention of Trojan infections. We always advise our readers not to trust every pop-up, link, email or an ad that comes on their screen, even if it seems legitimate. Avoiding unsafe web locations, shady installers and sketchy web content can greatly help them to stay away from unpleasant and harmful infections. Having proper antivirus software is highly recommended as one of the best things users could do to ensure reliable protection for their system. If regularly updated, a good antivirus can detect potentially harmful scripts and can indicate the users about them before a major damage is done. However, some advanced Trojans like Armsvc.exe Trojan may be though to detect and remove even with the antivirus and may require additional assistance and some specialized software. The removal guide below can provide some manual instructions as well as a specialized removal tool, with the help of which no Trojan can remain hidden on your system.
Violet is an active writer with a passion for all things cyber security. She enjoys helping victims of computer virus infections remove them and successfully deal with the aftermath of the attacks. But most importantly, Violet makes it her priority to spend time educating people on privacy issues and maintaining the safety of their computers. It is her firm belief that by spreading this information, she can empower web users to effectively protect their personal data and their devices from hackers and cybercriminals.
Violet is an active writer with a passion for all things cyber security. She enjoys helping victims of computer virus infections remove them and successfully deal with the aftermath of the attacks. But most importantly, Violet makes it her priority to spend time educating people on privacy issues and maintaining the safety of their computers. It is her firm belief that by spreading this information, she can empower web users to effectively protect their personal data and their devices from hackers and cybercriminals.
A number of users have recently reported issues with armsvc.exe. Many claim armsvc.exe affects the efficiency of their systems. And it is the suspect that creates the bugs on their computer.
Many say that armsvc.exe is a legitimate file that infiltrates our system and triggers serious issues with an armsvc.exe virus.
All could be assumed, but we can’t definitely claim whether this is a virus or trojan horse without strong evidence and testing. However, we have provided you with all the information and solutions in this guide if you also face this issue.
You just have to check at the article closely. We did all the background analysis for you. And we believe that you will learn how to solve this problem by the end of the article.
Before we start with the solution, let’s first take a lot at What is armsvc.exe!!!

armsvc.exe is just an executable file which is associated with Adobe Reader XI 11.0.03 software. This program is developed by Adobe Systems Incorporated and this is a legitimate process that can be found running in Windows Task Manager.
[box title=”” border_width=”1″ border_color=”#fff8ef” border_style=”solid” bg_color=”#fff8ef” align=”left”]
This does not use a lot of power of the CPU. You don’t have to do anything when you are using it. Some users claim that it is a virus or malware which breaks and causes a lot of damage to their Computer.
Some claim it consumes the power of CPUs and GPUs and causes the output of your Computer to decline significantly. This will happen if users upload malware files from unauthorized websites instead of legitimate armsvc.exe.
You just need to run an antivirus search on your PC to make sure that you have some harmful malware enabled or a legal executable. When the antivirus check is complete and armsvc.exe shows.
[/box]
Read the below-mentioned instruction to know what to do after you find this executable file malicious.
Is Armsvc.exe Safe, or is it a Virus or Malware?
To confirm if armsvc.exe is a legitimate file or not, you must check the location of the file. The address of this executable file is C:\Program Files\Adobe\Reader 11.0\Reader\AdobeCollabSync.exe You will find this file here and not elsewhere.
When Windows Task Manager is opened go to View -> choose Columns and choose “Image Path Name” to add an address column to your Task Manager. It might be a wise decision to analyze this process further if you consider a suspect directory here.
Microsoft’s Task Explorer is another resource that often lets you spot wrong processes. Open the program and switch on ‘Check Legends’ under Options (it does not need to be installed). Now go to Screen-> Pick columns and add a column named “Verified Signer.”
When the “Verified Signer” is reported as “Unable to verify” otherwise search for a second. In all good Windows operations, there is no verified signature sign for neither positive nor negative signature.
Some important facts about armsvc.exe that you should know are the following:
- Publisher: Adobe Systems Incorporated
- Location: C:\Program Files\Adobe\Reader 11.0\Reader\ subfolder.
- Size: 1.15 Mb
- Full Path: C:\Program Files\Adobe\Reader11.0\Reader\AdobeCollabSync.exe
You must confirm the legitimacy of this executable file before you decide to delete or remove it from your computer. To do so, you can find this file in Windows Task Manager.
[box title=”” border_width=”1″ border_color=”#343e47″ border_style=”solid” bg_color=”#effaff” align=”left”]
Once you find its location, you can compare it to the above-mentioned facts. The suspicion that you may be diagnosed by a virus should be resolved quickly.
You can install a Full Security Program such as Malwarebytes to completely delete the armsvc.exe virus. Note, not every tool can detect any type of malware, and various solutions should be tried until effective results are achieved.
Furthermore, the virus’ configuration itself will cause armsvc.exe deletion. In this scenario, Secure Mode with Networking must be allowed.
[/box]
A protected system that deactivates most processes and just activates the tools and drivers are required. If you have a security program there, you should run an overview of the system.
Can I Remove or Delete Armsvc.exe?
Any protected executable file without a legitimate purpose should not be removed, because this can affect the performance of any programs associated with the file.
Make sure all the applications and systems are up-to-date to prevent potential file manipulation issues. Program and test drivers upgrades are frequent. As long as security improvements are concerned there is little to no chance of such issues.
Approximately 9 per cent of individuals delete this file according to various reports online, and it may be secure, but you can test yourself if it is secure or a virus.
[box title=”” border_width=”1″ border_color=”#fff8ef” border_style=”solid” bg_color=”#fff8ef” align=”left”]
Therefore, you need to download a trustworthy program to encounter this issue.
If the file is identified as harmful, armsvc.exe will then be disabled and the related malware will be eliminated. However, the best solution to these suspicious issues is Reimage. You may launch a complete system analysis using Reimage and it will help greatly.
If this is not a trojan or malware, but you need to disable armsvc.exe. You can uninstall Epson Event Manager from a device by utilizing its uninstaller, located at MsiExec.exe /I{AC76BA86-7AD7-1033-7B44-AB0000000001}.
That is the most critical aspect of the program’s workstation. If it’s not uninstallable, you may need to uninstall Adobe Reader XI 11.0.03 to completely remove it. In the Windows Control Panel, you can use the Add / Remove program option.
[/box]
Also, You can completely delete this program from your computer if you no longer use Epson Creativity Suite and armsvc.exe. To do so, select ‘appwiz.cpl’ and click Windows + R KEY simultaneously.
Find and uninstall or remove Adobe Reader XI 11.0.03. in the list of installed programs.
Common Armsvc.exe Error Messages
You may encounter the following error messages regarding armsvc.exe.
- “Cannot find armsvc.exe.”
- “armsvc.exe Application Error.”
- “armsvc.exe is not a valid Win32 application.”
- “Error starting program: armsvc.exe.”
- “armsvc.exe has encountered a problem and needs to close. We are sorry for the inconvenience.”
- “armsvc.exe not found.”
- “Faulting Application Path: armsvc.exe.”
- “armsvc.exe failed.”
- “armsvc.exe is not running.”
These.exe error messages may appear during a program launch, throughout its software execution, during Adobe Reader XI 11.0.03, during Windows initialization or shutdown.
Or even while you are downloading your Windows operating system. Having records of when and where the armsvc.exe mistake happens is crucial in solving problems.
How to Fix Armsvc.exe?
One of the easiest approaches to prevent Adobe Reader XI 11.0.03 problems is with a clean and virus free computer. This ensures the malware scannings are completed, the hard drive is cleaned up by Cleanmgr and SFC / scannow.
You no longer need to uninstall programs, you control all self-start programs with MSConfig, so you can update the Windows automatically. Do not overlook backup or at least identify restore points regularly.
You may try to recall what you did or the last thing you installed in your system before the issue you are facing turns into a bigger problem. Using the command “resmon” to classify the issue processes.
