In this guide, we will show you a couple of methods to fix the ‘adbd cannot run as root in production builds’ error. adb root command allows you to “adb push/pull” to system directories and run numerous important commands as “adb remount” or “adb disable-verify”.
However, quite a few users have voiced their concern that they are trying to run level commands but are being greeted with the aforementioned error. This is happening in spite of the fact that their device is rooted via Magisk. So if you are also in the same boat, then this guide is here to help you out. Follow along for the fix.
Table of Contents
It is recommended that you try out each of the below-mentioned workarounds and then see which one spells out success. So with that in mind, let’s get started. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
FIX 1: Via Magisk Module
This module will only work if “adbd” is located in /system/bin (the actual binary, not the symlink) rather than in /sbin (you could verify the same root supported File Explorer) and it should be an arm64 device [use CPU Z to verify the same].
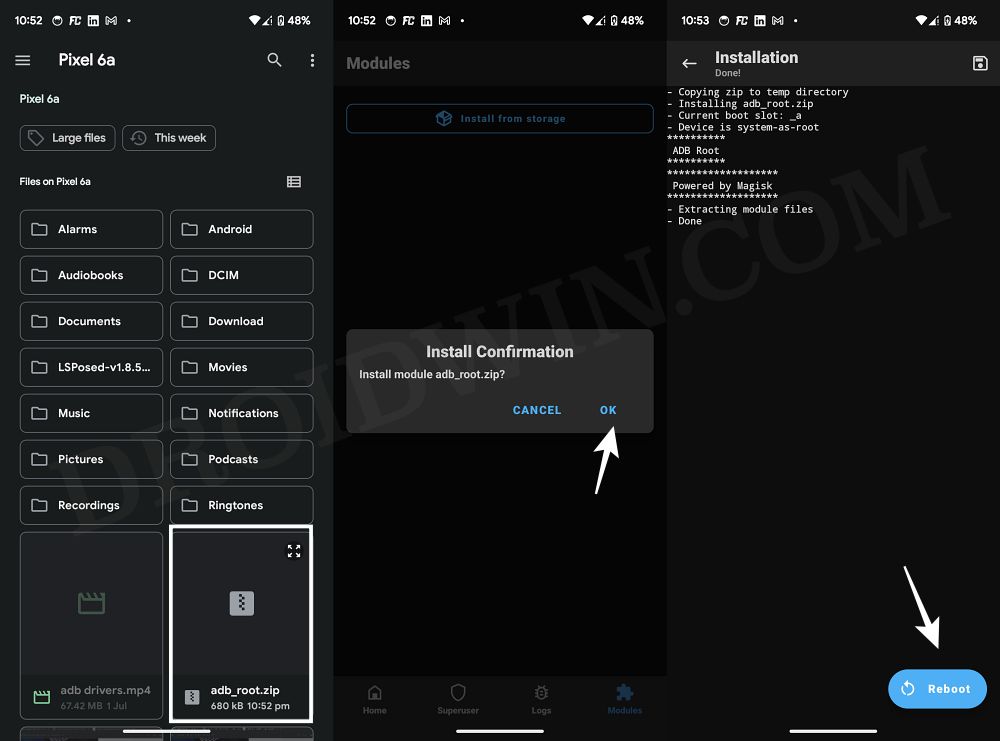
- First off, download the module onto your device from GitHub.
- Then launch Magisk, go to Modules, select the module, and tap OK.
- Now wait for the module to be flashed. Once done, hit Reboot.
- Check if it fixes the ‘adbd cannot run as root in production builds’ error.
FIX 2: Using the su Command
The adbd from the CMD window executes commands on your device as user:shell. If you want the adbd to act as user:root, then you’ll have to execute adb root. However, it might not be possible on stock ROMs to grant the adbd root permissions [even if the other device is rooted with Magisk, it’s still a production build!]. So you could opt for an alternate route by executing the below two commands and see if they get the job done.
- First off, download and extract Android SDK Platform Tools on your PC.
- Then enable USB Debugging on your device and connect it to your PC.
- Now open CMD inside platform tools and type in the following commands
adb shell su
- You will get a Magisk request on your device, tap Grant.
- Finally, execute the desired command and check out the result.
That’s it. These were the two different methods that should help you fix the adbd cannot run as root in production builds error. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
- Fix ADB cannot connect to Daemon with OpenCore Legacy Patcher
- Fix ADB Push Remote Write Failed: No space left on device
- Format Data/Factory Reset Android via ADB Command
- How to Set up and Run Shizuku [Wireless Debugging, Root, ADB]
Introduction
In this guide, we separated adb commands from adb shell commands and saw their differences. In this other guide, we explained the various build variants in Android; development (eng and userdebug) build and production/user build. You can go through the guides first before proceeding because we won’t be talking about them in detail here.
