10/04/2024 10:07:00 AM
The APK Signer Tool is a crucial utility for Android developers and enthusiasts who need to sign APK files for deployment on Android devices. This tool ensures that APKs are properly signed with a cryptographic key, a mandatory requirement for Android apps before they can be installed. The latest version of the APK Signer Tool for Windows introduces new features and improvements to make signing APKs faster and more user-friendly, catering to both beginners and experienced developers.
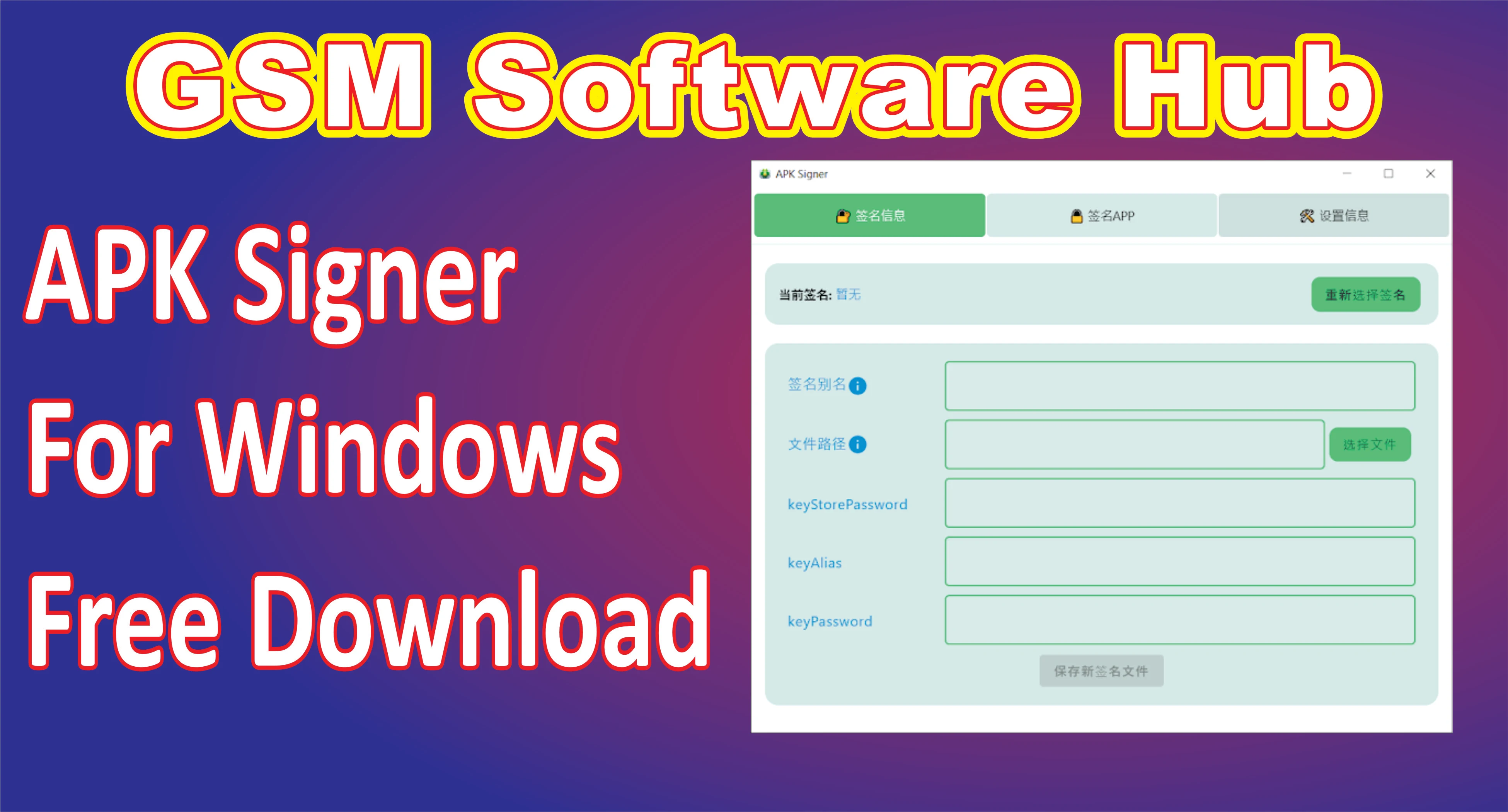
Key Features
- Enhanced User Interface: The tool now offers a more intuitive and simplified user interface. It’s easier to navigate, making the signing process smoother, even for users new to APK development.
- Support for Multiple Key Formats: The update allows users to sign APKs using a wider variety of key formats, including
.jks,.pem, and.pk8. This flexibility means developers can use different types of keystores depending on their preferences or project requirements. - Batch Signing: A standout feature of the latest version is the ability to sign multiple APK files in batch mode. This feature saves significant time for developers who work with numerous APKs at once.
- Support for V1 and V2 APK Signature Schemes: The tool supports both the V1 (Jar Signature) and V2 (Full APK Signature) schemes, ensuring compatibility across different Android versions.
- Cross-Platform Compatibility: Although this is a Windows tool, it offers cross-platform compatibility by generating APKs that can be deployed across various operating systems and devices.
- Error Logs and Debugging: The update includes more detailed error logs and debugging information, making it easier for developers to identify issues and fix them promptly.
| Info | Details |
|---|---|
| Tool Name | Apk Signer Tool |
| Version | (Latest Version) |
| Tool Size | 52.52 MB |
| Password | Free |
| File Hosting By | GSM Software Hub |
| Uploaded By | MS |
How to Use APK Signer Tool for Windows
- Download and Install: Start by downloading the latest version of the APK Signer Tool for Windows from the official website or trusted sources. Install it following the on-screen instructions.
- Prepare Your APK: Make sure the APK you wish to sign is ready. Also, ensure you have the necessary keystore file and passwords.
- Open the APK Signer Tool: Launch the tool and select the APK file you wish to sign.
- Choose Key Format: Select the appropriate key format based on your keystore. Enter the required passwords when prompted.
- Select Signature Scheme: Choose between the V1 and V2 signature schemes, or enable both if needed for compatibility with a wide range of Android devices.
- Sign the APK: Once all fields are filled out, click the “Sign APK” button. The tool will process the APK and display a success message once completed.
- Batch Sign: For batch signing, simply select multiple APKs and follow the same process. The tool will sign each one sequentially.
- Save the Signed APK: After signing, the APK will be ready for deployment. Save it to your desired location.
Conclusion
The latest APK Signer Tool for Windows is an essential asset for Android app developers, offering powerful features like batch signing, support for multiple key formats, and compatibility with both V1 and V2 signature schemes. With its improved user interface and detailed error logs, it simplifies the process of signing APKs, ensuring that they are ready for secure distribution across Android devices. Whether you’re an experienced developer or just starting out, this tool is a must-have for your development toolkit.
Single Click Links Button
Apk Signer Tool
Download Link
Facebook Link
Telegram Link
WhatsApp Link
Uber Apk Signer
A tool that helps to sign, zip aligning and verifying