[box title=”” border_width=”1″ border_color=”#343e47″ border_style=”solid” bg_color=”#effaff” align=”left”]
You can also attempt to fix the installation, or in case of Windows 8, you can execute the DISM.exe /Online /Cleanup-image /Restorehealth command in case of critical problems, instead of reinstalling Windows.
This enables the operating system to be fixed without missing any data. You can sometimes consider that the following tools are helpful for analyzing the armsvc.exe mechanism on your computer.
The security task manager shows all active Windows tasks and synchronized hidden processes such as a keyboard and browser tracking. The probability that it is Spyware, malware or a potential Trojan horse is indicated by a single security risk rating.
[/box]
This antivirus application detects and removes spyware, adware, trojans, keyloggers, viruses and trackers from your hard disk.
Download or Reinstall Armsvc.exe
If you have chosen to uninstall the armsvc.exe, we suggest you not to consider downloading. This program will contribute to many other Trojans or viruses being set up on your machine by installing the application from the website.
Moreover, because they are hidden as executable files, you can’t recognise such viruses. Therefore, the software should be reinstalled when you have the choices to download or reinstall.
Adobe Reader XI 11.0.03 may be reinstalled with the original application.
Operating System Information
- Windows XP
- Windows ME
- Windows Vista
- Windows 2000
- Windows 7
- Windows 8.1
- Windows 10
Conclusion!
There are several .exe problems that you may encounter on your PC. However, we aim to provide you with all the effective solutions to fight these problems and make your computer protected.
That’s all we have for you regarding the armsvc.exe removal guide. We hoped that we have been successful in giving you all the essential information you needed.
[box title=” ” border_width=”2″ border_color=”#fff8e5″ border_style=”solid” bg_color=”#fff8e5″ align=”left”]
[icon icon=”info” size=”1x” color=”#ffffff” bordercolor=”#dd3333″ bgcolor=”#dd3333″]
Click Here to Run a free Scan for Armsvc.exe Related Errors.
[/box]
Simple Steps To Eliminate Malicious Application
Armsvc.exe is a legitimate process that is part of the Adobe Acrobat Update Service, which helps keep Adobe Acrobat Reader software up to date. This process runs quietly in the background on your Windows computer and is responsible for checking for and installing updates to Adobe Acrobat Reader. It does this automatically, so you don’t need to take any action.
If you use Adobe Acrobat Reader, Armsvc.exe is an important part of keeping the software current and secure. However, if you don’t use Adobe Acrobat Reader or prefer to manually update your software, you can disable this update service to save system resources.
While Armsvc.exe itself is not malware, it’s important to be cautious. Some malicious programs might use names similar to Armsvc.exe to pretend they are legitimate files. To make sure you are dealing with the genuine Armsvc.exe, check that the file is located in the correct Adobe Acrobat folder and is not flagged by your antivirus software.
In summary, Armsvc.exe is a necessary and legitimate process for updating Adobe Acrobat Reader. Still, always ensure that it is the genuine file and not a disguised piece of malware by verifying its location and running security scans if needed.
Threat Summary |
| Name: Armsvc.exe |
| Category: Trojan |
|
Characteristics: Threat actors behind this infection can employ it for several hateful purposes |
| Threat level: High |
|
Symptoms: Frequent system crashes and freezes, slow performance of the infected PC, error messages, etc. |
| Distribution: Fake email attachments, deceptive ads, insecure sites |
Armsvc.exe: Depth Analysis
Trojans like Armsvc.exe can be made use of for a variety of hateful activities. It’s a quite new malware, so we cannot yet inform you precisely what this virus is going to do inside your computer. However, there are so many things related to the infection that you need to beware of. It can be used to steal important information kept inside the device and also extract money from the victims using different tactics. It can allow cyber crooks remotely gain access to the compromised PCs who can then do all the criminals tasks themselves.
Furthermore, Armsvc.exe can spy on you and record your activities through camera, microphone and via other ways. It can log your keystrokes and collect all the data you type through your keyboard. Moreover, it can make your device as a part of botnet and attack other computer machines through the network. Threat actors can employ this parasite to mine cryptocurrencies as well. This is the process that requires a lot of system resources to be consumed. As a result, regular crashes and freezes as well as overall system slowdowns issues will be likely. To avoid this occurrence, remove Armsvc.exe from the device as quickly as possible.
What are the harmful effects of Armsvc.exe infection?
Trojan horses like Armsvc.exe are malicious programs that appear to be harmless or useful software but contain hidden malicious code. Once installed on a computer or device, Trojans can cause a range of harmful effects, including stealing sensitive information, controlling the system, and spreading malware to other devices. Some harmful abilities of Trojans are as follows:
- Stealing Sensitive Information: One of the primary objectives of Trojans like Armsvc.exe is to steal sensitive data, such as usernames, passwords, credit card numbers, and other personal information. Once the malware is installed on a PC, it can access and capture the user’s keystrokes, take screenshots, and even record audio and video. This info can then be used for identity theft, financial fraud, and other hateful activities.
- Controlling Devices: Armsvc.exe can also give hackers remote control of a device, enabling them to perform a range of malicious activities. For example, attackers can employ it to access and modify files, delete or encrypt data, and even take over a device’s camera and microphone. In some cases, internet criminals may use Trojans to create network of compromised systems, known as botnet, which can be used for further attacks.
- Spreading Malware: Threat actors can also use Armsvc.exe to spread malware to other devices, either by sending infected files or by exploiting vulnerabilities in software or operating systems. This can lead to a rapid spread of malware and a significant increase in the number of compromised devices.
- Encrypting Data: Some Trojans are designed to encrypt data on a computer and demand a ransom payment in exchange for the decryption key. This type of attack is known as ransomware and can be devastating for organizations and individuals that rely on their data to operate.
- Destructive Attacks: Trojans can also be used to launch destructive attacks, such as deleting or corrupting files, disrupting network activity, ort even causing physical damage to systems. These attacks can be used to sabotage businesses, governments, and critical infrastructure, causing significant financial and reputational damage.
In short, Armsvc.exe is a significant threat to the security and privacy of both individuals and organizations. It can steal sensitive information, control devices, spread malware, encrypt data, and launch destructive attacks.
Armsvc.exe can spread ransomware infections:
Trojans are a common method used by cyber criminals to spread ransomware, a type of malware that encrypts the victim’s files and demands payment in exchange for the decryption key. Armsvc.exe is typically disguised as a legitimate program or file and is delivered to the targeted systems through email attachments, malicious links, or infected software downloads.
Once the Trojan is installed on the computer, it silently downloads and installs the ransomware. The ransomware then begins encrypting the victim’s files, making them inaccessible to the user. The attacker then demands payment, typically in the form of cryptocurrency, in exchange for the decryption key that can unlock the files. The consequences of a ransomware attack can be severe, both for individuals and organizations. Here are some of the potential consequences of a ransomware attack spread by Trojans like Armsvc.exe:
- Loss of Data: Ransomware can cause the victim to lose access to important files, such as personal photos, financial records, and business documents. If the victim does not pay the ransom, the files may be permanently lost.
- Financial Loss: Ransomware attacks can be costly, both in terms of the ransom demanded and the cost of recovering lost data or repairing damage to the device or network.
- Reputation Damage: Organizations that suffer a ransomware attack may suffer damage to their reputation, particularly if sensitive data is compromised.
- Legal Consequences: If the victim’s data contains personal or sensitive information, the attacker may be in violation of data protection laws, leading to legal consequences.
- Disruption of Business: Ransomware attacks can disrupt business operations, leading to lost revenue, missed deadlines, and other negative consequences.
To sum up, Trojans are a common method used by cyber criminals to spread ransomware. The consequences of a ransomware attack can be severe.
What could be the consequences of Armsvc.exe’s ability of stealing data?
The consequences of Armsvc.exe’s ability to steal information can be severe and long-lasting. One of the primary consequences is identity theft. Threat actors can make use of the stolen data to create fake identities or take over existing ones. This can lead to financial losses, damage to credit scores, and legal problems for the victim. Additionally, victims of identity theft may spend months or even years trying to resolve the damage caused by the theft of their personal information.