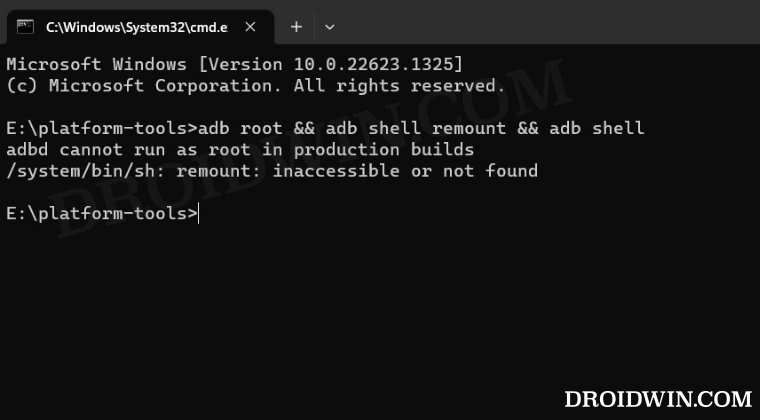
Some adb commands and adb shell commands require root to run, this means your device should be rooted, if not, you can’t execute such commands – a good example where commands require root is when interacting with system files and directories. In the case of adb shell, you need to grant root to the interactive shell on your Android device. This is done simply by running the adb shell command adb shell su. When it comes to adb, things are complicated here. Granting root to the interactive shell (adb shell su) only works with adb shell commands and not adb commands. In the case of adb commands, it is the adbd (adb daemon) that needs to run as root using the command adb root. The problem here is that this is only possible in development builds (eng and userdebug builds) and not with production builds (also called user builds). Since our devices all come with production builds, this means we all should get the error message adbd cannot run as root in production builds when we try to give root to the adbd using the command adb root.
How then is it possible to start the adbd with root access? This is exactly what we will be seeing in this guide. You will see the various tricks and hacks to run the adbd as root, just ride along.
Why Run adbd With Root Rights?
We are familiar with the adb pull and adb push commands. Using these commands, you can easily transfer files between a computer and the internal storage of your device. It’s also possible to do such operations with the system root directory – but adbd running as root is the thing here. If adbd is running as root (insecure mode), then you can easily make the /system partition and other ro partitions as rw using adb (the command is adb remount) and you will be able to use the adb pull and adb push commands in the system root directory as well as use other commands like adb disable-verity.
Note that if you are running a custom kernel or development Android build, it’s likely that it already implements this functionality. But if you are running a stock (made by the phone manufacturer) kernel or production build on your device, it’s obvious that adbd is running in secure mode, even if you are rooted. If the later case applies to you, then follow the methods below to run adbd in insecure mode – all you need is a rooted device.
Method 1: Using Chainfire’s adbd Insecure App
This app might only be compatible with older Android versions (maybe 5 and below). The changes the app makes are not permanent, so after a reboot, all modifications are reversed requiring you to set up the app again. For simplicity and if you want an automatic setup after each reboot, the app includes a toggle for this – but USB debugging must be ON always. Let’s see how to use this app to run adbd in root mode:
— Root your device
— Enable USB debugging
— Download and install the latest version of adbd Insecure app for free here. You can as well download the app from Play Store but it’s a paid app there – you can do this to support the developer.
— Launch the app, grant root and tick Enable insecure adbd. The patching will start right away and when done, you will see Binary: Insecure under the Current status section. If you want automatic patching after a reboot (because changes will be reversed), consider ticking Enable at boot.

— You can now test things out by running the command adb root. If you don’t get the adbd cannot run as root in production builds error or you get adbd is already running as root, then you got success. If things aren’t successful, then you have to try the next method.

— Note that if you have USB connected when the app activates or deactivates adbd root mode, you may need to unplug/replug the cable or run adb kill-server, then adb start-server on your computer before adb will work again.
— If this app fails to work and instead causes issues like your computer doesn’t recognize your device and other adb or USB debugging issues, then either reverse the patching, reboot your device or uninstall the app.
Method 2: Using ADB Root Module
This is a Magisk module that works on Android 9 and 10 (might not work on lower and higher versions). The module works on arm64 devices only.
For safety, don’t forget to disable the module once you’ve done all the things you need. Don’t use it constantly.
The module provides its own adbd binary, which is the binary obtained from AOSP sources with the following patch that disables props checks and usb auth:
diff --git a/adb/daemon/main.cpp b/adb/daemon/main.cpp
index d064d0d..a520bfd 100644
--- a/adb/daemon/main.cpp
+++ b/adb/daemon/main.cpp
@@ -51,48 +51,11 @@
static const char* root_seclabel = nullptr;
static bool should_drop_capabilities_bounding_set() {
-#if defined(ALLOW_ADBD_ROOT)
- if (__android_log_is_debuggable()) {
- return false;
- }
-#endif
- return true;
+ return false;
}
static bool should_drop_privileges() {
-#if defined(ALLOW_ADBD_ROOT)
- // The properties that affect `adb root` and `adb unroot` are ro.secure and
- // ro.debuggable. In this context the names don't make the expected behavior
- // particularly obvious.
- //
- // ro.debuggable:
- // Allowed to become root, but not necessarily the default. Set to 1 on
- // eng and userdebug builds.
- //
- // ro.secure:
- // Drop privileges by default. Set to 1 on userdebug and user builds.