multiple Android application packages (APKs) with either debug or provided release certificates (or multiple). It
supports v1, v2, v3 Android signing scheme
and v4 Android signing scheme. Easy and convenient debug signing
with embedded debug keystore. Automatically verifies signature and zipalign after every signing.
Main features:
- zipalign, (re)signing and verifying of multiple APKs in one step
- verify signature (with hash check) and zipalign of multiple APKs in one step
- built-in zipalign & debug keystore for convenient usage
- supports v1, v2, v3 and v4 android apk singing scheme
- support for multiple signatures for one APK
- crypto/signing code relied upon official implementation
Basic usage:
java -jar uber-apk-signer.jar --apks /path/to/apks
This should run on any Windows, Mac or Linux machine where JDK8 is installed.
Requirements
- JDK 8
- Currently on Linux 32bit: zipalign must be set in
PATH
Download
Grab jar from the latest Release
Demo
Command Line Interface
-a,--apks <file/folder> Can be a single apk or a folder containing multiple apks. These are used
as source for zipalining/signing/verifying. It is also possible to
provide multiple locations space seperated (can be mixed file folder):
'/apk /apks2 my.apk'. Folder will be checked non-recursively.
--allowResign If this flag is set, the tool will not show error on signed apks, but
will sign them with the new certificate (therefore removing the old
one).
--debug Prints additional info for debugging.
--dryRun Check what apks would be processed without actually doing anything.
-h,--help Prints help docs.
--ks <keystore> The keystore file. If this isn't provided, will tryto sign with a debug
keystore. The debug keystore will be searched in the same dir as
execution and 'user_home/.android' folder. If it is not found there a
built-in keystore will be used for convenience. It is possible to pass
one or multiple keystores. The syntax for multiple params is
'<index>=<keystore>' for example: '1=keystore.jks'. Must match the
parameters of --ksAlias.
--ksAlias <alias> The alias of the used key in the keystore. Must be provided if --ks is
provided. It is possible to pass one or multiple aliases for multiple
keystore configs. The syntax for multiple params is '<index>=<alias>'
for example: '1=my-alias'. Must match the parameters of --ks.
--ksDebug <keystore> Same as --ks parameter but with a debug keystore. With this option the
default keystore alias and passwords are used and any arguments relating
to these parameter are ignored.
--ksKeyPass <password> The password for the key. If this is not provided, caller will get a
user prompt to enter it. It is possible to pass one or multiple
passwords for multiple keystore configs. The syntax for multiple params
is '<index>=<password>'. Must match the parameters of --ks.
--ksPass <password> The password for the keystore. If this is not provided, caller will get
a user prompt to enter it. It is possible to pass one or multiple
passwords for multiple keystore configs. The syntax for multiple params
is '<index>=<password>'. Must match the parameters of --ks.
-l,--lineage <path> The lineage file for apk signer schema v3 if more then 1 signature is
used. See here https://bit.ly/2mh6iAC for more info.
-o,--out <path> Where the aligned/signed apks will be copied to. Must be a folder. Will
create, if it does not exist.
--overwrite Will overwrite/delete the apks in-place
--skipZipAlign Skips zipAlign process. Also affects verify.
-v,--version Prints current version.
--verbose Prints more output, especially useful for sign verify.
--verifySha256 <cert-sha256> Provide one or multiple sha256 in string hex representation (ignoring
case) to let the tool check it against hashes of the APK's certificate
and use it in the verify process. All given hashes must be present in
the signature to verify e.g. if 2 hashes are given the apk must have 2