Another effect of Armsvc.exe’s ability to steal data is financial fraud. Internet crooks can use the stolen data to make unauthorized purchases or withdrawal from the victim’s bank account. This can result in financial losses for the affected person, as well as damage to their credit score. In some cases, victims may not be able to recover the stolen funds, leading to long-term financial problems.
A Trojan’s ability to steal data can also lead to the loss of sensitive business information. Cyber criminals can use the stolen data to gain access to company networks and steal valuable business data, such as intellectual property or trade secrets. This can lead to significant financial losses and damage to the company’s reputation. In some cases, the loss of sensitive business information can lead to the failure of the company.
Finally, a Trojan’s ability to steal data can lead to the spread of malware. Cybercriminals can use the stolen data to send targeted phishing emails or malware-laden attachments to the victim’s contacts. This can lead to the spread of malware to other devices, creating a domino effect of security breaches and data thefts.
In brief, the consequences of Armsvc.exe’s ability to steal data are severe and can have long-lasting effects on the victim’s life. It is important for individuals and companies to take proactive steps to protect their devices and data from these types of threats, including using antivirus software, avoiding suspicious websites and downloads, and regularly updating their security software.
How did my PC get infected with this virus?
There are several ways through which such malware threat may find its way into your computer. Some of the common methods include:
- Spam emails: Suspicious links in spam emails can lead to the installation of viruses.
- Online free hosting resources: Free hosting resources available on the internet can also be a source of malware infection.
- Hidden installation: Viruses can be installed secretly along with other applications, especially freeware or shareware utilities.
- P2P resources: If you employ illegal peer-to-peer (P2P) resources to download pirated software, the risk of virus infection increases.
- Trojans: Trojans can be used to spread Armsvc.exe by disguising the threat as a legitimate file or program.
Trojan often spreads through spam emails that contain malicious attachments or links. Cybercriminals create convincing-looking emails that seem legitimate, such as a message from a bank, shipping company, or government agency. These emails entice recipients to download and open the attachment or click on the link. Once clicked, the malicious payload downloads and executes on the user’s computer, infecting it with the malware. In some cases, the payload may be embedded within the email itself, allowing it to execute as soon as the email is opened.