- bool ro_secure = android::base::GetBoolProperty("ro.secure", true);
- bool ro_debuggable = __android_log_is_debuggable();
-
- // Drop privileges if ro.secure is set...
- bool drop = ro_secure;
-
- // ... except "adb root" lets you keep privileges in a debuggable build.
- std::string prop = android::base::GetProperty("service.adb.root", "");
- bool adb_root = (prop == "1");
- bool adb_unroot = (prop == "0");
- if (ro_debuggable && adb_root) {
- drop = false;
- }
- // ... and "adb unroot" lets you explicitly drop privileges.
- if (adb_unroot) {
- drop = true;
- }
-
- return drop;
-#else
- return true; // "adb root" not allowed, always drop privileges.
-#endif // ALLOW_ADBD_ROOT
+ return false;
}
static void drop_privileges(int server_port) {
@@ -183,9 +146,7 @@ int adbd_main(int server_port) {
// descriptor will always be open.
adbd_cloexec_auth_socket();
- if (ALLOW_ADBD_NO_AUTH && !android::base::GetBoolProperty("ro.adb.secure", false)) {
- auth_required = false;
- }
+ auth_required = false;
adbd_auth_init();
diff --git a/adb/services.cpp b/adb/services.cpp
index 8518f2e..24f9def 100644
--- a/adb/services.cpp
+++ b/adb/services.cpp
@@ -78,12 +78,6 @@ void restart_root_service(int fd, void *cookie) {
WriteFdExactly(fd, "adbd is already running as root\n");
adb_close(fd);
} else {
- if (!__android_log_is_debuggable()) {
- WriteFdExactly(fd, "adbd cannot run as root in production builds\n");
- adb_close(fd);
- return;
- }
-
android::base::SetProperty("service.adb.root", "1");
WriteFdExactly(fd, "restarting adbd as root\n");
adb_close(fd);The binary is required because adb root is usually disabled in compile time by most vendors.
— You should be rooted.
— Download the latest version of the module here.
— Flash it in Magisk and reboot your device.
— You can now test things out by running the command adb root. If you don’t get the adbd cannot run as root in production builds error or you get adbd is already running as root, then you got success. If things aren’t successful, then you have to try the next method.
Method 3: Editing The default.prop File
This method should work for development builds. By default, you should be able to get adbd running as root in eng and userdebug builds but in case this doesn’t happen, then this method should definitely let adbd run as root.
— You should be rooted.
— Go to the system root directory and open the file default.prop in a text or code editor. If adbd wasn’t running as root it was because ro.debuggable was set to 0. Replace 0 with 1 (i.e ro.debuggable=1) and save the file, then reboot your device.
— Test to see that adbd is now running as root. ro.debuggable=1 tells adbd it’s allowed to run as root. This may work, but if it doesn’t, it’s probably because the version of Android you’re using wasn’t compiled with the ALLOW_ADBD_ROOT flag, and the adbd code isn’t configured to check the ro.debuggable setting – which might be the case in production builds.
— Note that the default.prop file can be found in other areas like /vendor but that is not the one you need (it won’t even have the ro.debuggable setting). In my case, the required default.prop file was located as /default.prop as you can see in the photo above.
Method 4: Patching The adbd Binary To Run As Root
Using this method, you can also get luck if the others have failed – but it might only work on older Android versions. You have to extract and unpack the boot image on your device in order to get the adbd binary. You need to Google around a bit how to extract the boot image in case you don’t know – I have even written an article how it’s done if your device comes with a MediaTek chipset (see here). An easier way is downloading the stock firmware of the current build on your device – sometimes, you can come across boot images of specific devices that have been uploaded online – if you are lucky to see that of your device, the boot image should be the same build as that on your device. After getting hold of the boot image, you need to unpack it. There are many tools available for unpacking/repacking the boot image. Let’s consider the magiskboot and AIK tools here.
Magiskboot:
You can find the magiskboot tool in the Magisk zip in some of the released Magisk versions here. In my case, I got it under Magisk v21.4 (listed as Magisk-v21.4.zip). It is also found under Magisk v21.3 (listed as Magisk-v21.3.zip) and others. You need to click on Assets below any of the sections to display a dropdown list for the download. After downloading, extract it and open the extraction folder. The tool will be located in arm and x86 subfolders – use any depending on your chipset. Not that the common subfolder contains the magisk.apk that you can install manually (as seen in photo three below – click any photo to enlarge).
Another way of getting the tool is when you rooted your device using the Magisk versions that have the Magisk zip. The tool will be installed in /data/adb/magisk [Did you know? magisk modules are installed in /data/adb/modules].

To unpack the boot image and ramdisk, the respective commands are:
magiskboot unpack boot.img magiskboot cpio ramdisk.cpio extract
The adbd binary is located in the sbin directory of ramdisk (might not be present on some boot images). You can then use Ghidra or Hex Editor to modify the binary as explained here. After doing everything, you need to use magiskboot to patch your ramdisk, and package up a new boot image. The repack command should create a new-boot.img file, that you can upload back to your Android device.
magiskboot cpio ramdisk.cpio "add 750 sbin/adbd patched_adbd" magiskboot repack boot.img
AIK Tool:
The Android Image Kitchen tool will also lets you unpack the boot image. You will get the ramdisk folder containing the sbin subfolder where the adbd binary is located. You can then skip to this section to modify the binary. After that, you need to repack a new boot image that you can upload back to your Android device. See how to use the AIK tool here.