signatures with exact these hashes (providing only one hash, even if it
matches one cert, will fail).
-y,--onlyVerify If this is passed, the signature and alignment is only verified.
--zipAlignPath <path> Pass your own zipalign executable. If this is omitted the built-in
version is used (available for win, mac and linux)
Examples
Provide your own out directory for signed apks
java -jar uber-apk-signer.jar -a /path/to/apks --out /path/to/apks/out
Only verify the signed apks
java -jar uber-apk-signer.jar -a /path/to/apks --onlyVerify
Sign with your own release keystore
java -jar uber-apk-signer.jar -a /path/to/apks --ks /path/release.jks --ksAlias my_alias
Provide your own zipalign executable
java -jar uber-apk-signer.jar -a /path/to/apks --zipAlignPath /sdk/build-tools/24.0.3/zipalign
Provide your own location of your debug keystore
java -jar uber-apk-signer.jar -a /path/to/apks --ksDebug /path/debug.jks
Sign with your multiple release keystores (see below on how to create a lineage file)
java -jar uber-apk-signer.jar -a /path/to/apks --lineage /path/sig.lineage --ks 1=/path/release.jks 2=/path/release2.jks --ksAlias 1=my_alias1 2=my_alias2
Use multiple locations or files (will ignore duplicate files)
java -jar uber-apk-signer.jar -a /path/to/apks /path2 /path3/select1.apk /path3/select2.apk
Provide your sha256 hash to check against the signature:
java -jar uber-apk-signer.jar -a /path/to/apks --onlyVerify --verifySha256 ab318df27
Process Return Value
This application will return 0 if every signing/verifying was successful, 1 if an error happens (e.g. wrong arguments) and 2 if at least 1 sign/verify process was not successful.
Debug Signing Mode
If no keystore is provided the tool will try to automatically sign with a debug keystore. It will try to find on in the following locations (descending order):
- Keystore location provided with
--ksDebug debug.keystorein the same directory as the jar executabledebug.keystorefound in the/user_home/.androidfolder- Embedded
debug.keystorepackaged with the jar executable
A log message will indicate which one was chosen.
Zipalign Executable
Zipalign is a tool developed by Google to optimize zips (apks). It is needed if you want to upload it to the Playstore otherwise it is optional. By default, this tool will try to zipalign the apk, therefore it will need the location of the executable. If the path isn’t passed in the command line interface, the tool checks if it is in PATH environment variable, otherwise it will try to use an embedded version of zipalign.
If --skipZipAlign is passed no executable is needed.
v1, v2 and v3 Signing Scheme
Android 7.0 introduces APK Signature Scheme v2, a new app-signing scheme that offers faster app install times and more protection against unauthorized alterations to APK files. By default, Android Studio 2.2 and the Android Plugin for Gradle 2.2 sign your app using both APK Signature Scheme v2 and the traditional signing scheme, which uses JAR signing.
APK Signature Scheme v2 is a whole-file signature scheme that increases verification speed and strengthens integrity guarantees by detecting any changes to the protected parts of the APK. The older jarsigning is called v1 schema.
APK Signature Scheme v3 is an extension to v2 which allows a new signature lineage feature for key rotation, which basically means it will be possible to change signature keys.
Signature Lineage File in Schema v3
This tool does not directly support the creation of lineage files as it is considered a task done very rarely. You can create a lineage file with a sequence of certificates with Google’s apksigner rotate and apply it as -- lineage arguments when signing with multiple keystores:
apksigner rotate --out sig.lineage \
--old-signer --ks debug1.keystore --ks-key-alias androiddebugkey \
--new-signer --ks debug2.keystore --ks-key-alias androiddebugkey