Instances have been reported where the Armsvc.exe was camouflaged as a legitimate tool, masquerading itself as messages that demand the launch of unwanted software or browser updates. Some online scams employ a technique to trick you into installing the virus manually, by making you an active participant in the process. Typically, these fake alerts will not indicate that you are installing ransomware. Instead, the installation will be disguised as an update for a legitimate program like Adobe Flash Player or some other suspicious program. The true nature of the installation will be concealed under these bogus alerts.
Using cracked apps and P2P resources for downloading pirated software can pose a significant threat to your device’s security, and it may lead to the injection of severe malware such as the Armsvc.exe.
Trojans are a popular attack vector for such infections. Hackers use Trojans to spread ransomware, RATs, cryptominers, data stealers by disguising the malware as a legitimate file or program. Once a victim downloads and executes the Trojan, the malware payload is unleashed on their system. Trojans can be spread through various channels, including malicious websites, social media platforms, and peer-to-peer networks. Cybercriminals often use social engineering tactics to trick users into downloading and executing Trojans.
Special Offer (For Windows)
Armsvc.exe can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Armsvc.exe has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
Antimalware Details And User Guide
Click Here For Windows Click Here For Mac
Important Note: This malware asks you to enable the web browser notifications. So, before you go the manual removal process, execute these steps.
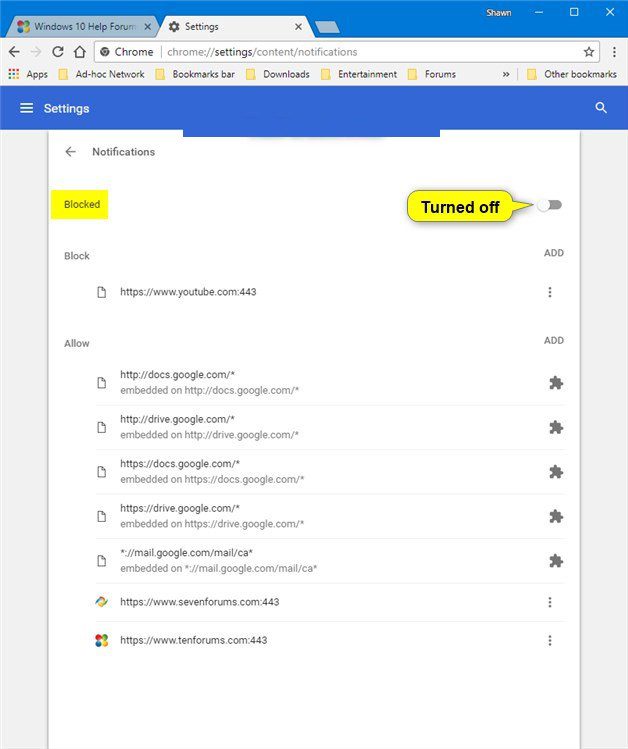
Google Chrome (PC)
- Go to right upper corner of the screen and click on three dots to open the Menu button
- Select “Settings”. Scroll the mouse downward to choose “Advanced” option
- Go to “Privacy and Security” section by scrolling downward and then select “Content settings” and then “Notification” option
- Find each suspicious URLs and click on three dots on the right side and choose “Block” or “Remove” option
Google Chrome (Android)
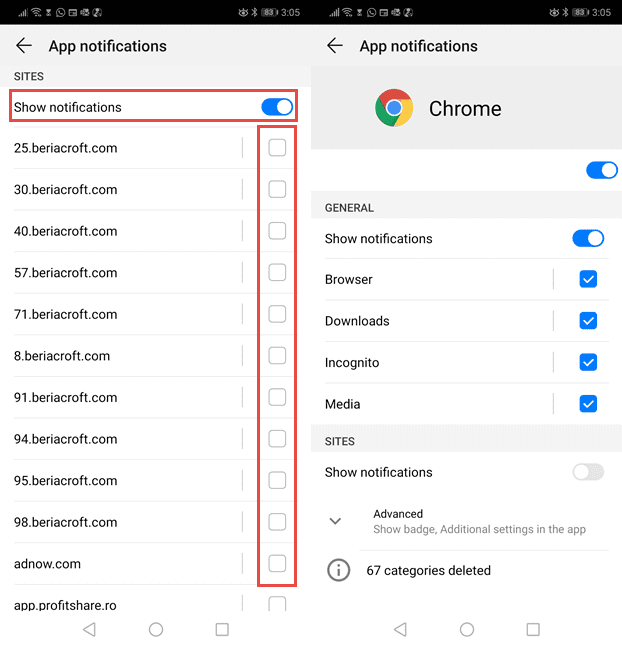
- Go to right upper corner of the screen and click on three dots to open the menu button and then click on “Settings”
- Scroll down further to click on “site settings” and then press on “notifications” option
- In the newly opened window, choose each suspicious URLs one by one
- In the permission section, select “notification” and “Off” the toggle button
Mozilla Firefox
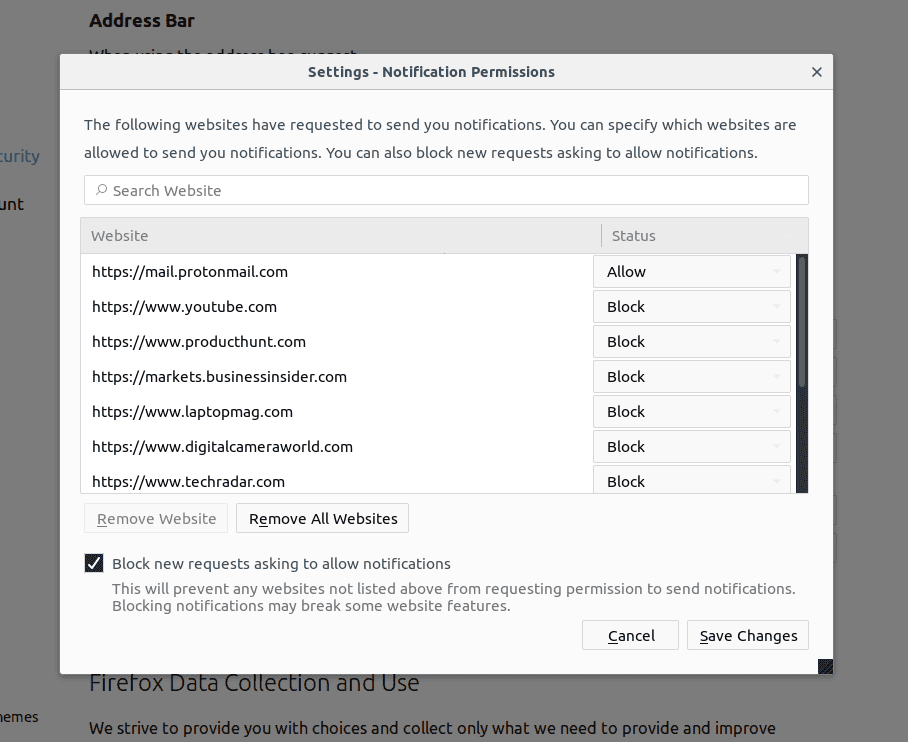
- On the right corner of the screen, you will notice three dots which is the “Menu” button
- Select “Options” and choose “Privacy and Security” in the toolbar present in the left side of the screen
- Slowly scroll down and go to “Permission” section then choose “Settings” option next to “Notifications”