Others:
There are also many other tools that you can use to unpack/repack boot images e.g carliv image kitchen, mkbootimg, abootimg, etc
Rooted Devices:
Another way of getting the adbd binary is if you are rooted. Having a root file manager, the binary is located in /system/bin or /bin. If you don’t see it there, check /sbin. First make a backup of the binary to a save place. Now move it to the internal storage and do the editing as explained here. After editing the binary, move it back to its location and set permission as it was previously (usually 755 or rwxr-xr-x). Reboot your device. If things don’t work or you face issues, delete the edited binary and replace with the backup you made earlier. Set permission and reboot.
Patching The adbd Binary
Like this guide and this one will suggest, you can easily edit the binary in Ghidra or Hex Editor. Note that Hydra doesn’t do a great job at directly modifying ARM binaries, so consider using a generic hex editor like HxD in such a case.
— The first guide is for Android versions older than Nougat where you have to search for the Local port disabled string, or 0x7d0, which is the shell user’s id in hex. This should bring you to the part of the code where adbd switches from root to the shell user. The goal here is to comment out that code, so the program never stops running as root.
// Don't run as root if running in secure mode.
if (should_drop_privileges()) {
drop_capabilities_bounding_set_if_needed();
minijail_change_gid(jail.get(), AID_SHELL);
minijail_change_uid(jail.get(), AID_SHELL);
// minijail_enter() will abort if any priv-dropping step fails.
minijail_enter(jail.get());
D("Local port disabled");
}— In the second guide (for Nougat and higher), you have to remove the calls to minijail_change_gid and minijail_change_uid. This can be done by searching for them and replacing the bytes with a series of NOP (no operation) commands i.e 00 BF.
Below is the call to minijail_change_gid in my case (your own values might be different):

To remove the call to minijail_change_gid, I had to find and replace the following series of bytes:
6D 69 6E 69 6A 61 69 6C 5F 63 68 61 6E 67 65 5F 67 69 64 <--- before 00 BF 00 BF 00 BF 00 BF 00 BF 00 BF 00 BF 00 BF 00 BF 00 <--- after
Below is the call to minijail_change_uid in my case (your own values might be different):

To remove the call to minijail_change_uid, do the same.
— You can now save the patched adbd binary. See a sample on how to use HxD here.
Method 5: Custom Kernel
This method is much more easier. You need to install a different adbd on your phone or install a custom kernel/distribution that includes a patched adbd. This can be done by searching online. Though some custom kernels don’t come with adb root, they allow you to easily patch the adbd which is usually hard to do in production builds. Sometimes, you can come across the patched stock boot image of your device online where the developer has modified adbd to run as root. But keep in mind to always use the same version of a boot image as the one on your device.
Are There Any Other Options?
If you are not able to get adbd running as root no matter how hard you’ve tried, there’s still a workaround, capable of substituting commands like adb pull and adb push (of system files/directories), and adb remount, etc. Adb shell commands are there to save you. Though adb shell commands might take much time, but you will also be able to achieve what you wanted if adbd was running as root. Let’s look at some examples below:
— To get started, you should have a rooted device and USB debugging should be enabled on your phone.
— Before doing anything, you will have to first grant root rights to the interactive shell on your Android device using adb shell su (or adb shell, then su) since you will be working with the system root directory.
— To remount ro partitions as rw, the command is mount -o rw,remount /<partition> e.g mount -o rw,remount /system and mount -o rw,remount /vendor.
— Transferring to a PC. You have to copy items from the system root directory to the internal storage first using.
cp <path-in-root>/<filename.extension> <path-on-sdcard>
Most files in the root directory don’t have file extensions, so the command should be:
cp <path-in-root>/<filename> <path-on-sdcard>
If you choose to change directory first, then the commands should be:
cd <path-in-root> cp <filename.extension> <path-on-sdcard>
Once the item is in the sdcard, you can then pull it to your computer using the adb command:
adb pull <path-on-sdcard>/<filename.extension> <path-on-PC>
Note that copying to sdcard can also be done manually if you have a rooted device and a root file manager installed. This is way easier.
— You should be very careful when doing operations in the root directory. It’s recommended never to use the adb shell mv command (adb shell cp is safe) unless you know what your are doing.
— Transferring from a PC. This is just the reverse of the above process. adb push <path-on-PC>/<filename.extension> <path-on-sdcard> will copy the item from your computer to the sdcard of your device. Now adb shell su and then cp [or mv] <path-on-sdcard>/<filename.extension> <path-in-root> will copy [or move] the item to the root directory. See a list of adb shell commands in this article.