java -jar uber-apk-signer.jar -a /path/to/apks --lineage sig.lineage (...)
Signed Release Jar
The provided JARs in the GitHub release page are signed with my private key:
CN=Patrick Favre-Bulle, OU=Private, O=PF Github Open Source, L=Vienna, ST=Vienna, C=AT
Validity: Thu Sep 07 16:40:57 SGT 2017 to: Fri Feb 10 16:40:57 SGT 2034
SHA1: 06:DE:F2:C5:F7:BC:0C:11:ED:35:E2:0F:B1:9F:78:99:0F:BE:43:C4
SHA256: 2B:65:33:B0:1C:0D:2A:69:4E:2D:53:8F:29:D5:6C:D6:87:AF:06:42:1F:1A:EE:B3:3C:E0:6D:0B:65:A1:AA:88
Use the jarsigner tool (found in your $JAVA_HOME/bin folder) folder to verify.
Build with Maven
Use the Maven wrapper to create a jar including all dependencies
Checkstyle Config File
This project uses my common-parent which centralized a lot of
the plugin versions as well as providing the checkstyle config rules. Specifically they are maintained in checkstyle-config. Locally the files will be copied after you mvnw install into your target folder and is called
target/checkstyle-checker.xml. So if you use a plugin for your IDE, use this file as your local configuration.
Tech-Stack
- Java 8
- Maven
License
Copyright 2016 Patrick Favre-Bulle
Licensed under the Apache License, Version 2.0 (the «License»);
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an «AS IS» BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
ApkSigner Tool | For Windows & Mac and Linux | 2024
Some APKs created at work lack signatures, causing issues during 360 reinforcement. However, the signature process provided by 360 reinforcement is complex. To simplify this, we’ve developed a small tool with a graphical interface for signing APK files. This tool is compatible with macOS, Windows, and Linux, and is built using JetBrains Compose Multiplatform.
.webp)
Main Functions:
Our tool simplifies APK signing with its user-friendly interface, supporting management of multiple signatures and one-click signing. It’s important to note that it doesn’t create signature files; users must prepare a signature file (usually in .keystore or .jks format), along with the ‘apksigner’ and ‘zipalign’ files from the appropriate Android SDK build-tools version, and ensure a Java development environment with JAVA_HOME configuration for ‘apksigner’.
How to Use?
You can employ our tool in various ways: by installing system-specific software packages like .dmg or .msi files (the preferred method), compiling the source code, or running the jar package. For Windows users, installation is straightforward – just execute the setup file, and afterward, locate the executable files at «C:\Program Files\ApkSigner».
Disclaimer:
This tool does not generate signature files and requires users to prepare necessary files and configurations beforehand.
Users are advised to handle sensitive signature files securely to prevent unauthorized access.
While efforts have been made to ensure the reliability and functionality of the tool, users are encouraged to use it with caution and to report any issues or concerns for improvement.
The tool is provided as-is, without warranties of any kind, and the developers shall not be held liable for any damages or loss arising from its use.
Usage of the tool implies acceptance of these terms and conditions.
The developers reserve the right to modify or discontinue the tool at any time.
| Info. | Details |
|---|---|
| Software Name: | ApkSigner Tool |
| Version: | 2024 |
| Password: | Free |
| File Size: | 49. MB |
| Files Hosted By: | https://misterrepack.blogspot.com/ |
Conclusion:
ApkSigner Tool provides a straightforward solution for signing APKs, enhancing efficiency and simplifying the process. Its graphical interface ensures ease of use across different operating systems. By streamlining APK signing, it alleviates the complexities often associated with this task.
Get This Tool:
Время на прочтение3 мин
Количество просмотров12K