- In the newly opened window, select all the suspicious URLs. Click on the drop-down menu and select “Block”
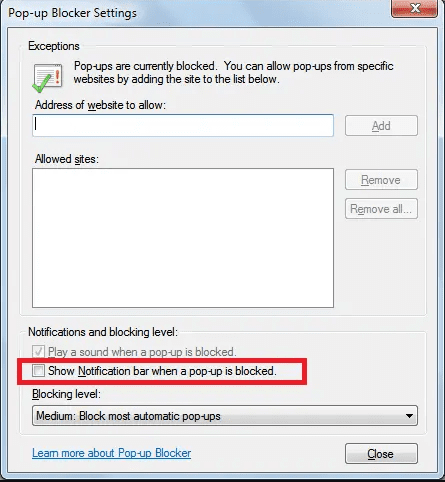
Internet Explorer
- In the Internet Explorer window, select the Gear button present on the right corner
- Choose “Internet Options”
- Select “Privacy” tab and then “Settings” under the “Pop-up Blocker” section
- Select all the suspicious URLs one by one and click on the “Remove” option
Microsoft Edge
- Open the Microsoft Edge and click on the three dots on the right corner of the screen to open the menu
- Scroll down and select “Settings”
- Scroll down further to choose “view advanced settings”
- In the “Website Permission” option, click on “Manage” option
- Click on switch under every suspicious URL
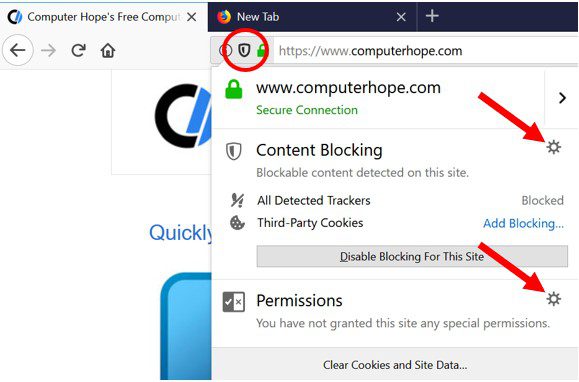
Safari (Mac):
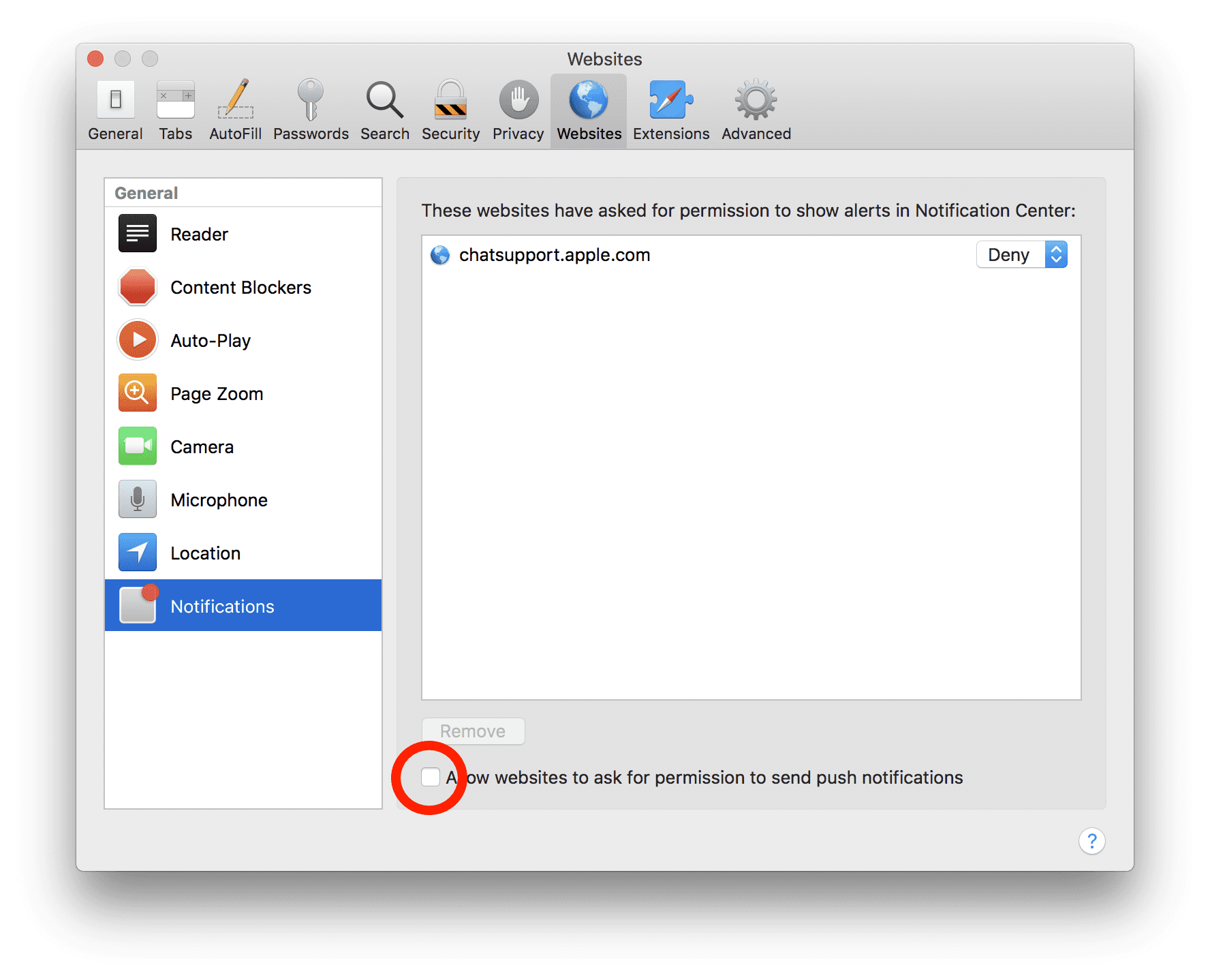
- On the upper right side corner, click on “Safari” and then select “Preferences”
- Go to “website” tab and then choose “Notification” section on the left pane
- Search for the suspicious URLs and choose “Deny” option for each one of them
Manual Steps to Remove Armsvc.exe:
Remove the related items of Armsvc.exe using Control-Panel
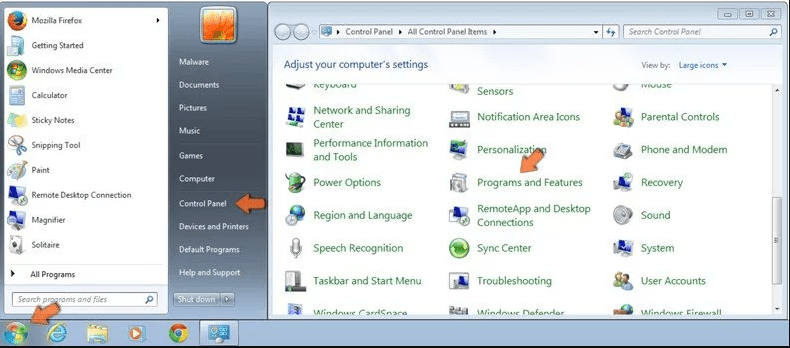
Windows 7 Users
Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
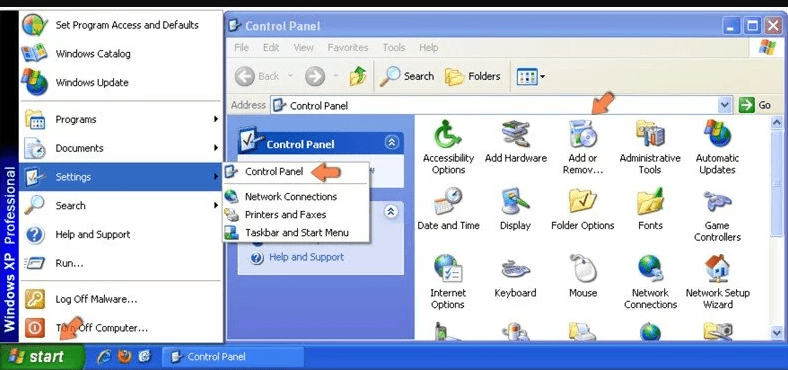
Windows XP Users
Click “Start” and then choose “Settings” and then click “Control Panel”. Search and click on “Add or Remove Program’ option
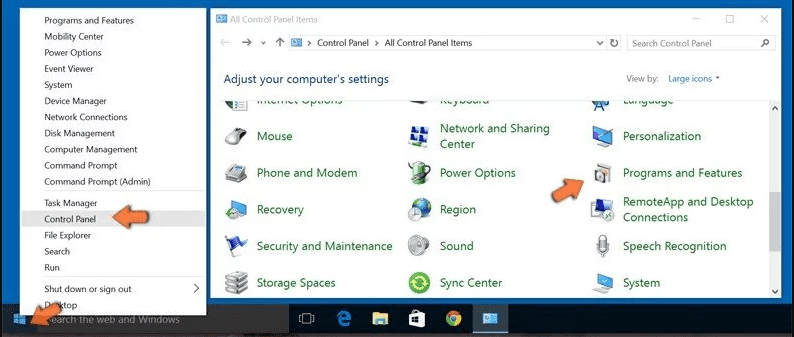
Windows 10 and 8 Users:
Go to the lower left corner of the screen and right-click. In the “Quick Access” menu, choose “Control Panel”. In the newly opened window, choose “Program and Features”
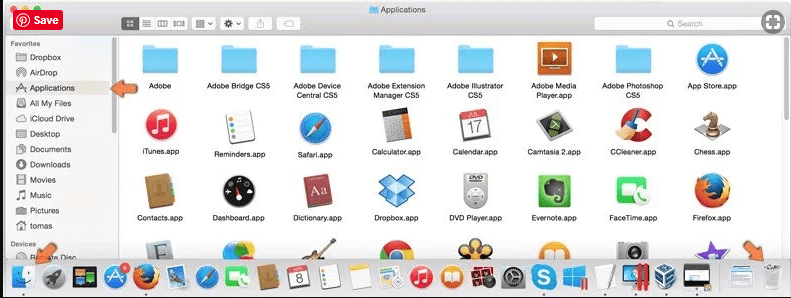
Mac OSX Users
Click on “Finder” option. Choose “Application” in the newly opened screen. In the “Application” folder, drag the app to “Trash”. Right click on the Trash icon and then click on “Empty Trash”.
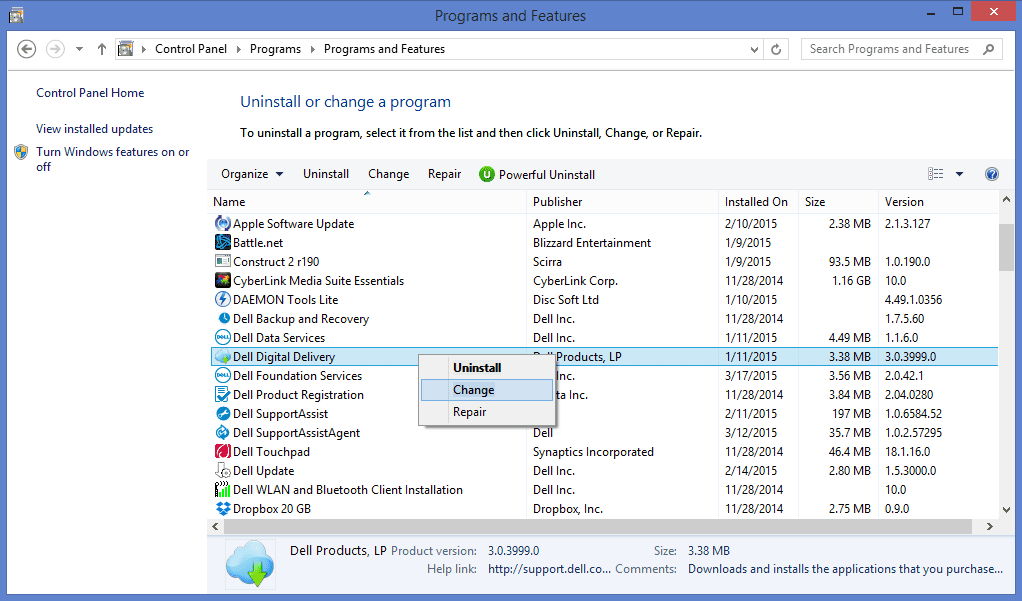
In the uninstall programs window, search for the PUAs. Choose all the unwanted and suspicious entries and click on “Uninstall” or “Remove”.
After you uninstall all the potentially unwanted program causing Armsvc.exe issues, scan your computer with an anti-malware tool for any remaining PUPs and PUAs or possible malware infection. To scan the PC, use the recommended the anti-malware tool.
Special Offer (For Windows)
Armsvc.exe can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Armsvc.exe has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
How to Remove Adware (Armsvc.exe) from Internet Browsers
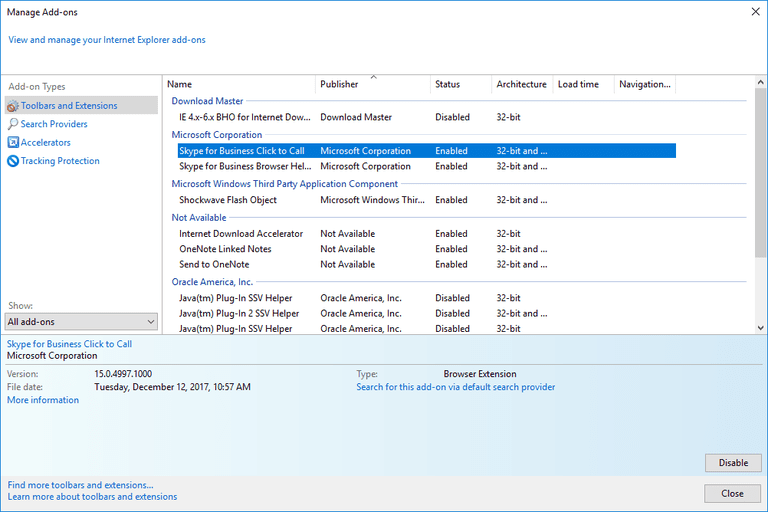
Delete malicious add-ons and extensions from IE
Click on the gear icon at the top right corner of Internet Explorer. Select “Manage Add-ons”. Search for any recently installed plug-ins or add-ons and click on “Remove”.
Additional Option
If you still face issues related to Armsvc.exe removal, you can reset the Internet Explorer to its default setting.