ADB Under Recovery
Some recovery will let you run adb commands. This can be possible on eng and userdebug builds. Some custom recoveries as well can allow adb in recovery mode. This is because custom recoveries come with a lot of modifications and provide much of their own custom binaries like adbd, sh, etc. If you unpack a custom recovery like TWRP using say AIK, you can go to the ramdisk folder then sbin to realize many of these binaries which might not be found in a stock recovery.
— A device should be listed under adb devices, either in recovery or sideload state when you run adb devices.
$ adb devices List of devices attached 05169339CG105301 recovery

— If adb devices shows the device, but in unauthorized state, then the recovery image doesn‘t honour the USB debugging toggle and the authorizations added under normal boot (because such authorization data stays in /data, which recovery doesn’t mount), nor does it support authorizing a host device under recovery. We can use one of the following options here instead.
$ adb devices List of devices attached 05169339CG105301 unauthorized
Eng & Userdebug Builds
— adbd service should be running as root by default under recovery in development builds if ro.debuggable=1 in prop.default. If adbd is not running as root in recovery mode, unpack the recovery image. Look inside the ramdisk folder and you will see a file named prop.default. Open it in a text or code editor. Change ro.debuggable=0 to ro.debuggable=1 and save.
Repack the image and flash to your device. You can then test to see if adbd is running as root while in recovery mode. This might not be possible in production builds.
— By default, adbd is always included into recovery image, as /system/bin/adbd. init starts adbd service automatically only in debuggable builds. This behaviour is controlled by the recovery specific /init.rc, whose source code is at bootable/recovery/etc/init.rc.
— Although recovery adb is built from the same code base as the one in the normal boot, only a subset of adb commands are meaningful under recovery, such as adb root, adb shell, adb push, adb pull, etc. Since Android Q, adb shell no longer requires manually mounting /system from recovery menu.
Custom Recovery
— Custom recoveries come with numerous features. You are also able to use shell commands while using a custom recovery and your device is usually detected in adb mode from recovery. This means custom recoveries should come with numerous binaries and command files. Extracting TWRP for example and going to the sbin subfolder of ramdisk, you should be able to see many binaries including sh, adbd, etc – most of the binaries that you will find in /system/bin. These might not be present in stock recoveries. The photos below show the unpacked ramdisk > sbin directory of a stock recovery (in production build) and a custom recovery (TWRP):
Stock recovery
For stock recovery that adb doesn’t run, the only time that the device is detected in adb mode under recovery is during the sideload start.

TWRP
Take note, there’s the twrp app (me.twrp.twrpapp) in one of the photos below which is installed on your device when you choose to install the TWRP app from recovery. You can manually install the app now that you have access to it [click on any of the photos below to enlarge]. The contents in the sbin subfolder have not been shown all.
Conclusion
— Like, Share & Comment 👍: We are done with our guide on how to get adbd running as root in production builds. If you find this post helpful, then scroll down to like and share. Also, drop a comment below in case of any difficulty.
— Donate ❤: Please help us to keep the site running. You can support us with whatever you have here.
— Report Broken Link, Any Error, Or Wrong Information ⚠: Is a link not working, or have you found an error that needs correction, or do you believe there’s an information you have read that is wrong, report to us here. We will verify and try to update as soon as possible. Don’t forget to give us the link that is broken or to point directly to the section that needs correction. Thanks for your loyalty.
— Contact 🗨: If you wish to contact the SakoPhone Team, then click here.
— Join Us ➕: Want to be part of the SakoPhone Team, join us here. Those eligible to join us are: Bloggers/Writers/Editors (to write helpful articles), Readers/Subscribers (to receive alert of every article we drop, Supporters (those who will cross-check articles and report errors, wrong details or broken links, provide helpful suggestions and information as well as increase traffic by sharing and recommending our articles to various platforms) and lastly Sponsors (those who can assist us financially with little donations to keep the site running).
- Author
- Recent Posts
I started writing code around 20 years ago, and throughout the years, I have gained a lot of expertise from hands-on experience as well as learning from others. This website has also grown with me and is now something that I am proud of.
The adbd cannot run as root in production builds 2022 is a standard code exception your system experiences due to the lack of root access. As a result, you must bypass the permissions checks and install a new adb shell on your machine to allow further code alterations and production builds preventing further complications.

Nevertheless, although you can experience it when your Android device fails to comply with the adb root flag, the answers take less than a minute. Hence, we developed and wrote the most sophisticated adb root magisk debugging article to teach you how to fix the error log using standard approaches and methods without further complications.
JUMP TO TOPIC
- When Does the Adbd Cannot Run as Root in Production Builds Bug Happen?
- – Running a Database Without Root Privileges
- How To Fix the Adbd Cannot Run as Root in Production Builds Exception?
- – Running the Adequate Emulator and Entering the Adbd Command
- – Modify the Binary Values Before Launching the Commands
- Conclusion
When Does the Adbd Cannot Run as Root in Production Builds Bug Happen?
The adbd cannot run as root in production builds emulator code exception usually happens when your system lacks Android Studio root permissions. In addition, this code exception can obliterate your programming experience when your Android version does not comply with the root flag and configurations, displaying a warning.