Короткий практический пример как разобрать apk приложение, что-то в нем изменить и собрать обратно в среде windows без использования android studio. Статья подойдет для новичков, сложного ничего не будет. Будем изменять (русифицировать) не полностью русифицированное приложение для видеокамеры ordro pro ep8.
На написание статьи подтолкнула другая статья на Хабр — habr.com/ru/articles/780694
Однако там описано, на мой взгляд, недостаточно подробно, новичкам будет тяжело. Кроме того, в приведенной статье использовались средства сборки-разборки под Linux, здесь будет windows-вариант.
В качестве цели для исследования будет выступать мобильное приложение в формате apk для камеры ordro pro ep8.
При эксплуатации это приложение демонстрирует вполне разумную локализацию, но в некоторых моментах все-таки «проглядывает оригинал» на иностранном языке:

Разбираем apk.
Самое простое, что можно сделать на старте — просто переименовать apk в zip и посмотреть на получившийся архив приложения:

Такой трюк позволяет сформировать общее представление о приложении, но не более. В своем содержимом файлы все равно будут иметь нечитаемый код:

Поэтому понадобится утилита apktool.
Устанавливать (инсталлировать) ее не нужно, только положить рядом с apk. Может также потребоваться java.
Проверить, установлена ли java можно так:

Далее команда apktool d com-ordro.apk полностью разберет приложение:

После этого можно наблюдать в том числе smali, о которых говорилось в уже упомянутой статье:

Файлов много, найти текст, который хотелось русифицировать, непросто. Поэтому пойдем по пути наименьшего сопротивления. Возьмем скриншот иероглифа из картинки приложения, переведем в текст и поищем этот текст по всем файлам в папках:
Как не сложно догадаться для каждого языка имеются соответствующие папки, в одной из которых и нашелся иероглиф. Нас интересует «папка для русского языка» (values-ru):