Windows XP users: Press on “Start” and click “Run”. In the newly opened window, type “inetcpl.cpl” and click on the “Advanced” tab and then press on “Reset”.
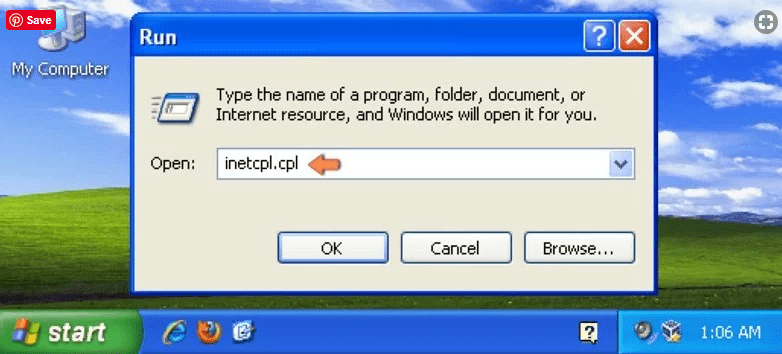
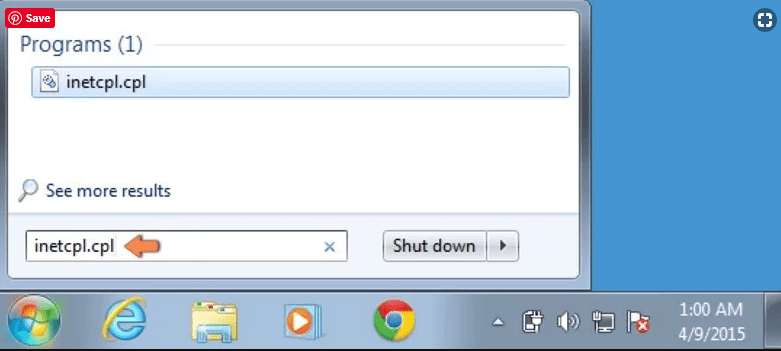
Windows Vista and Windows 7 Users: Press the Windows logo, type inetcpl.cpl in the start search box and press enter. In the newly opened window, click on the “Advanced Tab” followed by “Reset” button.
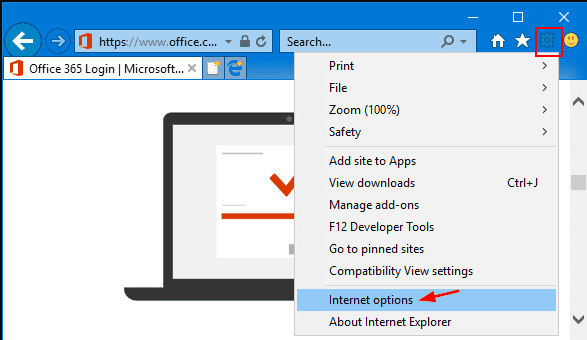
For Windows 8 Users: Open IE and click on the “gear” icon. Choose “Internet Options”
Select the “Advanced” tab in the newly opened window
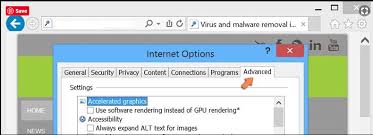
Press on “Reset” option
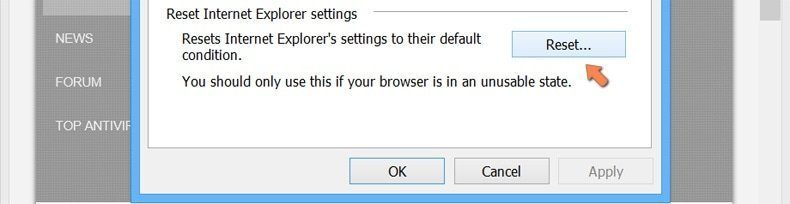
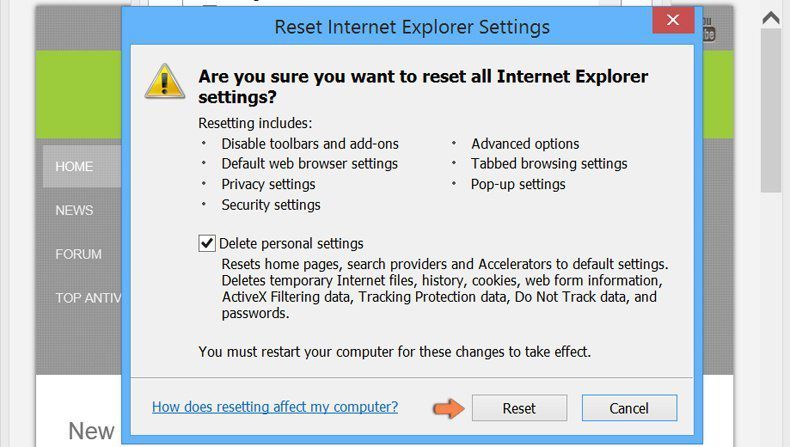
You have to press on the “Reset” button again to confirm that you really want to reset the IE
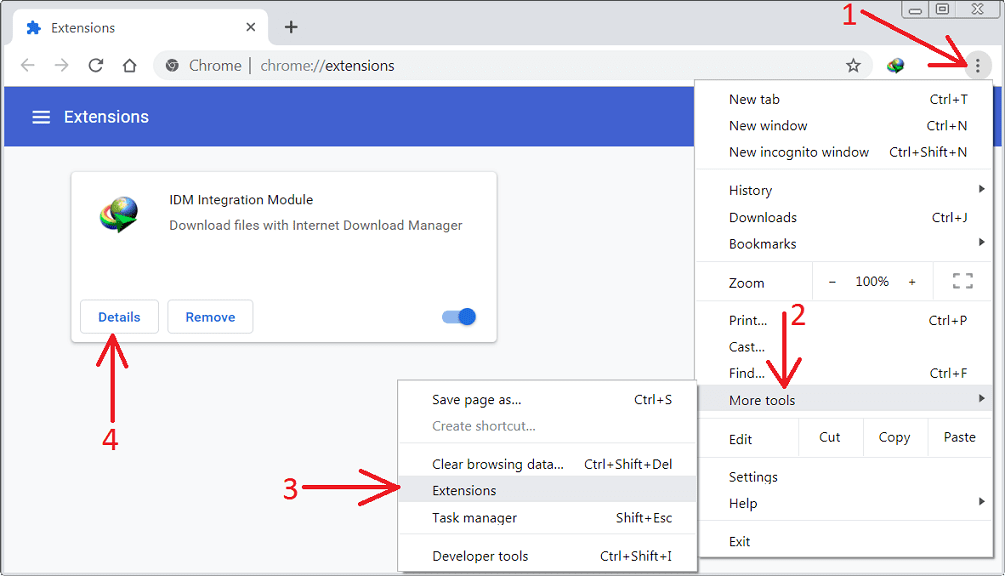
Remove Doubtful and Harmful Extension from Google Chrome
Go to menu of Google Chrome by pressing on three vertical dots and select on “More tools” and then “Extensions”. You can search for all the recently installed add-ons and remove all of them.
Optional Method
If the problems related to Armsvc.exe still persists or you face any issue in removing, then it is advised that your reset the Google Chrome browse settings. Go to three dotted points at the top right corner and choose “Settings”. Scroll down bottom and click on “Advanced”.
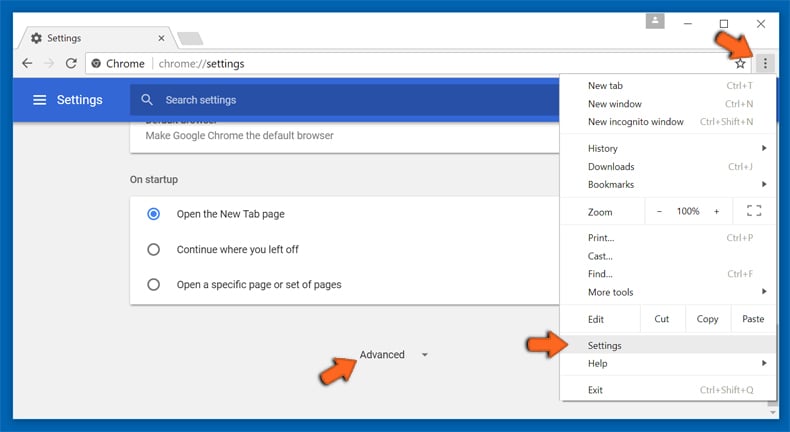
At the bottom, notice the “Reset” option and click on it.