Therefore, the adb root not working mistake is inevitable when your main document or application misses the root permissions for the main commands. Although this sounds irrelevant for complex projects or files, it can ruin your fully functional script regardless of how correct the other processes are.
For example, adbd insecure Android 12 builds require specific inputs and permissions to render the commands, which, if missed, raise warnings and terminate the program. As a result, we will reproduce the adbd insecure exception using advanced syntaxes and functions, although remaking the error log is sometimes challenging due to permission flaws.
On the flip side, we confirmed a similar adbd cannot run as root in production builds Windows 11 log when the Android version does not comply with the root flag and configurations.
Henceforth, the system displays a warning documenting the flaws and inconsistencies, although you have the latest version and advanced code snippets. In addition, users can experience a similar adb root Android 11 mistake due to permission checks, which should not be surprising when completing your project.
Still, let us reproduce and display the error log before teaching and applying the solutions to your document to prevent further complications.
– Running a Database Without Root Privileges
This article’s invalid chapter exemplifies the procedure of running a database without root privileges. As a result, your system confirms the inconsistencies and indicates the failed operation, although some elements are fully functional.

So, we will show you the system’s visual output after running the emulator and opening the command prompt.
The following example provides the complete error log:
C: #Users#Ji Hoon #AppData#Local #AndroidWSdk#platform-tools>
C: #Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> #AndroidWSdk#platform-tools>
C: #Users#Ji Hoon #AppData#Local #AndroidWSdk#platform-tools> user sa
#Users#Ji Hoon #AppData#Loca IWAndroidWSdk#platform-tools> se sa
C: #Users#Ji Hoon #AppData#Local Dalam uca kaman Lo KAPPALOOTTO LOUTK
#Users#Ji Hoon #AppData#Local #AndroidWSdk#platform-tools> users WAPDALLO LOUTK
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> muser sa Dalam Mo LOOTS
Users#Ji Hoon #AppData#Loca | #AndroidWSdk#platform-tools> user sa kala
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> user sa kala
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> user sa kala
Users#Ji Hoon #AppData#Loca | #AndroidWSdk#platform-tools> user sa kala PayOOTSK
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> user sa kala
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> users on IWAPDALAM LO
Users#Ji Hoon #AppData#Loca | #AndroidWSdk#platform-tools> users on IWAPDALAM LO
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> users on IWAPDALAM LO
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> se sa KAPPALOOTTO LOUTK
Users#Ji Hoon #AppData#Loca I WAndroidWSdk#platform-tools> se sa KAPPALOOTTO LOUTK
#Users#Ji Hoon #AppData#Local #AndroidWSdk#platform-tools> st #AndroidWSdk#platform-tools>
#Users#Ji Hoon #AppData#Local
#Users#Ji Hoon #AppData#Local muser sm
#AndroidWSdk#platform-tools>
#UsersWJi Hoon #AppData#Loca I WAndroidWSdk#platform-tools>
C: #Users#Ji Hoon #AppData#Loca | #Android#Sdk#platform-tools> WAndroidWSdk#platform-tools>Is
C: #Users#Ji Hoon #AppData#Loca I AdbWinApi.dll AdbWinUsbApi.dll dmtracedump.exe
NOTICE.txt, etcltool.exe
(adb.exe, fastboot.exe)
C: #Users#Ji Hoon #AppData#Local api TATTOFOTOMS Andron aron hprof-conv.exe
libwinpthread-1.dll make_f2fs.exe lib64 COUTSK 123 make_f2fs_casefold.exe mke2fs.conf
mke2fs.exe package.xml #Android#Sdk#platform-tools> source.properties sqlite3.exe systrace X
Although we could list other elements and values, we kept the visual output as short as possible. Still, the debugging approaches apply to all syntaxes and scripts.
How To Fix the Adbd Cannot Run as Root in Production Builds Exception?
You can fix the adbd that cannot render as root in the production code exception by unlocking the bootloader. In addition, you can overcome the error log by running the adequate emulator and entering the adbd root command. Both debugging techniques prevent further complications and obstacles.
This section confirms overcoming the mistake takes a minute and works for all scripts regardless of elements and commands. Still, we suggest unlocking the bootloader as your primary debugging choice because it does not mess up other features and inputs.
However, isolating the failed document or file before implementing the debugging method is excellent, especially with complex documents and applications.
The following list helps you unlock the bootloader and fix the mistake:
- Turn off your device to initiate the procedure.
- Power on the unit by holding the power button and volume up and down keys.
- The device loads and boots into the bootloader.
- Use a USB cable to plug the device into your computer.
- Start the terminal on your machine by holding Ctrl + Alt + T.
- Type the following command line before pressing enter: sudo fastboot oem unlock
- Accept the unlocking terms on your device screen after it boots up.
- Reboot your device by pushing the power button. Your system indicates the button’s location on the start screen.
This solution applies to all devices, although the start screen differs for each operating system. Alternatively, use the following command lines if the sixth debugging steps did not fix the issue:
adb shell setprop ro.debuggable 1
adb shell setprop persist.service.adb.enable 1
adb root
This code snippet completes the debugging procedure and reenables further processes.