В файле находим частично непереведенные названия вкладок, кнопок и т.д. Изменяем текст на правильный:

Не лишним будет заглянуть в иные, рядом расположенные файлы:

Собираем обратно в apk.
После того, как все необходимые изменения внесены, можно приступить к сборке нового apk.
Сборка apk осуществляется также apktool командой apktool b com-ordro, где в качестве аргумента — папка с файлами, в которых происходили изменения.
Готовый файл apk будет в папке dist:

Однако, если данный файл перенести на мобильный и попытаться установить — попытка завершится неудачей. Необходимы дополнительные манипуляции с файлом apk перед переносом.
Необходимо выполнить выравнивание содержимого apk (aligning) и его подпись (sign).
Здесь частично будут использованы сведения из статьи medium.com/@sandeepcirusanagunla/decompile-and-recompile-an-android-apk-using-apktool-3d84c2055a82
Но так как, сведения из статьи немного устарели, как например, в части алгоритма шифрования, будут использоваться немного иные команды.
Алгоритм следующий.
1.Создаем ключ-пару, который «подпишем» наш apk:
keytool -genkeypair -keyalg DSA -keysize 2048 -keystore my-release-key.keystore -alias alias_name -validity 10000Пароль можно задать любой как и данные, ввод которых можно пропускать, нажимая enter.

На выходе рядом с apk появится файл — ключ-пара:
2. Подпишем файл(signing), используя нашу ключ-пару.
jarsigner -verbose -sigalg SHA256withDSA -digestalg SHA256 -keystore my-release-key.keystore com-ordro.apk alias_nameВ терминале увидим при успешном выполнении примерно следующий вывод:

Однако, если проверить подписанное приложение jarsigner -verify -verbose -certs com-ordro.apk может выскочить ошибка, которая в дальнейшем не позволит установиться приложению на мобильном:

Можно пойти по длинному пути и исправить ошибку с ключ-парой и сертификатами, но мы поступим проще. Подпишем и выровняем apk с помощью uber-apk-signer.
Скачав uber-apk-signer.jar в папку с готовым apk, выполним команду:
java -jar uber-apk-signer.jar -a com-ordro.apk
*Данная команда заменяет собой 2 предыдущих шага с выравниванием и подписанием.
Она использует все тот же zipalign.exe и создает ключ-пару. Если zipalign нет, то его нужно скачать и добавить его в PATH.

На выходе получим готовый apk, который уже можно устанавливать на мобильном:

Результат:

Спасибо за внимание.
Приложение до и после, а также файлы для работы можно скачать — здесь.
ps. для тех кого интересует вопрос (как и меня) собственно по камере — можно ли с нее получать поток, в обход мобильного приложения — да, возможно rtsp:\\192.168.1.1:554
Apk Signer Tool: A Graphical Interface for Signing APKs on Windows and Mac
Introduction:
Some APKs packaged at work prompt «no signature» during 360 reinforcement, but the signature process provided by 360 reinforcement is too cumbersome, so we developed a small tool to use a graphical interface to sign APK files. This software is developed based on Jet Brains Compose Multiplatform and supports macOS, Windows, and Linux.

Main Function:
This APP is designed to facilitate you to operate signed APKs through a graphical interface. It supports management and switching of multiple signatures, one-click signing of APKs, etc. The tool does not provide the function of generating signature files. To use this tool, you need to prepare the following in advance:
How To Use:
- Run system-specific software packages such as .dmg or .mist
- Compile source code
- Run the jar package
Conclusion:
The tool is a Windows command-line application that runs in PowerShell and creates a wrapper around your Android app. After the app is wrapped, you can change the app’s functionality by configuring mobile application management policies in Intune. Before running the tool, review Security considerations for running the App Wrapping Tool. To download the tool, go to the Microsoft Intune App Wrapping Tool for Android on GitHub.