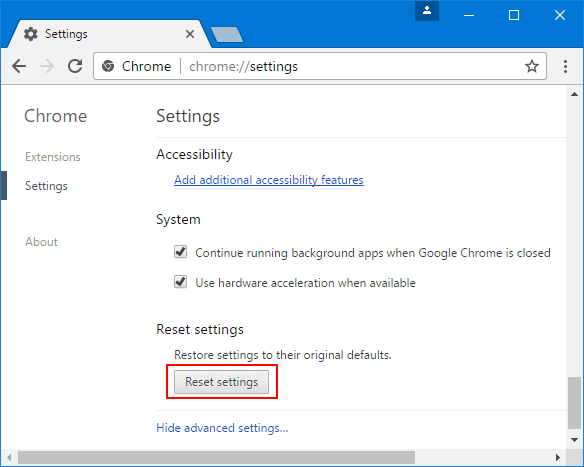
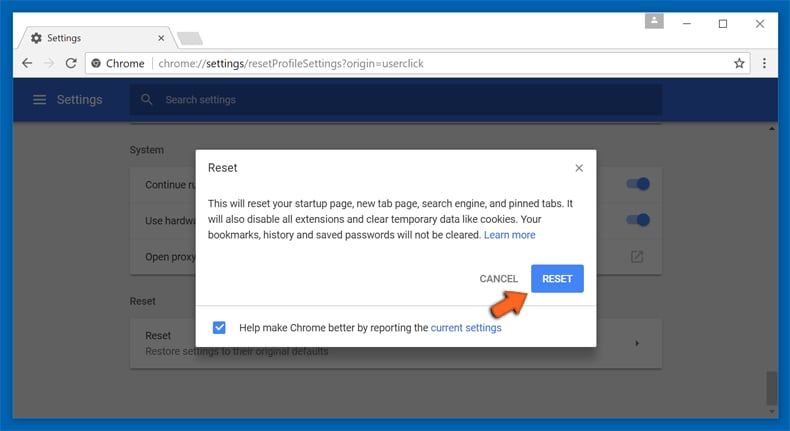
In the next opened window, confirm that you want to reset the Google Chrome settings by click on the “Reset” button.
Remove Armsvc.exe plugins (including all other doubtful plug-ins) from Firefox Mozilla
Open the Firefox menu and select “Add-ons”. Click “Extensions”. Select all the recently installed browser plug-ins.
Optional Method
If you face problems in Armsvc.exe removal then you have the option to rese the settings of Mozilla Firefox.
Open the browser (Mozilla Firefox) and click on the “menu” and then click on “Help”.
Choose “Troubleshooting Information”
In the newly opened pop-up window, click “Refresh Firefox” button
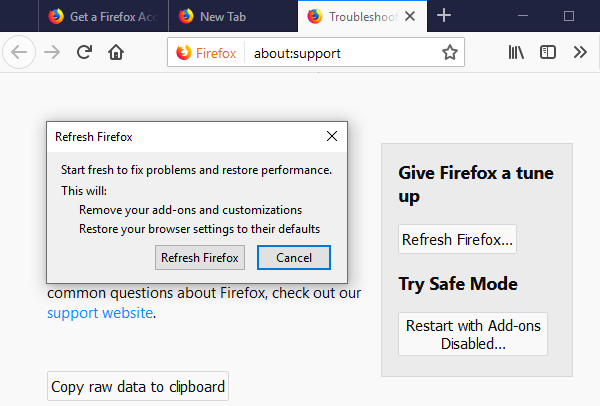
The next step is to confirm that really want to reset the Mozilla Firefox settings to its default by clicking on “Refresh Firefox” button.
Remove Malicious Extension from Safari
Open the Safari and go to its “Menu” and select “Preferences”.
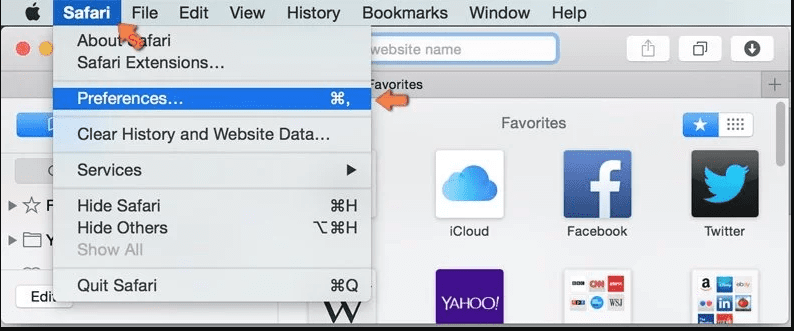
Click on the “Extension” and select all the recently installed “Extensions” and then click on “Uninstall”.
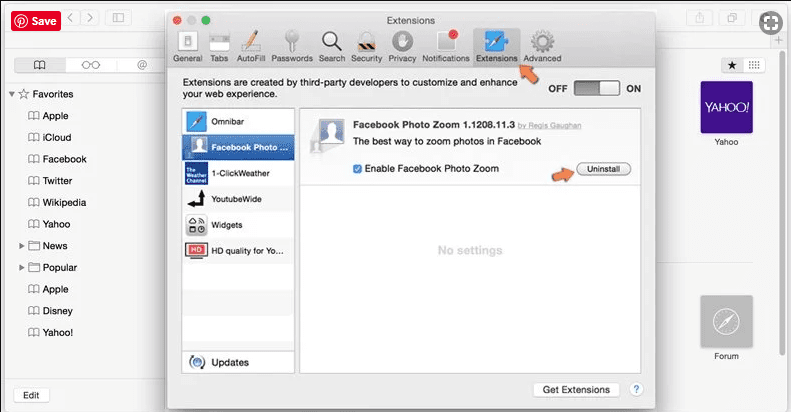
Optional Method
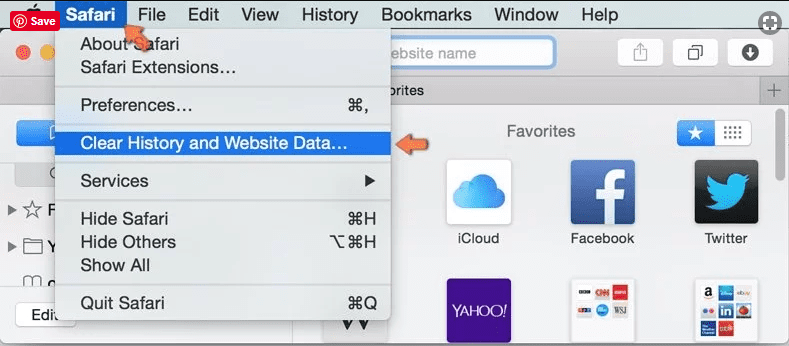
Open the “Safari” and go menu. In the drop-down menu, choose “Clear History and Website Data”.
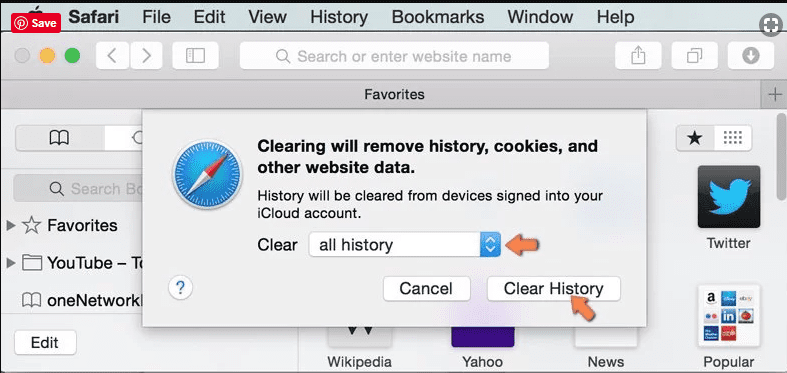
In the newly opened window, select “All History” and then press on “Clear History” option.