– Running the Adequate Emulator and Entering the Adbd Command
This article’s second solution suggests running the appropriate emulator and entering the adbd root command before launching the processes. This debugging procedure resolves the inconsistencies that failed due to the underprivileged root permissions.

As a result, the old emulator fails to render the inputs and launch the command lines, although the snippet appears fully functional. So, this method requires only two steps before displaying the correct output.
The following list teaches the necessary debugging steps:
- Open your Android virtual devices in the studio.
- Select the hardware and choose a device definition.
The system displays a visual output confirming the successful procedure. The following example provides the result after choosing the device definition:
C:#Users#Ji Hoon #AppData#Loca IWAndroid#Sdk#platform – tools > adb devices
List of devices attached
Emulator – 1564 offline
C:#Users#Ji Hoon #AppData#Loca IWAndroid#Sdk#platform – tools > adb devices
List of devices attached
Emulator – 1564 offline
C:#Users#Ji Hoon #AppData#Local #AndroidWSdk#platform – tools > adb devices
List of devices attached
Emulator – 7264 offline
C:#UsersWJi Hoon #AppData#Loca I WAndroidWSdk#platform – tools > adb root
restarting adbd as root
C:WUsersWJi Hoon #AppData#Local #Android#Sdk#platform – tools > adb shell
generic_x86: # cd /data/data/com.Hellow.example54
/system/bin/sh: cd: /data/data/com.Hellow.example54: No such file or directory
2 generic_x86:/ # cd /data/data
generic_x86:/data/data # Is android
com.android.apps.tag
com.android.backupconfirm
com.android.theme.color.purple
com.android.theme.color.space
com.android.theme. font.notoser ifsource X A
As you can tell, this stack trace does not display the code exception and indicates the system carried out the intended emulator without obstacles. However, if the bug persists and terminates your program, we suggest modifying the binary.
– Modify the Binary Values Before Launching the Commands
Changing the binary values before launching the commands is another excellent debugging procedure that works for all documents. However, you must create a new project and import the adbd binaries extracted from the original document.
Your program should analyze the Android source code and binary values, which are critical when completing your project. As a result, we will exemplify the Android source code you must target for the new project before listing the byte series.
The following example provides a good source code:
if (should_drop_privileges ()) {
drop_capabilities_bounding_set_if_needed();
minijail_change_gid (jail.get (), AID_SHELL);
minijail_change_uid (jail.get (), AID_SHELL);
// the minijail_enter() command will abort if any priv-dropping step fails.
minijail_enter (jail.get ());
D (“Local port disabled”);
}
Lastly, introduce the byte series to remove the calls to the UID and GID commands. You can learn more about this procedure in the following code snippet:
01 BF 002 BF 03 BF 04 BF <- replaced with NOPs
Your system should no longer experience the error log after implementing these solutions.
Conclusion
The adbd that cannot run as root in production code exception happens when your system lacks specific root permissions. So, let us remember this article’s critical points before fixing your project:
- The bug can occur when your Android version does not comply with the root flag and configurations
- Reproduce the stack trace by running a database without root privileges
- Unlocking the bootloader is the primary debugging procedure
- Changing the binary values before launching the commands is another excellent debugging procedure
This article proves overcoming the error log is straightforward and takes a minute, which is excellent for complex documents. We encourage you to open the application and implement the solutions.
Skip to content
Navigation Menu
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
Description
@topjohnwu So much thanks for your Magisk firstly. I have rooted my PIXEL already following your provided method successfully. It looked below when I used command of adb shell
sailfish:/ $ su
sailfish:/ #
However, I still received hint like adbd cannot run as root in production builds after I tried command of adb reboot, even I have downloaded app of adb insecure, and enabled insecure adbd and restarted adb server, it also infoed me adbd cannot run as root in production builds.
How can I do next to fix it?

You should upgrade or use an alternative browser.
-
#1
I’m running Android 13. I’ve used Magisk to root the device but the command
results in
adbd cannot run as root in production buildsI already tried «adbd Insecure v2.00.apk» but it fails with the message
Is there a way to fix this?
-
#2
/system/bin/adbd with magisk module. create new directory in /data/adb/modules and place your files
/data/adb/modules/my_module/system/bin/adbd
/data/adb/modules/my_module/module.prophttps://topjohnwu.github.io/Magisk/guides.html#magisk-modules
or escalate to privileged shell and stream file content over stdin/stdout (linux only)
adb shell "su -c 'dd bs=1m if=/dev/block/bootdevice/by-name/boot 2> /dev/null'" > boot.img
adb shell "su -c 'dd bs=1m of=/dev/block/bootdevice/by-name/boot'" < path/to/boot.img
-
#3
you can overlay/system/bin/adbdwith magisk module. create new directory in/data/adb/modulesand place your files/data/adb/modules/my_module/system/bin/adbd /data/adb/modules/my_module/module.prophttps://topjohnwu.github.io/Magisk/guides.html#magisk-modules
or escalate to privileged shell and stream file content over stdin/stdout (linux only)
adb shell "su -c 'dd bs=1m if=/dev/block/bootdevice/by-name/boot 2> /dev/null'" > boot.img adb shell "su -c 'dd bs=1m of=/dev/block/bootdevice/by-name/boot'" < path/to/boot.img
Thank you very much for your reply.