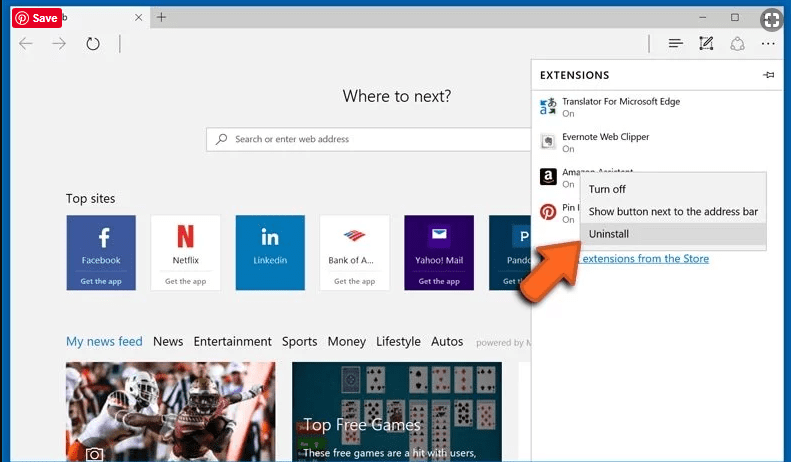
Delete Armsvc.exe (malicious add-ons) from Microsoft Edge
Open Microsoft Edge and go to three horizontal dot icons at the top right corner of the browser. Select all the recently installed extensions and right click on the mouse to “uninstall”
Optional Method
Open the browser (Microsoft Edge) and select “Settings”
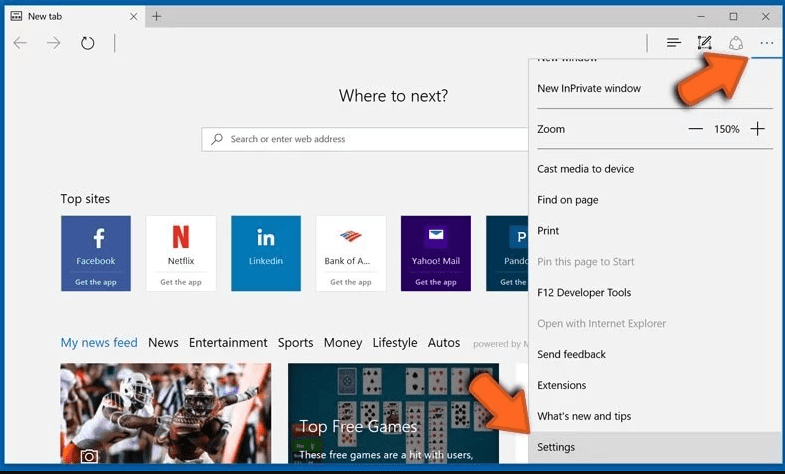
Next steps is to click on “Choose what to clear” button
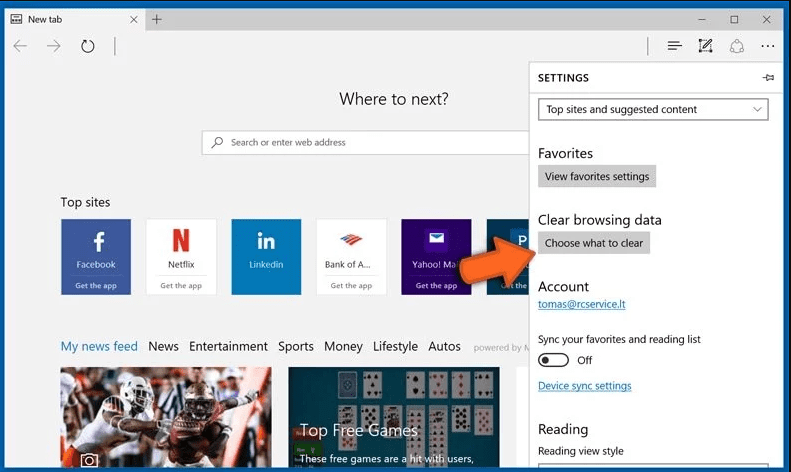
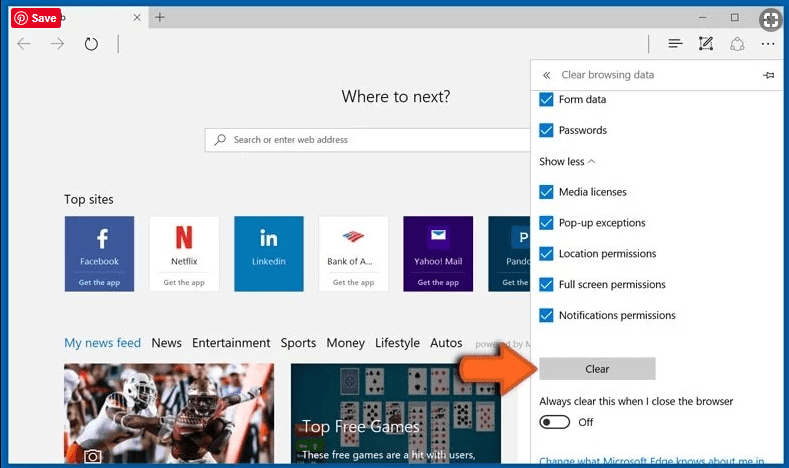
Click on “show more” and then select everything and then press on “Clear” button.
How to Prevent Armsvc.exe Attack?
Although no security measures can guarantee complete protection against malware, there are certain precautions you can take to prevent dreadful cyber threats from infecting your device. Be vigilant while installing free software, and read through the installer’s additional offers carefully.
Users should be cautious when opening emails from unknown senders or any messages that seem suspicious or out of the ordinary. If the sender or address is unfamiliar, or the content is unrelated to anything you are expecting, it is best not to open the message. It is highly unlikely that you could win a prize in a contest you didn’t enter, so be wary of any emails claiming that you won something. If the email subject appears to be related to something you are anticipating, it is important to thoroughly examine all aspects of the message. Scammers often make mistakes, so carefully scrutinizing the content of the email could help you identify any fraudulent activity. Remember, it is always better to err on the side of caution and avoid opening emails or letters that appear suspicious.
It is also crucial to keep all software and security programs up-to-date to prevent vulnerabilities that malware can exploit. Using cracked or unknown programs is a significant risk for Trojan-based attacks. Cybercriminals often distribute Trojans disguised as legitimate software, such as patches or license checks. However, it is challenging to differentiate between trustworthy software and malicious Trojans since some Trojans may even have the functionality that users seek.
To mitigate this risk, it is crucial to avoid using untrusted programs altogether and only download software from reputable sources. Before downloading any program, users should research it thoroughly and read reviews from trusted sources. It is also recommended to consult anti-malware message boards to gather additional information on any software that may raise suspicion. Ultimately, the best defense against Trojan attacks is to exercise caution and avoid downloading software from untrusted sources.
Conclusion
In most cases, the PUPs and adware gets inside the marked PC through unsafe freeware downloads. It is advised that you should only choose developers website only while downloading any kind of free applications. Choose custom or advanced installation process so that you can trace the additional PUPs listed for installation along with the main program.
Special Offer (For Windows)
Armsvc.exe can be creepy computer infection that may regain its presence again and again as it keeps its files hidden on computers. To accomplish a hassle free removal of this malware, we suggest you take a try with a powerful Spyhunter antimalware scanner to check if the program can help you getting rid of this virus.
Do make sure to read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
Special Offer (For Macintosh) If you are a Mac user and Armsvc.exe has affected it, then you can download free antimalware scanner for Mac here to check if the program works for you.