How would method 1 work? I find a different binary of adbd that has the root feature enabled and overlay the original with it through a Magisk module?
-
#4
I already tried «adbd Insecure v2.00.apk» but it fails with the message
you found already, just unzip the assets/adbd.21.png from apk
-
#5
you found already, just unzip the assets/adbd.21.png from apk
I checked the file you mentioned and it has those contents:

What should I do with them?
-
#6
adbd cannot run as root in production builds
Why do you need this?
-
#7
I would like to do some automated testing on my device using Appium to check if my website works correctly.
As I understood, adb root is needed to do it properly.
-
#8
/data/data/eu.chainfire.adbd/files/adbd.21.png: ELF executable, 32-bit LSB arm, static, stripped
-
#9
I would like to do some automated testing on my device using Appium to check if my website works correctly.
As I understood, adb root is needed to do it properly.
Basically: ADB is a commandline tool which acts as a client-server programm. You send ADB commands (usually from a desktop PC, but also possible from a rooted mobile) as a client to the adbd (daemon) on another device. The adbd executes those commands on the other device as user:shell. If you want the adbd acts as user:root then you have to execute adb root. BUT it’s not possible to grant the adbd root permissions on a stock ROM (production builds). Even if the other device is rooted with Magisk it’s still a production build!
The only way to execute commands as root via ADB on another device is
-
#10
just rename the file > adbd
/data/data/eu.chainfire.adbd/files/adbd.21.png: ELF executable, 32-bit LSB arm, static, stripped
I created the structure you recommended
/data/adb/modules/adbRoot/module.prop
/data/adb/modules/adbRoot/system/bin/adbdI opened Magisk and could see the module enabled.
Then restarted adbd
But there was still the error
adbd cannot run as root in production builds
Then I found out on this page https://source.android.com/docs/core/ota/modular-system/adbd
that adbd moved on Android 13, supposedly to this location:
/apex/com.android.adbd/bin/adbdThen I also created this file for the Magisk module
/data/adb/modules/adbRoot/system/apex/com.android.adbd/bin/adbdAgain, I restarted adb
But the result still is the same
adbd cannot run as root in production builds
Anything else I could do/something that is wrong?
-
#11
Basically: ADB is a commandline tool which acts as a client-server programm. You send ADB commands (usually from a desktop PC, but also possible from a rooted mobile) as a client to the adbd (daemon) on another device. The adbd executes those commands on the other device as user:shell. If you want the adbd acts as user:root then you have to executeadb root. BUT it’s not possible to grant the adbd root permissions on a stock ROM (production builds). Even if the other device is rooted with Magisk it’s still a production build!The only way to execute commands as root via ADB on another device is
Thank you very much for your input.
Are you saying there is nothing that can be done by replacing the adbd file or the config?
Do you think the solution by alecxs to replace the binary is not working?
-
#12
Thank you very much for your input.
Are you saying there is nothing that can be done by replacing the adbd file or the config?
Do you think the solution by alecxs to replace the binary is not working?
Still do not understand the reason. Assume the command adb root is successful. how to proceed then?
-
#13
adb root:
These criterias have to be met to execute adb root.
In case the adbd gets root permissions, then you keep the privileges to run:
adb disable-verity
enable-verity
sideload OTAPACKAGE
remount [-R]
unroot(For further information see ‘adb help’)
All the other ADB commands don’t require the adbd to be rooted.
-
#14
found some magisk modules, maybe one of these binaries work for android 13 if you place it system/apex
-
#15
To use/install the patched adbd I need a device with root permissions. Otherwise it wouldn’t be possible to copy the adbd to /system/bin and make it executable. Having that patched adbd in /system/bin, I’m able to use the command adb root which let’s me execute ADB commands with root permissions.
Why not using
? Why I need a adbd with root permissions on a rooted device?
-
#16
adb pull /dev/block/bootdevice/by-name/userdata
-
#17
@WoKoschekk most likely he don’t need it. we don’t know. but there are cases where it can be useful, for exampleadb pull /dev/block/bootdevice/by-name/userdata
Apart from the fact that it’s not possible to restore such an image (e.g. corrupted encryption) you have to copy 128GB (minus the system) or more via USB. There is a reason why TWRP saves the data as a TAR archive and splits it into 1GB chunks.
I know there are more examples for a rooted adbd. But it could all be done in a root shell, too.
-
#18
I have posted workaround for streaming partitions with su (refer to 2. method in post #2) but it does not work on windows (not even with dos2unix)
-
#19
The partition mirrors ~/dm-0 and so on are based on AVB and the device-mapper layer.
I have posted workaround for streaming partitions withsu
Yes, I know the ‘netcat’ method. Of course it’s better to have a desktop PC and its storage for large images like /data. Better than an external sd. But you could also use the device’s shell to create tar files.